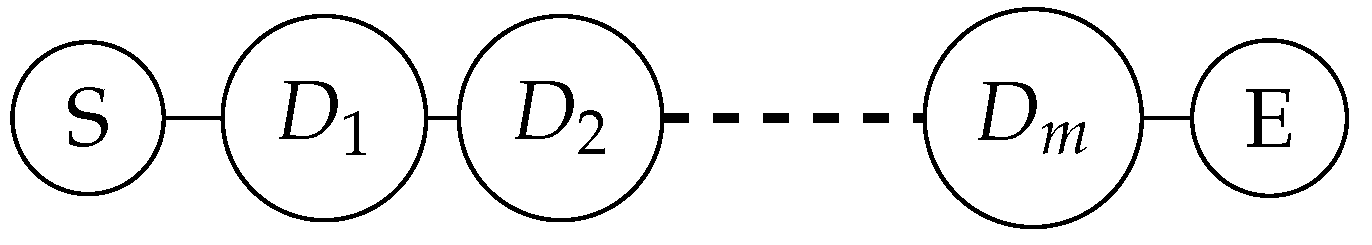1. Introduction
As cloud computing and big data become more prevalent, data security and privacy protection are increasingly important. Secure multi-party computation is a mode of computation that protects the privacy of inputs, and it has a wide range of applications in fields such as e-commerce, medical service, financial transactions, etc. Its main goal is to enable two or more parties to perform a confidential computation task without revealing their own inputs to each other or to anyone else. Yao et al. [
1] proposed the millionaire problem in 1982, which was the first to introduce the idea of secure computation. Since then, various secure multi-party computation problems have been proposed and solved, such as privacy comparison [
2,
3,
4,
5], secure summation [
6,
7,
8], set intersection and union [
9,
10], Manhattan distance [
11], and others. Secure multi-party computation in the classical domain relies on classical homomorphic encryption techniques based on hard mathematical problems. However, with the development of quantum computing technology, classical secure multi-party computation faces the threat of quantum computing. Shor’s algorithm [
12] challenges the hard mathematical problems in the classical domain. Quantum secure multi-party computation, on the other hand, is based on the principles of quantum mechanics, providing superior security performance and the ability to easily detect eavesdroppers. The BB84 quantum key distribution protocol [
13] initiated the research on quantum cryptography. Since then, many QKD protocols have been proposed and experimentally demonstrated, aiming to overcome some practical challenges, such as the rate-loss limit, the finite-key effect, and the coherent attack. In 2018, Lucamarini et al. [
14] proposed and demonstrated a QKD protocol that overcomes the rate-loss limit without quantum repeaters, using a technique called twin-field QKD. In 2021, Proietti et al. [
15] realized an experimental quantum conference key agreement among eight parties, using a quantum network based on entangled photon pairs. In 2022, Zeng et al. [
16] proposed and experimentally verified a QKD protocol that uses mode-pairing to achieve high key rates and robustness against channel noise. Gao et al. [
17] presented a simple security proof of coherent-one-way QKD, which is a QKD protocol that uses weak coherent pulses and one-way post-processing. Lavie et al. [
18] improved the coherent-one-way QKD protocol for high-loss channels, by introducing advantage distillation and decoy states. In 2023, Wang et al. [
19] performed a tight finite-key analysis for mode-pairing QKD, which reduces the key consumption and improves the key rate. Yin et al. [
20] demonstrated a quantum secure network with digital signatures and encryption. Zhou et al. [
21] achieved experimental quantum communication that overcomes the rate-loss limit without global phase tracking. Schiansky et al. [
22] implemented a quantum–digital payment system that combines QKD, quantum money, and blockchain technology. Furthermore, more and more researchers have applied quantum techniques to secure multi-party computation fields such as privacy comparison [
23,
24,
25], secure multi-party summation [
26,
27,
28], set intersection and union [
29,
30,
31], Manhattan distance [
32], etc.
In this paper, we address the quantum secure multi-party summation (QSMS) problem, a fundamental and important problem in quantum secure multi-party computation (QSMC). QSMS enables multiple parties to compute the sum of their input data in a privacy-preserving way. It serves as a building block for more complex secure multi-party computations. Let
be the participants, and
be their private data. The encryption function is f(x) and the decryption function is d(y). The goal is to securely compute the following equationtext:
In 2002, Heinrich [
33] proposed the idea of quantum summation, and collaborated with Kwas et al. [
34] in 2004 to study the problem of quantum Boolean summation. In 2007, Vaccaro et al. [
35] applied quantum summation to anonymous voting protocols. Since then, more and more researchers have started to study the problem of secure multi-party summation, and they have constructed protocols with unique features based on different quantum resources. In 2010, Chen et al. [
26] proposed quantum two-party and multi-party secure summation based on GHZ states. In 2014, Zhang et al. [
27] realized high-capacity quantum summation using single photons in polarization and spatial modes. In 2015, Zhang et al. [
36] proposed a secure three-party summation protocol without the help of a semi-honest third party. In 2016, Shi et al. [
28] constructed secure multi-party summation and multiplication protocols based on quantum Fourier transform. In 2017, Liu et al. [
37] proposed a quantum secure multi-party summation protocol based on two-particle Bell states. In 2018, Yang et al. [
38] proposed a tree-structured quantum secure multi-party summation protocol. In 2019, Ji et al. [
39] proposed a quantum secure multi-party summation protocol based on entanglement swapping. In 2021, Zhang et al. [
40] implemented a secure three-party semi-quantum summation protocol using single photons. In recent years, there have been some new research points on quantum secure multi-party summation protocols. In 2022, Ye et al. [
41] proposed a semi-quantum summation scheme that is immune to collective dephasing noise and has stronger robustness. In the same year, Shi et al. [
42] proposed device-independent secure multi-party modulo 2 summation and modulo d summation protocols based on MDI-QKD technology, using weak coherent pulses as quantum resources, and applying only simple-gate operations and Bell measurements, which have stronger practicality; Hayashi et al. [
43] proposed a quantum secure multi-party summation protocol based on secure modulo zero-sum randomness; Cai et al. [
44] pointed out that traditional secure summation protocols may suffer from impersonation attacks wherein fake data are sent by impostor parties, resulting in erroneous summation results, and proposed an improved scheme. In 2023, Wang et al. [
45] proposed an identity authentication method based on exchange encryption, which can solve the problem of impersonating parties in secure multi-party summation protocols. In the same year, Li et al. [
46] proposed a new quantum secure multi-party summation protocol based on Shamir’s threshold scheme and d-dimensional GHZ states, which uses a (k,n)-threshold method, and has a lower computational cost than the (n,n) threshold quantum secure multi-party summation protocol.
Generally speaking, researchers have conducted in-depth studies on quantum secure multi-party summation protocols using different quantum resources. However, most of these protocols are based on the quantum gate circuit model, where classical information is encoded into quantum states by fixed quantum state preparation or fixed gate operations, and the security of quantum channels is ensured by adding and measuring decoy bits; thus, the security of the information needs to be improved further. Quantum graph states, as a kind of quantum states that describe the complex entanglement relationship of multi-body quantum systems, have advantages such as scalability, measurement friendliness, and error tolerance, provide a stronger security than the methods based on the quantum mechanics itself by using random graph state structures and random encryption gate operations, which provide a new idea for quantum secure multi-party computation. But from the current point of view, quantum graph states are mainly used as a technical framework for the implementation of quantum algorithms, and the research on applying quantum graph state technology to quantum secure multi-party summation is still relatively rare. Raussendorf [
47] first proposed the concept of quantum Cluster states in 2001. Based on this, Hein et al. [
48] proposed multi-body entanglement based on quantum graph states in 2004. In 2016, Liang et al. [
49] proposed a quantum secret sharing protocol based on quantum graph states, applying the idea of matrix splitting method to the quantum domain. In 2019, Tian et al. [
50] proposed a multi-party collaborative quantum computation protocol based on redundant graph states, using a special graph state structure to achieve multi-party collaborative computation. In 2020, Dou et al. [
51] proposed protocols such as privacy comparison and multi-party secure summation based on quantum graph states, using some basic measurement properties of graph states to achieve secure multi-party summation. However, these studies only apply fixed graph state structures and fixed gate operations.
In this paper, we propose a graph state-based secure multi-party summation protocol based on previous research. First, each participant prepares a random graph state structure to hold data, encrypts data with a private key, and encodes data with random gate operations. Second, the participants send the graph state to a semi-honest third party (TP) and announce their graph state structure. We assume that the TP will follow the protocol honestly, but may try to learn additional information from the messages he receives or sends. The TP performs stabilizer measurements according to the graph state structure announced by the participants. If any stabilizer is in the −1 eigenstate, this indicates that eavesdropping or channel noise may have occurred during the transmission, the graph state structure is destroyed, and the protocol is terminated; if all stabilizers are in the +1 eigenstate, this indicates that the graph state has been securely transmitted. The TP then performs measurements according to the announced graph state structure and recovers the data bits (encrypted by the private key). Finally, after obtaining all the data, the TP performs summation and sends the summation data to the participants for joint decryption. Since the TP does not need to send quantum resources to the participants in advance, the number of participants can change at any time. The TP only needs to compute those graph states that have undergone secure transmission; thus, the protocol has higher flexibility. This paper designs a graph-based secure two-party sum protocol and two secure multi-party sum protocols (tree-shaped and ring-shaped) to adapt to different application scenarios. These protocols provide a new idea for applying graph state technology to solve secure multi-party computation problems and lay a foundation for extending other secure multi-party computation problems in the future.
The contributions of this paper are as follows:
1. We propose a secure multi-party summation protocol based on graph states, capable of solving both secure two-party summation and secure multi-party summation problems.
2. We apply the properties of graph states, such as structural security, scalability, and measurement friendliness, to solve secure multi-party computation problems, offering a novel approach to the application of graph states.
3. The protocol utilizes random graph state structures and random encryption gate operations, enhancing security and efficiency compared to previous protocols. It also allows for the dynamic addition and deletion of participants, increasing flexibility.
4. Experimental verification is also conducted to showcase its effectiveness and practicality. We prove the correctness and security analyses of the protocol. We provide detailed explanations of the application methods of various graph state properties.
The structure of this paper is shown in
Figure 1.
Section 2 introduces the basic properties of quantum graph states.
Section 3 presents the specific content of the quantum secure two-party summation protocol and secure multi-party summation protocol.
Section 4 verifies the effectiveness and practicality of the protocol through experiments.
Section 5 proves the correctness and security of the protocol, and provides a comparative analysis of the protocol. Finally,
Section 6 provides a summary and outlook.
2. Preliminaries
This section presents the fundamental notions and distinctive features of quantum graph states.
2.1. Definition of Quantum Graph States and Stabilizer
Quantum graph states are composed of many vertices and edges. Vertices represent quantum bits, and edges represent the entanglement relationship between quantum bits. G = (V,E) denotes a graph, where V represents the set of vertices, and E represents the set of edges. For any vertex , and its adjacent vertex , there is . The process of generating a graph state is as follows:
1. Apply H gate to all vertices, resulting in state;
2. Apply CZ gate to all edges, such as , to make the basis entangled.
This generates the graph state
.
Next, we introduce the stabilizer representation of graph states. Stabilizers are very helpful for understanding graph states, because they can not only describe the structure of graph states, but also verify and correct them. For each vertex , let N(a) be the set of vertices adjacent to it. Vertex a applies X gate to itself, and applies Z gate to the vertices in N(a), which forms a stabilizer for vertex a. Each vertex has a stabilizer, and all stabilizers can fix a graph state. For a graph G, its stabilizer is denoted as , where . When a stabilizer is applied to a graph state, the graph state remains unchanged, that is, .
Here are some examples of graph states and stabilizers.
It is the simplest graph state shown in
Figure 2, generated by applying the H gate and the CZ gate to
.
. From this expression, we can see that applying
to it results in
, which is obviously equal to the original expression, so its stabilizer is
. Similarly, the original expression can also be expanded as
. Obviously,
is also its stabilizer. Expanding the expression further, the final result is
, and its stabilizers are
and
.
The star graph state is shown in
Figure 3. It is expressed in Dirac notation as:
. The stabilizers are shown in
Table 1.
These are the main graph state structures that are used in this paper, and other forms of graph states are similar.
2.2. The Measurement Properties of Quantum Graph States in Various Bases
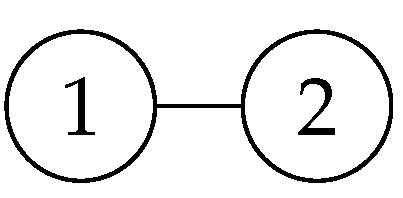
The text below explains the measurement characteristics of quantum graph states under the X and Y bases. The first is the measurement on the X basis. The properties are shown in
Figure 4.
It is easy to see that, when both X-basis measurement results are 0, it directly becomes the graph state on the right in the figure above. When the measurement result of the vertex above is 1, the Z gate needs to be applied to D; when the measurement result of the vertex below is 1, the Z gate needs to be applied to S and E.
Next, consider the graph state measured in the Y-basis, whose properties are shown in
Figure 5.
It can be easily derived that, when all three Y-basis measurement results are 0, it directly becomes the graph state on the right in the figure above. In other cases, some operations are needed. The truth table is shown in
Table 2.
2.3. Verifying the Completeness of Quantum Graph States by Stabilizer Measurement
The important role of stabilizer coding is to verify the completeness of the graph state structure. In fact, all stabilizers constitute a set of commutative mechanical complete sets for the N-qubit system [
52], so they have a set of common eigenstates. The graph state is the common eigenstate of all its stabilizer eigenvalues being
. If the graph state structure changes, bit flips (X) or phase flips (Z) occur. For some stabilizers, its commutative structure was destroyed, and the eigenvalues of the stabilizers associated with the erroneous bits became
. This is the basic principle that stabilizers can verify the completeness of graph states. Stabilizer measurement is an experimental method to implement the completeness detection of graph states, and the following steps are included: (1) Set an auxiliary bit c, initially
, to test the eigenstate of a certain stabilizer. (2) For a certain stabilizer
, apply the H gate,
gate, and H gate to the bit a, and apply the
gate to each bit b connected to a. (3) Measure the auxiliary bit c. If the result is 1, it means that the stabilizer is in the
eigenstate, the graph state structure is destroyed, or a flip occurs. It is easy to prove that, due to the special structure of the graph state, measuring the auxiliary bit c will not cause the collapse of the graph state. Note: If the measurement result of the auxiliary bit c is 0, it does not mean that the stabilizer must be in the
eigenstate, and some operations may cause the stabilizer to be in a superposition state. But if after multiple measurements all the stabilizer measurement results of the graph state are 0, the probability of graph state completeness will be very high.
2.4. Measurement Properties of Quantum Graph States under Different Quantum Gate Encodings
Finally, we discuss the changes in the graph state when X or Z gates are applied to encode data. First, we define the inverse operation of the graph state, which is performed to measure the encoded data. For a graph state
, we apply CZ gates to all connected edges, and then apply H gates to all vertices, to achieve the inverse operation of the graph state,
. If the graph state is not encoded, we have
. Next, we look at the measurement properties of the graph state for two vertices when X or Z gates are applied. For the simplest graph state, refer to
Figure 2. First, we consider applying X gate to encode data on vertex 1 and Z gate to encrypt data on vertex 2. It is easy to find that, when the data are 00 or 11, according to the property of the graph state stabilizer, the graph state remains unchanged. Perform the inverse operation on the graph state. The result is
. When the data are 10, apply the X gate to vertex 1, and the measurement result is
. When the data are 01, apply the Z gate to vertex 2, and the measurement result is
. It can be seen that, for this encoding method, the modulo 2 addition of the measurement results is the same as the modulo 2 addition of the original data. Using the same method, we can derive that, for two vertices using ZX gate, XX gate, ZZ gate to encode data can result in the same conclusion. That is to say, for the graph state of two vertices, randomly select X gate or Z gate to encode data, the measurement result of the graph state is the same as the modulo 2 addition of the original data. Moreover, if you do not know what kind of encryption gate operation is used on the two vertices, it is impossible to determine whether the data of the two vertices are 0 or 1 by the measurement result. This provides an idea for the privacy comparison and secure summation of the two participants.
To generalize the graph state situation, we examine the measurement outcomes of applying Z or X gates to a graph state with multiple vertices (e.g., three).
Figure 6 shows an example of such a graph state.
When we apply the Z gate to encode data on vertex 2, the original graph state becomes . By applying the inverse operation of the graph state, the graph state becomes . The measurement result is consistent with the encoded data. When we apply the X gate to encode data on vertex 2, the original graph state becomes . By applying the inverse operation of the graph state, the graph state becomes , that is, three bits are flipped based on the original encoded data, and the measurement result can be obtained by flipping three bits. For , by taking the second bit as the center, the 123-bit flip is realized, and the original data can be obtained at . It is easy to derive that, for multiple qubits, randomly using X gate or Z gate to encode data, the Z-bit encryption part does not need to be decoded, and the X-bit encryption part is applied with bit flip, and the original data can be obtained. Random encryption gate operations further enhance the security of the data.
Furthermore, if we apply the X gate and Z gate to encode data on vertex 2, the original graph state becomes . By applying the inverse operation of the graph state, the graph state becomes ; similarly, the result of applying Z gate and X gate encoding is . The phenomenon of 3-bit flip after applying the X gate is the same as before. For the measurement result decoding, it can be realized by flipping three bits. For and , after decoding, they become and , which are consistent with the target results that X gate and Z gate (or Z gate and X gate) want to achieve. If a series of X gates and Z gates are applied to the same bit, because , , and , it is known that it is the same as the modulo 2 addition result of the encoded data. That is to say, the data encoded by random X gate or Z gate are modulo 2 addition homomorphic, and the modulo 2 addition result of the original data can be obtained after decryption. It is also easy to find that, if multiple random gate operations are encrypted, the modulo 2 addition of the measurement results after decryption is the same as the modulo 2 addition of the original data.
That is to say, whether it is to measure after encoding the same graph state multiple times (equivalent to achieving summation during encoding), or to sum up after measuring multiple graph states separately, the same result can be obtained. This provides an idea for the secure multi-party summation of multiple participants. The specific proof will be introduced in the following sections.
3. Secure Multi-Party Summation Protocol Based on Graph State
This section presents a comprehensive overview of secure summation protocols, including a secure two-party summation protocol and two secure multi-party summation protocols based on graph state. The focus of this section is Protocol 2. We will give a specific example to illustrate how Protocol 2 is implemented, and explain the method of adding and deleting participants. Protocol 1 and Protocol 3 are simplified versions of Protocol 2.
3.1. Protocol 1: Secure Two-Party Summation Protocol
Protocol description: Alice and Bob encrypting and summing their respective data with the assistance of a third party (TP). The TP only knows the final summation result, but does not know the specific values of Alice and Bob. It should be noted that, if the TP announces the summation result, Alice and Bob can subtract the summation result from their own data, and thus infer the data of the other party. Therefore, achieving absolute security in a two-party summation protocol is not possible. However, in certain application scenarios, it may be feasible to enforce confidentiality by prohibiting the TP from disclosing the summation result. For instance, in a large-scale project bidding process, where the TP acts as the project initiator, Alice and Bob may collaborate to submit a joint bid. Both parties aim to maximize their individual amounts to maximize profits, while also striving for a competitive joint bid price. Prior to the announcement of the bid evaluation result, the TP is aware of the sum of Alice and Bob’s bids for comparison with other consortia, but the specific values of each party’s bid remain unknown to all three parties involved.
The specific secure two-party summation protocol is shown in
Figure 7.
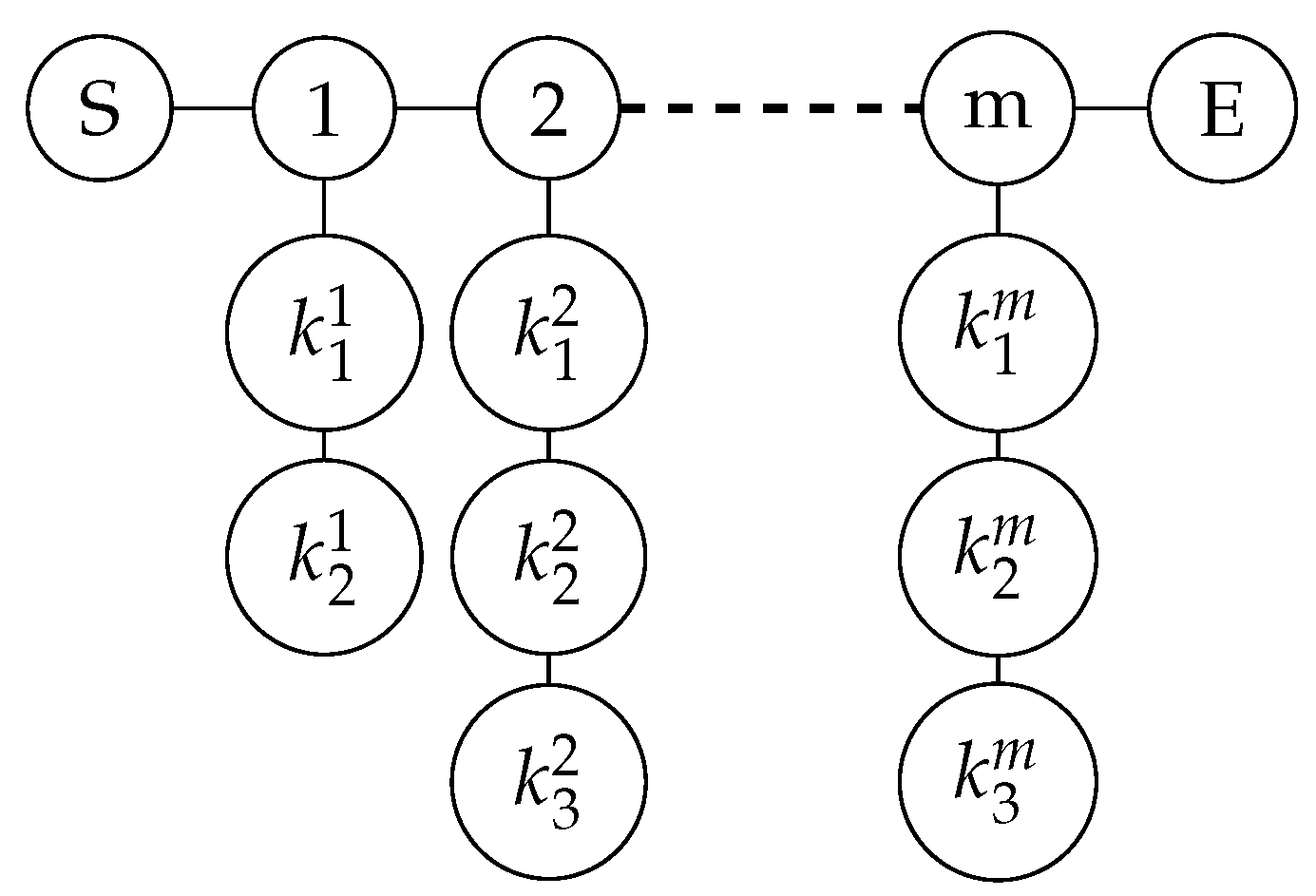
Let Alice’s data be A = {}, Bob’s data be B = {}, m is a value far greater than the number of bits of both parties’ data, which is negotiated by both parties. The protocol goal is for TP to obtain . The specific steps of the protocol are as follows:
Step 1: Prepare graph state. Participants Alice and Bob, respectively, prepare private keys
and
. According to the values of Y, participants Alice and Bob, respectively, prepare graph states, and each group of graph states includes S (start) bit and E (end) bit. If
, there are three vertices on each column, which are
,
, and
. That is to say,
denotes the vertex in the i-th column and the j-th row. If
, there are four vertices on each column, the specific form of which is shown in
Figure 8.
The randomness of the structure prevents the adversary from forging data.
Step 2: Encrypt data and encode graph state. Alice and Bob prepare private keys and , respectively. Alice and Bob first encrypt the data with X, obtaining secret strings ; . Next, let us consider Alice’s case first, and Bob’s case is similar to Alice’s. Alice determines which bit to encrypt to the data to according to the value of Y. For , the data are encrypted to ; for , the data are encrypted to . The encryption method is as follows: For , no operation is performed; for , an X or Z gate is randomly applied to the bit to be encrypted. Alice records her encryption method, i.e., records a sequence of I, X, Z (a total of m). I is for , X or Z is for . Bob encrypts the data and encodes the graph state in the same way. Alice and Bob send the encoded graph state to the TP through the quantum channel.
Step 3: Graph state verification and secure summation. After confirming that all bits have been received, Alice and Bob announce the values of Y to the TP, and the TP verifies and decodes the graph state according to the values of Y. For , the TP removes the stabilizer containing the bit, i.e., only keeps the first row of quantum bits; for , the TP removes the stabilizer containing the bit, i.e., keeps the first and second rows of quantum bits; the TP measures all the remaining stabilizers (about 1.5 m + 2), and if there is a stabilizer with a measurement result of , it means that the graph state has been damaged during transmission, and the TP terminates the protocol or notifies the sender to resend. If all the stabilizer measurement results are , the TP proceeds to the next step.
For
, the TP performs X-basis measurement on
i,
, and keeps
as D (data). For
, the TP performs Y-basis measurement on
i,
,
, and keeps
as D. The graph state is shown in
Figure 9.
According to the measurement results in the X and Y bases, the graph state is transformed into a new graph state by applying gate operations to adjust the state. The new graph state is shown in
Figure 10.
The specific methods of measuring in the X, Y bases and adjusting the graph state are described in
Section 2 of this paper. After obtaining the new graph state, the TP performs the inverse operations and measurements on Alice and Bob’s graph states and performs modulo 2 addition on the results, obtaining the secret string D. That is,
.
Step 4: Decryption. Alice and Bob make the decryption keys according to their own encryption sequences (consisting of m gate operations of I, X, and Z),
, and
. The specific method is, for each X gate, apply bit flip to the adjacent three bits in
and
. For example, if Alice applies an X gate to the i-th bit, then apply bit flip to {
,
,
}, obtaining the decryption key
; Bob makes the decryption key
according to his own encryption sequence and
. The final decryption key is obtained by performing modulo 2 addition on
and
. That is,
. There are three ways to calculate
, one is for Alice to send
to Bob, and Bob makes
and sends it to the TP. The second is for Alice and Bob to send
and
to a semi-honest third party
, and
sends the calculated
to the TP. The third is to use the property introduced in the first part of
Section 2.4 for the TP to send two vertices in a group of graph states to Alice and Bob, respectively. Alice and Bob randomly choose X or Z gates to encode according to their own data, and the TP calculates the modulo 2 sum of Alice and Bob’s decryption keys.
In summary, after the TP obtains , it can decrypt the sum data D, . The protocol ends. is the final summation result.
3.2. Protocol 2: Secure Multi-Party Summation Protocol
Protocol description: Multiple participants encrypt and sum their respective data with the assistance of a third party (TP). The TP only knows the final summation result, but does not know the specific values of each participant. This protocol is developed based on the secure two-party summation protocol, and has a wide range of application scenarios in the current technology background of cloud computing and big data. Let
be the set of participants, and
be the k-th participant. Let
’s data be
, where m is a value far greater than the number of bits of each participant’s data agreed by all participants, and the goal of the protocol is to obtain
without leaking
. The secure multi-party summation protocol is shown in
Figure 11.
The specific steps of the protocol are as follows:
Step 1: Prepare the graph state. Each participant generates a random key
, and prepares the graph state according to the value of Y. When
, there are three vertices on each column; when
, there are four vertices on each column, the specific form of which is shown in
Figure 8.
Step 2: Encrypt the data and encode the graph state. Each participant prepares a random private key , and encrypts the data, obtaining the secret string . According to the value of , prepares the third group of random private keys , where the rule is: when , ; when , , that is, randomly choose X or Z gate. At this point, each participant has three groups of random keys, each with its own function: is used to encrypt the original data, preventing the TP from obtaining the original data by inference after measurement; is used to randomly select the graph state structure, preventing eavesdroppers on the quantum channel from obtaining the data; is used to encrypt the data with random gate operations, preventing eavesdroppers from stealing the data after the participants disclose the value of .
Next, use the graph state to encrypt and encode: determines which bit to encode the data to according to the value of . For , encode the data to ; for , encode the data to . The encryption method is to apply the corresponding gate operation to the bit according to the value of {}. sends the encoded graph state to the TP through the quantum channel.
Step 3: Graph state verification and secure summation. After confirming that all the bits have been received, all the participants P disclose the value of Y, and the TP verifies and decodes the graph state according to the value of Y. For , the TP removes the stabilizer containing the bit, that is, only keeps the first row of quantum bits; for , the TP removes the stabilizer containing the bit, that is, keeps the first and second rows of quantum bits; the TP measures all the remaining stabilizers (about 1.5m+2 for each participant), and if there is a stabilizer with a measurement result of , it means that the graph state has been damaged during transmission, and the TP terminates the protocol or notifies the sender to resend. If all the stabilizer measurement results are , the TP proceeds to the next step.
For
, the TP performs X-basis measurement on
i,
, and keeps
as D (data). For
, the TP performs Y-basis measurement on
i,
,
, and keeps
as D. The graph state is shown in
Figure 9.
According to the measurement results in the X and Y bases, the graph state is transformed into a new graph state by applying gate operations to adjust the state.The new graph state is shown in
Figure 10.
After obtaining the new graph state, the TP performs the inverse operations and measurements on each participant’s graph state and applies modulo 2 addition to the results, obtaining the secret string .
Step 4: Decryption. Any participant makes the decryption key according to and . The specific method is, if , apply bit flip to the adjacent three bits {, , } in ; if or I, do nothing, and obtain the decryption key .
The TP randomly selects a participant , and sends the secret string D to him through the classical channel. The participant decrypts the data D as , and then selects the next participant from the pool of participants to be decrypted. Note that, to prevent the participants from colluding to crack the data of other participants, should randomly select when choosing. sends to , and decrypts as , until the last participant , decrypts as .
announces the final summation result . The protocol ends.
3.3. An Example of Protocol 2
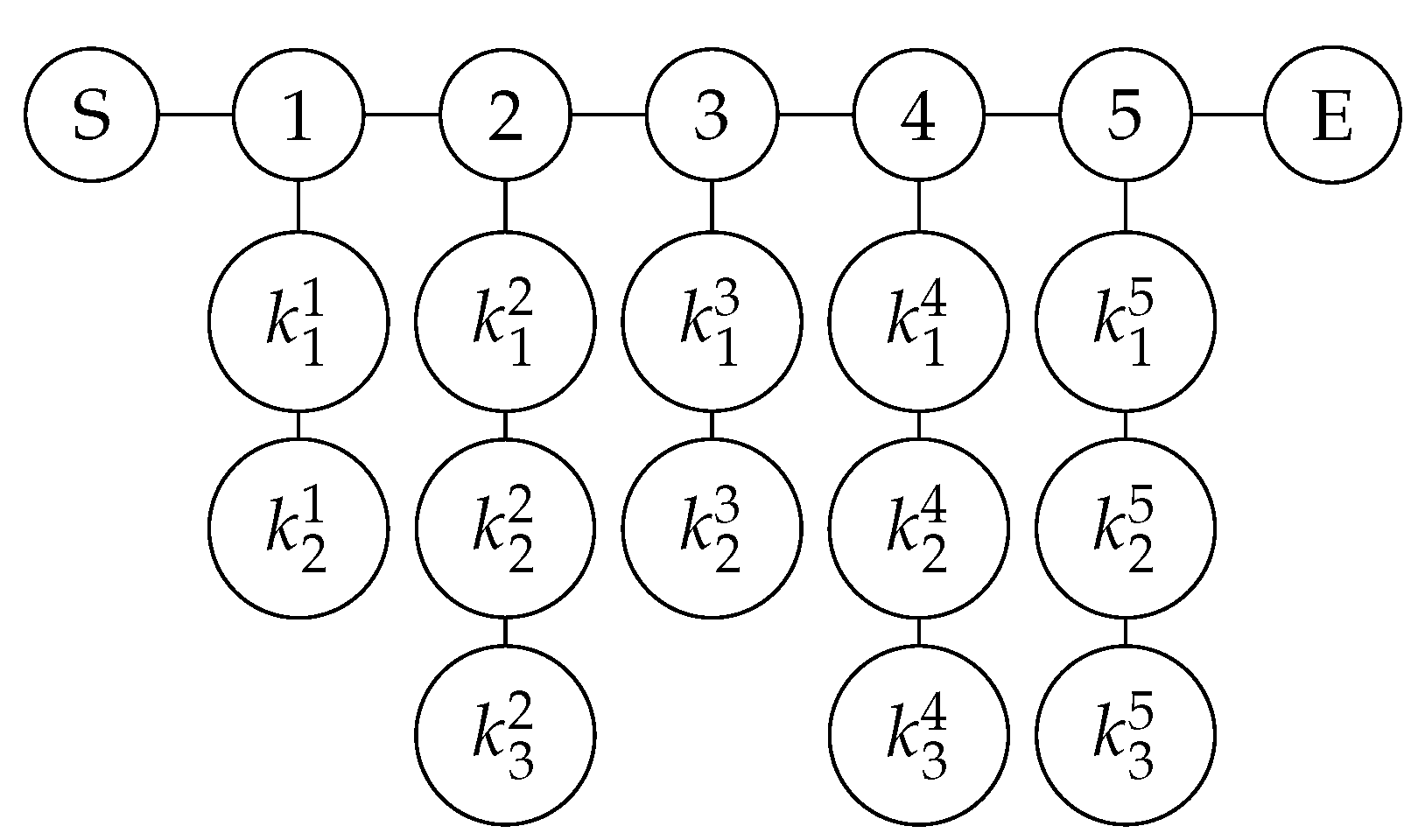
Suppose there are three participants, holds the data 0101010, holds the data 0011010, holds the data 0110100, and the expected sum result is .
Step 1: Prepare the graph state. Each participant generates a random key , , , and prepares the graph state according to the value of Y; when , there are three vertices on each column; when , there are four vertices on each column.
Step 2: Encrypt the data and encode the graph state. The three participants randomly generate private keys , , , and encrypt the data, obtaining the secret string , , . According to the value of S, the three participants P make the key Z, , , . The three participants determine which bit to encode the data to according to the value of Y. For , the data are encoded to the third quantum bit on the column; for , the data are encoded to the fourth quantum bit on the column. The encryption method is to apply the corresponding gate operation to the bit in the set of {}. sends the encoded graph state to the TP through the quantum channel.
Step 3: Graph state verification and secure summation. After confirming that all bits have been received, all participants P announce the value of Y, and the TP verifies and decodes the graph state according to the value of Y. Taking participant
as an example,
. When
, the TP removes the stabilizer containing the bit
, that is, only keeps the first row of quantum bits; when
, the TP removes the stabilizer containing the bit
, that is, he keeps the first and second rows of quantum bits; the following situations are similar. The final determined stabilizers are shown in
Table 3.
The TP performs stabilizer measurement; if there is a stabilizer with measurement result of , it means that the graph state has been damaged during transmission, and the TP terminates the protocol or notifies the sender to resend. If all stabilizer measurement results are , the TP continues to the next step.
The TP simplifies the graph state; for , the TP applies X basis measurement to i and , and keeps as (data). For , the TP applies Y basis measurement to i, , and , and keeps as . Afterwards, the TP obtains a 1D linear graph state, the TP applies the inverse operation and measurement to the graph state, and obtains the measurement result. , , , .
Step 4: Decryption. The three participants calculate the decryption key separately, if , apply bit flip to the adjacent three bits {, , } in X; if or I, do nothing, and obtain the decryption key , , . The TP randomly selects a participant , taking as an example, and sends the secret string D to him through the classical channel. The participant decrypts the data D as , selects the next participant from the pool to be decrypted, taking as an example, , the same operation, . This is the final sum result, which is consistent with the expected sum result, and the protocol ends.
3.4. Adding or Deleting Participants
Based on the secure multi-party summation protocol provided in this paper, participants can be added or deleted arbitrarily. Due to the fact that the TP does not need to prepare quantum states in advance and send them to the relevant participants, how many participants participate in the summation is completely determined by the participants themselves. Before the decryption operation in step 4 is executed (the TP can announce a deadline), all participants can freely choose to participate or quit. The added participants can participate in this round of secure multi-party summation calculation by sending the graph state to the TP and announcing their graph state structure; participants who have participated and announced the graph state structure can also notify the TP that they no longer participate in this round of secure multi-party summation calculation. In addition, if the graph state submitted by some participants fails the stabilizer measurement, then the participant cannot participate in this round of calculation, and the protocol can still be executed normally. After the deadline, the TP no longer accepts new submissions. The TP sums up the data of the participants who passed the stabilizer measurement. And send the sum result to the qualified participants for joint decryption, and to obtain the final sum result.
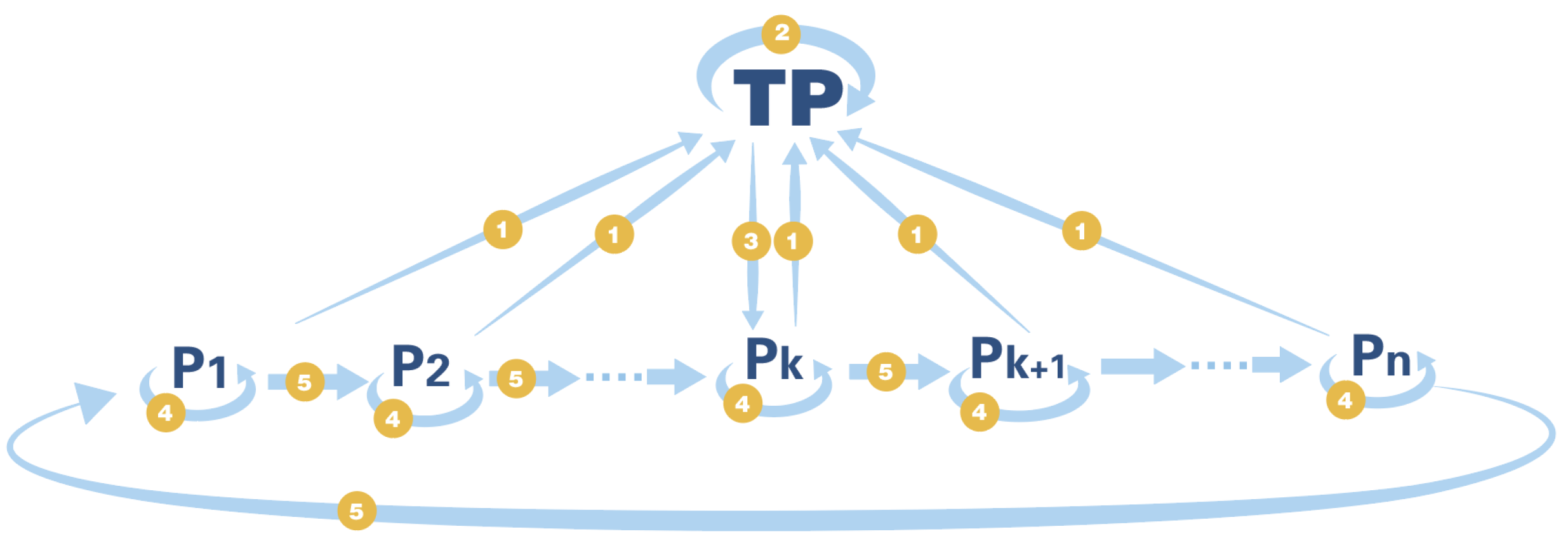
3.5. Protocol 3: A Simplified, Ring-Shaped Secure Multi-Party Summation Protocol without TP
Protocol description: Based on protocol 2, we propose a simplified, ring-shaped secure multi-party summation protocol without the help of a semi-honest third party. Let n participants be
. Let
hold the data
, the goal of the protocol is to obtain
without leaking
. The specific protocol is shown in
Figure 12.
The following are the specific steps of the protocol:
Step 1: Select the initial participant and prepare the graph state. The system randomly selects a participant
as the initial participant, who prepares the initial graph state is shown in
Figure 13.
Step 2: Encrypt data and encode graph state. Each participant prepares a random private key , and encrypts the data, obtaining the secret string . According to the value of , prepares a second group of random private keys , where the rule is: when , ; when , , that is, randomly choose X or Z gate. At this point, each participant has two groups of random keys, is used to encrypt the original data, preventing other participants from measuring and stealing the original data; uses random gate operations to encrypt the data, preventing external attackers from eavesdropping and stealing the data.
Next, use the graph state to encrypt and encode: applies the corresponding gate operation to the bit according to the value of {}, noting that the S and E bits are not encoded. sends the encoded graph state to the next participant through the quantum channel, and detects whether the quantum channel is eavesdropped by adding decoy bits, announcing positions, measuring, etc.
Step 3: Secure summation. After all participants have encoded their data in turn, they send it back to the initial participant , who performs the inverse operation and measurement on the jointly encrypted graph state of all participants, obtaining the modulo 2 sum of the secret strings of n participants . The modulo 2 process is completed during the gate operation of n participants on the graph state. The measurement result D is the result after the modulo 2 sum.
Step 4: Joint decryption. The initial participant makes the decryption key according to encryption sequences and . The specific method is, if , apply bit flip to the adjacent three bits {, , } in ; if or I, do nothing, and obtain the decryption key . decrypts the data D as , and then randomly selects the next participant from the pool of participants to be decrypted. sends to , and decrypts as , until the last participant , decrypts as .
announces the final summation result . The protocol ends.
4. Experimental Verification
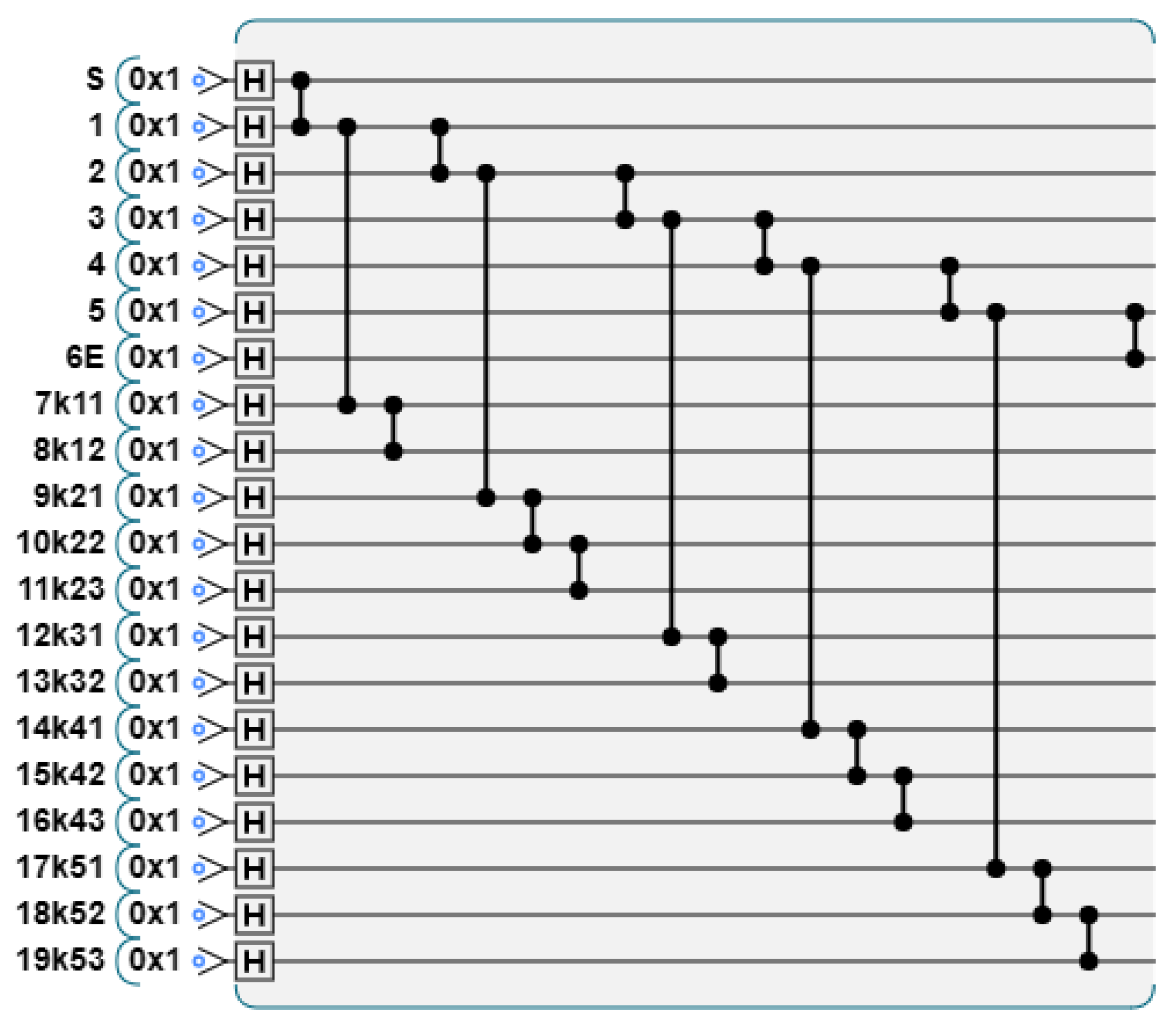
To verify the correctness and practicality of the protocol, we conducted experimental verification using IBM’s quantum cloud platform. Protocol 1 and Protocol 3 are simplified versions of Protocol 2. For simplicity, we take Protocol 2 as an example for experimental verification. We will explain step by step how to conduct the experiment according to the steps of Protocol 2. For convenience of presentation, we define the data bit m = 5, the number of participants n = 3, and considering that QCEngine shows quantum circuits more friendly, some key algorithms of quantum circuits are shown by QCEngine.
Step 1: Prepare graph state. Each participant prepares a graph state according to the value of Y. We take
as an example, whose Y value is
. When
, there are three vertices on each column; when
, there are four vertices on each column. The graph state structure prepared according to the Y value is shown in
Figure 14.
The generated quantum circuit diagram is shown in
Figure 15.
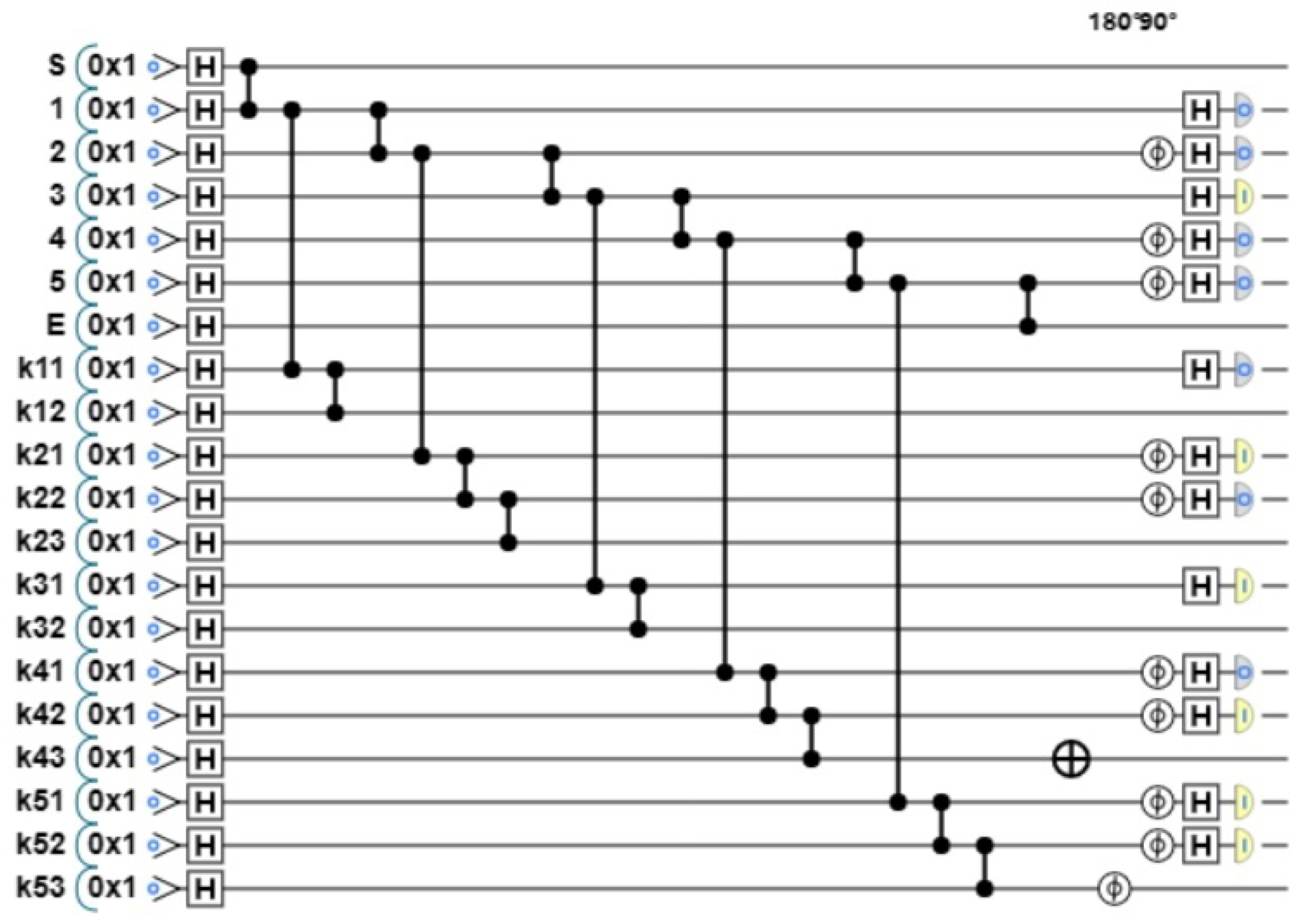
Step 2: Encode the graph state. Each participant encodes the graph state according to their own data. We take
as an example. Its data are
, and the randomly generated private key is
.
. According to the value of S,
made the key
, and the quantum circuit diagram after encoding is shown in
Figure 16.
For simplicity, the transmission and reception of quantum bits are no longer simulated. It is assumed that the TP has received the graph state submitted by .
Step 3: Graph state verification and secure summation. announces the value of Y, and the TP verifies and decodes the graph state according to the value of Y. For
, the TP removes the stabilizer containing the bit
, that is, only keeps the first row of quantum bits; for
, the TP removes the stabilizer containing the bit
, that is, keeps the first and second rows of quantum bits. The Y value of
is
, and the stabilizer of the graph state is shown in
Table 4.
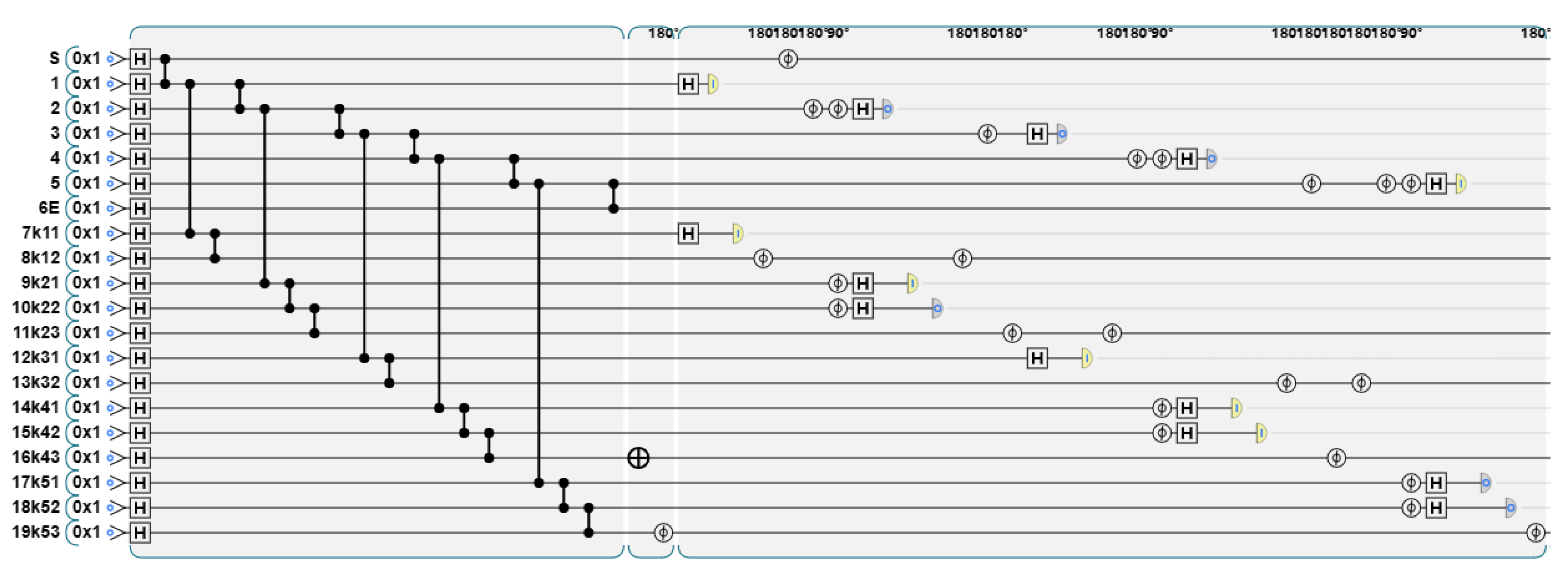
We take vertex 4 as an example to perform stabilizer measurement. The quantum circuit diagram after stabilizer measurement is shown in
Figure 17.
The TP can confirm whether the quantum graph state has been eavesdropped during transmission by multiple measurements. If the graph state structure remains intact, all stabilizers are in the +1 eigenstate, and the auxiliary bit is consistent with the initial setting value. If the graph state structure changes or some bit is affected by entanglement measurement, measurement retransmission or pauli gate, etc., the auxiliary bit will flip, and the eavesdropping behavior will be detected.
For the graph state that has passed the stabilizer measurement, the TP will simplify it according to the announced graph state structure, and adjust the graph state to a linear shape to facilitate the summation operation. As mentioned earlier, according to the graph state structure announced by
, the TP performs the measurement, and the graph state structure obtained is shown in
Figure 18.
The quantum circuit diagram is shown in
Figure 19.
According to the results of X-basis measurement and Y-basis measurement, the original graph state is adjusted appropriately, and the new graph state structure is shown in
Figure 20.
The adjustment method according to the measurement results is detailed in
Section 2. One of the cases of the quantum circuit diagram is shown in
Figure 21. Apply X-basis measurement to vertex 1 and
, and the measurement result is 11. According to the adjustment rule, apply Z gate to
, and apply Z gate to S and vertex 2. Then,
replaces vertex 1. Apply Y-basis measurement to vertex 2,
, and
, and the measurement result is 010. Apply Z gate to
, vertex 3, and
. Then,
replaces vertex 2. Apply X-basis measurement to vertex 3 and
, and the measurement result is 01, apply Z gate to
and vertex 4; then,
replaces vertex 3. Apply Y-basis measurement to vertex 4,
, and
, and the measurement result is 011, apply Z gate to
; then,
replaces vertex 4. Apply Y-basis measurement to vertex 5,
, and
, and the measurement result is 100, apply Z gate to
; then,
replaces vertex 5. At this point, the original graph state has been adjusted to a linear shape.
The TP applies the inverse operation and measurement of the graph state. The quantum circuit diagram and the result are shown in
Figure 22 and
Figure 23.
The figure shows the measurement results of the vertices S to E and the newly added vertices D1–D5. For simplicity, we omit the measurement results of other nodes. From the measurement results, it can be seen that the original vertices 1–5 are in the maximum entangled state, and the data-carrying D1–D5 are in the unique eigenstate. The data carried are 0001000, corresponding to the vertices S, D1, D2, D3, D4, D5, E, respectively. In this way, the encrypted data of are obtained.
The TP performs the above operations on the graph states submitted by all participants and obtains the measurement results, as shown in
Table 5.
The TP sums up the measurement results .
Step 4: Joint decryption. Each participant makes a decryption key according to and . The specific method is, if , apply bit flip to the adjacent three bits {, , } in ; if or I, do nothing, and obtain the decryption key . For this example, , , . The TP randomly selects a participant , and sends the secret string D to him through the classical channel. In this example, it is assumed that the three participants decrypt in turn. , , , is the final summation result, and the protocol ends.
Verification: The original data sum is , removes the head and tail vertices S and E, which is consistent with the expected result, further confirming the correctness and effectiveness of the protocol.