1. Introduction
Quantum computation maps information processing into the manipulation of (typically microscopic) physical systems governed by quantum mechanics. Although quantum computation holds the promise to solve problems that are believed to be classically intractable, practical quantum computation suffers from various noise sources, ranging from fabrication defects and control inaccuracies to fluctuations in external physical environments. Such noise greatly hinders the practicability of quantum computation on unprotected, bare physical qubits beyond proof-of-concept demonstrations.
While any kind of error is unwanted and would possibly affect the quality of the computation processes, there is a significant difference between the harmfulness of different types of errors. The most “benign” error happens locally and independently on single qubits; such errors can, in principle, be compressed arbitrarily with quantum error correction under reasonable assumptions on the error rates [
1,
2]. More-malicious errors might introduce time correlations (e.g., non-Markovian errors) or space correlations (e.g., crosstalk) and are more challenging to mitigate. Of particular interest is the
leakage error, where a piece of quantum information escapes from a confined, finite-dimensional Hilbert space used for computation, called the
computational subspace, to a
leaked subspace of a larger Hilbert space. Such escaped information might undergo arbitrary and uncontrolled processes and is harder to detect, let alone correct. More seriously, typical frameworks of quantum error correction only deal with errors happening within the computational subspace and are either unable to be applied or scale poorly with the leakage error. It is, thus, of great importance to be able to detect, correct, or even suppress leakage errors in order to conduct large-scale quantum computation.
This paper focuses on estimating the leakage error rate associated with a given quantum processor, preferably efficiently and accurately. This task is part of a process usually referred to as benchmarking, providing an estimate of certain characteristics of a piece of the quantum device before proceeding with subsequent actions. In the context of leakage benchmarking, the information can be used as a criterion to accept or abort a newly fabricated quantum processor or as feedback information on leakage-suppressing gate schemes.
Given the diverse nature of errors occurring in quantum computation, many different benchmarking schemes have been proposed over the years. A large class of benchmarking schemes, collectively called
randomized benchmarking (RB), extracts error information from the fit result of multiple experiments with different lengths [
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14]. Compared to tomography-based methods or direct fidelity estimation [
15,
16], RB schemes are typically more gate-efficient, and the fitting results are typically insensitive to state preparation and measurement (SPAM) errors, making them ideal candidates for benchmarking gate errors. These protocols have been successfully implemented in many quantum experiments [
17,
18,
19,
20,
21].
The first theoretical framework for RB-based leakage benchmarking was given by Wallman et al. [
22]. Without any prior assumption on the SPAM noise, this protocol was able to provide an estimate for the sum of the leakage rate and the
seepage rate, i.e., the rate information in the leaked subspace comes back to the computational subspace. Refs. [
8,
23] later gave a detailed analysis of the protocol and illustrated this framework with several examples relevant to superconducting devices. The authors were also able to differentiate the leakage from the seepage with reasonable assumptions on the SPAM noise. Based on these protocols, several experimental characterizations of single-qubit leakage noise have been proposed in superconducting quantum devices [
24,
25], quantum dots [
26], and trapped ions [
27].
There are two major limitations to the existing protocols [
8,
11,
22,
23]. First, all protocols require that the quantum gates act nontrivially on the leakage subspaces, in order to eliminate non-Markovian behavior originating from residual information stored in the leakage subspace. As most practical gate schemes only focus on their actions on computational subspaces rather than the leakage subspaces, leakage benchmarking schemes built upon them typically do not work in general, multi-qubit quantum systems. Second, most existing protocols can only estimate the sum of the leakage rate and the seepage rate without prior knowledge of SPAM noise, and the SPAM information is required if we need to obtain the leakage and seepage rates separately. As there is typically only one set of state preparation and measurements within one run of benchmarking, the SPAM errors do not become amplified and cannot be measured accurately [
28]. Such inaccuracy would further affect the accuracy of gate leakage rate estimation. A natural question arises:
How can one characterize the leakage rate of a multi-qubit system without operating the leakage subspace while maintaining robustness to SPAM noise?In this paper, we propose a leakage benchmarking scheme based on RB, dedicated to benchmark leakage rates on multi-qubit systems. Compared to existing protocols requiring the leakage subspace to be fully twirled, our scheme only requires having access to the Pauli group with gate-independent, time-independent, and Markovian noise. Assuming each qubit has only one-dimensional leakage space, such a gate set does not twirl the leakage subspace as a whole, but instead twirls each invariant subspace of the Pauli group individually. This allows us to formulate the LRB process as a classical Markovian process between different invariant subspaces, which can be described by a Markovian
Q-matrix [
29]. The leakage and seepage rates of the system can then be estimated by leveraging the spectral property of the Markovian process, which can, in turn, be estimated similarly to RB protocols on the computational subspace.
The
Q-matrix has a dimension exponential with respect to the number of qubits in general, and thus, the spectral property is hard to measure using LRB experiments. To further simplify the problem, we studied the spectrum of the
Q-matrix in two physically motivated scenarios: The first model, named
leakage damping noise, assumes that leakage happens at most one qubit and leakage does not “hop” from one qubit to another, which is the generalization of amplitude damping noise [
30] in the computational subspace; the second model assumes that each qubit undergoes an independent leakage process. In both cases, the spectral property of the
Q-matrix can be significantly simplified and easier for data analysis. We also show how to calculate the corresponding average leakage rates on the above two noise scenarios of the proposed LRB protocol. As an illustration of the leakage damping noise model, we found that the noise model of commonly used two-qubit gates such as iSWAP, SQiSW, and CZ gates belongs to this form.
Building upon the foundation of leakage randomized benchmarking (LRB) protocols, we delve deeper into the study of leakage benchmarking for specific multi-qubit gates, which is a crucial aspect of quantum hardware development. To this end, we propose an interleaved variant of the LRB (iLRB) protocol that allows for the benchmarking of individual gates, rather than a set of gates. We show that the leakage rate can be extracted in general for arbitrary target gates with access to noiseless Pauli gates and performed a more-careful analysis when Pauli gates were implemented as noisy. In addition, we show that the leakage rate of the target gate can still be extracted under certain physically motivated assumptions that inherently apply to flux-tuning gates in superconducting quantum computation. To demonstrate the applicability of the iLRB protocol, we applied it to the case of flux tunable superconducting quantum devices [
31], constructed its noise model, and benchmarked the leakage rate of the
gate.
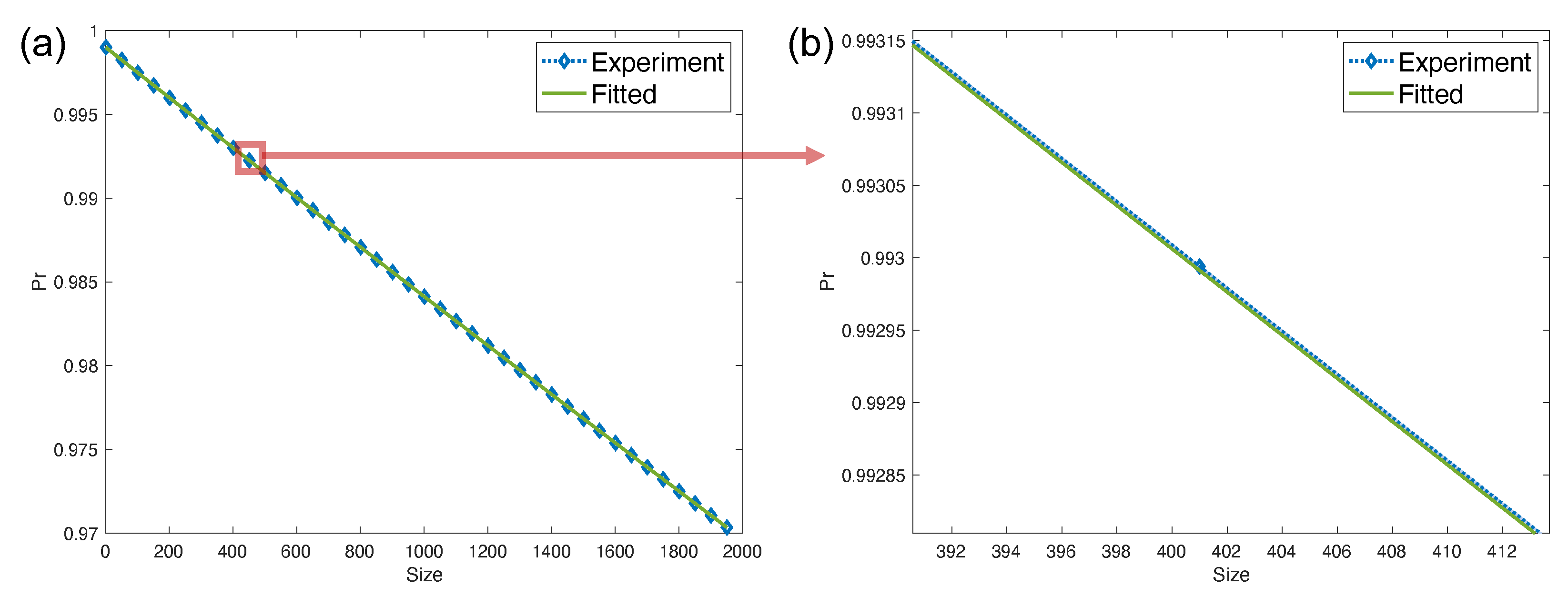
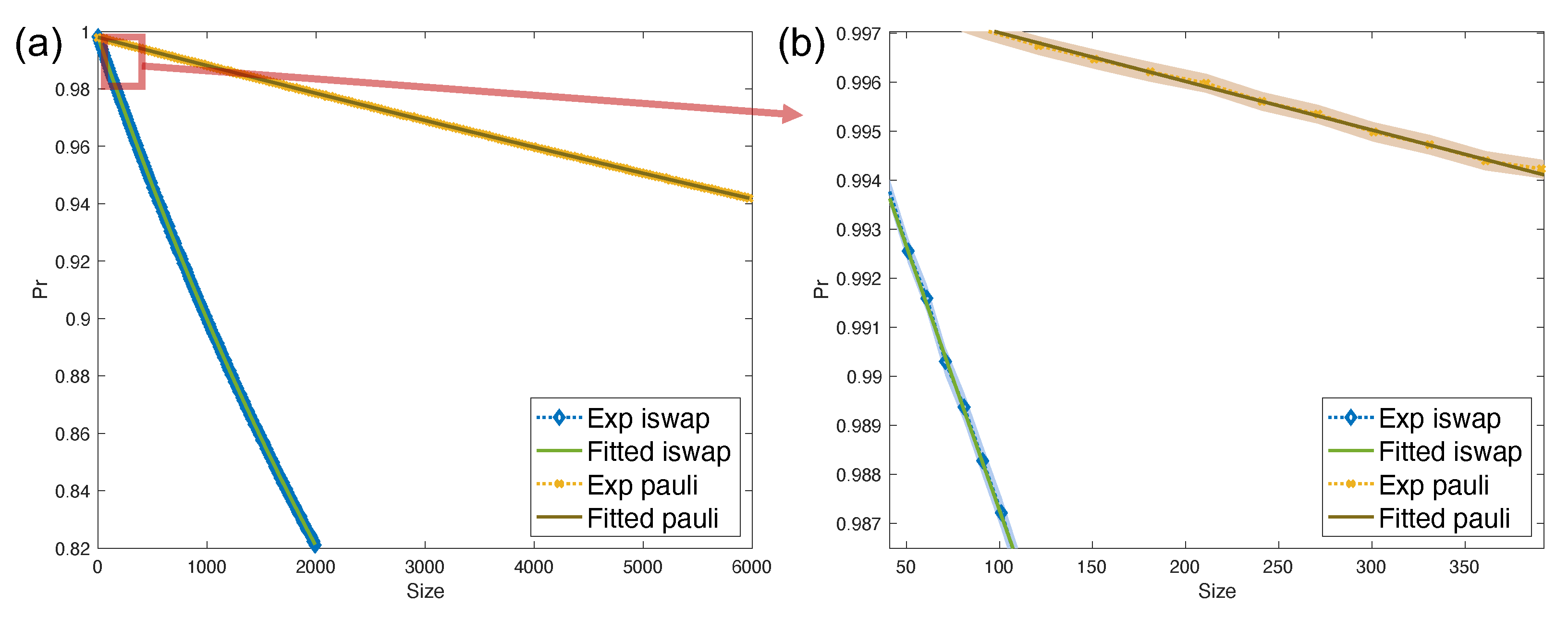
This paper targets both theorists and experimentalists, as it seeks to establish an experiment-friendly leakage benchmarking scheme. We offer a thorough theoretical analysis for multi-qubit scenarios, as well as a numerical verification of the average leakage rate for the iSWAP gate. This was achieved by extracting the noise model of the iSWAP gate from its Hamiltonian evolution.
In
Section 2, we introduce the fundamental concepts and notations.
Section 3 presents our LRB protocol and analyzes the calculation of the average leakage rate using this method. In
Section 4, we provide a detailed examination of the average leakage rate under two leakage models: single-site leakage and no crosstalk.
Section 5 proposes the iLRB protocol for any target gate that commutes with the noise channel, focusing on a special leakage damping noise. In
Section 6, we numerically validate the LRB and iLRB protocols. Additionally, we introduce the leakage damping noise model for
gates in flux-tunable superconducting quantum devices, based on their Hamiltonian evolution. We also tested the iLRB protocols numerically using the noise model of the
gate. Finally,
Section 7 concludes the paper with a discussion of our work and suggestions for future research directions.
2. Notations
In order to characterize leakage, we assume that the quantum states lie in a Hilbert space with finite dimension d that decomposes into a computational and a leakage subspace, denoted as and respectively. Let and be the dimensions of and . Unless explicitly specified, we assume throughout the paper that a single qubit (site) lies in a three-dimensional Hilbert space with basis , where the computational subspace is spanned by and the leakage subspace by . In other words, higher-level excitations of a qubit can be ignored. We call such a system a single qubit with leakage.
A composite system of n qubits with leakage lies in a Hilbert space , where () represents the computational (leakage) subspace of the qubit k. We define the computational subspace of be where no qubits leaks, that is, . Hence , and . The projector on the computational subspace is a tensor product where is the projector onto the computational subspace on the k-th qubit. Note that the projector onto the leakage subspace on the k-th qubit is and the projector onto the leakage subspace , where is the identity operator on . For each , we define to be the subspace where qubit k is leaked if and only if . The corresponding projector onto is . Note that , and . For each Hilbert space , denote the trace-normalized projector associated to the projector .
We assume the noise of interest to be Markovian and time-independent throughout this paper. Given an ideal unitary
, we denote
as the corresponding ideal unitary channel acting on the whole space. Given a completely positive trace-preserving (CPTP) channel
characterizing the noisy implementation of
, we further denote
as the noise information of
accounting leakage. Note that
as
is a unitary channel. The average leakage and seepage rates of a channel
are defined as [
23]
We often write
and
when the noise channel
being referred to is unambiguous. Unless explicitly specified, we use the term “leakage noise” to represent both leakage and seepage errors.
The Pauli group with phase is defined as , where are Pauli-X/Y/Z matrices respectively. Let . For an element , its corresponding ideal unitary channel in the full space is defined as . For sake of simplicity, we identify the element P with its corresponding ideal channel , and use as a shorthand for the corresponding noisy implementation .
Inspired by the Pauli-transfer matrix (PTM) representation [
32], here we define the
condensed-operator representation of linear operators as the Liouville representation [
33] with respect to the orthonormal operator basis
. The basis is not complete in the sense that it does not span
; for a linear operator
not lying in the span of
,
is understood as the projection of
onto the span of
followed by the vectorization, that is,
where
is the
twirling projector from
to
.
For sake of clarity, in the following, we represent the condensed operator representations under the basis
, and the adjoints under the basis
. Note that
. Under such basis choice, for a generic linear operator
, we have
For a superoperator
, the corresponding condensed operator representation is then
Since
does not form a complete basis, compositions of condensed operator representations do not directly translate to compositions of the corresponding linear operators; rather they translate to compositions of the twirled versions of the corresponding linear operators through the twirling projector
. More specifically, we have
We denote
throughout the paper.
3. Leakage Randomized Benchmarking Protocol
Here we present a leakage randomized benchmarking protocol that does not require actions on the leakage subspace or assumptions about SPAM errors. Our protocol is based on the assumption that the noise, represented by the operator , is Markovian, time-independent, and gate independent. We further assume we have access to a noisy measurement operator close to the projector to the computational subspace .
- (1)
Given a sequence length m, sample a sequence of m Paulis from uniformly i.i.d., and perform them sequentially to a fixed (noisy) initial state , obtaining . Measure the output state under and estimate the probability through repeated experiments.
- (2)
Repeat Step (1) multiple times to estimate , the expectation of under random choices of from .
- (3)
Repeat Step (2) for different m, and fit to a multi exponential decay curve .
The average leakage rate and seepage rate are estimated with the fitted exponents . The number of exponents for depends on the specific noise model of . In the following, we will show the explicit representation of and .
The Pauli group
can twirl any quantum state in computational subspace to the maximum mixed state [
34,
35], i.e.,
, where
is a quantum state in computational subspace. Here we expand the twirling of a Pauli group from computational subspace to the entire Hilbert space, as shown in Lemma 1.
Lemma 1. Let be the twirling projector such that for any quantum state ρ. Then it can be equivalently represented as the expectation of all the Pauli channels, Lemma 1 can be obtained from the twirling properties of Pauli group
in the computational subspace. We postpone the proof of Lemma 1 into
Appendix A. With Lemma 1, we can construct the connections of
and the multi-exponential decay curve
, as shown in the following theorem.
Theorem 1. Given Pauli group with gate-independent leakage error channel Λ, the average output probability in LRB protocol , where is the condensed-operator representation of Λ and is some noisy state determined by the input state . The average leakage rate equals and the average seepage rate equals .
Proof. Let
be the ideal gate elements sampled from
. Then the expectation of the probability for measuring computational basis equals
where
is the input state with state preparation noise. Equation (10) holds by Lemma 1; Equations (13) and (14) follows from Equations (6) and (
4) respectively.
By the definition of
Q, we have
Moreover, for every
it holds that
since
preserves the trace. This indicates that
Q is a Markov chain transition matrix. By the definitions of
and
in Equation (2), we have
and
□
Theorem 1 demonstrates that Pauli-twirled quantum channels with leakage can be represented as Markov chains operating on distinct leakage subspaces, including the computational subspace itself. The leakage properties can be inferred from the spectral characteristics of the transition matrix, akin to analyses of RB protocols in the computational space [
36]. However, this framework does not directly provide an easily applicable LRB scheme, as the transition matrix
Q typically has a dimension of
, resulting in complex matrix exponential decay behavior as the number of qubits increases.
Nonetheless, estimating the leakage rate can be significantly simplified in scenarios where the number of qubits is small enough to allow manageable matrix exponential decay or when additional assumptions can be made about the leakage behavior. In the subsequent sections, we propose several physically relevant leakage noise models with straightforward theoretical exponential decay curves suitable for experimental implementation.
4. Average Leakage Rate for Specific Noise
In this section, we present two specific leakage noise models—single-site leakage damping noise and crosstalk-free leakage noise. We also provide the respective average leakage rates for each model.
In the following, we investigate the average leakage rate for specific leakage noise where leakage only happens on a single site (qubit). For any
, we define
such that
forms a basis of the specific leakage subspace
where only the qubit
i is leaking. Let
be the leakage subspace that exactly one qubit is leaking, with the corresponding basis set
. We propose a
single-site leakage damping noise model as a generalization to the amplitude damping noise [
30]:
Definition 1. Let set . Define the Kraus operatorswhere probabilities for any with well-defined probabilities and . The single-site leakage damping noise model is defined as a CPTP map Λ
such thatfor any input state ρ. Denote the average leak and seep probabilities associated with the i-th site asrespectively. In the above definition, the parameters
can be understood as the probability of the state
flipped to
after the leakage damping noise, and
in
denotes that the noise model has no effect on the Hilbert space with leakage happens on more than one site. It is easy to check that
, hence
is a CPTP map [
30] in Hilbert space
. Additionally, we introduce Equation (
21) to simplify the representation, and we will find that the average leakage and seepage rates are only related to
and
for all of
. The prefactor
is added to fit the definition of “average” leakage and seepage rates in Equation (2).
4.1. Single-Site Leakage Noise
For the particular noise model described in Definition 1, we can simplify the average leakage rate from Theorem 1 as stated in the following theorem.
Theorem 2. Let Λ
be a single-site leakage damping channel as described in Definition 1. Let and be as defined in Equation (21), and assume that for all i and . Then after performing n-site LRB protocol, the expectation of the probability for measuring computational basis , where are real numbers, , and for , . The average leakage and seepage rates of Λ
are and respectively. Proof. If the noise model is described by Definition 1, the corresponding condensed-operator representation only acts non-trivially on the
-dimensional subspace spanned by
, as follows
where
are defined in Equation (
21). This transition matrix can be illustrated in
Figure 1. Equation (
22) holds since
, and similarly we can obtain other elements of
Q.
Although the spectrum of the transition matrix
Q cannot be explicitly solved in the general case, it is possible to derive bounds on all its eigenvalues by examining its characteristic polynomial. For simplicity, we prove the theorem under a generic scenario where
and
. In this case, it can be demonstrated that all eigenvalues of
Q are distinct, making
Q inherently diagonalizable. A detailed analysis of situations where algebraic multiplicities arise can be found in
Appendix B.
Denote
. Consider
where
. Hence
is an eigenvalue of
Q. Let
then the roots of function
are meanwhile the eigenvalues of
Q. Note that
As
and
, we have
. It can be seen that
and
always have different signs, indicating a zero in
for all
. As
, there is only one zero left to be determined, which is guaranteed to be real since all the other zeros are real. Let
When
,
and
have the same sign, and
Therefore we have
,
,
,
indicating f having a zero in .
To summarize, we have a complete characterization of all eigenvalues of Q, namely
,
;
= 1.
By Theorem 1, the average leakage and seepage rates for the Pauli group with this specific noise equal and respectively. □
We assume in Theorem 2 that for all i. When for some i, the matrix Q might not be fully diagonalizable, requiring more complex data processing schemes. From a physical perspective, such complications can be mitigated by preparing the initial state such that the initial leakage on qubit i is negligible. Theorem 2 shows that when the seepage probability of all qubits are close to each other and close to leakage probability, i.e., and for all of , then the multi-exponential decay will approximately collapse to two-exponential decay with . With the properties of the eigenstates for eigendecomposition of the transition matrix Q, we can further simplify the exponential curve to a single decay since the coefficient of equals zero when the state preparation noise is negligible. The leakage and seepage of the n-qubit system can be consequently derived according to , and , as shown in the following corollary.
Corollary 1. Let the leakage noise Λ be as described in Definition 1 such that and for different , and assume state preparation is noiseless, then after performing n-site LRB protocol, the expectation of the probability for measuring computational basis , where are some real constants. The average leakage and seepage rates of Λ are , and respectively.
The decay rate
obtained from the LRB experiment does not provide sufficient information to fully determine
and
. Rather, additional prior knowledge is required, such as the ratio of the leakage and the seepage rates. We postpone the proof of this corollary into
Appendix C.
4.2. Cross-Talk-Free Leakage Noise
Previous studies have indicated that crosstalk in real devices can be significantly minimized [
19]. In the subsequent subsection, we demonstrate that the exponential decay can be simplified under the condition that leakage noise occurs independently and locally across different qubits. We make the assumption that the local noise adheres to Definition 1 for each individual gate. It is important to note that in this context, the noise is inherently single-site, as each qubit possesses only one leakage site.
Corollary 2. By performing the LRB circuit in n-site crosstalk free system for the Pauli group, the expectation of the output probability for the computational subspace of the k-th qubit is equal to , and the average leakage and seepage rateswhere , and are some real numbers, are leakage rates associated with Equation (21) in the k-th qubit. We postpone the proof of the corollary into
Appendix D. This corollary can be obtained by restricting the noise in Theorem 2 to be the tensor product form of each local noise on a single qubit. Then if
or we know the relationship between
and
with the analysis of the system, we can estimate
by fitting
from
for all of
independently. We note that the crosstalk-free noise is different from the noise defined in Definition 1, since only a single qubit can leak in Definition 1. By Corollary 2, the fitted curve associated with
will not follow a single exponential decay, since
We can check that when
n equals to 2, there will be 3 exponents,
and
with average leakage rate
= 1 − (1 −
)(1 −
) and seepage rate
=
(1 −
+
)(1 −
+
) −
(1 −
)(1 −
).
5. Interleaved LRB Protocol for Specific Target Gates
In this section, we focus on benchmarking specific target gates. Benchmarking the leakage rate of an arbitrary target gate
T differs from benchmarking the leakage rate of the Pauli group, as the target gate does not readily form the Pauli group. We propose an interleaved variant of the leakage for the previous interleaved randomized benchmarking protocol [
10], named iLRB (interleaved leakage randomized benchmarking). We note that the target gate channel
can be any gate scheme, provided that the associated leakage noise model conforms to the form discussed in this section. The iLRB protocol is outlined as follows:
- (1)
Sample a sequence of m Paulis from and perform them sequentially to the noisy initial state interleaved by target gate to obtain . Measure the output states and estimate = through repeated experiments.
- (2)
Repeat Step (1) multiple times to estimate , the expectation of under random choices of .
- (3)
Sample a sequence of m Paulis in , and perform them sequentially to the prepared noisy initial state , i.e., . Measure the output states and estimate through repeated experiments.
- (4)
Repeat Step (3) multiple times to estimate , the expectation of under random choices of .
- (5)
Repeat Steps (2), (4) for different m, and fit the exponential decay curves of , with respect of m.
When the leakage noise of the Pauli gates is negligible compared to that of the target gate , we can benchmark any target gate where has the same leakage noise as in Definition 1, by only performing the first two steps of the above iLRB protocol. In this case, we can directly leverage Theorem 2 to obtain the average leakage rate of .
When the leakage noise of the Pauli gates is not negligible, however, steps (3) and (4) are needed to separate the target gate leakage from the Pauli gate leakage, and more assumptions on the target gate leakage noise are needed. We assume a specific case of the noise model in Definition 1, where the target gate
has the noisy implementation
and the noise
is defined in Definition 2 with the same value for all of
in Equation (
21). Similarly, we assume that
with noise channel
as defined in Definition 2 also having same value for all of
in Equation (
21).
Definition 2. We define the simplified single-site leakage damping noise
model as a CPTP map Λ
such thatfor any input sate ρ, wherewhere for any i, with . Definition 2 is to be regarded as a particular case of Definition 1, with at most a single leak happening between each and . Such a simplified noise model has important applications such as measuring leakage for two-qubit gates on superconducting quantum chips. See more details in the next section. The requirement of the noise model for iLRB protocol can be further relaxed to more than a single leak between each and with the same leak probability.
With the assumption of the above noise model, the average leakage rate of target gate can be estimated with exponential decay curves of obtained from iLRB protocol, as shown in the following theorem. Usually, the state preparation noise is negligible compared with gate and measurement noise, we also show that assuming state preparation is noiseless, we can further simplify the iLRB protocol to single-exponent decay curves in the following theorem.
Theorem 3. For any n-site target gate where its noisy implementation , and the noise of Pauli group both have the formations as in Definition 2 with noise parameter be respectively, after performing the iLRB protocol, the expectation of the output probabilitieswhere , and the average leakage and seepage rates for target gate T equal respectively. Assuming state preparation is noiseless, we can further simplify Equations (34) and (35) to Proof. By Theorem 2, we have
, and
. Since
, and
both have formations as in Definition 2, then
where
. Let
with condensed-operator representation
Q. Since the
-th element of
Q is
for
, then we have
We also provide the details for the representation of
Q in
Appendix E. Let
be the eigenvalue of
Q, with the representation of
Q we have
which implies we have eigenvalues
and
and
. Specifically, the multiplicity of
equals
. We postpone the proof of Equation (
46) into
Appendix F.
The average leakage rate for T gate can then be determined as = = , and seepage rate .
The single exponential decay result of this theorem for noiseless preparation noise can be obtained from Theorem 3 and the properties of the eigenstates for the eigendecomposition of the transition matrix
Q. We postpone the proof into
Appendix G. □
By leveraging of Theorem 3, we can estimate using the fitted estimated from iLRB protocol.