A Systematic Review on Password Guessing Tasks
Abstract
:1. Introduction
- Based on what the user knows, such as passwords, PINs, etc.;
- Based on what the user owns, such as U-shields, encryption cards, etc.;
- Based on what the user is, such as human physiological characteristics (fingerprints, iris, face, voice, etc.) and user behavior characteristics (handwriting, mouse movement speed, keyboard tapping frequency, etc.);
- Multi-factor authentication technology, that is, multiple combinations of the above three authentications.
1.1. Related Surveys and Reviews
1.2. Objectives and Contributions
- First, we classify password-guessing-related research into two categories according to the application scenarios: trawling password guessing and targeted password guessing. We compare and analyze those methods for researchers to understand the current status of password guessing.
- Second, we provide an extensive list of benchmark datasets for password guessing tasks so that interested researchers can easily find out baselines for their works.
- Third, we conduct an extensive bibliometric analysis from multiple perspectives to comprehensively depict the relationships among the existing password guessing studies.
- Finally, we discuss the open challenges of password guessing in terms of diverse application scenarios, guessing efficiency, and the combination of traditional and deep learning methods. Thus, this review helps to ease the efforts to find these requirements.
1.3. Paper Structure
2. Research Method
2.1. Research Questions
- What are the current neural approaches for password guessing?
- How can the literature on password guessing be organized into a taxonomy that categorizes similar approaches based on the DL model, type of data, and application scenario?
- Which benchmark datasets are available for password guessing?
- What bibliometric relationships exist between the existing research studies?
- What are the open challenges regarding password guessing?
2.2. Search Strategy
2.3. Study Selection
- Works that employed deep learning or traditional probabilistic method to model password guessability, such as PCFG, GAN, and VAE.
- Works published from the year 2016 onward. Since previous works have been reviewed in some works and this review aims to describe recent developments in the field of password guessing, we limited the publication time.
- Long papers or regular papers published in the main track of the conference or journal.
- Works published by top-tier venues, especially cybersecurity-related conferences or journals, such as S&P, CCS, NDSS, USENIX Conference, IEEE TDSC, or IEEE TIFS.
- Works published before 2016.
- Published works that did not contain the content of modeling password guessing.
- The experimental platform is not a desktop computer.
- Duplicated works.
3. Datasets
4. Password Guessing
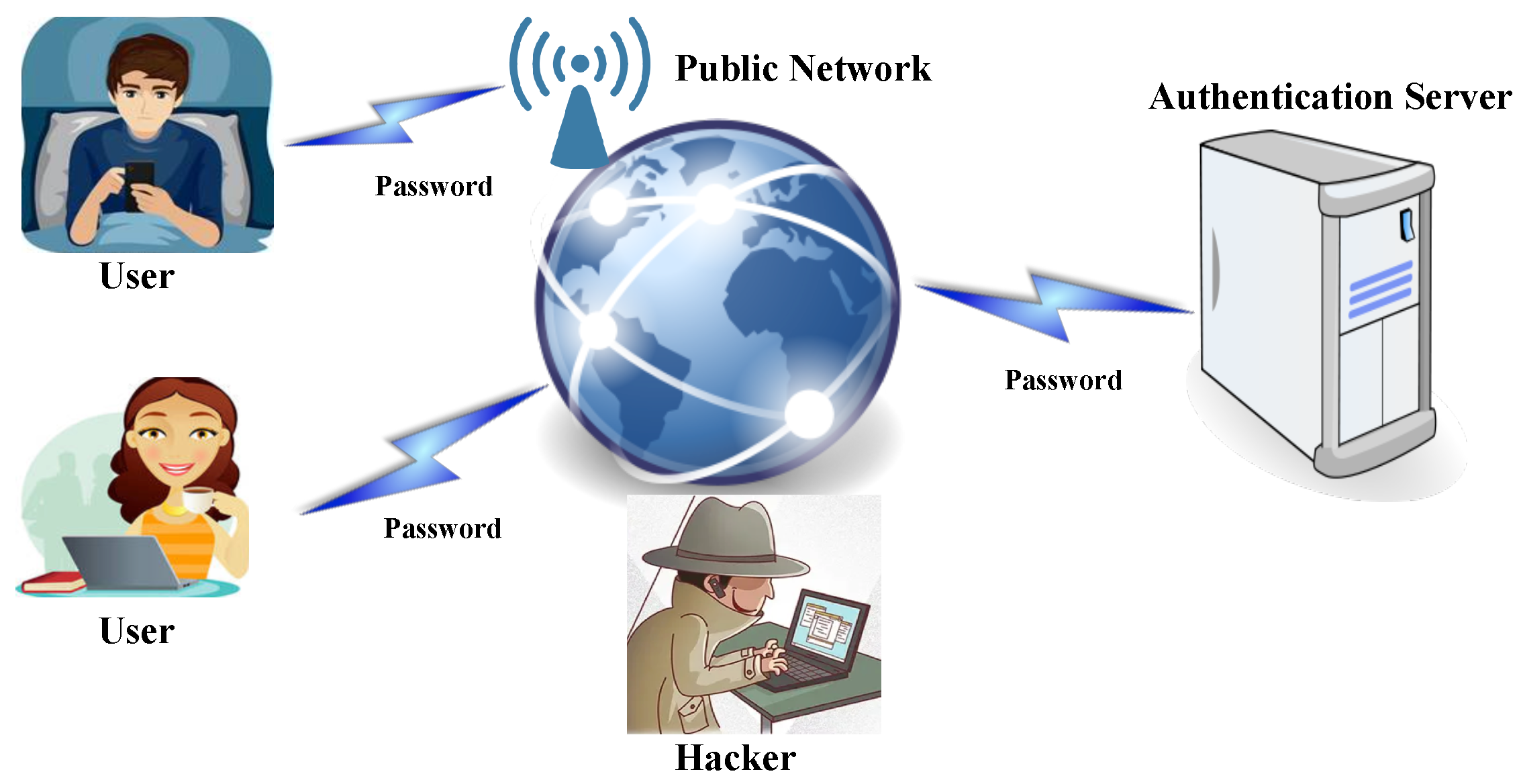
- According to whether the attack process requires interaction with the server, the password guessing attack can be classified into offline password guessing and online password guessing. The former attack requires the authentication server to store the user account password file and then the attacker makes a password guess on the local host. In this situation, the number of guesses that can be attempted is limited only by the attacker’s computing resources. The latter does not require a password file, and the attacker only needs to be connected to the network. However, the number of guesses that can be attempted is often limited by the server’s security policy, such as the US National Identity Standards NIST-800-63-3, which stipulates that the maximum number of failed logins allowed for a government website system in a month is 100, and the account will be locked if it exceeds 100 [15].
- According to whether the attack process utilizes the user’s personal information, password guessing attacks can be classified into trawling password guessing and targeted password guessing. While trawling guessing mainly exploits the user’s tendency to choose popular passwords, targeted guessing not only exploits the vulnerability of ordinary users to use popular passwords but also exploits the vulnerability of users to reuse passwords and construct passwords using personal information. With the help of information such as personally identifiable information and historical passwords, the success rate of targeted password guessing is significantly higher than trawling guessing with the same number of guesses.
- According to whether deep neural network methods of artificial intelligence are used in the attack process, password guessing attacks can be classified into neural attacks and traditional attacks. The former treats password guessing as a text generation task and relies on AI-related techniques to generate text passwords on a large-scale password training corpus. The latter encapsulates other methods, excluding deep neural network guessing methods.
4.1. Trawling Password Guessing
4.1.1. Traditional Trawling Password Guessing Methods
- John the Ripper (JTR), https://github.com/openwall/john (accessed on 20 June 2023). Originally, JTR was a password guessing tool that focuses on cracking UNIX/ Linux system weak passwords. There are four modes in JTR—single crack mode, wordlist crack mode, incremental mode, and external mode. Simple crack mode is specifically for users who use the account as the password. For example, an account username is ’admin’; the corresponding password may be ’admin888’ or ’admin123’. The wordlist crack mode requires the user to specify a dictionary file. Then, JTR performs password cracking based on the dictionary file. The incremental mode automatically tries all possible combinations of characters to be used as passwords. This mode is powerful but has a high time and space overhead. The external mode allows the user to develop a cracking module in C and then hook up the cracking module to the JTR environment to crack the password.
- HashCat, https://github.com/hashcat/hashcat (accessed on 20 June 2023). HashCat is the world’s fastest and most advanced password recovery utility, supporting five unique attack modes for over 300 highly optimized hashing algorithms. Hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and MacOS, and has facilities to help enable distributed password cracking.
- L0phtCrack, https://l0phtcrack.gitlab.io/ (accessed on 20 June 2023). The L0phtCrack project was created in 1997 by a group of hackers. After development and maintenance, the password auditing tool L0phtCrack was officially announced as open source. As a dedicated tool, L0phtCrack can be used to evaluate the strength of passwords and to help people in need recover lost passwords through brute force, dictionary, rainbow attacks, and other technical means.
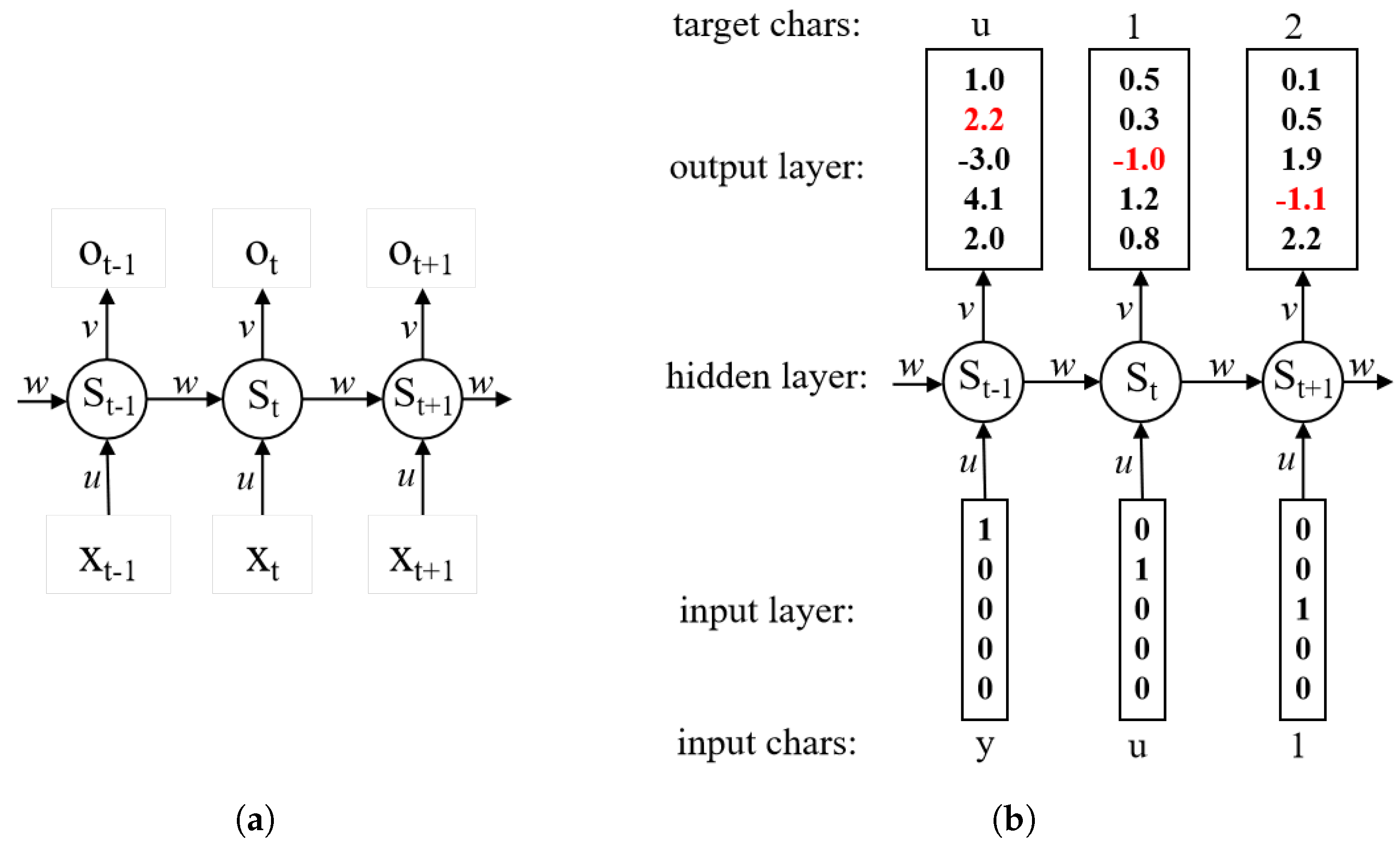
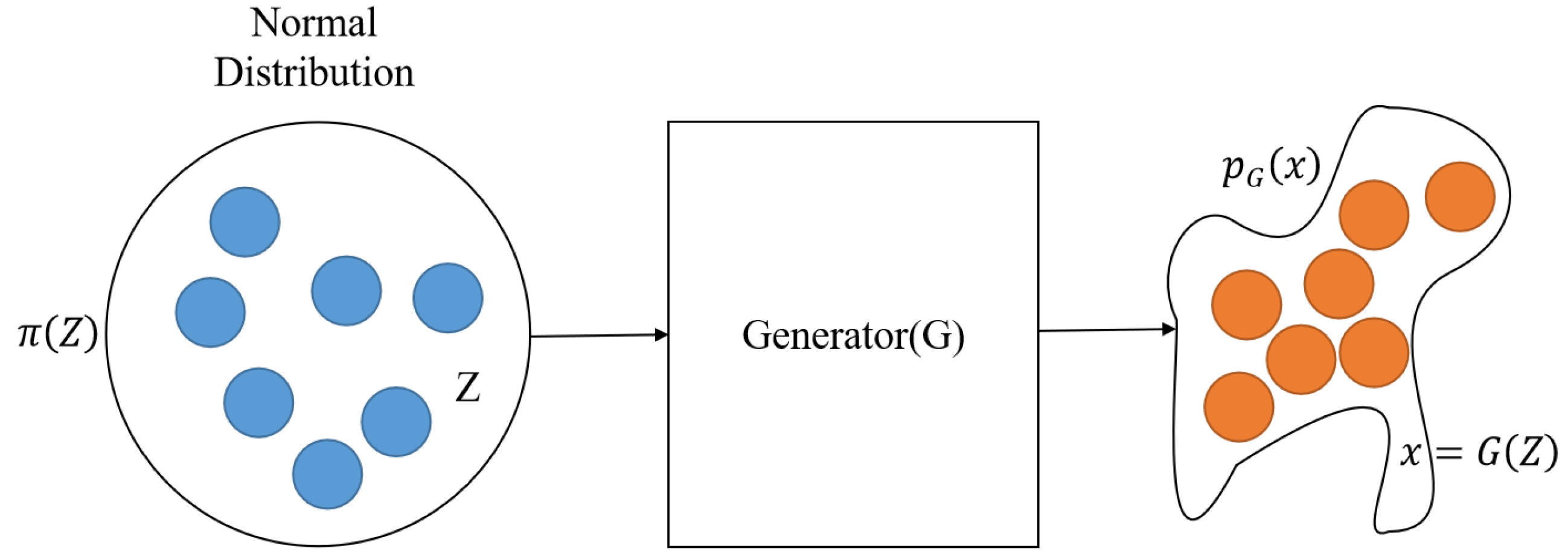
4.1.2. Neural Trawling Password Guessing Methods
- The password sequence from the training set is input to the RNN model for training in sequential text generation.
- The trained RNN guessing model aims to generate the next password character based on the existing password characters until the output termination character position.
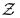 to distribution but that pathway also allows to change to
to distribution but that pathway also allows to change to 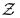 . In short, the flow model finds a duplex pathway between distributions
. In short, the flow model finds a duplex pathway between distributions 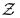 and . Of course, such reversibility comes at the cost that the data dimensions of
and . Of course, such reversibility comes at the cost that the data dimensions of 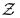 and must be the same.
and must be the same.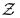 and distributions is a tough job. The flow model goes through three steps. First, the Non-linear Independent Components Estimation (NICE) [65] achieves a reversible solution from the distribution to the Gaussian distribution. Later, RealNVP [66] proposes a reversible solution from the distribution to the conditional non-Gaussian distribution. Then, GLOW [67] designs a reversible solution from distribution
and distributions is a tough job. The flow model goes through three steps. First, the Non-linear Independent Components Estimation (NICE) [65] achieves a reversible solution from the distribution to the Gaussian distribution. Later, RealNVP [66] proposes a reversible solution from the distribution to the conditional non-Gaussian distribution. Then, GLOW [67] designs a reversible solution from distribution 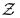 to the distribution, where the distribution can be the same complex as the
to the distribution, where the distribution can be the same complex as the 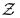 distribution.
distribution.4.2. Targeted Password Guessing
4.2.1. Traditional Targeted Password Guessing Methods
4.2.2. Neural Targeted Password Guessing Methods
5. Bibliometric Analysis
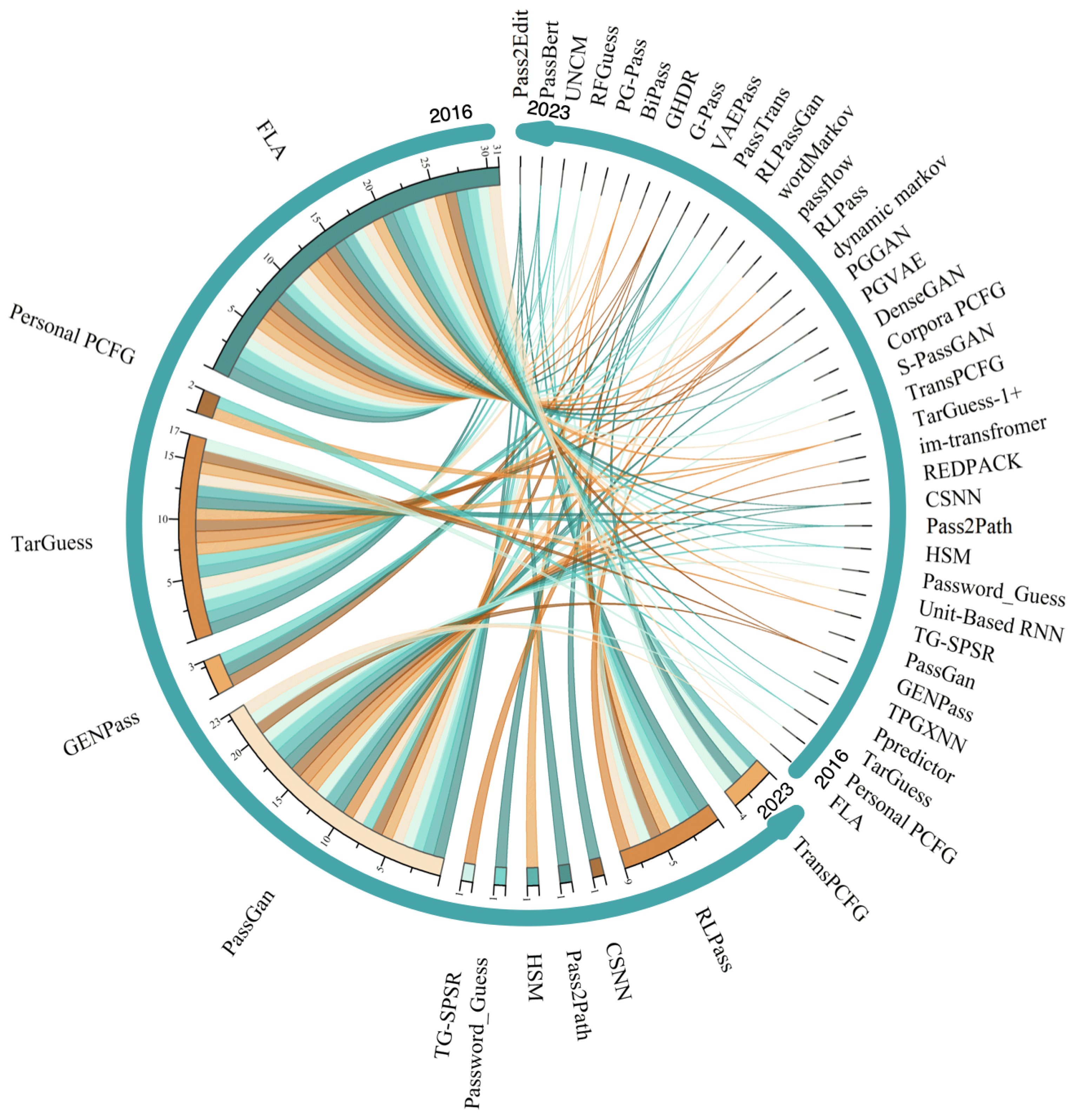
5.1. Statistics of Technology
Fine-Grained Technical Statistics
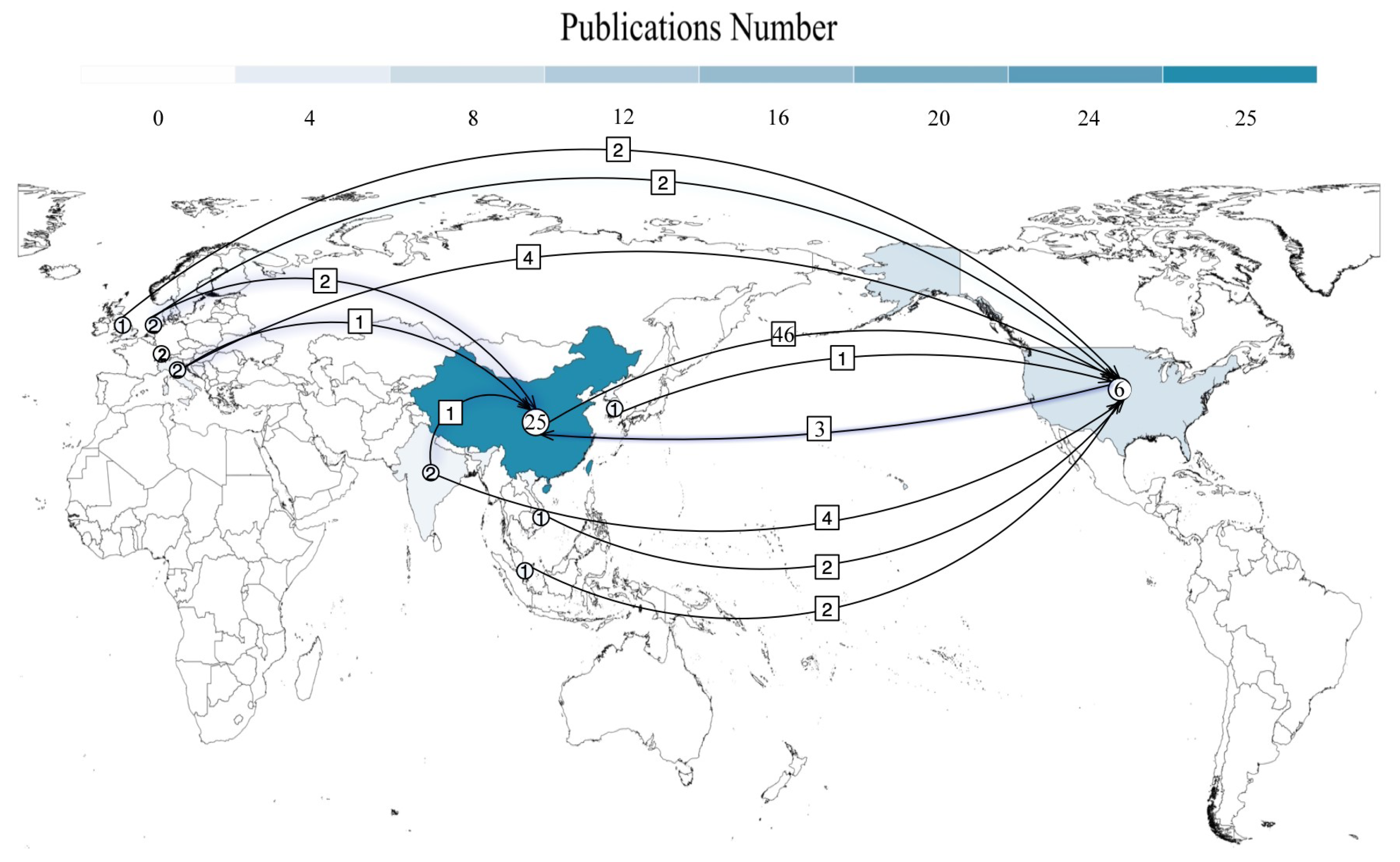
5.2. Cross-Citation Analysis
6. Challenges and Future Trends
6.1. Diverse Application Scenarios
6.2. Improving Guessing Efficiency
6.3. Combing Traditional and Deep Learning Methods
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| Name | Title |
|---|---|
| Pass2Edit | Pass2Edit: A Multi-Step Generative Model for Guessing Edited Passwords [77] |
| PassBert | Improving Real-world Password Guessing Attacks via Bi-directional Transformers [61] |
| UNCM | Universal Neural-Cracking-Machines: Self-Configurable Password Models from Auxiliary Data [41] |
| RFGuess | Password Guessing Using Random Forest [31] |
| PG-Pass | PG-Pass: Targeted Online Password Guessing Model based on Pointer Generator Network [73] |
| Pass2Path | Beyond Credential Stuffing: Password Similarity Models Using Neural Networks [75] |
| BiPass | PassMon: A Technique for Password Generation and Strength Estimation [49] |
| GHDR | A Honeywords Generation Method Based on Deep Learning and Rule-Based Password Attack [89] |
| G-Pass | Password Guessing Based on GAN with Gumbel-Softmax [45] |
| VAEPass | VAEPass: A lightweight passwords guessing model based on variational auto-encoder [56] |
| PassTrans | PASSTRANS: An improved password reuse model based on Transformer [74] |
| RLPassGan | RLPassGAN: Password Guessing Model Based on GAN with Policy Gradient [47] |
| WordMarkov | WordMarkov: a new password probability model of semantics [30] |
| passflow | PassFlow: Guessing Passwords with Generative Flows [68] |
| dynamic Markov | Dynamic Markov model: Password guessing using probability adjustment method [29] |
| PGGAN | PGGAN: Improve Password Cover Rate Using the Controller [90] |
| PGVAE | Modeling Password Guessability via Variational Auto-Encoder [55] |
| DenseGAN | DenseGAN: A Password Guessing Model Based on DenseNet and PassGAN [52] |
| Corpora PCFG | Corpora-based Password Guessing: An Effcient Approach for Small Training Sets [91] |
| S-PassGAN | A GAN-based approach for password guessing [44] |
| TransPCFG | TransPCFG: Transferring the Grammars From Short Passwords to Guess Long Passwords Effectively [27] |
| TarGuess-1+ | A New Targeted Password Guessing Model [92] |
| improved transfromer | Research on Password Cracking Technology Based on Improved Transformer [60] |
| REDPACK | Generating Optimized Guessing Candidates toward Better Password Cracking from Multi-Dictionaries Using Relativistic GAN [93] |
| CSNN | CSNN: Password guessing method based on Chinese syllables and neural network [40] |
| HSM | Password Guessing Based on Semantic Analysis and Neural Networks [39] |
| Password_Guess | Efficient Password Guessing based on a Password Segmentation Approach [94] |
| Unit-Based RNN | A Coarse-Grained Password Model with Memorable Unit-Based Recurrent Neural Networks [38] |
| TG-SPSR | Tg-spsr: A systematic targeted password attacking model [72] |
| PassGan | PassGAN: A Deep Learning Approach for Password Guessing [43] |
| GENPass | GENPass: A Multi-Source Deep Learning Model for Password Guessing [95] |
| TPGXNN | An Analysis of Targeted Password Guessing Using Neural Networks [96] |
| Ppredictor | Password Predictability Using Neural Networks [37] |
| TarGuess | Targeted Online Password Guessing: An Underestimated Threat [4] |
| Personal PCFG | A study of personal information in human-chosen passwords and its security implications [5] |
| FLA | Fast, Lean, and Accurate: Modeling Password Guessability using Neural Networks [33] |
| RLPass | Improving Password Guessing via Representation Learning [51] |
References
- Wang, D. Research on Key Issues in Password Security. Ph.D. Thesis, Peking University, Beijing, China, 2017. [Google Scholar]
- Bonneau, J.; Herley, C.; van Oorschot, P.C.; Stajano, F. The Quest to Replace Passwords: A Framework for Comparative Evaluation of Web Authentication Schemes. In Proceedings of the IEEE Symposium on Security and Privacy (SP 2012), San Francisco, CA, USA, 21–23 May 2012; pp. 553–567. [Google Scholar]
- Bonneau, J. The Science of Guessing: Analyzing an Anonymized Corpus of 70 Million Passwords. In Proceedings of the IEEE Symposium on Security and Privacy (SP 2012), San Francisco, CA, USA, 21–23 May 2012; pp. 538–552. [Google Scholar]
- Wang, D.; Zhang, Z.; Wang, P.; Yan, J.; Huang, X. Targeted Online Password Guessing: An Underestimated Threat. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; Weippl, E.R., Katzenbeisser, S., Kruegel, C., Myers, A.C., Halevi, S., Eds.; ACM: New York, NY, USA, 2016; pp. 1242–1254. [Google Scholar]
- Li, Y.; Wang, H.; Sun, K. A study of personal information in human-chosen passwords and its security implications. In Proceedings of the 35th Annual IEEE International Conference on Computer Communications (INFOCOM 2016), San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar]
- Das, A.; Bonneau, J.; Caesar, M.; Borisov, N.; Wang, X. The Tangled Web of Password Reuse. In Proceedings of the 21st Annual Network and Distributed System Security Symposium (NDSS 2014), San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Ives, B.; Walsh, K.R.; Schneider, H. The domino effect of password reuse. Commun. ACM 2004, 47, 75–78. [Google Scholar] [CrossRef]
- Veras, R.; Collins, C.; Thorpe, J. A Large-Scale Analysis of the Semantic Password Model and Linguistic Patterns in Passwords. ACM Trans. Priv. Secur. 2021, 24, 20:1–20:21. [Google Scholar] [CrossRef]
- Zhang, T.; Cheng, Z.; Qin, Y.; Li, Q.; Shi, L. Deep Learning for Password Guessing and Password Strength Evaluation, A Survey. In Proceedings of the 19th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom 2020), Guangzhou, China, 29 December 2020–1 January 2021; Wang, G., Ko, R.K.L., Bhuiyan, M.Z.A., Pan, Y., Eds.; pp. 1162–1166. [Google Scholar]
- Zhang, J.; Yang, C.; Zheng, Y.; You, W.; Su, R.; Ma, J. A Preliminary Analysis of Password Guessing Algorithm. In Proceedings of the 29th International Conference on Computer Communications and Networks (ICCCN 2020), Honolulu, HI, USA, 3–6 August 2020; pp. 1–9. [Google Scholar]
- Kaloudi, N.; Li, J. The AI-Based Cyber Threat Landscape: A Survey. ACM Comput. Surv. 2020, 53, 20:1–20:34. [Google Scholar] [CrossRef]
- Linghu, Y.; Li, X.; Zhang, Z. Deep Learning vs. Traditional Probabilistic Models: Case Study on Short Inputs for Password Guessing. In Proceedings of the Algorithms and Architectures for Parallel Processing—19th International Conference (ICA3PP 2019), Melbourne, VIC, Australia, 9–11 December 2019; Proceedings Part I—Lecture Notes in Computer Science. Wen, S., Zomaya, A.Y., Yang, L.T., Eds.; Springer: Cham, Switzerland, 2019; Volume 11944, pp. 468–483. [Google Scholar]
- Pearman, S.; Thomas, J.; Naeini, P.E.; Habib, H.; Bauer, L.; Christin, N.; Cranor, L.F.; Egelman, S.; Forget, A. Let’s Go in for a Closer Look: Observing Passwords in Their Natural Habitat. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security (CCS 2017), Dallas, TX, USA, 30 October–3 November 2017; Thuraisingham, B.M., Evans, D., Malkin, T., Xu, D., Eds.; ACM: New York, NY, USA, 2017; pp. 295–310. [Google Scholar]
- Kitchenham, B. Procedures for Performing Systematic Reviews. Keele 2004, 33, 1–26. [Google Scholar]
- Grassi, P.A.; Perlner, R.A.; Fenton, J.L.; Burr, W.E. NIST Special Publication 800-63B Digital Identity Guidelines; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2017. [Google Scholar]
- Weir, M.; Aggarwal, S.; de Medeiros, B.; Glodek, B. Password Cracking Using Probabilistic Context-Free Grammars. In Proceedings of the 30th IEEE Symposium on Security and Privacy (S&P 2009), Oakland, CA, USA, 17–20 May 2009; IEEE Computer Society: Washington, DC, USA, 2009; pp. 391–405. [Google Scholar]
- Ma, J.; Yang, W.; Luo, M.; Li, N. A Study of Probabilistic Password Models. In Proceedings of the 2014 IEEE Symposium on Security and Privacy (SP 2014), Berkeley, CA, USA, 18–21 May 2014; pp. 689–704. [Google Scholar]
- Morris, R.; Thompson, K. Password Security—A Case History. Commun. ACM 1979, 22, 594–597. [Google Scholar] [CrossRef]
- Riddle, B.L.; Miron, M.S.; Semo, J.A. Passwords in use in a university timesharing environment. Comput. Secur. 1989, 8, 569–579. [Google Scholar] [CrossRef]
- Wu, T.D. A Real-World Analysis of Kerberos Password Security. In Proceedings of the Network and Distributed System Security Symposium (NDSS 1999), San Diego, CA, USA, 3–5 February 1999. [Google Scholar]
- Klein, D.V. Foiling the cracker: A survey of, and improvements to, password security. In Proceedings of the 2nd USENIX Security Workshop, Portland, OR, USA, 27–28 August 1990; pp. 5–14. [Google Scholar]
- Liu, E.; Nakanishi, A.; Golla, M.; Cash, D.; Ur, B. Reasoning Analytically about Password-Cracking Software. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP 2019), San Francisco, CA, USA, 19–23 May 2019; pp. 380–397. [Google Scholar]
- Pasquini, D.; Cianfriglia, M.; Ateniese, G.; Bernaschi, M. Reducing Bias in Modeling Real-world Password Strength via Deep Learning and Dynamic Dictionaries. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 2021), Online, 11–13 August 2021; pp. 821–838. [Google Scholar]
- Cheng, H.; Li, W.; Wang, P.; Liang, K. Improved Probabilistic Context-Free Grammars for Passwords Using Word Extraction. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP 2021), Toronto, ON, Canada, 6–11 June 2021; pp. 2690–2694. [Google Scholar]
- Xu, M.; Wang, C.; Yu, J.; Zhang, J.; Zhang, K.; Han, W. Chunk-Level Password Guessing: Towards Modeling Refined Password Composition Representations. In Proceedings of the CCS ’21: 2021 ACM SIGSAC Conference on Computer and Communications Security, Online, 15–19 November 2021; Kim, Y., Kim, J., Vigna, G., Shi, E., Eds.; ACM: New York, NY, USA, 2021; pp. 5–20. [Google Scholar]
- Gage, P. A New Algorithm for Data Compression. C Users J. 1994, 12, 23–38. [Google Scholar]
- Han, W.; Xu, M.; Zhang, J.; Wang, C.; Zhang, K.; Wang, X.S. TransPCFG: Transferring the Grammars From Short Passwords to Guess Long Passwords Effectively. IEEE Trans. Inf. Forensics Secur. 2021, 16, 451–465. [Google Scholar] [CrossRef]
- Narayanan, A.; Shmatikov, V. Fast dictionary attacks on passwords using time-space tradeoff. In Proceedings of the 12th ACM Conference on Computer and Communications Security (CCS 2005), Alexandria, VA, USA, 7–11 November 2005; Atluri, V., Meadows, C.A., Juels, A., Eds.; ACM: New York, NY, USA, 2005; pp. 364–372. [Google Scholar] [CrossRef]
- Guo, X.; Liu, Y.; Tan, K.; Mao, W.; Jin, M.; Lu, H. Dynamic Markov Model: Password Guessing Using Probability Adjustment Method. Appl. Sci. 2021, 11, 4607. [Google Scholar] [CrossRef]
- Xie, J.; Cheng, H.; Zhu, R.; Wang, P.; Liang, K. WordMarkov: A New Password Probability Model of Semantics. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, ICASSP 2022, Online, 23–27 May 2022; pp. 3034–3038. [Google Scholar]
- Wang, D.; Zou, Y.; Zhang, Z.; Xiu, K. Password Guessing Using Random Forest. In Proceedings of the 32th USENIX Security Symposium (USENIX Security 2023), Anaheim, CA, USA, 9–11 August 2023. [Google Scholar]
- Ciaramella, A.; D’Arco, P.; Santis, A.D.; Galdi, C.; Tagliaferri, R. Neural Network Techniques for Proactive Password Checking. IEEE Trans. Dependable Secur. Comput. 2006, 3, 327–339. [Google Scholar] [CrossRef]
- Melicher, W.; Ur, B.; Komanduri, S.; Bauer, L.; Christin, N.; Cranor, L.F. Fast, Lean, and Accurate: Modeling Password Guessability Using Neural Networks. In Proceedings of the 2017 USENIX Annual Technical Conference (USENIX ATC 2017), Santa Clara, CA, USA, 12–14 July 2017. [Google Scholar]
- Hochreiter, S.; Schmidhuber, J. Long Short-Term Memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef]
- Chung, J.; Gülçehre, Ç.; Cho, K.; Bengio, Y. Empirical Evaluation of Gated Recurrent Neural Networks on Sequence Modeling. arXiv 2014, arXiv:1412.3555. [Google Scholar]
- Huang, Z.; Xu, W.; Yu, K. Bidirectional LSTM-CRF Models for Sequence Tagging. arXiv 2015, arXiv:1508.01991. [Google Scholar]
- Dahiya, M. Password Predictability Using Neural Networks. Int. J. Adv. Res. Comput. Sci. 2017, 8, 248–250. [Google Scholar]
- Xu, R.; Chen, X.; Shi, J. A coarse-grained password model with memorable unit-based recurrent neural networks. In Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing (SAC 2019), Limassol, Cyprus, 8–12 April 2019; Hung, C., Papadopoulos, G.A., Eds.; ACM: New York, NY, USA, 2019; pp. 1890–1897. [Google Scholar]
- Fang, Y.; Liu, K.; Jing, F.; Zuo, Z. Password guessing based on semantic analysis and neural networks. In Proceedings of the Chinese Conference on Trusted Computing and Information Security, Wuhan, China, 17–18 October 2018; Springer: Cham, Switzerland, 2018; pp. 84–98. [Google Scholar]
- Zhang, Y.; Xian, H.; Yu, A. CSNN: Password guessing method based on Chinese syllables and neural network. Peer-to-Peer Netw. Appl. 2020, 13, 2237–2250. [Google Scholar] [CrossRef]
- Pasquini, D.; Ateniese, G.; Troncoso, C. Universal Neural-Cracking-Machines: Self-Configurable Password Models from Auxiliary Data. arXiv 2023, arXiv:2301.07628. [Google Scholar]
- Goodfellow, I.J.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.C.; Bengio, Y. Generative Adversarial Networks. arXiv 2014, arXiv:1406.2661. [Google Scholar] [CrossRef]
- Hitaj, B.; Gasti, P.; Ateniese, G.; Pérez-Cruz, F. PassGAN: A Deep Learning Approach for Password Guessing. In Proceedings of the Applied Cryptography and Network Security—17th International Conference (ACNS 2019), Bogota, Colombia, 5–7 June 2019; Lecture Notes in Computer Science. Deng, R.H., Gauthier-Umaña, V., Ochoa, M., Yung, M., Eds.; Springer: Cham, Switzerland, 2019; Volume 11464, pp. 217–237. [Google Scholar]
- Vi, B.N.; Tran, N.N.; The, T.G.V. A GAN-based approach for password guessing. In Proceedings of the RIVF International Conference on Computing and Communication Technologies (RIVF 2021), Hanoi, Vietnam, 19–21 August 2021; pp. 1–5. [Google Scholar]
- Zhou, T.; Wu, H.T.; Lu, H.; Xu, P.; Cheung, Y.M. Password Guessing Based on GAN with Gumbel-Softmax. Secur. Commun. Netw. 2022, 2022, 5670629. [Google Scholar] [CrossRef]
- Jang, E.; Gu, S.; Poole, B. Categorical Reparameterization with Gumbel-Softmax. In Proceedings of the 5th International Conference on Learning Representations (ICLR 2017), Toulon, France, 24–26 April 2017. [Google Scholar]
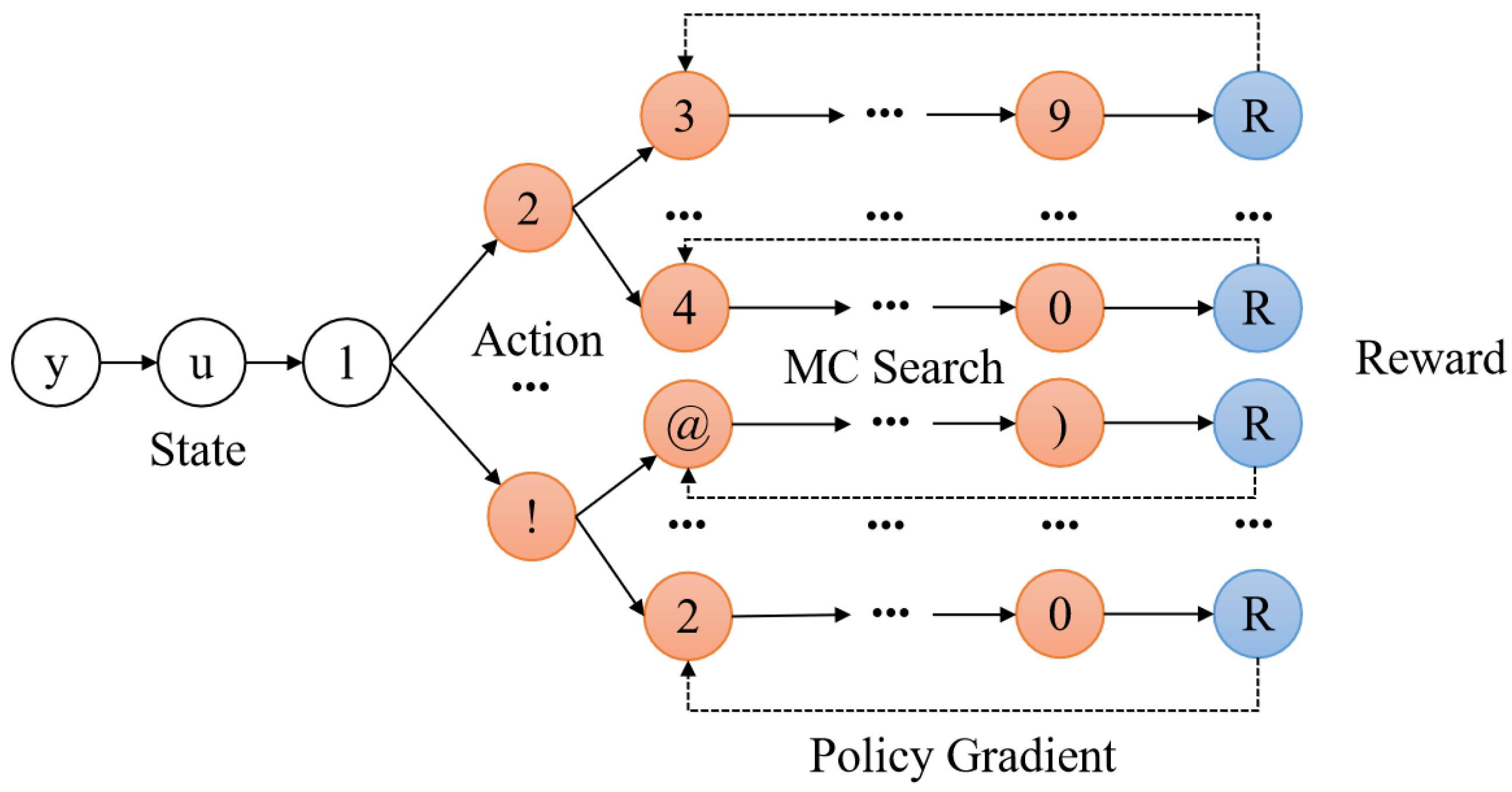
- Huang, D.; Wang, Y.; Chen, W. RLPassGAN: Password Guessing Model Based on GAN with Policy Gradient. In Proceedings of the International Conference on Security and Privacy in New Computing Environments, Online, 10–11 December 2021; Springer: Cham, Switzerland, 2021; pp. 159–174. [Google Scholar]
- Yu, L.; Zhang, W.; Wang, J.; Yu, Y. SeqGAN: Sequence Generative Adversarial Nets with Policy Gradient. In Proceedings of the Thirty-First AAAI Conference on Artificial Intelligence, San Francisco, CA, USA, 4–9 February 2017; Singh, S., Markovitch, S., Eds.; AAAI Press: Atlanta, GA, USA, 2017; pp. 2852–2858. [Google Scholar]
- Murmu, S.; Kasyap, H.; Tripathy, S. PassMon: A Technique for Password Generation and Strength Estimation. J. Netw. Syst. Manag. 2022, 30, 13. [Google Scholar] [CrossRef]
- Browne, C.; Powley, E.J.; Whitehouse, D.; Lucas, S.M.; Cowling, P.I.; Rohlfshagen, P.; Tavener, S.; Liebana, D.P.; Samothrakis, S.; Colton, S. A Survey of Monte Carlo Tree Search Methods. IEEE Trans. Comput. Intell. AI Games 2012, 4, 1–43. [Google Scholar] [CrossRef]
- Pasquini, D.; Gangwal, A.; Ateniese, G.; Bernaschi, M.; Conti, M. Improving Password Guessing via Representation Learning. In Proceedings of the 42nd IEEE Symposium on Security and Privacy (SP 2021), San Francisco, CA, USA, 24–27 May 2021; pp. 1382–1399. [Google Scholar]
- Fu, C.; Duan, M.; Dai, X.; Wei, Q.; Wu, Q.; Zhou, R. DenseGAN: A Password Guessing Model Based on DenseNet and PassGAN. In Proceedings of the 2021 IEEE Sustainable Power and Energy Conference (iSPEC), Nanjing, China, 23–25 December 2021; pp. 296–305. [Google Scholar]
- Huang, G.; Liu, Z.; van der Maaten, L.; Weinberger, K.Q. Densely Connected Convolutional Networks. In Proceedings of the 2017 IEEE Conference on Computer Vision and Pattern Recognition (CVPR 2017), Honolulu, HI, USA, 21–26 July 2017; pp. 2261–2269. [Google Scholar]
- Kingma, D.P.; Welling, M. Auto-Encoding Variational Bayes. In Proceedings of the 2nd International Conference on Learning Representations (ICLR 2014), Banff, AB, Canada, 14–16 April 2014. [Google Scholar]
- Wang, J.; Li, Y.; Chen, X.; Zhou, Y. Modeling Password Guessability via Variational Auto-Encoder. In Proceedings of the 24th IEEE International Conference on Computer Supported Cooperative Work in Design (CSCWD 2021), Dalian, China, 5–7 May 2021; pp. 348–353. [Google Scholar]
- Yang, K.; Hu, X.; Zhang, Q.; Wei, J.; Liu, W. VAEPass: A lightweight passwords guessing model based on variational auto-encoder. Comput. Secur. 2022, 114, 102587. [Google Scholar] [CrossRef]
- Dauphin, Y.N.; Fan, A.; Auli, M.; Grangier, D. Language Modeling with Gated Convolutional Networks. In Proceedings of the 34th International Conference on Machine Learning (ICML 2017), Sydney, NSW, Australia, 6–11 August 2017; Volume 70, pp. 933–941. [Google Scholar]
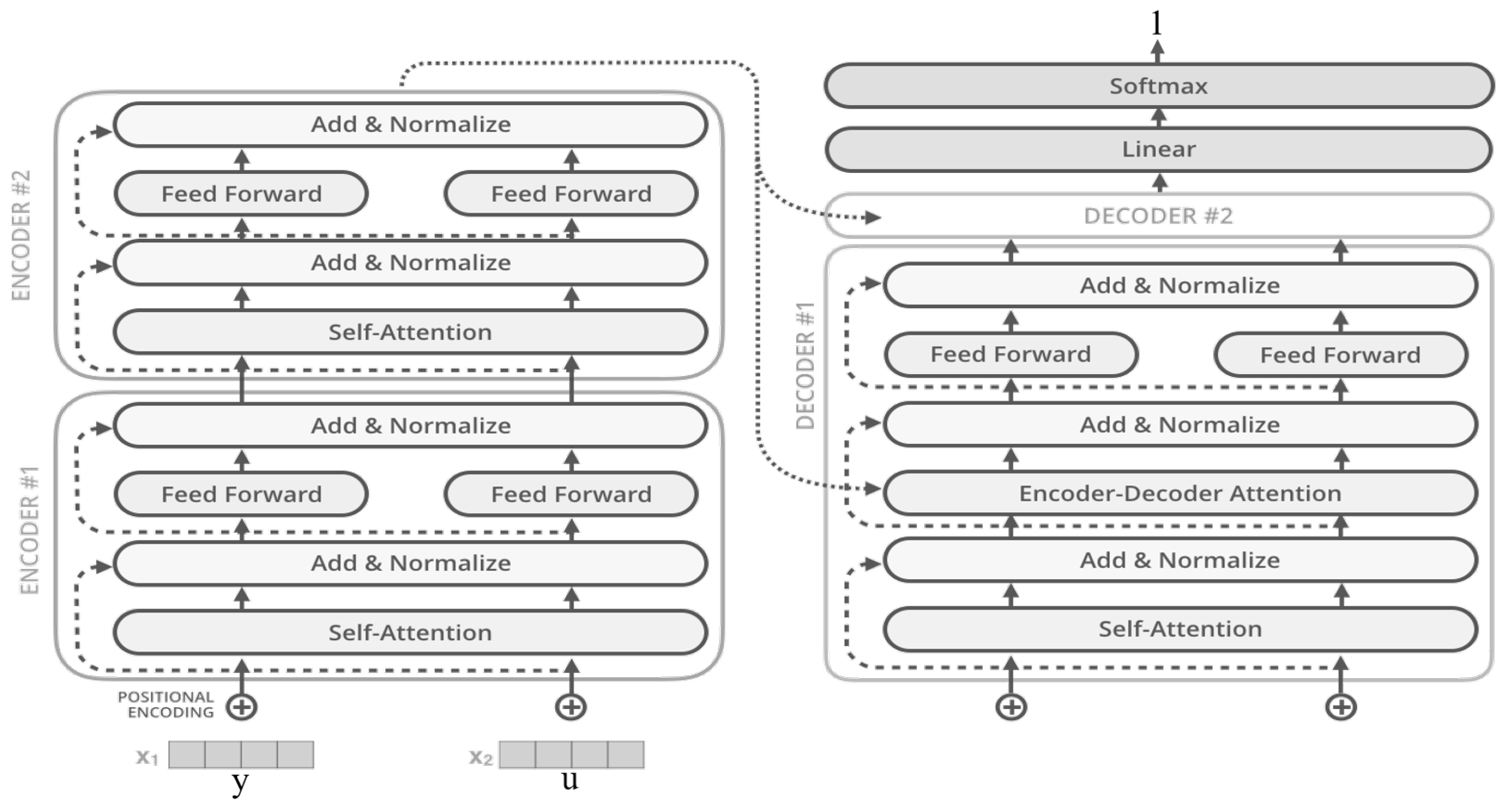
- Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, L.; Polosukhin, I. Attention is All you Need. In Proceedings of the Advances in Neural Information Processing Systems 30: Annual Conference on Neural Information Processing Systems 2017, Long Beach, CA, USA, 4–9 December 2017; Guyon, I., von Luxburg, U., Bengio, S., Wallach, H.M., Fergus, R., Vishwanathan, S.V.N., Garnett, R., Eds.; Curran Associates Inc.: Red Hook, NY, USA, 2017; pp. 5998–6008. [Google Scholar]
- Bahdanau, D.; Cho, K.; Bengio, Y. Neural Machine Translation by Jointly Learning to Align and Translate. In Proceedings of the 3rd International Conference on Learning Representations (ICLR 2015), San Diego, CA, USA, 7–9 May 2015. [Google Scholar]
- He, S.; Fu, J.; Chen, C.; Guo, Z. Research on password cracking technology based on improved transformer. Proc. J. Phys. Conf. Ser. 2020, 1631, 012161. [Google Scholar] [CrossRef]
- Xu, M.; Yu, J.; Zhang, X.; Wang, C.; Zhang, S.; Wu, H.; Han, W. Improving Real-world Password Guessing Attacks via Bi-directional Transformers. In Proceedings of the 32th USENIX Security Symposium (USENIX Security 2023), Anaheim, CA, USA, 9–11 August 2023; USENIX Association: Berkeley, CA, USA, 2023. [Google Scholar]
- Dell’Amico, M.; Filippone, M. Monte Carlo Strength Evaluation: Fast and Reliable Password Checking. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; Ray, I., Li, N., Kruegel, C., Eds.; ACM: New York, NY, USA, 2015; pp. 158–169. [Google Scholar]
- Albrecht, M.R.; Mareková, L.; Paterson, K.G.; Stepanovs, I. Four Attacks and a Proof for Telegram. In Proceedings of the 44th IEEE Symposium on Security and Privacy, SP 2023, San Francisco, CA, USA, 22–25 May 2023; pp. 87–106. [Google Scholar]
- Papamakarios, G.; Nalisnick, E.T.; Rezende, D.J.; Mohamed, S.; Lakshminarayanan, B. Normalizing Flows for Probabilistic Modeling and Inference. J. Mach. Learn. Res. 2021, 22, 57:1–57:64. [Google Scholar]
- Dinh, L.; Krueger, D.; Bengio, Y. NICE: Non-linear Independent Components Estimation. In Proceedings of the 3rd International Conference on Learning Representations (ICLR 2015), San Diego, CA, USA, 7–9 May 2015. [Google Scholar]
- Dinh, L.; Sohl-Dickstein, J.; Bengio, S. Density estimation using Real NVP. In Proceedings of the 5th International Conference on Learning Representations, ICLR 2017, Toulon, France, 24–26 April 2017. [Google Scholar]
- Kingma, D.P.; Dhariwal, P. Glow: Generative Flow with Invertible 1 × 1 Convolutions. In Proceedings of the Advances in Neural Information Processing Systems 31: Annual Conference on Neural Information Processing Systems 2018 (NeurIPS 2018), Montreal, QC, Canada, 3–8 December 2018; Bengio, S., Wallach, H.M., Larochelle, H., Grauman, K., Cesa-Bianchi, N., Garnett, R., Eds.; Springer: Cham, Switzerland, 2018; pp. 10236–10245. [Google Scholar]
- Pagnotta, G.; Hitaj, D.; Gaspari, F.D.; Mancini, L.V. PassFlow: Guessing Passwords with Generative Flows. arXiv 2021, arXiv:2105.06165. [Google Scholar]
- Wang, D.; Wang, P. The Emperor’s New Password Creation Policies. In Proceedings of the 20th European Symposium on Research in Computer Security, Vienna, Austria, 21–25 September 2015. [Google Scholar]
- Cheswick, W.R. Rethinking passwords. Commun. ACM 2013, 56, 40–44. [Google Scholar] [CrossRef]
- Lai, R.W.F.; Egger, C.; Reinert, M.; Chow, S.S.M.; Maffei, M.; Schröder, D. Simple Password-Hardened Encryption Services. In Proceedings of the 27th USENIX Security Symposium (USENIX Security 2018), Baltimore, MD, USA, 15–17 August 2018; pp. 1405–1421. [Google Scholar]
- Zhang, M.; Zhang, Q.; Liu, W.; Hu, X.; Wei, J. TG-SPSR: A Systematic Targeted Password Attacking Model. KSII Trans. Internet Inf. Syst. 2019, 13, 2674–2697. [Google Scholar]
- Li, Y.; Li, Y.; Chen, X.; Shi, R.; Han, J. PG-Pass: Targeted Online Password Guessing Model based on Pointer Generator Network. In Proceedings of the 25th IEEE International Conference on Computer Supported Cooperative Work in Design (CSCWD 2022), Hangzhou, China, 4–6 May 2022; pp. 507–512. [Google Scholar]
- He, X.; Cheng, H.; Xie, J.; Wang, P.; Liang, K. Passtrans: An Improved Password Reuse Model Based on Transformer. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, ICASSP 2022, Online, 23–27 May 2022; pp. 3044–3048. [Google Scholar]
- Pal, B.; Daniel, T.; Chatterjee, R.; Ristenpart, T. Beyond Credential Stuffing: Password Similarity Models Using Neural Networks. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP 2019), San Francisco, CA, USA, 19–23 May 2019; pp. 417–434. [Google Scholar]
- 4iQ. Identities in the Wild: The Tsunami of Breached Identities Continues May 2018; Technical Report; 4iQ: Los Altos, CA, USA, 2018. [Google Scholar]
- Wang, D.; Zou, Y.; Xiao, Y.A.; Ma, S.; Chen, X. Pass2Edit: A Multi-Step Generative Model for Guessing Edited Passwords. In Proceedings of the 32th USENIX Security Symposium (USENIX Security 2023), Anaheim, CA, USA, 9–11 August 2023. [Google Scholar]
- Ho, J.; Jain, A.; Abbeel, P. Denoising Diffusion Probabilistic Models. In Proceedings of the Advances in Neural Information Processing Systems 33: Annual Conference on Neural Information Processing Systems 2020 (NeurIPS 2020), Online, 6–12 December 2020. [Google Scholar]
- Song, Y.; Ermon, S. Improved Techniques for Training Score-Based Generative Models. In Proceedings of the Advances in Neural Information Processing Systems 33: Annual Conference on Neural Information Processing Systems 2020 (NeurIPS 2020), Online, 6–12 December 2020. [Google Scholar]
- Nichol, A.Q.; Dhariwal, P. Improved Denoising Diffusion Probabilistic Models. In Proceedings of the 38th International Conference on Machine Learning (ICML 2021), Online, 18–24 July 2021; Volume 139, pp. 8162–8171. [Google Scholar]
- Li, Y.; Tarlow, D.; Brockschmidt, M.; Zemel, R.S. Gated Graph Sequence Neural Networks. In Proceedings of the 4th International Conference on Learning Representations (ICLR 2016), San Juan, Puerto Rico, 2–4 May 2016. [Google Scholar]
- Kipf, T.N.; Welling, M. Semi-Supervised Classification with Graph Convolutional Networks. In Proceedings of the 5th International Conference on Learning Representations (ICLR 2017), Toulon, France, 24–26 April 2017. [Google Scholar]
- Velickovic, P.; Cucurull, G.; Casanova, A.; Romero, A.; Liò, P.; Bengio, Y. Graph Attention Networks. arXiv 2017, arXiv:1710.10903. [Google Scholar]
- Hamilton, W.L.; Ying, Z.; Leskovec, J. Inductive Representation Learning on Large Graphs. In Proceedings of the Advances in Neural Information Processing Systems 30: Annual Conference on Neural Information Processing Systems 2017, Long Beach, CA, USA, 4–9 December 2017; pp. 1024–1034. [Google Scholar]
- Lan, Z.; Chen, M.; Goodman, S.; Gimpel, K.; Sharma, P.; Soricut, R. ALBERT: A Lite BERT for Self-supervised Learning of Language Representations. In Proceedings of the 8th International Conference on Learning Representations (ICLR 2020), Addis Ababa, Ethiopia, 26–30 April 2020. [Google Scholar]
- Liu, Q.; Chen, B.; Lou, J.; Zhou, B.; Zhang, D. Incomplete Utterance Rewriting as Semantic Segmentation. In Proceedings of the 2020 Conference on Empirical Methods in Natural Language Processing (EMNLP 2020), Online, 16–20 November 2020; Association for Computational Linguistics: Cedarville, OH, USA, 2020; pp. 2846–2857. [Google Scholar]
- Raffel, C.; Shazeer, N.; Roberts, A.; Lee, K.; Narang, S.; Matena, M.; Zhou, Y.; Li, W.; Liu, P.J. Exploring the Limits of Transfer Learning with a Unified Text-to-Text Transformer. J. Mach. Learn. Res. 2020, 21, 140:1–140:67. [Google Scholar]
- Yang, Z.; Dai, Z.; Yang, Y.; Carbonell, J.G.; Salakhutdinov, R.; Le, Q.V. XLNet: Generalized Autoregressive Pretraining for Language Understanding. In Proceedings of the Advances in Neural Information Processing Systems 32: Annual Conference on Neural Information Processing Systems 2019 (NeurIPS 2019), Vancouver, BC, Canada, 8–14 December 2019; pp. 5754–5764. [Google Scholar]
- Yang, K.; Hu, X.; Zhang, Q.; Wei, J.; Liu, W. A Honeywords Generation Method Based on Deep Learning and Rule-Based Password Attack. In Proceedings of the Security and Privacy in New Computing Environments, Xi’an, China, 30–31 December 2022; Shi, W., Chen, X., Choo, K.K.R., Eds.; Springer International Publishing: Cham, Switzerland, 2022; pp. 294–306. [Google Scholar]
- Guo, X.; Liu, Y.; Tan, K.; Jin, M.; Lu, H. PGGAN: Improve Password Cover Rate Using the Controller. Proc. J. Phys. Conf. Ser. 2021, 1856, 012012. [Google Scholar] [CrossRef]
- Gan, X.; Chen, M.; Li, D.; Wu, Z.; Han, W.; Chen, H. Corpora-based Password Guessing: An Efficient Approach for Small Training Sets. In Proceedings of the 2021 IEEE 4th International Conference on Electronics and Communication Engineering (ICECE), Xi’an, China, 17–19 December 2021; pp. 311–319. [Google Scholar]
- Xie, Z.; Zhang, M.; Yin, A.; Li, Z. A New Targeted Password Guessing Model. In Proceedings of the Information Security and Privacy—25th Australasian Conference (ACISP 2020), Perth, WA, Australia, 30 November–2 December 2020; Liu, J.K., Cui, H., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020; Volume 12248, pp. 350–368. [Google Scholar] [CrossRef]
- Nam, S.; Jeon, S.; Moon, J. Generating Optimized Guessing Candidates toward Better Password Cracking from Multi-Dictionaries Using Relativistic GAN. Appl. Sci. 2020, 10, 7306. [Google Scholar] [CrossRef]
- Deng, G.; Yu, X.; Guo, H. Efficient Password Guessing Based on a Password Segmentation Approach. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM 2019), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Xia, Z.; Yi, P.; Liu, Y.; Jiang, B.; Wang, W.; Zhu, T. GENPass: A Multi-Source Deep Learning Model for Password Guessing. IEEE Trans. Multim. 2020, 22, 1323–1332. [Google Scholar] [CrossRef]
- Zhou, H.; Liu, Q.; Zhang, F. Poster: An analysis of targeted password guessing using neural networks. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (S&P), San Jose, CA, USA, 22–24 May 2017. [Google Scholar]


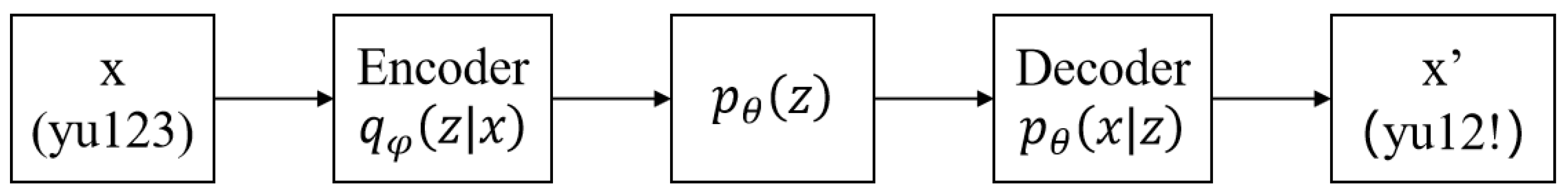

| Abbreviation | Description |
|---|---|
| AE | Auto-Encoder |
| CNN | Convolutional Neural Network |
| CRF | Conditional Random Field |
| DL | Deep Learning |
| GAN | Generative Adversarial Network |
| NLP | Natural Language Processing |
| PCFG | Probabilistic Context-Free Grammar |
| RL | Reinforcement Learning |
| RNN | Recurrent Neural Network |
| SVM | Support Vector Machine |
| PII | Personal Identifiable Information |
| Work | Year | Contributions |
|---|---|---|
| A Large-Scale Analysis of the Semantic Password Model and Linguistic Patterns in Passwords [8] | 2021 | Provided a comprehensive evaluation of semantic password grammars in terms of sample size, probabilistic smoothing, and linguistic information. |
| Deep Learning for Password Guessing and Password Strength Evaluation: A Survey [9] | 2020 | Surveyed state-of-the-art deep learning methods for password guessing and password strength evaluation before 2019. |
| A Preliminary Analysis of Password Guessing Algorithm [10] | 2020 | Took the Coverage metric to quantify the involvement of personal information in the creation of an individual password and used the Monte Carlo and zxcvbn methods to assess password strength. |
| The AI-Based Cyber Threat Landscape: A Survey [11] | 2020 | Explored research examples of cyber attacks posed by combining the “dark” side of AI with the attack techniques and introduced an analytic framework for modeling those attacks. |
| Deep Learning vs. Traditional Probabilistic Models: Case Study on Short Inputs for Password Guessing [12] | 2019 | Focused on the comparative analysis of deep learning algorithms and traditional probabilistic models on strings of short-length passwords. |
| Let’s Go in for a Closer Look: Observing Passwords in Their Natural Habitat [13] | 2017 | Shown that password reuse in both exact and partial form is extremely rampant. |
| Term 1 | Term 2 |
|---|---|
| password guessing | neural network |
| password cracking | neural approach |
| password attacking | machine learning |
| password guessability | deep learning |
| password predictability | VAE |
| password reuse | Transformer |
| password probability model | PCFG |
| trawling | GAN |
| targeted | Markov |
| Name | Type | Affiliation | Language | Timestamp | Causes of Leakage | Size | Times |
|---|---|---|---|---|---|---|---|
| Tianya | Social Website | China | Chinese | Dec. 2011 | Hacker Attacks | 30,233,633 | 3 |
| Dodonew | Games and E-commerce | China | Chinese | Dec. 2011 | Hacker Attacks | 16,231,271 | 8 |
| CSDN | Programmer Forum | China | Chinese | Dec. 2011 | Hacker Attacks | 6,428,287 | 14 |
| 12306 | Railway Website | China | Chinese | Dec. 2014 | Crash Attack | 131,653 | 6 |
| 126 | China | Chinese | Oct. 2015 | Crash Attack | 136,711,126 | 2 | |
| 163 | China | Chinese | Oct. 2015 | Crash Attack | 118,100,272 | 2 | |
| 17173 | Games Website | China | Chinese | Dec. 2011 | Crash Attack | 18,333,810 | 0 |
| Rockyou | Games | USA | English | Dec. 2009 | SQL Injection | 32,603,388 | 18 |
| 000webhost | Free Web Hosting | USA | English | Oct. 2015 | Programming Errors | 15,251,073 | 8 |
| Battlefield | Games Website | USA | English | Jun. 2011 | Hacker Attacks | 417,453 | 0 |
| Single.org | Dating Website | USA | English | Oct. 2010 | SQL Injection | 16,250 | 0 |
| Faithwriters | Writing Forum | USA | English | Mar. 2009 | SQL Injection | 9709 | 0 |
| Hak5 | Hacking Forum | USA | English | Jul. 2009 | Hacker Attacks | 2987 | 0 |
| Myspace | Social Website | USA | English | May 2016 | Hacker Attacks | 30,213,024 | 5 |
| Social Website | USA | English | May 2012 | Hacker Attacks | 22,805,966 | 2 | |
| Gmail | Russia | Russian | Sep. 2014 | Phishing Attacks | 4,929,090 | 2 | |
| Mail.ru | Russia | Russian | Sep. 2014 | Phishing Attacks | 4,932,688 | 0 | |
| Yandex.ru | Search Engine | Russia | Russian | Sep. 2014 | Phishing Attacks | 1,261,810 | 0 |
| Flirtlife.de | Marriage Website | Germany | German | May 2006 | Hacker Attacks | 115,589 | 0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, W.; Yin, Q.; Yin, H.; Xiao, W.; Chang, T.; He, L.; Ni, L.; Ji, Q. A Systematic Review on Password Guessing Tasks. Entropy 2023, 25, 1303. https://doi.org/10.3390/e25091303
Yu W, Yin Q, Yin H, Xiao W, Chang T, He L, Ni L, Ji Q. A Systematic Review on Password Guessing Tasks. Entropy. 2023; 25(9):1303. https://doi.org/10.3390/e25091303
Chicago/Turabian StyleYu, Wei, Qingsong Yin, Hao Yin, Wei Xiao, Tao Chang, Liangliang He, Lulin Ni, and Qingbing Ji. 2023. "A Systematic Review on Password Guessing Tasks" Entropy 25, no. 9: 1303. https://doi.org/10.3390/e25091303
APA StyleYu, W., Yin, Q., Yin, H., Xiao, W., Chang, T., He, L., Ni, L., & Ji, Q. (2023). A Systematic Review on Password Guessing Tasks. Entropy, 25(9), 1303. https://doi.org/10.3390/e25091303






