Abstract
Measurement-device-independent quantum key distribution (MDI-QKD) completely closes the security loopholes caused by the imperfection of devices at the detection terminal. Commonly, a symmetric MDI-QKD model is widely used in simulations and experiments. This scenario is far from a real quantum network, where the losses of channels connecting each user are quite different. To adapt such a feature, an asymmetric MDI-QKD model is proposed. How to improve the performance of asymmetric MDI-QKD also becomes an important research direction. In this work, an advantage distillation (AD) method is applied to further improve the performance of asymmetric MDI-QKD without changing the original system structure. Simulation results show that the AD method can improve the secret key rate and transmission distance, especially in the highly asymmetric cases. Therefore, this scheme will greatly promote the development of future MDI-QKD networks.
1. Introduction
Quantum key distribution (QKD) can unconditionally ensure the theoretical security of information transmission between two or more distant users with quantum mechanics. In the process of development from theory to practice, there are many challenges to realizing remote and secure quantum key distribution in the practical applications. With various theoretical ideas and experimental schemes being put forward, many challenges have been overcome. The BB84 protocol [1] proposed by Bennett realizes two-point communication and the Ekert91 and BBM92 protocols have been proposed successively [2,3]. Although QKD has been proven to have unconditional security in theory, imperfect devices can lead to some security loopholes that hinder the development of QKD protocols in practical applications. In practical applications, we often use weak coherent sources (WCSs) with multi-photon components, and Eve can eavesdrop with photon-number splitting (PNS) attacks [4]. Fortunately, the decoy-state method proposed [5,6] can solve PNS attacks and obtain rapid development both theoretically and experimentally [7,8,9]. Considering the imperfection of the detector, Lo firstly proposed the MDI-QKD protocol [10] which thoroughly solves the security loopholes mainly at the detection terminal. With the advantages of the MDI-QKD protocol, the MDI-QKD protocol attracts extensive attention and has been greatly studied in theory and experiments [11,12,13,14,15,16,17,18].
In previous work, the MDI-QKD was mainly studied in symmetric scenarios for simplicity. With the development of theory and technology, researchers have paid more attention to the asymmetric MDI-QKD protocol in recent years. To achieve good interference at the detection terminal, Lo proposed an asymmetric seven-intensity MDI-QKD [19], which can improve the performance of MDI-QKD in practical asymmetric structures based on the four-intensity MDI-QKD [11]. Consequently, asymmetric MDI-QKD is more suitable for the common QKD networks. However, due to its asymmetric nature, its performance is inferior to that of the original symmetric scheme. Improving the performance of asymmetric MDI-QKDs has become an urgent problem that needs to be addressed.
Inspired by the advantage distillation (AD) method [20,21,22,23], we study the principle of the method and find that the AD method can be successfully applied to the asymmetric seven-intensity MDI-QKD protocol. Compared with the original protocol, the performance of the asymmetric protocol has been significantly improved, which provides another theoretical verification that the post-processing AD method can improve the performance of the QKD protocol. This method can divide the original key string into blocks of only a few bits to achieve a high key correlation and greatly improve the protocol’s performance. The paper is organized as follows: In Section 2, we review the asymmetric seven-intensity MDI-QKD protocol and introduce the protocol with AD. The results of numerical simulations are shown in Section 3. Finally, summaries are given in Section 4.
2. Methods
2.1. Asymmetric MDI-QKD
Here, we mainly describe the process of the asymmetric seven-intensity MDI-QKD protocol, which develops from the four-intensity symmetric protocol, as follows:
- (1).
- State preparation. Alice (Bob) randomly prepares the signal state only in Z basis with (), and prepares the decoy states only in X basis with intensities of , (,), satisfying the formula < ( < ). When preparing the vacuum state of intensity o, Alice (Bob) does not choose any base. The prepared states will be sent to Charlie to perform measurement;
- (2).
- Measurement. Charlie performs the Bell state measurement (BSM) after receiving the quantum states sent from Alice and Bob;
- (3).
- Announcement. After Alice and Bob repeat the above steps and enough counting events are recorded, Charlie publicly announces the BSM results. Subsequently, they announce the selected bases and intensities;
- (4).
- Parameter estimation. After finishing the quantum transmission phase, Alice and Bob can estimate the lower bound of single-photon yield and the upper bound of single-photon error rate (QBER) using the decoy-state technology;
- (5).
- Post-processing. Alice and Bob perform key reconciliation and privacy amplification on the raw key data to obtain the final secret key.
The decoupled bases are used in the asymmetric seven-intensity MDI-QKD protocol, thus the protocol can perform decoy states in the X basis only to estimate and can use = to obtain the single-photon yield in Z basis [11]. Then, the secret key rate can be calculated by the following formula [10,11,19]:
where and each correspond to the probability that Alice or Bob emits the signal states of or , respectively. and are the gain and QBER in the Z basis, is the lower (upper) bound of single-photon yield (QBER), which can be estimated from the decoy-state technology, is the binary entropy function, and is the error correction efficiency.
Based on the asymmetric seven-intensity MDI-QKD protocol above, the performance can be further improved by optimization techniques such as joint estimations and collective constraints [11]. Referring to the joint estimations method, the common part is extracted from the following two parameters , to optimize the key rate. is used in the following subsection. is a piecewise function where < [19,24]. These parameters , and can be estimated accurately by the decoy-state technology in the original MDI-QKD protocol [10,11]. The following formulas can estimate these parameters which lead to a much higher rate in distilling the secure final key:
where denotes the photon-number distribution of the source at Alice’s (Bob’s) side, and are the gain and the total quantum bit errors [25], and is the combination of the gain of the decoy state and the vacuum state. is the standard error, and its value is set to 5.3 here. The expression for is equal to when < , otherwise the expression equals [19,24]. Considering the effect of statistical fluctuations on multiple observations, the method of collective constraints can provide tighter constraint conditions between different sources () than independent bounds. Thus, these parameters can be further optimized to achieve a higher key rate by the joint constraints method [8].
By the above formulas, we can calculate the final secret key rate of the asymmetric seven-intensity MDI-QKD protocol.
2.2. Asymmetric MDI-QKD with AD
Many previous works have demonstrated that the AD method can further improve the performance of QKD [20,21,22,23]. In this section, we improve the secure key rate and transmission distance of the asymmetric seven-intensity MDI-QKD protocol with the AD method. An additional AD method is performed between parameter estimation and post-processing step, and highly correlated bit pairs are discriminated from weakly correlated information. The security of AD method will be analyzed in an entanglement-based scheme. Alice prepares the quantum state and sends the second particle to Bob through the quantum channel. Since Eve controls the quantum channel by certain value (i = 0, 1, 2, 3), the quantum state shared between Alice and Bob after transmission can be expressed by the following formula:
and . For the quantum state , the bit error rate of Alice and Bob’s measurements on different bases can be expressed as (four-state or six-state protocol), (four-state or six-state protocol), and (six-state protocol). Eve can steal information and reduce the key rate by choosing the certain value and the secret key rate can be given by [20]:
In the AD method, Alice and Bob divide their own raw bits into blocks and of size b. Then, choosing a random binary value c, Alice sends to Bob. Bob compares this bitstring with their bitstring and accepts the security of information only if the results are either all zeros or all ones in the block. In the two cases accepted, Alice (Bob) saves the first bit of the initial string as the raw key. Thus, AD can discern highly correlated bitstring from weakly correlated information as the final raw key. Obviously, the successful probability of the AD method on a certain block of size b can be calculated by:
After performing the AD step, the practical QBER value in the Z basis can be replaced by , and the practical QBER in the X basis also can be recalculated. The quantum state shared between Alice and Bob can be replaced by:
The QKD protocol enhanced by the AD method can achieve the secret key at rate [20]:
Based on the previous analysis, the AD method can be combined with the QKD protocol. It has been widely used in other protocols in previous works. Similarly, the AD method can be applied to further optimize the properties of quantum channels in the asymmetric MDI-QKD. When the AD method is combined with the asymmetric seven-intensity MDI-QKD protocol, the secret key rate can be estimated by the following formula:
where is the probability of both Alice and Bob’s signal states emitting single-photon events, is the successful probability of the AD method, is the error rate value after the AD method, and and are the single-photon error rate in the X and Z bases, respectively. Note that , , and can be estimated with the decoy-state method.
3. Results
In this work, we explore the combination of a QKD and a post-processing method. We adopt the asymmetric seven-intensity MDI-QKD protocol and the AD method, which can improve the performance of asymmetric MDI-QKD protocol greatly. In this section, numerical simulations of the asymmetric seven-intensity MDI-QKD protocol with AD method are given and the simulation parameters are shown in Table 1. After analyzing the simulation results, we obtained the following significant research results.

Table 1.
The basic system parameters used in our numerical simulations. and are the efficiency and dark count rate of detectors at Charlie’s side; : the misalignment error of the QKD system; : the error correction efficiency; N: the number of pulse pairs Alice and Bob send.
We analyze the secret key rate of the asymmetric MDI-QKD protocol with and without the AD method, and the corresponding comparison results are shown in Figure 1 under different conditions = 0 dB, 12 dB, 24 dB. The figure shows that the key rate with and without AD are consistent within a short distance. However, for example, the red line with = 12 dB, the AD method has a clear advantage at a transmission loss of about 33 dB, and a final transmission loss reaching 39 dB as well as the secret key rate showing a clear improvement. For a more obvious exploration of the reason, we present Figure 2 with respect to b. We can observe that, in the above example, the value of b at about 33 dB has changed from 1 to 2, indicating that the AD method begins to work. With the increase of transmission loss, the AD method requires a larger b value to obtain a tight correlation from weak correlation. Furthermore, the results of the above case are similar to the other two cases ( = 0 dB, = 24 dB). Therefore, the AD method can improve the key generation rate of asymmetric MDI-QKD over a long distance.
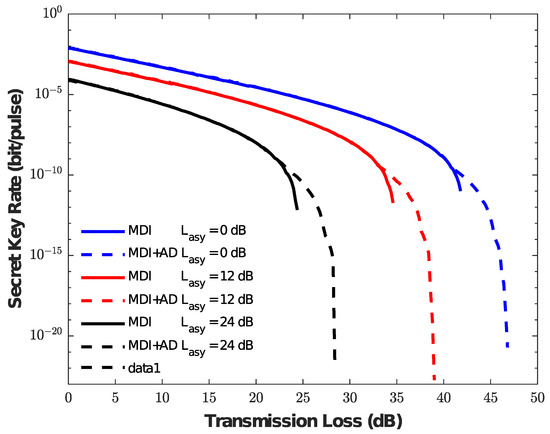
Figure 1.
Comparison of the secret key generation rate versus the transmission loss. The value is the loss difference of Alice to Charlie and Bob to Charlie. The different colors represent loss difference, which is = 0 dB, = 12 dB, and = 24 dB, respectively. The solid line represents the secret key without the AD method, and the dotted line represents the secret key with the AD method.
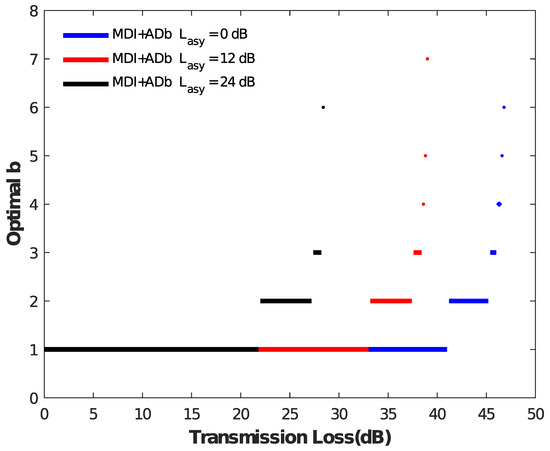
Figure 2.
Results of the optimal b versus the transmission loss. The black, red, and blue represent the values = 0 dB, = 12 dB, and = 24 dB, respectively. When value b is not equal to 1, the AD method can further improve the secret key rate and transmission distance of the asymmetric MDI-QKD protocol.
Additionally, we also further investigate the specific effects of the AD method on an asymmetric MDI-QKD under various values , and the results are shown in Figure 3. We describe the meaning of Figure 3 and give a detailed definition of the improved percentage. Generally, when the degree of asymmetry is large, the deterioration of the key rate becomes more obvious. However, after the AD method is used, it can be clearly seen in Figure 3 that the improvement effect of the AD method becomes more obvious with the increase of the degree of asymmetry. For example, the improved percentage can reach about 35% when the value = 35 dB, which means that AD method can better solve some transmission performance bottlenecks of the entire network.
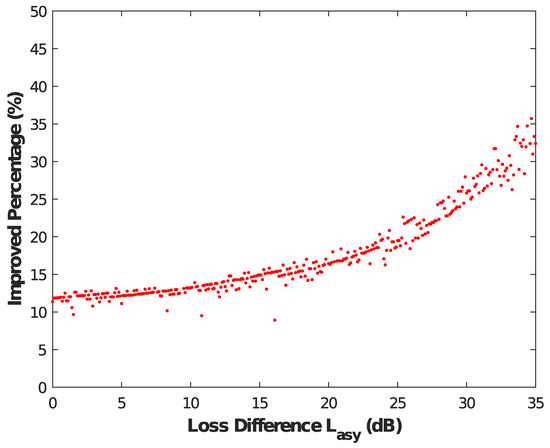
Figure 3.
Results of the value versus the improved percentage. The improved transmission loss is the difference of the maximum transmission loss of the asymmetric MDI-QKD with and without the AD method, and we define the improved percentage as the difference divided by the latter. With the increasing degree of asymmetry, the improved percentage also becomes better.
By the above analysis, the AD method indeed can increase the propagation distance when the number of pulse pairs . In order to further analyze the finite size effects, we give the simulation results in Figure 4 under different values of N when the value = 12 dB. As can be seen from Figure 4, the AD method improves the performance of the asymmetric MDI-QKD protocol under various finite-size effects. Even though there is a large statistical fluctuation when the number of pulse pairs , the AD method can still tolerate transmission losses of more than 5 dB, which means that AD method can also be more adaptable with finite-size cases.
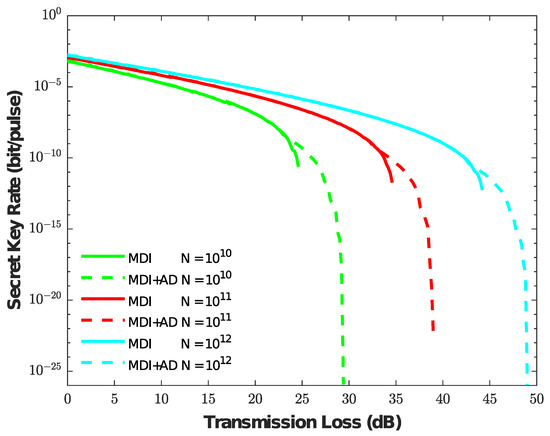
Figure 4.
Comparison of the secret key generation rate versus the transmission loss when the value = 12 dB. The different colors represent the values , , and , respectively. The solid line represents the secret key without the AD method, and the dotted line represents the secret key with the AD method.
4. Conclusions
The AD method, a classical algorithm based on information theory, can be combined with QKD without changing the existing system structure. Specifically, the AD method can be combined with an asymmetric seven-intensity MDI-QKD to improve the robustness effectively, so as to distinguish and extract highly correlated bit pairs from the weakly correlated information as the final secret key. The AD method has a better performance for the asymmetric MDI-QKD protocol. The greater the degree of asymmetry, the better the improvement of the AD method. The AD method can also improve the performance of the asymmetric MDI-QKD protocol under various finite-size effects, and can be more adaptable with finite-size cases. Our work may play a role in measurement-device-independent networks.
Author Contributions
Conceptualization, J.L. and Q.W.; Methodology, K.Z., J.L., H.D., C.Z. and Q.W.; Software, K.Z., J.L., H.D. and C.Z.; Validation, K.Z., J.L., H.D., X.Z., C.Z. and Q.W.; Formal analysis, K.Z., J.L., X.Z. and C.Z.; Investigation, J.L. and C.Z.; Resources, Q.W.; Data curation, K.Z., J.L., X.Z. and C.Z.; Writing—original draft, K.Z. and X.Z.; Writing—review & editing, J.L., H.D., X.Z. and Q.W.; Visualization, K.Z. and J.L.; Supervision, X.Z. and Q.W.; Project administration, Q.W.; Funding acquisition, X.Z. and Q.W. All authors have read and agreed to the published version of the manuscript.
Funding
We gratefully acknowledge the financial support from the National Natural Science Foundation of China (12074194, 12104240, 62101285); Industrial Prospect and Key Core Technology Projects of Jiangsu provincial key R&D Program (E2022071); Natural Science Foundation of Jiangsu Province (BK20192001, BK20210582); Postgraduate Research & Practice Innovation Program of Jiangsu Province (KYCX20_0726); Natural Science Foundation of the Jiangsu Higher Education Institutions (21KJB140014), and NUPTSF (NY220122, NY220123).
Institutional Review Board Statement
Not applicable.
Data Availability Statement
The data that support the findings of this study are available from the corresponding author upon reasonable request.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, 9–12 December 1984. [Google Scholar]
- Ekert, A.K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991, 67, 661–663. [Google Scholar] [CrossRef] [PubMed]
- Bennett, C.H.; Brassard, G.; Mermin, N.D. Quantum cryptography without Bell’s theorem. Phys. Rev. Lett. 1992, 68, 557. [Google Scholar] [CrossRef] [PubMed]
- Lutkenhaus, N.; Jahma, M. Quantum key distribution with realistic states: Photon-number statistics in the photon-number splitting attack. New J. Phys. 2002, 4, 44. [Google Scholar] [CrossRef]
- Lo, H.K.; Ma, X.F.; Chen, K. Decoy State Quantum Key Distribution. Phys. Rev. Lett. 2005, 94, 230504. [Google Scholar] [CrossRef]
- Wang, X.B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 2005, 94, 230503. [Google Scholar] [CrossRef]
- Wang, X.B. Three-intensity decoy-state method for device-independent quantum key distribution with basis-dependent errors. Phys. Rev. A 2013, 87, 12320. [Google Scholar] [CrossRef]
- Yu, Z.W.; Zhou, Y.H.; Wang, X.B. Statistical fluctuation analysis for measurement-device-independent quantum key distribution with three-intensity decoy-state method. Phys. Rev. A 2015, 91, 032318. [Google Scholar] [CrossRef]
- Zhang, C.H.; Zhang, C.M.; Wang, Q. Improving the Performance of Practical Decoy-State Measurement-Device-Independent Quantum Key Distribution with Biased Basis Choice. Theor. Comput. Phys. 2018, 70, 331. [Google Scholar] [CrossRef]
- Lo, H.K. Measurement-Device-Independent Quantum Key Distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Zhou, Y.H.; Yu, Z.W.; Wang, X.B. Making the decoy-state measurement-device independent quantum key distribution practically useful. Phys. Rev. A 2016, 93, 042324. [Google Scholar] [CrossRef]
- Liu, H.; Wang, W.; Wei, K.; Fang, X.T.; Li, L.; Liu, N.L.; Liang, H.; Zhang, S.J.; Zhang, W.; Li, H.; et al. Experimental Demonstration of High-Rate Measurement-Device-Independent Quantum Key Distribution over Asymmetric Channels. Phys. Rev. Lett. 2019, 122, 160501. [Google Scholar] [CrossRef]
- Chen, Y.P.; Liu, J.Y.; Sun, M.S.; Zhou, X.Y.; Zhang, C.H.; Li, J.; Wang, Q. Experimental measurement-device-independent quantum key distribution with the double-scanning method. Opt. Lett. 2021, 46, 3729–3732. [Google Scholar] [CrossRef]
- Jiang, C.; Yu, Z.W.; Hu, X.L.; Wang, X.B. Higher key rate of measurement-deviceindependent quantum key distribution through joint data processing. Phys. Rev. A 2021, 103, 012402. [Google Scholar] [CrossRef]
- Lu, F.Y.; Wang, Z.H.; Yin, Z.Q.; Wang, S.; Wang, R.; Guo, G.C.; Han, Z.F. Unbalanced-basis-misalignment-tolerant measurement-device-independent quantum key distribution. Optica 2022, 9, 886–893. [Google Scholar] [CrossRef]
- Cao, Y.; Li, Y.H.; Yang, K.X.; Jiang, Y.F.; Li, S.L.; Hu, X.L.; Abulizi, M.; Li, C.L.; Zhang, W.J.; Sun, Q.C.; et al. Long-Distance Free-Space Measurement-Device-Independent Quantum Key Distribution. Phys. Rev. Lett. 2020, 125, 260503. [Google Scholar] [CrossRef] [PubMed]
- Wei, K.J.; Li, W.; Tan, H.; Li, Y.; Min, H.; Zhang, W.J.; Li, H.; You, L.X.; Wang, Z.; Jiang, X.; et al. High-Speed Measurement-Device-Independent Quantum Key Distribution with Integrated Silicon Photonics. Phys. Rev. X 2020, 10, 031030. [Google Scholar] [CrossRef]
- Jie, G.; Yuan, F.; Lu, F.Y.; Wang, S.; Yin, Z.Q.; He, D.Y.; Chen, W.; Zhou, Z.; Wang, H.Z.; Teng, J.; et al. Robust and Adaptable Quantum Key Distribution Network without Trusted Nodes. Optica 2022, 9, 812. [Google Scholar]
- Wang, W.Y.; Xu, F.H.; Lo, H.K. Asymmetric Protocols for Scalable High-Rate Measurement-Device-Independent Quantum Key Distribution Networks. Phys. Rev. X 2019, 9, 041012. [Google Scholar] [CrossRef]
- Renner, R. Security of quantum key distribution. Int. J. Quant. Inf. 2008, 6, 1–127. [Google Scholar] [CrossRef]
- Wang, R.Q.; Zhang, C.M.; Yin, Z.Q.; Li, H.W.; Wang, S.; Chen, W.; Guo, G.C.; Han, Z.F. Phase-matching quantum key distribution with advantage distillation. New J. Phys. 2022, 24, 73049. [Google Scholar] [CrossRef]
- Li, H.W.; Zhang, C.M.; Jiang, M.S.; Cai, Q.Y. Improving the performance of practical decoy-state quantum key distribution with advantage distillation technology. Commun. Phys. 2022, 5, 53. [Google Scholar] [CrossRef]
- Li, H.W.; Wang, R.Q.; Zhang, C.M.; Cai, Q.Y. Improving the performance of twin-field quantum key distribution with advantage distillation technology. arXiv 2022, arXiv:2202.10059. [Google Scholar]
- Xu, F.H.; Curty, M.; Qi, B.; Lo, H.K. Practical aspects of measurement-device-independent quantum key distribution. New J. Phys. 2013, 15, 113007. [Google Scholar] [CrossRef]
- Wang, Q.; Wang, X.B. Simulating of the measurement-device independent quantum key distribution with phase randomized general sources. Sci. Rep. 2014, 4, 4612. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).