1. Introduction
In 2000, Ahlswede et al. [
1] proposed the general concept of network coding. In particular, they investigated the single-source multicast network coding problem, where the source symbols generated by a single source node are required to multicast to multiple sink nodes through a noiseless network while the nodes in the network are allowed to process the received information. It was proven in [
1] that if coding is applied at the intermediate nodes (rather than routing only), the source node can multicast source symbols to all the sink nodes at the theoretically maximum rate, i.e., the smallest minimum cut capacity separating a sink node from the source node, as the alphabet size of both the information source and the channel transmission symbol tends toward infinity. In 2003, Li et al. [
2] proved that linear network coding over a finite alphabet is sufficient for optimal multicast by means of a vector space approach. Independently, Koetter and Médard [
3] developed an algebraic characterization of linear network coding by means of a matrix approach. Jaggi et al. [
4] further presented a deterministic polynomial-time algorithm for constructing a linear network code. For comprehensive discussions of network coding, we refer the reader to [
5,
6,
7,
8,
9,
10].
In the paradigm of network coding, information-theoretic security in the presence of a wiretapper is naturally considered (cf. [
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23,
24,
25,
26,
27,
28]), called the
secure network coding problem. In the model of secure network coding over a wiretap network, (i) the source node multicasts the source symbols to all the sink nodes, which, as legal users, are required to correctly decode the source symbols; and (ii) the wiretapper, who can access any one but not more than one wiretap set of communication channels, is not allowed to obtain any information about the source symbols. The classical information-theoretically secure models, e.g., Shannon’s cipher system [
29], secret sharing [
30,
31] and the wiretap channel II [
32], can be regarded as special cases of the secure network coding model. In particular, a wiretap network is called an
r-
wiretap network if the wiretapper can fully access an arbitrary subset of, at most,
r edges, where the non-negative integer
r is called the
security level.
In the model of secure network coding, to guarantee the required information-theoretic security, it is necessary to randomize the source symbols to combat the wiretapper. Cai and Yeung [
11] presented a code construction for the
r-wiretap network. El Rouayheb et al. [
12] further showed that the Cai–Yeung code construction can be viewed as a network generalization of the code construction for wiretap channel II in [
32]. Motivated by El Rouayheb et al., Silva and Kschischang [
13] proposed a universal design of security network codes based on rank-metric codes. For the construction of security network codes in [
11,
12,
13]. However, the existing upper bounds on the minimum required alphabet size may be too large for implementation for certain applications in terms of computational complexity and storage requirement. Feldman et al. [
33] showed that for a given security level, the alphabet size can be reduced by sacrificing a small fraction of the information rate. However, if the information rate is not sacrificed, whether it is possible to reduce the required alphabet size is considered an open problem [
12,
17]. Recently, Guang and Yeung [
18] developed a systematic graph-theoretic approach to improve the upper bound on the minimum required alphabet size for the existence of secure network codes, achieving an improvement of general significance. Subsequently, in order to tackle the problem of secure network coding when the information rate and the secure level may vary over time, Guang et al. [
19] put forward local-encoding-preserving secure network coding, where a family of secure linear network codes is called local-encoding-preserving if all the codes in this family use a common local encoding operation at each intermediate node in the network. They also constructed a family of local-encoding-preserving secure linear network codes applicable for all possible pairs of rate and security level. We note that the variable-rate linear network coding problem without security consideration was previously investigated by Fong and Yeung [
34].
In this paper, we put forward the model of multiple linear-combination security network coding, where multiple linear combinations (containing single linear combination as a special case) of the source symbols are required to be protected from the wiretapper. More precisely, in this model over an
r-wiretap network, (i) the single source node generates source symbols over a finite field
F, and all the source symbols are required to be correctly decoded at all the sink nodes; and (ii) for a predefined set of linear combinations of the source symbols, the wiretapper, who can fully access any channel subset of a size not larger than
r, is not allowed to obtain any information about these linear combinations. For the above security model with security level
r, the (linear-combination) security capacity is defined as the maximum average number of source symbols that can be securely multicast to all the sink nodes for one use of the network under the above linear-combination security constraint. A model related to the current work is that considered by Bhattad and Narayanan [
23], which contains weakly secure network coding as a special case. The relation between the current work and that of Bhattad and Narayanan [
23] is discussed in
Appendix A.
In this paper, we investigate the security capacity and the code construction for this model and analyze the asymptotic behavior of the security capacity and code construction for a sequence of linear-combination security models. The main contributions and organization of this paper are as follows:
In
Section 2, we formally present the model of linear-combination security network coding and the preliminaries, including the necessary notation and definitions.
In
Section 3, we characterize the security capacity by considering different cases of the security level
r. We first prove that
is the maximum security level such that the source symbols can be securely multicast to all sink nodes with a positive rate, where
is the smallest minimum cut capacity separating a sink node from the source node. Therefore, the security capacity is zero for
. For any nontrivial security level
, we prove upper bounds on the security capacity in terms of the ratio
of the rank of the linear-combination security constraint to the number of source symbols.
We further develop a systematic construction of linear security network codes, which is applicable to an arbitrary linear-combination security model. Based on the obtained upper bounds and the developed code construction, we fully characterize the security capacity for any possible pair of the number of the source symbols and the linear-combination security constraint. We also determine the threshold value such that there is no penalty on the security capacity compared with the capacity without any security consideration when the ratio is not larger than .
In
Section 4, we fully characterize the asymptotic behavior of the security capacity for a sequence of linear-combination security models and prove that our code construction is asymptotically optimal.
We conclude in
Section 5 with a summary of our results.
2. Preliminaries
Consider a communication network whose communication channels are point-to-point. The network is represented by a directed acyclic graph , where and are finite sets of nodes and edges, respectively. Here, an edge in the graph corresponds to a point-to-point channel in the network. In the graph , multiple edges between two nodes are allowed. We assume that an element in a finite field F can be reliably transmitted on each edge for each use. We use and to denote the tail node and the head node of an edge e, respectively. For a node , we let and , i.e., and are the set of input edges and the set of output edges, respectively. Furthermore, a sequence of edges is called a (directed) path from the node to the node if for . For two nodes u and v with , an edge subset is called a cut separating v from u if no path exists from u to v upon removing the edges in C. The capacity of a cut separating v from u is defined as the size of this cut. A cut C separating v from u is called a minimum cut separating v from u if there does not exist a cut separating v from u such that . The capacity of a minimum cut separating v from u is called the minimum cut capacity separating v from u, as denoted by . There is a single source node and a set of sink nodes on the graph . Without loss of generality, we assume that the source node s has no input edges and that every sink node has no output edges, i.e., . The graph , together with s and T, forms a network denoted by .
The source node
s generates
Lsource symbols that are independent and identically distributed (i.i.d.) random variables with a uniform distribution on the finite field
F. All the source symbols are required to be multicast to every sink node
t in
T by using the network
multiple times, i.e., transmitting multiple elements in
F on each edge by using the edge multiple times. There is a wiretapper who can eavesdrop any edge subset of a size up to the security level
r, while, for a positive integer
, the
linear combinations of the source symbols
over the finite field
F are required to be protected from the wiretapper, where
are constants in
F; that is, the wiretapper is not allowed to obtain any information about the multiple linear combinations of the source symbols given in (
1). Furthermore, we let
, and
is an
matrix. Then, the
linear combinations in (
1) can be written as
. Without loss of generality, we assume that
and that the matrix
has full column rank, i.e.,
In this model, the security level
r is known by the source node and sink nodes, but which edge subset is eavesdropped by the wiretapper is unknown. It suffices to consider only the wiretap sets of a size exactly equal to
r. Then, we let
where each edge subset
is called a
wiretap set. We use
to denote the above linear-combination security model.
Next, we define a (linear-combination) security network code for the security model . In order to combat the wiretapper, we may need randomness to randomize the source symbols. However, as we show, it is not always necessary to randomize the source symbols. As part of the code to be defined, we assume that the key is a random variable uniformly distributed over a finite set , which is available only at the source node s. The key and the source symbols are assumed to be mutually independent. A security network code is defined as follows. First, we let and be arbitrary outputs of the source symbol and the key , respectively, . We further let , which is the output of the vector of source symbols . A security network code consists of:
A
local encoding function for each edge
, where
with
denoting the image set of
;
A decoding function for each sink node
:
to decode the source symbols
at
t.
Furthermore, we use
to denote the message transmitted on each edge
by using the code
under
and
. With the encoding mechanism described in (
2), we readily see that
is a function of
and
, as denoted by
(i.e.,
), where
can be obtained by recursively applying the local encoding functions
according to any ancestral order of the edges in
. More precisely, for each
, we have
where
and
for an edge subset
so that
. We call
the
global encoding function of the edge
e for the code
.
For the security model , a security network code is admissible if the following decoding and security conditions are satisfied:
Decoding condition: All the source symbols are correctly decoded for each sink node
, i.e., for each
,
Security condition: for each wiretap set,
,
where
, and
is the random variable transmitted on the edge
e.
For an admissible
security network code
, we let
for each edge
e in
, which is regarded as the number of times the edge
e is used for transmission when applying the code
. We further let
. Then, the
rate of
is defined by
which is the average number of source symbols that can be securely multicast to all the sink nodes for one use of the network using the code
.
Furthermore, the
security capacity for this model
is defined as the maximum rate of all admissible
security network codes, i.e.,
According to the definition of the rate in (
5), characterizing the security capacity
is equivalent to determining the minimum
over all the admissible
security network codes, i.e.,
For instance, a special case of the linear-combination security model
is algebraic-sum security network coding, as elaborated below. In this model, the source node
s generates
L source symbols
, which are required to be multicast to every sink node
, and the wiretapper, who can eavesdrop any edge subset of size
r, is not allowed to obtain any information about the
m algebraic sums of the source symbols:
where
, and
. For this algebraic-sum security model, when
, we adopt the convention that
for all
. Then, Equation (
6) becomes
, i.e., the algebraic sum
of all the
L source symbols is required to be protected from the wiretapper. When
, we have
, where
; thus, all the source symbols
are required to be protected from the wiretapper. This is the standard model of secure network coding, which has been widely studied in the literature, e.g., [
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23,
24].
An example scenario for the application of the linear-combination security model is as follows. A predefined set of linear combinations of the source symbols is required to be protected from the wiretapper, while other linear combinations are unprotected. The source node
s generates
L source symbols
in the finite field
F, which are required to be multicast to every sink node
. The
matrix
is regarded as an
F-valued parity-check matrix. We denote the solution space of the system of linear equations
over
F as
, i.e.,
where
is the zero row
-vector. According to the value of
, for every output
of
, the vector space
can be partitioned into
cosets of the solution space given by
, where
In this scenario, we desire to protect the information as to which coset
the vector
lies in, which may contain some useful information for the wiretapper. In other words, the information about the specified linear combinations
needs to be protected from the wiretapper, while other linear combinations are unprotected.
3. Characterization of the Capacity ofthe Security Model
3.1. Upper Bounds on the Security Capacity
Consider a linear-combination security model
. We first consider the trivial case of
, where
. In this case, for a sink node
such that
, the wiretapper is able to decode the source symbols, provided that the sink node
t correctly decodes them. This shows that the security capacity is
for
, which implies that
is an upper bound on the maximum security level for which the source symbols can be multicast with a positive rate. For another trivial case
, the security model
becomes a single-source multicast network coding problem without any security consideration. Given the fact that the maximum rate at which the source symbols can be correctly multicast to all the sink nodes is
(cf. [
1,
6]), we thus obtain that
or, equivalently,
Next, we consider
. We readily see that an admissible
security network code
is also a network code such that all the
L source symbols can be correctly decoded at each
. This immediately implies that
can be lower-bounded by
for any security level
, i.e.,
Furthermore, we present the following lemma, which asserts a non-trivial lower bound on
.
Lemma 1. Consider a linear-combination security model with a security level of , where . Let . Then, Proof. First, we claim that
where
. To see this, we consider an arbitrary row vector
and obtain
where the equality
holds because the source symbols
are i.i.d. with the uniform distribution on
F.
We now consider an arbitrary admissible
security network code:
. For an edge subset
C that separates a sink node
from the source node
s, it follows from the decoding condition (
3) that
. This immediately implies that
Furthermore, for any wiretap set
with
, it follows from the security condition (
4) that
Combining (
11) and (
12), we obtain
where the inequality (
13) holds because
takes values in
, and the inequality (14) follows from
and the inequality (15) follows from
.
Combining (
9) and (15), we obtain
Note that the above inequality is true for each sink node
and all the pairs
of the cut
C separating
t from
s and the wiretap set
such that
. We thus obtain
where
. For each
, we have
According to the definition of
, this lower bound is achievable for some
and
such that
. It then follows that
Furthermore, since
is an integer, we have
In addition, because the above lower bound (
16) on
is valid for any admissible
security network code
, we obtain
The lemma is thus proven. □
The lower bounds in (
7) and (
8) on
apply to all
. For a specific value of
, one of them can be tighter than the other. By comparing these bounds, we can readily obtain the upper bounds on the security capacity
as stated in the following theorem.
Theorem 1. Consider a linear-combination security model with a security level of , where . Let Proof. By comparing the lower bounds ((
7) and (
8)) on
, we immediately obtain
if
, then
implying that
If
, we have
implying that
We have thus proven the theorem. □
3.2. Characterization of the Security Capacity
Next, we present a code construction for the security model with , which shows that the upper bounds in Theorem 1 for both cases of are tight. We thus obtain a full characterization of the security capacity for the security model , as stated in the following theorem.
Theorem 2. Consider a linear-combination security model over a finite field F, where and . Let This theorem reveals the somewhat surprising fact that for the case of
, there is no penalty on the security capacity compared with the capacity without any security consideration. In
Section 4, we further investigate the asymptotic behavior of the security capacity for a sequence of the security models as
L tends toward infinity. We not only characterize the asymptotic behavior of the security capacity but also show the asymptotic optimality of our construction.
We first define a linear security network code for the security model
. Briefly, a
security network code
is
linear if the local encoding functions for all the edges are linear. Specifically, we recall that
is an arbitrary output of the vector of source symbols
. Let
, where the non-negative integer
z is specified later. Then, the key
is a random row vector uniformly distributed on
. We further let
be an arbitrary output of
. Consequently, for a
linear security network code
, all the global encoding functions
are linear functions of
and
. Therefore, there exists an
F-valued
matrix
for each
such that
where
, and
is called the
global encoding matrix of the edge
e for the code
. In particular, if
, then the code
is called a
scalar-linear security network code.
In the following, for the nontrivial case of a security model with a security level of , we develop a construction of admissible linear security network codes that can be applied to any pair . This code construction shows that the upper bounds in Theorem 1 for both cases of are tight, which we state in the following theorem.
Theorem 3. Consider a linear-combination security model over a finite field F, where , and . LetThen, there exists an admissible linear security network code such that 3.3. Proof of Theorem 3
In this subsection, we provide the proof of Theorem 3, which includes three parts: code construction, verification of the decoding condition and verification of the security condition.
- ▸
Code construction:
We consider a linear-combination security model
over a finite field
F, where
and
. In the following, we construct an admissible
linear security network code such that the
L source symbols can be securely multicast to all the sink nodes by transmitting
n symbols on each edge, i.e., using the network
n times, where
(cf. (
21) and (
22)). For any
, we let
i.e.,
According to (
24), when
, it is unnecessary to randomize the source symbols to guarantee linear-combination security. Furthermore, for any pair
satisfying (
24), we observe that
The first inequality in (
25) is straightforward. To prove the second inequality, we consider two cases below.
- Case 1:
.
According to (
24) we have
, and thus:
Furthermore, it follows from (
23) that for
,
and for
,
(cf. (
18) for the first inequality in the above equation). Together with (
26), we immediately prove that
for this case.
- Case 2:
.
According to (
24), we have
Furthermore, it follows from (
23) that for
,
(cf. (
17) for the first inequality in the above equation), and for
,
Together with (
27), we immediately obtain that
for this case. Combining the two cases, we have proven the second inequality in (
25).
According to (
25), we have
. This implies that the
symbols in
F generated by the source node
s, which contain the
L source symbols and the key of
z symbols, can be multicast to all the sink nodes in
T by using the network
n times. To elaborate this, we first claim that
When
, it follows from (
23) that
When
, according to (
23), we obtain
where the last two inequalities follow from (
23) and (
25), respectively.
Thus, we have proven (
28).
Now, we let
be the
source symbols, and divide them into
n groups
,
and
, where for
,
contains
source symbols, and
contains the remaining
source symbols. Here, we note from (
25) and (
28) that
Thus, it suffices to construct, at most, 2 scalar-linear network codes of dimensions
and
, respectively, to multicast the
source symbols to all the sink nodes.
Let
be a
-dimensional scalar-linear network code in the network
, of which the global encoding vectors are column vectors
in
for all
, and let
be an
-dimensional scalar-linear network code on
, of which the global encoding vectors are column vectors
in
for all
(cf. [
1,
2] and [
6]). We use two codes
and
to construct an
-dimensional (vector-) linear network code
on the network
such that
n symbols are transmitted on each edge
. Specifically, for each
, we let
which is an
F-valued
matrix regarded as the global encoding matrix for the code
.
Next, for an edge
, we use
to denote the vector space spanned by the column vectors of the matrix
, i.e.,
Furthermore, for a wiretap set
, we use
to denote the
matrix whose column vectors are the column vectors of
for all the edges
, i.e.,
Then, similarly, we use
to denote the vector space spanned by the column vectors of the matrix
, i.e.,
Hence, we readily see that
Now, we claim that there exist
F-valued column
-vectors
such that
To show this, we prove by induction on
that if we have
linearly independent column vectors
in
such that
then we can choose a column vector
such that
provided that
. We consider
where the inequality (
30) follows because
inequality (31) follows from
according to (
25) and inequality (32) follows from
Thus, we have proven the existence of such vectors
that satisfy the condition (
29).
With the vectors
, we let
U be an
F-valued
invertible matrix such that
are the first
column vectors of
U. Furthermore, we consider an
matrix
where
is the
zero matrix. In particular, when
(cf. (
24)),
. Recalling that
has full column rank, we readily see that
also has full column rank. With the full-column-rank matrix
, we let
be an
F-valued
invertible matrix such that the column vectors of
are the first
column vectors of
. Then, we define the matrix
which is of size
and also invertible over
F.
Now, we consider the transformation
of the code
by the matrix
Q, i.e.,
is an
F-valued
-dimensional linear network code on the network
, of which all the global encoding matrices are
(cf. the transformation of a scalar-linear network code in [
6], Section 19.3.1 and [
19], Theorem 2). Next, we show that
is an admissible
F-valued
linear security network code for the security model
by verifying the decoding and security conditions.
Remark 1. We now discuss the computational complexity of our code construction. Our code construction consists of two parts: (i) constructing the two linear network codes and of different dimensions, which are used to multicast all the symbols to the sink nodes; and (ii) constructing the transformation matrix Q, or equivalently, constructing the column -vectors that satisfy the condition (29). We analyze the complexity of the two parts as follows. The linear network codes and can be constructed in polynomial time (cf. [4,6,7]); To obtain the column -vectors that satisfy (29), we, in turn, choose vectors as follows: According to ([35], Lemma 11), the vectors can be found in
By combining the above analysis, our code construction can be implemented in polynomial time.
- ▸
Verification of the decoding condition:
We continue to consider the output of the source , where is the vector of source symbols, and is the key. In using the code , the implementation of the global encoding matrices is equivalent to linearly transforming into , then using the code to multicast to all the sink nodes in T.
Since the vector can be correctly decoded at each when applying the code , can be also correctly decoded at each , as can the vector of source symbols. Thus, we have verified the decoding condition.
- ▸
Verification of the security condition:
In order to verify the security condition (
4), we need the next lemma, which plays a crucial role in our code construction. This lemma provides a necessary and sufficient condition for a linear security network code to satisfy the security condition (
4). For an edge
,
denotes the vector space spanned by the column vectors of
, i.e.,
Furthermore, for a wiretap set
, we let
be the
matrix that contains all the column vectors of the global encoding matrices
for all the edges
, i.e.,
We let
be the vector space spanned by the column vectors of
. Evidently,
Lemma 2. For the security model over a finite field F with , let be an F-valued linear security network code, of which the global encoding matrices are matrices . Then, for the code , the security condition (4) is satisfied if and only ifwhere is an matrix as defined in (33). Now, we start to verify the security condition for our code construction. Toward this end, according to Lemma 2, it suffices to verify (
35). For the constructed
linear security network code
, we have
(cf. (
29)). We recall (
34) that
is an
invertible matrix. Then, according to (
36), we immediately obtain
We note that
Furthermore, we write
where we recall that
are the first
column vectors of
U,
is the
identity matrix and
is the
zero matrix. Then, we can see that
where (
39) follows from
(cf. (
34)), and (40) follows because the column vectors of
are the first
column vectors of
. Combining (
38) and (40) with (
37), we immediately prove that
Thus, according to Lemma 2, we have verified the security condition. Combining all the above, Theorem 3 has been proven.
3.4. An Example to Illustrate Our Code Construction
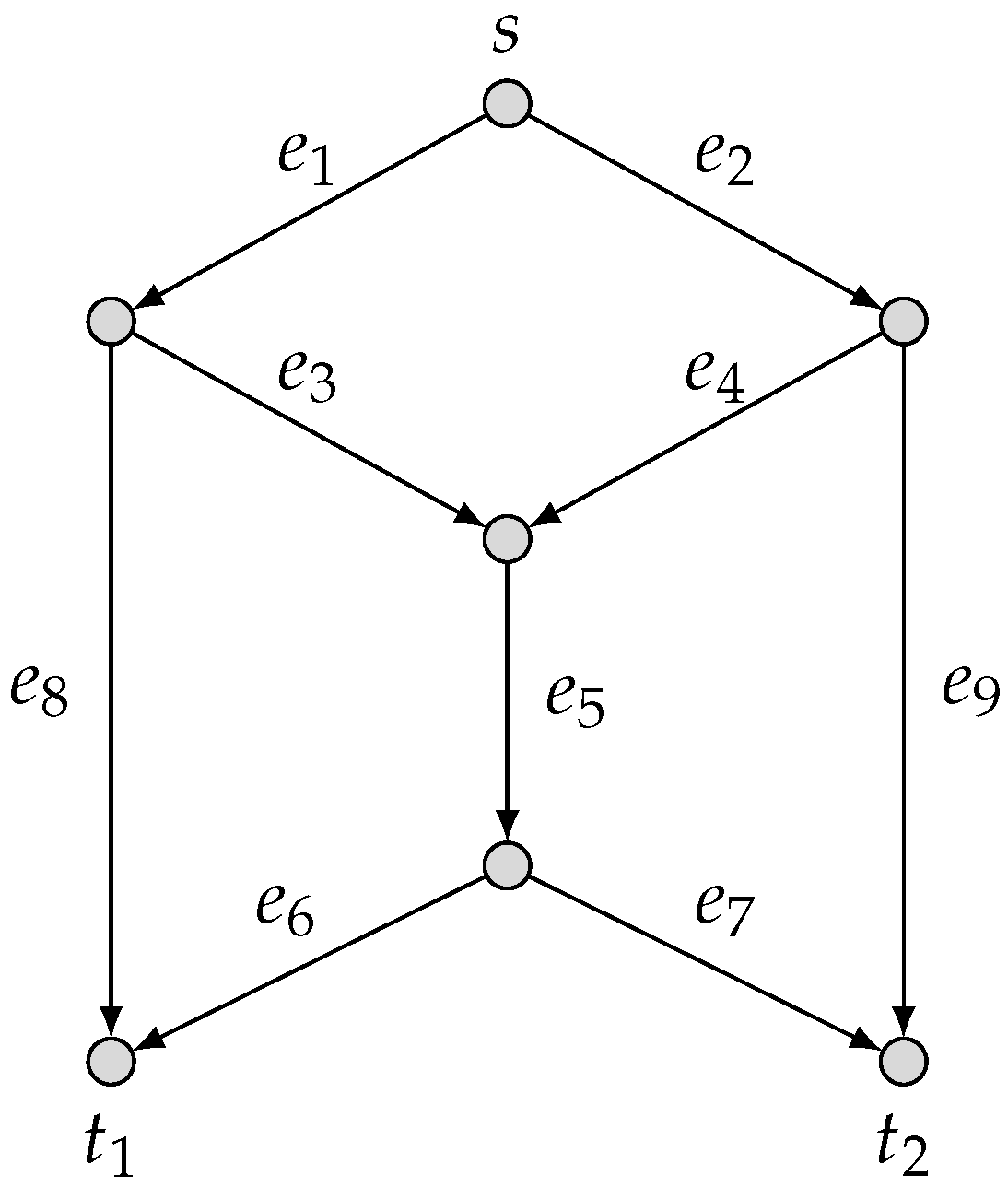
Let
be the butterfly network as depicted in
Figure 1. For the security model
, we consider two linear-combination security models
and
over the field
, where
Namely, in the
security model, the algebraic sum
of the two source symbols is required to be protected from the wiretapper, and in the
security model, the algebraic sums
and
of the source symbols are required to be protected from the wiretapper.
In this model, the source node
s generates two source symbols
and
in
, and the algebraic sum
needs to be protected. According to (
41), we have
Therefore, we have
, i.e., the first case in Theorem 2. Next, we construct an optimal
-valued
linear security network code for the
security model, which achieves a security capacity of 2.
According to our code construction, it follows from (
23) and (
24) that we take
and
because
. We first consider an
-valued two-dimensional scalar-linear network code
on the network
, which is used to multicast two source symbols
and
in
to sink nodes
and
. The global encoding matrices (vectors) of
are
Clearly, the code
is not secure for the algebraic sum
because the wiretapper can obtain
by accessing the edge
on which
is transmitted. Based on the code
, we now construct a
scalar-linear security network code for the
security model.
Next, we let
, an
-valued column 2-vector such that
(cf. (
29)). Then, let
, a
invertible matrix on
such that
is the first column vector of
U. Furthermore, since
, we have
(cf. (
33)) and let
, which is a
invertible matrix on
such that
is the first column vector of
. According to (
34), we calculate
. Now, we obtain an admissible
-valued
scalar-linear security network code
, of which the global encoding matrices (vectors) are
. Specifically,
We use
, which takes values in
, to denote the message transmitted on each edge
. According to the above global encoding matrices of
, the messages
transmitted on the edges
are
as depicted in
Figure 2. We can readily verify the decoding and security conditions for the code
. In particular, in this case, we see that although no randomness is used to randomize the source symbols, the wiretapper cannot obtain any information about the algebraic sum
when any one edge is eavesdropped.
In this model, the source node
s generates three source symbols
and
in
, and two algebraic sums
and
need to be protected. According to (
41), we note that
; thus,
Therefore, we have
, i.e., the second case in Theorem 2. Next, we construct an optimal
-valued
linear security network code for the
security model, which achieves a security capacity of
.
According to our code construction, it follows from (
23) and (
24) that we take
and
because
according to
and
. We consider an
-valued four-dimensional (where
) linear network code
of rate 2, which is used to multicast the three source symbols
,
and
and a key
k in
to the sink nodes
and
. The
global encoding matrices of
are
We note that the code
is not secure because the wiretapper can obtain some information about
by accessing the edge
on which
and
are transmitted. Based on the code
, we now construct a linear secure network code for the
security model.
Let
be two
-valued column 4-vectors such that
(cf. (
29)). Then, let
be a
invertible matrix on
such that
and
are the first two column vectors of
U. Furthermore, since
, as mentioned above, we have
(cf. (
33)). Also let
be a
invertible matrix on
such that the column vectors of
are the first two column vectors of
. According to (
34), we calculate
Now, we obtain an admissible
-valued
linear security network code
, of which the
global encoding matrices are
; specifically,
We use
, which takes values in
, to denote the message transmitted on each edge
. According to the above global encoding matrices of
, the messages
transmitted on the edges
are
as depicted in
Figure 3.
For the and security models, as discussed in the above example, according to Theorem 3, admissible linear security network codes with rates of 2 and , respectively, can be constructed if the field size is . However, we see in the example that the field , of size 3 is sufficient for our code construction. This implies that the bound in Theorem 3 on the field size is only sufficient but not necessary for our code construction.
4. Asymptotic Behavior of the Security Capacity
In this section, we investigate the asymptotic behavior of the security capacity. For a fixed network and a security level r, we consider a sequence of the security models. The following theorem characterizes the asymptotic behavior of the security capacity for a sequence of security models .
Theorem 4. Consider a sequence of linear-combination security models over a finite field F for , where and . denotes the security capacity for each model . Letwhere for . If , then, If , with κ satisfying , then,
Proof. We first consider the case of
. Then, there exists a non-negative sequence,
with
, such that
We now use Theorem 2 to show that
To show this, consider the following two cases:
If
, it follows from (
19) that
If
, then we obtain
where the equality follows from (
20), and the inequality follows from (
42).
Combining (
43) and (
7) with Lemma 1, we further obtain that for each pair
,
We note that
Together with (
44), we have thus proven that
Next, we consider a case in which
, where
. Then, there exists a sequence
,
satisfying
such that
Here, we note that
may be negative. Together with
and
, there exists a positive integer
such that for each
,
which implies that
According to (
20) in Theorem 2, we have
so that
Thus, the theorem is proven. □
According to Theorem 4, we can see that for a sequence of security models
that satisfies
or
, where
, our code construction is
asymptotically optimal, i.e.,
where
is the code constructed for each model
by our code construction. To illustrate this, in the following, we consider several specific sequences of security models.
First, we consider a sequence of security models
in which all the ranks
are upper-bounded by a constant, such as
m, e.g., the security constraint of multiple algebraic sums,
as discussed in the last paragraph of
Section 2. With this, we have
which implies the inequality
. It then follows from the first case of Theorem 4 that
Next, we show that our code construction is asymptotically optimal. We first note that
Together with the first case of Theorem 3 (cf. (
21)), the constructed code
achieves a rate of
. This immediately implies that the equality (
45) is satisfied, namely that our code construction is asymptotically optimal for this example.
Next, we consider a sequence of security models
in which all the ranks
satisfy
We note that the sequence of
is not upper-bounded. According to Theorem 4, we can obtain the asymptotic behavior of the security capacity for the sequence of models
as follows:
Furthermore, it follows from Theorem 3 that
where
is the code constructed for each model
by the code construction. Comparing (
46) and (
47), we immediately see that the equality (
45) holds, which shows that our code construction is asymptotically optimal for this example.
Finally, we consider the special sequence of security models
for
, where
, i.e.,
for all
. This linear-combination security constraint is equivalent to protecting all the source symbols from the wiretapper, so each model
is equivalent to the standard secure-network coding model. Thus, we have
On the other hand, for each pair
, it follows from
and Theorem 3 that the
linear security network code
constructed by our code construction has a rate of
This implies that
Combining (
48) and (
49), we see that the equality (
45) holds, and thus, our code construction is also asymptotically optimal for this example.