Hybrid Threshold Denoising Framework Using Singular Value Decomposition for Side-Channel Analysis Preprocessing
Abstract
1. Introduction
- Three hard threshold calculation methods of truncated singular value decomposition are refined and defined based on the Schatten norm. These hard threshold selection methods are the normalized singular value threshold method, norm ratio singular value threshold method, and contribution rate singular value threshold method;
- Two kinds of singular value soft threshold operations are introduced to shrink and damping singular vectors, respectively;
- A hybrid threshold denoising framework using singular value decomposition based on low-rank matrix approximation (LRMA) theory was proposed by combining singular value hard threshold truncation and singular value soft threshold operation. The hybrid threshold denoising framework included normalized threshold shrinkage, norm ratio threshold shrinkage, contribution threshold shrinkage, normalized threshold damping, norm ratio threshold damping, and contribution threshold damping;
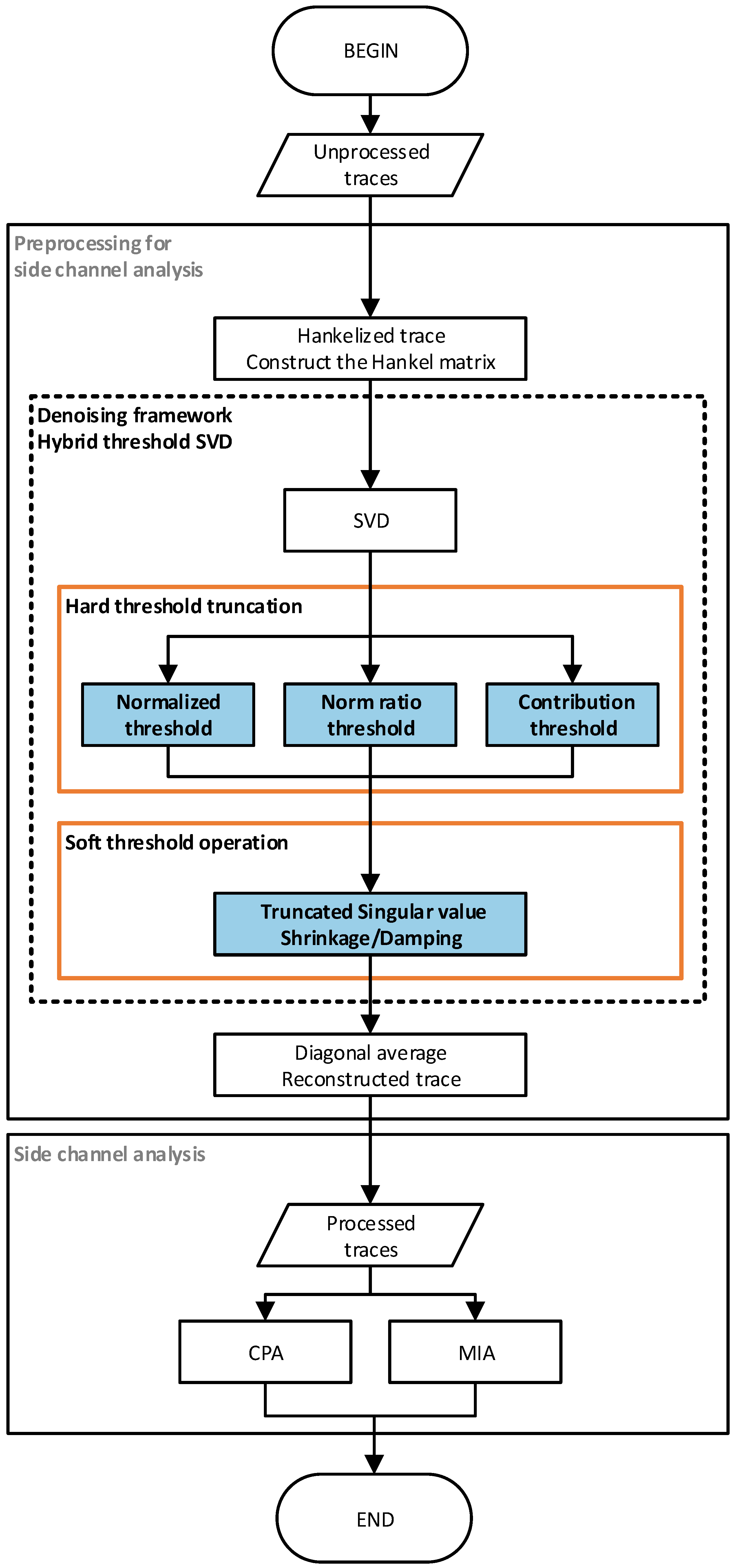
- Two kinds of non-profiled analysis experiments are carried out, which are Correlation Power Analysis (CPA) and Mutual Information Analysis (MIA). In Figure 1, the flow chart of the side-channel analysis based on the hybrid threshold denoising framework using singular value decomposition is given. In this paper, indicators such as signal-to-noise ratio (SNR) and success rate (SR) are used to evaluate the experimental results. The experimental results of CPA and MIA express the effectiveness of the proposed hybrid threshold denoising framework in side-channel analysis preprocessing.
2. Preliminaries
2.1. Separability, LRMA, and LRHA
2.2. Schatten Norm
2.3. Singular Value Decomposition
3. Methodology
3.1. Hard Threshold
3.1.1. Normalized Threshold
3.1.2. Norm Ratio Threshold
3.1.3. Contribution Threshold
3.2. Soft Threshold
3.2.1. Threshold Shrinkage
3.2.2. Threshold Damping
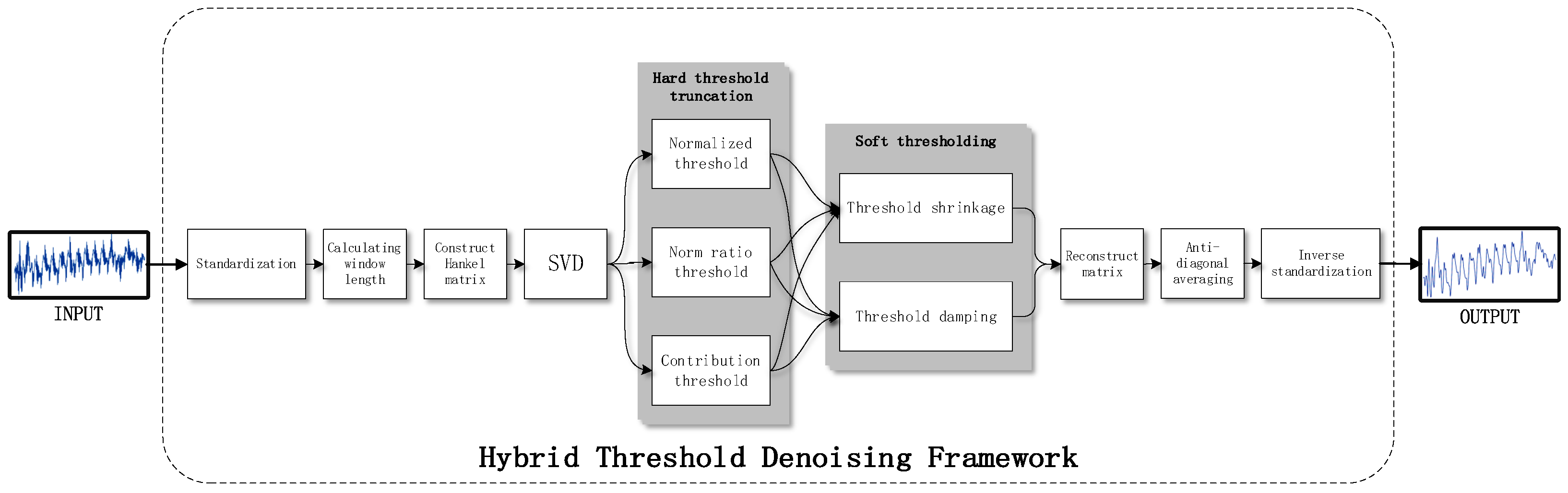
3.3. Hybrid Threshold
3.3.1. Truncated Shrinkage SVD
| Algorithm 1 Normalized threshold truncated shrinkage SVD (NTS-SVD) |
| Input: Hankelized trace H, normalized threshold Output: Normalized threshold truncated shrinkage diagonal matrices
|
3.3.2. Truncated Damping SVD
| Algorithm 2 Norm ratio threshold truncated shrinkage SVD (NRTS-SVD) |
| Input: Hankelized trace H, norm ratio threshold Output: Norm ratio threshold truncated shrinkage diagonal matrices
|
| Algorithm 3 Contribution threshold truncated shrinkage SVD (CTS-SVD) |
| Input: Hankelized trace H, contribution threshold Output: Contribution threshold truncated shrinkage diagonal matrices
|
| Algorithm 4 Normalized threshold truncated damping SVD (NTD-SVD) |
| Input: Hankelized trace H, normalized threshold , damping parameter Output: Normalized threshold truncated damping diagonal matrices
|
| Algorithm 5 Norm ratio threshold truncated damping SVD (NRTD-SVD) |
| Input: Hankelized trace H, norm ratio threshold , damping parameter Output: Norm ratio threshold truncated damping diagonal matrices
|
| Algorithm 6 Contribution threshold truncated damping SVD (CTD-SVD) |
| Input: Hankelized trace H, normalized threshold , damping parameter Output: Normalized threshold truncated damping diagonal matrices
|
4. Experiment
4.1. Preparation
Datasets
- DPA v2: The SASEBO-GII FPGA is employed as the encryption device during signal acquisition in the public database process, operating at a clock frequency of 24 MHz to execute the AES-128 encryption algorithm with stable clock signals. The oscilloscope utilized for signal acquisition boasts a measurement bandwidth of 5 GHz and sampling rate of 5G sampling points per second. Each trace comprises 3253 sampling points, spanning over ten rounds (15.6 clock cycles), with each cycle containing 208.333 sample points, and the collected traces are perfectly aligned. We have selected the final round of AES-128 encryption as our target for attack and collected 100 sample points in each trace for data preprocessing. Below, we display the first trace of the dataset and highlight the area of interest for the attack which corresponds to the last round of the AES-128 encryption, as shown in Figure 3a.
- AES_HD: This is an unprotected AES-128 implemented on FPGA, which was written in VHDL in a round-based architecture that takes 11 clock cycles for each encryption. The AES-128 core is integrated with a UART module to enable external communication, and the design is optimized to expedite measurements and mitigate potential DC offset issues resulting from environmental fluctuations during extended measurement periods. The implementation is realized on a Xilinx Virtex-5 FPGA of the SASEBO GII evaluation board. Side-channel analysis is conducted by capturing electromagnetic radiation emitted from a decoupling capacitor on the power line using a highly sensitive near-field electromagnetic probe. The acquired data are recorded using a Teledyne LeCroy Waverunner 610zi oscilloscope. A total of 500,000 traces are obtained, each corresponding to a randomly generated plaintext and comprising 1250 sample points, as shown in Figure 3b.
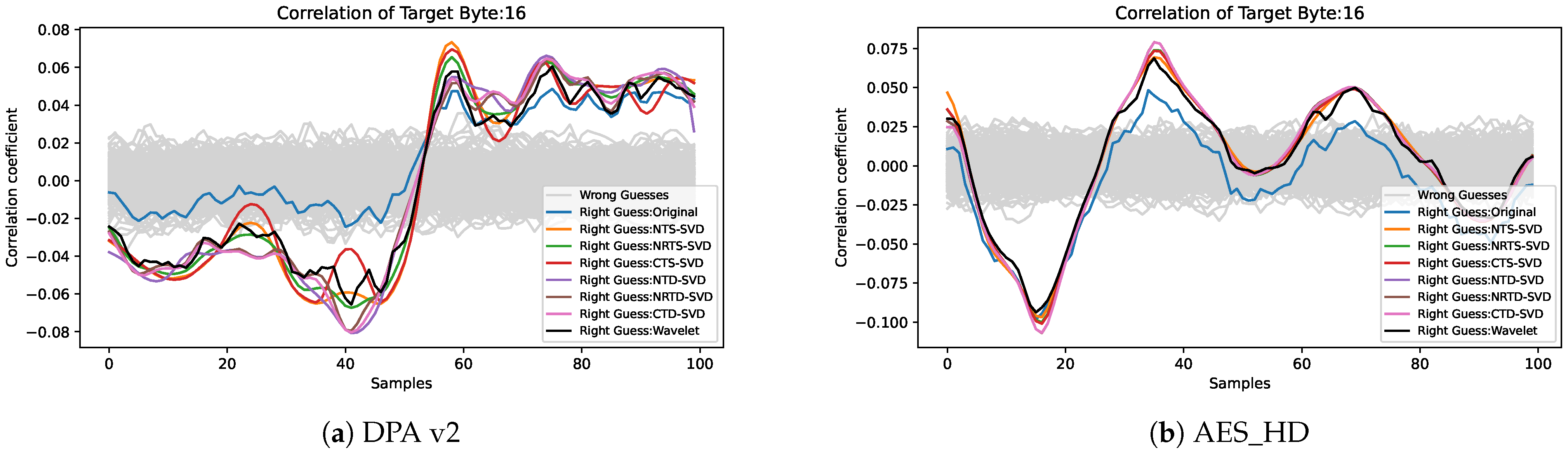
4.2. Result
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
Appendix A. SNR Comparison of Each Byte of AES-128 Last Round Key
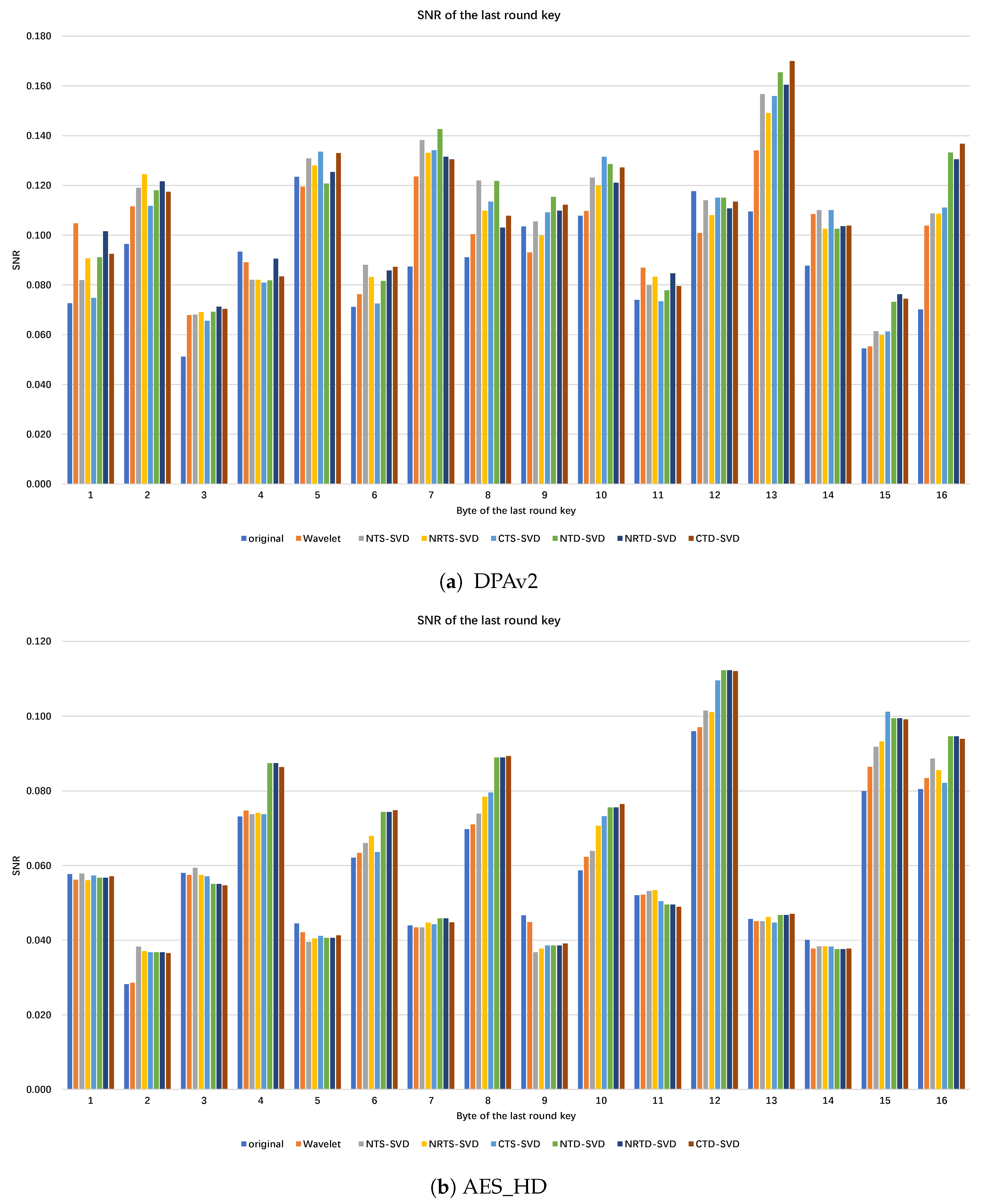
References
- Sun, S.; Zhang, H.; Cui, X.; Li, Q.; Dong, L.; Fang, X. Analysis of Electromagnetic Information Leakage Based on Cryptographic Integrated Circuits. Entropy 2021, 23, 1508. [Google Scholar] [CrossRef] [PubMed]
- Seçkiner, S.; Köse, S. Preprocessing of the physical leakage information to combine side-channel distinguishers. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2021, 29, 2052–2063. [Google Scholar] [CrossRef]
- Salomon, D.; Weiss, A.; Levi, I. Improved Filtering Techniques for Single-and Multi-Trace Side-Channel Analysis. Cryptography 2021, 5, 24. [Google Scholar] [CrossRef]
- Le, T.H.; Clédière, J.; Serviere, C.; Lacoume, J.L. Noise reduction in side channel attack using fourth-order cumulant. IEEE Trans. Inf. Forensics Secur. 2007, 2, 710–720. [Google Scholar] [CrossRef]
- Souissi, Y.; Guilley, S.; Danger, J.l.; Mekki, S.; Duc, G. Improvement of power analysis attacks using Kalman filter. In Proceedings of the 2010 IEEE International Conference on Acoustics, Speech and Signal Processing, Dallas, TX, USA, 14–19 March 2010; pp. 1778–1781. [Google Scholar]
- Liu, W.; Wu, L.; Zhang, X.; Wang, A. Wavelet-based noise reduction in power analysis attack. In Proceedings of the 2014 Tenth International Conference on Computational Intelligence and Security, Kunming, China, 15–16 November 2014; pp. 405–409. [Google Scholar]
- Feng, M.; Zhou, Y.; Yu, Z. EMD-based denoising for side-channel attacks and relationships between the noises extracted with different denoising methods. In Information and Communications Security: Proceedings of the 15th International Conference, ICICS 2013, Beijing, China, 20–22 November 2013; Proceedings 15; Springer: Berlin/Heidelberg, Germany, 2013; pp. 259–274. [Google Scholar]
- Merino Del Pozo, S.; Standaert, F.X. Blind source separation from single measurements using singular spectrum analysis. In Cryptographic Hardware and Embedded Systems–CHES 2015: Proceedings of the 17th International Workshop, Saint-Malo, France, 13–16 September 2015; Proceedings 17; Springer: Berlin/Heidelberg, Germany, 2015; pp. 42–59. [Google Scholar]
- Sun, D.; Zhou, X.; Wang, Z.; Ou, C.; Huang, W.; Ai, J. POSTER: Using Improved Singular Value Decomposition to Enhance Correlation Power Analysis. In Security and Privacy in Communication Networks: Proceedings of the 11th EAI International Conference, SecureComm 2015, Dallas, TX, USA, 26–29 October 2015; Proceedings 11; Springer: Berlin/Heidelberg, Germany, 2015; pp. 598–601. [Google Scholar]
- Ai, J.; Wang, Z.; Zhou, X.; Ou, C. Improved wavelet transform for noise reduction in power analysis attacks. In Proceedings of the 2016 IEEE International Conference on Signal and Image Processing (ICSIP), Beijing, China, 13–15 August 2016; pp. 602–606. [Google Scholar]
- Gan, H.; Zhang, H.; Khan, M.S.; Wang, X.; Zhang, F.; He, P. An improved empirical mode decomposition for power analysis attack. China Commun. 2017, 14, 94–99. [Google Scholar] [CrossRef]
- Cheng, K.; Song, Z.; Cui, X.; Zhang, L. Hybrid denoising based correlation power analysis for AES. In Proceedings of the 2021 IEEE 4th Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Chongqing, China, 18–20 June 2021; Volume 4, pp. 1192–1195. [Google Scholar]
- Huang, W.; Wang, R.; Chen, Y.; Li, H.; Gan, S. Damped multichannel singular spectrum analysis for 3D random noise attenuation. Geophysics 2016, 81, V261–V270. [Google Scholar] [CrossRef]
- Hassani, H.; Mahmoudvand, R.; Zokaei, M. Separability and window length in singular spectrum analysis. Comptes Rendus Math. 2011, 349, 987–990. [Google Scholar] [CrossRef]
- Harmouche, J.; Fourer, D.; Auger, F.; Borgnat, P.; Flandrin, P. The sliding singular spectrum analysis: A data-driven nonstationary signal decomposition tool. IEEE Trans. Signal Process. 2017, 66, 251–263. [Google Scholar] [CrossRef]
- Abdi, H.; Williams, L.J. Principal component analysis. Wiley Interdiscip. Rev. Comput. Stat. 2010, 2, 433–459. [Google Scholar] [CrossRef]
- Wang, C.; Zhu, Z.; Gu, H.; Wu, X.; Liu, S. Hankel low-rank approximation for seismic noise attenuation. IEEE Trans. Geosci. Remote Sens. 2018, 57, 561–573. [Google Scholar] [CrossRef]
- Silverman, L. Realization of linear dynamical systems. IEEE Trans. Autom. Control 1971, 16, 554–567. [Google Scholar] [CrossRef]
- Khan, M.A.R.; Poskitt, D.S. Window Length Selection and Signal-Noise Separation and Reconstruction in Singular Spectrum Analysis; Department of Econometrics and Business Statistics, Monash University: Melbourne, VIC, Australia, 2011. [Google Scholar]
- Adamjan, V.M.; Arov, D.Z.; Kreĭn, M. Analytic properties of Schmidt pairs for a Hankel operator and the generalized Schur-Takagi problem. Math. USSR-Sb. 1971, 15, 31. [Google Scholar] [CrossRef]
- Fazel, M. Matrix Rank Minimization with Applications. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 2002. [Google Scholar]
- Natarajan, B.K. Sparse approximate solutions to linear systems. SIAM J. Comput. 1995, 24, 227–234. [Google Scholar] [CrossRef]
- Wilkinson, J.; Reinsch, C.; Golub, G.; Reinsch, C. Singular value decomposition and least squares solutions. In Linear Algebra; Springer: Berlin/Heidelberg, Germany, 1971; pp. 134–151. [Google Scholar]
- Nadakuditi, R.R. Optshrink: An algorithm for improved low-rank signal matrix denoising by optimal, data-driven singular value shrinkage. IEEE Trans. Inf. Theory 2014, 60, 3002–3018. [Google Scholar] [CrossRef]
- Hansen, P.C. The truncated SVD as a method for regularization. BIT Numer. Math. 1987, 27, 534–553. [Google Scholar] [CrossRef]
- Liebenwein, L.; Maalouf, A.; Feldman, D.; Rus, D. Compressing neural networks: Towards determining the optimal layer-wise decomposition. Adv. Neural Inf. Process. Syst. 2021, 34, 5328–5344. [Google Scholar]
- Cai, J.F.; Candès, E.J.; Shen, Z. A singular value thresholding algorithm for matrix completion. SIAM J. Optim. 2010, 20, 1956–1982. [Google Scholar] [CrossRef]
- Hassani, H. Singular spectrum analysis: Methodology and comparison. J. Data Sci. 2007, 5, 239–257. [Google Scholar] [CrossRef] [PubMed]
- Brier, E.; Clavier, C.; Olivier, F. Correlation power analysis with a leakage model. In Cryptographic Hardware and Embedded Systems-CHES 2004: Proceedings of the 6th International Workshop Cambridge, MA, USA, 11–13 August 2004; Proceedings 6; Springer: Berlin/Heidelberg, Germany, 2004; pp. 16–29. [Google Scholar]
- Gierlichs, B.; Batina, L.; Tuyls, P.; Preneel, B. Mutual information analysis: A generic side-channel distinguisher. In Cryptographic Hardware and Embedded Systems–CHES 2008: Proceedings of the 10th International Workshop, Washington, DC, USA, 10–13 August 2008; Proceedings 10; Springer: Berlin/Heidelberg, Germany, 2008; pp. 426–442. [Google Scholar]
- Mangard, S.; Oswald, E.; Popp, T. Power Analysis Attacks: Revealing the Secrets of Smart Cards; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2008; Volume 31. [Google Scholar]
- Standaert, F.X.; Gierlichs, B.; Verbauwhede, I. Partition vs. comparison side-channel distinguishers: An empirical evaluation of statistical tests for univariate side-channel attacks against two unprotected cmos devices. In Information Security and Cryptology–ICISC 2008: Proceedings of the 11th International Conference, Seoul, Republic of Korea, 3–5 December 2008; Revised Selected Papers 11; Springer: Berlin/Heidelberg, Germany, 2009; pp. 253–267. [Google Scholar]
- Clavier, C.; Danger, J.L.; Duc, G.; Elaabid, M.A.; Gérard, B.; Guilley, S.; Heuser, A.; Kasper, M.; Li, Y.; Lomné, V.; et al. Practical improvements of side-channel attacks on AES: Feedback from the 2nd DPA contest. J. Cryptogr. Eng. 2014, 4, 259–274. [Google Scholar] [CrossRef]
- Bhasin, S.; Jap, D.; Picek, S. AES HD Dataset—50,000 Traces. AISyLab Repository. 2020. Available online: https://github.com/AISyLab/AES_HD (accessed on 1 June 2023).
- Doget, J.; Prouff, E.; Rivain, M.; Standaert, F.X. Univariate side channel attacks and leakage modeling. J. Cryptogr. Eng. 2011, 1, 123–144. [Google Scholar] [CrossRef]


| References | Filtering Technique | Side-Channel Distinguishers | Security Metrics |
|---|---|---|---|
| [4] | Higher-Order Statistics | DPA, CPA | SNR 1, POD 2 |
| [5] | Kalman Filter | SPA, DPA, CPA | MTD 3 |
| [6] | Wavelet | DPA, CPA | SR 4 |
| [7] | EMD-Conv, EMD-IIT | CPA | SNR, SR |
| [8] | SSA | MCP-DPA, TA | SNR, SR |
| [9] | Z-score + SVD | CPA | SR |
| [10] | SSA + DFA + Wavelet | CPA | SR |
| [11] | EMD-IMFs | CPA | PV 5 |
| [12] | Butterworth-LPF + EMD + Wavelet | CPA | CC 6 |
| Preprocessing Method | DPA v2 | AES_HD | ||
|---|---|---|---|---|
| MCV | Improvement | MCV | Improvement | |
| Original (baseline) | 0.049 | - | 0.048 | - |
| Wavelet [6] (comparison) | 0.061 | 24.55% | 0.069 | 42.20% |
| NTS-SVD | 0.073 | 50.88% | 0.069 | 43.50% |
| NRTS-SVD | 0.065 | 34.52% | 0.074 | 52.94% |
| CTS-SVD | 0.070 | 43.19% | 0.073 | 52.04% |
| NTD-SVD | 0.066 | 36.17% | 0.079 | 63.47% |
| NRTD-SVD | 0.065 | 33.71% | 0.079 | 63.46% |
| CTD-SVD | 0.065 | 34.42% | 0.079 | 63.37% |
| Preprocessing Method | DPA v2 | AES_HD | ||
|---|---|---|---|---|
| CPA | MIA | CPA | MIA | |
| Original (baseline) | 4350 | 8550 | 1272 | 6130 |
| NTS-SVD | 3960 | 4010 | 633 | 5950 |
| NRTS-SVD | 3130 | 4270 | 627 | 5950 |
| CTS-SVD | 4020 | 3720 | 633 | 5960 |
| NTD-SVD | 1220 | 4010 | 629 | 5460 |
| NRTD-SVD | 1450 | 4270 | 627 | 5440 |
| CTD-SVD | 1240 | 4000 | 633 | 5330 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Zhang, H.; Fang, X.; Cui, X.; Ning, W.; Wang, D.; Fan, F.; Shu, L. Hybrid Threshold Denoising Framework Using Singular Value Decomposition for Side-Channel Analysis Preprocessing. Entropy 2023, 25, 1133. https://doi.org/10.3390/e25081133
Wang Y, Zhang H, Fang X, Cui X, Ning W, Wang D, Fan F, Shu L. Hybrid Threshold Denoising Framework Using Singular Value Decomposition for Side-Channel Analysis Preprocessing. Entropy. 2023; 25(8):1133. https://doi.org/10.3390/e25081133
Chicago/Turabian StyleWang, Yuanzhen, Hongxin Zhang, Xing Fang, Xiaotong Cui, Wenxu Ning, Danzhi Wang, Fan Fan, and Lei Shu. 2023. "Hybrid Threshold Denoising Framework Using Singular Value Decomposition for Side-Channel Analysis Preprocessing" Entropy 25, no. 8: 1133. https://doi.org/10.3390/e25081133
APA StyleWang, Y., Zhang, H., Fang, X., Cui, X., Ning, W., Wang, D., Fan, F., & Shu, L. (2023). Hybrid Threshold Denoising Framework Using Singular Value Decomposition for Side-Channel Analysis Preprocessing. Entropy, 25(8), 1133. https://doi.org/10.3390/e25081133






