1. Introduction
Spatially coupled low-density parity check (SC-LDPC) codes have been proven to improve the belief propagation (BP) thresholds up to the maximum a posterior (MAP) thresholds of the underlying LDPC block codes for the binary erasure channel (BEC) [
1]. Afterwards, many new structures were proposed to achieve better thresholds or low-complexity/delay decoding, including designing the coupling pattern, eliminating small absorbing/trapping sets, introducing slight irregularities and so on [
2,
3,
4]. In addition, most of the literature focused on applying the concept of spatial coupling on other error correction codes to improve the decoding thresholds, such as spatially coupled repeat-accumulate (SC-RA) codes, spatially coupled turbo codes (SC-TCs), spatially coupled precoded rateless codes and so on [
5,
6,
7]. Moreover, spatial coupling need not be limited to forming a single chain, and more general structures formed by connecting multiple coupled chains were presented to improve the decoding thresholds [
8,
9,
10]. Different from connecting multiple identical coupled chains, the SC-LDPC codes constructed by parallelly connecting multiple different chains (PC-MSC-LDPC) were proposed in [
11], which showed that the thresholds of the PC-MSC-LDPC code ensembles with flexible rates are very close to Shannon limits over the BEC.
The studies stated above mainly focused on the asymptotic performance analysis of the SC-LDPC ensembles. To analyze the finite-length performances, a scaling law for predicting the error probability of the SC-LDPC codes over the BEC using the peeling decoder (PD) was proposed in [
12], which extended the finite-length analysis for LDPC codes in [
13]. At each iteration, if the variable node is not erased through the channel or connected to a degree-one check node, it will be recovered successfully and then removed from the decoding graph along with all its attached edges. This decoding process gives rise to a sequence of residual graphs. Therefore, the analysis of the PD process is equivalent to analyzing the evolution of the residual graphs, which can be transformed to analyze the evolution of the degree distributions (DDs) on the residual graphs. In [
13], it was pointed out that the DDs on the residual graphs at any time converge to a multivariate Gaussian. As a result, by computing the mean and the variance of the DDs evolution during the PD process, the error probability can be estimated. Following this principle, a finite-length analysis for the loop ensemble constructed by connecting two identical coupled chains was presented in [
14], which showed that connecting two coupled chains can result in better thresholds and improved finite-length performances.
These finite-length analyses focused on particular code structures, either the single SC-LDPC code ensemble or the loop ensemble. When the code structure is changed, these analyses will be either very complicated or invalid. According to the working principle of PD, it can be seen that the core of the finite-length analysis over the BEC is analyzing the DDs evolution of variable nodes and check nodes on the residual graph. The essence is to determine whether one variable/check node on the residual graph is removed or not according to the erasure probabilities computed by the received messages from the connected edges, which depends on the interconnections between the variable nodes and check nodes. Inspired by this, we proposed a general finite-length performance analysis from the perspective of the base matrix for SC-LDPC codes. We considered embedding the base matrix into analyzing the residual graph evolution during the decoding process. In particular, based on the base matrix, we derived the mean graph evolution and estimated the variance of the DDs on the residual graphs at each iteration to predict the error probabilities. To verify the effectiveness of the proposed finite-length analysis, we considered the PC-MSC-LDPC codes because they have special connection structures that cannot be analyzed by the existing analyses. Using this expression, we plot the predicted error probabilities for different PC-MSC-LDPC codes and also show the error probabilities by simulations. The comparison results show that the predicted error probabilities can fit the simulated ones well. Since this analysis is performed on the base matrix, it can be applied to other spatially coupled code ensembles defined by the base matrix, including the single SC-LDPC code ensemble and the loop ensemble. The analysis results of the conventional SC-LDPC codes demonstrate this statement.
This paper is organized as follows. In
Section 2, we describe the SC-LDPC and PC-MSC-LDPC code ensembles using the base matrix. In
Section 3, we analyze the graph evolution based on the base matrix, including the mean graph evolution and the variance estimation. In
Section 4, we show and compare the results for different PC-MSC-LDPC codes and the conventional SC-LDPC codes. In
Section 5, we conclude our work.
2. Construction of PC-MSC-LDPC Codes
2.1. SC-LDPC Codes
A SC-LDPC coupled chain was constructed by coupling L disjoint and small -regular LDPC protographs. Each protograph was placed at one position in order and each position was denoted by u, . Here, we considered a conventional fully connected coupling pattern to couple these L protographs. Specifically, let , which denotes the greatest common divisor of J and K. Then, there are check nodes and variable nodes at each position with and . To couple these L protographs, we spread J edges of each variable node at position u to all adjacent check nodes at position , . In turn, for each check node at position u, K edges will be connected to all nearby variable nodes at position , . To terminate the coupled chain, extra positions only including additional check nodes will be added at the end.
A
SC-LDPC coupled chain can be viewed as a protograph and its associated incidence matrix
, called a base matrix, is defined in (
1), where the submatrices
,
are identical
all-one matrices. A
SC-LDPC code can be obtained by taking an “
M-lifting” of the
coupled chain [
15]. Specifically, the parity check matrix can be generated by replacing each one entry by one
random permutation matrix and each zero entry by one
all-zero matrix.
2.2. PC-MSC-LDPC Codes
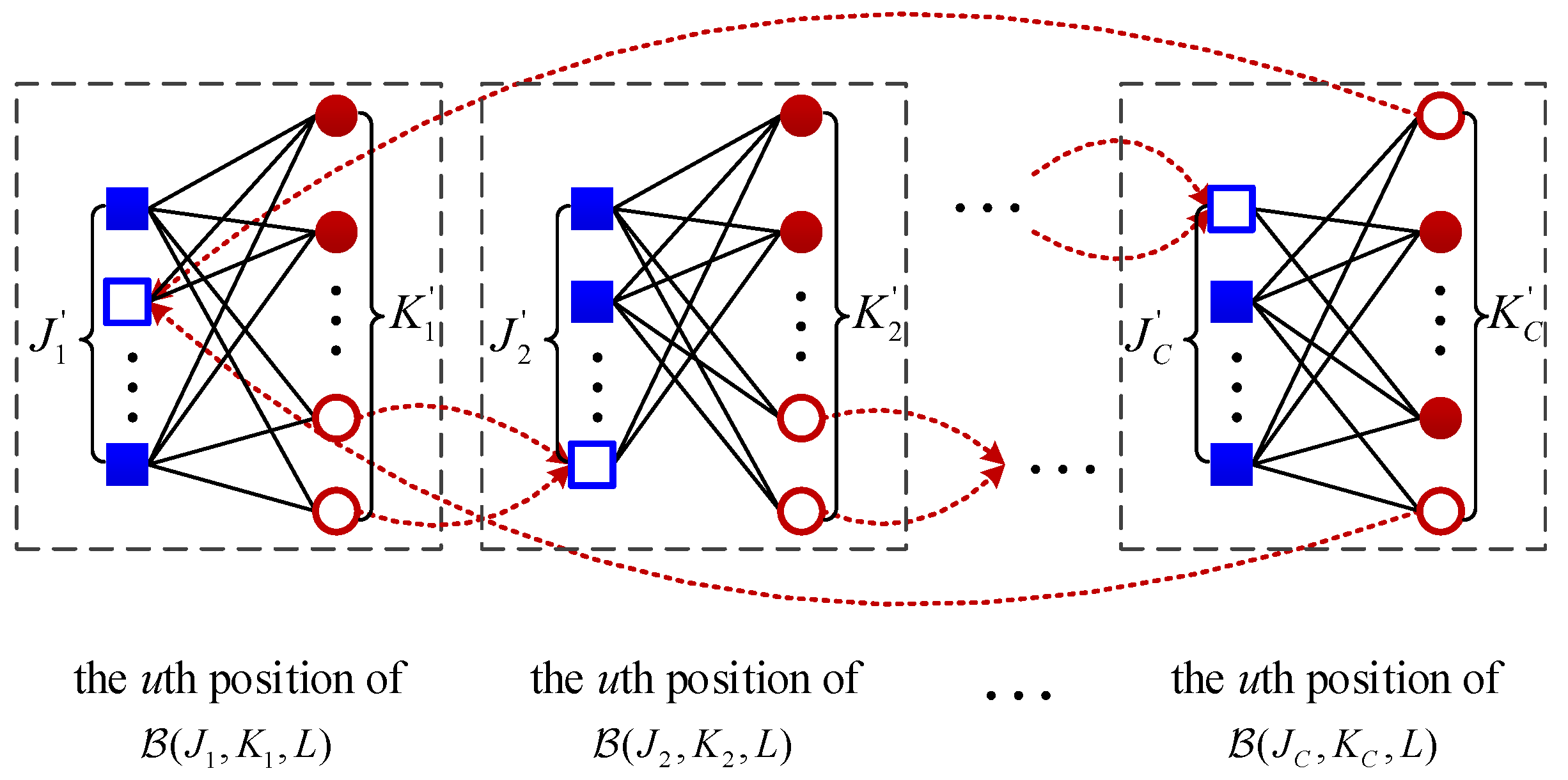
Consider C independent and unconnected coupled chains with the same coupling length L, where each chain has a different rate. The kth chain is denoted as and there are check nodes and variable nodes at each position, where , , and . The base matrix is denoted as and the size is . Let and .
Then, connect these
C chains parallelly by edge exchanges. Specifically,
a variable nodes and
b check nodes are randomly selected for each position
u of every chain
, where
and
. Next, break the edges between these selected
a variable nodes and
b check nodes at each position
u of
and simultaneously connect these broken edges to
b check nodes at each position
u of
with
. The construction process starts from
and stops until
. Take the
uth position to illustrate this process in
Figure 1, where the blue blank squares and red blank circles are the selected check nodes and variable nodes, respectively, and the red dash lines represent the exchange edges between two adjacent chains. The base matrix is
where
denotes the remaining matrix after removing the exchange edges from the base matrix
and
represents the interconnections between the chain
and
,
and
. The size of
is
.
and
. Denote the PC-MSC-LDPC code ensemble defined by this base matrix as
. Take an “
M-lifting” operation on this base matrix and obtain the parity check matrix of a PC-MSC-LDPC code. Denote the PC-MSC-LDPC code as
. More details about the asymptotic performance analysis can be found in [
11].
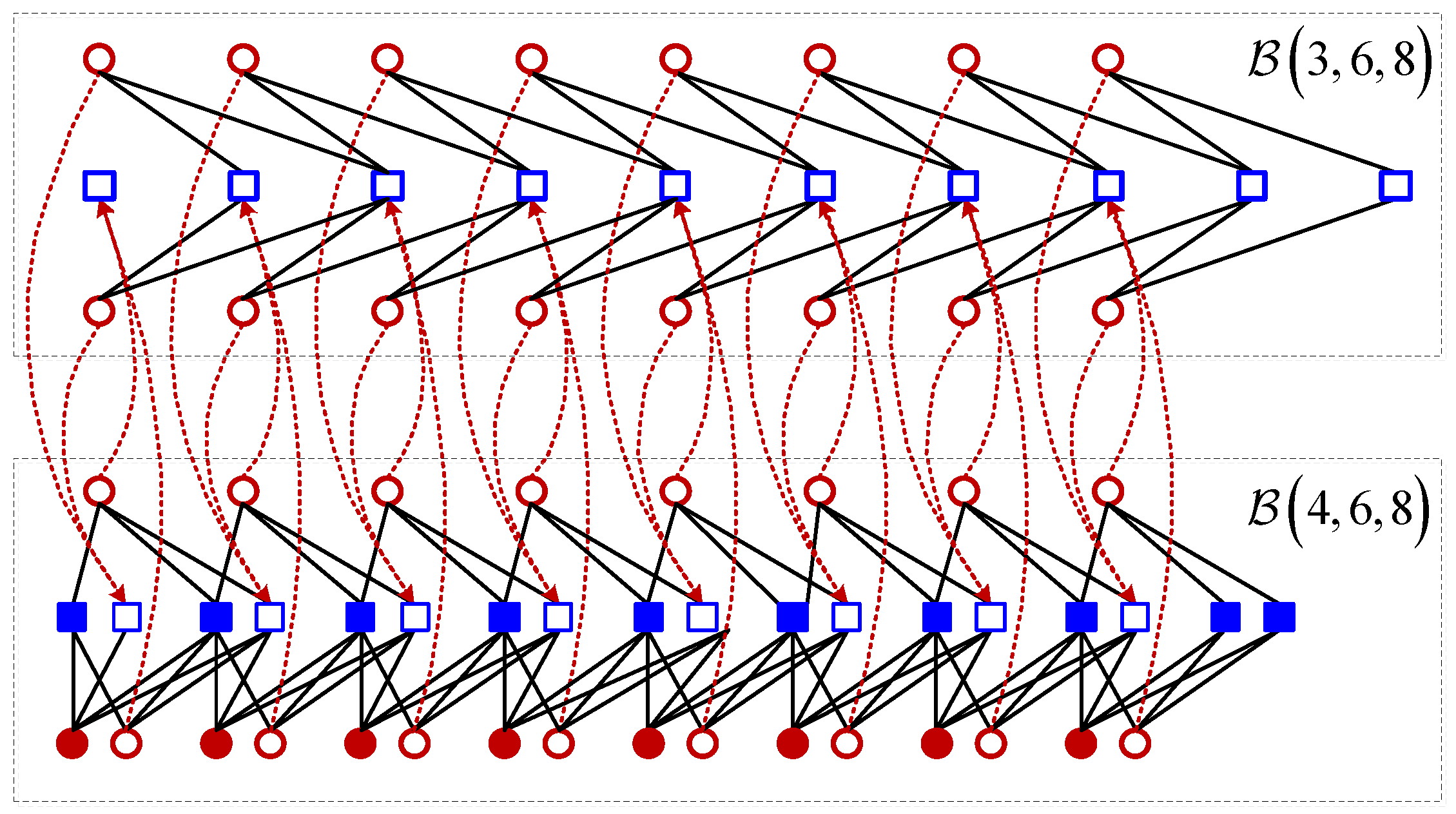
Example: Consider two coupled chains:
and
. Since
,
for
and
,
for
, we have
and
. Thus, we need to select two variable nodes and one check node at each position for
. The connection structure of these two chains in parallel is shown in
Figure 2, where the blue blank squares denote the selected one check node and the red blank circles are the selected two variable nodes. Specifically, at each position, we break the two edges between two variable nodes and one check node of
and connect them to one selected check node of
at the same position (shown in dash lines). Then, we break the two edges between these two selected variable nodes and one selected check node of
, and connect them to one check node of
(shown in red dash lines). The base matrix can be obtained by (
2).
3. Graph Evolution under Peeling Decoder
Following the PD working principle, we proposed a general finite-length analysis based on the base matrix to predict the error probabilities. Without a loss of generality, we considered the PC-MSC-LDPC codes transmitted over the BEC with erasure probability under PD.
3.1. Denotations of DDs
As described in
Section 2, denote the check node at the
ith row of the base matrix
as Type-
i check node and the variable node at
jth column as Type-
j variable node, where
and
. The number of each type of check/variable node is
M. The degrees of Type-
i check node and Type-
j variable node are
and
, respectively, where
is the entry at the
ith row and
jth column of
.
To describe the graph evolution under PD, let l denote time and let it be normalized by . Since the PD peels off one variable node at each iteration from the decoding graph and there are variable nodes in total at the start of the decoding process, iterations are required on average in order to reach the empty graph and realize successful decoding, i.e., .
Let denote the number of the remaining Type-j variable nodes and denote the number of edges connected to Type-i check nodes with degree s at time l, where , , . and are defined as the DDs at time l.
Denote
and
as the normalized versions, where they can be obtained by normalizing
and
with
M at normalized time
.
Since the expected values are required during the graph evolution, denote the expected values of and as and .
3.2. Mean Graph Evolution
Initialization Step: The number of the correctly received Type-
j variable nodes is
after passing the BEC with erasure probability
. At
, PD removes all these correctly received variable nodes along with their attached edges from the decoding graph. The expected number of Type-
j variable nodes is given by
and the normalized version is
.
At
, since PD removed all correctly received variable nodes along with their attached edges from the decoding graph, the check nodes on the residual graph will lose edges and the degree will be decreased. If the degree of a Type-
i check node with degree
is decreased to
s, it means that a total of
edges of this check node are connected to the correctly received variable nodes. Therefore, the expected value of
is
At the right side of Equation (
5), the former part
represents the total number of edges connected to Type-
i check nodes with degree
s and the latter part is the probability that the degree of a Type-
i check node is
s. The normalized version is
.
Evolution Step: At time l, one degree-one check node is randomly selected and then removed along with its connected variable node and all connected edges. A new residual graph is produced.
The mean graph evolution is determined by the expected values of
and
, which can be obtained by solving the following differential equations:
where
,
,
, and they have unique solutions. As pointed out in [
13], when
, any samples of
and
follow
and
closely. The solutions of Equations (
6) and (
7) are given as follows.
Solution of Equation (
6): At time
l, assume the removed degree-one check node to be a Type-
c check node, which is chosen randomly from all degree-one check nodes on the residual graph with uniform probability
.
Then, the variable node connected to this removed Type-
c degree-one check will be removed. Denote the probability that this variable node is a Type-
j variable node as
.
where the denominator represents the total number of variable nodes connected to Type-
c check nodes.
Since a Type-
j variable node with probability
is removed, the variation for the variable nodes is
Solution of Equation (
7): At time
l, if this Type-
j variable node connected to the removed Type-
c degree-one check node is removed, all the attached edges will be deleted, which results in every connected check node losing one edge. Then, denote the probability that a Type-
i check node loses one edge as
and, specifically,
.
Since a Type-
c check node with degree one and an edge connected to it are removed, the variation in the check nodes for the case
can be calculated as
For the case
, the graph loses one edge with probability
. This lost edge is connected to a degree-
s check node with probability
As a result, the graph will lose
s edges of Type-
i check nodes with degree
s and gain
edges of the Type-
i check nodes with degree
. The expected graph evolution is
where
for
.
Since the fraction of degree-one check nodes on the graph determines the successful decoding, we only consider the variation in the degree-one check nodes. In conclusion, by using Equations (
10) and (
14), the expected graph evolutions can be derived.
On the variable node side, we can obtain
On the degree-one check node side, we can obtain
where
and
.
Decoding Criteria: To ensure the successful decoding, the total number of degree-one check nodes must be kept positive until the whole graph is peeled off. Therefore, the BP threshold can be defined as the maximum
to ensure that the mean fraction of degree-one check nodes
is strictly positive for any
.
3.3. Variance Estimation
After describing the expected evolution of the random process
, we need to compute the variance of
for estimating the error probability of the PC-MSC-LDPC codes. As pointed out in [
12], for sufficiently large
M, the distribution of
can converge to a Gaussian distribution with mean
in Equation (
17) and variance
in Equation (
18). Therefore, we can estimate the variance empirically around the mean value using a large set of samples of
at time
.
4. Performance Analysis and Results
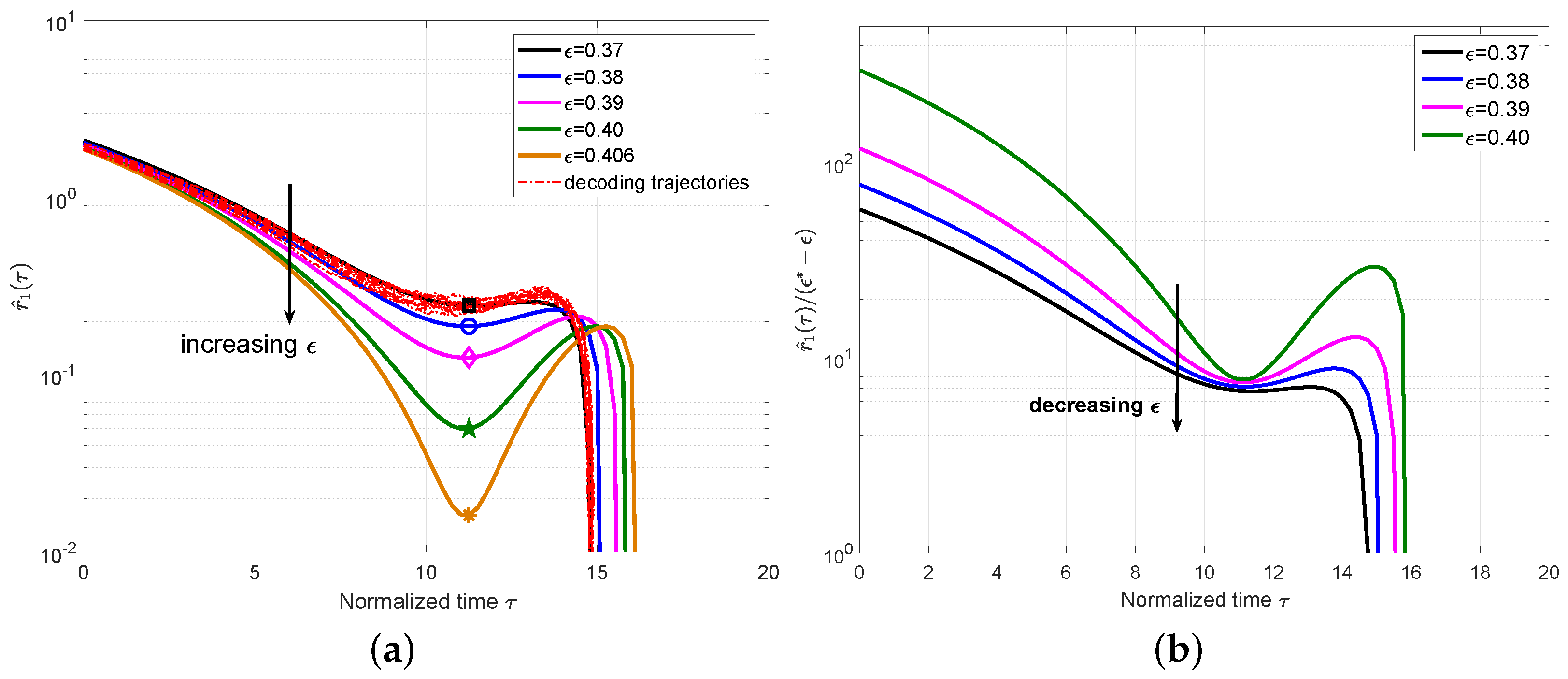
We first show the mean value
for the PC-MSC-LDPC code ensemble
with different
and
in
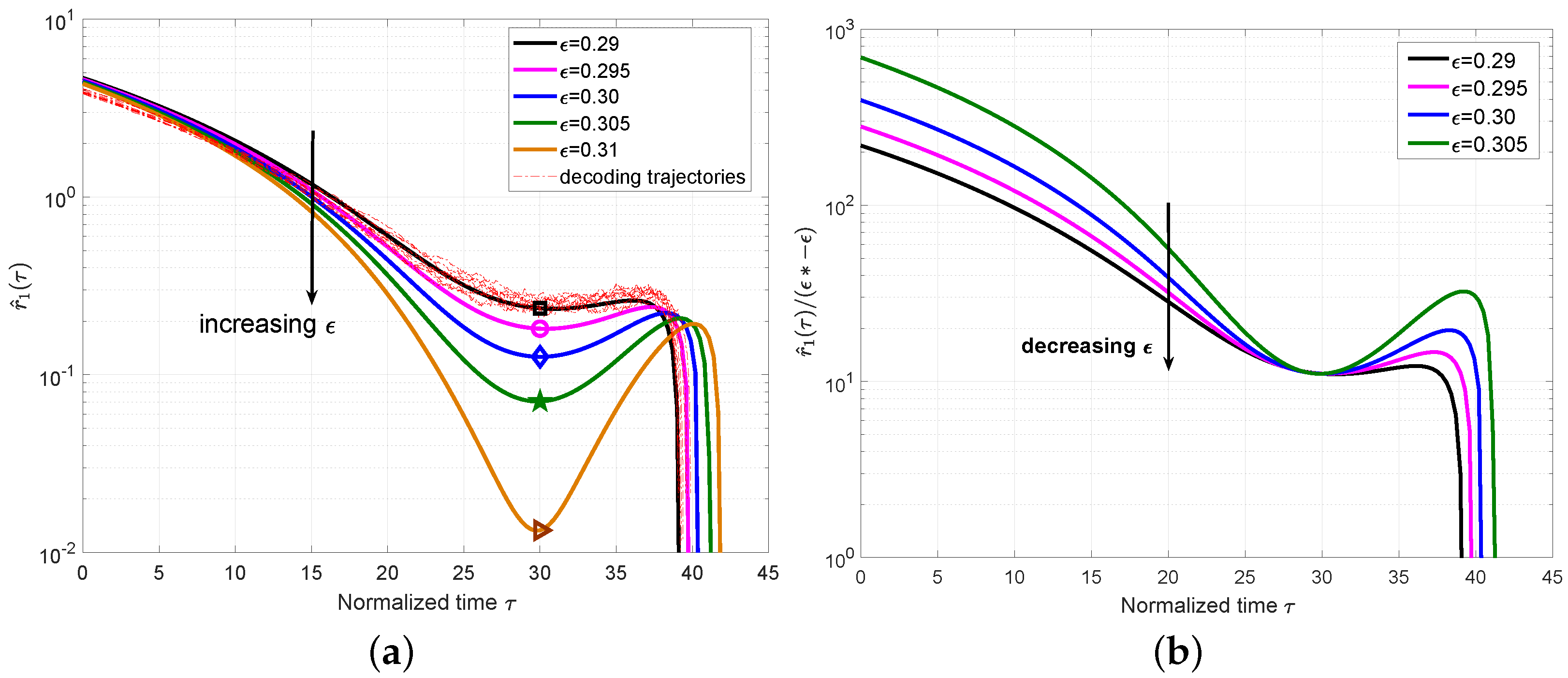
Figure 3a. For
, we also plot a set of 10 simulated decoding trajectories to confirm that they indeed concentrate around the predicted mean evolution. From
Figure 3a, we can clearly observe that the local minimum decreases as
increases and will be close to zero at the BP threshold
computed by the density evolution in [
11], which also coincides with the definition of the BP threshold in
Section 3.2. The time at this local minimum was defined as the
critical point and denoted as
.
In order to associate the error probability with
, we considered a first-order Taylor expansion around the threshold
for
at
.
We plot
for the ensemble
in
Figure 3b. The approximately constant values can be observed for different
at
, which indicates that it is reasonable to remove the high-order components in Equation (
19). Using
, we can obtain
, which can characterize the expected number of degree-one check nodes for a given
at the critical point
.
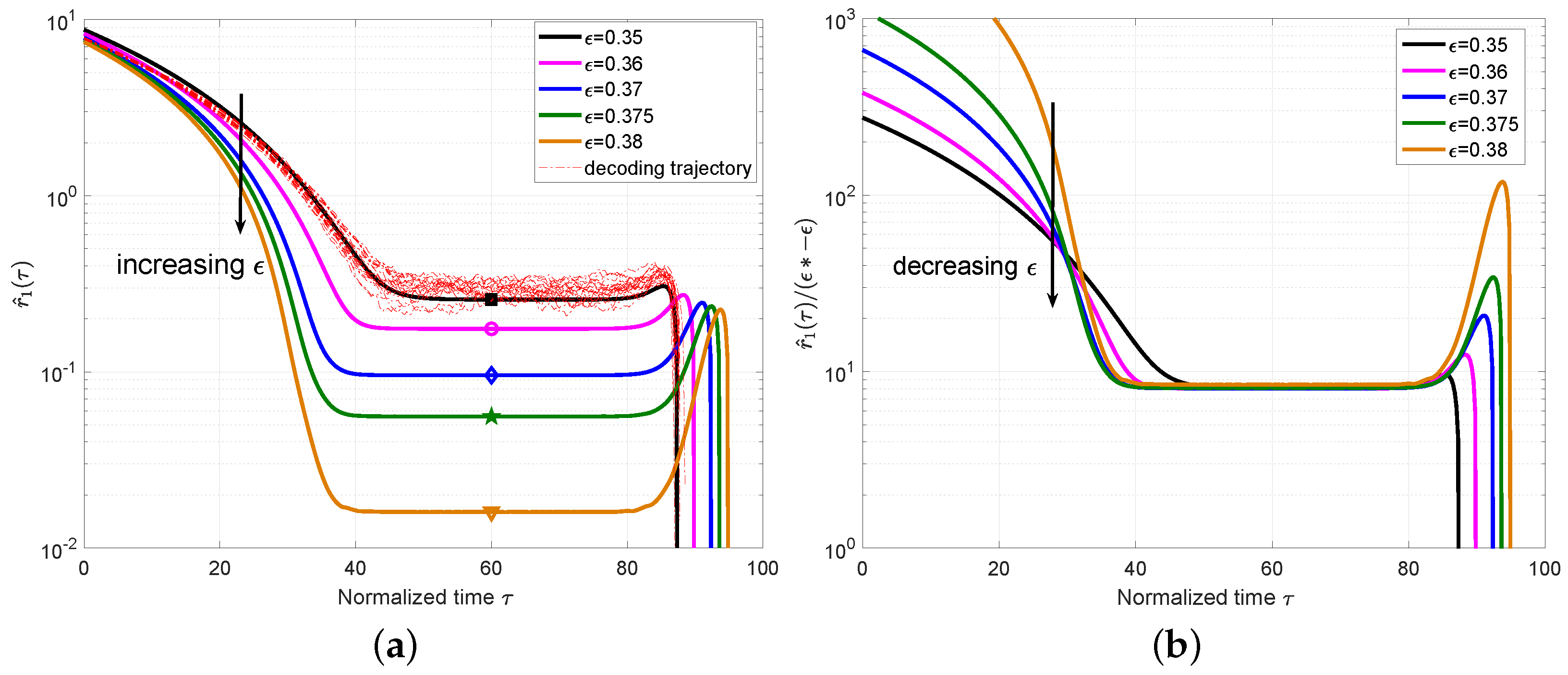
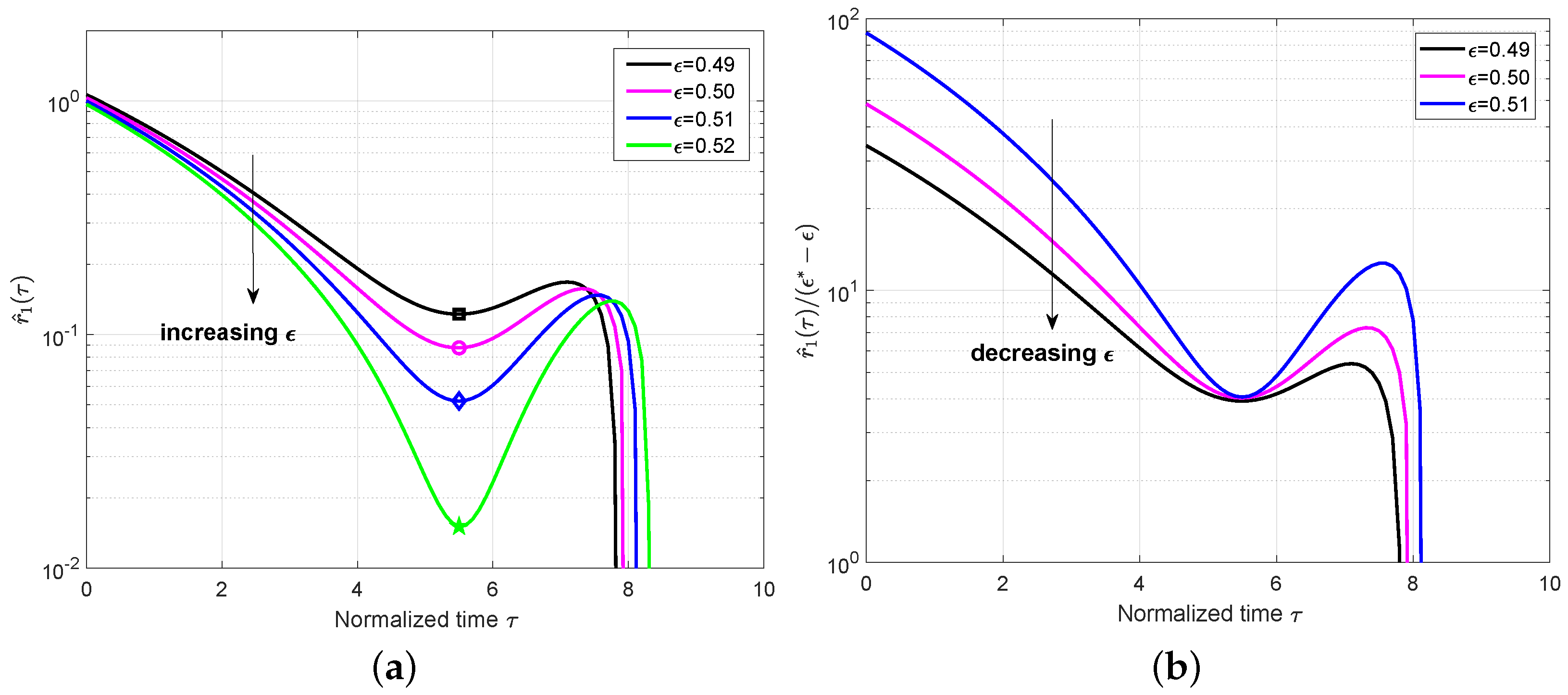
Then, we extended the analysis to the case of
and plot the mean value
of the ensemble
with
in
Figure 4a, which also includes a set of 10 simulated decoding trajectories for
to verify the accuracy of the mean evolution. Different from the ensemble
, we can observe that the local minimum appears not only at one critical point but also for a period of time. This phase is named as a
steady phase and the critical point
can be any time during this phase. At this steady phase, the expected number of degree-one check nodes is almost constant, which confirms the conclusion in [
1] that the decoding waves travel away from the boundaries toward the center of the coupled chain at a constant speed. We also plot
for the ensemble
in
Figure 4b. The approximately constant values can be observed for different
at
.
As pointed out in [
12], the fraction of degree-one check nodes at
dominates the code performance, so we only need to estimate the variance
at
. Specifically, we produced a set of
samples of
for each
by using one randomly generated code from the PC-MSC-LDPC ensemble under the PD. For the ensemble
, the estimated
for different
and
M is listed in
Table 1.
Since
converges to a Gaussian distribution [
13], the error probability at
can be obtained.
Using Equation (
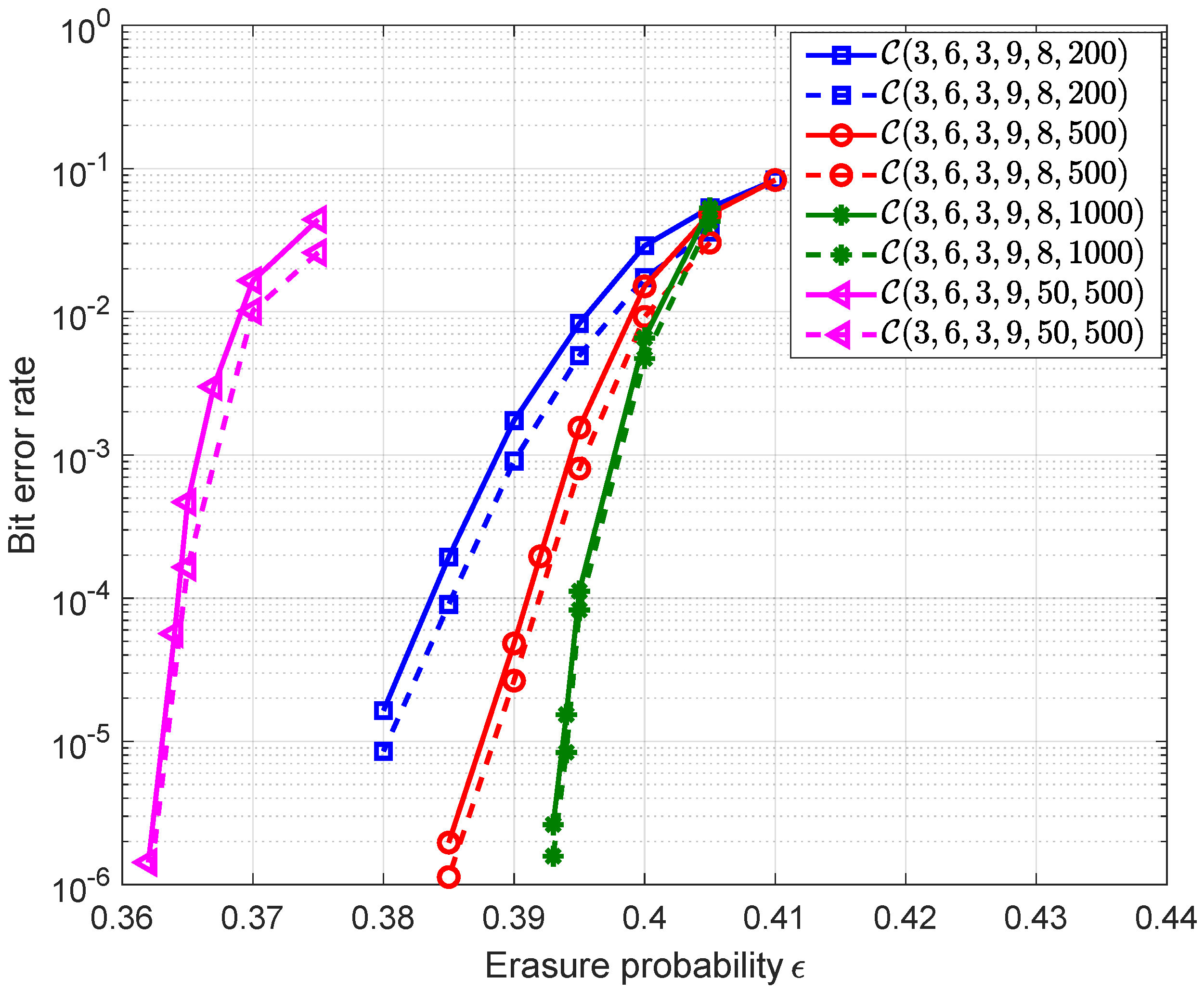
20), we show the predicted error probabilities (dash lines) for different PC-MSC-LDPC codes in
Figure 5 and also plot the simulated ones (solid lines) for comparisons. The results show that the predicted error probabilities are consistent with the simulated error probabilities but small gaps can be observed for relatively small
M. They are caused due to two reasons. One is the deviation between the mean value
and the true mean value of the process
, but it deviates from the true mean value of the process
by less than
. As
, any sample of
follows
closely. The other is the negligence of the decoding failure at
caused by the small cycles or stopping sets in the graph. This effect is more severe for smaller values of
M. However, since the SC-LDPC code ensemble has a linear growth of minimum distance with block length
, the codes with small cycles or low-weight stopping sets can hardly be found for sufficiently large
M. Therefore, when
M increases to a few thousands, the effects on the prediction accuracy will be small enough to be ignored.
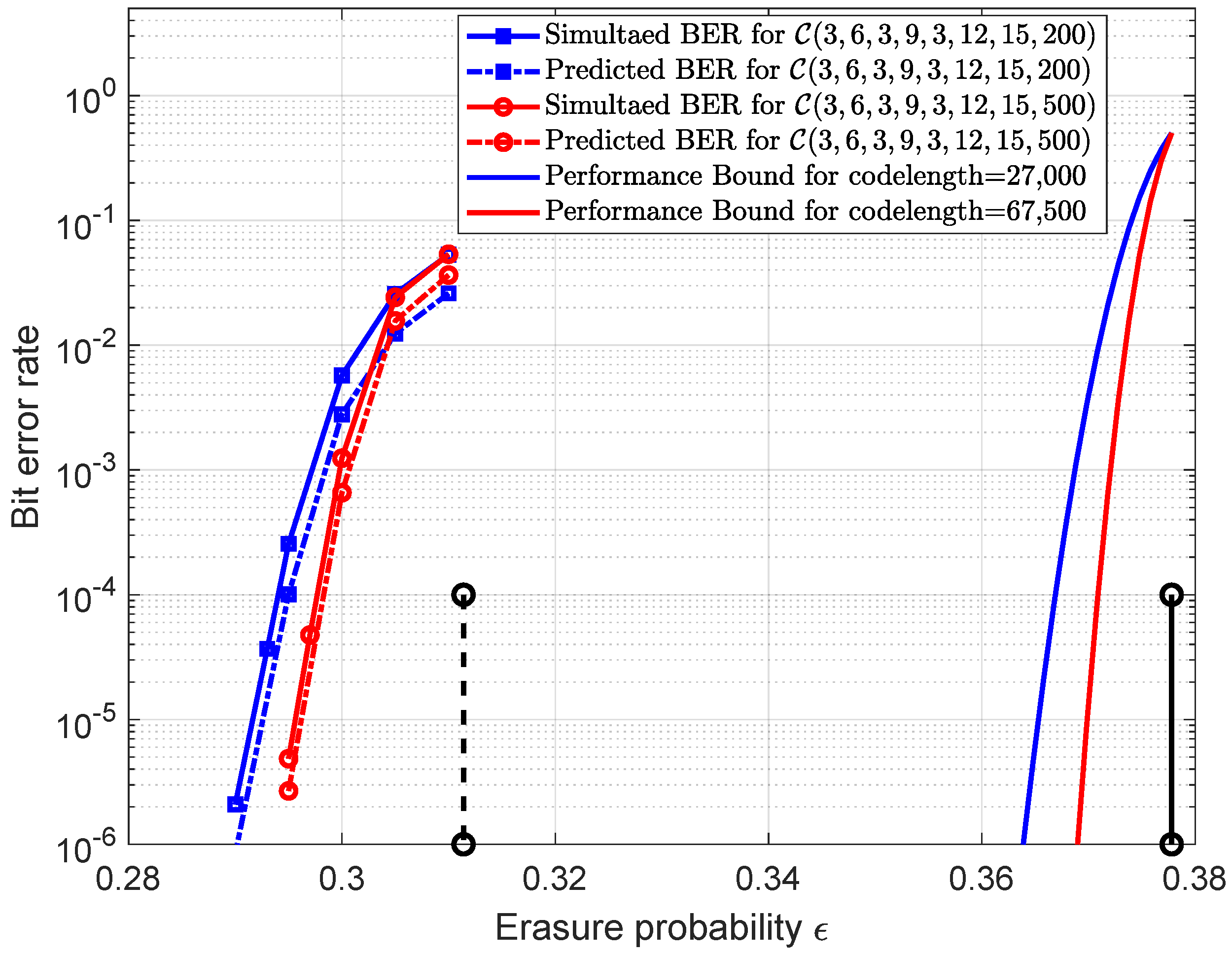
Next, we extended the analysis to the case of connecting three different chains and considered the ensemble
. The mean value
with
and different
is plotted in
Figure 6. Similar results can be observed that, when approaching the threshold
, the
values gradually decrease to approximately zero. In
Table 2, the
values are calculated for the codes generated from the ensemble
. The predicted error probabilities and the simulated ones for these codes are shown in
Figure 7. The comparison results show that these two curves can match well and that the accuracy of the prediction gets better as
M becomes larger. For comparison, the finite length performance bounds obtained by Equation (290) in [
16] for different codelengths along with the BP threshold and Shannon limit are also plotted in
Figure 7, from which we can observe that the gaps between the error probability curves and performance bounds are almost equal to the gap between the BP threshold and Shannon limit. It is known that the finite-length performance is consistent with the BP threshold. By increasing the coupling length, the BP threshold can be improved to be close to the Shannon limit, which can result in the error probabilities approaching the finite-length performance bounds.
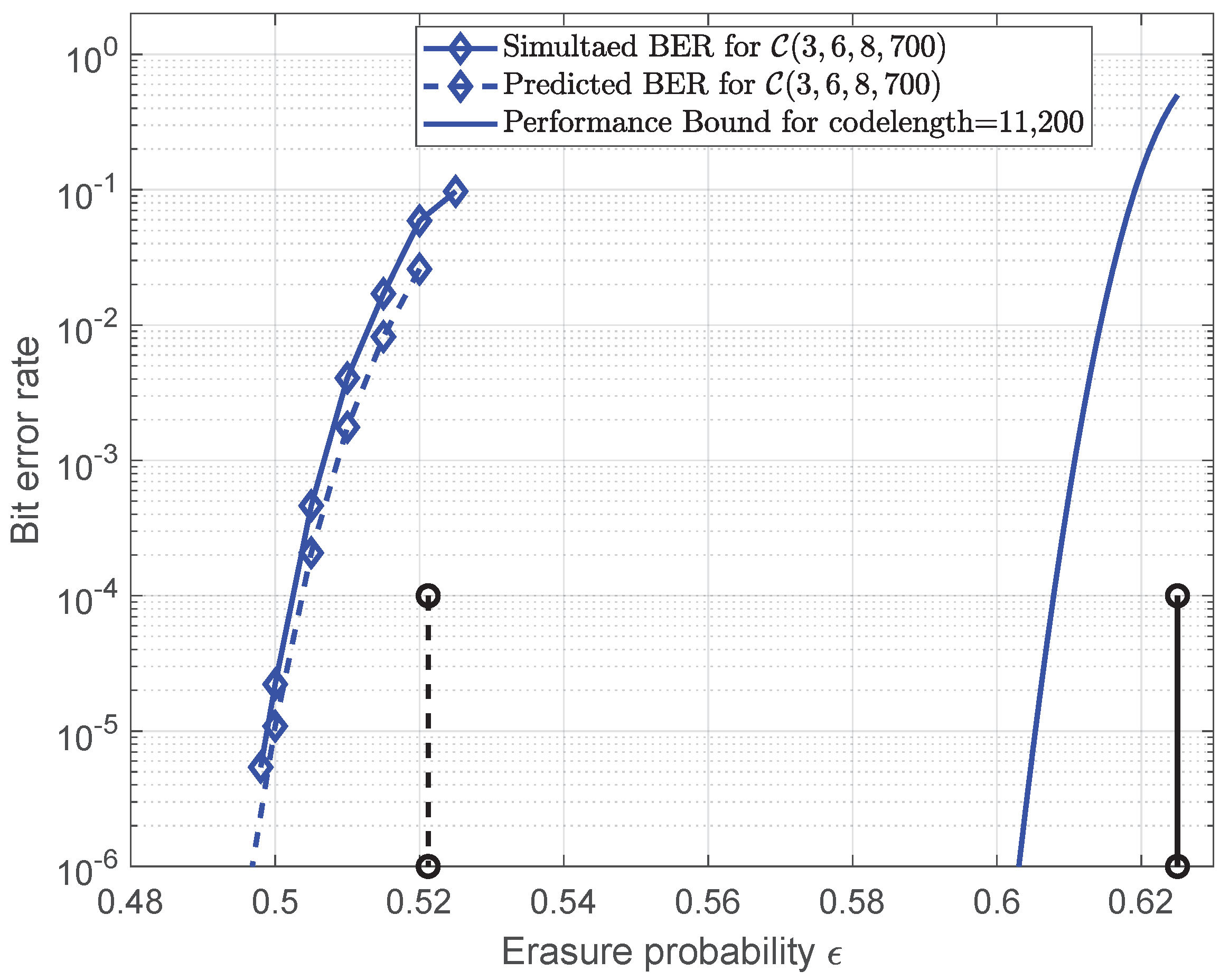
Finally, we applied the analysis to the conventional SC-LDPC code
. The mean value
with different
and plot
is shown in
Figure 8. It can be observed that the local minimum values decrease when increasing
to the BP threshold
and that they are small enough to be close to zero at
. In addition, the approximately constant
can be observed at the critical point as expected. Following similar steps, we computed and list the
values for different
in
Table 3. Using Equation (
20), the predicted error probability for
can be plotted in
Figure 9. It was shown that the predicted performance using this error probability expression can fit well with the simulated performance, which can demonstrate the effectiveness of the proposed finite-length analysis for other SC-LDPC code ensembles.