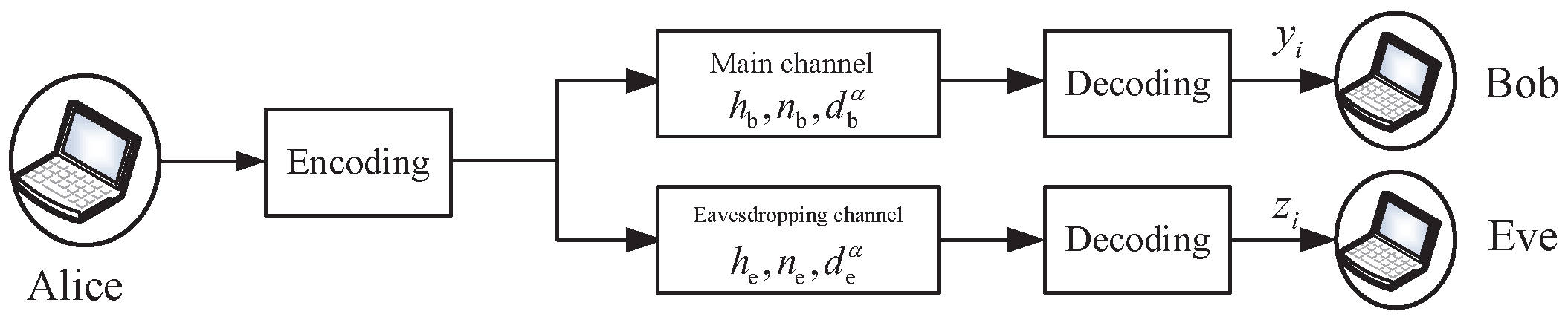1. Introduction
In recent years, with the wide development of wireless communications, privacy and security in wireless communication networks are receiving increased attention. The main reason is that, due to the broadcasting nature of wireless transmissions, the communication between legitimate users is vulnerable to eavesdropping by malicious third parties. To enhance security, many encryption schemes have been proposed to improve the security of wireless communications. However, these encryption schemes inevitably increase the overhead of communications [
1,
2]. The encryption and decryption processes also require more processing resources, which impair the timeliness of the information deliveries.
In order to address security concerns, physical layer security has been proposed as a promising technology for ensuring secure wireless communications. Note that wireless channels suffer from random fading and noises. These physical characteristics can be used to encrypt the information under transmission by reducing the amount of data that can be accessed by potential eavesdropping nodes. In [
3], Wyner extended Shannon’s cryptosystem in the framework of information theory in 1975. Wyner proposed the security capacity concept to evaluate the information rate that could be reliably and securely transmitted over a wireless channel. He concluded that when the eavesdropping channel quality is poorer than that of the primary channel, there exists a coding method that can provide reliable communication for the legitimate user while making it impossible for a malicious eavesdropper to decode any useful information from the captured signal. Specifically, when the instantaneous capacity of the eavesdropping channel from the source node to the eavesdropping node is smaller than the rate of the transmitted codeword, the eavesdropping node is unable to decode the source node information; thus, the legitimate transmission remains secure. However, if the instantaneous capacity of the eavesdropping channel is higher than the rate of the source codewords, the eavesdropping node would be able to successfully decode the source node’s codewords. In this case, an interception event occurs. Thus, we can reduce the
interception probability and improve the security level by increasing the coding rate of the source. Nevertheless,
the probability of outages (i.e., when the instantaneous capacity of the main channel is smaller than the coding rate of the source) decreases with the coding rate. In light of this contradiction, the optimal trade-off between the security and the reliability of physical layer communication has been widely investigated in [
4]. Previous works, e.g., [
5,
6], also presented many meaningful results in the field of physical layer security. However, few works have demonstrated the ability to reduce these issues at the same time.
For communication systems, we need to consider the reliability and security of the system as well as the timeliness of communications. In previous works, the delay was widely used to measure the timeliness of communications. Recently, the emergence of AoI [
7] has become a better option for precisely measuring timeliness. Specifically, the average AoI and peak AoI of systems are often used to describe the performances of real-time systems. For systems gathering information and providing status updates, however, more stringent timeliness is required. Thus, more researchers are measuring timeliness with the AoI violation probability instead of the mean AoI and peak AoI. The AoI violation probability was defined in [
8] to highlight the potential damage caused by very large ages. For a single source single destination system with an FCFS serving policy, the explicit AoI violation probability has been studied in [
9]. The violation probability of the peak AoI in wireless communication systems, considering practical physical layer constraints, was investigated in [
10]. An approximate closed expression of the outage probability of the peak AoI exceeding a certain threshold was presented in [
11]. In this paper, we investigate the timeliness of the system in terms of the violation probability of peak AoI as a measure of communication timeliness.
1.1. Motivations
Due to the contradiction between the outage probability and the interception probability, we are motivated to consider the following problem.
Can we design a transmission mechanism that simultaneously reduces the outage probability and the interception probability to some extent?
In this paper, we propose an SNR-gated transmission control for the source node. Specifically, the proposed method improves performance by hindering packet transmissions in slots when an outage or an interception is expected to occur. Specifically, Alice gives up its chance to transmit a packet if the estimated power gain of the main channel is smaller than a certain threshold so that possible outages can be avoided. We also consider the timeliness of transmissions in terms of the probability of peak AoI. By using a weighted sum function of the outage probability, the interception probability, and the violation probability of the peak AoI, we are able to know how these metrics vary with the transmitting power and arrival rate of the source node.
1.2. Related Works
Most of the existing studies on physical layer security assume that the legitimate receivers have perfect estimations of channel conditions. Since the channel estimations are often not error-free, this assumption is not very practical. In fact, channel estimation errors exist in both legitimate receivers and eavesdroppers [
12,
13,
14]. In most channel estimation techniques, the channel state information (CSI) is obtained through a transmitted signal in the guided frequency band. However, it is usually difficult or impossible for the transmitter to know the state of the channel to the eavesdropper through estimations. In [
12], it was shown that the errors in the channel estimation decrease the traversal secrecy rate. In [
14], the authors investigated the optimal power allocation for artificial noise in the secure transmission, which considers the effect of the imperfect CSI on legitimate receivers.
In physical layer security-related research, errors in channel estimation reduce both the reliability and security of the system. Moreover, the correlation between the main and eavesdropping channels can also have a significant impact on system reliability and security. Most researchers assumed independent premises for the main and eavesdropping channels [
15]. In actual radio environments, the proximity between the legitimate receiver and eavesdropper, along with similar surrounding scatterers, can cause a high correlation between the received signals of the two receivers. Some research has shown that this correlation can improve performance under certain conditions [
16,
17,
18]. However, the results in [
16] indicate that this correlation causes a loss in traversal secrecy capacity. Nonetheless, a strong channel correlation does not necessarily indicate a high probability of communication disruption. Reference [
17] proposed that the correlation impact on the system security performance is not singular but is related to various factors, such as the average signal-to-noise ratio at the receiver, the channel gain ratio, and the set target rate.
In this paper, we propose an SNR-gated transmission control scheme for a three-node system accounting for channel estimation error and correlation between the main and eavesdropping channels. We use the outage probability as a measure of system reliability, and the interception probability as a measure of system security. With these metrics, we investigate the performances of systems with and without the SNR-gated transmission control, and with saturated or unsaturated traffic input, respectively. We also investigate the trade-off among these metrics through a weighted-sum function. By using some mathematical tools, the minimum weighted sum can be found efficiently.
1.3. Main Contributions
The contributions of this paper are summarized as follows.
- (1)
We propose a novel SNR-gated transmission control scheme to reduce the outage probability and the interception probability at the same time. By hindering transmissions with possible outages and interceptions, the power consumption of the system is also reduced, which further enhances the timeliness of the system.
- (2)
We consider the performances of systems with unsaturated traffic input, which is more realistic in practical engineering.
- (3)
We present the outage probability, the interception probability, and peak AoI violation probability explicitly, which are essential for improving and optimizing the reliability, safety, and timeliness of the system.
1.4. Organization
The rest of the paper is organized as follows. We present the transmission model for wireless networks in
Section 2. In
Section 3, we present the proposed SNR-gated transmission control scheme and derive the outage probability, the interception probability, and the violation probability of peak AoI in closed form. The Monte Carlo simulation and numerical results are presented in
Section 4. Finally, we present our conclusions in
Section 5.
2. System Model
We consider a wireless network wherein Alice transmits confidential information to Bob, while a third party (Eve) attempts to eavesdrop on this confidential information, as shown in
Figure 1. We denote the received signals at Bob and Eve, respectively, as
,
. We denote the average transmit power of Alice as
P. We assume that the channels suffer from block Rayleigh fading and additional white Gaussian noise. Thus, the channel gain coefficients (
and
) are zero-mean Gaussian random variables, while the noises (
and
) are independent complex Gaussian random variables with zero mean and variances (
and
). We denote the distance between Alice and Bob as
, the distance between Alice and Eve as
, and the path loss factor as
. The instantaneous received signal-to-noise ratio at Bob and Eve can be expressed as
,
.
We denote the signal bandwidth as
W. Thus, the instantaneous capacities of the main channel and eavesdropping channel are given, respectively by:
2.1. Channel Estimation
We estimate the fading gain of the channel by using an MMSE estimator during the guided frequency transmission period [
19]. The estimation of Bob’s channel gain and the estimation error are denoted by
and
, respectively. Thus, we have,
We assume that
and
are independent zero-mean complex Gaussian random variables, and have [
20]
As we know in [
21], the estimation error of the channel coefficient error variance is
, where
is the pilot power. We denote the estimated SNR at Bob as
and
, both of which are exponentially distributed given by random variables with the pdf:
Due to the estimation errors, the actual instantaneous SNR at Bob can be expressed as a function of the estimated SNR and the SNR error [
22]:
2.2. Channel Correlation Coefficient
Since Bob and Alice are closely located, the main channel and the eavesdropping channel would be correlated. Thus, the channel gain coefficient between Alice and Eve can be expressed as in [
23]:
In Equation (
6),
is the channel gain coefficient of the main channel.
and
are zero-mean Gaussian random variables that are independently and identically distributed. Parameter
represents the correlation coefficient between the gain of the main channel and the eavesdropping channel. Moreover, the signal received by Eve can be expressed as
, where
represents the additive white Gaussian noise at the eavesdropper’s receiver. Thus, the SNR at Eve can also be expressed as follows:
2.3. Traffic Model
In most previous studies, it was assumed that Alice always had packets to transmit (i.e., the saturated traffic model), so that the probability of the unsuccessful packet reception equals the probability that the channel gain is smaller than a certain threshold. In practical implementations, we need to consider the unsaturated traffic model instead. Specifically, the unsaturated model and the saturated model are explained as follows.
Saturated traffic model: The next packet arrives immediately when the transmission of the previous packet is complete so that Alice always has packets to transmit.
Unsaturated traffic model: The packets are generated according to a certain random process. Thus, there are slots where Alice does not have a packet to transmit. In this paper, we assume that the packets arrive with a geometric process with parameter . That is, Alice has a new packet with a probability in each slot. Thus, the average inter-arrival time would be .
2.4. Reliability and Safety Metrics
We denote the code word transmission rate as
and the confidential message rate as
. If the main channel capacity is less than the data rate
, an outage event occurs. That is, the outage probability is given by:
Since the transmission of a packet is successful with probability
(no outage occurs), the service time of a packet (i.e., the number of slots to transmit a packet to Bob successfully) follows a geometric distribution with parameter
. That is,
Thus, we have
.
We denote the cost of protecting message transmissions from eavesdropping as
. If the capacity of the eavesdropping channel satisfies
, Eve will be able to decode the message and an interception event occurs. Thus, the interception probability of the eavesdropping channel is given by:
Note that both the above-mentioned outage probability and interception probability are probabilities conditioned on the fact that there are always enough messages for transmission. That is:
2.5. Violation Probability of Peak AoI
The AoI of the system is defined as the length of the period between the current time and the time at which the latest received update is generated. Thus, a smaller AoI indicates fresher information. At the moment
t, AoI is expressed as [
7]:
wherein
r(t) is the timestamp of the latest update received at the receiver at time
t. The peak AoI is defined as the age of a packet at the time it is received [
24], i.e.,
wherein
is the inter-departure time and
is the system time of the packet.
3. SNR-Gated Transmission
In order to reduce the outage probability and the interception probability simultaneously, we propose an SNR-gated transmission control scheme in this section. Note that an outage might occur when the main channel is poor while an interception may occur if the main channel is relatively strong. Therefore, it is reasonable to control the transmission of Alice, and only perform transmission in slots where the estimated SNR of the main channel is neither too small nor too large.
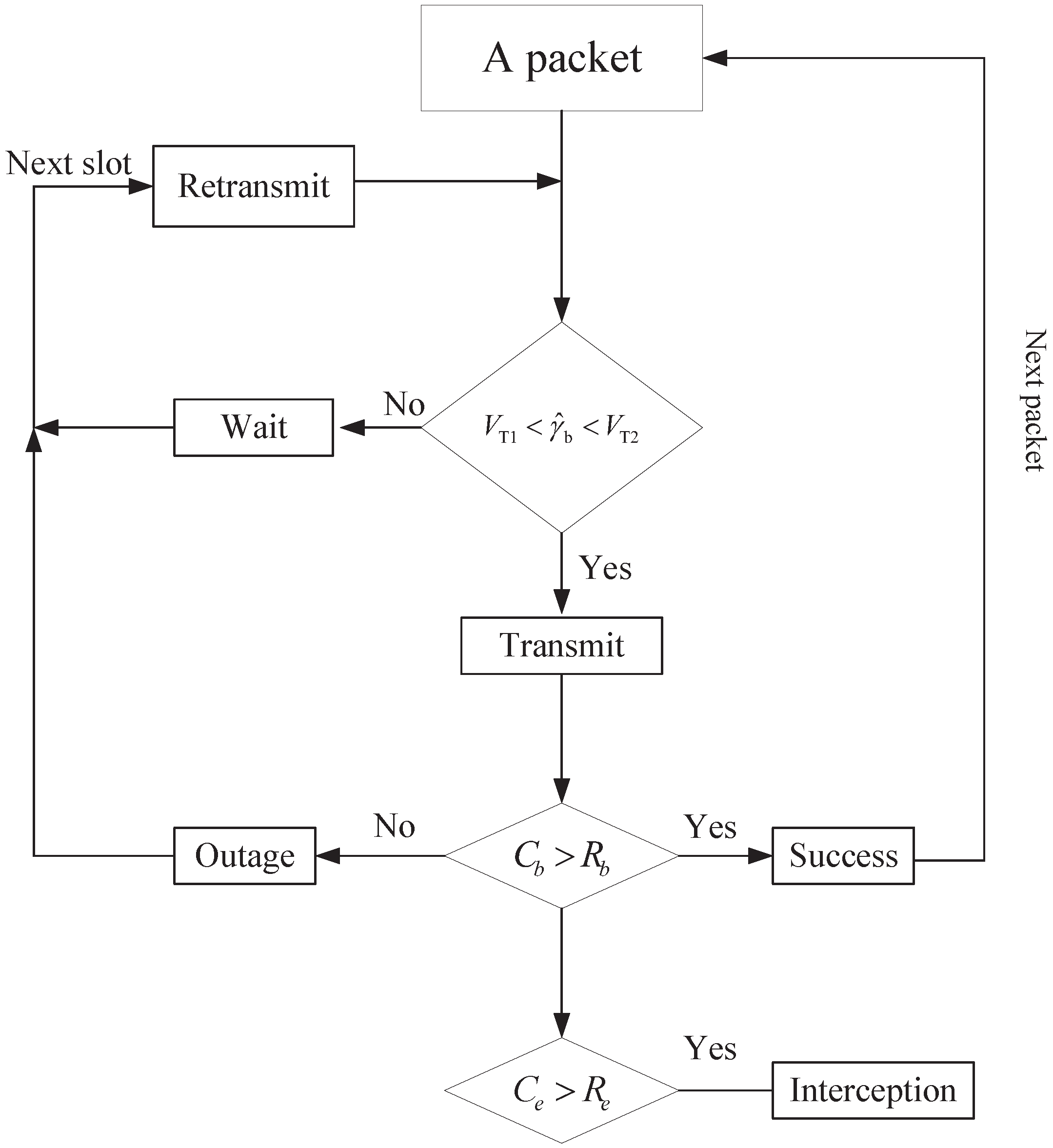
Figure 2 shows the transmission process of data packets under the SNR-gated transmission control.
Specifically, when the packet obtains its chance to be transmitted, we shall check if the estimated SNR of the main channel falls into the desired range . If yes, the packet will be transmitted. If not, the packet needs to wait and will be retransmitted in the next time slot. When the packet is transmitted in the current slot, an outage can still possibly occur, in which case, the packet will be retransmitted in the next time slot. A packet is considered as successfully transmitted only if no outage occurs.
3.1. Outage Probability
3.1.1. Outage Probability under Saturated Model
We denote the lower and upper SNR thresholds of the control scheme as and . That is, Alice performs a transmission if and only if the estimated SNR satisfies . In other cases, the packet will not be transmitted; thus the probability of outage and interception is reduced. First, the outage probability of the saturated model is given by the following proposition.
Proposition 1. Regarding saturated transmission, the outage probability is expressed as follows:
3.1.2. Outage Probability under the Unsaturated Model
Second, in the unsaturated model, Alice does not have any transmission slot with probability . The corresponding actual outage probability is given by the following proposition.
Proposition 2. Regarding unsaturated transmissions, the outage probability is expressed as follows:
From
Appendix A.2, the load factor plays a crucial role in the unsaturated transmission scenario.
3.2. Interception Probability
3.2.1. Interception Probability under Saturated Model
Since we determine whether to transmit a packet based on the estimated SNR of the main channel, we will define and derive the interception probability of the system as follows.
Proposition 3. In saturated transmissions, the interception probability can be expressed as follows:
Equation (
16) indicates that the transmission of data through the channel is determined by the channel quality of the main channel. As the system is fully saturated in terms of transmission, the probability of the packet being intercepted in the channel is the probability that the capacity of the eavesdropping channel is greater than the secrecy overhead.
3.2.2. Interception Probability under Unsaturated Model
Proposition 4. Regarding unsaturated transmissions, the interception probability is expressed as follows:
Therefore, after our comparative analysis and calculation, we see that, by using the SNR-gated transmission control, the reduction of the possibility of sending packets on the sender side does reduce the outage probability and interception probability. Thus, it satisfies our expectation to improve transmission reliability and security simultaneously.
3.3. Timeliness Analysis
We formulate the transmission over the main channel as a Geom/Geom/1 queuing policy [
25] and measure the timeliness of the received packet by Bob by the violation probability of the peak AoI.
Since the traffic models of packets in the channel are different, we will analyze the timeliness in two parts. There are two commonly used packet service policies: the first-come, first-served policy (FCFS) and the last-come, first-served policy (LCFS) [
24]. In this paper, we assume that the packets are served according to the FCFS rule. In the unsaturation traffic model, we assume that the state updates are generated according to a geometric process. Thus, both the inter-arrival time
and service time
are independent and geometrically distributed random variables, with mean
and
, respectively.
First, if the service of a packet is completed before the arrival of the next packet, the service of the next packet begins immediately upon its arrival. Second, if the service of the current packet is not completed before the next arrives, the arriving packet needs to wait before starting its service. Thus, interval
between the departures can be expressed as follows:
The distribution of the inter-arrival time, the service time, and the system time can be expressed as follows:
wherein
.
We use the violation probability of the peak AoI as the measure of data freshness, which is expressed as follows:
where
is the threshold value of the peak AoI [
26].
We compare the service rate before and after using the SNR-gated transmission control. For the transmission without SNR-gated transmission control, since there is no transmission constraints, packets can be sent in each slot, with a successful probability:
By using our SNR-gated transmission control, we only attempt to transmit a packet when the estimated SNR
of the main channel is greater than
and less than
. Thus, the service rate of the main channel is:
Since SNR-gated transmission control reduces the possibility of transmission, the probability of a successful packet delivery would also be reduced.
3.3.1. Saturation Transmission Model
In this case, the server is loaded at full capacity. Specifically, a new state update arrives precisely when the last update packet leaves the queue. At this point, the inter-departure time
is equal to the service time
. Therefore, we have
and
. Thus, we have:
For the saturated transmission model, the service rate is mainly affected by the SNR-gated transmission control. Since the saturation transmission model generates a new packet immediately when a packet is delivered, the packet arrival rate can be considered as
. Thus, we have:
3.3.2. Unsaturated Transmission Model
In the unsaturated transmission model, the server is not fully loaded, so the load factor is not equal to one. In this case, is not equal to due to the additional waiting time.
We know that our SNR-gated transmission control mainly changes the service rate to . By replacing with , we have
Proposition 5. The violation probability of peak AoI can be expressed explicitly as follows: 3.4. Joint Optimization of Safety, Reliability, and Timeliness
In this section, we jointly optimize the safety, reliability, and timeliness of the system through a weighted sum function
, wherein
are weighing coefficients and
. By using different weights, the performance-oriented aspects of the transmission system are different. For example, when we set
close to unity, the reliability of the system plays the most significant role among the three dimensions. When we require a better timeliness performance, we could set
as close to unity. We can find the optimal solution more intuitively by using the MATLAB construction function. Specifically, the optimization problem of the integrated performance can be expressed as follows:
wherein
is the updating rate of Alice,
is the range of power. In the saturated transmission model, we do not need to consider the optimization over
since we have
. In this case, J can be rewritten as follows:
Since the above equation is an inequality-constrained optimization problem that satisfies the Karush–Kuhn–Tucker (KKT) condition [
27], we will discuss it in the following cases. By setting
, the optimized transmit power
can be obtained. We simplify
,
, and
, and have the following proposition:
Proposition 6. In the saturated transmission model, the optimal transmit power is given by:
- (1)
When , the optimal solution is ;
- (2)
When , the optimal solution is ;
- (3)
When , the optimal solution is ,
wherein is and is .
4. Simulation Results
In this section, we evaluate the safety, reliability, and timeliness of the system through the simulation results. We set the main channel bandwidth as
Hz, the eavesdropping channel bandwidth as
Hz, the distance between Alice and Bob as
m, and the distance between Alice and Eve as
m. We set the main channel noise power spectral density as
W and the eavesdropping channel noise power spectral density as
W. The main channel Rayleigh channel parameter
is set to 4 and the path loss factor
is set to 2 [
28]. To verify the obtained theoretical (TH) results, we also performed corresponding Monte Carlo (MC) simulations. Specifically, we set the simulation time to 10,000 s and block spacing to
. We assume that the main channel and the eavesdropping channel are correlated.
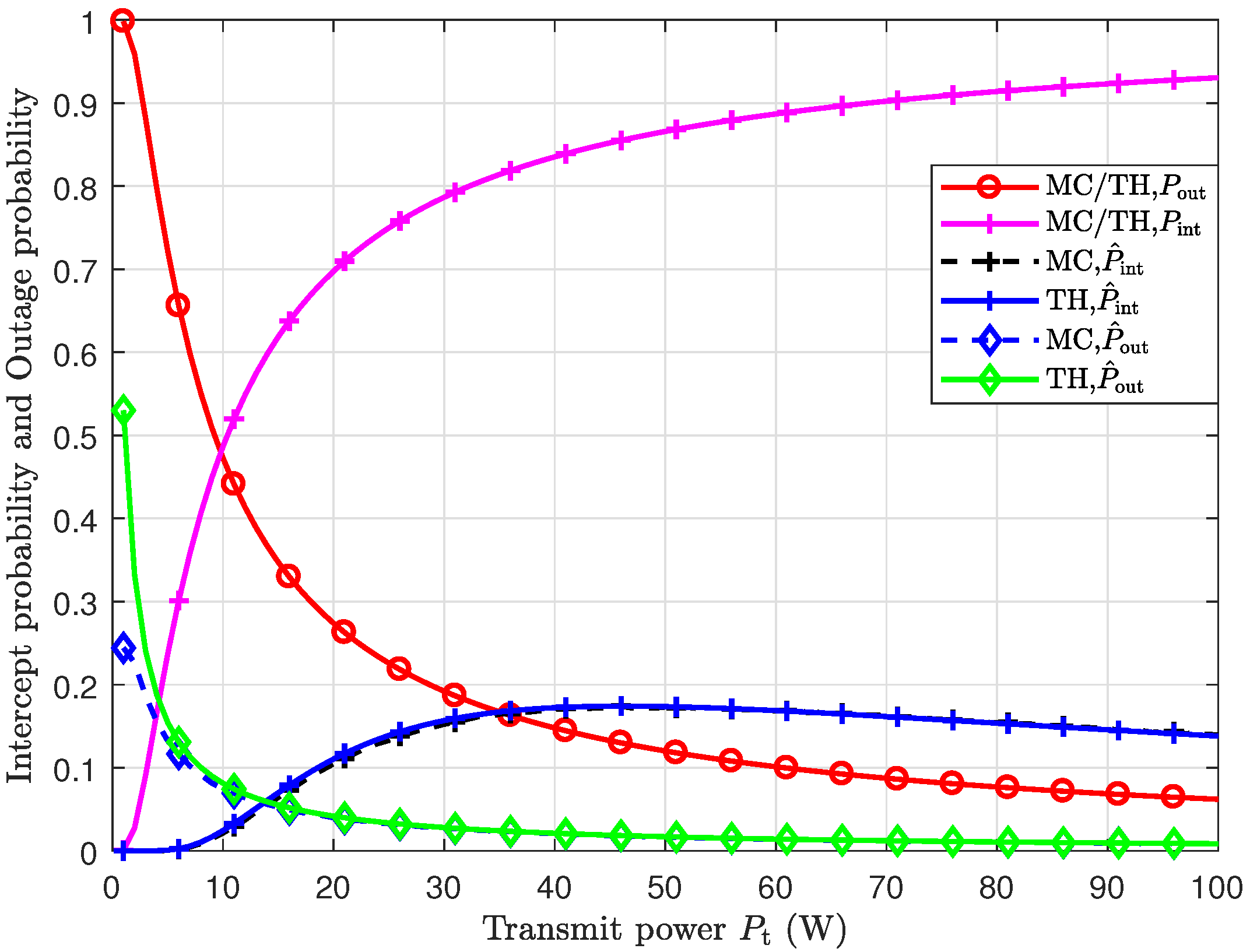
In
Figure 3, we compare the interception probabilities and outage probabilities with and without using the SNR-gated transmission control scheme. From the figure, we can see that the outage probability decreases with the increase in transmit power
. More importantly, both the outage probability and interception probability are significantly decreased when the SNR-gated transmission control scheme is used. Therefore, we can conclude that the SNR-gated transmission control scheme can effectively improve reliability and safety simultaneously.
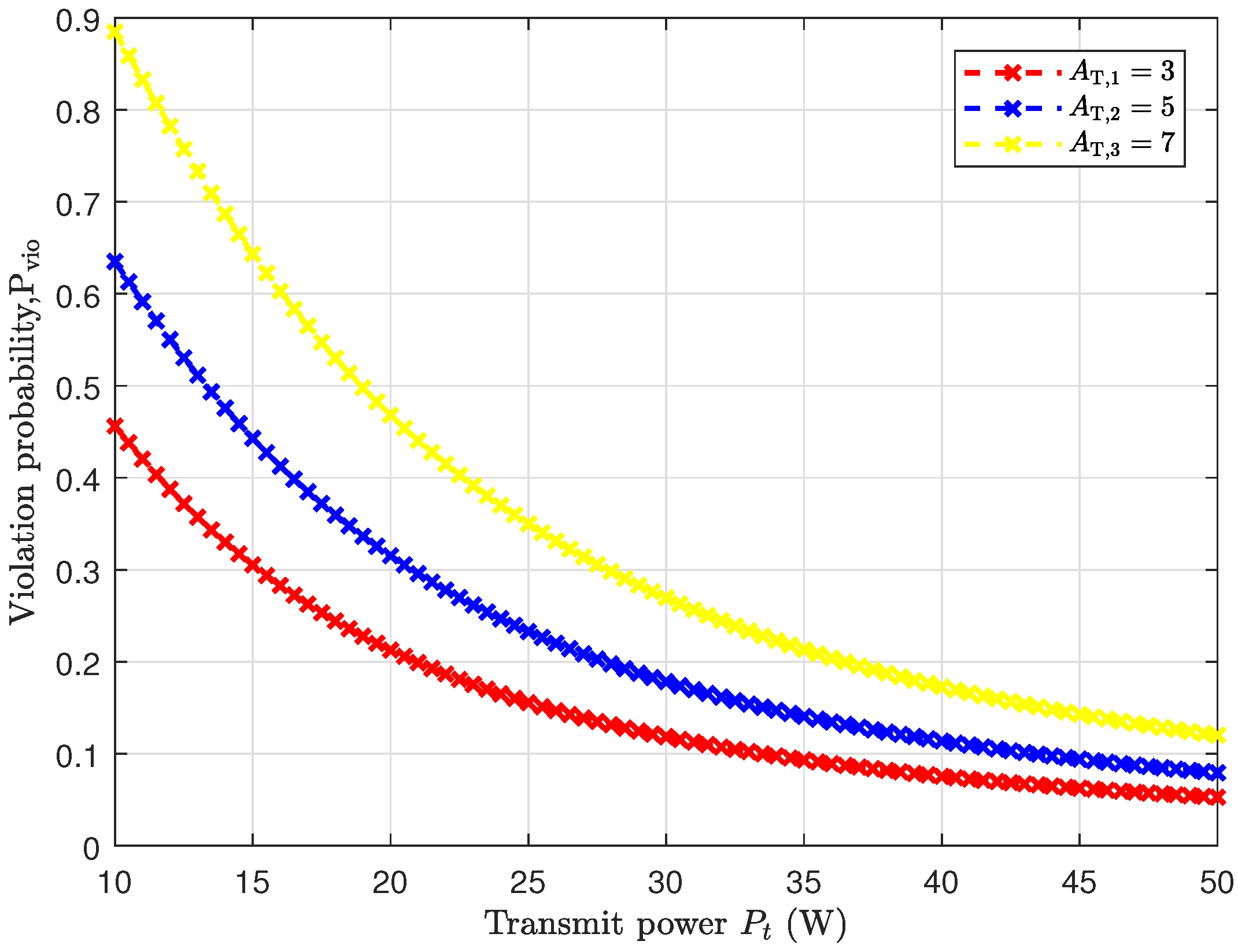
In
Figure 4, we investigate the correlation between the transmitted power and the probability of peak AoI violation in the saturated model with SNR-gated transmission control. It is seen that as the transmission power increases, the probability of peak AoI violation decreases. By reducing the threshold of violation, the probability of peak AoI violation also decreases. This is due to the fact that increasing the threshold results in a smaller probability for the peak AoI exceeding the threshold.
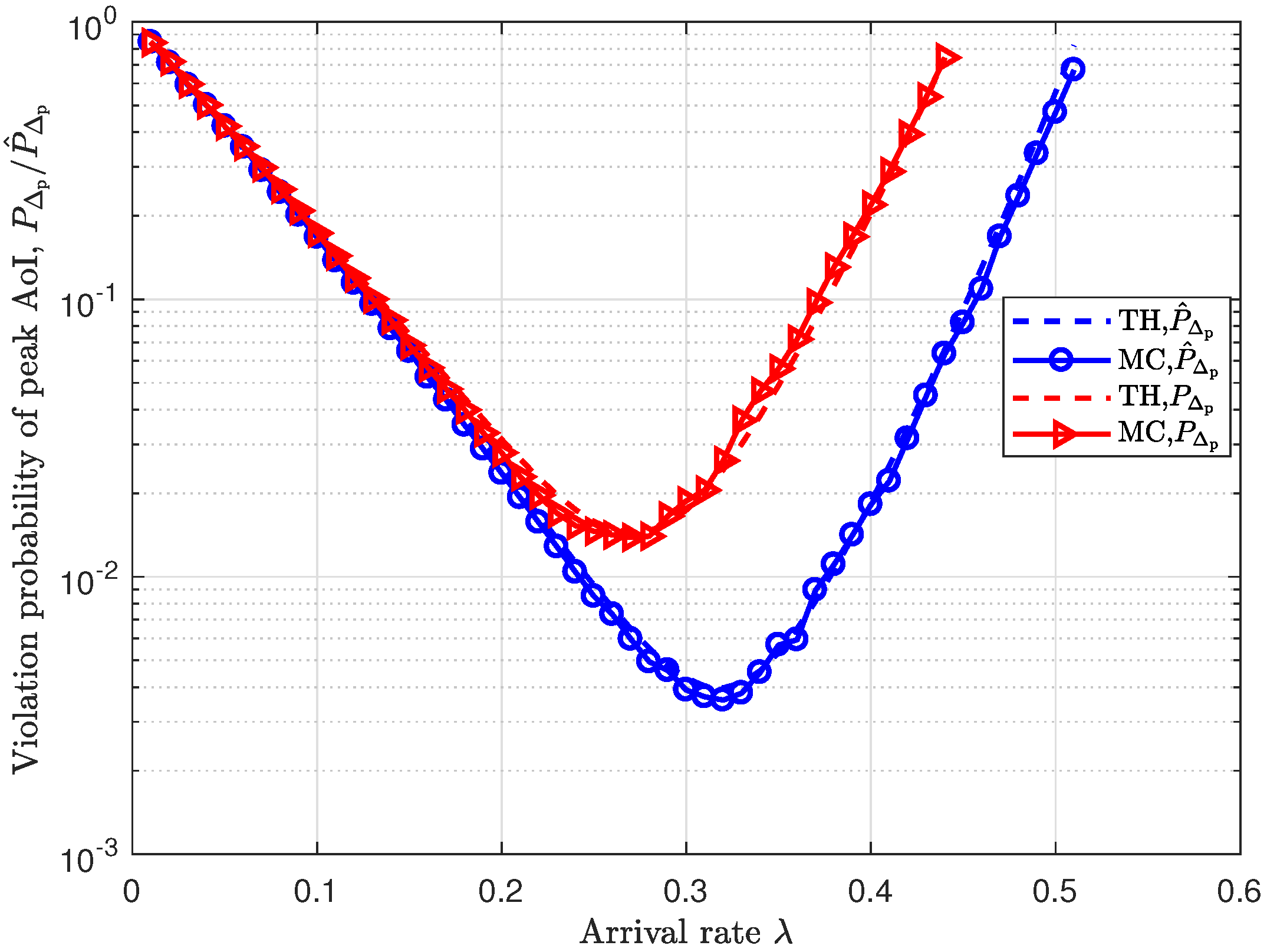
Figure 5 shows how the violation probability of peak AoI varies with the packet arrival rate
under the unsaturated traffic model. We observe that the violation probability decreases first and then increases. However, the peak AoI violation probability is larger than when the SNR-gated transmission control scheme is not used. This is because many transmissions are stopped, which leads to a lower service rate and, thus, degrades the timeliness.
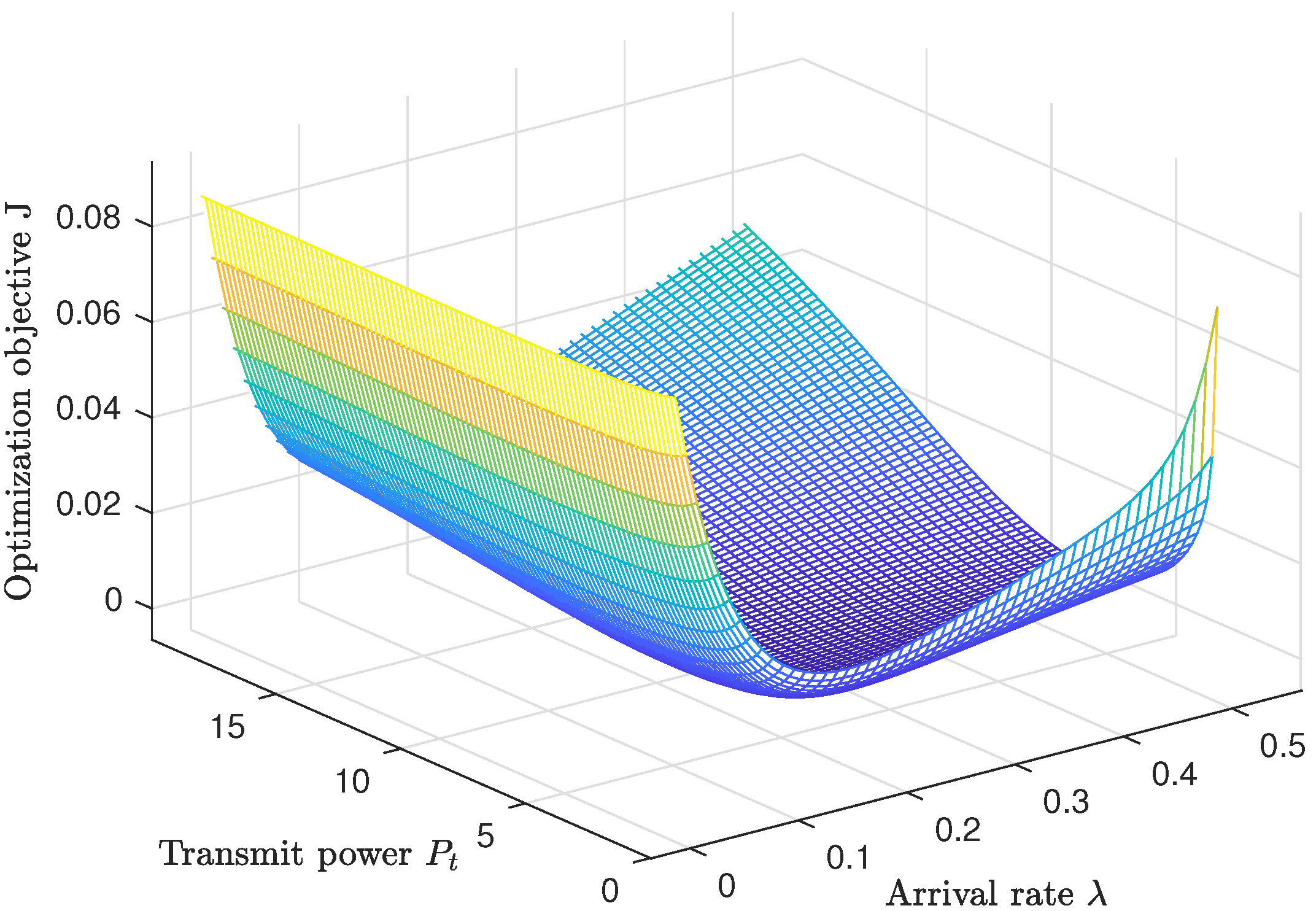
In
Figure 6, we present a three-dimensional graph of the weighted sum of the outage probability, interception probability, and PAoI violation probability. The
x-axis represents the transmit power, the
y-axis represents the arrival rate
, and the
z-axis represents the weighted sum of the three probabilities J. It is observed that the weighted sum has a bowl-shaped structure with a minimum point when the transmit power and the arrival rate are neither too small nor too large. This optimal point can be calculated through numerical computation.
5. Conclusions
In this paper, we investigate the security, reliability, and timeliness of a three-node physical layer security system, where the main channel and the eavesdropping channel are correlated. We propose an SNR-gated transmission control scheme and derive closed-form expressions for the outage probability, interception probability, and peak AoI violation probability. Our analysis and numerical results demonstrate the effectiveness of the proposed SNR-gated transmission control scheme; we explicitly derive the probabilities of data outage and interception while enhancing timeliness through the control of the data arrival rate. Moreover, we optimize the transmit power of the source node to minimize the weighted sum probability of outages, interceptions, and peak AoI violations. In the future, we plan to study the system with the adaptive rate, which is an interesting direction, as well as explore the eavesdropping channel model with relay nodes, which is another interesting research direction.