Abstract
Quantum key distribution (QKD) has great potential in ensuring data security. Deploying QKD-related devices in existing optical fiber networks is a cost-effective way to practically implement QKD. However, QKD optical networks (QKDON) have a low quantum key generation rate and limited wavelength channels for data transmission. The simultaneous arrival of multiple QKD services may also lead to wavelength conflicts in QKDON. Therefore, we propose a resource-adaptive routing scheme (RAWC) with wavelength conflicts to achieve load balancing and efficient utilization of network resources. Focusing on the impact of link load and resource competition, this scheme dynamically adjusts the link weights and introduces the wavelength conflict degree. Simulation results indicate that the RAWC algorithm is an effective approach to solving the wavelength conflict problem. Compared with the benchmark algorithms, the RAWC algorithm can improve service request success rate (SR) by up to 30%.
1. Introduction
Optical fibers have been deployed worldwide [1] and serve as one of the most common inter-regional communication infrastructures. Due to the openness of the network and some vulnerabilities in existing communication technologies [2], optical networks are facing severe information security challenges. In recent years, malicious cyberattacks have occurred in many areas [3,4,5].
Classical encryption methods with mathematical complexity [6,7] have been quite challenged, especially in the face of quantum computing [8,9]. Most existing cryptographic systems are based on the Rivest–Shamir–Adleman (RSA) and elliptic-curve cryptography (ECC) algorithms [10]. However, the Shor quantum algorithm can crack the RSA and ECC algorithms in polynomial time [11]. Post-quantum cryptography (PQC) [12] and quantum key distribution (QKD) [13] can resist attacks from quantum computers. By using the PQC algorithm instead of the ECC or RSA algorithms, the security of today’s electronic commerce will be effectively guaranteed [14,15]. The PQC algorithm is executed efficiently on hardware systems [16]. It is usually subject to side-channel attacks during implementation, which affect security [17,18,19]. Lightweight PQC is typically implemented in a constrained environment with limited devices, where attackers access the device during normal device operation [20]. Thus, additional protection against electromagnetic attacks is required. Currently, the PQC algorithm is still in the stages of development and verification, and its application and popularization are facing many challenges. QKD can be implemented as it is a relatively mature encryption method against attacks.
QKD provides theoretically unconditional security when combined with the one-time pad encryption algorithm [21,22]. QKD is based on the basic law of quantum mechanics [23,24], so it is possible for both the sender and the receiver to detect any third-party intervention. To meet the requirements of secure multi-user communication, it is necessary to construct multi-point interconnected QKD networks. Because deploying dedicated optical fibers for QKD alone is too costly, we use wavelength division multiplexing (WDM) technology to multiplex quantum signals and classical signals into the same optical fiber for transmission [25]. It has been proven to be feasible to integrate QKD into optical networks by WDM technology [26,27,28,29]. In addition, to further improve the utilization of wavelength resources as well as the transmission capacity of the fiber, time division multiplexing (TDM) [30] and space division multiplexing (SDM) [31] can also be adopted in QKD optical networks (QKDON).
Software-defined networking (SDN) is a new type of network virtualization technique, whose core lies in the ability to define and control the networks programmatically [32]. The introduction of the SDN technique in optical networks can improve the programmability and flexibility of the networks. Recently, some researchers have proposed the architecture of QKD over software-defined optical networks [33]. In this network architecture, quantum key pools (QKPs) between two QKD nodes are constructed to store and manage quantum keys. The SDN controller is deployed to determine the configuration and employment of QKPs through the OpenFlow protocol. QKDON supporting SDN technique can efficiently manage the network-wide key resources in QKPs through centralized control.
Although the QKD technique is continuously being improved and the key generation rate is getting higher, it cannot fully meet the encryption needs of the explosive development of data services. Many different solutions are proposed to achieve resource allocation, including routing, wavelength, and quantum key methods. Table 1 compares focus points and performance metrics of the related works [33,34,35,36,37] with our scheme, where ‘-’ means that this issue is not involved in the corresponding paper. Ref. [33] proposed the KoD scheme to allocate resources and update keys for different services, considering key-updating cases based on time complexity and data complexity. The RWTA algorithm in ref. [34] assigned quantum key channels based on the key-updating periods to enhance security. The dynamic DSKP scheme was proposed in ref. [35] to generate and assign quantum keys for users’ different demands. Ref. [36] took the quantum key allocation process and the QKP key supplement process into account from the perspective of system efficiency and security, designing the DDKA scheme to satisfy the efficiency and lightweight requirements of IoT applications. To minimize the wastage of keys and maximize the utilization efficiency of resources, ref. [37] dynamically adjusted the link evaluation indicators by considering key volume, the key generation rate, and the number of path hops comprehensively, and selected the optimal path.

Table 1.
The comparison of the related schemes with the RAWC scheme.
Most of the resource allocation algorithms in the aforementioned papers use the link length as the link weight, and carry out the routing allocation with the Dijkstra algorithm, while other schemes dynamically allocate resources for the security requirements of different service requests. Nevertheless, the quantum key generation rate is low, and the wavelength channels for data transmission are limited. We need to consider resource surplus status in QKDON. In addition, multiple service requests may arrive at the same time under practical application scenarios. These services compete for wavelength resources as they occupy the same link, resulting in service blocking.
This paper reconstructs the routing scheme and proposes a resource-adaptive algorithm with wavelength conflicts (RAWC). Firstly, the number of real-time network resources available is taken as an important factor in the scheme to achieve network load balancing. Then, we introduce the wavelength conflict mechanism to determine the communication path, so that the communication success rate is improved by minimizing wavelength competition.
The rest of this paper is organized as follows. Section 2 introduces the point-to-point QKD mechanism. Section 3 shows the QKD relay method used. Section 4 describes the SDN-based QKP technique. Section 5 presents the problems and application scenarios addressed by the scheme. Section 6 discusses the proposed RAWC scheme and algorithm. Section 7 shows and analyzes the simulation results. Section 8 discusses several issues that can be explored in future work. Finally, Section 9 concludes this paper.
2. Point-to-Point QKD Mechanism
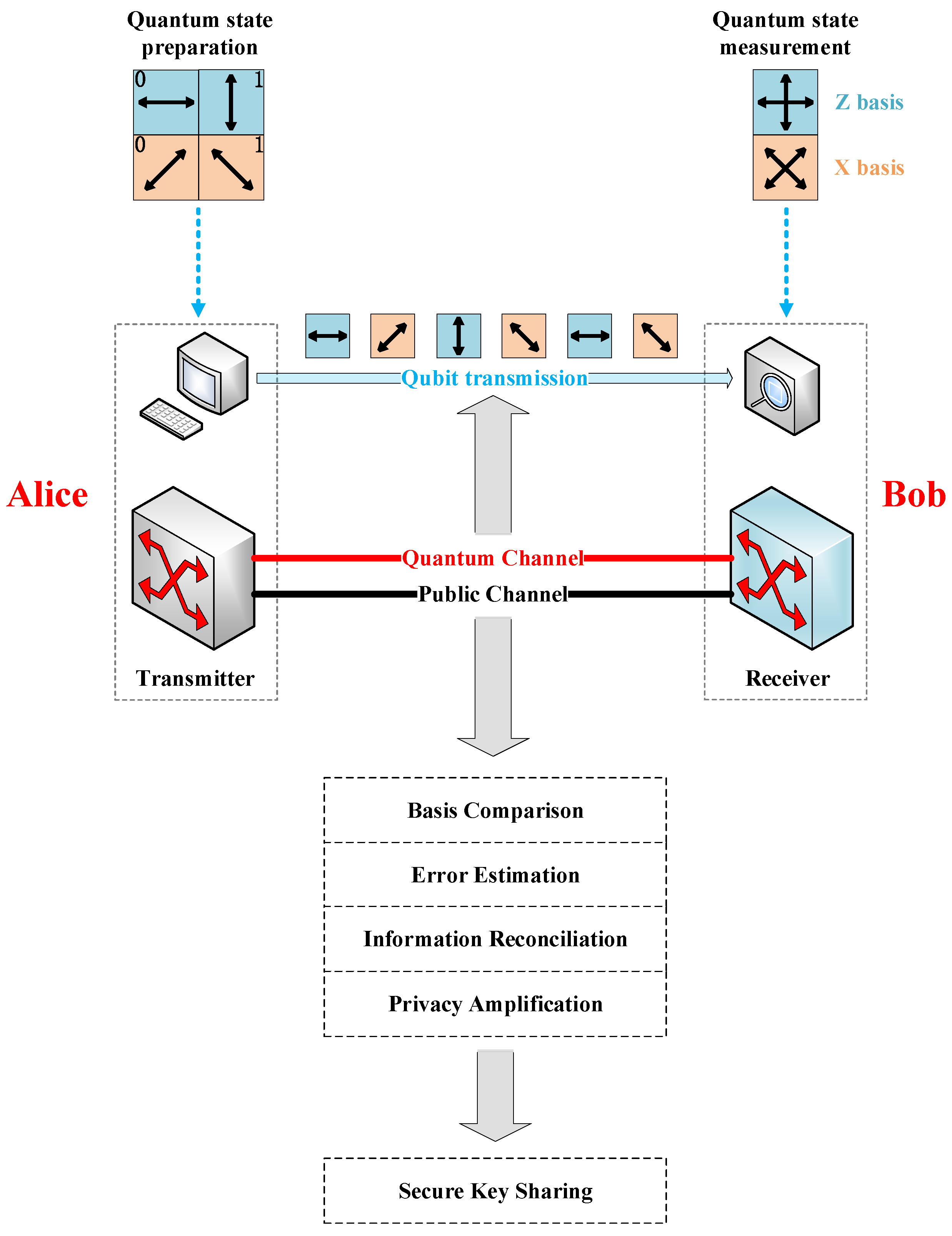
This section describes the point-to-point QKD mechanism. BB84 protocol [13], the first QKD protocol, is the most technically mature protocol. In this protocol, the sender, Alice, encodes random binary bits using four single-photon polarization states, i.e., “horizontal ()”, “vertical ()”, “+45° ()”, and “−45° ()”, and sends them to the receiver, Bob, via the quantum channel (QCh). and constitute the Z basis, while and constitute the X basis, where the Z basis and the X basis are conjugate. Conventionally, suppose and represent the binary value 0, and and represent the binary value 1. 0 and 1 are called qubits. The correct bit information is obtained when Bob chooses the measurement basis corresponding to Alice to measure the received single photon. When Bob uses one measurement basis to measure the single-photon polarization state of another measurement basis, there is a 50% chance that he will receive different data from Alice.
The point-to-point QKD mechanism based on the BB84 protocol is introduced below, as shown in Figure 1. The QKD process consists of the following steps:
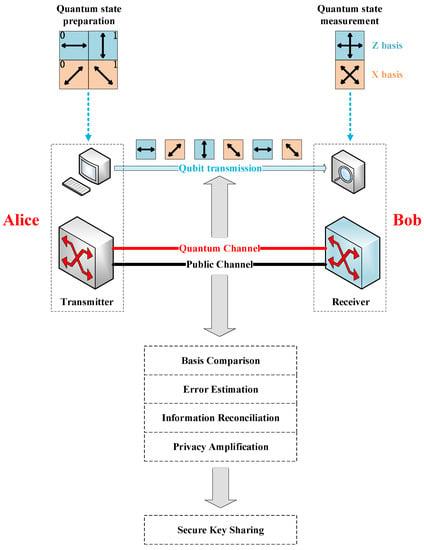
Figure 1.
Point-to-point QKD mechanism based on BB84 protocol.
- Alice generates two random sequences of the same length, and , where determines the chosen measurement basis and determines the single-photon polarization state to be sent. Alice prepares the single-photon polarization states (i.e., qubits, called raw keys) from the chosen random sequence and sends them to Bob via QCh.
- Bob selects a random sequence to determine the measurement basis, performs measurement for the received quantum states, and records the measurement results as .
- Alice announces the sequence of the measurement basis chosen via the public channel (PCh). Bob compares it with his own sequence of the measurement basis. When they choose the same basis, Alice and Bob keep the data and convert them into bit information (called sifted keys); otherwise, the data is discarded.
- Alice and Bob disclose part of the sifted keys to perform error estimation and calculate the corresponding quantum bit error rate. If the quantum bit error rate is higher than a set error threshold, the QKD process is terminated, and step 1 is repeated.
- Finally, Alice and Bob complete the post-processing process via PCh, including information reconciliation and privacy amplification, to obtain the final secure bits (called secret keys).
As shown in Figure 1, two channels are required for QKD, i.e., QCh for transmitting quantum signals and PCh for classical information exchange. To save fiber resources, we multiplex quantum signals and classical signals into the same optical fiber for transmission based on WDM technology. Given the crosstalk between classical and quantum signals, there is always a certain wavelength separation between QCh and PCh [28].
In recent years, researchers have paid more attention to the measurement-device-independent (MDI) protocol [38]. In the MDI protocol, the detection device is controlled by a third party, Charlie. Alice and Bob jointly send quantum signals to Charlie to complete the key sharing. This protocol eliminates the detector vulnerability of the actual QKD system. Since the proposal of the MDI protocol, research on long-distance and high-rate MDI-QKD in practical networks has increased [39,40], and its use has been extended to free space [41]. In addition, the multi-user scheme of the MDI protocol is useful for resisting detection attacks [42]. Similar to the MDI protocol, the twin-field (TF) protocol is also a three-party protocol. Based on single-photon interference, it can break through the rate–distance limit of QKD under the condition of guaranteeing the security of keys [43]. Minder et al. implemented a 454 km TF-QKD [44]. Wang et al. extended the security key distribution distance to 833.8 km [45].
3. Trusted Relay
QKDON is composed of multiple nodes and fiber links. However, the limited transmission distance of point-to-point QKD cannot accommodate QKD between two remote nodes. Hence, the distance of key distribution needs to be extended using relay technology [46]. In this paper, we use trusted relay-based networking technology.
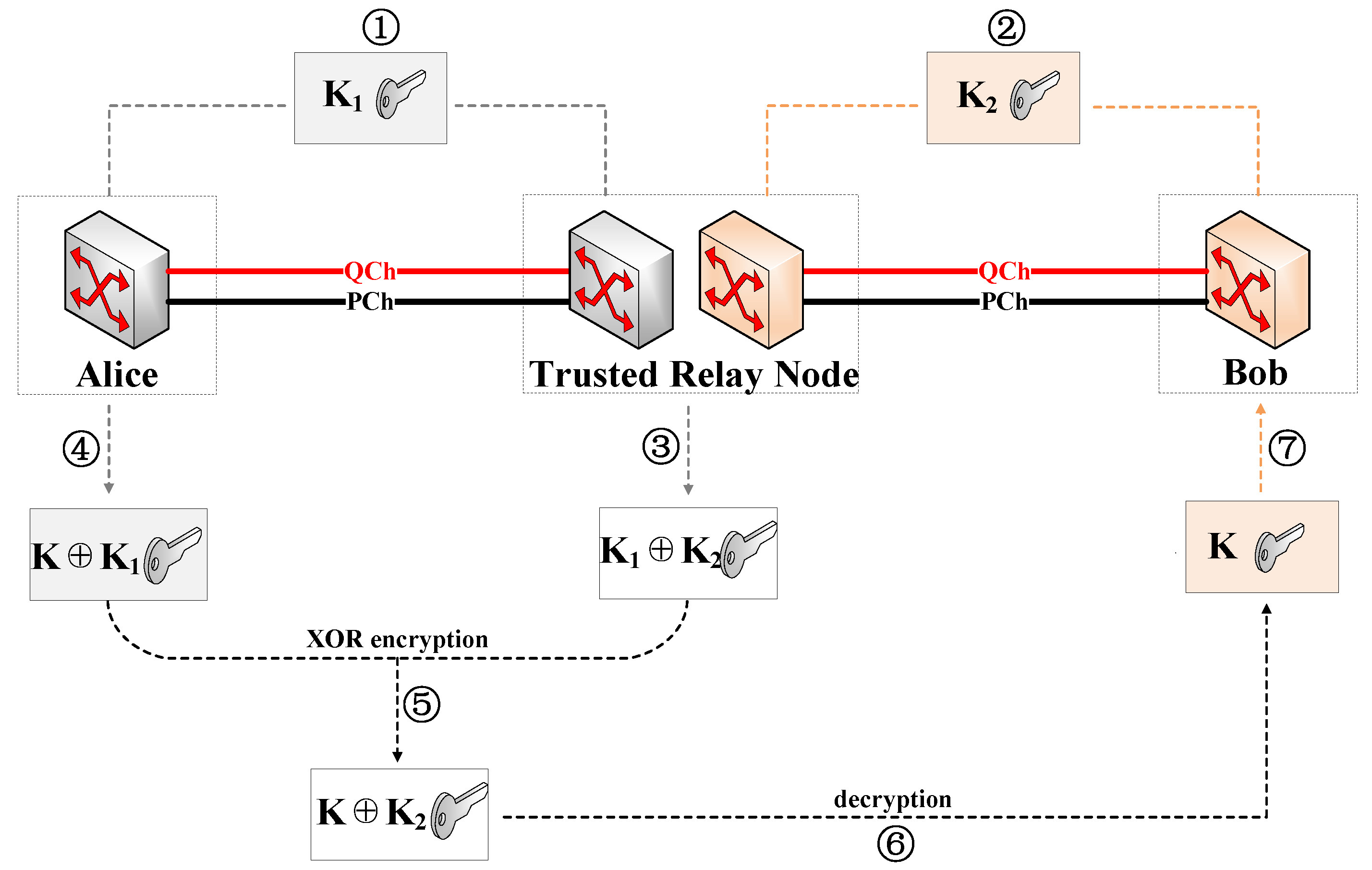
As shown in Figure 2, assuming that Alice and Bob share a quantum key K via a trusted relay node, its relay principle can be summarized in the following steps: ➀ The shared key is generated between the sender Alice and the relay node in the form of QKD. ➁ The shared key is generated between the relay node and the receiver Bob. ➂ he relay node performs XOR operation on key and key and stores the obtained key temporarily. ➃ Alice uses key to encrypt the key K to be shared with Bob and sends the obtained key to the relay node. ➄ The relay node performs an XOR operation with the temporarily stored key and key to obtain the encryption key and sends it to Bob. ➅ Bob decrypts the obtained key with the key to obtain key K. ➆ Finally, Alice and Bob obtain the shared key K.
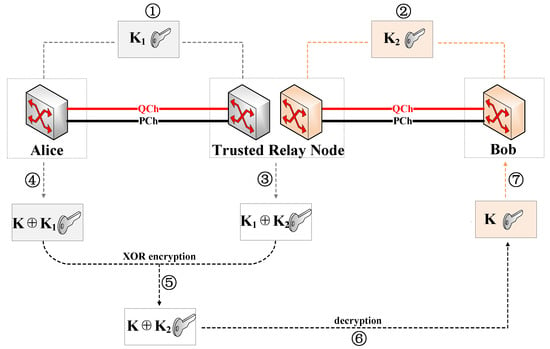
Figure 2.
Schematic diagram of the relay principle.
The QKD path with multiple relay nodes has to be established for two end nodes with long distances. Then, the keys are transmitted along the QKD path using hop-by-hop encryption and decryption. As specified in the above steps, each relay node can obtain the key shared between two end nodes through decryption; hence, these relay nodes must be trusted. In QKDON, all QKD nodes can act as the source and destination nodes to request services and also as relay nodes to share quantum keys.
4. Quantum Key Storage and Provision
The key generation rate in the current QKD system is still low. Consequently, quantum keys are extremely valuable network resources in QKDON. Generally, a key storage device embedded in each QKD node is used to store quantum keys.
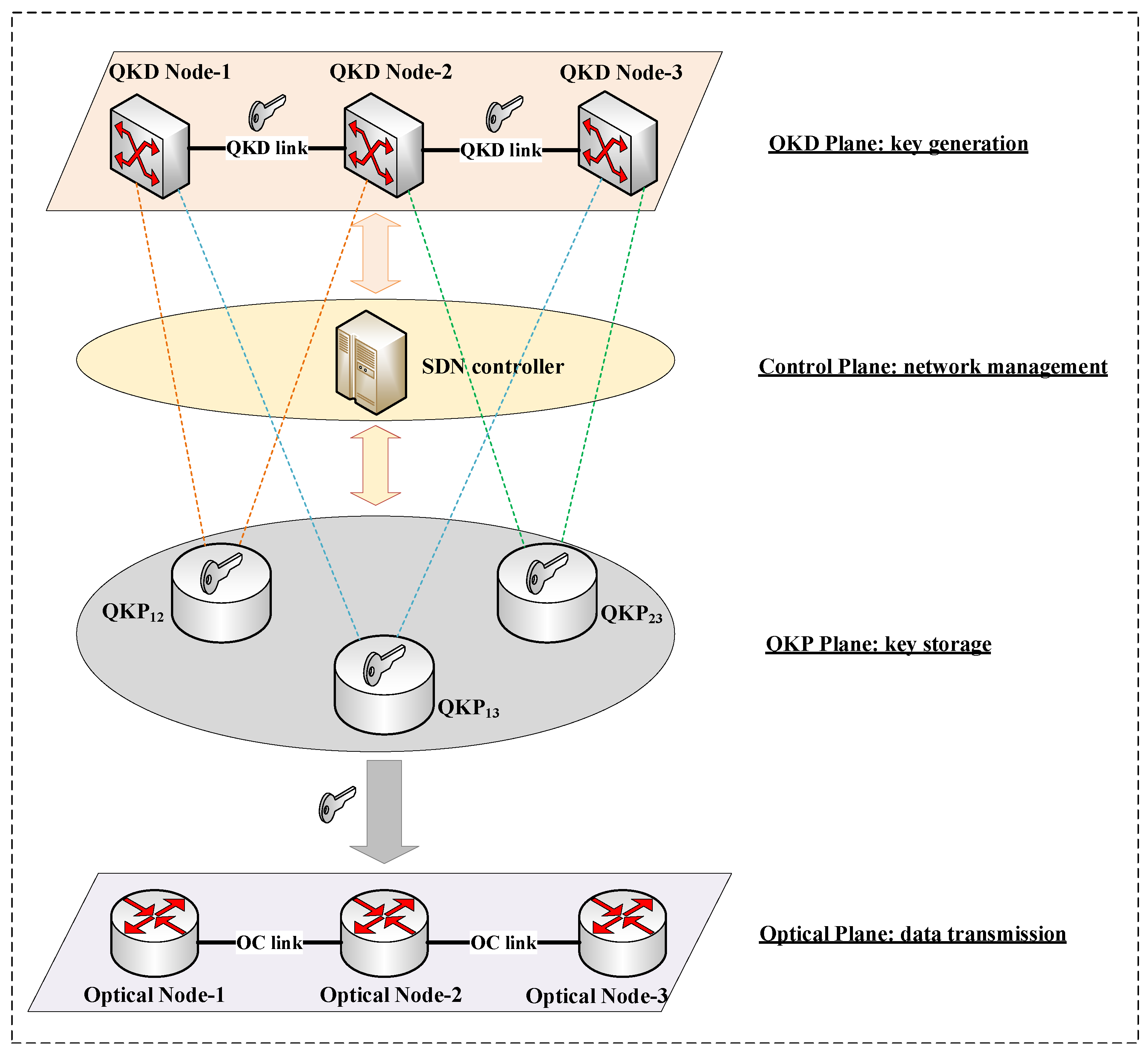
Constructing a quantum key pool (QKP) can improve the quantum key provisioning capability [47]. We virtualize quantum keys generated between two QKD nodes and store them in a cache device, namely, QKP. Two QKD nodes directly connected via a fiber link can construct QKPs, such as and in Figure 3. Node-1 and Node-3 cannot distribute keys directly, so the end-to-end is constructed using the relaying method mentioned in Section 3. QKP stores the generated keys continuously. Therefore, QKP supplies the accumulated keys in a timely manner when the encryption service is in high demand.
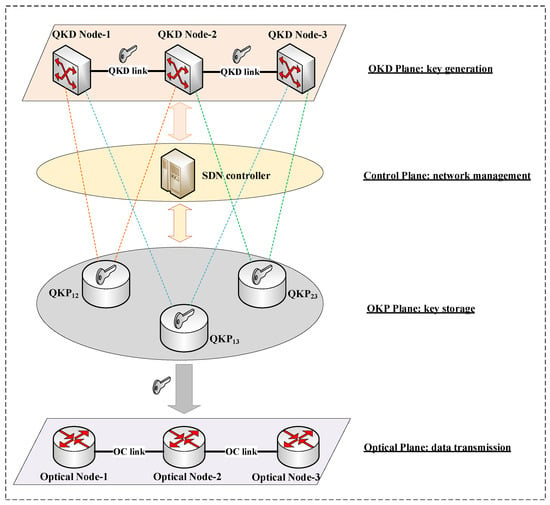
Figure 3.
QKP architecture based on SDN.
The key-sharing process between non-adjacent nodes requires quantum keys of each relay node. It is necessary to select the QKD path reasonably and manage the limited quantum key resources. QKP monitors the remaining number of quantum keys and the key generation rate in real time. The SDN controller manages QKPs through real-time information and schedules key resources to meet the encryption requirements [47]. The QKD links between QKD nodes in Figure 3 include QCh and PCh, which are used for the QKD process. Optical nodes are connected through optical communication links (OC links, i.e., data channels) to transmit service data. Based on WDM technology, the above three channels can be multiplexed into the same optical fiber [25].
5. Problem Statement
The wavelength channels for actual communication are selective. QCh and PCh for the QKD process and the data channel (DCh) for data transmission are usually placed in the C-band and O-band [25,48]. The total number of wavelengths should conform to the commercial WDM systems [34]. Additionally, the existing key generation rate only reaches the order of Mbps at the transmission distance of 50 km [49], so quantum keys in QKP are scarce resources. Therefore, it is important to allocate wavelengths and quantum keys efficiently and reasonably.
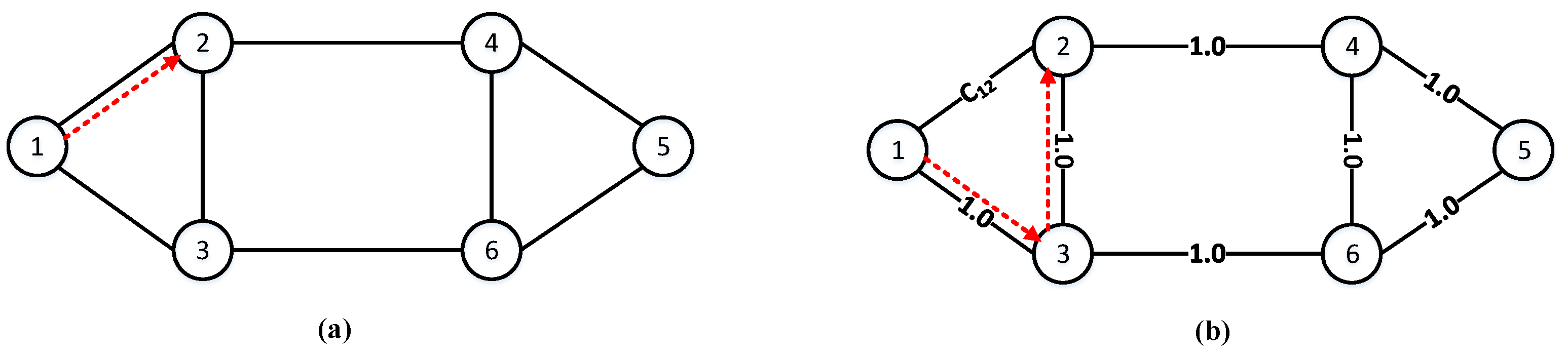
To clearly illustrate the above, the six-node network topology in Figure 4 is taken as an example. Now, we consider the change in the service request success rate and resource utilization. For simplicity, the node pair (1, 2) is used as the request node pair, where “1” and “2” represent the serial numbers of the source and destination nodes, respectively. As shown in Figure 4a, when only fixed parameters such as link lengths are used as link weights, the communication path selected by the Dijkstra algorithm is fixed as path 1→2 (red arrow). The continuous arrival of requests (1, 2) will aggravate the load on link 1→2, and may even run out of resources. Then, it is impossible to guarantee secure data transmission. Eventually, request (1, 2) is blocked. As shown in Figure 4b, when introducing the real-time residual wavelengths and quantum keys, the link weights dynamically change with the resource consumption of each service request. Assume that initially each link weight in Figure 4b is 1.0, and the weight of link 1→2 becomes at some point. If the relationship is satisfied, the shortest path for the request (1, 2) is path 1→3→2. Each time the request (1, 2) arrives, the communication path is selected according to the dynamically changing link weight. Thereafter, path 1→3→6→4→2 may also be taken as the communication path. In short-distance QKDON, where network resources are limited and some links do not carry services (such as link 1→3 and link 3→2, mentioned above), too many free wavelength channels and quantum keys will be wasted. If communication paths are selected based on the real-time remaining number of wavelengths available for each link, and the real-time remaining number of quantum keys available in QKP, the load pressure on the link is relieved. Finally, the encryption efficiency of the QKP is improved indirectly, and even the success rate of requests is increased.
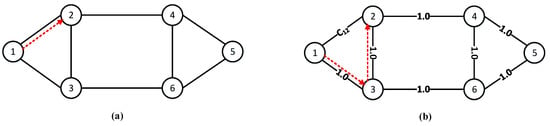
Figure 4.
An example of routing assignment for the six-node network topology. (a) Static routing: fixed parameters such as link lengths are used as weights; (b) Dynamic routing: the real-time remaining number of resources is used as weights.
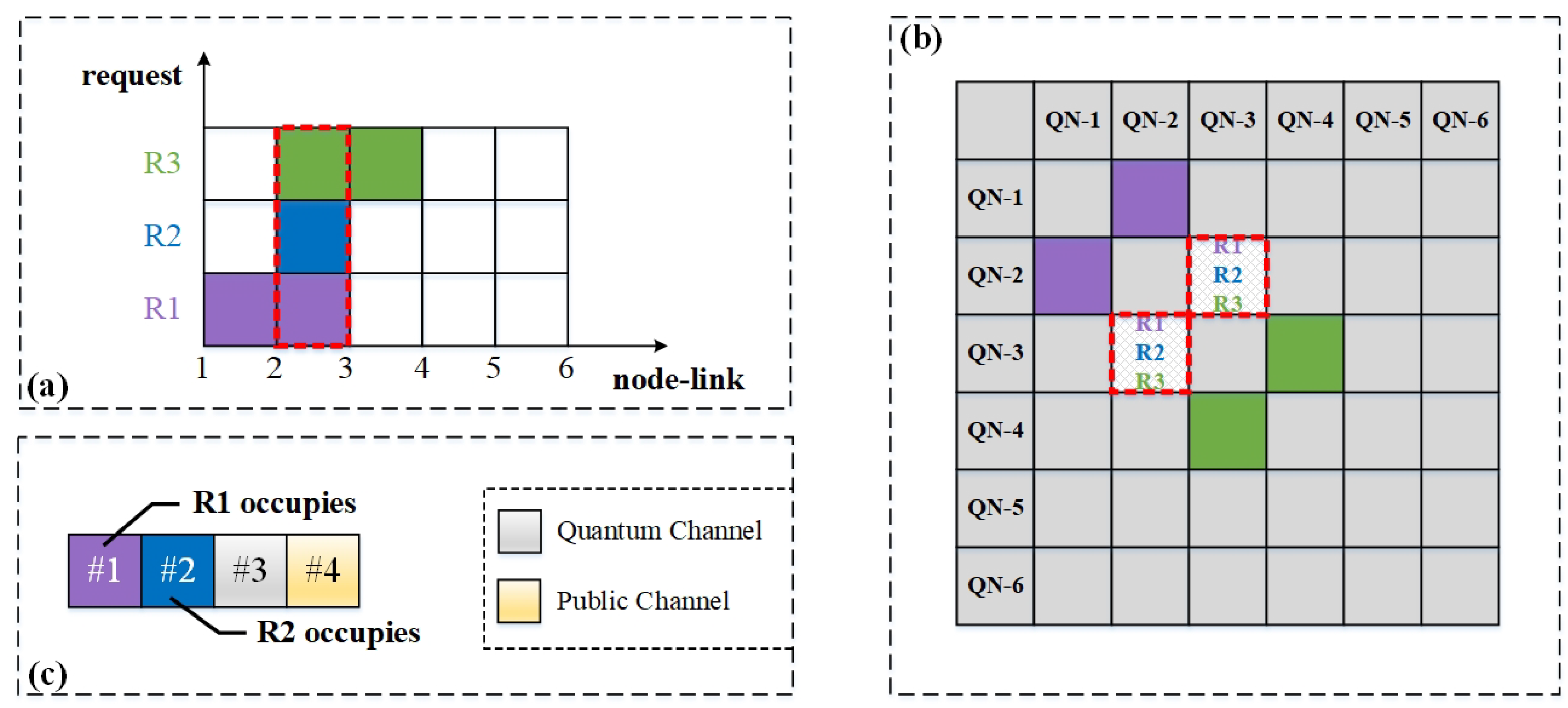
Moreover, wavelength conflicts occur frequently when multiple service requests arrive simultaneously and occupy the same link, given the limited wavelength resources. Figure 5 demonstrates the potential conflicts due to multiple services sharing wavelength resources. As shown in Figure 5a, the horizontal coordinate represents the nodes and links, and the numbers on it represent the serial numbers of nodes. The colored boxes between every two numbers show the occupancy of the links and wavelength channels by different service requests and the vertical coordinate represents the service requests. Suppose three requests arrive simultaneously at a certain moment, namely requests R1: (1, 3), R2: (2, 3), and R3: (3, 4). Their communication paths are path 1→2→3, path 2→3, and path 3→2→4, respectively. It can be seen that the three requests share the wavelength resources on the link 2→3. Figure 5b shows the mapping of the corresponding case in Figure 5a in the adjacency matrix, where the upper and lower diagonal matrices are symmetrical, since the network topology is undirected. Figure 5c shows the wavelength channel occupancy of the shared link 2→3, with each box representing a wavelength channel on the link. For simplicity, consider the case where there are four wavelength channels on link 2→3. Channels #3 and #4 are used as QCh and PCh, respectively; the remaining two channels, #1 and #2, can only provide data transmission for two service requests. When R1, R2, and R3 arrive at the same time, we try to assign wavelength channels to them. At this time, two wavelength channels need to meet the data transmission requirements of three services; thus, wavelength conflicts will occur. Then, one service request must be blocked, such as the request R3, as shown in Figure 5c. Therefore, to improve the success rate of requests, we should avoid potential wavelength conflicts in the resource allocation process.
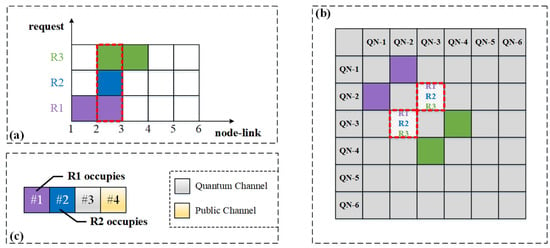
Figure 5.
An example of wavelength conflicts. (a) Occupancy of links and wavelength channels by multiple services; (b) Mapping of resource occupancy in the adjacency matrix; (c) Wavelength occupancy for shared link 2→3.
To summarize, which scheme to allocate limited wavelength resources and rare quantum keys to in order to reduce wavelength conflicts and blocking probability is an important research topic in short-distance QKDON.
6. The Proposed RAWC Scheme
6.1. Scheme Description
In this section, a resource-adaptive routing scheme with wavelength conflicts (RAWC) is proposed. The RAWC scheme is applied in scenarios where wavelength resources on links and quantum keys in QKP are limited and the simultaneous arrival of service requests occurs. Additionally, we consider short-distance QKDON, which means that point-to-point QKD can be carried out between any two nodes that are directly connected. The two nodes on the link generate keys directly via QCh and PCh, so the impact of link length on service requests can be ignored.
The RAWC scheme is divided into two specific cases from the perspective of routing allocation: ➀ Only one QKD service request arrives at a certain moment. Considering the characteristics of QKDON fully, the real-time remaining number of wavelengths available for each link and the real-time remaining number of quantum keys available in QKP are introduced into the calculation of link weights. After the arrival of each QKD service request, the communication path is calculated with the Dijkstra algorithm dynamically based on the resource surplus status. This facilitates the preference of the path with more wavelengths and quantum keys remaining to reduce the waste of resources on the service-free transmission link. In this way, network load balancing and the efficient utilization of network resources are achieved. ➁ Specifically, when m QKD service requests arrive at the same time, the K-shortest-path (KSP) algorithm is used to calculate the K shortest paths for each request. Then, the wavelength conflict degree of each of the K paths for the current request is calculated. The path with the lowest wavelength conflict degree is selected as the communication path, which is calculated according to the method described in Section 6.2.2. Considering the influence of other requests, the path with low wavelength conflicts is preferentially selected when assigning routing for the current request. Therefore, the service blocking caused by potential wavelength competition will be reduced, which improves the request success rate. Table 2 lists some of the notations and definitions used in this paper.

Table 2.
Notations and definitions.
6.2. Scheme Detail
In the following, we describe the steps and algorithm of the proposed RAWC scheme. Based on the analysis in Section 6.1, the path selection method for the RAWC scheme is described in detail below.
6.2.1. Link Weight
The link weight is calculated according to the real-time remaining number of wavelengths available on each link and quantum keys available in the corresponding QKP:
where denotes the weight of link; and represent the initial number of wavelengths on each link and the initial number of quantum keys stored in QKP for each link, respectively, i.e., the maximum number of wavelengths and the maximum number of quantum keys; and represent the real-time remaining number of wavelengths available on link and the real-time remaining number of quantum keys available in QKP, respectively; and and are the weight adjustment factors . As can be seen in Equation (1), the more wavelength channels and quantum keys are available, the smaller the corresponding weight value.
When only one QKD service request arrives at a certain time, the Dijkstra algorithm is used to complete the routing calculation based on Equation (1). The path with the minimum weight value is taken as the communication path of the service.
6.2.2. Wavelength Conflict Degree
When m QKD service requests (for ease of description, the m service requests are numbered , , …, ) arrive simultaneously at a given moment, wavelength conflicts caused by multiple services occupying the same link must be considered. The KSP algorithm is used to calculate K alternative paths for each service request. After determining the alternative paths for each service request, the wavelength conflict degree of each alternative path needs to be calculated. For service request , the wavelength conflict degree of its alternative path is calculated as follows:
where denotes the jth alternative path of the QKD service request ; is the link set contained in the path ; is a link of this link set; is the total number of available wavelengths for path ; represents the communication path selected for service request ; and is the wavelength conflict marker of each link. When the communication path of request other than the service request contains link, it means that the two services have to share the wavelength resources of link; then, , otherwise . Note that the wavelength conflict degree is introduced to predict potential wavelength competition when choosing the path. It does not necessarily mean that wavelength conflicts will occur. The path with low wavelength conflicts is preferred to reduce the interference between service requests and improve the success rate of service requests.
The path selection procedure based on wavelength conflict degree is as follows:
- Calculate the wavelength conflict degree of each alternative path for request . Firstly, assume for the moment that the path with the smallest weight of the other service requests is their communication path, which is used to calculate the wavelength conflict degree of each alternative path for . Then, the wavelength conflict degree of each alternative path for is calculated according to Equation (2). Finally, the path with the minimum wavelength conflict degree is selected as the communication path, denoted as .
- Calculate the wavelength conflict degree of each alternative path for request . According to step 1, when calculating the wavelength conflict degree of the alternative paths for , the communication path of is determined as . The path with the smallest weight of the other service requests is assumed to be their communication path. Then, calculate the wavelength conflict degree of each alternative path for . Finally, select the path with the smallest wavelength conflict degree as the communication path, denoted as .
- Calculate the wavelength conflict degree of each alternative path for request . According to steps 1 and 2, the communication paths for and are and , respectively. Assume that the path with the smallest weight of the other service requests is their communication path. Then, calculate the wavelength conflict degree of each alternative path for . Finally, select the path with the smallest wavelength conflict degree as the communication path, denoted as .
And so on and so forth, until the communication paths of all service requests are calculated.
6.3. RAWC Algorithm
Based on the above scheme description, the RAWC algorithm is designed. It is divided into two cases: ➀ Only one QKD service request arrives at a certain time, in which case there is no wavelength conflict, as shown in Algorithm 1; ➁ Multiple QKD service requests arrive simultaneously at a certain time and there are wavelength conflicts, as shown in Algorithm 2. The schemes for both cases are divided into three steps, i.e., routing calculation, wavelength assignment, and quantum key assignment. In the routing computation, case 1 needs to adaptively calculate the communication path with the Dijkstra algorithm for the QKD service request arriving at each moment. Case 2 first uses the KSP algorithm to calculate K alternative paths for each QKD service request, and then calculates the wavelength conflict degree of each alternative path.
| Algorithm 1 The case without wavelength conflicts |
| Input: , , , , , Output: SR, WRU, QKU of QKD service requests
|
| Algorithm 2 The case with wavelength conflicts |
| Input: , , , , , Output: SR, WRU, QKU of QKD service requests
|
7. Simulation Results and Analysis
To evaluate the feasibility and performance of the RAWC algorithm in QKDON, the simulation was performed on both the six-node network topology (shown in Figure 5) and the NSFNET topology, which consists of 14 nodes and 21 links. This paper studies short-distance QKDON with limited network resources and scenarios where multiple QKD service requests arrive simultaneously. In our work, the quantum channel and the public channel occupy two wavelengths, and each link has the same total number of wavelengths for the data channel. Without special instructions, there are 40 wavelengths on each link. In addition, it is assumed that each QKP stores the same number of quantum keys. In the following simulation, we set the link weighting factors to . The arrival of QKD service requests follows a Poisson distribution. The holding time of each service request is fixed and the same. When the duration of the services at a certain moment is over, the services at the next moment arrive. The channels are released when the services end their occupation of the data channels. To select more alternate paths, Section 6.2.2 employs the KSP algorithm with .
This section evaluates the performance of this scheme by comparing different schemes based on the following three metrics: service request success rate (SR), wavelength resource utilization (WRU), and quantum key utilization (QKU). SR refers to the proportion of QKD services that can successfully obtain quantum keys from QKP and can be successfully transmitted to the total services, indirectly reflecting the encryption efficiency of QKP and the ability of the network to guarantee service transmission. WRU and QKU are utilized to describe the usage of network resources of QKDON.
7.1. Verification of the RAWC Algorithm on the Six-Node Network Topology
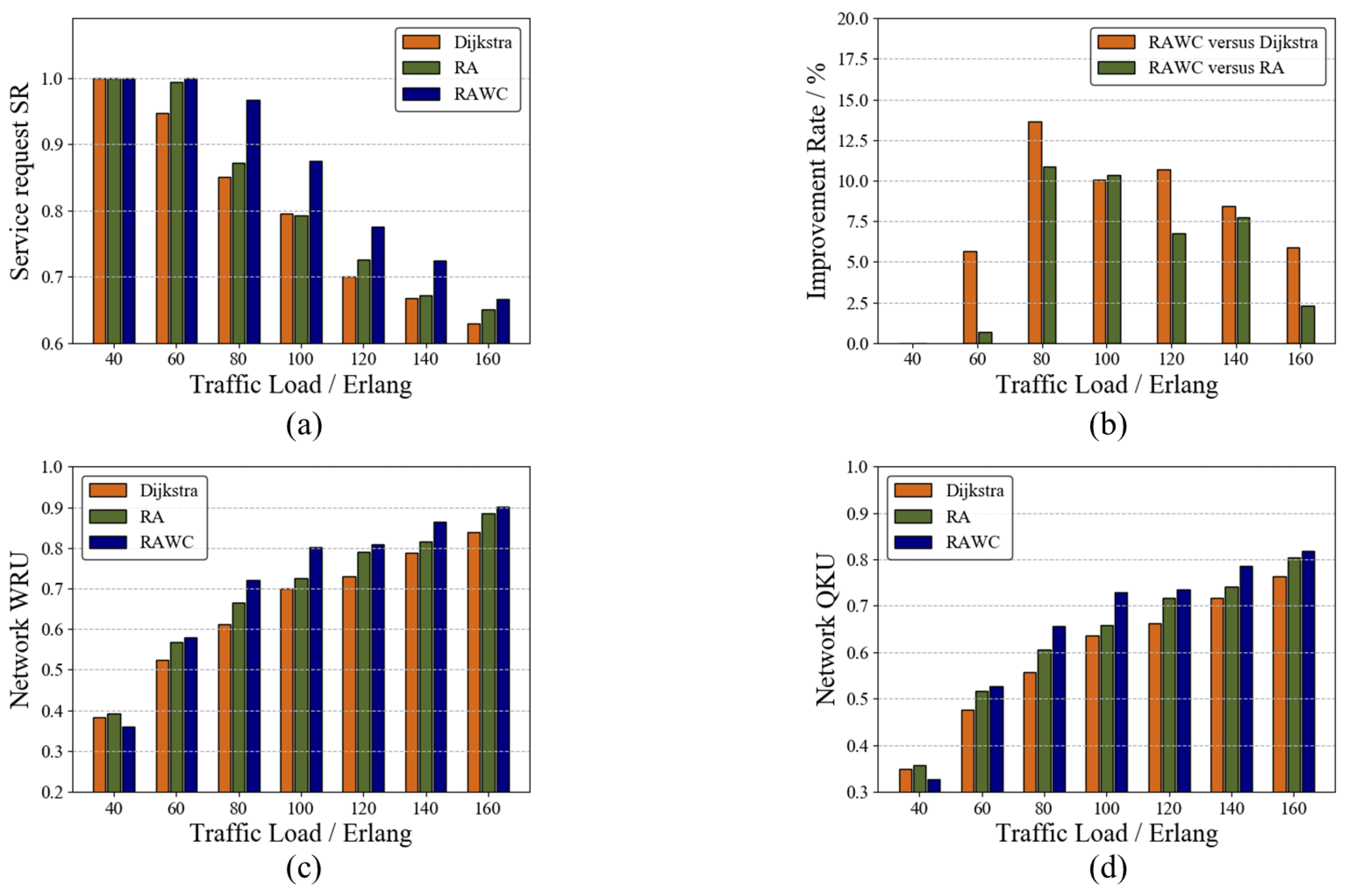
Figure 6 shows the performance of this scheme on the six-node network topology. The Dijkstra routing algorithm and the resource-adaptive (RA) algorithm are used as two benchmark schemes to verify the performance improvement in the RAWC algorithm in terms of the service request success rate and resource utilization. In this paper, the Dijkstra routing algorithm takes the link length as the link weight, and the RA algorithm does not consider wavelength conflicts. Figure 6a,b compare SRs of different algorithms, and the percentage improvement in the RAWC algorithm in SR compared with other algorithms, respectively. As the traffic load increases, the SRs of all three algorithms decrease. Due to limited network resources, the increase in traffic load reduces the ability of QKDON to provide wavelength channels and QKP to provide key services. Additionally, it can be observed that the lowest SR is achieved under the Dijkstra algorithm, and the highest SR under the RAWC algorithm. At a traffic load of 80 Erlang, the proposed RAWC algorithm improves SR by up to 13.5% compared with the Dijkstra algorithm. This is because using only the path length as the link weight increases the link load pressure, which causes service blocking. Even if a dynamic routing scheme is adopted, not taking into account the competition for wavelength resources blocks services. Figure 6c,d show the wavelength resource utilization (WRU) and quantum key utilization (QKU) of the three schemes, respectively. From the figures, it can be seen that both WRU and QKU increase with the increase in traffic load, which is the result of increased network resource consumption. When the traffic load is 40 Erlang, the advantages of the RAWC algorithm are not observable because the traffic is low. As the traffic load increases gradually, WRU and QKU of the proposed RAWC algorithm are consistently found to be the highest. The RAWC algorithm gives priority to the links with more remaining resources when selecting the communication path. The above simulation results show that the RAWC algorithm is the optimal choice for achieving load balancing.
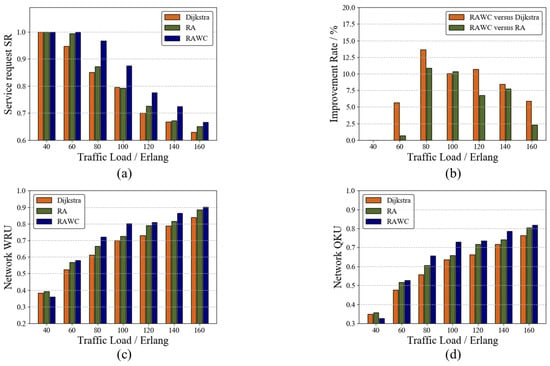
Figure 6.
Performance comparison of different algorithms on the six-node network topology. (a) SR; (b) Improvement rate; (c) WRU; (d) QKU.
7.2. Service Request SR on Two Network Topologies
7.2.1. Comparison of Different Schemes
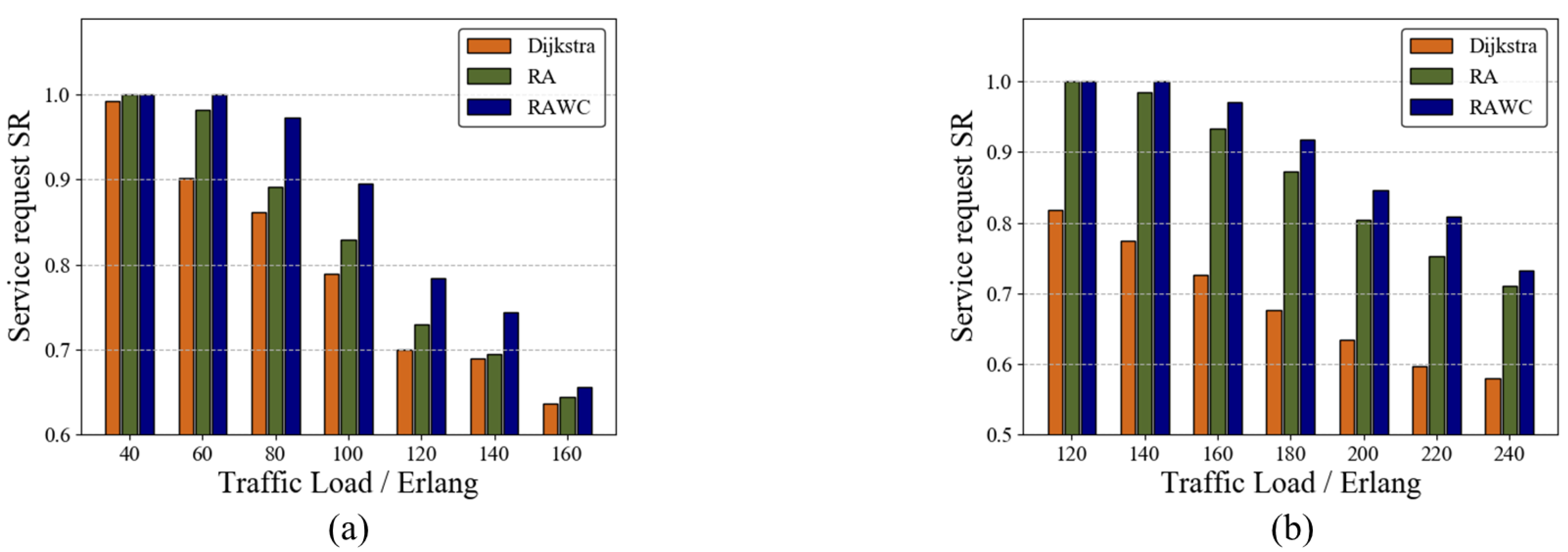
To further verify the performance of the RAWC scheme, we applied the algorithm on both the six-node topology and the NSFNET topology. Figure 7a,b illustrate the results of SR versus traffic load for the three schemes on the six-node network topology and the NSFNET topology, respectively, with other initial conditions consistent in both networks. The SR decreases as the traffic load increases in both networks, with the RAWC scheme always having a higher SR than the other two schemes. On NSFNET topology, the proposed RAWC scheme improves SR by 30% on average compared with the Dijkstra algorithm. When the traffic load increases to a certain level, the gap between the RA scheme and the RAWC scheme gradually decreases. The reason is that the moment of arrival of multi-service requests set in this paper is fixed. As the service traffic base increases, the proportion of service requests completed by the RAWC scheme compared to the RA scheme decreases, which will be reflected in Section 7.2.3.
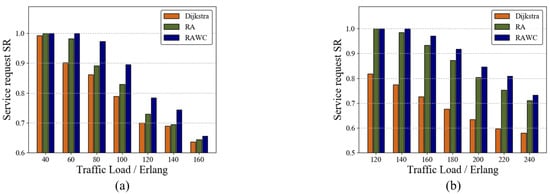
Figure 7.
SR of the three schemes. (a) Six-node network topology; (b) NSFNET topology.
7.2.2. Service Request SR of the RAWC Scheme in Different Resource Cases
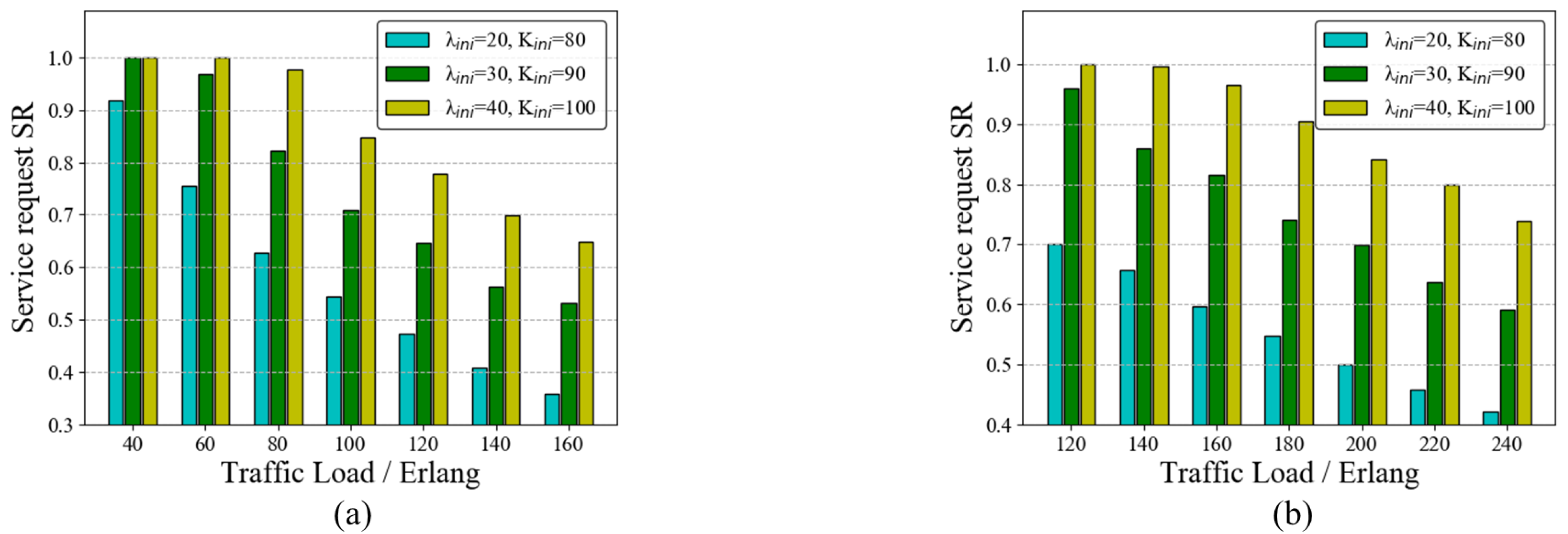
In this paper, we consider the following three resource cases: ➀ Case 1: the initial number of wavelength channels in the network is set to 20, and the initial number of quantum keys stored in QKP corresponding to each link is set to 80; ➁ Case 2: ; ➂ Case 3: . The SRs of the RAWC scheme in the three cases on the six-node network topology and the NSFNET topology are shown in Figure 8a,b, respectively. It is clear that with a fixed traffic load, the more initial resources are in QKDON, the higher the service request success rate is. This indicates that initial resources in the network should be supplemented as much as possible for QKP to ensure more secure service transmission.
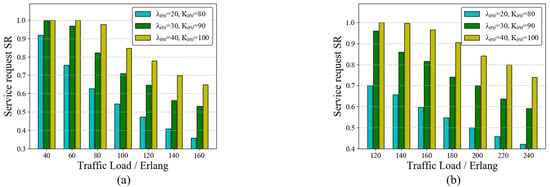
Figure 8.
SR of the RAWC algorithm in different cases (case 1: ; case 2: ; case 3: ). (a) Six-node network topology; (b) NSFNET topology.
7.2.3. Service Request SR of the RAWC Scheme under Different Scenarios
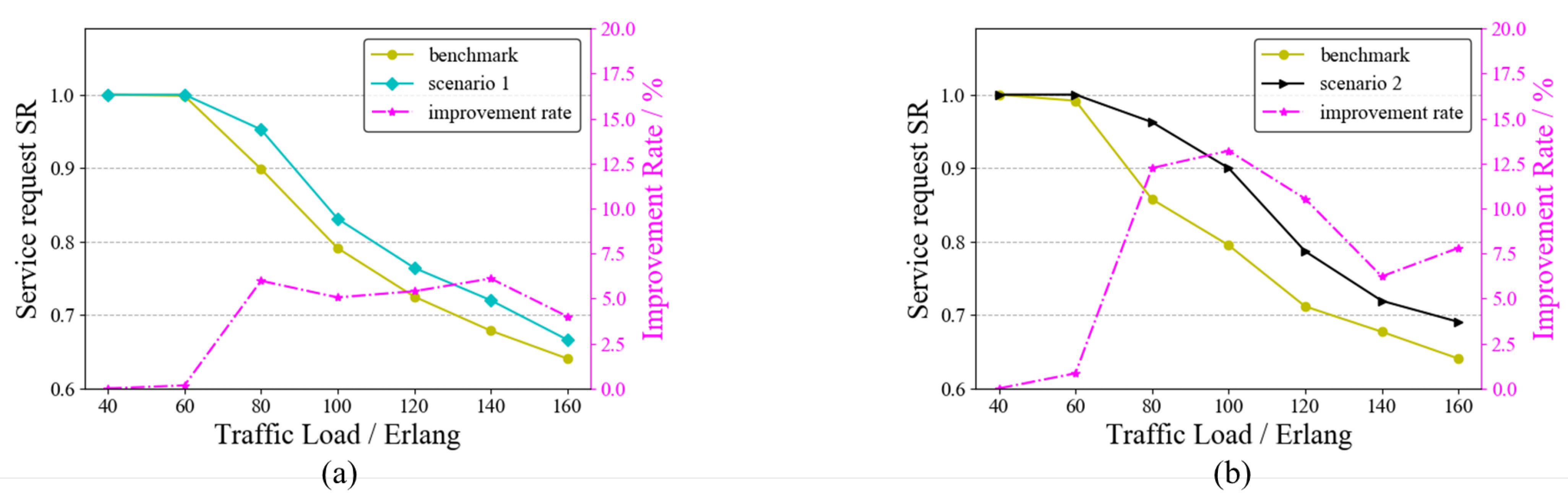
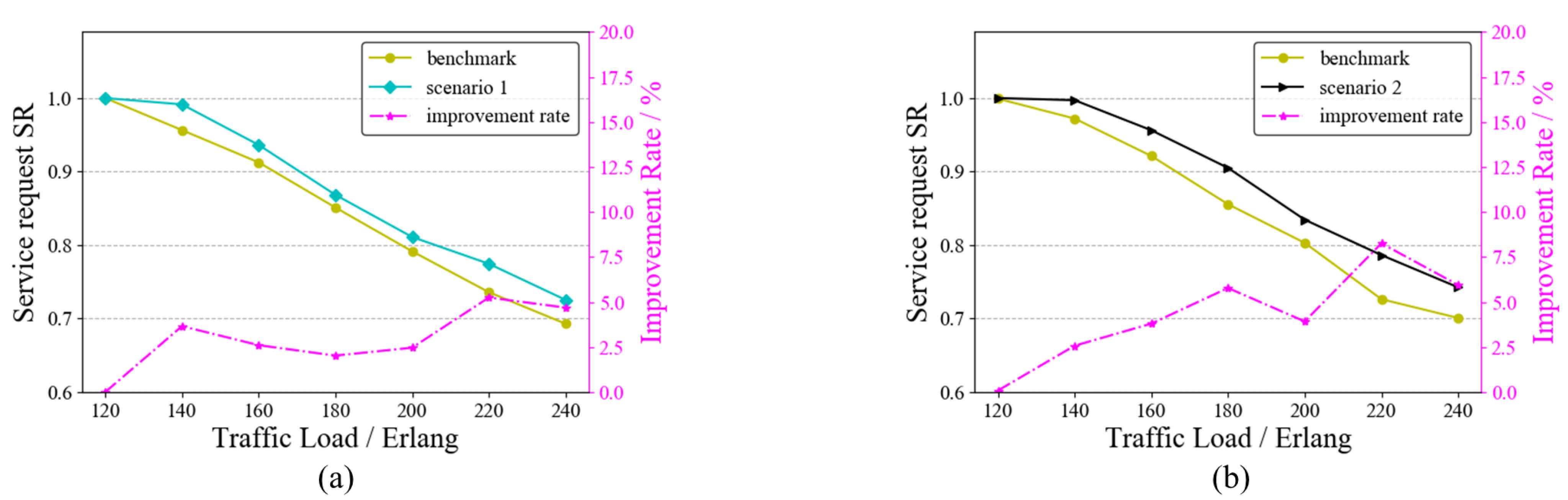
In the service request model of this paper, there may be one or more services arriving at each moment. Multiple requests arriving at one moment may lead to wavelength conflicts. To test the ability of the RAWC algorithm to solve the wavelength conflict problem, we set up two scenarios: ➀ Scenario 1: there are four moments with multiple service requests arriving at the same time; ➁ Scenario 2: there are eight moments with multiple service requests arriving at the same time. As a comparison, both the benchmark algorithm and the RAWC algorithm were applied to these two scenarios, where the benchmark algorithm is RA and no competition for wavelength resources is considered. Figure 9 and Figure 10 demonstrate the results of the two algorithms on the six-node network topology and the NSFNET topology, respectively. The vertical coordinates on the right side indicate the percentage improvement in the RAWC algorithm in SR compared with the benchmark scheme under each scenario. As shown in Figure 9a,b, the RAWC algorithm (cyan line in Figure 9a and black line in Figure 9b) has a higher SR than the benchmark algorithm (yellow line in all Figures) under both scenario 1 and scenario 2. In addition, the RAWC algorithm under scenario 2 has a higher improvement over the benchmark algorithm for the same traffic load compared to scenario 1. Under scenario 1, the improvement rate is up to 6% at a traffic load of 140 Erlang; under scenario 2, the improvement rate is up to 13% at a traffic load of 100 Erlang. The reason is that there is a higher number of multiple services under scenario 2, and the RAWC algorithm can better avoid the path with more wavelength conflicts to meet the transmission requirements of more services than the benchmark algorithm. Figure 10a,b show the comparison results of the two schemes on NSFNET under scenario 1 and scenario 2, respectively. It should be noted that the simulation results on NSFNET topology are similar to the six-node network topology, except for some differences in performance improvement. On NSFNET topology, the maximum SR improvement in the RAWC scheme is no more than 10%, which is related to the network topology itself. To summarize, for the problem of multi-service request arrival, we can effectively improve the network performance by considering wavelength conflicts in the dynamic routing scheme.
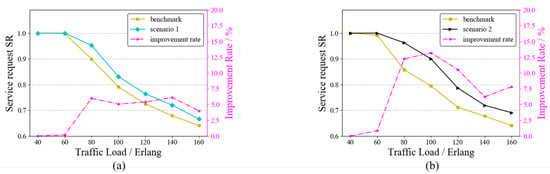
Figure 9.
SR of the RAWC algorithm under different scenarios on the six-node network topology. (a) Scenario 1; (b) Scenario 2.
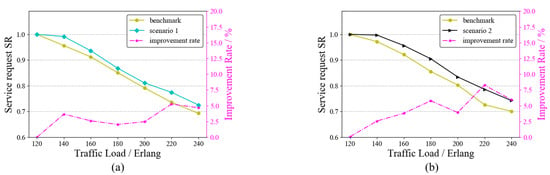
Figure 10.
SR of the RAWC algorithm under different scenarios on NSFNET topology. (a) Scenario 1; (b) Scenario 2.
8. Open Discussion and Future Outlook
In this work, we attempted to investigate the resource conflict problem in the practical application scenario of QKDON and present a model to solve the problem. Our results validate the feasibility of the model. Nevertheless, some assumptions are made in this model, such as the initial number of wavelengths and keys and the service traffic. We aim to consider the impact of QKD on the network comprehensively. We discuss several issues which will be explored in future work, below.
- Allocation of multiple network resources: The routing scheme proposed in this paper only considers the allocation of the wavelength and key resources. Based on the use of WDM technology to construct QKDON, TDM and SDM technologies further improve resource utilization and transmission capacity. Therefore, the introduction of the above two techniques and the allocation of time slots and fiber resources can be considered in future research.
- Survivability of QKDON: With the development of QKD technology, the survivability issues of QKDON have also received extensive attention. Actually, due to factors such as natural disasters or man-made damage, link failure will inevitably occur. The study of the survivability of QKDON is of great importance for the practicality of QKD. Survivability involves two aspects: protection and recovery. Different from classical optical networks, the failure of QKDON will make it impossible to generate quantum keys. Therefore, how to protect the quantum channel in the network and recover the service transmission in time after the failure is an important research topic.
- Applicability of QKD and other encryption methods: Post-quantum cryptography (PQC) is another secure encryption method that can be used to resist quantum computing in addition to QKD. QKD solves the key distribution problem, while PQC studies the security of cryptographic algorithms in quantum environments. QKD and PQC differ in terms of practical conditions and application scenarios. Assessing the applicability of QKD and PQC for different security requirements is a worthwhile research topic in the network. In addition, we need to compare the costs of deploying QKD devices and PQC in different security-demanding circumstances.
9. Conclusions
In this paper, a routing scheme for QKD optical networks (QKDON) is described. In QKDON with limited resources, multiple services arriving at the same time may lead to wavelength conflicts. By introducing the wavelength conflict mechanism and considering the change in network resources, the RAWC routing scheme is presented to assign keys and wavelengths and select the communication path with the least conflict. The performance of the RAWC algorithm is evaluated under different scenarios on the six-node network topology and the NSFNET topology. Simulation results show that the RAWC algorithm has a higher service request success rate and resource utilization than the benchmark scheme. This means that our scheme is beneficial for load balancing and effectively solves the problem of wavelength competition. In addition, increasing initial resources in the network can ensure the secure transmission of more services. In future work, the allocation of multiple network resources and multiple service requirements will be further investigated.
Author Contributions
Conceptualization, T.Z.; methodology, T.Z., X.F. and Q.N.; software, T.Z. and B.D.; validation, T.Z.; formal analysis, T.Z.; investigation, T.Z.; resources, B.G.; data curation, T.Z.; writing—original draft preparation, T.Z.; writing—review and editing, T.Z., X.F. and Q.N.; visualization, T.Z.; supervision, B.G.; funding acquisition, B.G. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Key-Area Research and Development Program of Guangdong Province (Grant No. 2018B030325002).
Institutional Review Board Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors would like to thank the reviewers for their valuable comments and suggestions.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Winzer, P.J. Scaling optical fiber networks: Challenges and solutions. Opt. Photonics News 2015, 26, 28–35. [Google Scholar] [CrossRef]
- Skorin-Kapov, N.; Furdek, M.; Zsigmond, S.; Wosinska, L. Physical-layer security in evolving optical networks. IEEE Commun. Mag. 2016, 54, 110–117. [Google Scholar] [CrossRef]
- Smith, K.T.; Jones, A.; Johnson, L.; Smith, L.M. Examination of cybercrime and its effects on corporate stock value. J. Inf. Commun. Ethics Soc. 2019, 17, 42–60. [Google Scholar] [CrossRef]
- Hallman, R.; Bryan, J.; Palavicini, G.; Divita, J.; Romero-Mariona, J. IoDDoS-the internet of distributed denial of sevice attacks. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security, Porto, Portugal, 24–26 April 2017; SCITEPRESS: Setúbal, Portugal, 2017; pp. 47–58. [Google Scholar]
- Connolly, L.Y.; Wall, D.S. The rise of crypto-ransomware in a changing cybercrime landscape: Taxonomising countermeasures. Comput. Secur. 2019, 87, 101568. [Google Scholar] [CrossRef]
- Desmedt, Y.; Quisquater, J.J. Public-key systems based on the difficulty of tampering (is there a difference between DES and RSA?). In Proceedings of the Advances in Cryptology—CRYPTO’86, Santa Barbara, CA, USA, 1986; Proceedings 6. Springer: Berlin/Heidelberg, Germany, 1986; pp. 111–117. [Google Scholar]
- Goldwasser, S.; Tauman Kalai, Y. Cryptographic assumptions: A position paper. In Proceedings of the Theory of Cryptography: 13th International Conference, TCC 2016-A, Tel Aviv, Israel, 10–13 January 2016; Proceedings, Part I 13. Springer: Berlin/Heidelberg, Germany, 2016; pp. 505–522. [Google Scholar]
- Zhong, H.S.; Wang, H.; Deng, Y.H.; Chen, M.C.; Peng, L.C.; Luo, Y.H.; Qin, J.; Wu, D.; Ding, X.; Hu, Y.; et al. Quantum computational advantage using photons. Science 2020, 370, 1460–1463. [Google Scholar] [CrossRef]
- Fisher, K.A.; Broadbent, A.; Shalm, L.; Yan, Z.; Lavoie, J.; Prevedel, R.; Jennewein, T.; Resch, K.J. Quantum computing on encrypted data. Nat. Commun. 2014, 5, 3074. [Google Scholar] [CrossRef]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the IEEE 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Moody, D. Post-Quantum Cryptography Standardization: Announcement and outline of NIST’s Call for Submissions. In Proceedings of the International Conference on Post-Quantum Cryptography-PQCrypto, Fukuoka, Japan, 24–26 February 2016. [Google Scholar]
- Bennett, C.H. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Bangalore, India, 9–12 December 1984. [Google Scholar]
- Sebastian, B.C.; Cenar, U.A. Advantage of Using Elliptic Curve Cryptography in SSL/TLS; Department of Computer Science University of California Santa Barbara, cs 290G Fall Term: Santa Barbara, CA, USA, 2015. [Google Scholar]
- Gupta, K.; Silakari, S. Ecc over rsa for asymmetric encryption: A review. Int. J. Comput. Sci. Issues (IJCSI) 2011, 8, 370. [Google Scholar]
- Xie, J.; Basu, K.; Gaj, K.; Guin, U. Special session: The recent advance in hardware implementation of post-quantum cryptography. In Proceedings of the 2020 IEEE 38th VLSI Test Symposium (VTS), San Diego, CA, USA, 5–8 April 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–10. [Google Scholar]
- Schamberger, T.; Renner, J.; Sigl, G.; Wachter-Zeh, A. A power side-channel attack on the CCA2-secure HQC KEM. In Proceedings of the Smart Card Research and Advanced Applications: 19th International Conference, CARDIS 2020, Virtual Event, 18–19 November 2020; Revised Selected Papers 19. Springer: Cham, Switzerland, 2021; pp. 119–134. [Google Scholar]
- Simmons, P. Security through amnesia: A software-based solution to the cold boot attack on disk encryption. In Proceedings of the 27th Annual Computer Security Applications Conference, Orlando, FL, USA, 5–9 December 2011; pp. 73–82. [Google Scholar]
- Kocher, P.C. Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems. In Proceedings of the Advances in Cryptology—CRYPTO’96: 16th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 1996; Proceedings 16. Springer: Berlin/Heidelberg, Germany, 1996; pp. 104–113. [Google Scholar]
- Abdulgadir, A.; Mohajerani, K.; Dang, V.B.; Kaps, J.P.; Gaj, K. A Lightweight Implementation of Saber Resistant Against Side-Channel Attacks. In Proceedings of the Progress in Cryptology–INDOCRYPT 2021: 22nd International Conference on Cryptology in India, Jaipur, India, 12–15 December 2021; Proceedings 22. Springer: Cham, Switzerland, 2021; pp. 224–245. [Google Scholar]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Lo, H.K.; Chau, H.F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 1999, 283, 2050–2056. [Google Scholar] [CrossRef]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145. [Google Scholar] [CrossRef]
- Wootters, W.K.; Zurek, W.H. A single quantum cannot be cloned. Nature 1982, 299, 802–803. [Google Scholar] [CrossRef]
- Runser, R.J.; Chapuran, T.; Toliver, P.; Goodman, M.; Jackel, J.; Nweke, N.; McNown, S.; Hughes, R.; Peterson, C.; McCabe, K.; et al. Demonstration of 1. In 3 μm quantum key distribution (QKD) compatibility with 1.5 μm metropolitan wavelength division multiplexed (WDM) systems. In Proceedings of the Optical Fiber Communication Conference, Anaheim, CA, USA, 6–11 March 2005; Optica Publishing Group: Washington, DC, USA, 2005; p. OWI2. [Google Scholar]
- Townsend, P.D. Simultaneous quantum cryptographic key distribution and conventional data transmission over installed fibre using wavelength-division multiplexing. Electron. Lett. 1997, 33, 188–190. [Google Scholar] [CrossRef]
- Qi, B.; Zhu, W.; Qian, L.; Lo, H.K. Feasibility of quantum key distribution through a dense wavelength division multiplexing network. New J. Phys. 2010, 12, 103042. [Google Scholar] [CrossRef]
- Peters, N.; Toliver, P.; Chapuran, T.; Runser, R.; McNown, S.; Peterson, C.; Rosenberg, D.; Dallmann, N.; Hughes, R.; McCabe, K.; et al. Dense wavelength multiplexing of 1550 nm QKD with strong classical channels in reconfigurable networking environments. New J. Phys. 2009, 11, 045012. [Google Scholar] [CrossRef]
- Wang, L.J.; Zou, K.H.; Sun, W.; Mao, Y.; Zhu, Y.X.; Yin, H.L.; Chen, Q.; Zhao, Y.; Zhang, F.; Chen, T.Y.; et al. Long-distance copropagation of quantum key distribution and terabit classical optical data channels. Phys. Rev. A 2017, 95, 012301. [Google Scholar] [CrossRef]
- Aguado, A.; Hugues-Salas, E.; Haigh, P.A.; Marhuenda, J.; Price, A.B.; Sibson, P.; Kennard, J.E.; Erven, C.; Rarity, J.G.; Thompson, M.G.; et al. Secure NFV orchestration over an SDN-controlled optical network with time-shared quantum key distribution resources. J. Light. Technol. 2017, 35, 1357–1362. [Google Scholar] [CrossRef]
- Yu, X.; Li, S.; Zhao, Y.; Cao, Y.; Nag, A.; Zhang, J. Routing, core and wavelength allocation in multi-core-fiber-based quantum-key-distribution-enabled optical networks. IEEE Access 2021, 9, 99842–99852. [Google Scholar] [CrossRef]
- Thyagaturu, A.S.; Mercian, A.; McGarry, M.P.; Reisslein, M.; Kellerer, W. Software defined optical networks (SDONs): A comprehensive survey. IEEE Commun. Surv. Tutor. 2016, 18, 2738–2786. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Colman-Meixner, C.; Yu, X.; Zhang, J. Key on demand (KoD) for software-defined optical networks secured by quantum key distribution (QKD). Opt. Express 2017, 25, 26453–26467. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Yu, X.; Wu, Y. Resource assignment strategy in optical networks integrated with quantum key distribution. J. Opt. Commun. Netw. 2017, 9, 995–1004. [Google Scholar] [CrossRef]
- Wang, H.; Zhao, Y.; Tornatore, M.; Yu, X.; Zhang, J. Dynamic secret-key provisioning in quantum-secured passive optical networks (PONs). Opt. Express 2021, 29, 1578–1596. [Google Scholar] [CrossRef] [PubMed]
- Chen, L.; Chen, Q.; Zhao, M.; Chen, J.; Liu, S.; Zhao, Y. DDKA-QKDN: Dynamic On-Demand Key Allocation Scheme for Quantum Internet of Things Secured by QKD Network. Entropy 2022, 24, 149. [Google Scholar] [CrossRef] [PubMed]
- Chen, L.Q.; Zhao, M.N.; Yu, K.L.; Tu, T.Y.; Zhao, Y.L.; Wang, Y.C. ADA-QKDN: A new quantum key distribution network routing scheme based on application demand adaptation. Quantum Inf. Process. 2021, 20, 1–22. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Yin, H.L.; Chen, T.Y.; Yu, Z.W.; Liu, H.; You, L.X.; Zhou, Y.H.; Chen, S.J.; Mao, Y.; Huang, M.Q.; Zhang, W.J.; et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 2016, 117, 190501. [Google Scholar] [CrossRef]
- Liu, H.; Wang, W.; Wei, K.; Fang, X.T.; Li, L.; Liu, N.L.; Liang, H.; Zhang, S.J.; Zhang, W.; Li, H.; et al. Experimental demonstration of high-rate measurement-device-independent quantum key distribution over asymmetric channels. Phys. Rev. Lett. 2019, 122, 160501. [Google Scholar] [CrossRef]
- Cao, Y.; Li, Y.H.; Yang, K.X.; Jiang, Y.F.; Li, S.L.; Hu, X.L.; Abulizi, M.; Li, C.L.; Zhang, W.; Sun, Q.C.; et al. Long-distance free-space measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2020, 125, 260503. [Google Scholar] [CrossRef] [PubMed]
- Hua, X.; Hu, M.; Guo, B. Multi-User Measurement-Device-Independent Quantum Key Distribution Based on GHZ Entangled State. Entropy 2022, 24, 841. [Google Scholar] [CrossRef] [PubMed]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef]
- Minder, M.; Pittaluga, M.; Roberts, G.L.; Lucamarini, M.; Dynes, J.; Yuan, Z.; Shields, A.J. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photonics 2019, 13, 334–338. [Google Scholar] [CrossRef]
- Wang, S.; Yin, Z.Q.; He, D.Y.; Chen, W.; Wang, R.Q.; Ye, P.; Zhou, Y.; Fan-Yuan, G.J.; Wang, F.X.; Chen, W.; et al. Twin-field quantum key distribution over 830-km fibre. Nat. Photonics 2022, 16, 154–161. [Google Scholar] [CrossRef]
- Van Meter, R.; Touch, J. Designing quantum repeater networks. IEEE Commun. Mag. 2013, 51, 64–71. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Wu, Y.; Yu, X.; Zhang, J. Time-scheduled quantum key distribution (QKD) over WDM networks. J. Light. Technol. 2018, 36, 3382–3395. [Google Scholar] [CrossRef]
- Nweke, N.; Toliver, P.; Runser, R.; McNown, S.; Khurgin, J.; Chapuran, T.; Goodman, M.; Hughes, R.; Peterson, C.; McCabe, K.; et al. Experimental characterization of the separation between wavelength-multiplexed quantum and classical communication channels. Appl. Phys. Lett. 2005, 87, 174103. [Google Scholar] [CrossRef]
- Lucamarini, M.; Patel, K.; Dynes, J.; Fröhlich, B.; Sharpe, A.; Dixon, A.; Yuan, Z.; Penty, R.; Shields, A. Efficient decoy-state quantum key distribution with quantified security. Opt. Express 2013, 21, 24550–24565. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).