Graphic Groups, Graph Homomorphisms, and Graphic Group Lattices in Asymmetric Topology Cryptography
Abstract
1. Introduction
1.1. Research Background
1.2. Basic Concepts and Definitions
2. Graphic Groups
2.1. Mixed Graphic Groups
2.2. Some Mixed Graphic Groups
2.2.1. Twin Mixed Graphic Groups
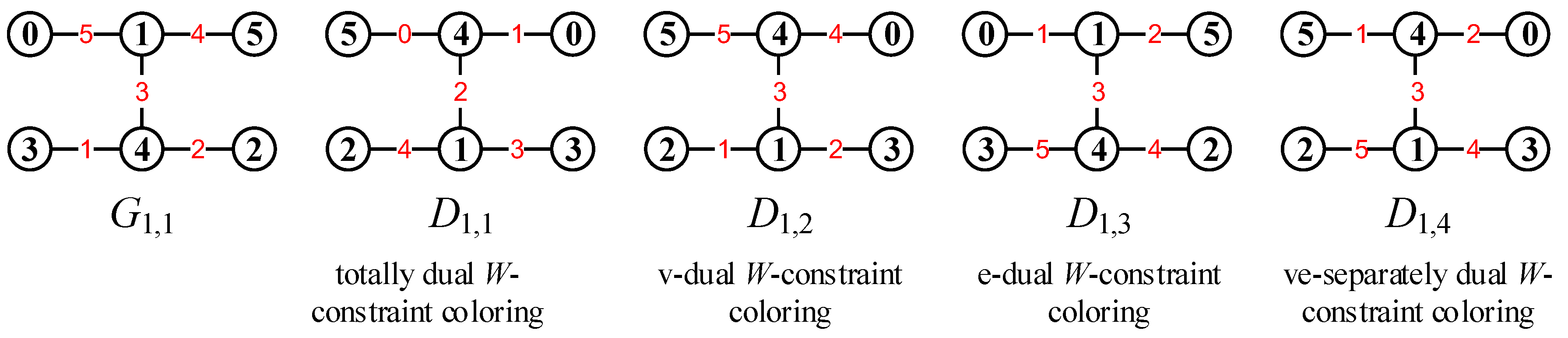
2.2.2. Dual Mixed Graphic Groups
2.2.3. Matching Mixed Graphic Groups
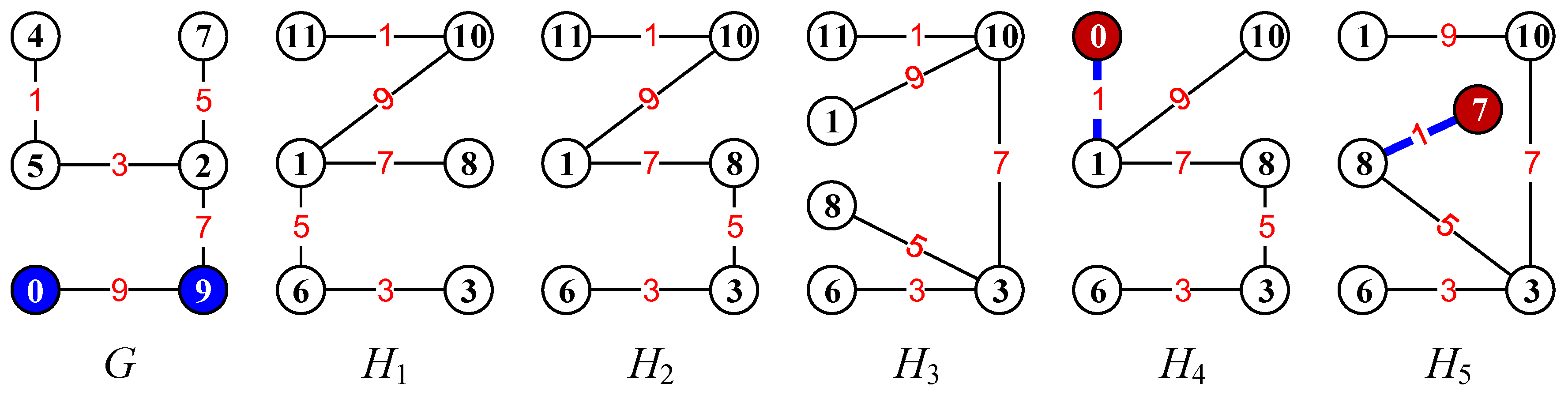
2.3. Infinite Mixed Graphic Groups and Their Homomorphisms
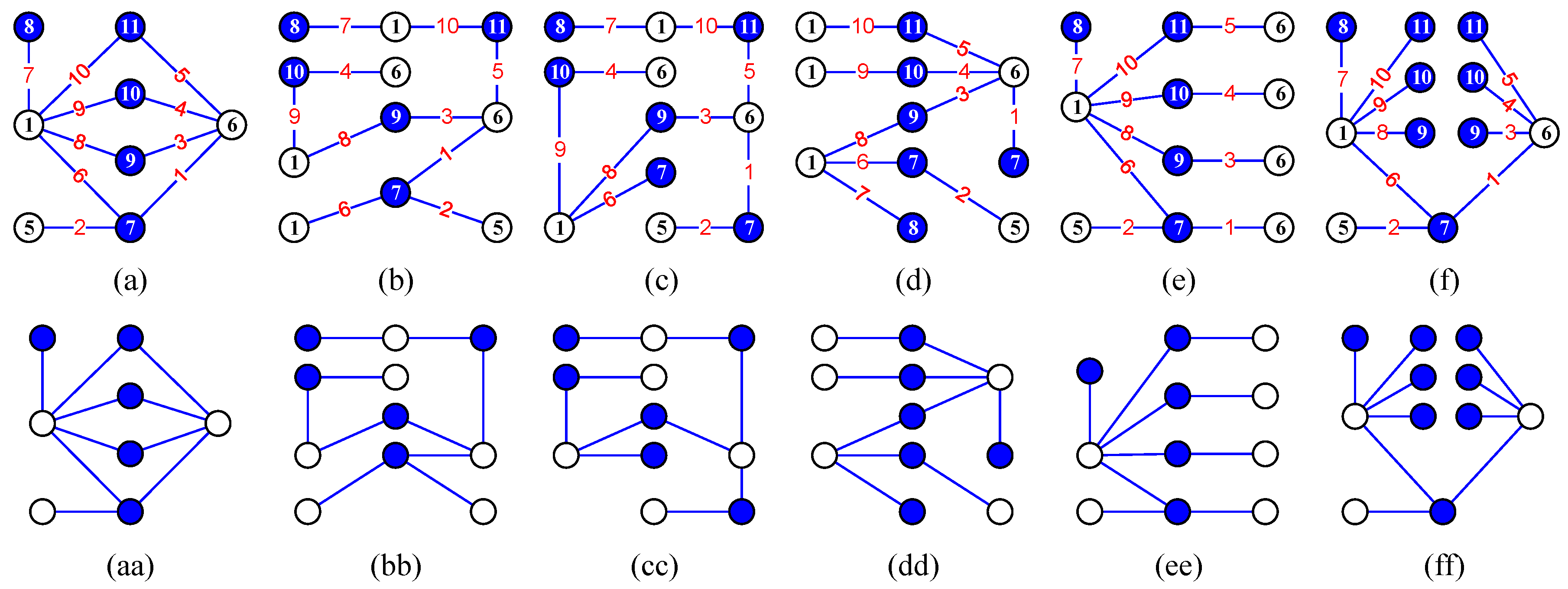
3. Graphic Lattices
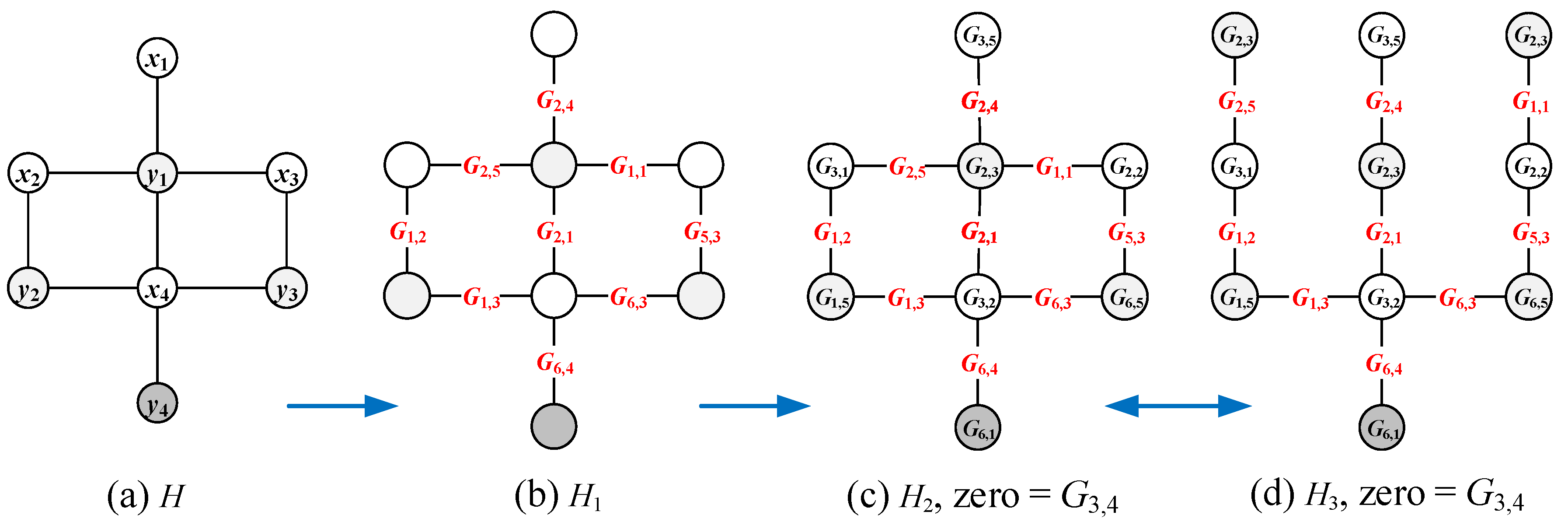
3.1. Mixed Graphic B-Group Lattices
3.2. Graphic Lattices Made by Graph Matchings
3.2.1. Traditional Graph and Its Complement
3.2.2. G-Complementary
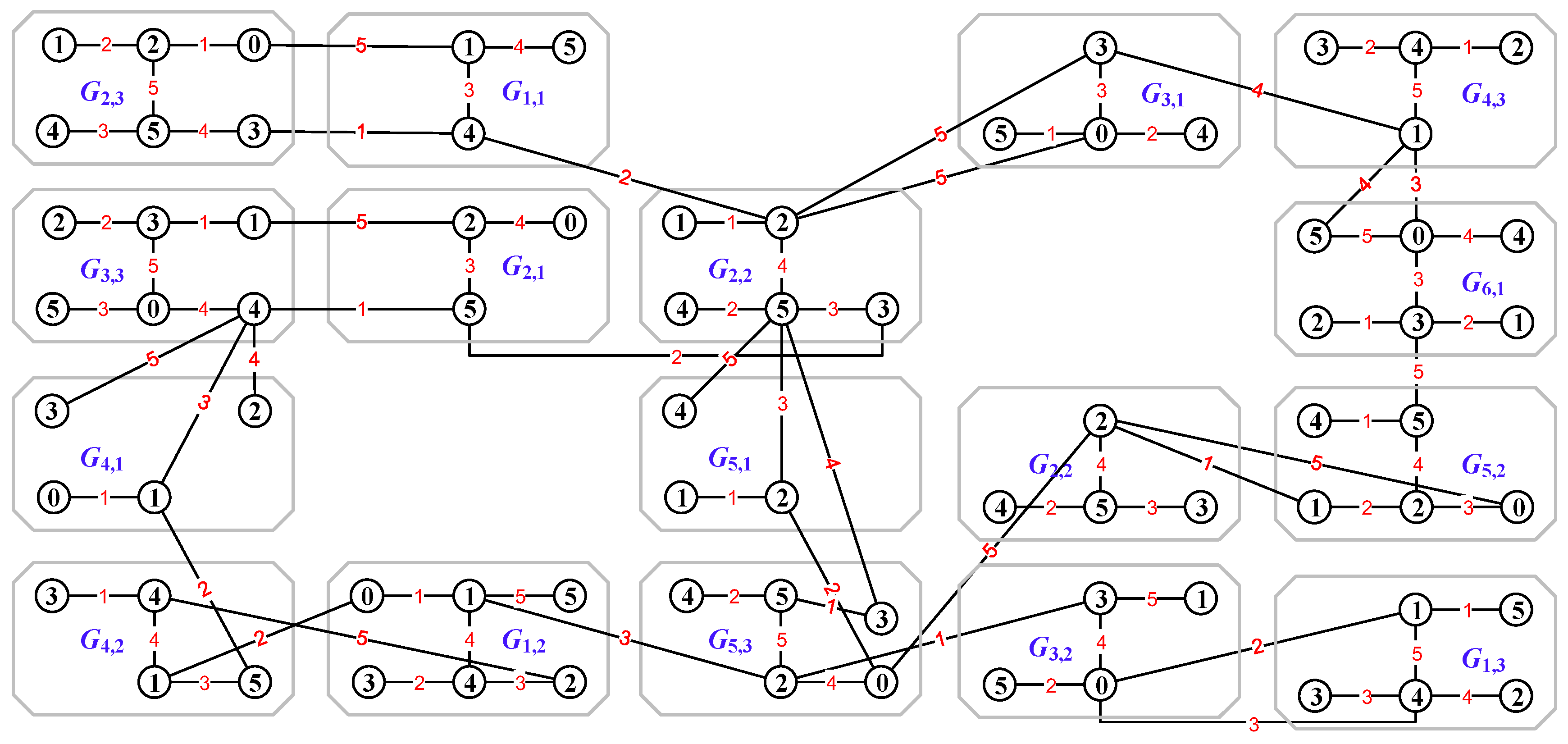
4. Encrypting Networks in Whole
4.1. Mixed Graphic Group Colorings in Encrypting Networks
4.2. Encrypting Tree-like Networks
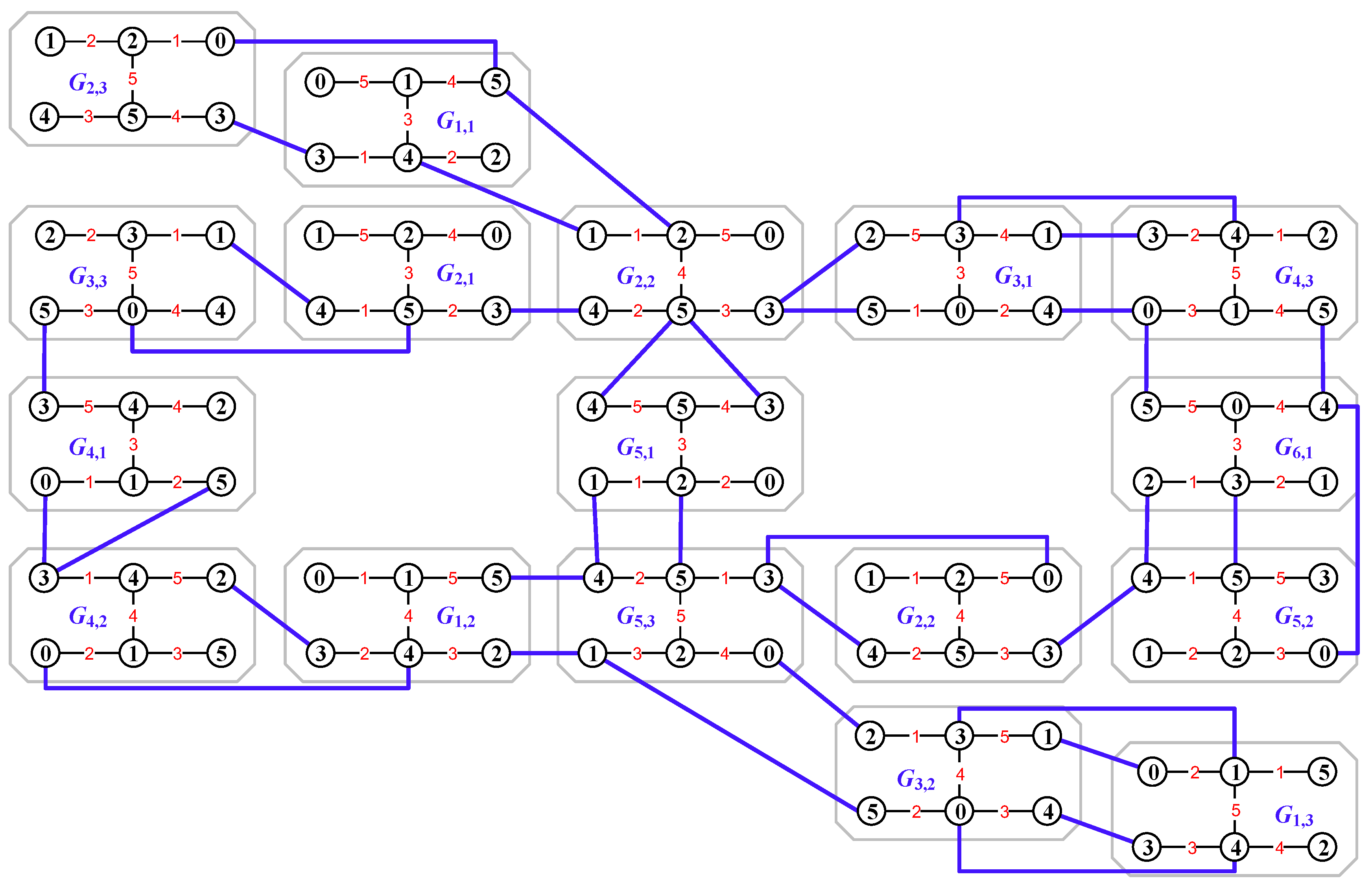
4.3. Graphic Lattices for the Encryption of Dynamic Networks
5. Summary
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Wang, X.; Liu, M. Survey of lattice-based cryptography. J. Cryptologic Res. 2014, 1, 13–27. (In Chinese) [Google Scholar]
- Anshel, I.; Anshel, M.; Goldfeld, D. An algebraic method for public-key cryptography. Math. Res. Lett. 1999, 6, 287–291. [Google Scholar] [CrossRef]
- Eick, B.; Kahrobaei, D. A new platform for cryptology? arXiv 2004, arXiv:math/0411077v1. [Google Scholar]
- Ostrovsky, R.; Skeith, W.E., III. Communication complexity in algebraic two-party protocols. In Proceedings of the 28th Annual International Cryptology Conference (Advances in Cryptology—CRYPTO 2008), Santa Barbara, CA, USA, 17–21 August 2008; pp. 379–396. [Google Scholar]
- Flores, R.; Kahrobaei, D.; Koberda, T. Algorithmic problems in right-angled Artin groups: Complexity and applications. J. Algebra 2019, 519, 111–129. [Google Scholar] [CrossRef]
- Kahrobaei, D.; Tortora, A.; Tota, M. Multilinear cryptography using nilpotent groups. arXiv 2019, arXiv:1902.08777v2. [Google Scholar]
- Anshel, I.; Atkins, D.; Goldfeld, D.; Gunnells, P.E. WalnutDSA™: A group theoretic digital signature algorithm. Int. J. Comput. Math. Comput. Syst. Theory 2021, 6, 260–284. [Google Scholar] [CrossRef]
- Kahrobaei, D.; Flores, R.; Noce, M. Group-based cryptography in the quantum era. Not. Am. Math. Soc. 2023, 70, 2–13. [Google Scholar] [CrossRef]
- Yao, B.; Sun, H.; Zhao, M.; Li, J.; Yan, G. On coloring/labelling graphical groups for creating new graphical passwords. In Proceedings of the 2017 IEEE 2nd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC 2017), Chengdu, China, 15–17 December 2017; pp. 1371–1375. [Google Scholar]
- Sun, H.; Zhang, X.; Zhao, M.; Yao, B. New algebraic groups produced by graphical passwords based on colorings and labellings. In Proceedings of the MATEC Web Conference (ICMITE 2017), Chengdu, China, 16–17 December 2017; Volume 139, p. 00152. [Google Scholar]
- Yao, B.; Mu, Y.; Sun, H.; Zhang, X.; Wang, H.; Su, J.; Ma, F. Algebraic groups for construction of topological graphic passwords in cryptography. In Proceedings of the 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC 2018), Chongqing, China, 12–14 October 2018; pp. 2211–2216. [Google Scholar]
- Yao, B.; Sun, H.; Su, J.; Wang, H.; Zhao, M. Various matchings of graphic groups for graphic lattices in topological coding. In Proceedings of the ICIBA 2020, Chongqing China, 6–8 November 2020; pp. 1–6. [Google Scholar]
- Zhao, M.; Yao, M.; Zhang, X.; Sun, Y.; Yao, B. Coding graphic groups for network security. In Proceedings of the IEEE 4th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC 2019), Chengdu, China, 20–22 December 2019; pp. 2118–2122. [Google Scholar]
- Zhao, M.; Yao, M.; Yao, B. On modular-2q graphic groups of topological coding for graphic passwords. In Proceedings of the IEEE International Conference on Information Technology, Big Data and Artificial Intelligence (ICIBA), Chongqing, China, 6–8 November 2020; pp. 458–462. [Google Scholar]
- Wang, H.; Su, J.; Yao, B. Graphic groups towards cryptographic systems resisting classical and quantum computers. In Proceedings of the IEEE 5th Information Technology and Mechatronics Engineering Conference (ITOEC), Chongqing, China, 12–14 June 2020. [Google Scholar]
- Yao, B. Graphic lattices and matrix lattices of topological coding. arXiv 2020, arXiv:2005.03937v1. [Google Scholar]
- Bondy, J.A.; Murty, U.S.R. Graph Theory; Springer: London, UK, 2008. [Google Scholar]
- Bondy, J.A.; Murty, U.S.R. Graph Theory with Application; MacMillan: London, UK, 1976. [Google Scholar]
- Bang-Jensen, J.; Gutin, G. Digraphs: Theory, Algorithms and Applications; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Gallian, J.A. A dynamic survey of graph labeling. Electron. J. Comb. 2022. [Google Scholar] [CrossRef] [PubMed]
- Yao, B.; Wang, H. Recent colorings and labelings in topological coding. arXiv 2021, arXiv:2106.15254v1. [Google Scholar]
- Yao, B.; Zhang, X.; Sun, H.; Su, J.; Ma, F.; Wang, H. Parameterized colorings and labellings of graphs in topological coding. arXiv 2022, arXiv:2207.03381v1. [Google Scholar]
- Yao, B.; Sun, H.; Zhang, X.; Mu, Y.; Sun, Y.; Wang, H.; Su, J.; Zhang, M.; Yang, S.; Yang, C. Topological graphic passwords and their matchings towards cryptography. arXiv 2018, arXiv:1808.03324v1. [Google Scholar]
- Wang, H.; Xu, J.; Yao, B. Twin odd-graceful trees towards information security. Procedia Comput. Sci. 2017, 107, 15–20. [Google Scholar] [CrossRef]
- Yao, B.; Liu, X.; Yao, M. Connections between labellings of trees. Bull. Iran. Math. Soc. 2017, 43, 275–283. [Google Scholar]
- Harary, F.; Palmer, E.M. Graphical Enumeration; Academic Press: Cambridge, MA, USA, 1973. [Google Scholar]
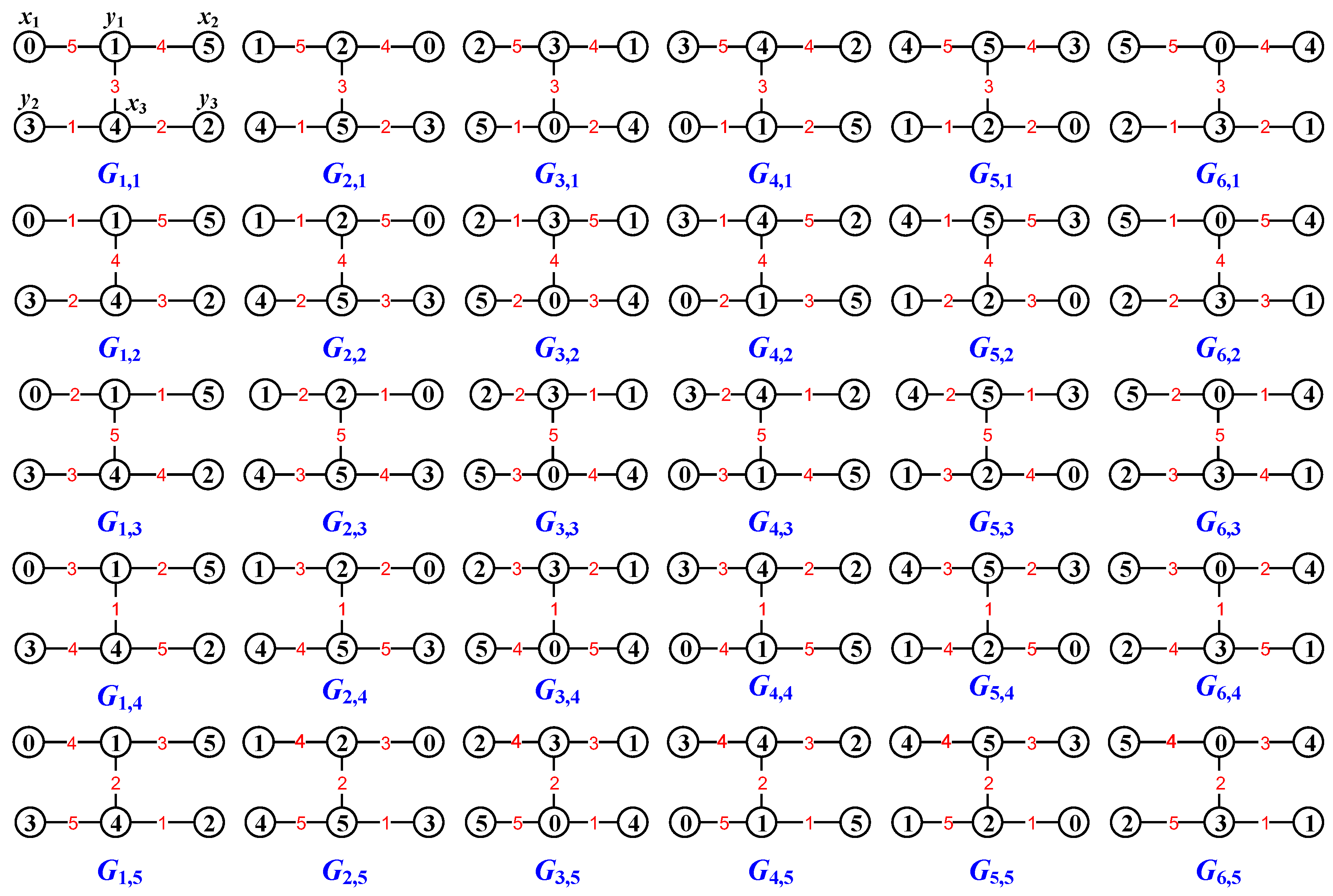

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, M.; Wang, H.; Yao, B. Graphic Groups, Graph Homomorphisms, and Graphic Group Lattices in Asymmetric Topology Cryptography. Entropy 2023, 25, 720. https://doi.org/10.3390/e25050720
Zhao M, Wang H, Yao B. Graphic Groups, Graph Homomorphisms, and Graphic Group Lattices in Asymmetric Topology Cryptography. Entropy. 2023; 25(5):720. https://doi.org/10.3390/e25050720
Chicago/Turabian StyleZhao, Meimei, Hongyu Wang, and Bing Yao. 2023. "Graphic Groups, Graph Homomorphisms, and Graphic Group Lattices in Asymmetric Topology Cryptography" Entropy 25, no. 5: 720. https://doi.org/10.3390/e25050720
APA StyleZhao, M., Wang, H., & Yao, B. (2023). Graphic Groups, Graph Homomorphisms, and Graphic Group Lattices in Asymmetric Topology Cryptography. Entropy, 25(5), 720. https://doi.org/10.3390/e25050720