1. Introduction
Secure multiparty computation (SMC) [
1,
2,
3] is a crucial cryptographic primitive which fits the following description: Assume that there is a function typically specified by a map
and a set of
n parties,
, who want to compute values of this function with respect to their private data. Each party
has its input
and output
, following correspondence
. Our target is to ensure that all parties in a subset
receive correct outputs from others while no information related to the input can be accessed. SMC has raised widespread concerns and has wide applications in electronic voting, cloud computing, online auction, etc.
A typical SMC [
4] application is Private Set Intersection (PSI), which also known as Private Matching (PM). Specifically, PSI permits two parties,
and
, who respectively have a private set
and
. Without disclosing any information that does not belong to this intersection, they seek to find the intersection
. There have been many applications of PSI, such as privacy-preserving data mining [
5], data outsourcing on cloud [
6], location-based privacy-preserving sharing [
7], testing of fully-sequenced human genomes [
8], proximity testing [
9], and other online services [
10].
Due to the extensive and important applications, there have been many suggestions for PSI protocols. In 2004, Freedman et al. [
4] first gave the definition of PSI and presented several PSI protocols by using homomorphic encryption and balanced hashing. Homomorphic encryption was first proposed by Rivest et al. in 1978 [
11]. A new symmetric homomorphic functional encryption using modular multiplications over a hidden ring was proposed [
12]. Then, some PSI protocols were proposed based on classical cryptography [
13,
14,
15,
16]. However, PSI reveals too much private information and it cannot meet the higher privacy requirements in some scenarios. In this case, Private Set Intersection Cardinality (PSI-CA) [
17] was introduced, which can securely determine the size of set intersection and can be used to generate association rules. In [
18], a PSI-CA protocol was the first to achieve security in the standard model under the Quadratic Residuosity QR assumption with linear complexities, which can hide the size of the client’s private set. In [
19], a PSI-CA protocol was proposed, which had linear computation and communication complexities and was the most efficient PSI-CA protocol in previously proposed PSI-CA protocols [
18,
19]. PSI-CA only outputs the intersection cardinality and does not reveal the specific content of the intersection. The security of classical PSI-CA protocols is based on the computational complexity assumptions, which are vulnerable to attack by the quantum algorithms [
20,
21,
22].
On the other hand, scholars began to seek a quantum approach to solving the PSI-CA problem. In [
23], Shi et al. presented two quantum protocols to solve the Oblivious Set-member Decision problem. These protocols can be used to privately compute multi-party set intersection and union in the quantum domain. In [
24], Shi et al. informally gave a definition of PSI first. Then they presented a quantum scheme for PSI based on
n encoded states,
n quantum operators, and
n von Neumann measurements. In [
25], Arpita gave a two-party protocol for computing set intersection securely in the quantum domain in a rational setting, where the players are trying to maximize their utilities. However, PSI reveals too much private personal information in some scenarios. In order to prevent revealing the specific content, Shi et al. proposed some quantum protocols of PSI-CA [
26,
27,
28]. PSI-CA and PSU-CA enable two parties, each with a private set, to jointly compute the cardinality of their intersection or union without disclosing any private information about their respective sets. These protocols are useful in social networks and for privacy-preserving data mining.
In this paper, following the idea in [
26], we propose a PSI-CA protocol based on a quantum homomorphic encryption scheme for the Toffoli gate. With the help of a semi-honest TP, two parties can use this protocol to privately obtain the number of all their private sets’ common elements. When the amount of data is large, two parties, which do not have strong quantum computing capabilities, only prepare and encrypt quantum single-particle states. The role of semi-honest TP is to execute the protocol loyally and record all the results of its intermediate computations. However, the TP cannot learn anything about the private information. In our protocol, the semi-honest third party (TP) can be used to perform Toffoli gate and decryption operations. It will keep a record of all its intermediate results and might try to infer the private inputs from the record. Our protocol is simpler and easier to implement.
This paper is organized as follows: we introduce some correlative preliminaries in
Section 2; we propose a quantum PSI-CA protocol in
Section 3; in
Section 4, we analyze the correctness and security of our protocol and describe the implementation of our protocols on the IBM Quantum Experience platform. A brief discussion and the concluding summary are given in
Section 5.
3. Quantum Private Computation Protocol for Set Intersection Cardinality
We use the definition of PSI-CA [
19]. Suppose that there are two parties, Alice and Bob. They input a private set
and
, respectively.
S is a complete set
and
. After running the PSI-CA protocol with a help of the semi-honest third party, Calvin, Alice and Bob output the cardinality of the intersection of their private sets, i.e.,
, without leaking any information about their sets. The quantum scheme for PSI-CA is described as follows:
(1) Alice and Bob each prepare a
-photon sequence, denoted by
. The first
n particles of
are prepared according to Alice’s and Bob’s private sets
:
The last
particles of
are dummy photons, which are randomly chosen from
.
(2) Alice and Bob work together to find the number of , denoted by , which means how many bits are equal and equal to in the last particles of .
They also permutate using the same permutation regulation . The new sequences are denoted by .
Each of them chooses a sequence,
, where
are randomly chosen from
. Then, she(he) uses the Quantum One-time Pad algorithm (QOTP) [
25] to encrypt the
kth particle of
and get
. The new particles sequence is denoted by
.
Alice (Bob) also inserts some checking particles, which are randomly chosen from , into and sends the new sequence to the third party Calvin.
After that, Alice(Bob) transmits the insert positions and to Calvin using the quantum secure direct communication (QSDC) protocol. QSDC is one of the most important branches of quantum communication and it directly transmits secret messages.
(3) After receiving , Alice, Bob, and Calvin perform the eavesdropping check using the insert positions and the measuring bases of checking particles. If the error rate exceeds the threshold they preset, they abort the scheme. Otherwise, they discard the measured photons in and Calvin gets two sequences .
Calvin prepares a sequence , where is randomly chosen from .
(4) Calvin executes some operations on the
ith quantum bits of
and gets:
Calvin measures using the X basis and compares the measurement result with . He also counts how many quantum bits are different and the number is denoted by . It is obvious that the intersection cardinality of is equal to .
We have to point out that if Alice and Bob apply a gate on each particle of in step(1), the private set union cardinality of is equal to using the PSI-CA quantum protocol.
4. Analysis and Comparison
4.1. Correctness Analysis
In this section, we illustrate the correctness of our protocol.
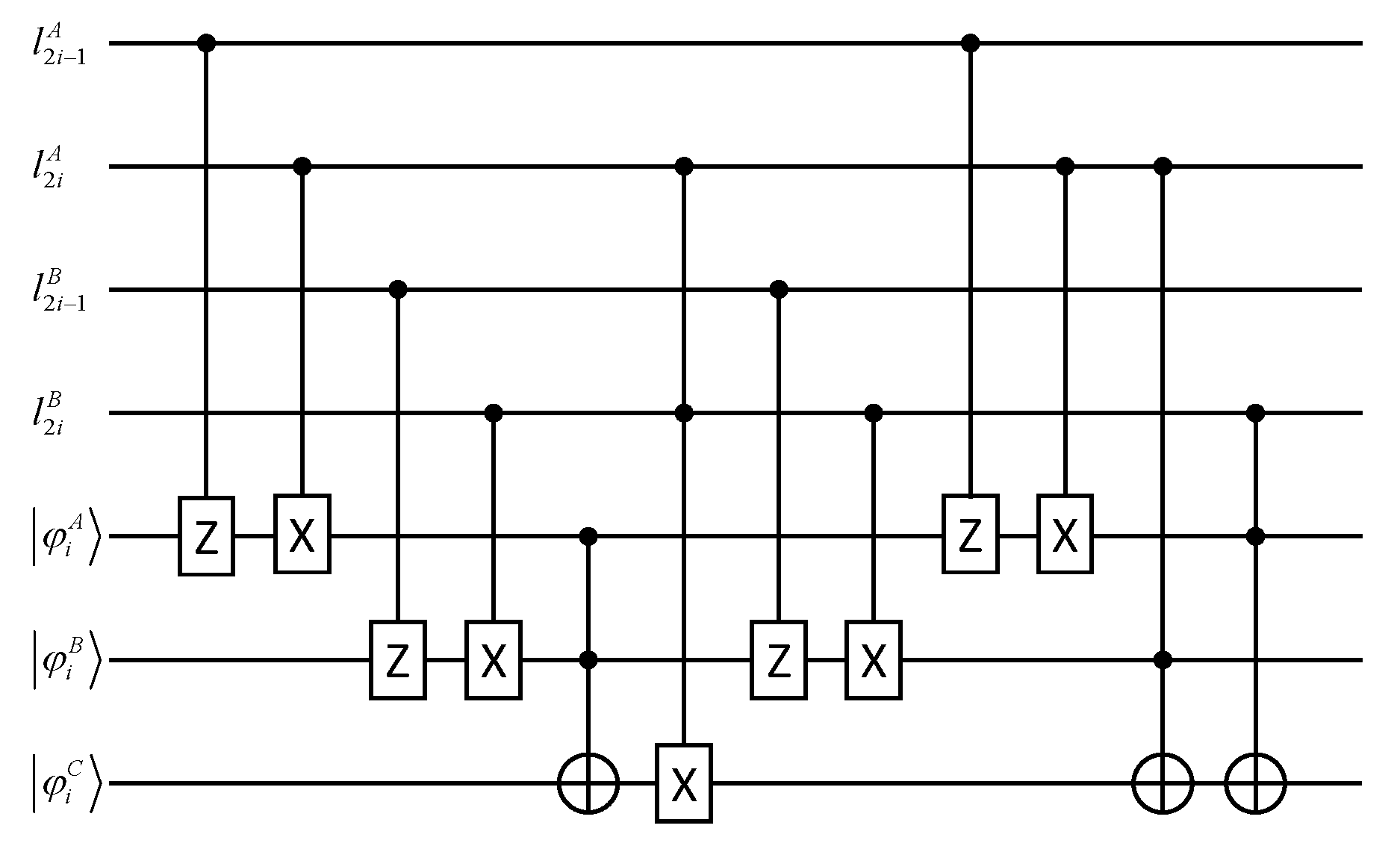
Figure 3 describes the circuit
U used to privately apply the
T gate on
, where
. For
, Alice, Bob and Calvin can use the circuit
U to privately calculate
. If
is reversed, they can determine
.
According to the circuit
U, it can be verified that
According to Equations (7)–(22), we can obtain
Calvin measures . If is different from , we can know . Alice and Bob have a common element in .
Suppose that the private set of Alice is and the private set of Bob is where a complete set is . The photon sequence of Alice is and the photon sequence of Bob is . Calvin prepares a sequence . Alice chooses a sequence and Bob chooses a sequence . Alice, Bob and Calvin perform some operations on using and get . Then they can get and the new photon sequence of Calvin is . Only the third photon in Calvin’s new sequence is different from the third photon of his original sequence . So we can get that Alice and Bob have only one common element in .
4.2. Implementation of Quantum PSI-CA Protocols on IBM Quantum Experience Platform
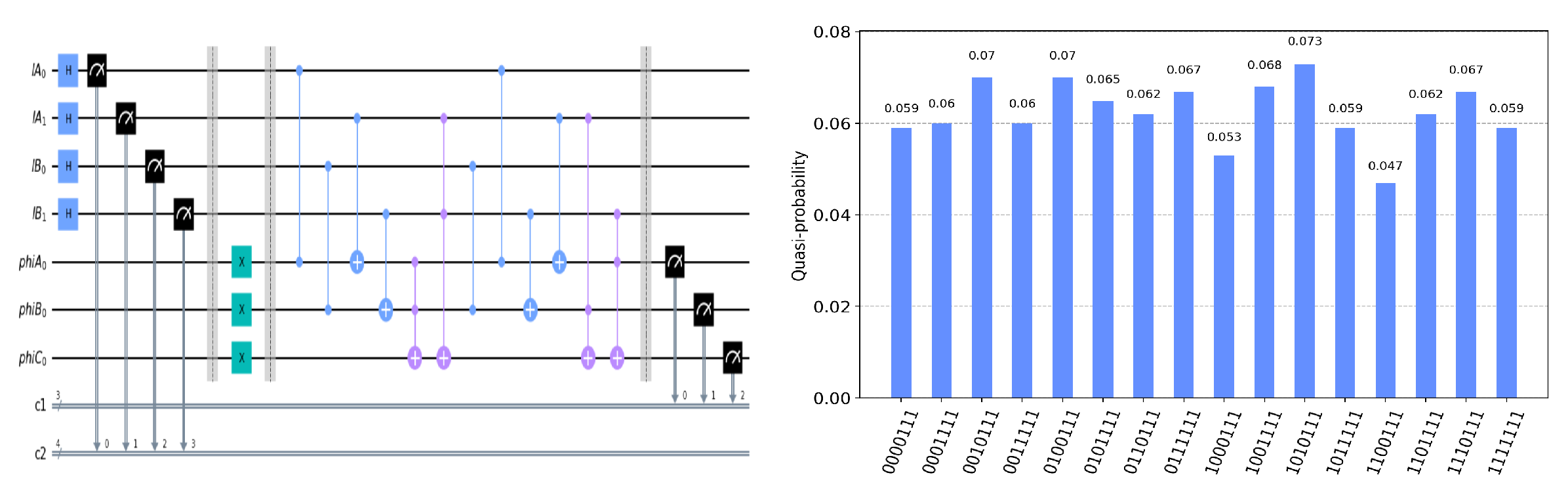
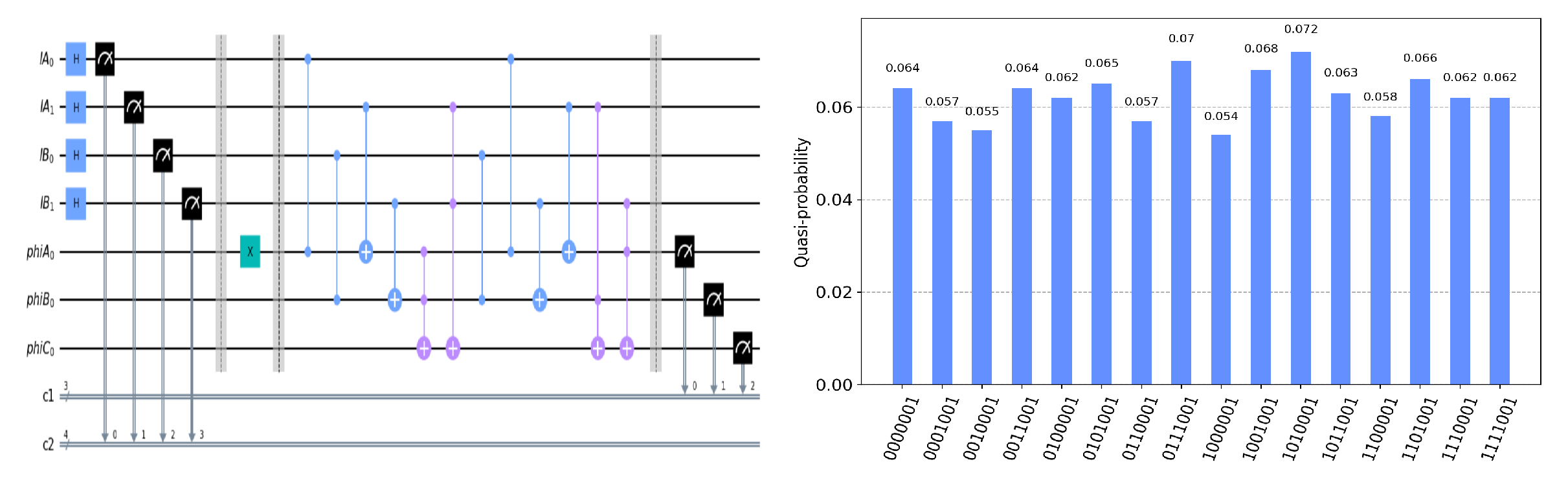
Now, we move forward through a similar approach to experimentally realize our PSI-CA protocol on the IBM Quantum Experience platform. Let us say the two parties, Alice and Bob, have a private set and , respectively, where S is a complete set and . For the encoding procedure, and are encoded into two -particle sequences. Alice, Bob, and Calvin can privately apply the T gate on their corresponding position particles using the IBM Quantum Experience platform. The measuring results of Calvin’s particle are related to the PSI-CA of .
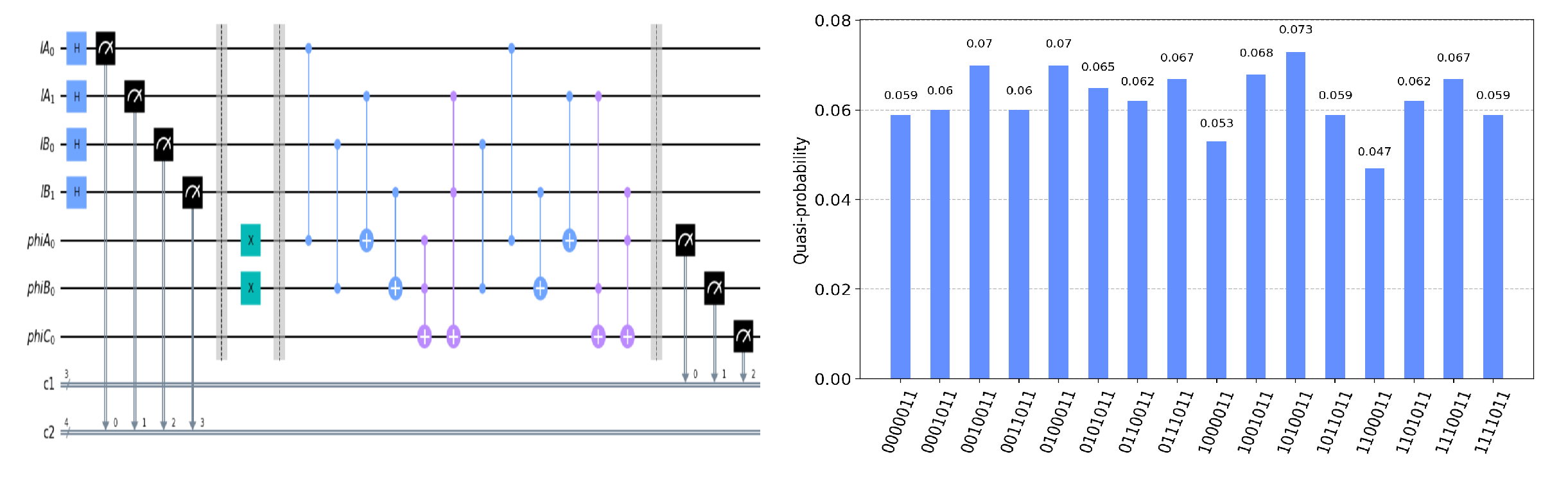
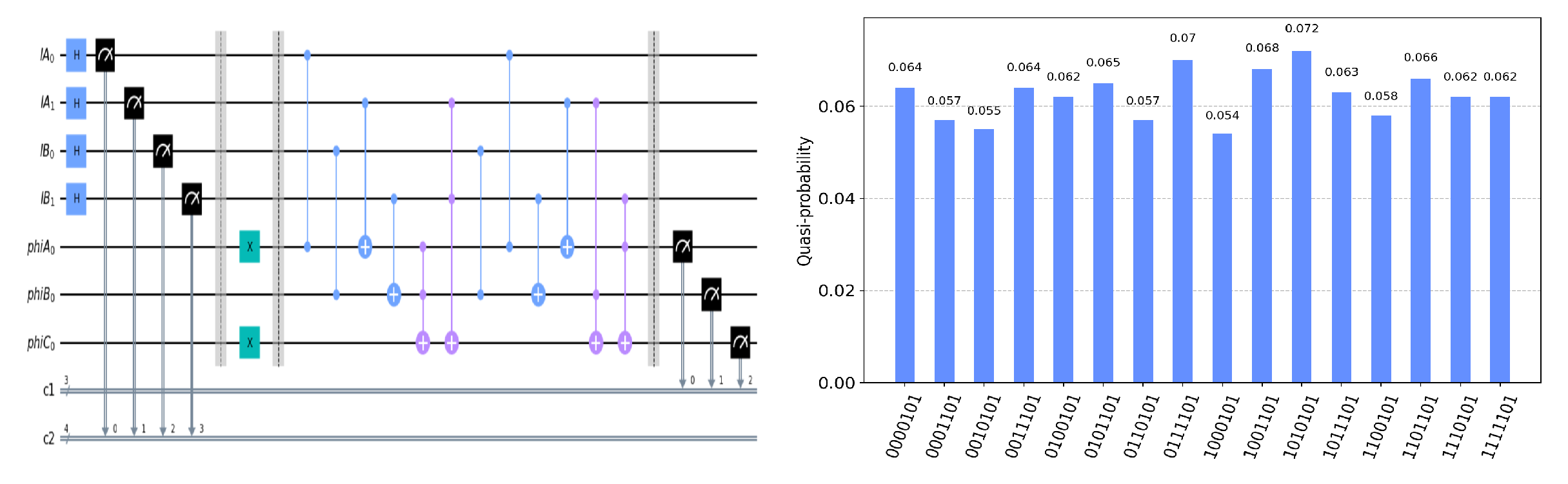
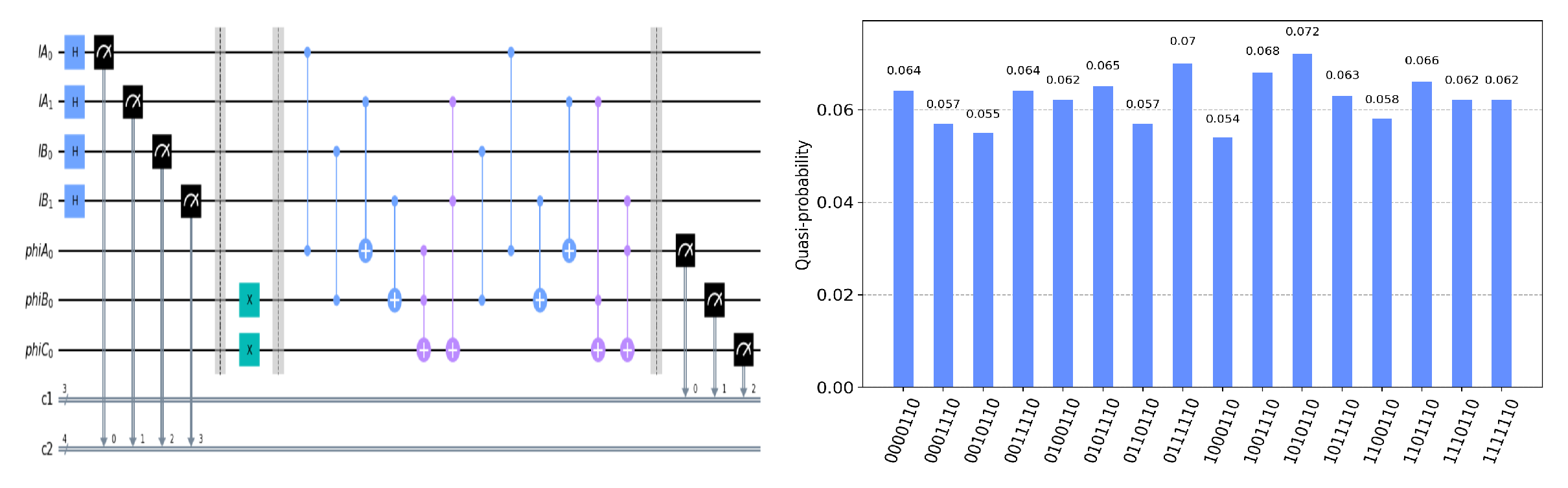
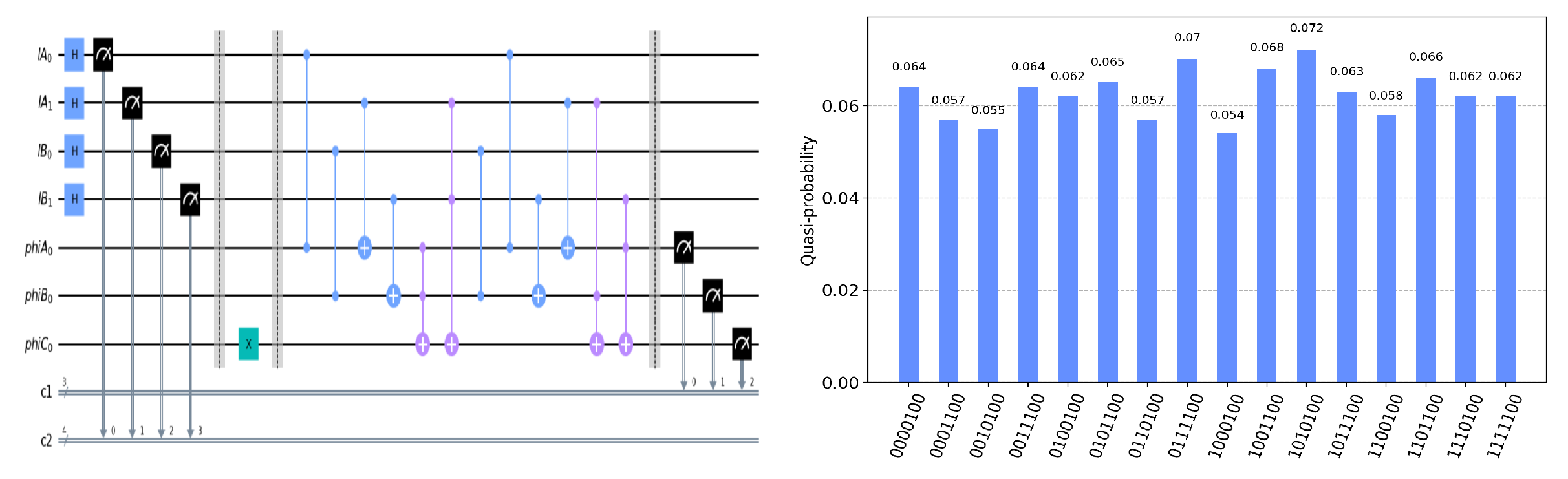
The circuit on the IBM Quantum Experience platform for privately computing for eight cases of
and the experiment results with 1024 shots for eight cases on the quantum circuit are shown in
Figure 4,
Figure 5,
Figure 6,
Figure 7,
Figure 8,
Figure 9,
Figure 10 and
Figure 11. In the experiment results’ figures, the x-axis represents 16 measurement results, and each of them includes the
and the information of
.The y-axis represents the frequency of each measurement result. The first three binary bits in the x-axis correspond to the output of
and the following four binary bits in the x-axis are
.
In
Figure 4,
. Take the measurement results “1101010”, for example, in
Figure 4, the last four bits 1010 represent the measurement results of
, which are used to control the gates in the quantum circuit. The first three bits 110 represent the new measurement result of
after operating the gates in the quantum circuit. From the frequency of each measurement result in
Figure 4, it can be verified that no matter what the
is, the circuit will act as a
T gate on
. Using the same analysis method, we can reach the same conclusion from the frequency of each measurement result in
Figure 5,
Figure 6,
Figure 7,
Figure 8,
Figure 9,
Figure 10 and
Figure 11.
4.3. Security Analysis
In this section, we verify the security of our quantum PSI-CA scheme by analyzing an external outside attack and a participant attack, respectively.
4.3.1. Outside Attacks
In terms of outside attacks, this protocol allows for outside eavesdroppers to attack the quantum channel and obtain Alice and Bob’s particle sequences in step (2). Checking particles are introduced to to defend against it. With several checking particles inserted, the security checking procedure in Step (3) can detect the intercept–resend attack, the measurement–resend attack, the entanglement–measure attack, and the denial-of-service (DOS) attack with a nonzero probability.
In addition to this naive attack, there are some special forms of attack such as the delay photon Trojan horse attack, the invisible photon eavesdropping (IPE) Trojan horse attack, and the photon-number-splitting (PNS) attack, which are also available to outside eavesdroppers. In response to these attacks, we use several defenses. To defeat the delay-photon Trojan horse attack, we can use a photon-number splitter. To defeat the IPE attack, we can insert filters in front of their devices to filter out the photon signal with an illegitimate wavelength. To defeat the PNS attack, we can use the technology of beam splitters to split the sampling signals and judge whether these received photons are single photons or multiple photons. Therefore, the outside attacks are invalid to our protocol.
4.3.2. Participant Attack
Gao et al. proposed the term “participant attack” in Ref. [
29], which has attracted much attention in the cryptanalysis of quantum cryptography. It underlines that malicious user attacks are typically more potent and should be given more consideration. We analyze the possibility that Alice, Bob, and Calvin could use participant attacks to learn knowledge about the private binary strings in our protocol. Since both Alice and Bob’s sequences are sent to Calvin after processing, it is most critical to consider Calvin’s behavior.
In our protocol, Calvin only gets two-particle sequences . Calvin applies the T gate on each sequence in step (3).
According to the definition of information-theoretic security given in
Section 2.3, we can know that the output state of step (2) in our protocol can be described as follows:
These calculations indicate that all the states obtained by Calvin are just totally mixed states. So Calvin cannot learn Alice’s and Bob’s private binary strings from the particle sequences he obtained.
4.4. Comparison
The related quantum PSI-CA protocols in [
27,
28] required entangled states, other complicated oracle operators and measurements in high dimensional Hilbert space, hence it is more feasible with the current technologies than those proposed with entangled states. Compared with some recently proposed protocols [
27,
28], our proposed quantum PSI-CA protocol has the following advantages. First, it only needs to take single photons as quantum resources and to apply single operators and measurements. Obviously, it is more feasible to prepare these resources and implement these operators and measurements. Second, our new protocol is more robust and can easily use the fault tolerant technologies due to single photons. Therefore, our new quantum protocol for PSI-CA is more practical and feasible compared with the existing protocols.