Efficient Equality Test on Identity-Based Ciphertexts Supporting Flexible Authorization
Abstract
1. Introduction
1.1. Our Contribution
1.2. Related Works
1.3. Organization
2. Preliminaries
2.1. Trapdoor Discrete Log (TDL) Groups
- : Given security parameter k as the input, the algorithm returns a tuple where T is used to denote the trapdoor, q is used to denote the prime order, g is used to denote a random generator, and G is used to denote a group.
- : Given the inputs of a security parameter k, denoting a tuple and h denoting a group element, the algorithm outputs , and holds.
2.2. Computational Diffie–Hellman (CDH) Problem
2.3. Decision Diffie–Hellman (DDH) Problem
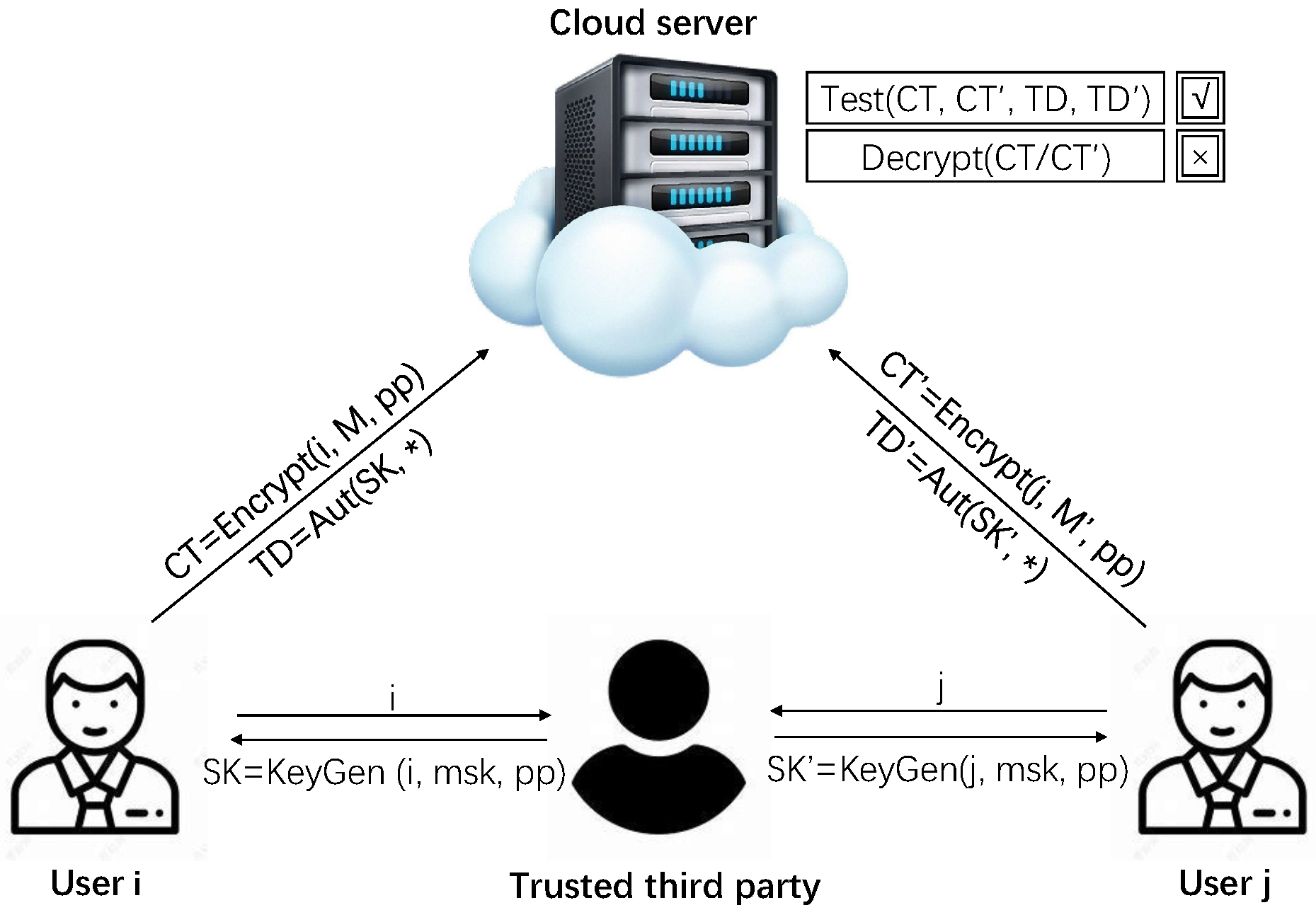
3. System Model and Definition
3.1. System Model
3.2. Definition of IBEET-FA
- : Taken security parameter k as the input, the public parameter and the master secret key will be gotten from the running result of the algorithm.
- : Given label i, master secret key , and public parameter as input, the algorithm returns the secret key .
- : Given the inputs of user i, a message M and public parameter , the algorithm returns the ciphertext .
- : Given label i, a private key , a ciphertext and public parameter as inputs, a message M will be gotten from the running result of the algorithm, or returns an error symbol ⊥.
- : Given user i and i’s secret key as inputs, the authorization procedure returns a trapdoor .
- : Given the inputs of i’ciphertext , i’trapdoor , j’ciphertext and j’trapdoor , the test procedure returns 1 if two ciphertexts contain the same message, otherwise returns 0.
- : Given the inputs of user i’private key and a ciphertext , the authorization procedure outputs a trapdoor .
- : Given the inputs of i’ciphertext , i’trapdoor , j’ciphertext and j’trapdoor , the test procedure returns 1 if two ciphertexts contain the same plaintext, otherwise returns 0.
- : Given the inputs of user i’private key , i’ciphertext , and j’ciphertext , the authorization procedure outputs a trapdoor .
- : Given the inputs of i’ciphertext , i’trapdoor , j’ciphertext and j’trapdoor , the test procedure returns 1 if two ciphertexts contain the same plaintext, otherwise returns 0.
- : Given the inputs of user i’private key and ciphertext , the authorization procedure returns a trapdoor .
- : Given user j and j’s secret key as inputs, the authorization procedure returns a trapdoor .
- : Given the inputs of i’ciphertext , i’trapdoor , j’ciphertext and j’trapdoor , the test procedure returns 1 if two ciphertexts contain the same message, otherwise returns 0.
- For any possible plaintext M in the plaintext space, , all equations hold.
- For any possible ciphertext of user i and any possible ciphertext of user j, if Decrypt:Aut-1: For two trapdoors of , , the following equality always holds thatAut-2: For two trapdoors of , , the following equality always holds thatAut-3: For two trapdoors of , , the following equality always holds thatAut-4: For two trapdoors of , , the following equality always holds that
- For any possible ciphertext of user i and any possible ciphertext of user j, if Decrypt, where be a negligible function about k:Aut-1: For two trapdoors of , , the following equality always holds thatAut-2: For two trapdoors of , , the following equality always holds thatAut-3: For two trapdoors of , , the following equality always holds thatAut-4: For two trapdoors of , , the following equality always holds that
3.3. Security Model
- Adv-I: For Aut- ( = 1, 2, 3), with Aut- trapdoor information, the adversary can not get the plaintext from the challenge ciphertext.
- Adv-II: For Aut- ( = 1, 2, 3), without Aut- trapdoor information, the adversary can not know the challenge ciphertext is from which plaintext.
- : Challenger firstly picks k as a security parameter, then gets public parameter by calling algorithm, sends to .
- : Allows to query for polynomially many times as follows.
- Key retrieve queries: calls algorithm and sends to . call the algorithm and send the result to A
- Decryption queries: runs algorithm and returns M(which might be ⊥) to .
- Authorization queries: For three types of authorization Aut- ( = 1, 2, 3),
- (a)
- i as input, sends to .
- (b)
- as input, sends to .
- (c)
- as input, sends to .
- : Adversary picks a target identity t which has not been queried in extract queries, and sends it to . Then chooses a message randomly, gets as the challenge ciphertext and sends it to .
- : continues issuing the same query as Phase 1. However, t can not be queried in this phase and can not be queried in a decryption query.
- : returns a message , if means wins the game.
- : Challenger firstly picks k as a security parameter, then gets public parameter by calling algorithm, and sends to .
- : Allows to issue polynomially times queries as in Game I.
- : Adversary sends to Challenger two messages , , and a target identity t, t can not be allowed to appear in extract query or Aut-1 authorization query phase. picks a bit randomly, uses encryption algorithm to get challenge ciphertext , then sends to .
- : Allows to continue issuing queries as Phase 1, but there are some restrictions as follows:
- i can not be queried in the Key retrieve query or Aut-1 authorizations queries;
- can not be queried in the decryption query;
- can not be queried in the authorizations query.
- : returns a bit , when holds, wins in the game.
4. Our Proposed IBEET-FA Scheme
4.1. The Proposed Scheme
- : Here k is a security parameter, and it is the size of plaintext messages, the algorithm works as follows:
- This algorithm calls the TDLGen algorithm of the TDL generator, then gets a tuple where T is the trapdoor, G is a group, g is a random generator, and q is the prime order.
- Picks some secure hash functions: , , , and .Gets the master secret key , the public parameter .
- : Choosing label i, the public parameter and master secret key as input, then calls SolveDL algorithm. as input, get a value such that . Furthermore, calls SolveDL algorithm again taking as input to get a value such that . Then outputs the secret key .
- : Taking a plaintext M, public parameter and user i as input, the algorithm works as follows:
- Compute one point .
- O is the origin, use point P, O to construct a ray with O as the endpoint.
- Choose a non zero point , then compute .
- Choose at random , then computeOutput the ciphertext .
- : Taking label i, a ciphertext , private key and public parameter as input, this algorithm computes and . Obtain point P as in algorithm and obtain with P, O as in algorithm. if hold, then returns M; and returns an error symbol ⊥ otherwise.
- : This authorization procedure returns a trapdoor .
- : The test procedure performs the following calculationsIt returns 1 if , or returns 0 otherwise.
- : This authorization procedure outputs a trapdoor .
- : This test procedure computesIt returns 1 if , or returns 0 otherwise.
- : This authorization procedure recovers with , then outputs a trapdoor
- : This test procedure computesIt returns 1 if , or returns 0 otherwise.
- : This authorization procedure returns a trapdoor .
- : This authorization procedure returns a trapdoor .
- : This test procedure computesIt returns 1 if , or returns 0.
4.2. Correctness
- The first requirement is satisfied obviously.
- According to the second requirement, for any , , , , all the following equations hold.
- Aut-1: Given , , get the following:Because point is taken from the ray corresponding to , point is taken from the ray corresponding to , if means and are taken from the same ray. So holds if .
- Aut-2: Givenandget the following:Because point is taken from the ray corresponding to , point is taken from the ray corresponding to , if means and are taken from the same ray. So holds if .
- Aut-3: Givenandget the following:Because point is taken from the ray corresponding to , point is taken from the ray corresponding to , if means and are taken from the same ray. So , i.e., holds if .
- Aut-4: Given , , get the following:Because point is taken from the ray corresponding to , point is taken from the ray corresponding to , if means and are taken from the same ray. So holds if .
- Now we prove the third condition holds.is a ray passing through point with O as its endpoint, is a ray passing through with O as its endpoint. Point is taken from the ray , and point is taken from the ray .
- Aut-1: If , we can get that , that is, point and point are taken from the same ray with O as the end point. For , is negligible, then we get that is also negligible for .
- Aut-2: If , we can get that , that is, point and point are taken from the same ray with O as the end point. For , is negligible, then we get that is also negligible.
- Aut-3: If , we can get that , that is, . For , is negligible, we get that is also negligible for .
- Aut-4: If , we can get that , that is, point and point are taken from the same ray with O as the end point. For , is negligible, we get that is also negligible for .
5. Security Analysis
5.1. OW-ID-CCA Security Against Adv-I
- Game1:
- : The challenger outputs public parameter , the master secret key .
- : Allows to do the following queries.
- 1.
- Hash queries: Suppose queries at most , , , , , times to hash oracles , , , , , , respectively.
- (a)
- , : Set original empty lists (resp.). For an identity i, the oracle picks (resp.) randomly, computes (resp.) and records the tuple (resp.) on hash list (resp.). (resp.) is returned to .
- (b)
- : Set original empty lists . For an input , the oracle picks a string randomly and records the tuple on hash list . is returned to .
- (c)
- , : Set original empty lists . For an input , the oracle picks randomly and records the tuple on hash list . is returned to .
- (d)
- : Set original empty lists . For an input , the oracle picks a string randomly and records the tuple on hash list . is returned to .
- 2.
- Key retrieve queries: For an identity i, challenger invokes hash oracles , to get hash values , , then runs algorithm to get the secret key . It returns to .
- 3.
- Decryption queries: For an identity i, ciphertext , challenger invokes key retrieve queries to obtain the secret key , then uses to call algorithm to obtain the message (which might be ⊥). It returns (or ⊥) to .
- 4.
- Authorization queries: For Aut- ( = 1, 2, 3),
- (a)
- : i as the input, runs algorithm with , then returns to .
- (b)
- : as the input, runs algorithm with , then returns to .
- (c)
- : as the input, runs algorithm with , then returns to .
- : Adversary submits to an identity t, and t has not been queried in previous extract query, randomly selects a message , and gets with the following equations.where the point is randomly taken from the ray passing through the point , and . Then, the challenge ciphertext is sent to .
- : Allows to issue the same type query as in Phase 1. However, in the key retrieve queries, t can not be allowed to query; and in the decryption queries, can not be queried.
- : returns a message , if , means in the game wins. The probability of adversary winning the game is:
- Game2:
- It is almost equivalent to Game 1, the modified parts are as follows:
- Game3:
- It is almost equivalent to Game2, the modified parts are as follows:
5.2. IND-ID-CCA Security Against Adv-II
- : For , algorithm generates n key pairs , where sets .
- : Allows algorithm to issue four types of queries as follows.
- 1.
- Hash queries:
- (a)
- , : Work in the same way as in .
- (b)
- : Works in the same way as in .
- (c)
- , : Works in the same way as in .
- (d)
- : Works in the same way as in .
- 2.
- Key retrieve queries: Given an identity i, searches tuple and tuple in list and list , sends to when holds. Otherwise, returns ⊥ to .
- 3.
- Decryption queries: For identity i and a query ciphertext , challenger searches tuple in list , and computes . If exists R, making equation true, returns M to . Otherwise, returns ⊥ to .
- 4.
- Authorization queries: For Aut- ( = 1, 2, 3),
- (a)
- : i as the input, challenger calls algorithm with , then sends to .
- (b)
- : as the input, challenger calls algorithm with , then sends to .
- (c)
- : given as input, challenger calls algorithm with , then sends to .
- : Adversary chooses two plaintext , and an identity t, there is a contraint that t can not be queried in extract queriy phase or Aut-1 authorization query phase. picks a bit randomly, then encrypts :challenger sends the obtained challenge ciphertext to the adversary .
- : issues the same type query as in Phase 1, and there are two following restrictions:
- 1.
- In the key retrieve query phase or Aut-1 authorizations query phase, i could not be allowed to query;
- 2.
- In the decryption query phase or the authorization query phase, could not be queried.
- : returns a bit . If holds, it means that wins the game, then outputs 1.
6. Efficiency Analysis
7. Conclusions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Boneh, D.; Crescenzo, G.D.; Ostrovsky, R.; Persian, G. Public key encryption with keyword search. In Proceedings of the Advances in Cryptology—EUROCRYPT 2004, Interlaken, Switzerland, 2–6 May 2004. [Google Scholar]
- Yang, G.; Tan, C.H.; Huang, Q.; Wong, D.S. Probabilistic public key encryption with equality test. In Proceedings of the Topics in Cryptology—CT-RSA 2010, San Francisco, CA, USA, 1–5 March 2010. [Google Scholar]
- Tang, Q. Towards public key encryption scheme supporting equality test with fine grained authorization. In Proceedings of the Australisian Conference on Information Security and Privacy (ACISP), Melbourne, Australia, 11–13 July 2011. [Google Scholar]
- Ma, S.; Huang, Q.; Zhang, M.W.; Yang, B. Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans. Inf. Forensics Secur. 2015, 10, 458–470. [Google Scholar] [CrossRef]
- Li, H.B.; Huang, Q.; Ma, S.; Shen, J.; Susilo, W. Authorized equality test on identity-based ciphertexts for secret data sharing via cloud storage. IEEE Access 2019, 7, 25409–25421. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Proceedings of the Advances in Cryptology—CRYPTO 1984, Santa Barbara, CA, USA, 19–22 August 1984. [Google Scholar]
- Paterson, K.G.; Srinivasan, S. On the relations between non-interactive key distribution, identity-based encryption and trapdoor discrete log groups. Des. Codes Cryptogr. 2009, 52, 219–241. [Google Scholar] [CrossRef]
- Chuah, M.; Hu, W. Privacy-aware bedtree based solution for fuzzy multi-keyword search over encrypted data. In Proceedings of the 31st International Conference on Distributed Computing Systems Workshops, Minneapolis, MN, USA, 20–24 June 2011. [Google Scholar]
- Park, D.J.; Kim, K.; Lee, P.J. Public key encryption with conjunctive field keyword search. In Proceedings of the International Conference on Information Security Applications(WISA), Jeju Island, Republic of Korea, 23–25 August 2004. [Google Scholar]
- Byun, J.W.; Rhee, H.S.; Park, H.A.; Lee, D.H. Off-line keyword guessing attacks on recent keyword search schemes over encrypted data. In Proceedings of the Secure Data Management(SDM), Seoul, Republic of Korea, 10–11 September 2006. [Google Scholar]
- Bellare, M.; Boldyreva, A.; O’Neill, A. Deterministic and efficiently searchable encryption. In Proceedings of the Advances in Cryptology—CRYPTO 2007, Santa Barbara, CA, USA, 19–23 August 2007. [Google Scholar]
- Tang, Q. Public key encryption schemes supporting equality test with authorisation of different granularity. IJACT 2012, 2, 304–321. [Google Scholar] [CrossRef]
- Tang, Q. Public key encryption supporting plaintext equality test and user-specified authorization. Secur. Commun. Netw. 2012, 5, 1351–1362. [Google Scholar] [CrossRef]
- Ma, S.; Zhang, M.W.; Huang, Q.; Yang, B. Public Key Encryption with Delegated Equality Test in a Multi-User Setting. Comput. J. 2015, 58, 986–1002. [Google Scholar] [CrossRef]
- Wu, T.; Ma, S.; Mu, Y.; Zeng, S.K. ID-Based Encryption with Equality Test Against Insider Attack. In Proceedings of the Australasian Conference on Information Security and Privacy (ACISP), Auckland, New Zealand, 3–5 July 2017. [Google Scholar]
- Ma, S. Authorized Equality Test of Encrypted Data for Secure Cloud Databases. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security Furthermore, Privacy in Computing Furthermore, Communications/12th IEEE International Conference On Big Data Science Furthermore, Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018. [Google Scholar]
- Huang, K.B.; Raylin, T.; Yu-Chi, C. PKE-AET:Public Key Encryption with Authorized Equality Test. Comput. J. 2015, 58, 2686–2697. [Google Scholar] [CrossRef]
- Huang, K.B.; Raylin, T.; Yu-Chi, C. A New Public Key Encryption with Equality Test. In Proceedings of the Network and System Security (NSS), Xi’an, China, 15–17 October 2014. [Google Scholar]
- Huang, K.B.; Yu-Chi, C.; Raylin, T. Semantic Secure Public Key Encryption with Filtered Equality Test-PKE-FET. In Proceedings of the 12th International Joint Conference on e-Business and Telecommunications (ICETE), Colmar, France, 20–22 July 2015. [Google Scholar]
- Huang, K.B.; Raylin, T.; Yu-Chi, C. Somewhat semantic secure public key encryption with filtered-equality-test in the standard model and its extension to searchable encryption. J. Comput. Syst. Sci. 2017, 89, 400–409. [Google Scholar] [CrossRef]
- Zhu, H.J.; Wang, L.C.; Ahmad, H.; Niu, X.X. Key-policy attribute-based encryption with equality test in cloud computing. IEEE Access 2017, 5, 20428–20439. [Google Scholar] [CrossRef]
- Wang, Q.; Peng, L.; Xiong, H.; Sun, J.F.; Qin, Z.G. Ciphertext-policy attribute-based encryption with delegated equality test in cloud computing. IEEE Access 2018, 6, 760–771. [Google Scholar] [CrossRef]
- Lin, X.J.; Sun, L.; Qu, H.p.; Zhang, X.S. Public key encryption supporting equality test and flexible authorization without bilinear pairings. Comput. Commun. 2021, 170, 190–199. [Google Scholar] [CrossRef]
- Zhu, H.J.; Wang, L.C.; Ahmad, H.; Niu, X.X. Pairing-free equality test over short ciphertexts. Int. J. Distrib. Sens. Netw. 2017, 13. [Google Scholar] [CrossRef]
- Ma, S. Identity-based encryption with outsourced equality test in cloud computing. Inf. Sci. 2016, 328, 389–402. [Google Scholar] [CrossRef]
- Duong, D.H.; Roy, P.S.; Susilo, W.; Fukushima, K.; Kiyomoto, S.; Sipasseuth, A. Chosen-ciphertext lattice-based public key encryption with equality test in standard model. Theor. Comput. Sci. 2022, 905, 31–53. [Google Scholar] [CrossRef]
- Amerini, I.; Anagnostopoulos, A.; Maiano, L.; Celsi, L.R. Deep Learning for Multimedia Forensics. Found. Trends Comput. Graph. Vis. 2021, 12, 309–457. [Google Scholar] [CrossRef]
- Susilo, W.; Guo, F.C.; Zhao, Z.; Wu, G. PKE-MET: Public-key encryption With multi-ciphertext equality test in cloud computing. IEEE Trans. Cloud Comput. 2022, 10, 1476–1488. [Google Scholar] [CrossRef]
- Lin, X.J.; Wang, Q.; Sun, L.; Qu, H. Identity-based encryption with equality test and datestamp-based authorization mechanism. Theor. Comput. Sci. 2021, 861, 117–132. [Google Scholar] [CrossRef]
- Deverajan, G.G.; Muthukumaran, V.; Hsu, C.; Karuppiah, M.; Chung, Y.; Chen, Y. Public key encryption with equality test for Industrial Internet of Things system in cloud computing. Trans. Emerg. Telecommun. Technol. 2021, 33, e4202. [Google Scholar] [CrossRef]
- Vaanchig, N.; Qin, Z.; Ragchaasuren, B. Constructing secure-channel free identity-based encryption with equality test for vehicle-data sharing in cloud computing. Trans. Emerg. Telecommun. Technol. 2020, 33, e3896. [Google Scholar] [CrossRef]
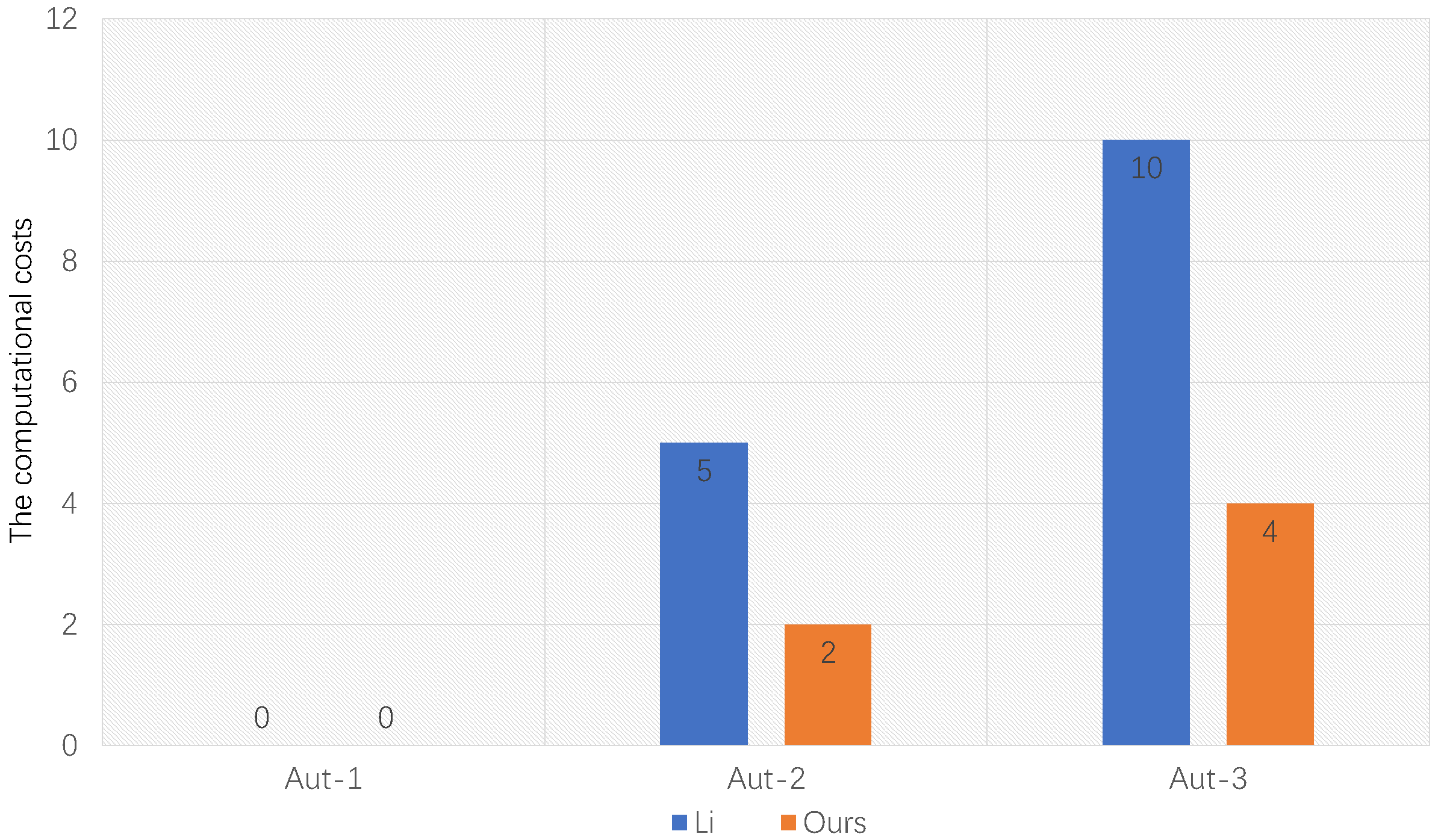
| Public Key | Secret Key | Ciphertext | |
|---|---|---|---|
| PKEET-FA [4] | |||
| PKEET-FA [23] | |||
| PKEET-FA [24] | |||
| IBEET-FA [5] | |||
| Our IBEET-FA |
| Encryption | Decryption | Authorization | Test | ID-Based | Pairings-Based | |
|---|---|---|---|---|---|---|
| PKEET-FA [4] Aut-1 | 6E | 5E | 0 | 2P + 2E | NO | YES |
| PKEET-FA [4] Aut-2 | 6E | 5E | 2E | 2P + 2E | NO | YES |
| PKEET-FA [4] Aut-3 | 6E | 5E | 2P + 2E | 2P + 2E | NO | YES |
| PKEET-FA [23] Aut-1 | 4E + 6I | 3E + 6I | 0 | 2E + 6I | NO | NO |
| PKEET-FA [23] Aut-3 | 4E + 6I | 3E + 6I | 4E | 6E + 6I | NO | NO |
| PKEET-FA [24] Aut-1 | 3E + I | 2E + I | 0 | 2E + 2I | NO | NO |
| PKEET-FA [24] Aut-2 | 3E + I | 2E + I | E | 2I | NO | NO |
| PKEET-FA [24] Aut-3 | 3E + I | 2E + I | 3E | 4E + 4I | NO | NO |
| IBEET-FA [5] Aut-1 | 7E | 3P + 2E | 0 | 4P | YES | YES |
| IBEET-FA [5] Aut-2 | 7E | 3P + 2E | P | 2P | YES | YES |
| IBEET-FA [5] Aut-3 | 7E | 3P + 2E | 2P | 2P | YES | YES |
| Our IBEET-FA Aut-1 | 3E | 2E | 0 | 2E + 2I | YES | NO |
| Our IBEET-FA Aut-2 | 3E | 2E | 2E | 2I | YES | NO |
| Our IBEET-FA Aut-3 | 3E | 2E | 4E | 2E + 2I | YES | NO |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, N. Efficient Equality Test on Identity-Based Ciphertexts Supporting Flexible Authorization. Entropy 2023, 25, 362. https://doi.org/10.3390/e25020362
Li N. Efficient Equality Test on Identity-Based Ciphertexts Supporting Flexible Authorization. Entropy. 2023; 25(2):362. https://doi.org/10.3390/e25020362
Chicago/Turabian StyleLi, Na. 2023. "Efficient Equality Test on Identity-Based Ciphertexts Supporting Flexible Authorization" Entropy 25, no. 2: 362. https://doi.org/10.3390/e25020362
APA StyleLi, N. (2023). Efficient Equality Test on Identity-Based Ciphertexts Supporting Flexible Authorization. Entropy, 25(2), 362. https://doi.org/10.3390/e25020362





