Cache-Based Privacy Protection Scheme for Continuous Location Query
Abstract
1. Introduction
- A new location caching scheme is proposed that uses caching techniques to reduce the number of interactions with LSPs, improves the cache hit rate through the designed query scheme and reduces the risk of privacy leakage in continuous location queries.
- When it is necessary to initiate a query to the LSPs, we use differential privacy techniques to perturb the anonymous location set to ensure the user’s location privacy during the query.
- By comparing with other schemes in terms of cache hit rate, query time, and degree of privacy protection, our scheme can better protect user-location privacy and reduce the overhead of communication with LSP.
2. Related Work
2.1. k-Anonymity Technology
2.2. Caching Technology
2.3. Differential Privacy
3. System Model and Definition
3.1. Objectives and Use Scenarios
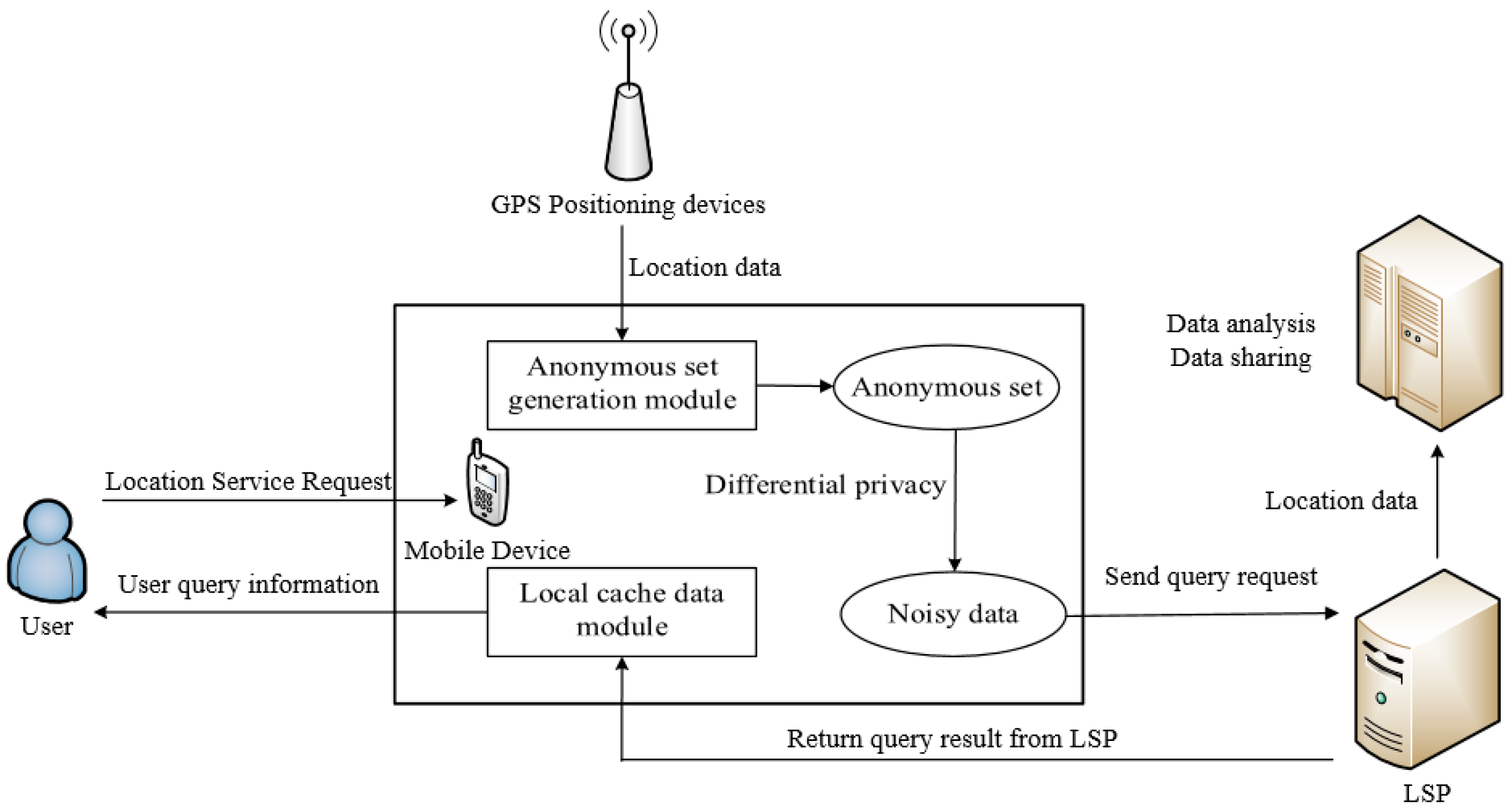
3.2. System Model
3.3. Attack Model
3.4. Variable-Order Markov Model
3.5. Differential Privacy
4. Cache-Based Location Privacy Protection Scheme
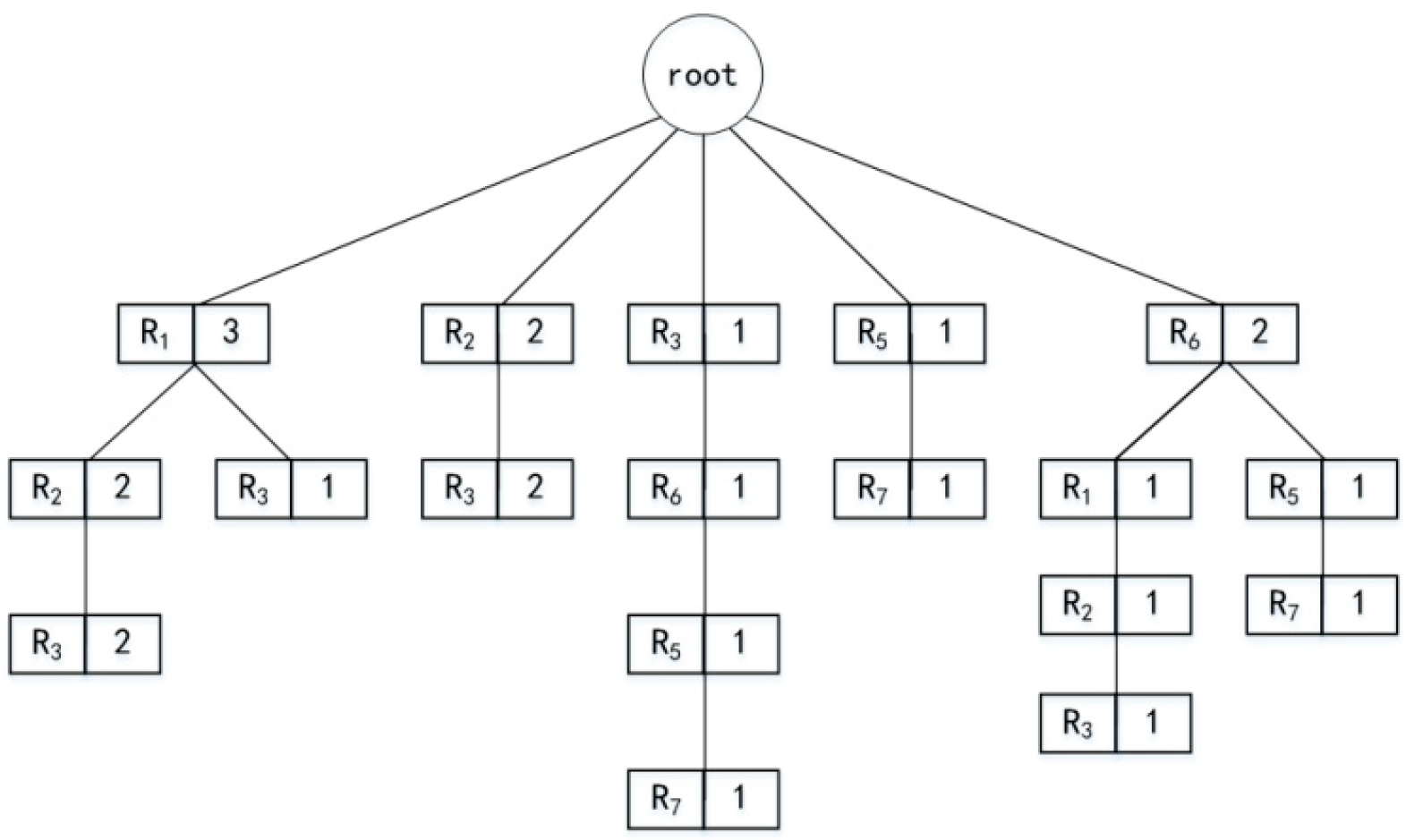
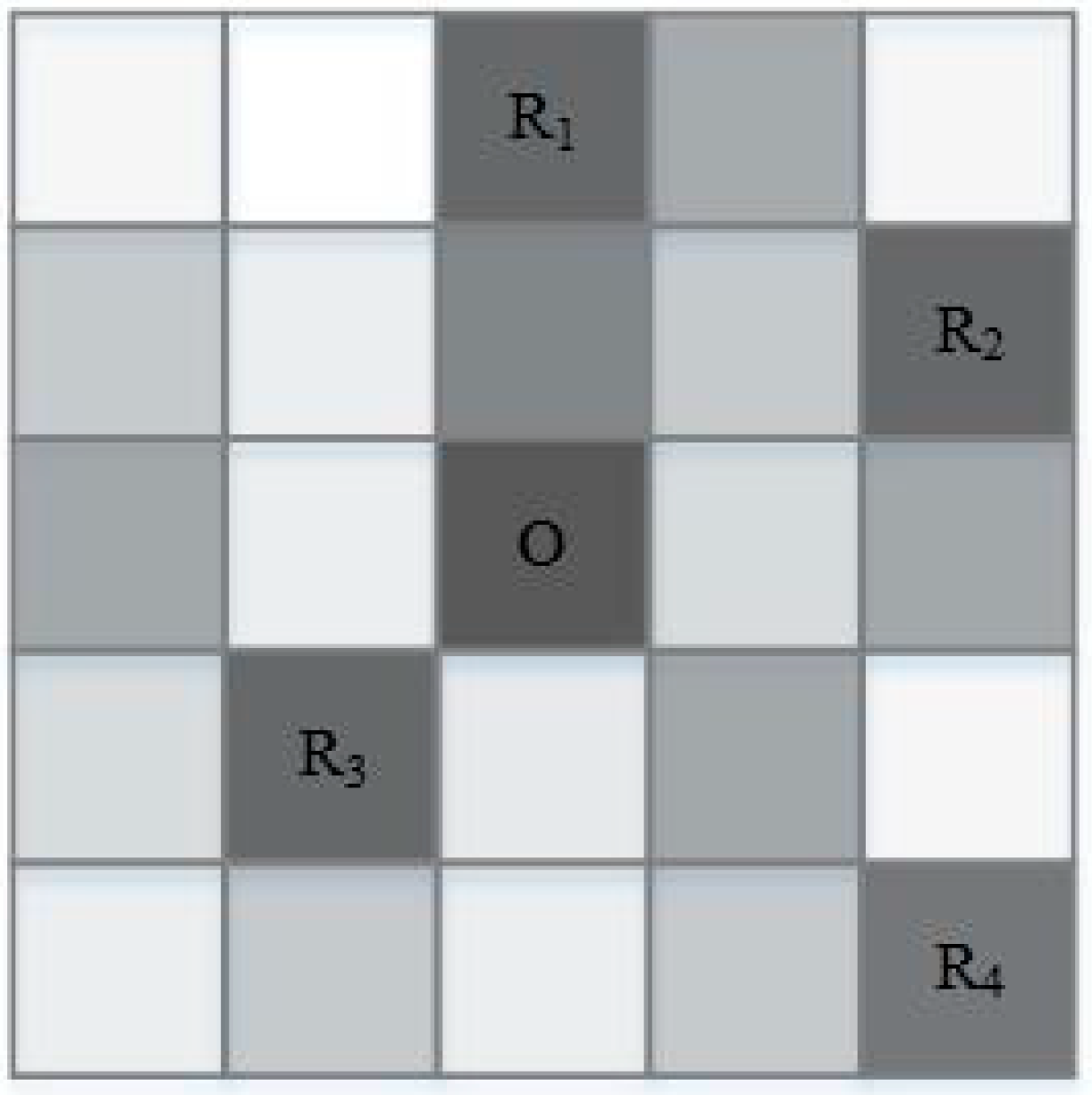
4.1. The Structure of the Local Cache Data
4.2. Anonymous Set Generation
4.2.1. Obtain Stay Points
4.2.2. Building and Prediction of Variable-Order Markov Model
| Algorithm 1: Variable-Order Markov Model Prediction |
| Input: LU, T, k Output: Z′ 1: Z′ = ; 2: while length (Z′) < k − 1 do 3: if length(LU) == 0 4: return Z′; 5: break; 6: while find (T, LU) return false do 7: LU = delete the earliest position point of LU; 8: m = length(LU); 9: Z′ = use m-order Markov model to predict all possible location points; 10: if num(Z′) ≥ k − 1 11: return Z′; 12: break; 13: else 14: LU = delete the earliest position point of LU; |
4.2.3. Generate Anonymous Sets
| Algorithm 2: Anonymous Query Set Generation Algorithm |
| Input: k, Z′, S, R, Local cache location dataset O, User’s current location loc Output: Anonymous location set Z 1: Z = ; 2: if length(Z′) ≥ k − 1 3: sort points in Z′ by predicted probability; 4: return Z = the first k − 1 points in Z′ + {loc + Lap(εi)}; 5: else 6: Z = Z′; 7: S′ = points in S that are in the range R; 8: sort points in S′ by query probability; 9: i = 0; 10: while length(Z) < k − 1 do 11: if S′[i] is not in Z and S′[i] is not in O 12: Z + = S′[i]; 13: if length(Z) == k − 1 14: break; 15: i + + ; 16: return Z = Z + {loc + Lap(εi)}; |
5. Security Analysis
6. Experiment
6.1. Experimental Simulation Settings
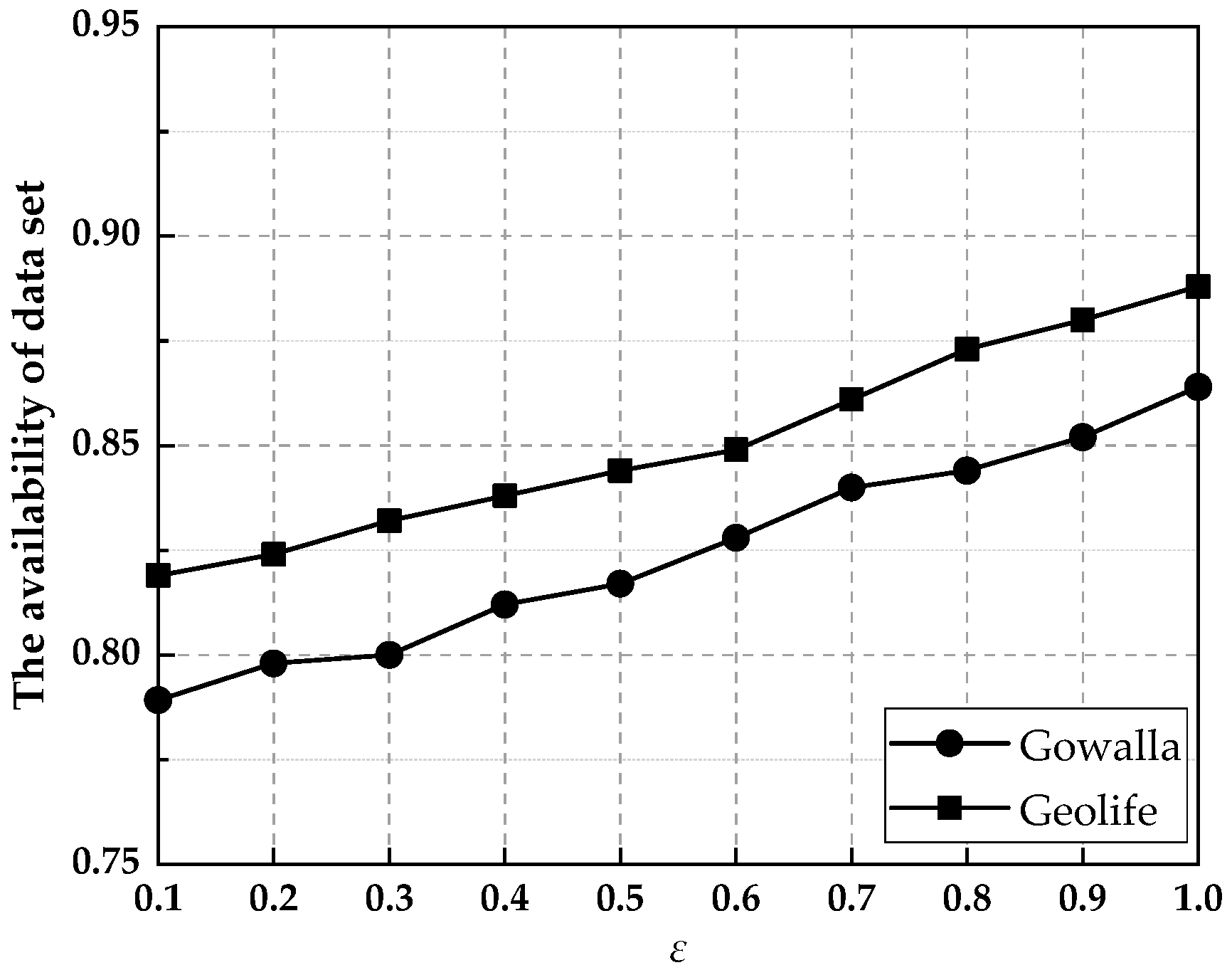
6.2. Data Availability
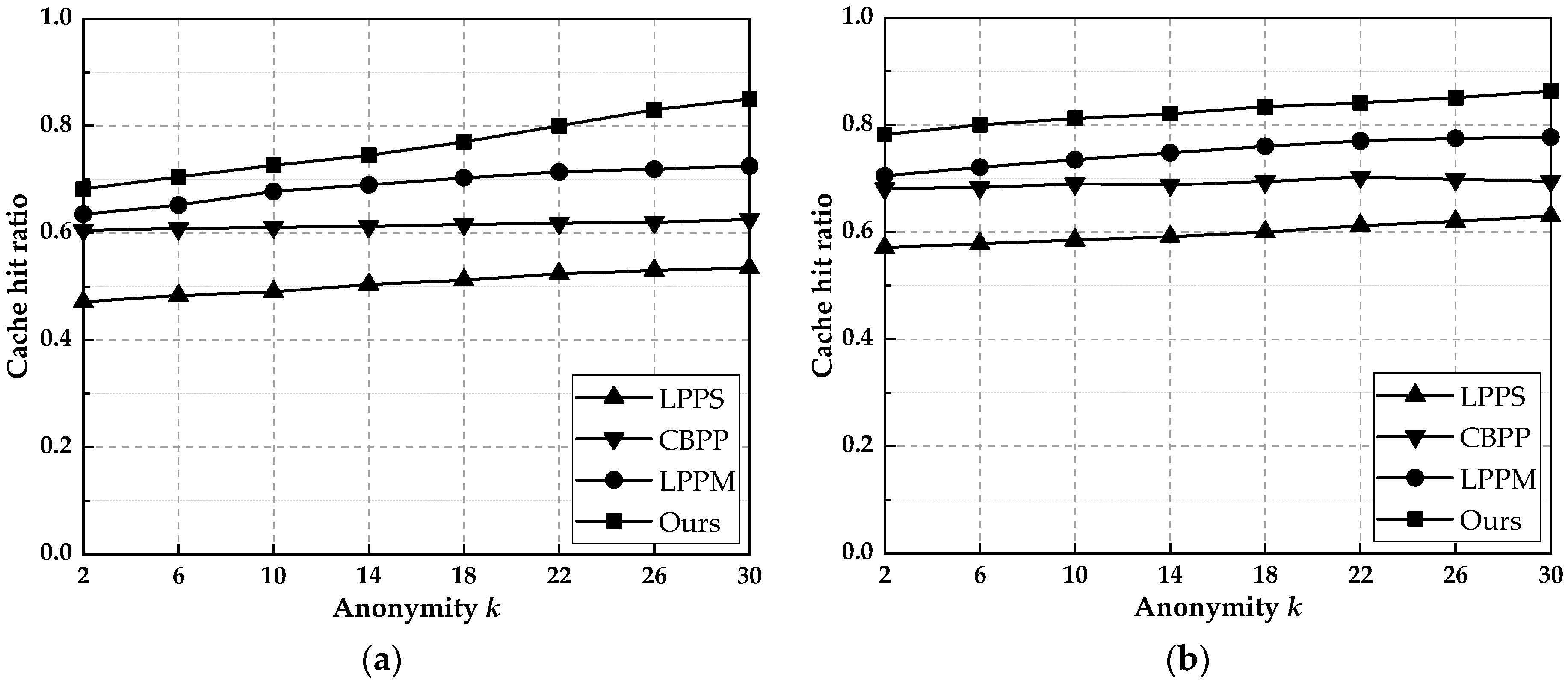
6.3. Cache Hit Rate
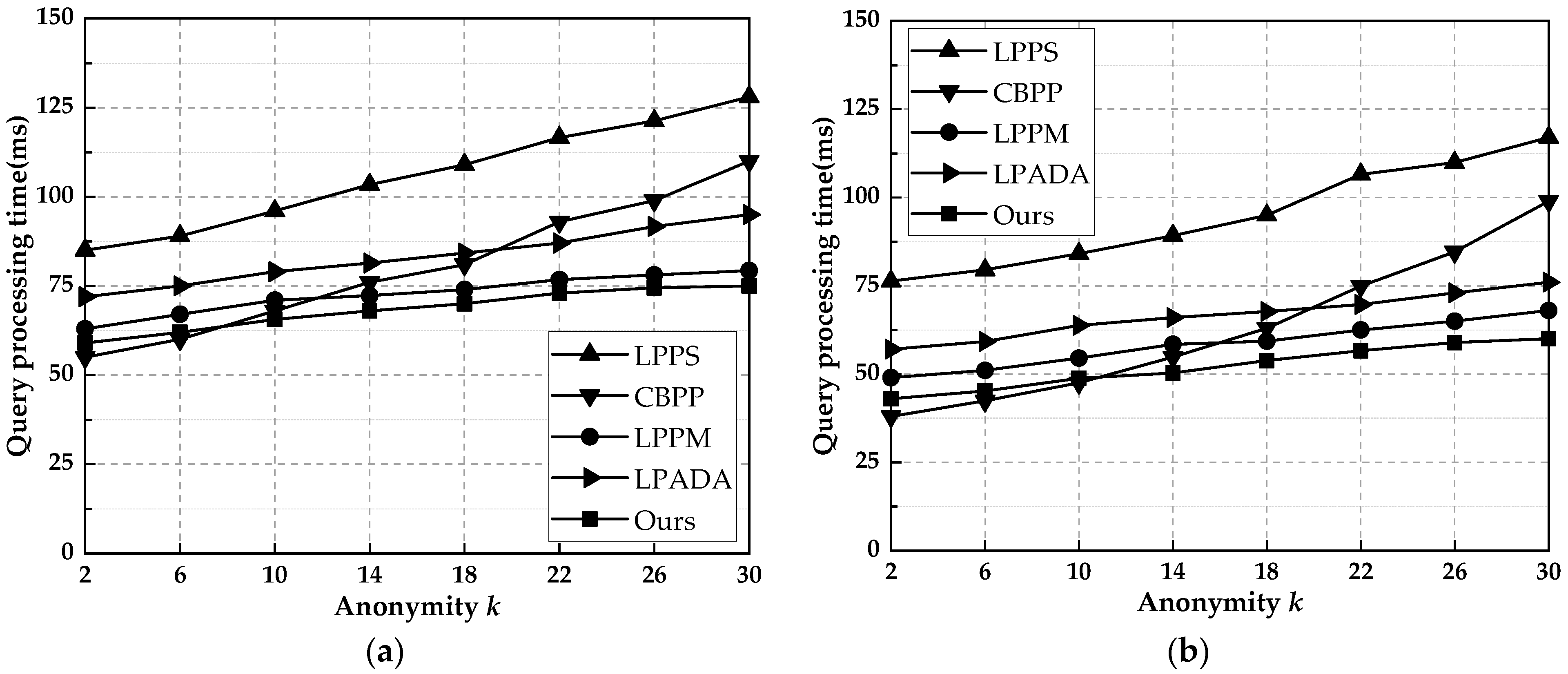
6.4. Query Time
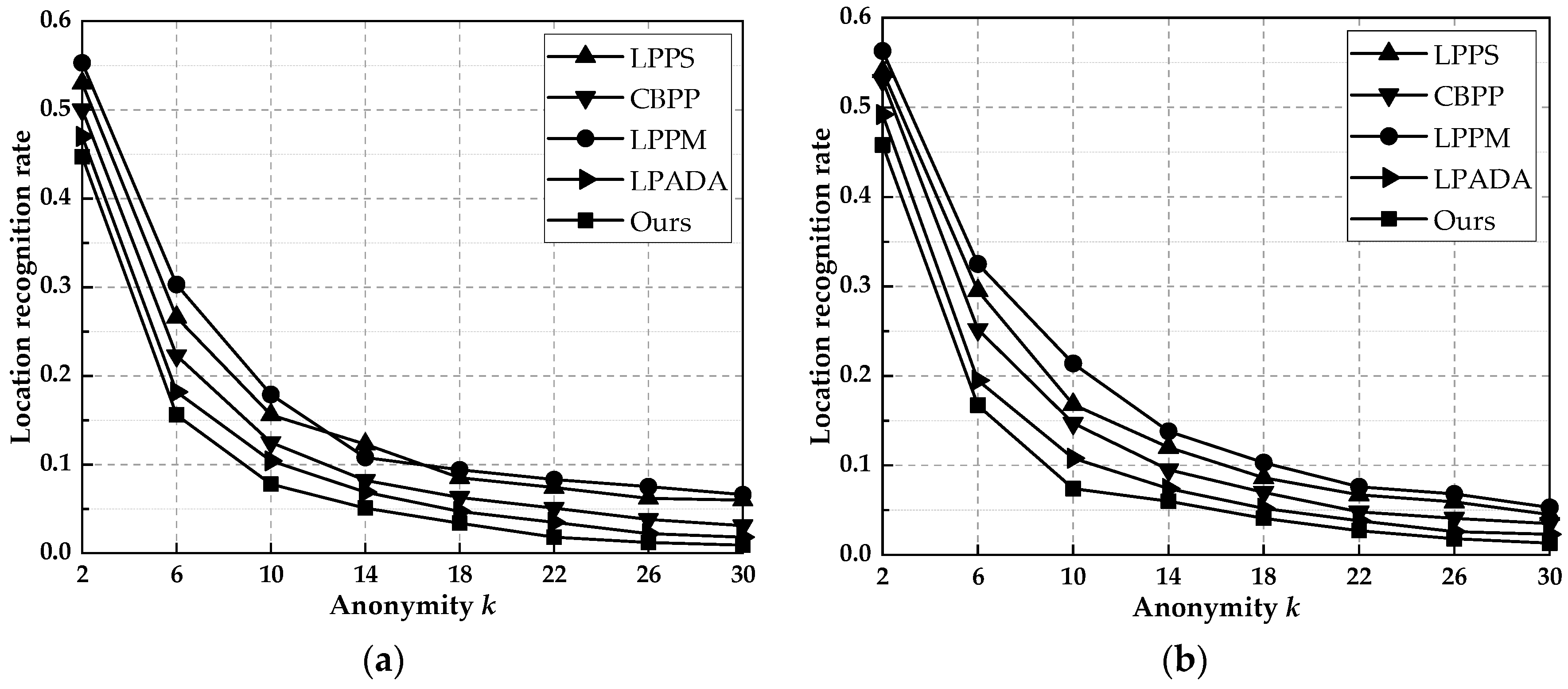
6.5. Degree of Privacy Protection
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Dilay, P.; Udai, P.R. Towards Privacy-Preserving Dummy Generation in Location-Based Services. Procedia Comput. Sci. 2020, 171, 1323–1326. [Google Scholar]
- Seo, Y.D.; Cho, Y.S. Point of interest recommendations based on the anchoring effect in location-based social network services. Expert Syst. Appl. 2021, 164, 114018. [Google Scholar] [CrossRef]
- Gao, T.; Zhao, L. Pseudonym Schemes Based on Location Privacy Protection in VANETs: A Survey. In Innovative Mobile and Internet Services in Ubiquitous Computing, Proceedings of the International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Lodz, Poland, 1–3 July 2020; Springer: Cham, Germany, 2020; pp. 597–605. [Google Scholar]
- Cai, J.L.Z.; Yan, M.; Li, Y. Using crowdsourced data in location-based social networks to explore influence maximization. In Proceedings of the IEEE INFOCOM 2016—The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar]
- Xu, C.; Zhu, L.; Liu, Y.; Guan, J.; Yu, S. DP-LTOD: Differential Privacy Latent Trajectory Community Discovering Services over Location-Based Social Networks. IEEE Trans. Serv. Comput. 2021, 14, 1068–1083. [Google Scholar] [CrossRef]
- Nisha, N.; Natgunanathan, I.; Xiang, Y. An Enhanced Location Scattering Based Privacy Protection Scheme. IEEE Access 2022, 10, 21250–21263. [Google Scholar] [CrossRef]
- Zhong, H.; Ni, J.; Cui, J.; Zhang, J.; Liu, L. Personalized location privacy protection based on vehicle movement regularity in vehicular networks. IEEE Syst. J. 2021, 16, 755–766. [Google Scholar] [CrossRef]
- Li, Y.; Qin, Y.; Wang, H. K-Nearest Neighbor Privacy Protection Query for Distributed Storage in Location-based Service. Wirel. Pers. Commun. 2021, 121, 1509–1532. [Google Scholar] [CrossRef]
- Andreoletti, D.; Ayoub, O.; Giordano, S.; Verticale, G.; Tornatore, M. Network-Based Contact Tracing for Detection of Covid-19 Contagions: A Privacy-Preserving Approach. IEEE Commun. Mag. 2021, 59, 42–48. [Google Scholar] [CrossRef]
- Chen, M.; Li, W.; Chen, X.; Li, Z.; Lu, S.; Chen, D. LPPS: A distributed cache pushing based k-anonymity location privacy preserving scheme. Mob. Inf. Syst. 2016, 2016, 7164126. [Google Scholar] [CrossRef]
- Zhu, S.; Lv, X.; Yu, L. Location Privacy Protection Method based on Variable-Order Markov Prediction Model. In Proceedings of the 2021 4th International Conference on Computer Science and Software Engineering (CSSE 2021), Singapore, 22–24 October 2021; pp. 25–30. [Google Scholar]
- Shao, Z.; Wang, H.; Zou, Y.; Gao, Z.; Lv, H. From Centralized Protection to Distributed Edge Collaboration: A Location Difference-Based Privacy-Preserving Framework for Mobile Crowdsensing. Secur. Commun. Netw. 2021, 2021, 5855745. [Google Scholar] [CrossRef]
- Rajasekar, S.S.; Palanisamy, C.; Saranya, K. Privacy-preserving location-based services for mobile users using directional service fetching algorithm in wireless networks. J. Ambient Intell. Humaniz. Comput. 2021, 12, 7007–7017. [Google Scholar] [CrossRef]
- Sweeney, L. k-Anonymity: A Model for Protecting Privacy. Int. J. Uncertain. Fuzziness Knowl.-Based Syst. 2002, 10, 557–570. [Google Scholar] [CrossRef]
- Gruteser, M.; Grunwald, D. Anonymous usage of location-based services through spatial and temporal cloaking. In Proceedings of the 1st International Conference on Mobile Systems, Applications and Services, San Francisco, CA, USA, 5–8 May 2003; ACM Press: New York, NY, USA, 2003; pp. 31–42. [Google Scholar]
- Jie, L.; Jun, X. Decentralized Location Privacy Protection Method of Offset Grid. In Proceedings of the 3rd International Conference on Mechatronics Engineering and Information Technology (ICMEIT 2019), Dalian, China, 29–30 March 2019; Atlantis Press: Paris, France, 2019; pp. 113–120. [Google Scholar]
- Zhang, Y.B.; Zhang, Q.Y.; Yan, Y.; Jiang, Y.L.; Zhang, M.Y. A k-Anonymous Location Privacy Protection Method of Polygon Based on Density Distribution. Int. J. Netw. Secur. 2021, 23, 57–66. [Google Scholar]
- Zhu, X.; Chi, H.; Niu, B.; Zhang, W.; Li, Z.; Li, H. Mobicache: When k-anonymity meets cache. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; IEEE Press: Piscataway, NJ, USA, 2013; pp. 820–825. [Google Scholar]
- Jung, K.; Park, S. Collaborative caching techniques for privacy-preserving location-based services in peer-to-peer environments. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 11–17. [Google Scholar]
- Hu, L.; Qian, Y.; Chen, M.; Hossain, M.S.; Muhammad, G. Proactive cache-based location privacy preserving for vehicle networks. IEEE Wirel. Commun. 2018, 25, 77–83. [Google Scholar] [CrossRef]
- Zhang, S.; Choo, K.K.R.; Liu, Q.; Wang, G. Enhancing privacy through uniform grid and caching in location-based services. Future Gener. Comput. Syst. 2018, 86, 881–892. [Google Scholar] [CrossRef]
- Zhang, S.; Li, X.; Tan, Z.; Peng, T.; Wang, G. A caching and spatial K-anonymity driven privacy enhancement scheme in continuous location-based services. Future Gener. Comput. Syst. 2019, 94, 40–50. [Google Scholar] [CrossRef]
- Cui, Y.; Gao, F.; Li, W.; Shi, Y.; Zhang, H.; Wen, Q.; Panaousis, E. Cache-based privacy preserving solution for location and content protection in location-based services. Sensors 2020, 20, 4651. [Google Scholar] [CrossRef]
- Nisha, N.; Natgunanathan, I.; Gao, S.; Xiang, Y. A novel privacy protection scheme for location-based services using collaborative caching. Comput. Netw. 2022, 213, 109107. [Google Scholar] [CrossRef]
- Huang, Q.; Xu, X.; Chen, H.; Xie, L. A vehicle trajectory privacy preservation method based on caching and dummy locations in the internet of vehicles. Sensors 2022, 22, 4423. [Google Scholar] [CrossRef]
- DWORK, C. Differential privacy. In International Colloquium on Automata, Languages, and Programming; Springer: Berlin, Germany, 2006; pp. 1–12. [Google Scholar]
- Wang, J.; Wang, F.; Li, H. Differential Privacy Location Protection Scheme Based on Hilbert Curve. Secur. Commun. Netw. 2021, 2021, 5574415. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhang, Q.; Li, Z.; Yan, Y.; Zhang, M.Y. A k-anonymous Location Privacy Protection Method of Dummy Based on Geographical Semantics. Int. J. Netw. Secur. 2019, 21, 937–946. [Google Scholar]
- Zhang, Q.; Zhang, X.; Wang, M.; Li, X. DPLQ: Location-based service privacy protection scheme based on differential privacy. IET Inf. Secur. 2021, 15, 442–456. [Google Scholar] [CrossRef]
- Li, H.; Wang, Y.; Guo, F.; Wang, J.; Wang, B.; Wu, C. Differential privacy location protection method based on the Markov model. Wirel. Commun. Mob. Comput. 2021, 2021, 4696455. [Google Scholar] [CrossRef]
- Zhang, J.; Li, Y.; Ding, Q.; Lin, L.; Ye, X. Successive Trajectory Privacy Protection with Semantics Prediction Differential Privacy. Entropy 2022, 24, 1172. [Google Scholar] [CrossRef] [PubMed]
- Kou, K.; Liu, Z.; Ye, H.; Li, Z.; Liu, W. A location privacy protection algorithm based on differential privacy in sensor network. Int. J. Embed. Syst. 2021, 14, 432–442. [Google Scholar] [CrossRef]
- Rahimifar, A.; Seifi Kavian, Y.; Kaabi, H.; Soroosh, M. Predicting the energy consumption in software defined wireless sensor networks: A probabilistic Markov model approach. J. Ambient Intell. Humaniz. Comput. 2021, 12, 9053–9066. [Google Scholar] [CrossRef]
- Pinelli, F.; Pedreschi, D.; Giannotti, F.; Nanni, M. Trajectory pattern mining. In Proceedings of the 13th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, San Jose, CA, USA, 12–15 August 2007; pp. 330–339. [Google Scholar]
| Symbol | Description |
|---|---|
| k | Number of location points in an anonymous set |
| ε | Privacy budget |
| Grid area identifier for the location point | |
| data | Location point query data |
| t | Time of data availability |
| L | User history track |
| Speed threshold | |
| T | History trajectory tree |
| m | Maximum order of trajectory tree |
| S | Location query probability table |
| R | Anonymous point query selection range |
| Z′ | Anonymous candidate set |
| Z | Anonymous location set |
| O | Local cache location dataset |
| Parameter | Values |
|---|---|
| Number of anonymous locations k | 2–30 |
| Privacy budget ε | 0.1–1.0 |
| Time of data availability t | 30 min |
| Speed threshold | 0.25 m/s |
| Maximum order of trajectory tree m | 3 |
| Anonymous point query range R | 0.5 km |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Z.; Miao, D.; Li, R.; Liu, Y.; Li, X. Cache-Based Privacy Protection Scheme for Continuous Location Query. Entropy 2023, 25, 201. https://doi.org/10.3390/e25020201
Liu Z, Miao D, Li R, Liu Y, Li X. Cache-Based Privacy Protection Scheme for Continuous Location Query. Entropy. 2023; 25(2):201. https://doi.org/10.3390/e25020201
Chicago/Turabian StyleLiu, Zhenpeng, Dewei Miao, Ruilin Li, Yi Liu, and Xiaofei Li. 2023. "Cache-Based Privacy Protection Scheme for Continuous Location Query" Entropy 25, no. 2: 201. https://doi.org/10.3390/e25020201
APA StyleLiu, Z., Miao, D., Li, R., Liu, Y., & Li, X. (2023). Cache-Based Privacy Protection Scheme for Continuous Location Query. Entropy, 25(2), 201. https://doi.org/10.3390/e25020201







