Image Encryption Using a New Hybrid Chaotic Map and Spiral Transformation
Abstract
:1. Introduction
2. Construction of the Hybrid Chaotic Map
2.1. Classic Chaotic Maps
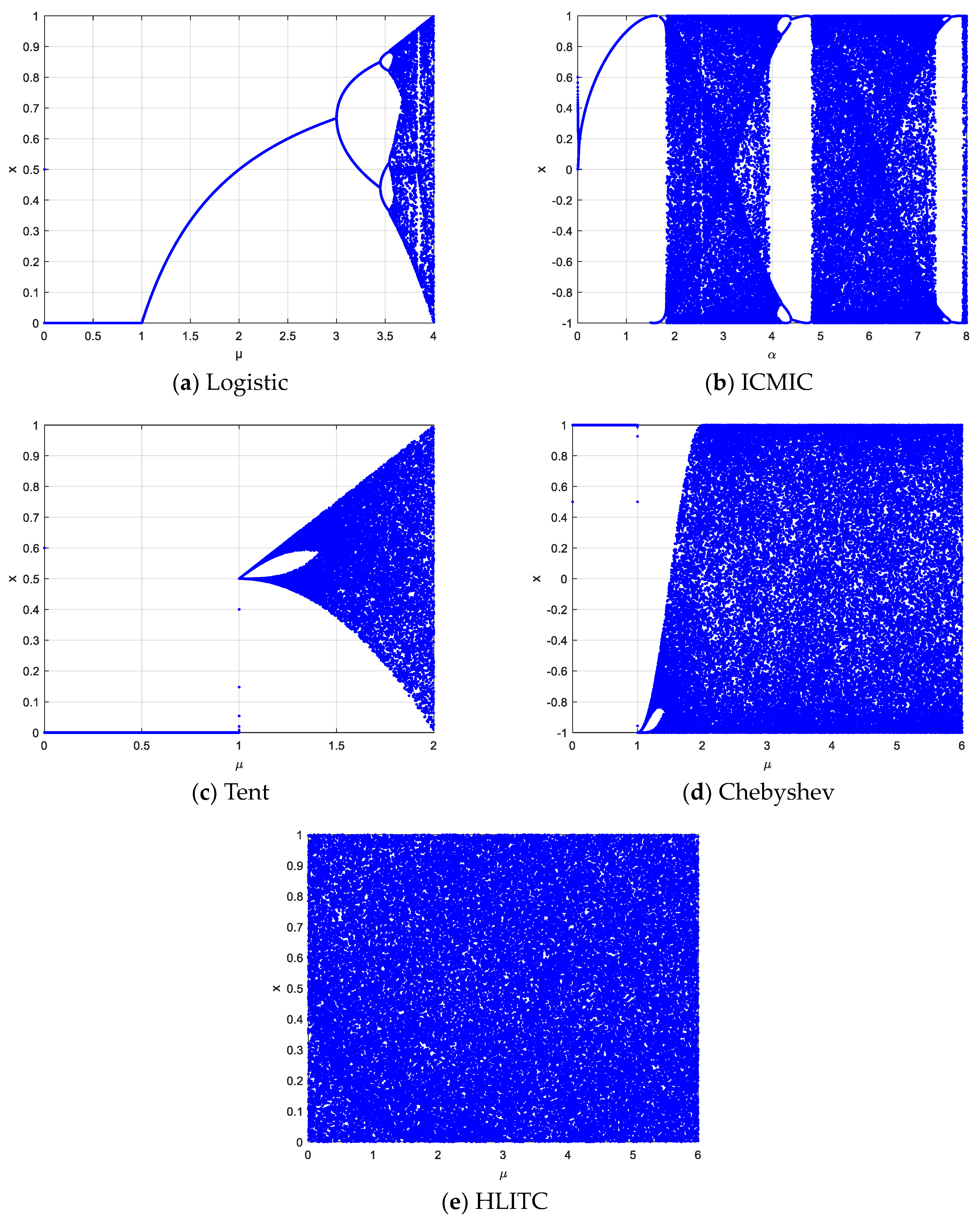
2.1.1. Logistic Map
2.1.2. ICMIC Map
2.1.3. Tent Map
2.1.4. Chebyshev Map
2.2. Proposed HLITC Chaotic System
2.3. Lyapunov Exponent
2.4. Information Entropy
2.5. Approximate Entropy
2.6. Randomness Testing
3. Image Encryption Based on a Hybrid HLITC Map
3.1. Key Generation
3.2. Image Encryption
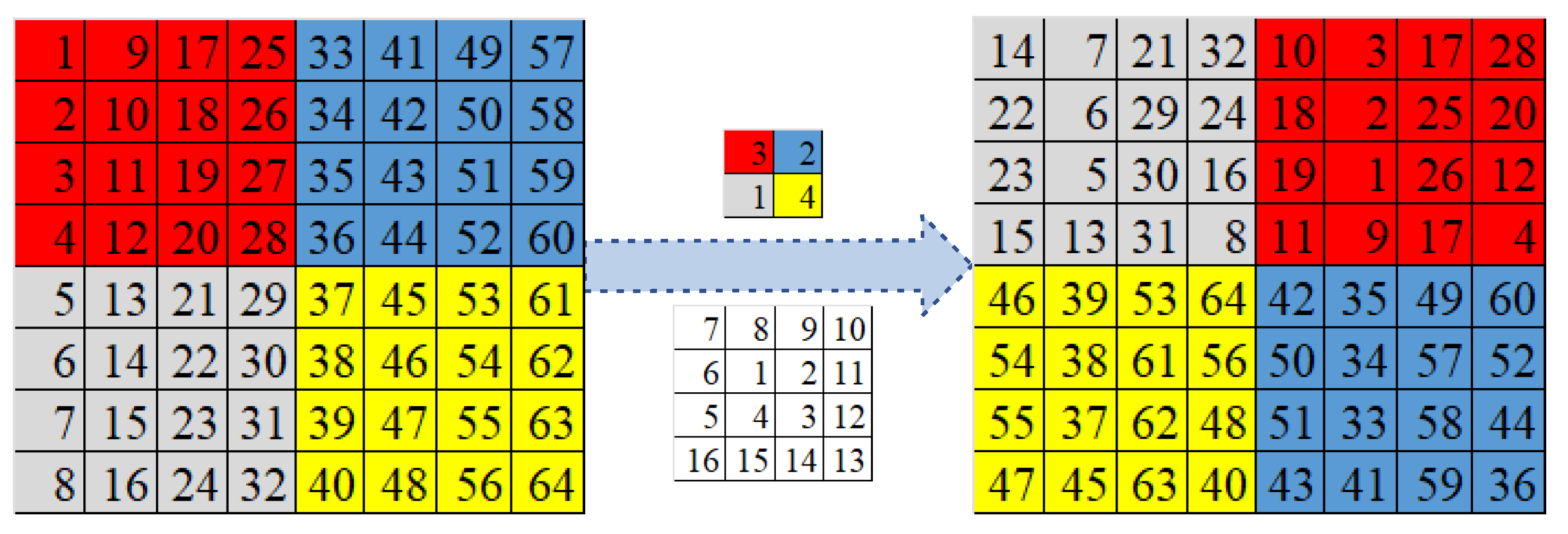
3.2.1. Image Scrambling Based on Spiral Transformation
3.2.2. Image Diffusion Based on a Chaotic Map
4. Experimental Results
4.1. Histogram Analysis
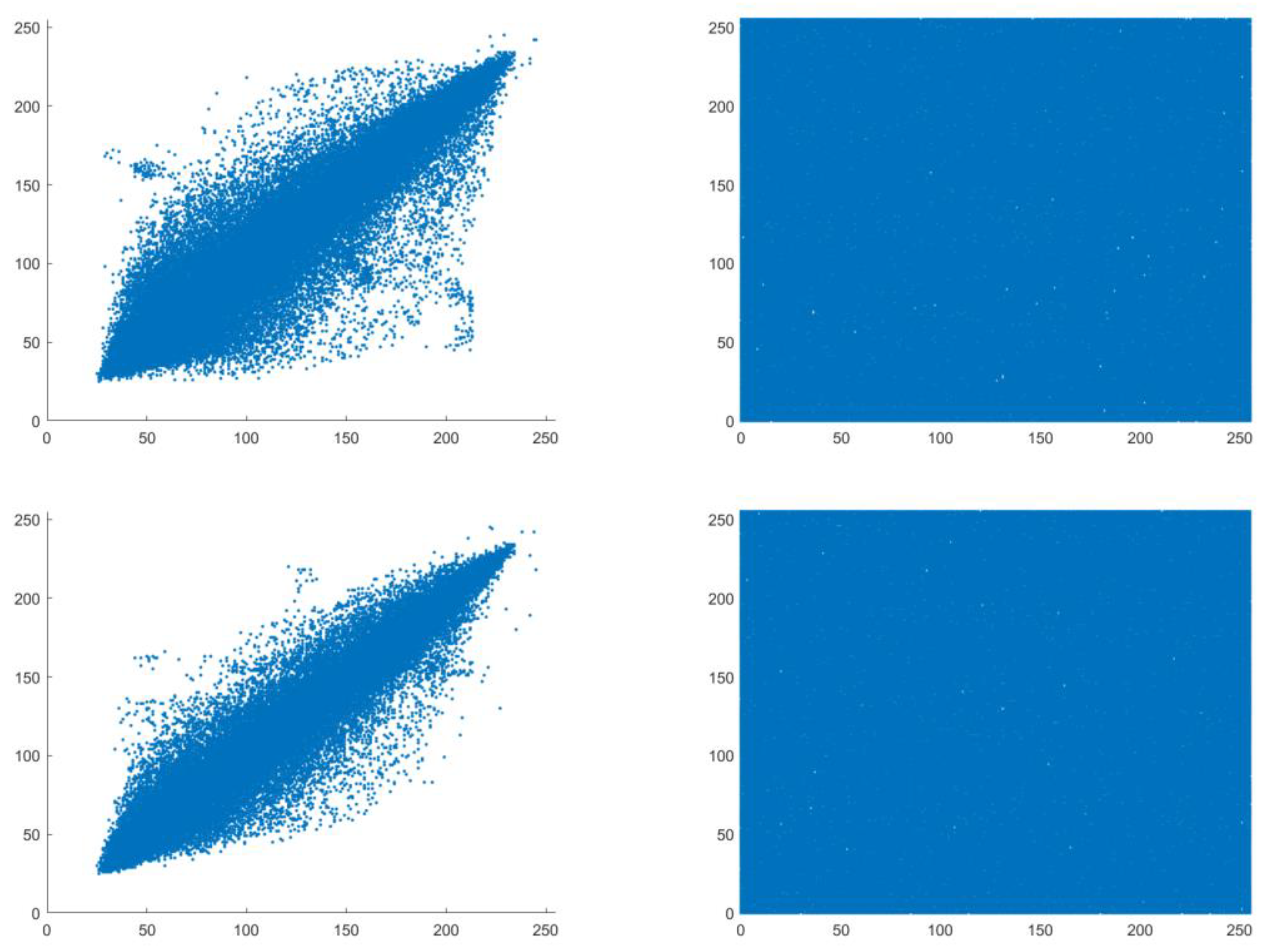
4.2. Correlation Analysis
4.3. Analysis of Differential Attack
4.4. Information Entropy Analysis
4.5. Running Time
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Sandryhaila, A.; Moura, J. Big data analysis with signal processing on graphs: Representation and processing of massive data sets with irregular structure. IEEE Signal Process. Mag. 2014, 31, 80–90. [Google Scholar] [CrossRef]
- Chen, J.; Kenli, L.; Tang, Z.; Bilal, K.; Yu, S.; Weng, C.; Li, K. A parallel random forest algorithm for big data in a spark cloud computing environment. IEEE Trans. Parallel Distrib. Syst. 2017, 28, 919–933. [Google Scholar] [CrossRef]
- Furini, M.; Gaggi, O.; Mirri, S.; Montangero, M.; Pelle, E.; Poggi, F.; Prandi, C. Digital twins and artificial intelligence as Pillars of personalized learning models. Commun. ACM 2022, 65, 98–104. [Google Scholar] [CrossRef]
- Yang, H.; Yin, J.; Yang, Y. Robust image hashing scheme based on low-rank decomposition and path integral LBP. IEEE Access 2019, 7, 51656–51664. [Google Scholar] [CrossRef]
- Sharma, S.; Gupta, V.; Juneja, M. A novel unsupervised multiple feature hashing for image retrieval and indexing (MFHIRI). J. Vis. Commun. Image Represent. 2022, 84, 103467. [Google Scholar] [CrossRef]
- Singh, C.; Sunitha, C.A. Chaotic and Paillier secure image data sharing based on blockchain and cloud security. Expert. Syst. Appl. 2022, 198, 116874. [Google Scholar] [CrossRef]
- Mai, H.E.; Envelope, E.R.; Envelope, I.E.; Envelope, E.S. Proposed hybrid encryption algorithm for robust 3D image communication over wireless channels. Optik 2023, 273, 170205. [Google Scholar]
- Zhu, C.; Sun, K. Chaotic image encryption algorithm by correlating keys with plaintext. China Commun. 2012, 9, 73–79. [Google Scholar]
- Tang, Z.; Yang, Y.; Xu, S.; Yu, C.; Zhang, X. Image encryption with double spiral scans and chaotic maps. Secur. Commun. Netw. 2019, 2019, 8694678. [Google Scholar] [CrossRef]
- Pareek, N.K.; Patidar, V.; Sud, K.K. Image encryption using chaotic logistic map. Image Vis. Comput. 2006, 24, 926–934. [Google Scholar] [CrossRef]
- Zhang, L.; Liao, X.; Wang, X. An image encryption approach based on chaotic maps. Chaos Solitons Fractals 2005, 24, 759–765. [Google Scholar] [CrossRef]
- Elpeltagy, M.S.; Abdelwahab, M.M.; Sayed, M.S. Image Encryption Using Camellia and Chaotic Maps. In Proceedings of the 2015 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), Abu Dhabi, United Arab Emirates, 7–10 December 2015; pp. 209–214. [Google Scholar]
- Kumar, K.; Roy, S.; Rawat, U.; Malhotra, S. IEHC: An efficient image encryption technique using hybrid chaotic map. Chaos Solitons Fractals 2022, 158, 111994. [Google Scholar] [CrossRef]
- Wang, X.Y.; Lei, Y.; Liu, R.; Kadir, A. A chaotic image encryption algorithm based on perceptron model. Nonlinear Dyn. 2010, 62, 615–621. [Google Scholar] [CrossRef]
- Akhshani, A.; Behnia, S.; Akhavan, A.; Hassan, H.A.; Hassan, Z. A novel scheme for image encryption based on 2D piecewise chaotic maps. Opt. Commun. 2010, 283, 3259–3266. [Google Scholar] [CrossRef]
- Chen, Z.; Li, H.; Dong, E.; Du, Y. A Hyper-Chaos Based Image Encryption Algorithm. In Proceedings of the 2010 Second International Conference on Intelligent Human-Machine Systems and Cybernetics, Nanjing, China, 26–28 August 2010; pp. 188–191. [Google Scholar]
- Hua, Z.; Zhou, B.; Zhou, Y. Image Content-Based Encryption Algorithm Using High-Dimensional Chaotic System. In Proceedings of the 2015 International Symposium on Nonlinear Theory and its Applications (NOLTA2015), Hong Kong, China, 1–4 December 2015; pp. 554–557. [Google Scholar]
- Wang, S.; Peng, Q.; Du, B. Chaotic color image encryption based on 4D chaotic maps and DNA sequence. Opt. Laser Technol. 2022, 148, 107753. [Google Scholar] [CrossRef]
- Ye, G.; Jiao, K.; Pan, C.; Huang, X. An effective framework for chaotic image encryption based on 3D logistic map. Secur. Commun. Netw. 2018, 2018, 8402578. [Google Scholar] [CrossRef]
- Gong, L.; Luo, H.; Wu, R.; Zhou, N. New 4D chaotic system with hidden attractors and self-excited attractors and its application in image encryption based on RNG. Phys. A Stat. Mech. Its Appl. 2022, 591, 126793. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y. Image encryption using 2D Logistic-adjusted-Sine map. Inf. Sci. 2016, 339, 237–253. [Google Scholar] [CrossRef]
- Wang, X.; Yang, J. A privacy image encryption algorithm based on piecewise coupled map lattice with multi dynamic coupling coefficient. Inf. Sci. 2021, 569, 217–240. [Google Scholar] [CrossRef]
- Zhu, H.; Zhao, Y.; Song, Y. 2D Logistic-Modulated-Sine-Coupling-Logistic Chaotic Map for Image Encryption. IEEE Access 2019, 7, 14081–14098. [Google Scholar] [CrossRef]
- Zhu, H.; Zhang, X.; Yu, H.; Zhao, C.; Zhu, Z. A Novel Image Encryption Scheme Using the Composite Discrete Chaotic System. Entropy 2016, 18, 276. [Google Scholar] [CrossRef]
- Zhu, H.; Zhang, X.; Yu, H.; Zhao, C.; Zhu, Z. An image encryption algorithm based on compound homogeneous hyper-chaotic system. Nonlinear Dyn. 2017, 89, 61–79. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Huang, H. Cosine-transform-based chaotic system for image encryption. Inf. Sci. 2019, 480, 403–419. [Google Scholar] [CrossRef]
- Gao, Z.; Liu, Z.; Wang, L. An Image Encryption Algorithm Based on the Improved Sine-Tent Map. Discret. Dyn. Nat. Soc. 2021, 2021, 9187619. [Google Scholar] [CrossRef]
- Yadav, A.; Saini, B.; Verma, V.K.; Pal, V. A joint medical image compression and encryption using AMBTC and hybrid chaotic system. J. Discret. Math. Sci. Cryptogr. 2021, 24, 2233–2244. [Google Scholar] [CrossRef]
- Zhang, S.; Liu, L. A novel image encryption algorithm based on SPWLCM and DNA coding. Math. Comput. Simul. 2021, 190, 723–744. [Google Scholar] [CrossRef]
- Wang, X.; Du, X. Pixel-level and bit-level image encryption method based on Logistic-Chebyshev dynamic coupled map lattices. Chaos Solitons Fractals 2022, 155, 111629. [Google Scholar] [CrossRef]
- Basha, S.M.; Mathivanan, P.; Ganesh, A.B. Bit level color image encryption using Logistic-Sine-Tent-Chebyshev (LSTC) map. Optik 2022, 259, 168956. [Google Scholar] [CrossRef]
- Di, H.; Chen, H.; Lingge, J.; Hongwen, Z.; Guangrui, H. Chaotic characteristics of a one-dimensional iterative map with infinite collapses. IEEE Trans. Circuits Syst. I Fundam. Theory Appl. 2001, 48, 900–906. [Google Scholar] [CrossRef]
- Diab, H. An efficient chaotic image cryptosystem based on simultaneous permutation and diffusion operations. IEEE Access 2018, 6, 42227–42244. [Google Scholar] [CrossRef]
- Shahna, K.U.; Mohamed, A. A novel image encryption scheme using both pixel level and bit level permutation with chaotic map. Appl. Soft Comput. 2020, 90, 106162. [Google Scholar] [CrossRef]










| Test Name | p-Value | Result |
|---|---|---|
| Approximate entropy test | 0.9548 | Success |
| Block frequency test | 0.0383 | Success |
| Cumulative sums (forward) test | 0.2631 | Success |
| FFT test | 0.2789 | Success |
| Frequency test | 0.2919 | Success |
| Linear complexity test | 0.8934 | Success |
| Longest runs of one test | 0.4398 | Success |
| Nonoverlapping template matching test | 0.9961 | Success |
| Overlapping template matching test | 0.4771 | Success |
| Binary matrix rank test | 0.9562 | Success |
| Runs test | 0.3959 | Success |
| Serial test | 0.0297 | Success |
| Maurer’s universal statistical test | 0.4439 | Success |
| Random excursion test | 0.3061 | Success |
| Random excursion variant test | 0.0527 | Success |
| Encryption Method (Ciphertext Image) | Histogram Variance |
|---|---|
| [33] (Lena) | 242.4651 |
| [34] (Lena) | 124.6218 |
| [30] (Lena) | 68.9023 |
| Our method (Lena) | 31.5731 |
| Our method (peppers) | 29.7752 |
| Our method (man) | 32.6184 |
| Our method (baboon) | 30.2543 |
| Metric | Our Method | Ref. [33] | Ref. [34] |
|---|---|---|---|
| NPCR | 99.6645 | 99.6052 | 99.6226 |
| UACI | 33.58 | 33.28 | 33.14 |
| Plaintext Image | Our Scheme | Ref. [33] | Ref. [34] |
|---|---|---|---|
| 7.4455 | 7.9986 | 7.9935 | 7.9926 |
| Stage | Lena | Peppers | Man | Baboon |
|---|---|---|---|---|
| encryption | 0.2565 | 0.2779 | 0.2761 | 0.2760 |
| decryption | 0.1566 | 0.1674 | 0.1589 | 0.1498 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, M.; Yang, H. Image Encryption Using a New Hybrid Chaotic Map and Spiral Transformation. Entropy 2023, 25, 1516. https://doi.org/10.3390/e25111516
Jiang M, Yang H. Image Encryption Using a New Hybrid Chaotic Map and Spiral Transformation. Entropy. 2023; 25(11):1516. https://doi.org/10.3390/e25111516
Chicago/Turabian StyleJiang, Mingfang, and Hengfu Yang. 2023. "Image Encryption Using a New Hybrid Chaotic Map and Spiral Transformation" Entropy 25, no. 11: 1516. https://doi.org/10.3390/e25111516
APA StyleJiang, M., & Yang, H. (2023). Image Encryption Using a New Hybrid Chaotic Map and Spiral Transformation. Entropy, 25(11), 1516. https://doi.org/10.3390/e25111516





