Information Hiding in the DICOM Message Service and Upper Layer Service with Entropy-Based Detection
Abstract
1. Introduction
- It shows the existence of ten new covert channels using the DICOM standard
- It categorizes the determined covert channels using the latest version of the hiding patterns taxonomy [10];
- It showcases an entropy-based detection methodology for real scenarios and known covert channels;
- It performs and experimental campaign to show how irregularities in Message ID can reveal when covert traffic is present.
2. Related Work
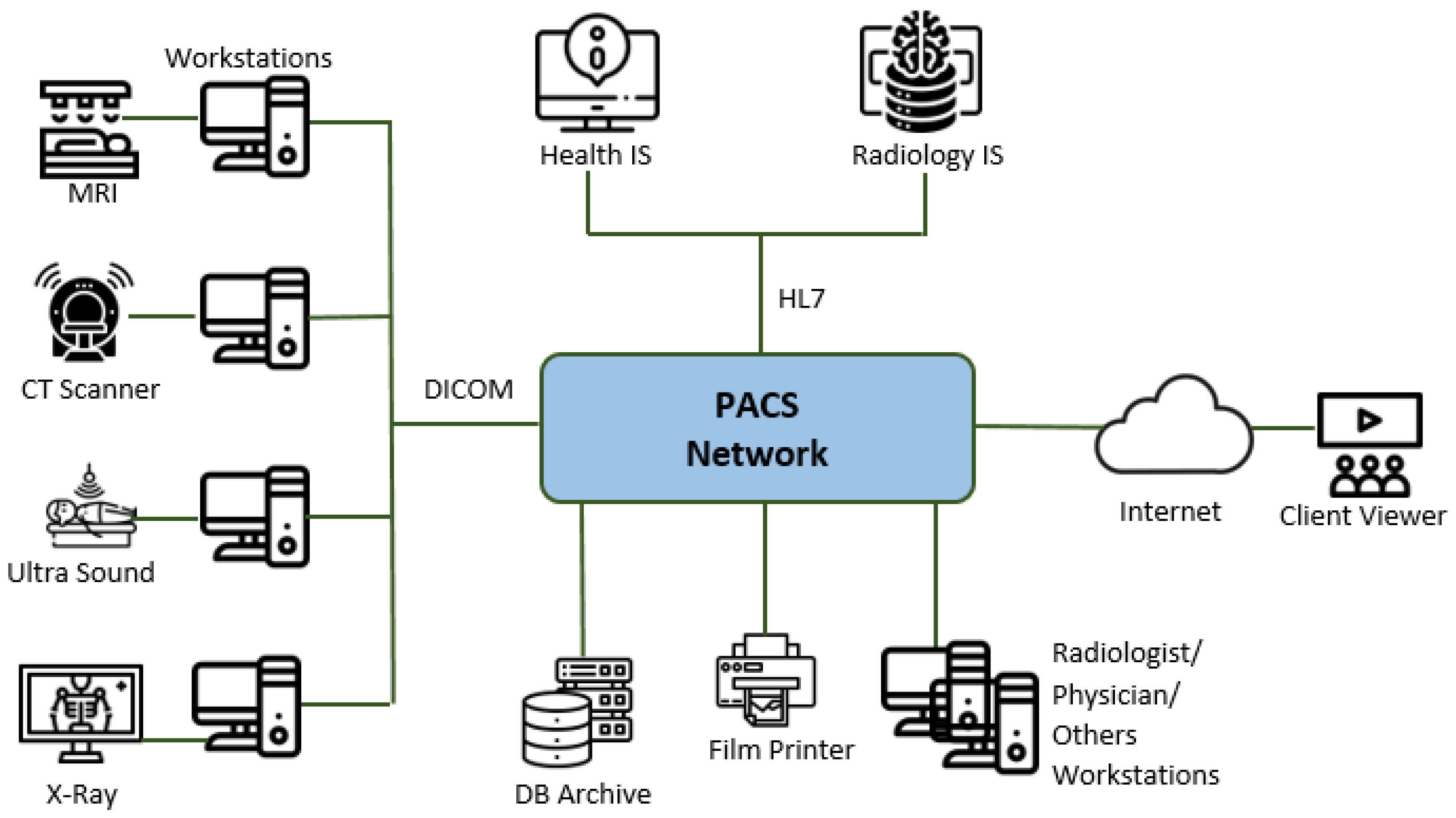
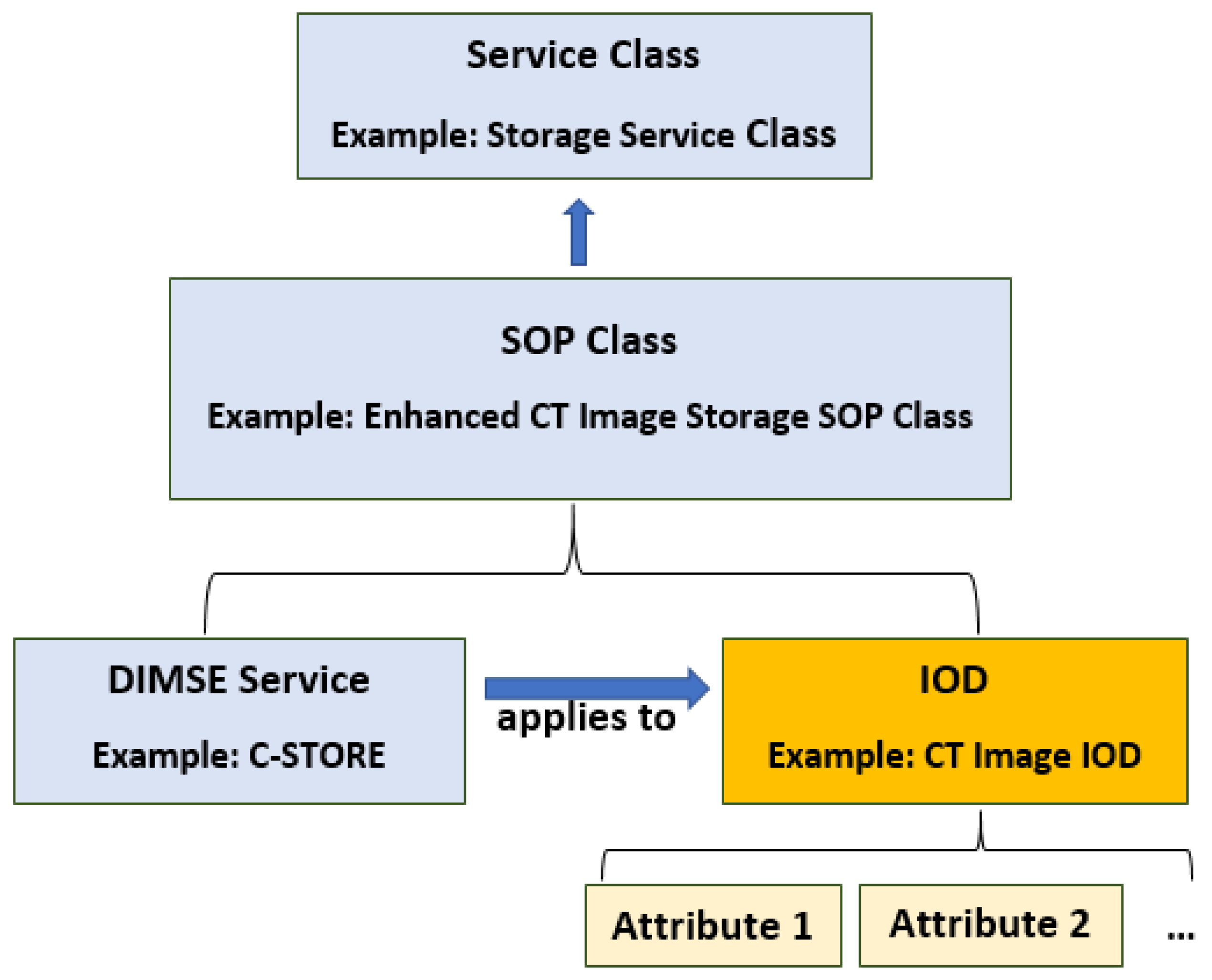
3. DICOM Basics
- DICOM Message Service (PS3.7) and Upper Layer Service (PS3.8);
- DICOM Web Service API and HTTP Service (PS3.18);
- Basic DICOM File Service (PS3.10);
- DICOM Real-Time Communication (PS3.22).
3.1. DICOM Message Service and Upper Layer Service
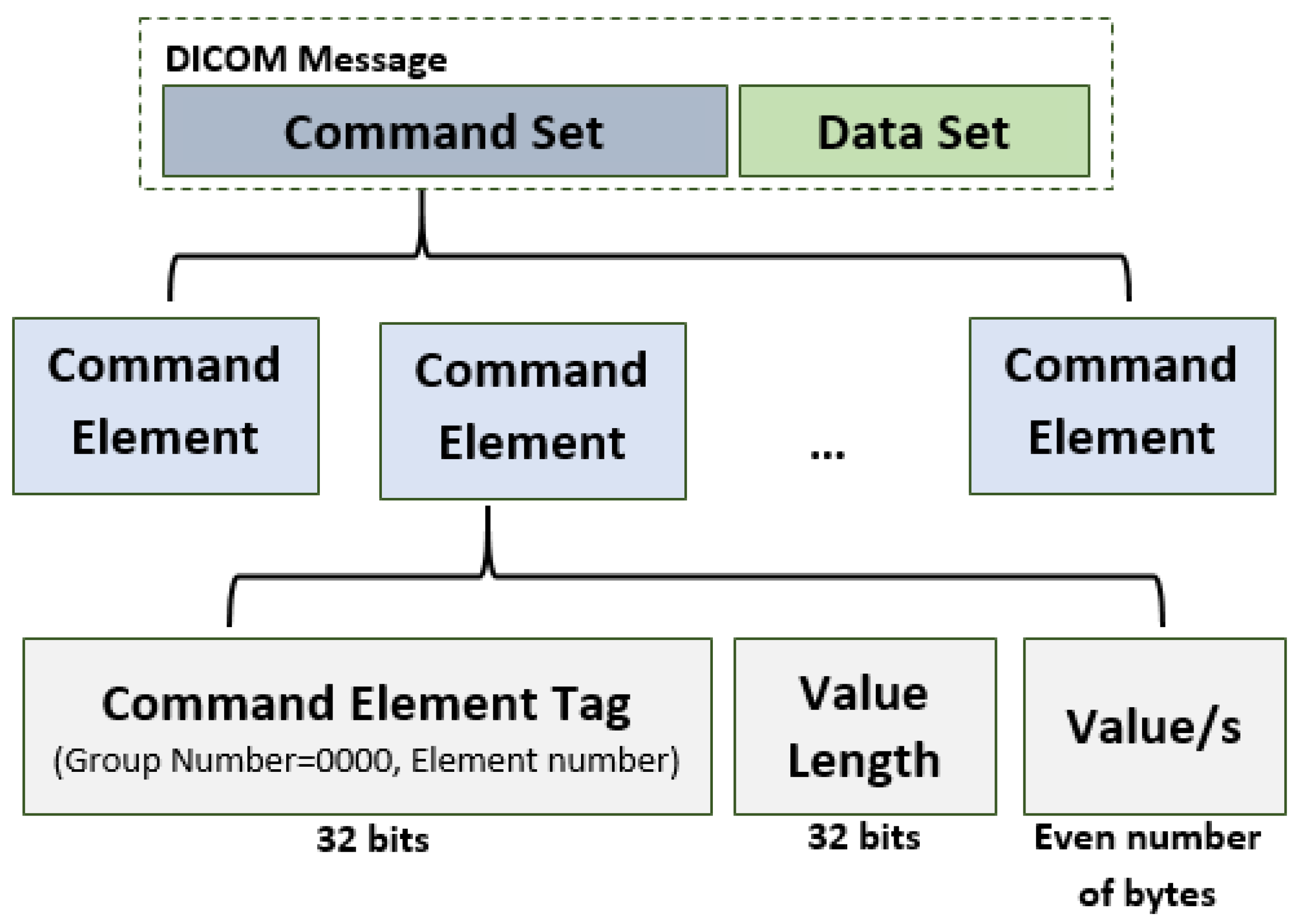
3.1.1. DICOM Messages
- Command Element Tag—an ordered pair of 16-bit unsigned integers (Group Number, Element Number). The Group Number for command element is always 0000;
- Value Length—a 32-bit unsigned integer representing the explicit length of the Value field in bytes;
- Value/s—an even number of bytes containing the Value(s) of the command element.
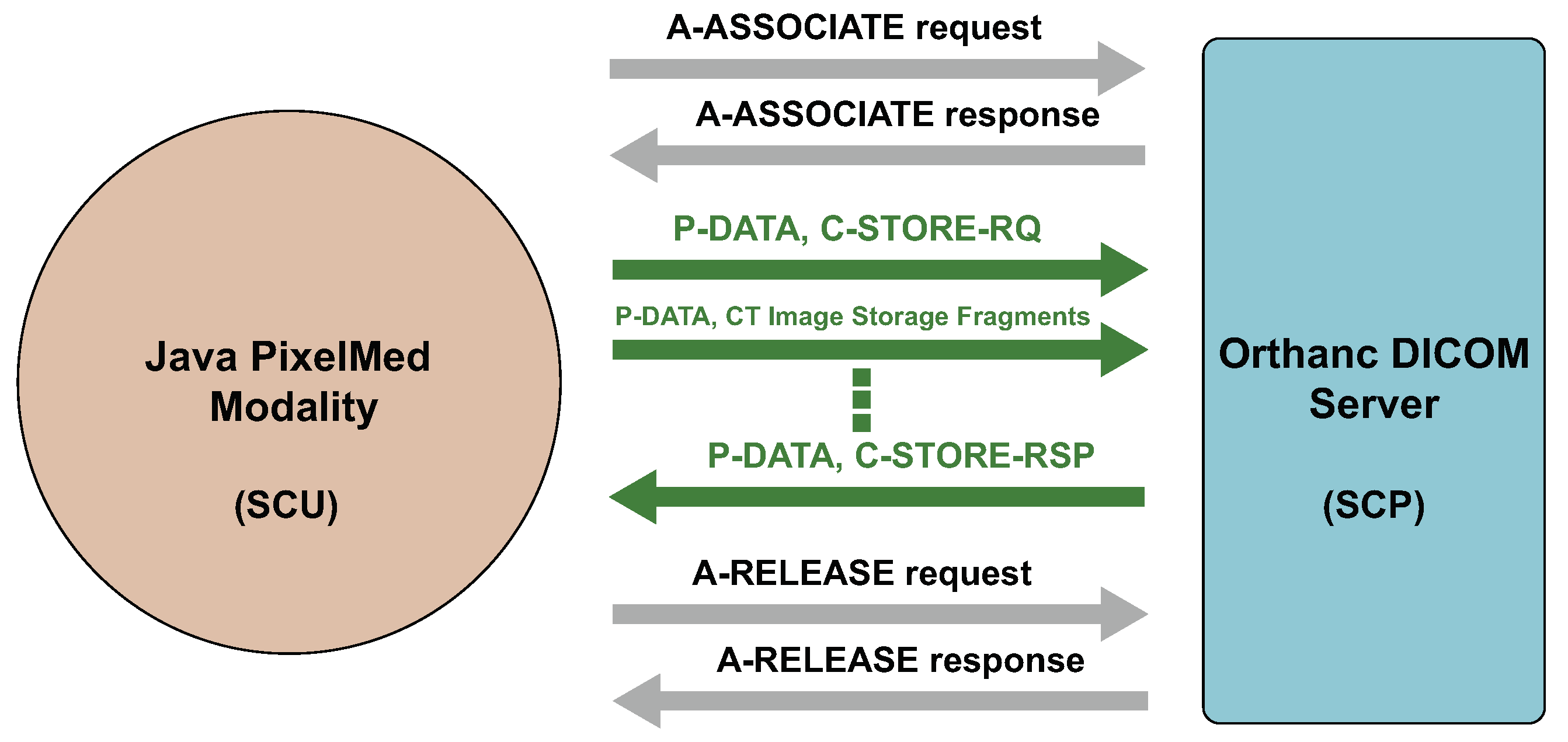
3.1.2. Association Establishment and Termination
4. New Covert Channels in DICOM
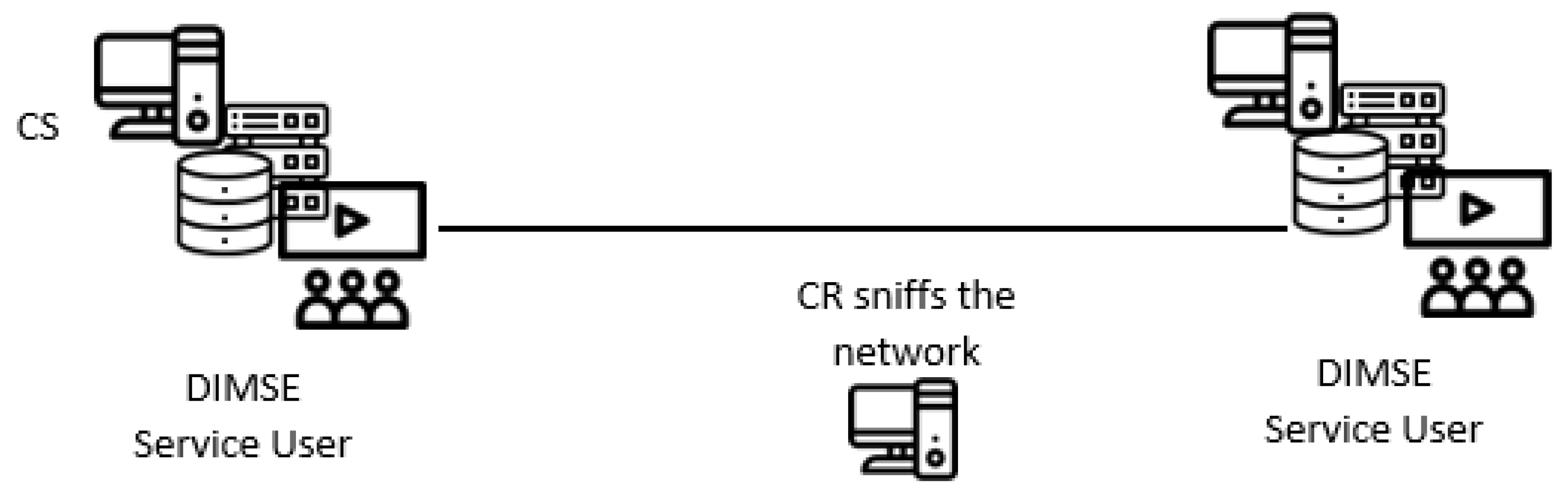
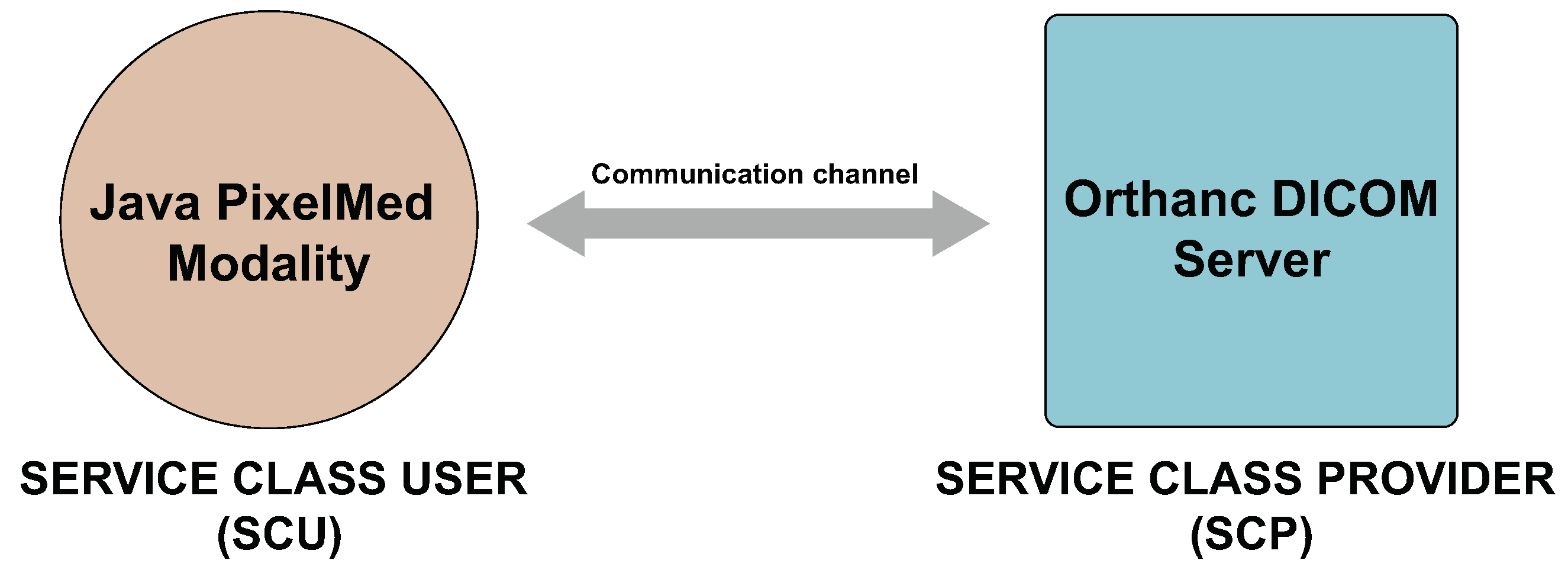
4.1. System Model
4.2. Covert Channels with Different Command Elements
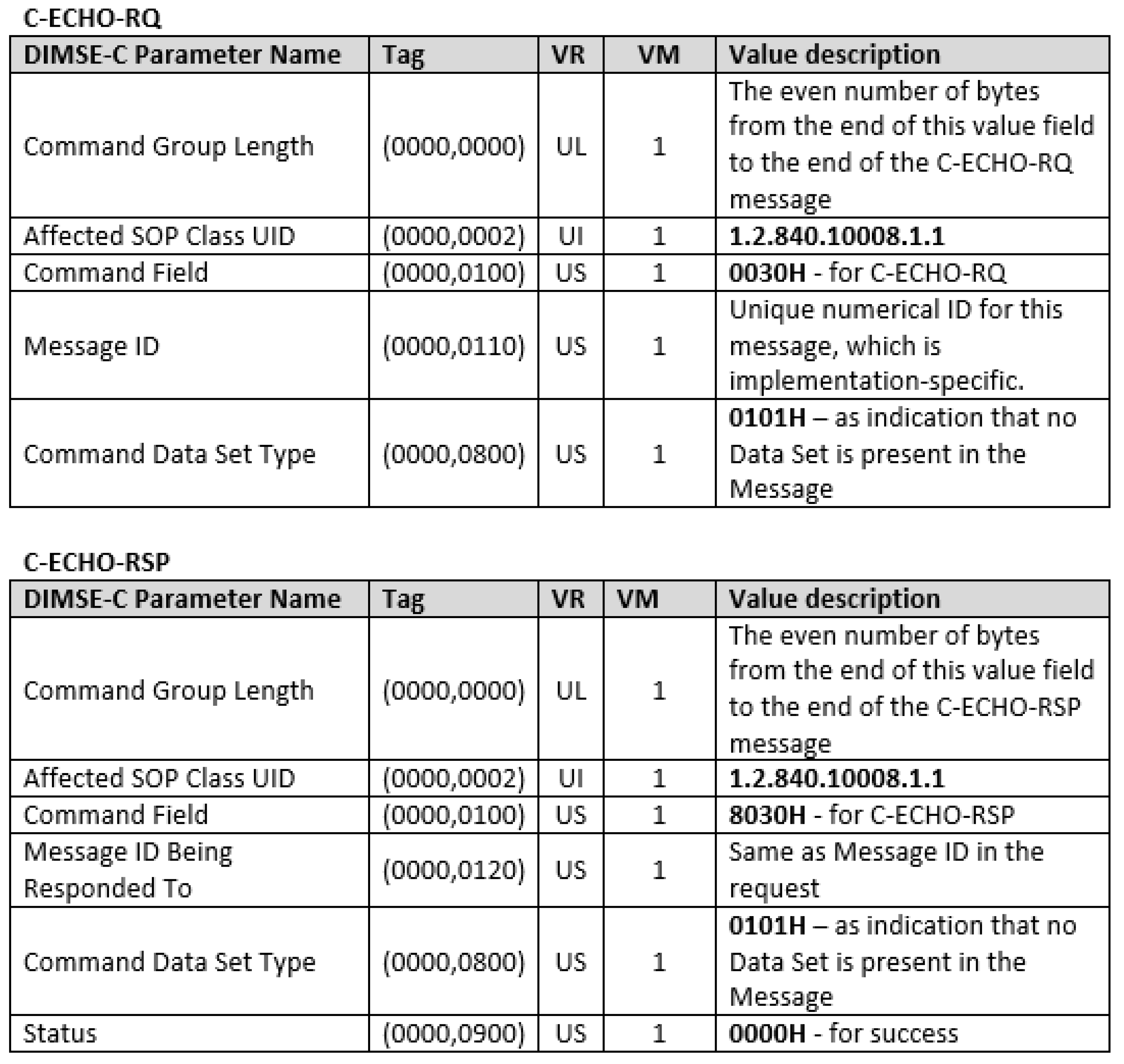
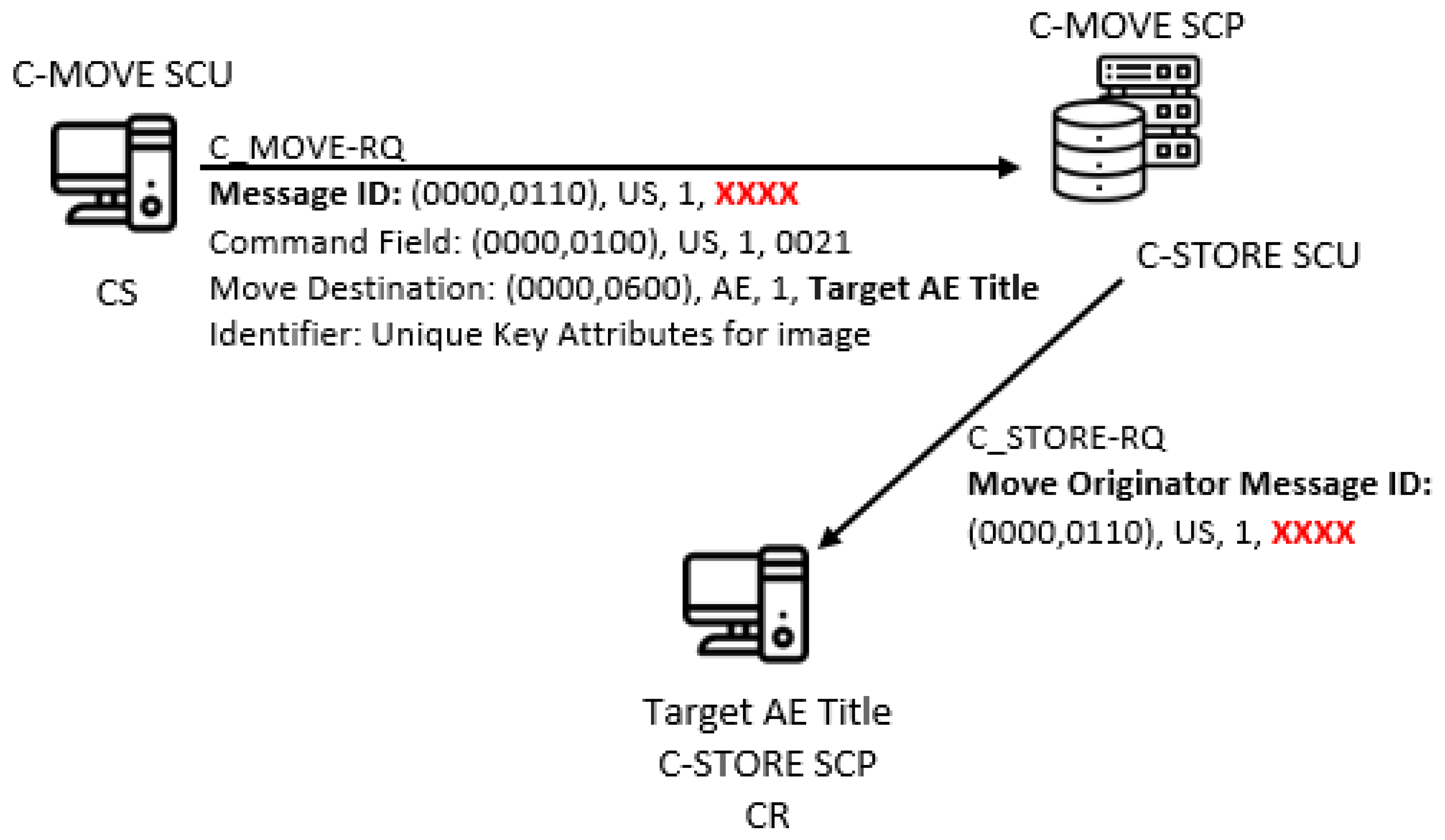
- Message ID—The request messages for each DIMSE service contain a mandatory Message ID command element, which is unique within the scope of a given Association. Its tag is equal to (0000,0110), and it contains a randomly generated and implementation-specific numerical 16-bit value (its VR is US). All response messages contain a field Message ID Being Responded To, which should be the same with the Message ID value from the appropriate request message. So one can hide 16 bits in the value field of Message ID per a DIMSE request message.Since the Message ID field is randomized, the embedding and representation pattern are both “Random State/Value Modulation” (EN4.2 and RN4.2n) [10].
- Command Data Set Type—The request or response messages for each DIMSE service contain a mandatory Command Data Set Type command element, with a tag equal to (0000,0800) and VR equal to US (with a fixed length of 2B). Its role is to indicate that a data set is present in the Message. It should be set to any value other than 0101H (Null), if there is a Data Set in the message (the previous versions of DICOM standard required this value to be set to 0102H). DIMSE services C-ECHO and N-DELETE do not have data set in their request and response messages. So one can hide 16 bits (different of Null) in the value field of Command Data Set Type per a DIMSE request message with a data set.The utilized field’s nature is almost entirely random (the value 0h cannot be used), so this covert channel is a form of the “State/Value Modulation” pattern (EN4 and RN4n), in particular it can be considered as a form of the sub-pattern “Random State/Value Modulation” (EN4.2 and RN4.2n) [10].
- Priority—The request messages for the C-STORE, C-FIND, C-GET and C-MOVE operations contain a mandatory Priority command element, with a tag equal to (0000,0700) and VR equal to US (with a fixed length of 2B). Only three value are allowed: 0002H (Low), 0000H (Medium) and 0001H (High). So, one can create a 1-bit covert channel by using one of the values to represent a binary ‘1’, and other of the value to represent binary ‘0’.A semantically relevant field with a set of allowed values is modified which renders this covert channel as a variant of the “State/Value Modulation” pattern (EN4 and RN4n) [10].
- Attribute Identifier List—The request messages for the N-GET operation contain an Attribute Identifier List command element, with the tag being equal to (0000,1005) and VR equal to AT. The value field contains an Attribute Tag for each of the n attributes applicable to this operation. So, one can create a 1-bit covert channel by using even values of n to represent a binary ‘1’, and odd values of n to represent a binary ‘0’.Again, this covert channel is a form of the “State/Value Modulation” pattern (EN4 and RN4n).
- Some command elements have application-specific code values, like Event Type ID in N-EVENT-REPORT request, and Action Type ID in N-ACTION request, so they can be used for encoding hiding bits. All these values are 16 bits long (their VR is US). Their utilization would be a form of the “State/Value Modulation” (EN4 and RN4n), too.
- Some command elements have textual values, like Move Destination in C-MOVE request and Move Originator Application Entity Title in C-STORE request which are AE, and Error Comment in some Status types of responses, which is LO. They can be used for hiding bits at the beginning and at the end of the string by using CC with whitespaces, cf. [5]. This channel is a form of the pattern EN3 “Elements/Features Enumeration” (EN3 and RN3n).
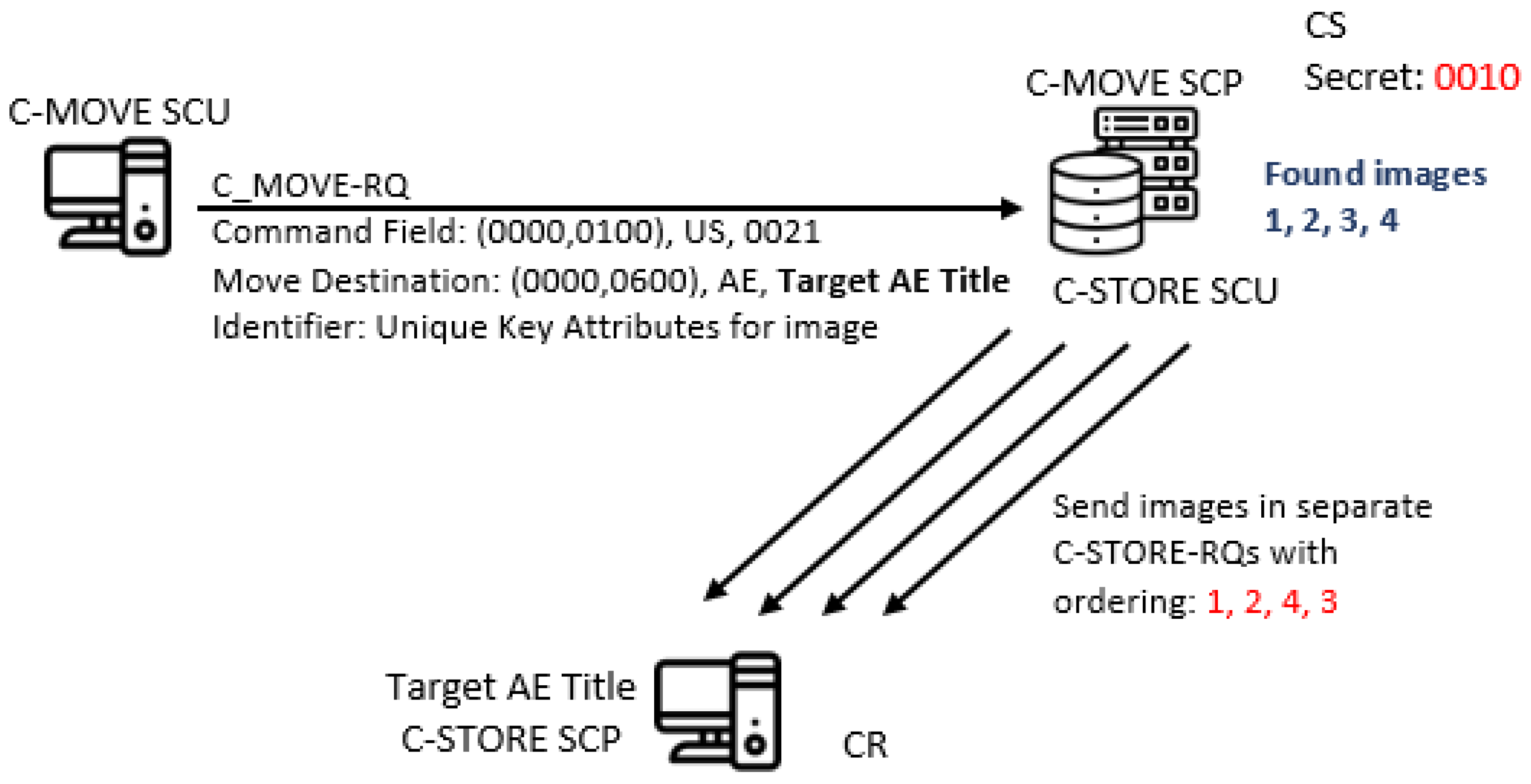
4.3. Covert Channel by Image Ordering in C-GET and C-MOVE Services
4.4. Covert Channel by Using Status Command Element in Responses
- Sending a response message with Status value of 0210H after any DIMSE request message, except for C-FIND, can represent a binary ‘1’;
- Sending a response message with Status value different from 0210H (usually 0000H) after any DIMSE request message, except for C-FIND, can represent a binary ‘0’.
4.5. Covert Channel by Using Cancellation Messages
- Sending a cancellation message immediately after C-FIND, C-MOVE or C-GET request messages can represent a binary ‘1’;
- Not sending a cancellation message immediately after C-FIND, C-MOVE or C-GET request messages can represent a binary ‘0’.
4.6. Covert Channel by Using Message ID in C-MOVE Service
5. Metrics and Countermeasures
5.1. Bandwidth Estimation
5.2. Robustness
5.3. Undetectability and Potential Countermeasures
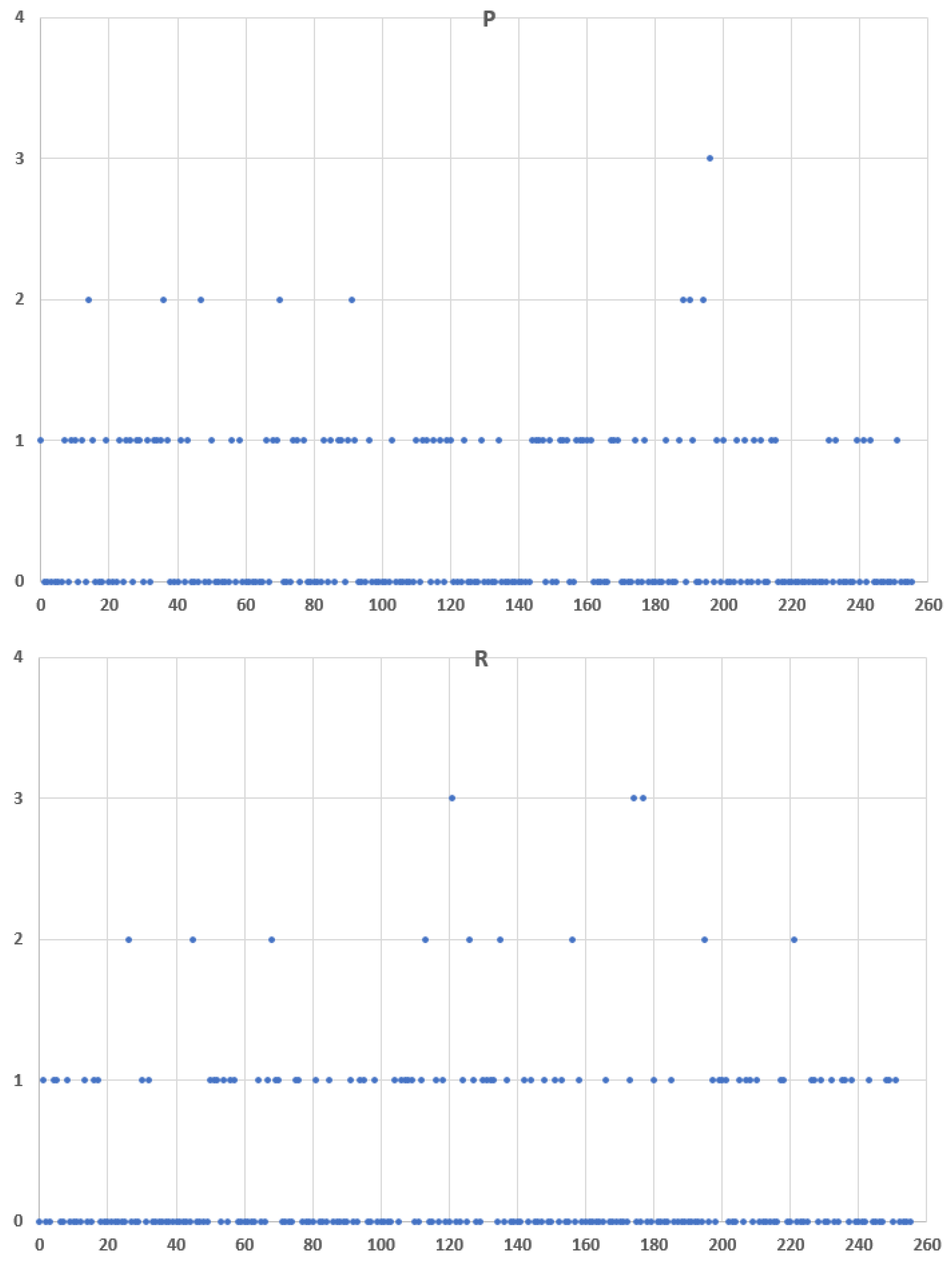
6. Entropy-Based Detection Methodology for Real Scenarios and Known Covert Channels
- Step 1. Choose the property which the warden wants to protect and which is potentially used by the covert channel (e.g., Message ID, Command Data Set Type, Status, Priority) and choose the network flow that it wants to examine.
- Step 2. Perform the following:
- –
- For a CC where the hidden bits are encoded directly into the values (e.g., Message ID, Command Data Set Type), take the consecutive property values from the suspected network flow, and from them construct the array of consecutive N-bit words. Calculate the probability distribution Q of elements in this array.
- –
- For a k-bit CC where k-bit values correspond to different states (e.g., Priority, Status), take the property’s events that correspond to different states and assign proper k-bit values (binary ‘1’ and ‘0’ for 1-bit CC) from the suspected traffic form the string of appropriate k-bit values and divide the string into an array of consecutive N-bit words. Calculate the probability distribution Q of elements in this array.
- Step 3. Perform the same procedure but for the pre-recorded regular traffic, and calculate the probability distribution P of elements in the obtained array. Calculate the entropy of P.
- Step 4. Calculate the cross-entropy , and compare it with the entropy of P. If there is a significant difference, the suspected network flow is probably used for clandestine communication.
Experimental Evaluation
- Scenario with legitimate traffic
- Scenario with implemented covert channel—sending an ASCII covert message
- Scenario with implemented covert channel—sending an AES encrypted covert message
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Conflicts of Interest
Abbreviations
| ACR | American College of Radiology |
| AE | Application Entity |
| AES | Advanced Encryption Standard |
| AT | Attribute Tag |
| CC | Covert Channel |
| CR | Covert Receiver |
| CS | Covert Sender |
| CT | Computed Tomography |
| DICOM | Digital Imaging and COmmunication in Medicine |
| DIMSE | DICOM Message Service Elements |
| DIMSE-C | DIMSE Composite |
| DIMSE-N | DIMSE Normalized |
| EC2 | Elastic Compute Cloud |
| GAN | Generative Adversarial Networks |
| HIS | Hospital Information System |
| HL7 | Health Level Seven |
| ID | Identifier |
| IODs | Information Object Definitions |
| LO | Long String |
| LSB | Least Significant Bit |
| MR | Magnetic Resonance |
| MRI | Magnetic Resonance Imaging |
| NEMA | National Electrical Manufacturers Association |
| PACS | Picture Archiving and Communication Systems |
| PET | Positron Emission Tomography |
| RIS | Radiology Information System |
| RQ | Request |
| RSP | Response |
| SCPs | Service Class Providers |
| SCUs | Service Class Users |
| SOPs | Service-Object Pairs |
| UI VR | Unique Identifier Value Representation |
| UID | Unique Identifier |
| UL | Unsigned Long |
| US | Unsigned Short |
| VM | Value Multiplicity |
| VR | Value Representation |
References
- Mann, K.S.; Bansal, E.A. HIS Integration Systems using Modality Worklist and DICOM. Procedia Comput. Sci. 2014, 37, 16–23. [Google Scholar] [CrossRef][Green Version]
- Pianykh, O.S. Digital Imaging and Communications in Medicine (DICOM): A Practical Introduction and Survival Guide, 2nd ed.; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Mirsky, Y.; Mahler, T.; Shelef, I.; Elovici, Y. CT-GAN: Malicious Tampering of 3D Medical Imagery using Deep Learning. In Proceedings of the 28th USENIX Conference on Security Symposium, Santa Clara, CA, USA, 14–16 August 2019; pp. 461–478. [Google Scholar]
- Duggal, A. Is There a Doctor in The House? Hacking Medical Devices and Healthcare Infrastructure. In Proceedings of the HITBSecConf 2017, Amsterdam, The Netherlands, 10–14 July 2017. [Google Scholar]
- Mileva, A.; Caviglione, L.; Velinov, A.; Wendzel, S.; Dimitrova, V. Risks and Opportunities for Information Hiding in DICOM Standard, Article No. 74. In Proceedings of the ARES 2021, Vienna, Austria, 17–20 August 2021. [Google Scholar]
- Caviglione, L. Trends and Challenges in Network Covert Channels Countermeasures. Appl. Sci. 2021, 11, 1641. [Google Scholar] [CrossRef]
- Mazurczyk, W.; Wendzel, S.; Zander, S.; Houmansadr, A.; Szczypiorski, K. Information Hiding in Communication Networks. Fundamentals, Mechanisms, and Applications; John Wiley & Sons: Hoboken, NJ, USA, 2016. [Google Scholar] [CrossRef]
- Mileva, A.; Panajotov, B. Covert channels in TCP/IP protocol stack-extended version. Open Comput. Sci. 2014, 4, 45–66. [Google Scholar] [CrossRef]
- Wendzel, S.; Zander, S.; Fechner, B.; Herdin, C. Pattern-based survey and categorization of network covert channel techniques. ACM Comput. Surv. (CSUR) 2015, 47, 2684195. [Google Scholar] [CrossRef]
- Wendzel, S.; Caviglione, L.; Mazurczyk, W.; Mileva, A.; Dittmann, J.; Krätzer, C.; Lamshöft, K.; Vielhauer, C.; Hartmann, L.; Keller, J.; et al. A Revised Taxonomy of Steganography Embedding Patterns. In Proceedings of the 16th International Conference on Availability, Reliability and Security (ARES 2021), Vienna, Austria, 17–20 August 2021. [Google Scholar] [CrossRef]
- Beek, C. McAfee Researchers Find Poor Security Exposes Medical Data to Cybercriminals. McAfee Blogs. 2018. Available online: https://securingtomorrow.mcafee.com/otherblogs/mcafee-labs/mcafee-researchers-findpoor-security-exposes-medical-data-tocybercriminals/ (accessed on 17 February 2021).
- Desjardins, B.; Mirsky, Y.; Ortiz, M.P.; Glozman, Z.; Tarbox, L.; Horn, R.; Horii, S.C. DICOM images have been hacked! Now what? Am. J. Roentgenol. 2020, 214, 727–735. [Google Scholar] [CrossRef] [PubMed]
- Harrison, A.S.; Sullivan, P.; Kubli, A.; Wilson, K.M.; Taylor, A.; DeGregorio, N.; Riggs, J.; Werner-Wasik, M.; Dicker, A.; Vinogradskiy, Y. How to Respond to a Ransomware Attack? One Radiation Oncology Department’s Response to a Cyber-Attack on Their Record and Verify System. Pract. Radiat. Oncol. 2021. [Google Scholar] [CrossRef] [PubMed]
- Girdhar, A.; Kumar, V. Digital image steganography: Survey and analysis of current methods. IET Image Process. 2018, 12, 1–10. [Google Scholar] [CrossRef]
- Kadhim, I.J.; Premaratne, P.; Vial, P.J.; Halloran, B. Comprehensive survey of image steganography: Techniques, Evaluations, and trends in future research. Neurocomputing 2019, 335, 299–326. [Google Scholar] [CrossRef]
- Sahu, A.K.; Swain, G. An Optimal Information Hiding Approach Based on Pixel Value Differencing and Modulus Function. Wirel. Pers. Commun. 2019, 108, 159–174. [Google Scholar] [CrossRef]
- Sahu, A.K.; Swain, G. High fidelity based reversible data hiding using modified LSB matching and pixel difference. J. King Saud Univ.—Comput. Inf. Sci. 2019. [Google Scholar] [CrossRef]
- Abd-Eldayem, M.M. A proposed security technique based on watermarking and encryption for digital imaging and communications in medicine. Egypt. Inform. J. 2013, 14, 1–13. [Google Scholar] [CrossRef]
- Tan, C.K.; Ng, J.C.; Xu, X.; Poh, C.L.; Guan, Y.L.; Sheah, K. Security Protection of DICOM Medical Images Using Dual-Layer Reversible Watermarking with Tamper Detection Capability. J. Digit. Imaging 2011, 24, 528–540. [Google Scholar] [CrossRef] [PubMed]
- Mantos, P.L.K.; Maglogiannis, I. Sensitive Patient Data Hiding using a ROI Reversible Steganography Scheme for DICOM Images. J. Med. Syst. 2016, 40, 156. [Google Scholar] [CrossRef] [PubMed]
- Bidgood, W.D.; Horii, S.C.; Prior, F.W.; Syckle, D.E.V. Understanding and Using DICOM, the Data Interchange Standard for Biomedical Imaging. J. Am. Med. Inform. Assoc. 1997, 4, 199–212. [Google Scholar] [CrossRef] [PubMed]
- Shannon, C. A mathematical theory of communication. Bell Syst. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Sanders, C.; Valletta, J.; Yuan, B.; Johnson, D.; Lutz, P. Employing Entropy in the Detection and Monitoring of Network Covert Channels. In Proceedings of the 2012 International Conference on Security and Management, Jaipur, India, 22–27 October 2012. [Google Scholar]
- Chow, J.; Li, X.; Mountrouidou, X. Raising Flags: Detecting Covert Storage Channels Using Relative Entropy. In Proceedings of the IEEE International Conference on Intelligence and Security Informatics (ISI), Beijing, China, 22–24 July 2017. [Google Scholar]
- Gianvecchio, S.; Wang, H. An Entropy-Based Approach to Detecting Covert Timing Channels. IEEE Trans. Dependable Secur. Comput. 2007, 4, 280–294. [Google Scholar] [CrossRef]
- Reeves, A.P.; Xie, Y.; Liu, S. Large-scale image region documentation for fully automated image biomarker algorithm development and evaluation. J. Med. Imaging 2017, 4, 024505. [Google Scholar] [CrossRef] [PubMed][Green Version]




| Name | Group | Type | Description |
|---|---|---|---|
| C-STORE | DIMSE-C | operation | It allows SCU to send a Composite SOP instance to an SCP, for SCP to store it |
| C-GET | DIMSE-C | operation | It allows SCU to fetch one or more Composite SOP instances from an SCP, based upon the attributes supplied by the SCU |
| C-MOVE | DIMSE-C | operation | It allows SCU to move one or more Composite SOP instances from an SCP, to a third party AE (often SCU itself), based upon the attributes supplied by the SCU |
| C-FIND | DIMSE-C | operation | It allows SCU to send attribute string that is matched against the attributes of SOP instances managed by the SCP. SCP returns for each match a list of requested attributes and their values. |
| C-ECHO | DIMSE-C | operation | It allows SCU to verify end-to-end communications with an SCP |
| N-EVENT-REPORT | DIMSE-N | notification | It allows SCU to report an event about a SOP instance to an SCP |
| N-GET | DIMSE-N | operation | It allows SCU to request the retrieval of information from an SCP |
| N-SET | DIMSE-N | operation | It allows SCU to request the modification of information by an SCP |
| N-ACTION | DIMSE-N | operation | It allows SCU to request an SCP to perform an action |
| N-CREATE | DIMSE-N | operation | It allows SCU to request an SCP to create an instance of a SOP Class |
| N-DELETE | DIMSE-N | operation | It allows SCU to request an SCP to delete an instance of a SOP Class |
| CC | System Sub−Model | Embedding Pattern | Representation Pattern | Bits per Service Message | DIMSE Services | Message Type |
|---|---|---|---|---|---|---|
| CC1.1 | DBasic, DPassive | EN4.2 | RN4.2n | 16 | All | Request |
| CC1.2 | DBasic, DPassive | EN4.2 | RN4.2n | 16 | All | Request\response |
| CC1.3 | DBasic, DPassive | EN4 | RN4n | 1 | C-STORE, C-FIND, C-GET, C-MOVE | Request |
| CC1.4 | DBasic, DPassive | EN4 | RN4n | 1 | N-GET | Request |
| CC1.5 | DBasic, DPassive | EN4 | RN4n | 16 | N-EVENT-REPORT, N-ACTION | Request |
| CC1.6 | DBasic, DPassive | EN3 | RN3n | 1 | C-MOVE, C-STORE or All | Request or response |
| CC2 | DBasic, DPassive | EN2 | RN2n | C-GET, C-MOVE with consecutive C-STORE | Request | |
| CC3 | DBasic, DPassive | EN4 | RN4n | 1 | All without C-FIND | Response |
| CC4 | DBasic, DPassive | ET2 | RT2n | 1 | C-FIND, C-MOVE and C-GET | Cancellation message request |
| CC5 | Indirect | EN4.2 | RN4.2n | 16 | C-MOVE with consecutive C-STORE | Request followed by response |
| Modality Scan/Exam | Average Duration | Average No. of Scans per Hour |
|---|---|---|
| Diagnostic X-ray exam | 15 min | 4 |
| MRI scan | 45–60 min per body part | 1.33–1 |
| CT scan | 15 min | 4 |
| PET/CT scan | 120 min | 0.5 |
| Ultrasound exam | 30–60 min | 2–1 |
| US Hysterosonogram exam | 45–60 min | 1.33–1 |
| Arthrogram exam | 45 min | 1.33 |
| Myelogram exam | 60 min | 1 |
| Discogram exam | 120 min | 0.5 |
| 1.9375 | 0.4214 | 0.1214 | 0.4059 |
| 1.9029 | 0.5340 | 0.1765 | 0.4551 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mileva, A.; Velinov, A.; Dimitrova, V.; Caviglione, L.; Wendzel, S. Information Hiding in the DICOM Message Service and Upper Layer Service with Entropy-Based Detection. Entropy 2022, 24, 176. https://doi.org/10.3390/e24020176
Mileva A, Velinov A, Dimitrova V, Caviglione L, Wendzel S. Information Hiding in the DICOM Message Service and Upper Layer Service with Entropy-Based Detection. Entropy. 2022; 24(2):176. https://doi.org/10.3390/e24020176
Chicago/Turabian StyleMileva, Aleksandra, Aleksandar Velinov, Vesna Dimitrova, Luca Caviglione, and Steffen Wendzel. 2022. "Information Hiding in the DICOM Message Service and Upper Layer Service with Entropy-Based Detection" Entropy 24, no. 2: 176. https://doi.org/10.3390/e24020176
APA StyleMileva, A., Velinov, A., Dimitrova, V., Caviglione, L., & Wendzel, S. (2022). Information Hiding in the DICOM Message Service and Upper Layer Service with Entropy-Based Detection. Entropy, 24(2), 176. https://doi.org/10.3390/e24020176







