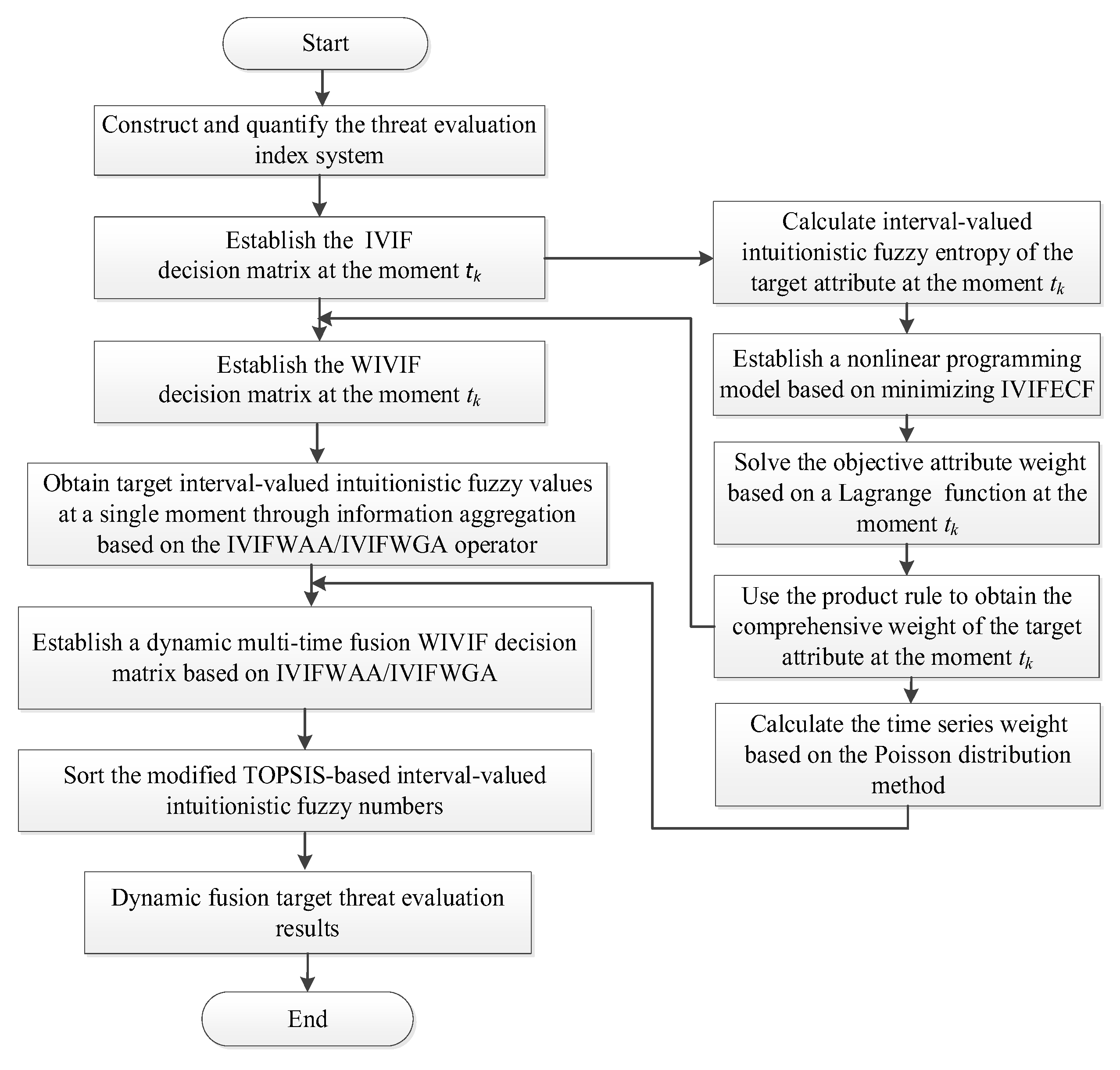
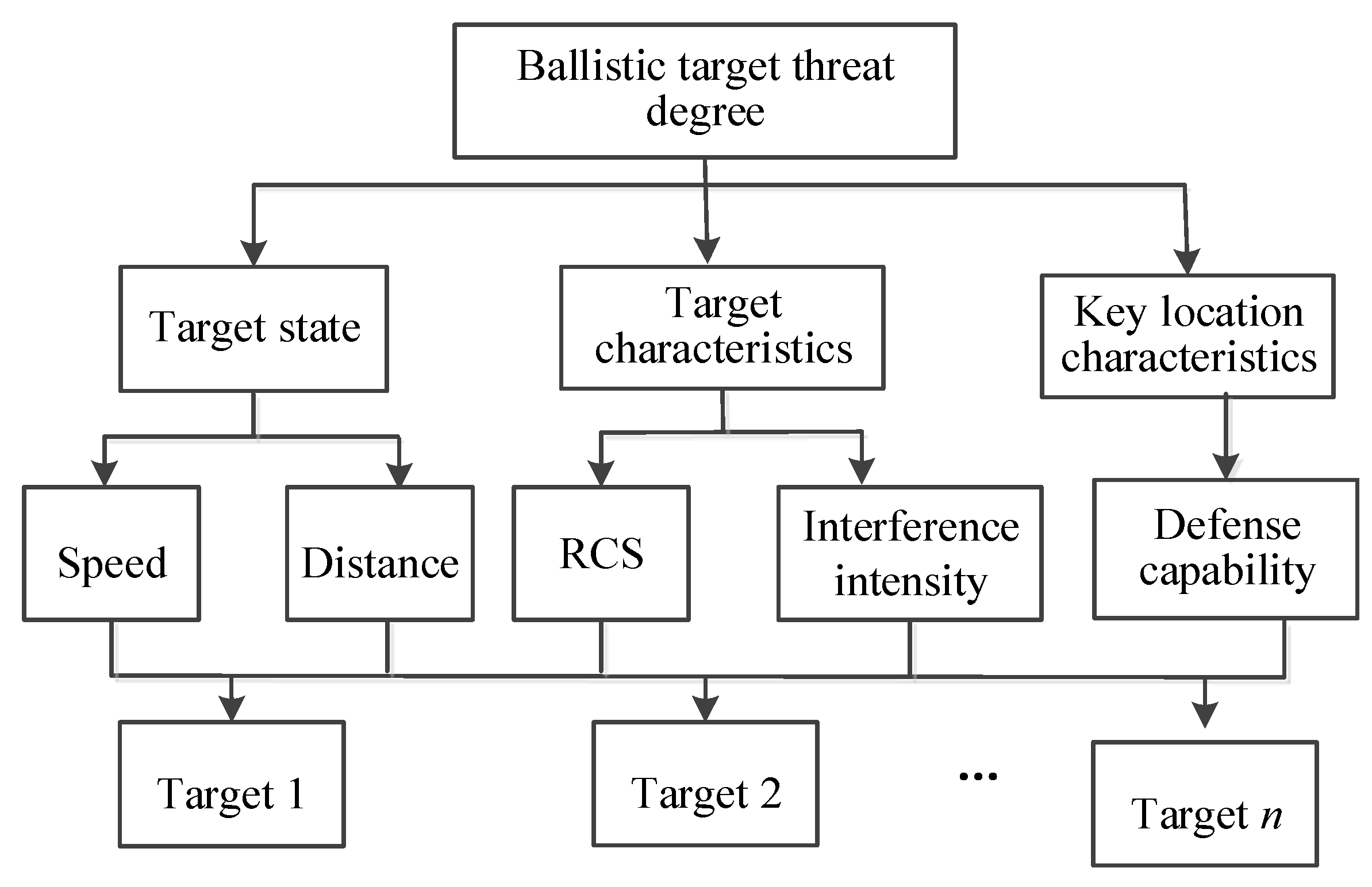
Step 3: Using Equation (19), we obtain the WIVIF decision matrix
of experts
,
,
at
.
Step 4: Use
and the IVIFWAA operator to aggregate the assessment results of each solution for each attribute, and calculate the WIVIF decision matrix
of three experts at
using Equations (20)–(23).
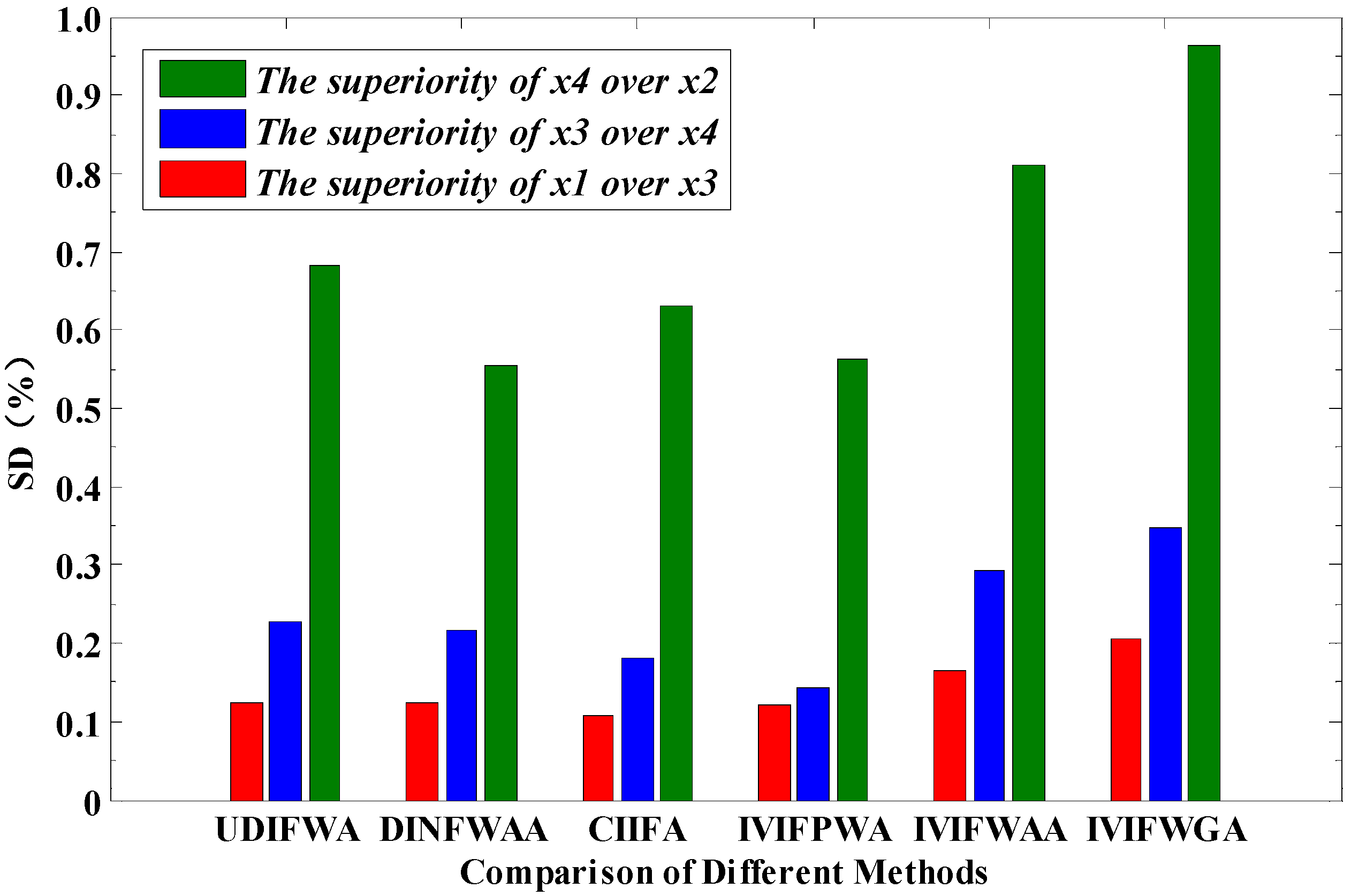
Specifically, according to Equation (36), the positive ideal distance between target and is calculated as follows: