APR-QKDN: A Quantum Key Distribution Network Routing Scheme Based on Application Priority Ranking
Abstract
1. Introduction
- (1)
- Data processing: During packet forwarding, classical network routing only needs to read the address field of the packet and the locally stored routing table, whereas trusted relay-based QKD network routing also needs to encrypt and decrypt the information carried in the packets, which has a much higher data processing overhead.
- (2)
- Forwarding capacity: The forwarding capacity of classical network routing depends mainly on the network bandwidth and is relatively fixed, while the forwarding capacity of trusted relay-based QKD network routing is also affected by the number of quantum keys stored inside the node and the associated links, so it is dynamically changing.
- (3)
- Success rate: The success rate of classical network routing is mainly influenced by network congestion, while the success rate of trusted relay-based QKD network routing is influenced by both the classical channel bandwidth and the quantum channel bandwidth.
- Considering the different importance and communication urgency of various applications in the actual use, we set a priority judgment criterion for application key requests in the scheme to quantify the priority of requests being processed.
- For specific scenarios of high concurrency, a fixed amount of secret key requests of applications reached in a short period are ranked by priority rather than merely relying on the order in which the key requests are reached. The requests will be processed later according to the ranking result.
- Depending on the permissible delay range for applications, secret key requests of applications with route failure are given a delayed retry instead of simply outright rejection and excessive infinite waiting.
2. QKD Network Model
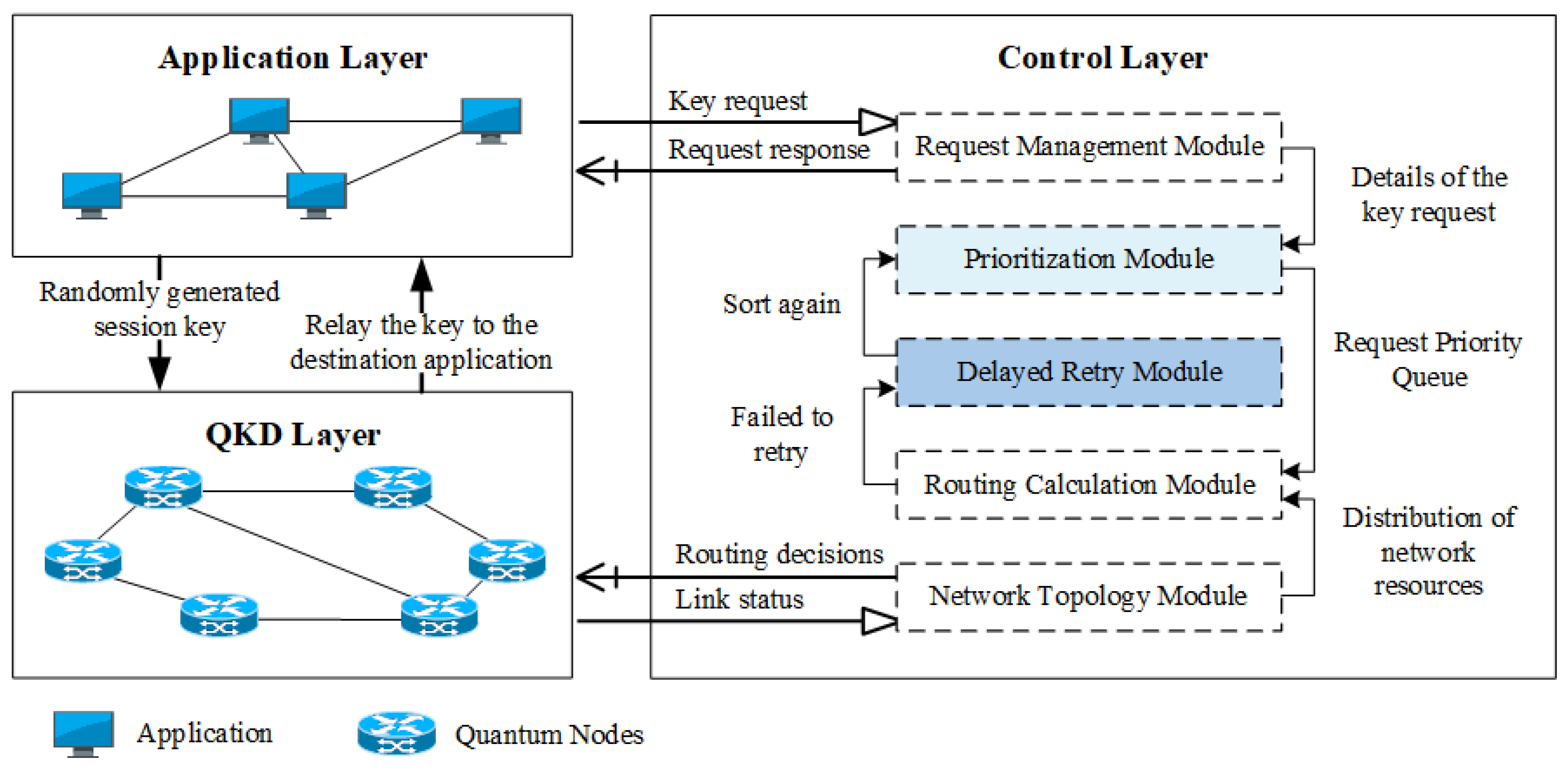
2.1. System Model
- Application layer: The application layer consists of various application entities involved in data transfer. This layer is the service body of the QKD network as well as the bridge between the QKD network and real users. The application in this layer will initiate a secret key request at any moment. This secret key request is submitted to the controller, and when the controller gets the secret key request, the application enters the blocking and waiting phase. Only when the application receives the request response information back from the controller can it begin the subsequent key generation phase.
- Control layer: The control layer contains five modules: request management module, priority ranking module, delay retry module, network topology module, and route calculation module. The request management module is used to receive the secret key request of applications and send the details contained in requests to the priority ranking module. Subsequently, the priority ranking module will rank the huge number of requests arriving within a short period by the present resource status of the QKD network and the priority judging criterion defined in advance. After finishing the ranking, the priority ranking module delivers the request priority queue to the route calculation module for path selection, which is carried out under a specified strategy. When a request meets with route failure owing to insufficient resources, the request is delivered by the route calculation module to the delay retry module where the application will determine whether to rejoin the request queue according to its acceptable delay range. If the current delay is not exceeded, the request can be handled again by the priority module until the route is successful or timeout. The routing calculation module interfaces with the network topology module to gather the network resource status and give a full network topology for path selection.
- QKD layer: The quantum nodes in the QKD layer report the resource storage and operation status to the controller’s network topology module in real-time. When the controller’s route calculation module completes the path selection, it distributes the corresponding routing decision to each quantum node in the QKD layer quantum node. Quantum nodes would update the local routing table entries. When the application receives the key request response, it transmits the session key relay to the target application through each quantum node in the QKD layer. Finally, the two communicating parties would have the same session key.
2.2. Relevant Definitions of the Model
- Quantum link: a virtual link between neighboring quantum nodes abstracted for QKD, the underlying physical form is the combination of quantum channel and measurement-based channel, the process of QKD contains the information transmission of these two channels.
- Link time slice: each quantum link has a particular key generation rate that can be divided, meaning that the key generation cycle can be divided evenly to produce a time slice. Later, for different secret key requests of applications, the time slice is allocated on demand, i.e., occupying a period in the key generation cycle for updating its session key.
- Link key: the secret key generated by each quantum link is called the link key. It is generated by the negotiation of neighboring quantum nodes.
- Link key pool: the link key pool is a virtual concept that manifests as a pair of local key pools in neighboring quantum nodes. The quantum keys generated by the idle link time slice are stored in the link key pool, which can directly provide key services for applications and support the case of insufficient link time slice.
- Application priority: depending on the degree of importance, each application will have a distinct priority. The same application may have different levels of data transmission urgency at different times, thereby the application priority might change dynamically. A higher priority secret key request of an application signifies that the application has a higher security requirement or the application urgently needs to obtain a key for confidential communication.
- Total key request: the meaning of total key request is the total amount of key requests of an application. It plays a significant part in determining the request priority. A large total key request of an application suggests that there would be more difficulties to allocate resources for the current application and comprehensive consideration of the existing network resource state is needed.
- Key update rate: it is similar to the total key request but influences more the consumption of time slices of the quantum link rather than the consumption of the number of keys remaining in each quantum node. The higher key update rate that an application demand indicates, the more time slice resources that the application needs to occupy. Nevertheless, the key generation rate of the link is limited. Once the time slice resources are occupied by an application, they are difficult to be released in a short time.
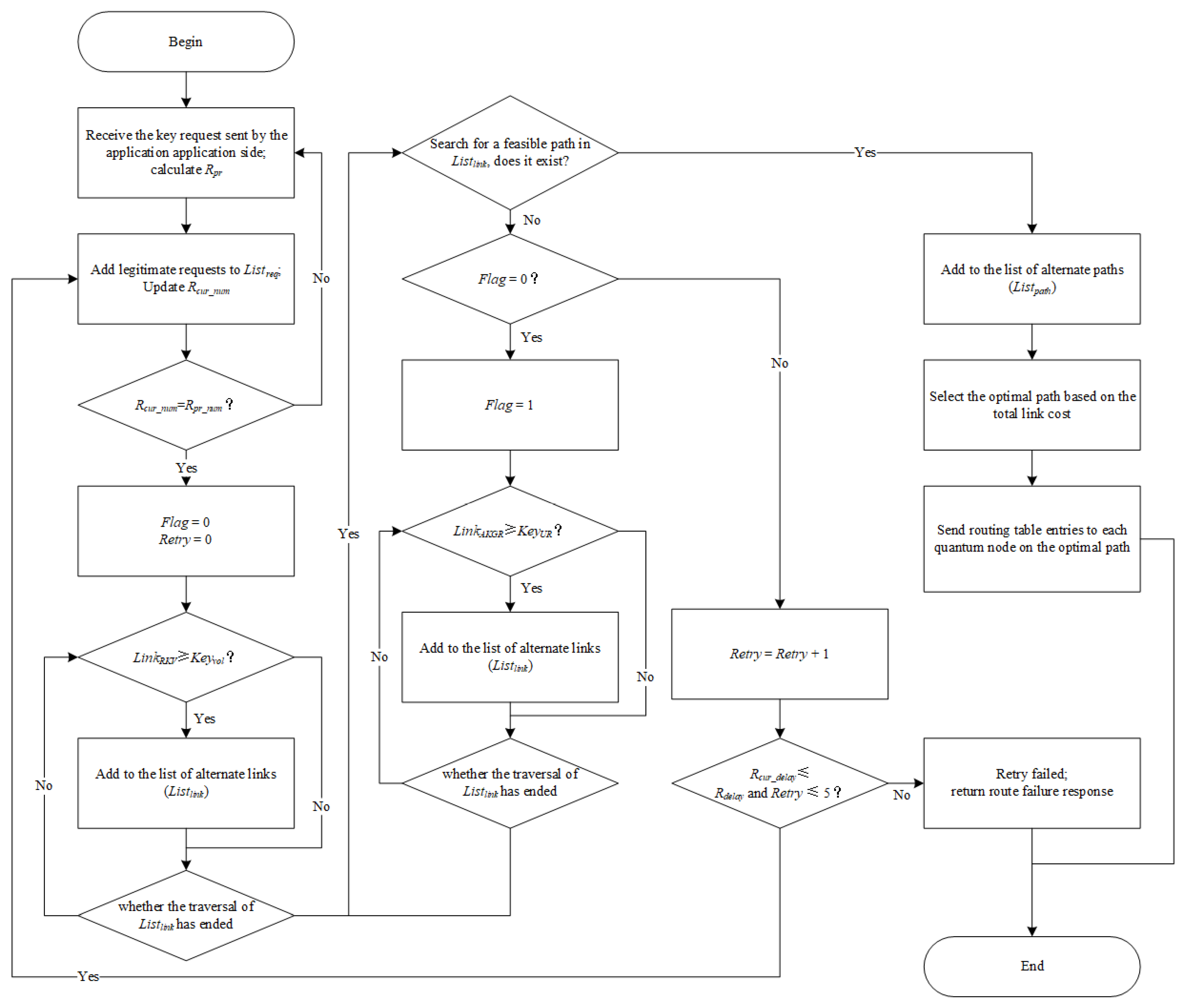
3. APR-QKDN Routing Scheme
3.1. Priority Judgment Criterion of Requests
- The total key request is less than the minimum number of remaining link keys in the link set: the request can be satisfied by the remaining link key solely and does not have to be allocated link time slices. Therefore, the priority judgment criterion of the request does not need to consider the effect of the key update rate. In this case, γ should be set to 0, and the priority judgment criterion can be expressed as follows:
- The total key request is higher than the maximum number of remaining link keys in the link set: the request can only obtain a key by being allocated a link time slice. Therefore, the priority judgment criterion of the request does not need to consider the effect of the total key request. In this case, β should be set to 0, and the priority judgment criterion can be expressed as follows:
- The total key request is between the minimum and the maximum number of remaining link keys in the link set: the specific approach to satisfy the application request cannot be determined directly. It is necessary to consider the total key request and the key update rate. In this case, and is of the same importance which can be derived as β = γ, and the priority judgment criterion can be expressed as Equation (1).
3.2. Routing Scheme
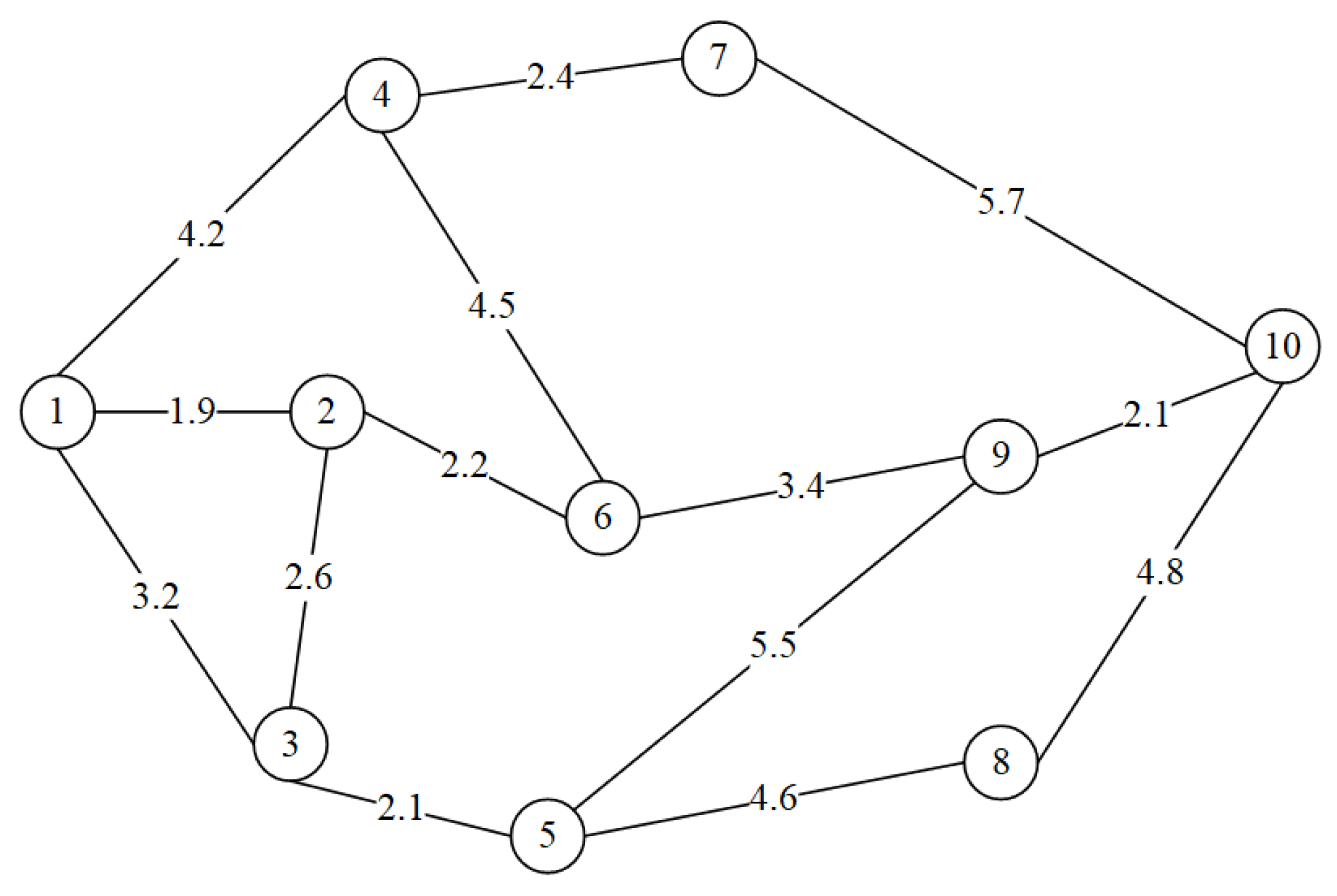
4. Simulation Experiment and Analysis
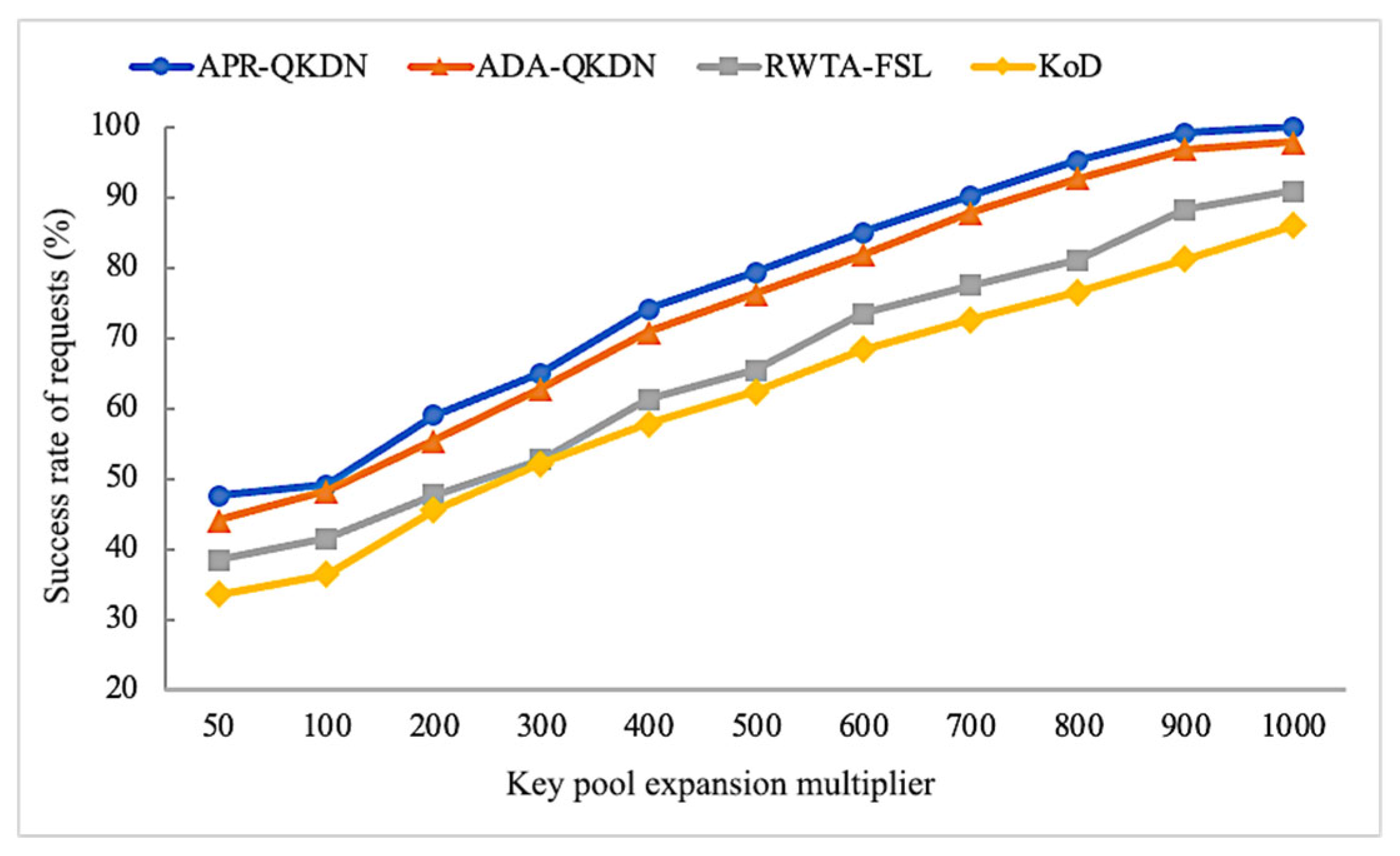
4.1. Performance Comparison under Different Key Pool Expansion Multiplier
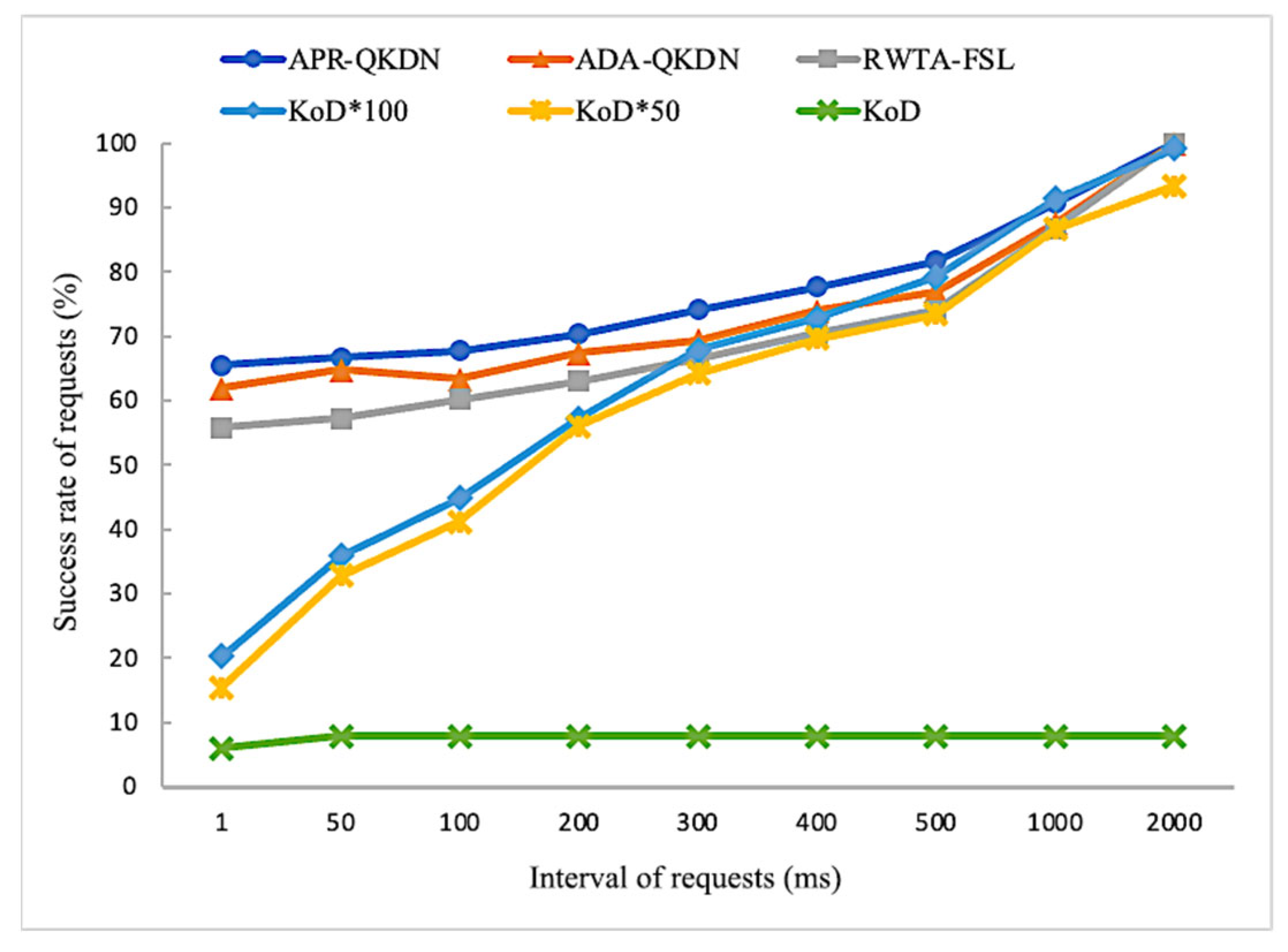
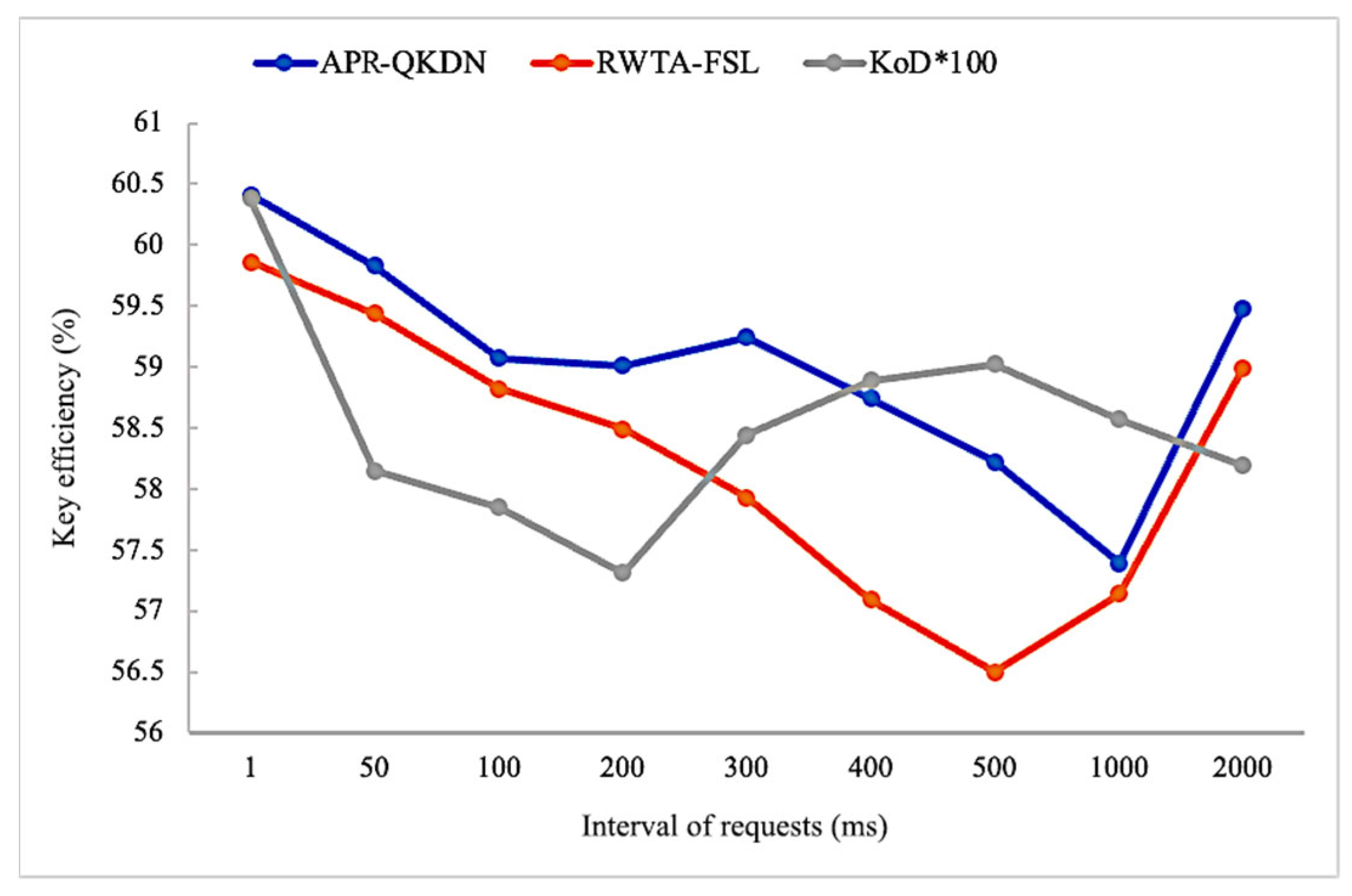
4.2. Performance Comparison under Different Intervals of Requests
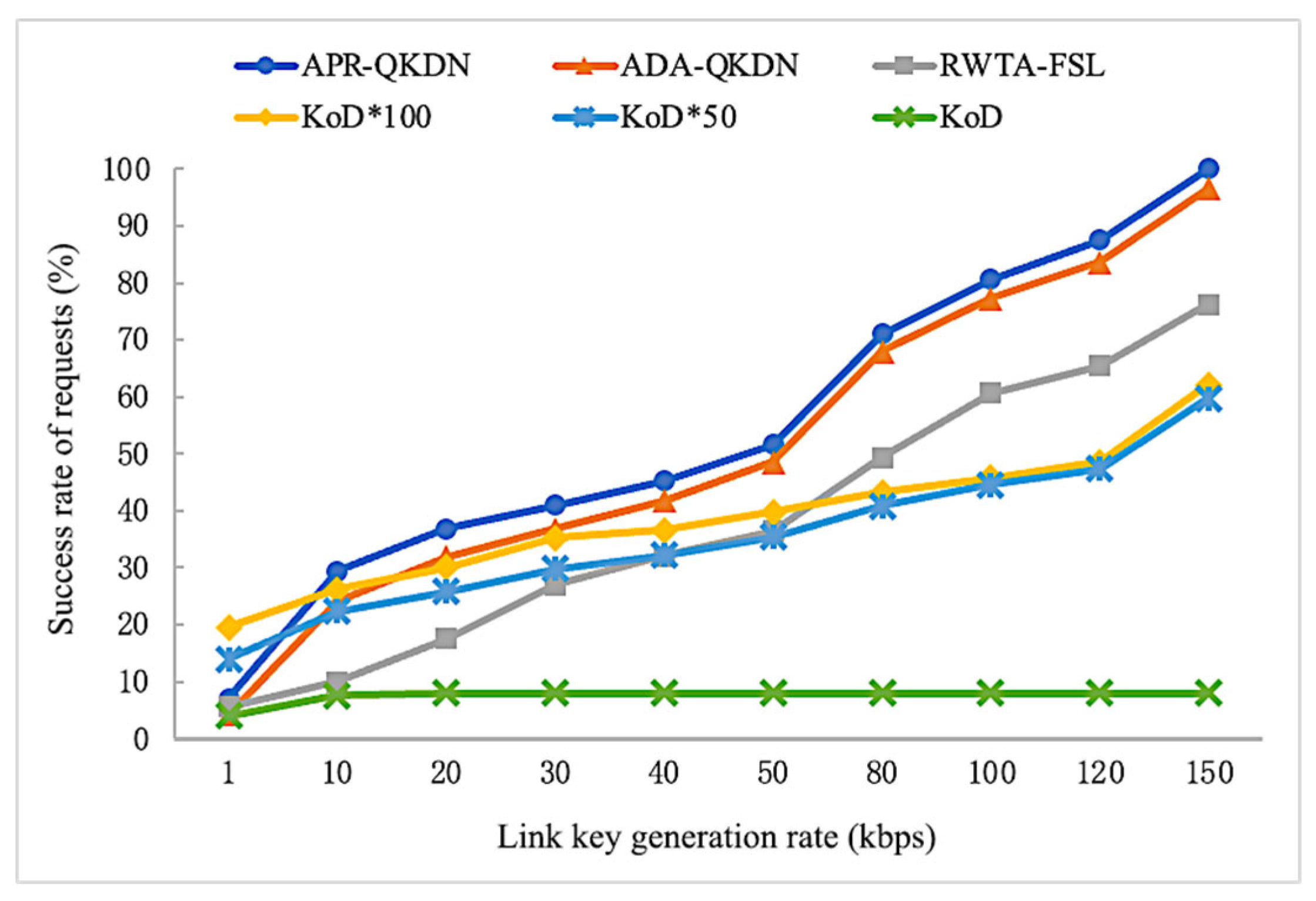
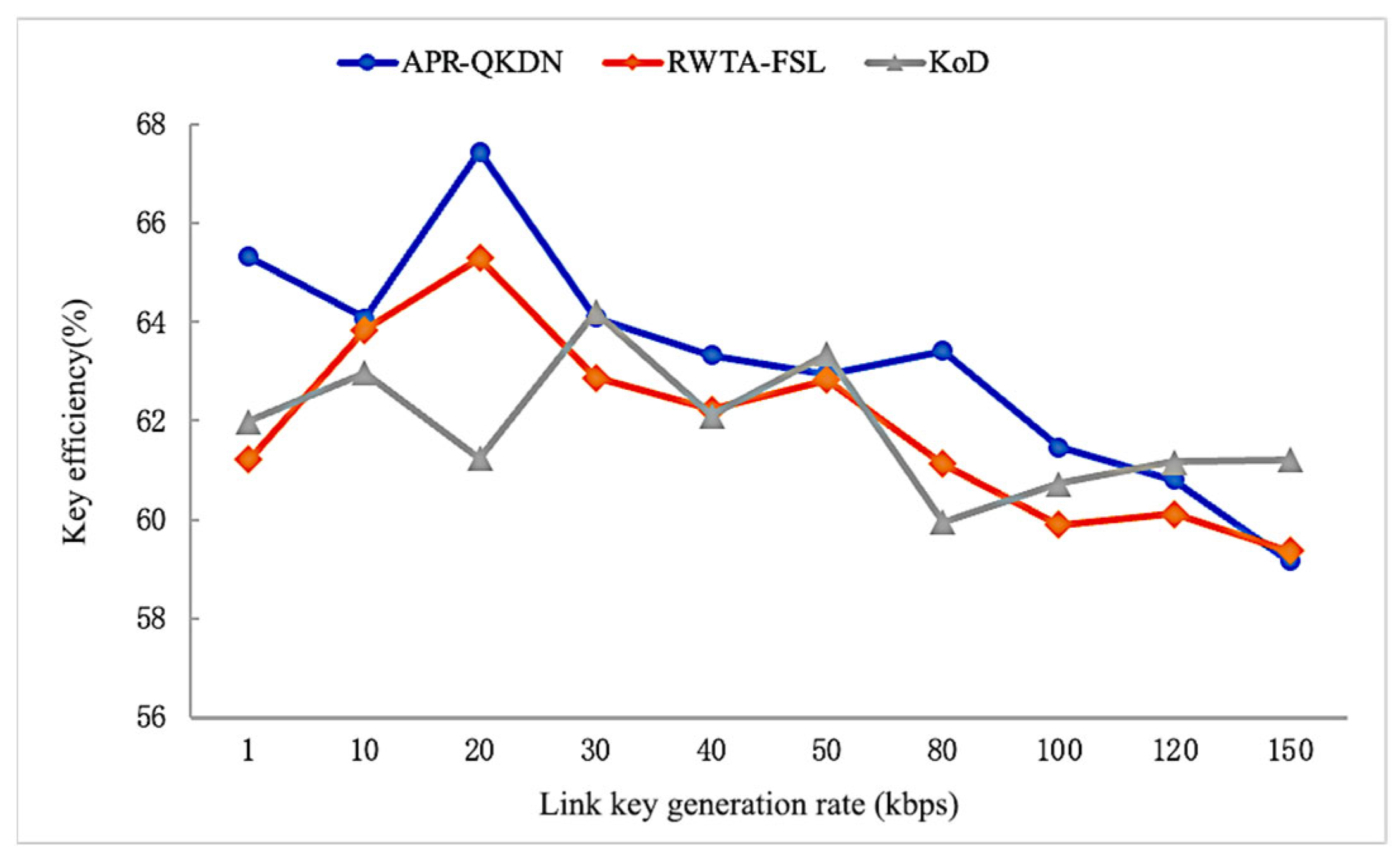
4.3. Performance Comparison under Different Link Key Generation Rate
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Liu, R.; Rozenman, G.G.; Kundu, N.K.; Chandra, D.; De, D. Towards the Industrialisation of Quantum Key Distribution in Communication Networks: A Short Survey. IET Quantum Commun. 2022, 3, 151–163. [Google Scholar] [CrossRef]
- Shi, R. A Generic Quantum Protocol for One-Sided Secure Two-Party Classical Computations. Quantum Inf. Process. 2019, 19, 22. [Google Scholar] [CrossRef]
- Beckwith, L.; Diehl, W. New Directions for NewHope: Improving Performance of Post-Quantum Cryptography through Algorithm-Level Pipelining. In Proceedings of the 2020 International Conference on Field-Programmable Technology (ICFPT), Maui, HI, USA, 9–11 December 2020; pp. 120–128. [Google Scholar]
- Feng, Z.; Li, S.; Xu, Z. Experimental Underwater Quantum Key Distribution. Opt. Express 2021, 29, 8725–8736. [Google Scholar] [CrossRef] [PubMed]
- Qi, B. Bennett-Brassard 1984 Quantum Key Distribution Using Conjugate Homodyne Detection. Phys. Rev. A 2021, 103, 012606. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in Quantum Cryptography. Adv. Opt. Photon. 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Aji, A.; Jain, K.; Krishnan, P. A Survey of Quantum Key Distribution (QKD) Network Simulation Platforms. In Proceedings of the 2021 2nd Global Conference for Advancement in Technology (GCAT), Bangalore, India, 1–3 October 2021; pp. 1–8. [Google Scholar]
- Meter, R.V. Quantum Networking and Internetworking. IEEE Netw. 2012, 26, 59–64. [Google Scholar] [CrossRef]
- Sharma, P.; Agrawal, A.; Bhatia, V.; Prakash, S.; Mishra, A.K. Quantum Key Distribution Secured Optical Networks: A Survey. IEEE Open J. Commun. Soc. 2021, 2, 2049–2083. [Google Scholar] [CrossRef]
- Amin, I.; Mishra, D.; Saini, R.; Aïssa, S. QoS-Aware Secrecy Rate Maximization in Untrusted NOMA With Trusted Relay. IEEE Commun. Lett. 2022, 26, 31–34. [Google Scholar] [CrossRef]
- Guerrini, S.; Chiani, M.; Conti, A. Secure Key Throughput of Intermittent Trusted-Relay QKD Protocols. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–5. [Google Scholar]
- Cao, Y.; Zhao, Y.; Li, J.; Lin, R.; Zhang, J.; Chen, J. Hybrid Trusted/Untrusted Relay-Based Quantum Key Distribution over Optical Backbone Networks. IEEE J. Sel. Areas Commun. 2021, 39, 2701–2718. [Google Scholar] [CrossRef]
- Wen, X.; Li, Q.; Wang, H.; Yang, H.; Bai, H. A Bayesian Based Finite-Size Effect Analysis of QKD; Smart Innovation, Systems and Technologies; Springer International Publishing: Cham, Germany, 2017; Volume 64, pp. 163–170. [Google Scholar]
- Van Assche, G. Quantum Cryptography and Secret-Key Distillation; Cambridge University Press: Cambridge, UK, 2006; p. 260. [Google Scholar]
- Scarani, V.; Bechmann-Pasquinucci, H.; Cerf, N.J.; Duek, M.; Lütkenhaus, N.; Peev, A.M. The Security of Practical Quantum Key Distribution. Rev. Mod. Phys. 2009, 81, 1301. [Google Scholar] [CrossRef]
- Ali, A. A Pragmatic Analysis of Pre- and Post-Quantum Cyber Security Scenarios. In Proceedings of the 2021 International Bhurban Conference on Applied Sciences and Technologies (IBCAST), Islamabad, Pakistan, 14–18 January 2021; pp. 686–692. [Google Scholar]
- Siddhu, V. Entropic Singularities Give Rise to Quantum Transmission. Nat. Commun. 2021, 12, 5750. [Google Scholar] [CrossRef] [PubMed]
- Yu, X.; Ning, X.; Zhu, Q.; Lv, J.; Zhao, Y.; Zhang, H.; Zhang, J. Multi-Dimensional Routing, Wavelength, and Timeslot Allocation (RWTA) in Quantum Key Distribution Optical Networks (QKD-ON). Appl. Sci. 2021, 11, 348. [Google Scholar] [CrossRef]
- Xu, U.-B.; Zhang, M.-S.; Li, Y.-P. Research and Design of QKD Network Random Routing Algorithm Based on Backtracking. J. Univ. Electron. Sci. Technol. China 2021, 50, 565–571. [Google Scholar]
- Cao, Y.; Zhao, Y.; Colman-Meixner, C.; Yu, X.; Zhang, J. Key on Demand (KoD) for Software-Defined Optical Networks Secured by Quantum Key Distribution (QKD). Opt. Express 2017, 25, 26453–26467. [Google Scholar] [CrossRef]
- Ma, W.; Liu, L.; Chen, B.; Gao, M.; Chen, H.; Wu, J. Routing, Wavelength and Time-Slot Assignment Approaches with Security Level in QKD-Enabled Optical Networks. In Proceedings of the 2020 Asia Communications and Photonics Conference (ACP) and International Conference on Information Photonics and Optical Communications (IPOC), Beijing, China, 24–27 October 2020; pp. 1–3. [Google Scholar]
- Chen, L.-Q.; Zhao, M.-N.; Yu, K.-L.; Tu, T.-Y.; Zhao, Y.-L.; Wang, Y.-C. ADA-QKDN: A New Quantum Key Distribution Network Routing Scheme Based on Application Demand Adaptation. Quantum Inf. Process. 2021, 20, 309. [Google Scholar] [CrossRef]
- Yu, X.; Liu, Y.; Zou, X.; Cao, Y.; Zhao, Y.; Nag, A.; Zhang, J. Secret-Key Provisioning with Collaborative Routing in Partially-Trusted-Relay-Based Quantum-Key-Distribution-Secured Optical Networks. J. Light. Technol. 2022, 40, 3530–3545. [Google Scholar] [CrossRef]
- Sharma, P.; Bhatia, V.; Prakash, S. Priority Order-Based Key Distribution in QKD-Secured Optical Networks. In Proceedings of the 2020 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), New Delhi, India, 14–17 December 2020; pp. 1–6. [Google Scholar]
- Zhang, K.; Yu, X.; Wang, Y.; Li, Y.; Zhao, Y.; Zhang, J. Service Priority Based Cross-Layer Routing and Resource Allocation in Quantum Key Distribution Enabled Optical Networks (QKD-ON). In Proceedings of the 2021 19th International Conference on Optical Communications and Networks (ICOCN), Qufu, China, 23–27 August 2021; pp. 1–3. [Google Scholar]
- Chen, L.; Chen, Q.; Zhao, M.; Chen, J.; Liu, S.; Zhao, Y. DDKA-QKDN: Dynamic On-Demand Key Allocation Scheme for Quantum Internet of Things Secured by QKD Network. Entropy 2022, 24, 149. [Google Scholar] [CrossRef]
- Sharma, P.; Bhatia, V.; Prakash, S. Efficient Ordering Policy for Secret Key Assignment in Quantum Key Distribution-Secured Optical Networks. Opt. Fiber Technol. 2022, 68, 102755. [Google Scholar] [CrossRef]
- Yang, C.; Zhang, H.; Su, J. The QKD Network: Model and Routing Scheme. J. Mod. Opt. 2017, 64, 2350–2362. [Google Scholar] [CrossRef]
- Yang, C.; Zhang, H.; Su, J. Quantum Key Distribution Network: Optimal Secret-Key-Aware Routing Method for Trust Relaying. China Commun. 2018, 15, 33–45. [Google Scholar] [CrossRef]
- Yao, J.; Wang, Y.; Li, Q.; Mao, H.; El-Latif, A.A.A.; Chen, N. An Efficient Routing Protocol for Quantum Key Distribution Networks. Entropy 2022, 24, 911. [Google Scholar] [CrossRef] [PubMed]

| Symbols | Meanings |
|---|---|
| priority judgment criterion of requests | |
| application priority | |
| total key request | |
| key update rate | |
| number of request retries | |
| maximum acceptable delay for requests | |
| maximum delay allowed by the system | |
| current delay of the request | |
| number of requests processed at one time | |
| current number of accumulated requests | |
| secret key request of applications | |
| source node of secret key requests | |
| destination node of secret key requests | |
| request priority queue | |
| list of alternate links | |
| list of optional paths | |
| number of remaining link keys | |
| available link key generation rate |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, L.; Zhang, Z.; Zhao, M.; Yu, K.; Liu, S. APR-QKDN: A Quantum Key Distribution Network Routing Scheme Based on Application Priority Ranking. Entropy 2022, 24, 1519. https://doi.org/10.3390/e24111519
Chen L, Zhang Z, Zhao M, Yu K, Liu S. APR-QKDN: A Quantum Key Distribution Network Routing Scheme Based on Application Priority Ranking. Entropy. 2022; 24(11):1519. https://doi.org/10.3390/e24111519
Chicago/Turabian StyleChen, Liquan, Ziyan Zhang, Mengnan Zhao, Kunliang Yu, and Suhui Liu. 2022. "APR-QKDN: A Quantum Key Distribution Network Routing Scheme Based on Application Priority Ranking" Entropy 24, no. 11: 1519. https://doi.org/10.3390/e24111519
APA StyleChen, L., Zhang, Z., Zhao, M., Yu, K., & Liu, S. (2022). APR-QKDN: A Quantum Key Distribution Network Routing Scheme Based on Application Priority Ranking. Entropy, 24(11), 1519. https://doi.org/10.3390/e24111519






