Logic Programming with Post-Quantum Cryptographic Primitives for Smart Contract on Quantum-Secured Blockchain
Abstract
- Logical programs in general and smart contracts among them are better suited for formal verification than procedural programs. In the case of procedural programs, a usual way to proceed is to construct a formal calculus with rigorous semantics and express a program as a set of expressions of that calculus [5,6]. Logic is formal calculus itself, so there is no need for translation to other systems, and the verification is easier.
- Logical contracts are usually more compact. In contrast to their procedural counterparts, they are limited only to what has to be done, without specifying how to achieve it.
- Expressing contracts in a logical language is less error prone [7], as they are much closer to the user-friendly specifications than the procedural programming languages.
1. Background and Related Work: Programming Language and Formal Models of Bitcoin-like Smart Contract
1.1. Timed Automata
1.2. Simplicity
1.3. BitML
- Participants broadcast a contract advertisement, which specifies the content of the contract and its preconditions (e.g., depositing a certain amount of bitcoins).
- Participants accept the contract and fulfill all the required preconditions. When all the needed participants commit to the contract, the contract is stipulated and can be executed.
- Executing the contract eventually results in a transfer of the bitcoins deposited by the participants, according to the logic defined by the contract.
1.4. Logical Contract
- Monitor compliance of the parties to a contract;
- Enforce compliance, by automatically performing actions to fulfill obligations, and/or by issuing warnings and remedial actions to respond to violations of obligations;
- Explore logical consequences of hypothetical scenarios;
- Query and update the Ethereum blockchain.
1.5. Probabilistic Logic Programs for Blockchain and Smart Contracts
1.6. Logicontract
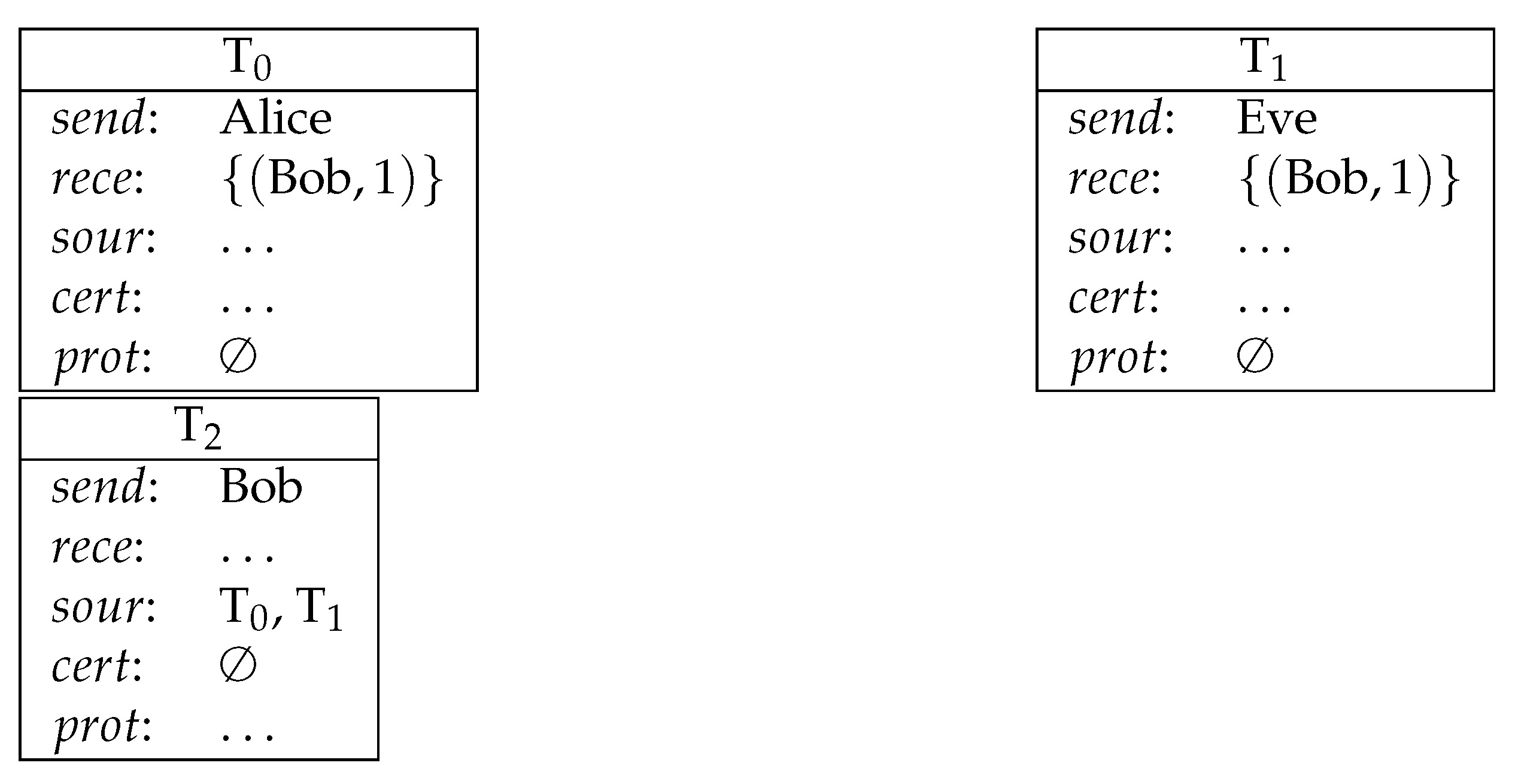
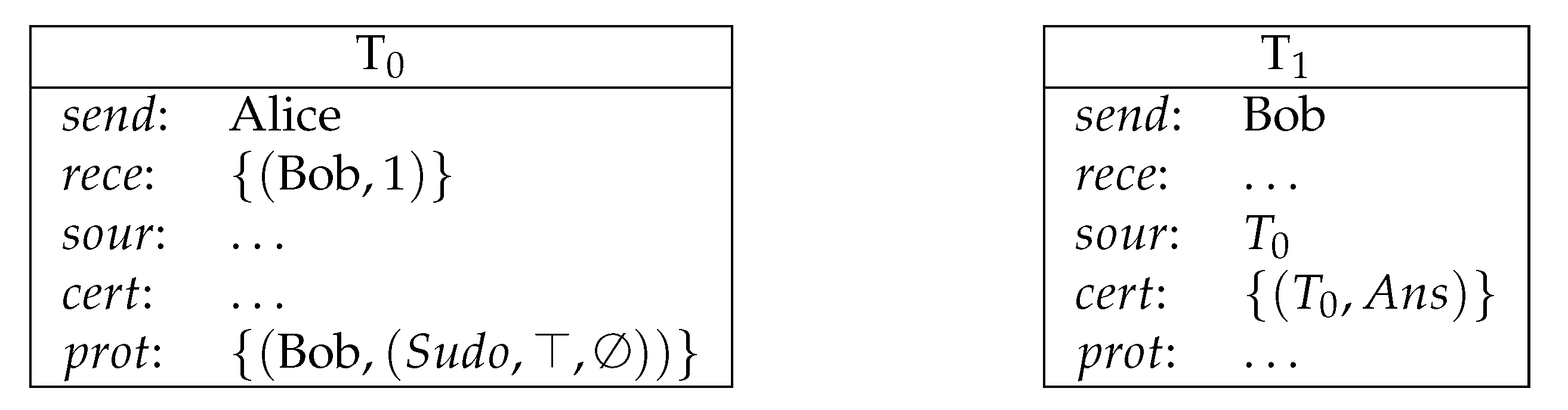
- T is the name of the transaction.
- stands for the sender of the transaction.
- stands for the set of ordered pairs and each of the pairs consists of a potential receiver of this transaction and the amount of the currency that the receiver will receive, i.e., .
- stands for the source of the transaction, which is a list of names of transactions that are redeemed by T.
- stands for the , which is a list of ordered pairs in which each pair consists of a receiver from rece and a formula that has to be fulfilled by the receiver to redeem the transaction, i.e., . In order to redeem T, has to provide as the certification of a following transaction.
- stands for the certification, which is a list of ordered pairs consisting of names of transactions and valuation functions that are supposed to satisfy protections of source transactions, i.e., . Valuation functions map variables to natural numbers. The list must provide a valuation function for each source transaction.
- The sender of T is one of the receivers in each of its source transactions.
- The certification of T evaluates correctly the protections of all sources.
- None of the sources has been already redeemed.
2. Logic Programming for Smart Contracts
2.1. Classical Logic Programming
2.2. Answer Set Programming
2.3. Transaction and Smart Contracts
- is the , which is a list of triples of logic programs, formulas and time locks. The number of triples must be the same as the number of receivers. Formally, . is a logical program of answer set programming. is either the logical truth ⊤ or a non-ground formula ϕ built from literals with connective . is the time lock, which is of the form for some natural number k.
- is the certification, which is a set of ordered pairs of which the first component is the name of a transaction and the second component is either a set of literals or a valuation function that maps variables to constants. Formally, .satisfies if is an answer set for and the time lock is satisfied by the global clock. satisfies , where is a non-ground formula ϕ built from literals with connective , if and the time lock is satisfied by the global clock. When the time lock is ∅, it is vacuously satisfied by the global clock.
- The sender of T is one of the receivers in each of its source transactions.
- The certification of T evaluates the protections of all its sources to be true.
- None of its source transactions has been redeemed.
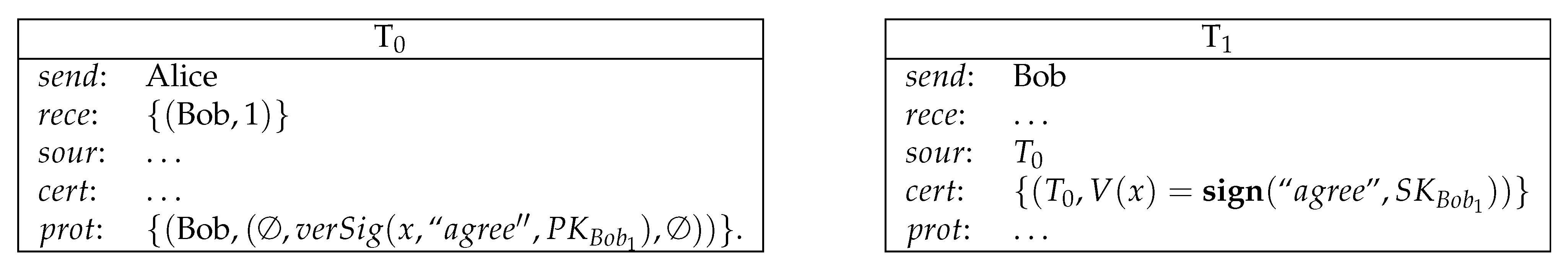
- For encryption, a secret key is a constant. The function maps to the corresponding public key . The encryption function maps a plain message m and public key to an encrypted message .
- For signature, the signing function maps a message m and a secret key to the signature . The atom is true when is the signature of m and with public key .
- The hash function is represent by a collision-resistant function .
2.3.1. Multi-Party Lottery
- Randomness. All tickets are equally likely to win.
- Unpredictability. No player can predict the winning ticket.
- Unforgeability. Tickets cannot be forged. In particular, it is impossible to create a winning ticket after the outcome of the random process is known.
- Verifiability. The number and the revenue of winning tickets are publicly verifiable.
- Decentralization. The random process does not rely on a single authority.
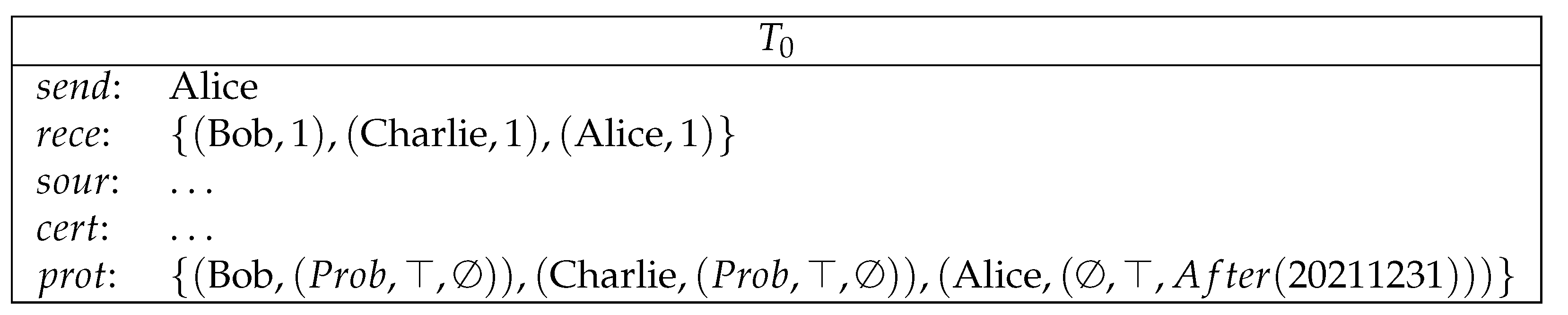
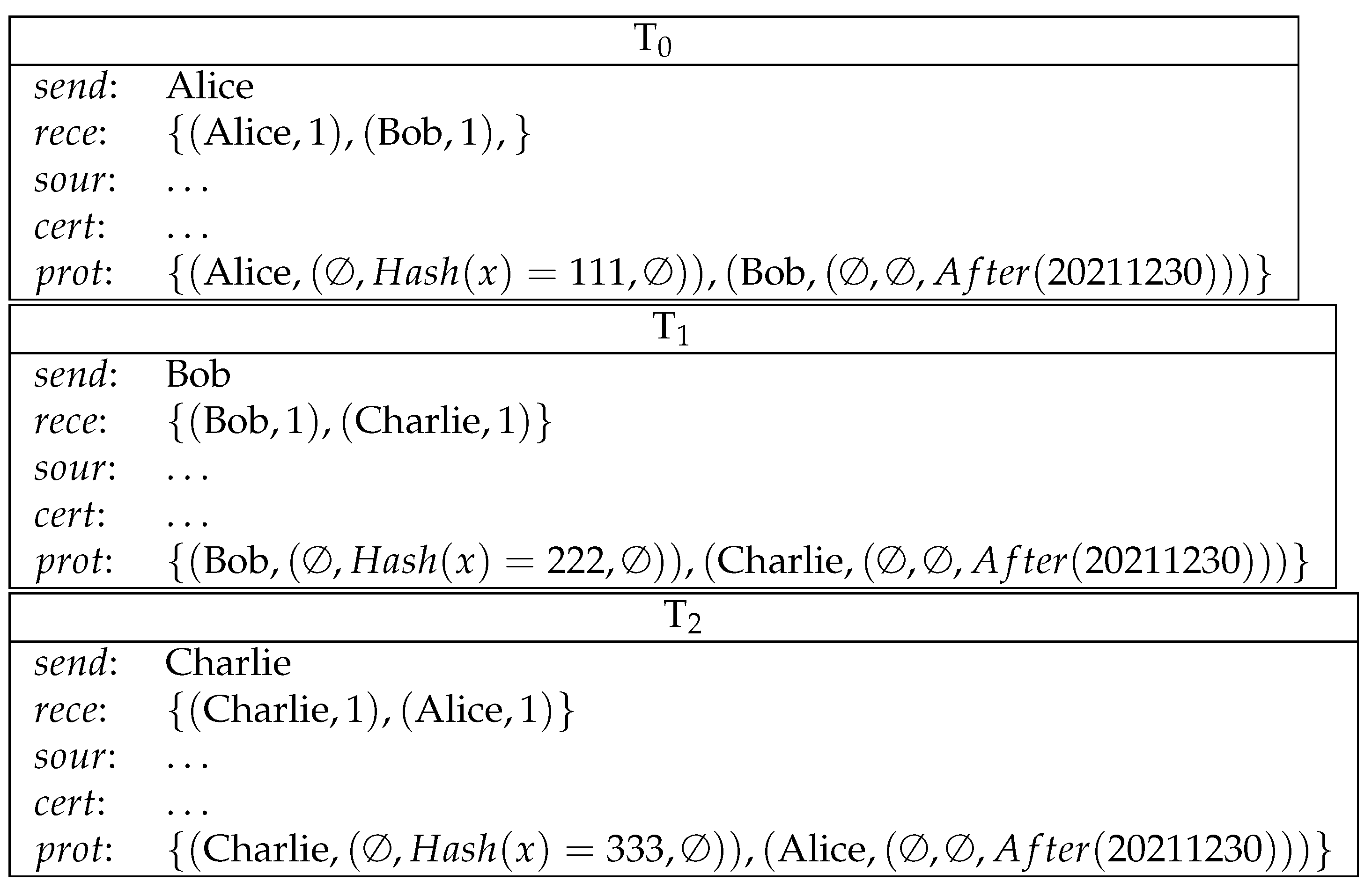
- Alice commits a secret to Bob by making a deposit. Bob commits a secret to Charlie by making a deposit. Charlie commits a secret to Alice by making a deposit. (See Figure 8).
- Alice sends a conditional transfer to Alice, Bob and Charlie. Bob sends a conditional transfer to Alice, Bob and Charlie. Charlie sends a conditional transfer to Alice, Bob and Charlie. (See Figure 9).Here, AliceWin is specified by , where means equivalence modulo 3. BobWin is specified by . CharlieWin is specified by . Alice can also redeem her conditional transfer after 20220130. This condition ensures that Alice can get her money back in case any participant aborts the lottery game before the results can be determined. This is similarly the case for Bob and Charlie.
- Alice reveals her secret and gets her deposit back. Bob reveals his secret and gets his deposit back. Charlie reveals his secret and gets his deposit back. (See Figure 10).
- Now, Alice, Bob and Charlie’s secrets are public and the winner can be determined. The winner redeems the loser’s conditional transfer and his/her own conditional transfer. If Alice is the winner, then she redeems , and . This is similarly true for Bob/Charlie when they are the winner. (See Figure 11).
2.3.2. Legal Service
3. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 23 July 2021).
- Szabo, N. The Idea of Smart Contracts. Available online: https://nakamotoinstitute.org/the-idea-of-smart-contracts (accessed on 23 July 2021).
- Bartoletti, M.; Cimoli, T.; Giamberardino, P.D.; Zunino, R. Vicious circles in contracts and in logic. Sci. Comput. Program. 2015, 109, 61–95. [Google Scholar] [CrossRef]
- Governatori, G.; Idelberger, F.; Milosevic, Z.; Riveret, R.; Sartor, G.; Xu, X. On legal contracts, imperative and declarative smart contracts, and blockchain systems. Artif. Intell. Law 2018, 26, 377–409. [Google Scholar] [CrossRef]
- Atzei, N.; Bartoletti, M.; Cimoli, T.; Lande, S.; Zunino, R. SoK: Unraveling Bitcoin Smart Contracts. Princ. Secur. Trust. LNCS 2018, 10804, 217–242. [Google Scholar] [CrossRef]
- Grishchenko, I.; Maffei, M.; Schneidewind, C. A Semantic Framework for the Security Analysis of Ethereum Smart Contracts. In International Conference on Principles of Security and Trust; Springer: Cham, Switzerland, 2018; pp. 243–269. [Google Scholar] [CrossRef]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A Survey of Attacks on Ethereum Smart Contracts (SoK). In Lecture Notes in Computer Science, Proceedings of the Principles of Security and Trust—6th International Conference, POST 2017, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2017, Uppsala, Sweden, 22–29 April 2017; Maffei, M., Ryan, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; Volume 10204, pp. 164–186. [Google Scholar] [CrossRef]
- Sun, X.; Sopek, M.; Wang, Q.; Kulicki, P. Towards Quantum-Secured Permissioned Blockchain: Signature, Consensus, and Logic. Entropy 2019, 21, 887. [Google Scholar] [CrossRef]
- Sun, X.; Wang, Q.; Kulicki, P.; Sopek, M. A Simple Voting Protocol on Quantum Blockchain. Int. J. Theor. Phys. 2019, 58, 275–281. [Google Scholar] [CrossRef]
- Sun, X.; Kulicki, P.; Sopek, M. Lottery and Auction on Quantum Blockchain. Entropy 2020, 22, 1377. [Google Scholar] [CrossRef] [PubMed]
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for hard lattices and new cryptographic constructions. In Proceedings of the 40th Annual ACM Symposium on Theory of Computing, Victoria, BC, Canada, 17–20 May 2008; Dwork, C., Ed.; ACM: New York, NY, USA, 2008; pp. 197–206. [Google Scholar] [CrossRef]
- Ducas, L.; Micciancio, D. Improved Short Lattice Signatures in the Standard Model. In Lecture Notes in Computer Science, Proceedings of the Advances in Cryptology—CRYPTO 2014—34th Annual Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2014; Part I; Garay, J.A., Gennaro, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8616, pp. 335–352. [Google Scholar] [CrossRef]
- Li, C.; Chen, X.; Chen, Y.; Hou, Y.; Li, J. A New Lattice-Based Signature Scheme in Post-Quantum Blockchain Network. IEEE Access 2019, 7, 2026–2033. [Google Scholar] [CrossRef]
- Wang, L.J.; Zhang, K.Y.; Wang, J.Y.; Cheng, J.; Yang, Y.H.; Tang, S.B.; Yan, D.; Tang, Y.L.; Liu, Z.; Yu, Y.; et al. Experimental authentication of quantum key distribution with post-quantum cryptography. NPJ Quantum Inf. 2021, 7, 67. [Google Scholar] [CrossRef]
- Rouhani, S.; Deters, R. Security, Performance, and Applications of Smart Contracts: A Systematic Survey. IEEE Access 2019, 7, 50759–50779. [Google Scholar] [CrossRef]
- Andrychowicz, M.; Dziembowski, S.; Malinowski, D.; Mazurek, L. Modeling Bitcoin Contracts by Timed Automata. In Lecture Notes in Computer Science, Proceedings of the Formal Modeling and Analysis of Timed Systems—12th International Conference, FORMATS 2014, Florence, Italy, 8–10 September 2014; Legay, A., Bozga, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8711, pp. 7–22. [Google Scholar] [CrossRef]
- Amnell, T.; Behrmann, G.; Bengtsson, J.; D’Argenio, P.R.; David, A.; Fehnker, A.; Hune, T.; Jeannet, B.; Larsen, K.G.; Möller, M.O.; et al. UPPAAL—Now, Next, and Future. In Lecture Notes in Computer Science, Proceedings of the Modeling and Verification of Parallel Processes, 4th Summer School, MOVEP 2000, Nantes, France, 19–23 June 2000; Cassez, F., Jard, C., Rozoy, B., Ryan, M.D., Eds.; Springer: Berlin/Heidelberg, Germany, 2000; Volume 2067, pp. 99–124. [Google Scholar] [CrossRef]
- O’Connor, R. Simplicity: A New Language for Blockchains. In Proceedings of the 2017 Workshop on Programming Languages and Analysis for Security, PLAS@CCS 2017, Dallas, TX, USA, 30 October 2017; ACM: New York, NY, USA, 2017; pp. 107–120. [Google Scholar] [CrossRef]
- Valliappan, N.; Mirliaz, S.; Vesga, E.L.; Russo, A. Towards Adding Variety to Simplicity. In International Symposium on Leveraging Applications of Formal Methods; Springer: Cham, Switzerland, 2018; pp. 414–431. [Google Scholar] [CrossRef]
- Bartoletti, M.; Zunino, R. BitML: A Calculus for Bitcoin Smart Contracts. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS 2018, Toronto, ON, Canada, 15–19 October 2018; Lie, D., Mannan, M., Backes, M., Wang, X., Eds.; ACM: New York, NY, USA, 2018; pp. 83–100. [Google Scholar] [CrossRef]
- Kowalski, R.A.; Sadri, F. Reactive Computing as Model Generation. New Gener. Comput. 2015, 33, 33–67. [Google Scholar] [CrossRef][Green Version]
- Kowalski, R.A.; Sadri, F. Programming in logic without logic programming. Theory Pract. Log. Program. 2016, 16, 269–295. [Google Scholar] [CrossRef][Green Version]
- Kowalski, R.A.; Sadri, F.; Calejo, M. How to do it with LPS (Logic-Based Production System). In Proceedings of the Doctoral Consortium, Challenge, Industry Track, Tutorials and Posters @ RuleML+RR 2017 hosted by International Joint Conference on Rules and Reasoning 2017 (RuleML+RR 2017), London, UK, 11–15 July 2017; Bassiliades, N., Bikakis, A., Costantini, S., Franconi, E., Giurca, A., Kontchakov, R., Patkos, T., Sadri, F., Woensel, W.V., Eds.; CEUR-WS.org: Aachen, Germany, 2017; Volume 1875. [Google Scholar]
- Azzolini, D.; Riguzzi, F.; Lamma, E.; Bellodi, E.; Zese, R. Modeling Bitcoin Protocols with Probabilistic Logic Programming. In Proceedings of the 5th International Workshop on Probabilistic Logic Programming, PLP 2018, Co-Located with the 28th International Conference on Inductive Logic Programming (ILP 2018), Ferrara, Italy, 1 September 2018; Bellodi, E., Schrijvers, T., Eds.; CEUR-WS.org: Aachen, Germany, 2018; Volume 2219, pp. 49–61. [Google Scholar]
- Azzolini, D.; Riguzzi, F.; Lamma, E. Analyzing Transaction Fees with Probabilistic Logic Programming. In Lecture Notes in Business Information Processing, Proceedings of the Business Information Systems Workshops—BIS 2019 International Workshops, Seville, Spain, 26–28 June 2019; Revised Papers; Abramowicz, W., Corchuelo, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; Volume 373, pp. 243–254. [Google Scholar] [CrossRef]
- Azzolini, D.; Riguzzi, F.; Lamma, E. A semantics for Hybrid Probabilistic Logic programs with function symbols. Artif. Intell. 2021, 294, 103452. [Google Scholar] [CrossRef]
- Bartoletti, M.; Cimoli, T.; Zunino, R. Fun with Bitcoin Smart Contracts. In International Symposium on Leveraging Applications of Formal Methods; Springer: Cham, Switzerland, 2018; pp. 432–449. [Google Scholar] [CrossRef]
- Lifschitz, V. Answer set programming and plan generation. Artif. Intell. 2002, 138, 39–54. [Google Scholar] [CrossRef][Green Version]
- Hölldobler, S.; Schweizer, L. Answer Set Programming and CLASP—A Tutorial. In Proceedings of the Young Scientists’ International Workshop on Trends in Information Processing (YSIP) Co-Located with the Sixth International Conference on Infocommunicational Technologies in Science, Production and Education (INFOCOM-6), Stavropol, Russia, 22–25 April 2014; Hölldobler, S., Malikov, A., Wernhard, C., Eds.; CEUR-WS.org: Aachen, Germany, 2014; Volume 1145, pp. 77–95. [Google Scholar]
- Cabalar, P.; Pearce, D.; Valverde, A. Answer Set Programming from a Logical Point of View. Künstliche Intell. 2018, 32, 109–118. [Google Scholar] [CrossRef]
- Baral, C.; Gelfond, M. Logic Programming and Knowledge Representation. J. Log. Program. 1994, 19/20, 73–148. [Google Scholar] [CrossRef]
- Dantsin, E.; Eiter, T.; Gottlob, G.; Voronkov, A. Complexity and expressive power of logic programming. ACM Comput. Surv. 2001, 33, 374–425. [Google Scholar] [CrossRef]
- Bernstein, D.J. Introduction to post-quantum cryptography. In Post-Quantum Cryptography; Bernstein, D.J., Buchmann, J., Dahmen, E., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 1–14. [Google Scholar] [CrossRef]
- Isidore, C. Americans Spend More on the Lottery Than on. Available online: https://money.cnn.com/2015/02/11/news/companies/lottery-spending/ (accessed on 25 August 2021).
- Chow, S.S.M.; Hui, L.C.K.; Yiu, S.; Chow, K.P. An e-Lottery Scheme Using Verifiable Random Function. In Lecture Notes in Computer Science, Proceedings of the Computational Science and Its Applications—ICCSA 2005, International Conference, Singapore, 9–12 May 2005; Proceedings Part III; Gervasi, O., Gavrilova, M.L., Kumar, V., Laganà, A., Lee, H.P., Mun, Y., Taniar, D., Tan, C.J.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3482, pp. 651–660. [Google Scholar] [CrossRef]
- Bentov, I.; Kumaresan, R. How to Use Bitcoin to Design Fair Protocols. In Lecture Notes in Computer Science, Proceedings of the Advances in Cryptology—CRYPTO 2014—34th Annual Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2014; Proceedings Part II; Garay, J.A., Gennaro, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8617, pp. 421–439. [Google Scholar] [CrossRef]
- Bartoletti, M.; Zunino, R. Constant-Deposit Multiparty Lotteries on Bitcoin. In Lecture Notes in Computer Science, Proceedings of the Financial Cryptography and Data Security—FC 2017 International Workshops, WAHC, BITCOIN, VOTING, WTSC, and TA, Sliema, Malta, 7 April 2017; Revised Selected Papers; Brenner, M., Rohloff, K., Bonneau, J., Miller, A., Ryan, P.Y.A., Teague, V., Bracciali, A., Sala, M., Pintore, F., Jakobsson, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; Volume 10323, pp. 231–247. [Google Scholar] [CrossRef]
- Grumbach, S.; Riemann, R. Distributed Random Process for a Large-Scale Peer-to-Peer Lottery. In Distributed Applications and Interoperable Systems; Chen, L.Y., Reiser, H.P., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 34–48. [Google Scholar]
- Miller, A.; Bentov, I. Zero-Collateral Lotteries in Bitcoin and Ethereum. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops, EuroS & P Workshops 2017, Paris, France, 26–28 April 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 4–13. [Google Scholar] [CrossRef]
- Reiter, R. A Logic for Default Reasoning. Artif. Intell. 1980, 13, 81–132. [Google Scholar] [CrossRef]
- Horty, J.F. Defaults with Priorities. J. Philos. Log. 2007, 36, 367–413. [Google Scholar] [CrossRef]

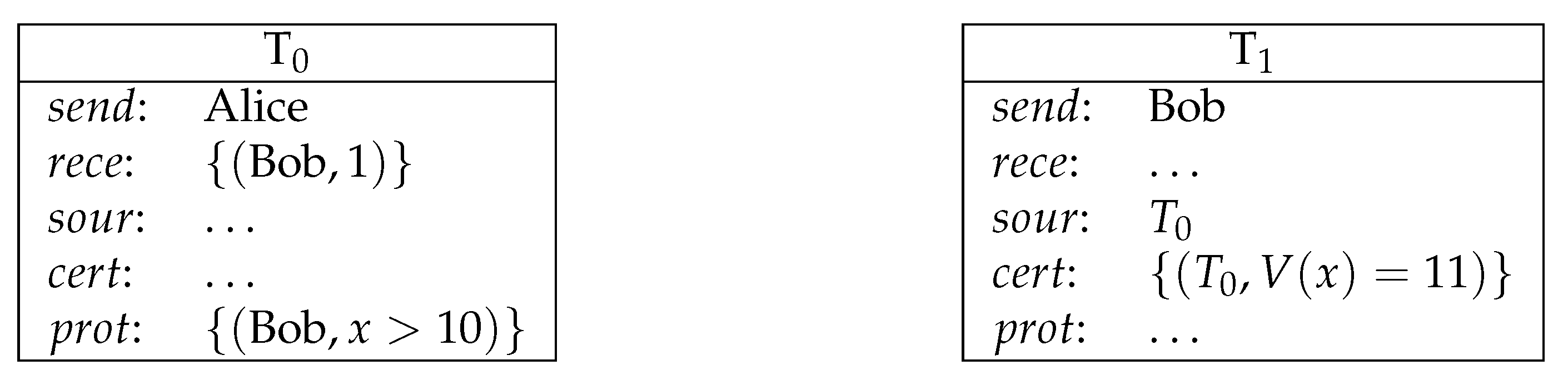
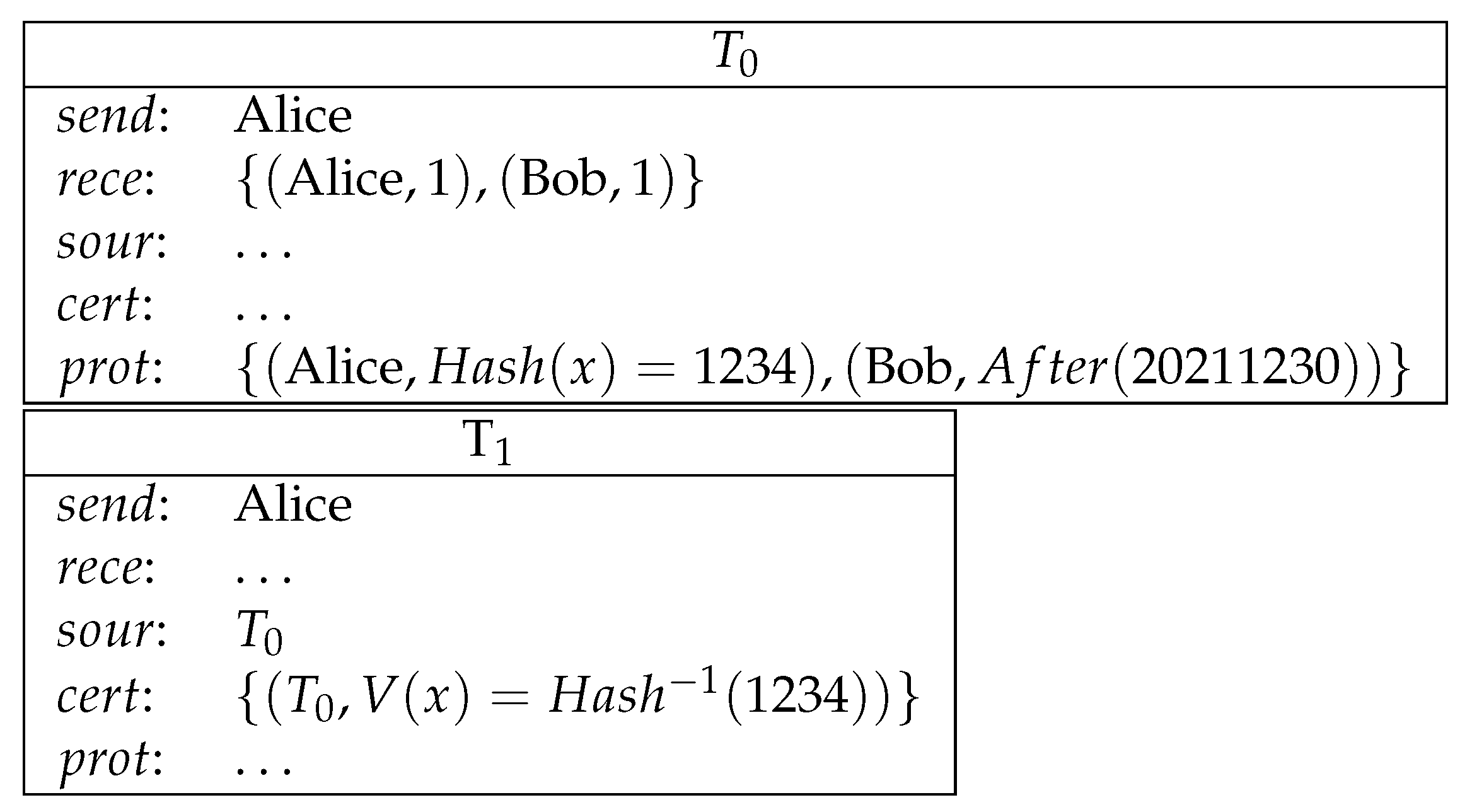

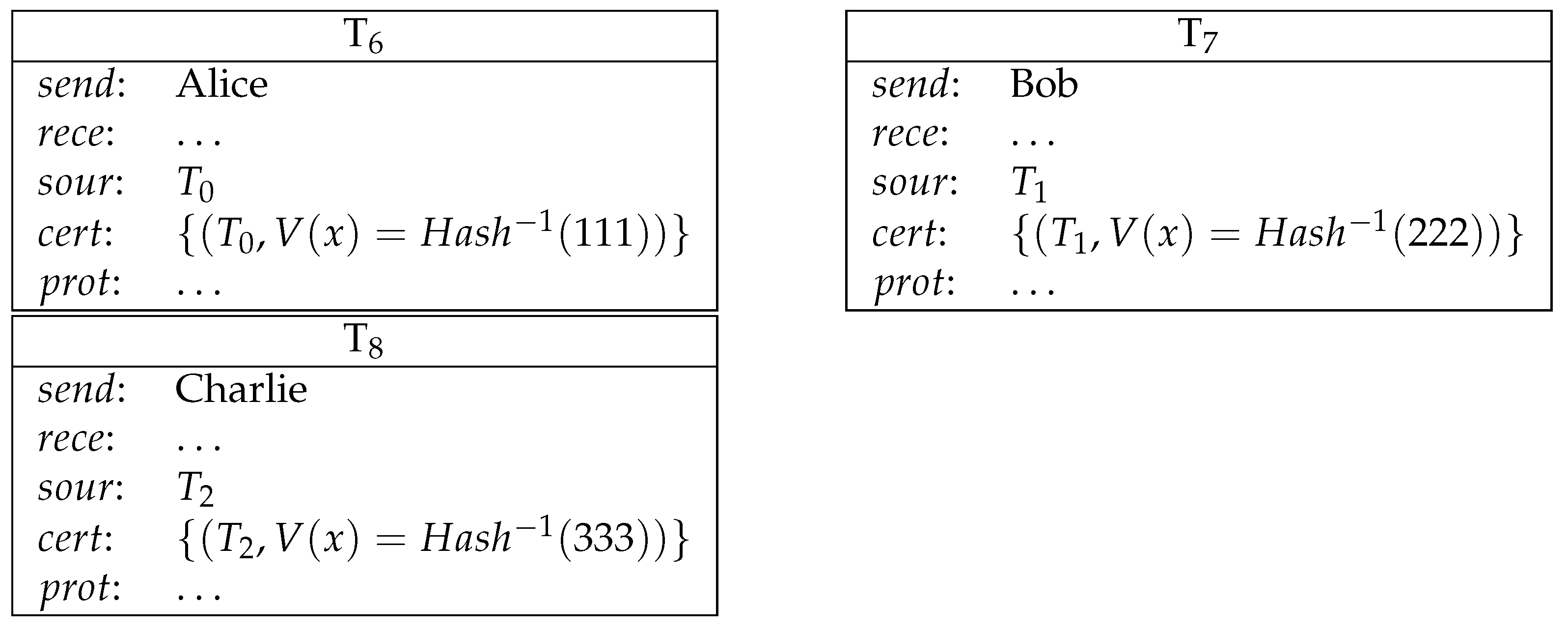
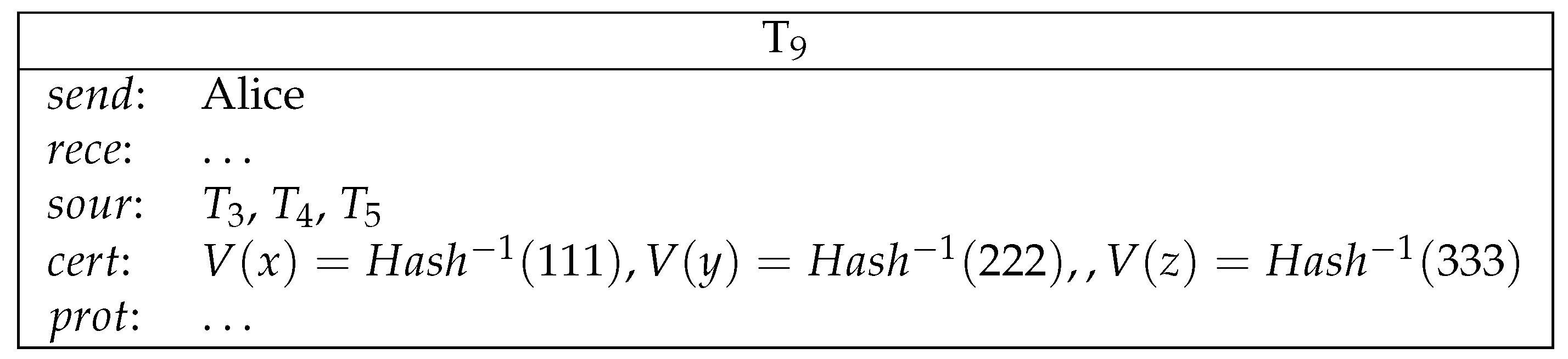
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, X.; Kulicki, P.; Sopek, M. Logic Programming with Post-Quantum Cryptographic Primitives for Smart Contract on Quantum-Secured Blockchain. Entropy 2021, 23, 1120. https://doi.org/10.3390/e23091120
Sun X, Kulicki P, Sopek M. Logic Programming with Post-Quantum Cryptographic Primitives for Smart Contract on Quantum-Secured Blockchain. Entropy. 2021; 23(9):1120. https://doi.org/10.3390/e23091120
Chicago/Turabian StyleSun, Xin, Piotr Kulicki, and Mirek Sopek. 2021. "Logic Programming with Post-Quantum Cryptographic Primitives for Smart Contract on Quantum-Secured Blockchain" Entropy 23, no. 9: 1120. https://doi.org/10.3390/e23091120
APA StyleSun, X., Kulicki, P., & Sopek, M. (2021). Logic Programming with Post-Quantum Cryptographic Primitives for Smart Contract on Quantum-Secured Blockchain. Entropy, 23(9), 1120. https://doi.org/10.3390/e23091120





