Abstract
With the development of wireless sensor networks (WSNs), energy constraints and network security have become the main problems. This paper discusses the dynamic of the Susceptible, Infected, Low-energy, Susceptible model under pulse charging (SILS-P) in wireless rechargeable sensor networks. After the construction of the model, the local stability and global stability of the malware-free T-period solution of the model are analyzed, and the threshold is obtained. Then, using the comparison theorem and Floquet theorem, we obtain the relationship between and the stability. In order to make the conclusion more intuitive, we use simulation to reveal the impact of parameters on . In addition, the paper discusses the continuous charging model, and reveals its dynamic by simulation. Finally, the paper compares three charging strategies: pulse charging, continuous charging and non-charging and obtains the relationship between their threshold values and system parameters.
1. Introduction
With the rapid development of Internet of Things technology in recent years, more and more scholars have focused on wireless sensor networks (WSNs). WSNs consist of many cheap wireless sensor nodes that consume power. Sensor nodes have acquisition, processing, control and communication functions, making WSNs widely used in various fields, such as collaborative detection of multiple unmanned aerial vehicles and fault diagnosis.
Sensor nodes use a multi-hop or single-hop mode to access the network through the data transmission link. No matter what kind of communication mode, a wireless link is needed for data transmission. It is very difficult to build a perfect security mechanism based on a wireless link. Therefore, the security of WSNs has attracted much attention.
The most fundamental reason that malware can spread in WSNs is the connectivity of the network. Since wireless links are used for data transmission among nodes, it is difficult to construct complex protection mechanisms. In order to curb the spread of malware among nodes, a research team has proposed the weight adaptation scheme [1]. The weight adaptation scheme can block the transmission of malware by reducing the transmission efficiency among nodes. In addition, with the development of WSNs, there has been a lot of studies on network security in recent years and some relevant literature is listed in Table 1.

Table 1.
Research on network security in WSNs.
At present, the research on network security is mostly based on the perspective of algorithms [10,11,12]. However, there are many perspectives on the research of network security, and it is also a direction that can combine the spread of malicious software with the dynamics of infectious diseases. Since the spread of malware is somewhat similar to the spread of biological viruses, the research on WSNs security can be carried over into the dynamics of infectious diseases [13]. For example, Wang et al. [14] proposed an effective and efficient immunization strategy for MWSNs based on pulse differential equations and the SIR model. Similarly, Liu et al. proposed an optimal control scheme based on the novel epidemic model (SILS) [15], and Cao et al. obtained the optimal control variables of immunization ratio and recovery ratio by using Pontryagin’s maximum principle based on the theory of infectious disease [16].
However, up to now, there have been few studies on the security of WSNs using impulse differential equation theory. Therefore, based on the dynamics of infectious diseases, this paper uses the impulse differential equation theory to study the node persistence and network security of WRSNs.
In addition to network security, energy constraints are also an important problem that restricts the development of WSNs [17]. With the development of WSNs, rechargeable technology is also a research trend [18,19,20]. In this paper, the residual energy of nodes and the concept of pulse charging are introduced. Because the charging time is relatively short in the whole network cycle, the charging behavior can be approximated as an instantaneous behavior. Compared with continuous charging, pulse charging is more energy saving. Thus, it is of great significance to study the application of pulse charging in WRSNs.
The main purpose of this study is to extend the existing network model [21] and verify the stability of disease-free periodic solutions and the persistence of disease. We improved the charging strategy of the existing model to make it more energy efficient. In the next section, we propose the improved version of the SILS model under pulse charging [21]. In Section 3, the stability of the periodic solution is proved by the next generation matrix and Floquet theory. In Section 4 we discuss the persistence of malware transmission. The persistence of malware transmission refers to the persistent spread of malware in WRSNs under certain conditions. The persistence theory of malware transmission is of great significance for study of the cyberspace security problem. In the last section, we verify the accuracy of the theory through simulation.
2. Epidemic Modeling
2.1. Epidemic Model under Continuous Charging Based on WSNs
Far-field charging is a widely used charging strategy, but this charging strategy is relatively inefficient, so it is often used in low-energy wireless systems such as RFID and WSNs [22]. The following is the low-energy wireless system model built based on far-field charging and epidemic model.
For briefness, sensor nodes are divided into five established compartments: Infected (), Susceptible (), low-energy infection (), low-energy susceptible to infection (), and hardware is damaged (). Malware attacks the sensor nodes in state with high probability. The sensor nodes in state are partially disabled due to malware attacks and perform malicious operations. The low-energy sensor nodes and are forced to sleep due to energy constraints. The sensor node in the D state is completely disabled due to irreparable hardware damage. Specifically, a sensor node in the dormant state cannot perform data transfer. Thus, low-energy infected nodes in cannot spread malware.
When the malware starts to run, the susceptible nodes in enter the communication range of the infected nodes in and are attacked by malware. Because the infected node is not familiar with the network topology, there is a data transfer coefficient for the spread of the malware [16]. Transforming from susceptible nodes to infected nodes is produced with a2I(t)S(t) and the positive number is used to denote the data transfer coefficient. The number of sensor nodes in S depends partly on , where is the birth rate. Some infected nodes become susceptible nodes at the conversion rate of , which is the repair rate. Both of the high-energy nodes and are transformed at a rate into the low-energy nodes and . To reduce the complexity of the model, the constant is used to denote the charging rate. It is assumed that all the charging rates are identical and invariant. Similarly, it assumes that all sensor nodes have the same mortality rate . Based on existing studies [21], the SILS model can be expressed as follows
Moreover, , and is constrained by
2.2. A Pulse Charging Model for SILS
WSNs with a low duty cycle can maintain permanent operation within a certain range of RF power density, and a pulse charging strategy can accomplish this purpose [22].
By introducing the impulse differential equation into the SILS model [21], we can achieve the SILS model of pulse charging (SILS-P) at different moments. The SILS model discusses a WSNs model of continuous charging while the SILS-P model proposes a new charging strategy based on the same WSNs model and reformulates the system.
In the SILS-P model, charging does not occur continuously but over a period of time that is much smaller than the cycle, which is why charging is seen as a pulse. As , the SILS-P model can be written as follows, which is used to describe the dynamic changes of nodes during charging.
where is the pulse charging period, and is used to represent the next instant of . Because the time of pulse charging is much less than one cycle, pulse charging can be regarded as instantaneous behavior. In a nutshell, pulse charging is the charging of low-power nodes at a series of time points (). When , the pulse charging model is governed by following Equations (2) and (3) does not consider dynamic changes caused by charging during this period.
The existence of disease-free periodic solutions is the periodic solution of T that satisfies the above system of equations when . Since = 0, we begin the analysis of Equations (2) and (3) by demonstrating the existence of disease-free periodic solutions, and we can obtain the system as follows [23]
When is a natural number, is the time interval between two pulse charges, and the pulse charges at times and .
From the last equation of Equations (2) and (1f), we obtain
If there is a disease-free periodic solution, then when . According to Equation (5), we can obtain the following limit results from system (4)
In this case, and satisfy the following impulse differential system
The solution of the on the interval is as follows
Let , using stroboscopic mapping, we can derive the functional relation . The relationship is as follows
Equation (9) has a mapping , such that . can be determined when Equation (9) is in equilibrium. Thus, Equation (9) has the equilibrium state as follows
is the point of cyclic convergence of at with as the period. Taking the positive equilibrium as the initial value of Equation (9), it is obvious that
Thus, by using the stability criterion of differential systems, the equilibrium state of Equation (9) is locally stable, which implies the global stability of . This means that the sequence will converge to the equilibrium state . Thus, we can obtain the periodic solution of Equation (7) as follows
According to Equation (9), we can obtain the equilibrium state of as follows
In the same way, it is obvious that the sequence will converge to the equilibrium state . According to Equation (6), we can obtain the periodic solution of Equation (7) as follows
3. Stability of a Malware-Free T-Period Solution
In this section, the local stability and global stability of the SILS-P model are analyzed.
Theorem 1.
When, the disease-free periodic solution of the system is locally asymptotically stable.
Proof.
For the sake of calculation, let be a square matrix of order . Let be the fundamental matrix of , and then let be the spectral radius of [23]. The stability of disease-free periodic solution in the SILS model is proved by Floquet theorem and we assume that are the Floquet multipliers of Equation (18) [14]. Let the small perturbation of the disease-free periodic solution of the system be , and linearize the approximation of system (2) and (3) to obtain the equations as follows
□
Hence, we can derive some matrices
Since is the fundamental matrix of , there exists , where ( is the identity matrix), obtained by Equation (12), Equation (14) and system (15), we can obtain the following matrix
When , from Equation (17), we have
We can infer the Floquet multipliers of Equation (18) as follows
According to Floquet theorem, the disease-free periodic solution is locally asymptotically stable if |ωi| < 1, where i = 1, 2. Therefore, we define thresholds
According to Floquet theorem, when , the disease-free periodic solution (,0,0,0,) of Equation (4) is locally asymptotically stable.
Theorem 2.
Whenand, the disease-free periodic solution of the system is global asymptotic stability.
Proof.
For WRSNs, we expect the number of nodes to be greater than or equal to the initial number of nodes in the stable state. Based on Equations (1a)–(1f), we define the condition as follows
□
The following system (22) can be obtained from Equations (2) and (3)
Based on system (22), we consider the following comparison system as follows
According to the impulse differential equation comparison theorem [24], we can obtain some inequalities as follows
When , . Moreover, there exists a positive , for any , there exists some inequalities as follows
Equation (26) can be obtained from the second and third equations of Equations (2) and (3)
According to the comparison theorem, we have , , and construct the following system, where is the solution to Equation (26).
The solution to Equation (27) can be expressed as follows
When , . When with goes to infinity, it exists and so we have
Hence, at any time , existing
Equation (31) can be obtained from the first and fourth equations of Equations (2) and (3)
In order to use the comparison theorem, transformation to Equation (31) is as follows
Equation (32) has a set of positive solutions and . By comparing the theorem of differential equations of impulses, we can obtain the inequality group of Equation (33) as follows
As tends to infinity, we have
At any , when , we have
When tends to infinity, . Thus, Theorem 2 is proved.
4. Persistence of Malware Transmission
In this section, the persistence of malware transmission is the focus of our discussion. If the system meets certain conditions, the spread of malware in the WRSNs will continue, which is known as the persistence of spreading malware.
Lemma 1.
There existssuch that the solution verifies the system of inequalities as follows, whenand
Proof.
In order to make WRSNs work normally, we want the number of nodes to be larger than the initial number when the system is stable. Therefore, according to Equation (1f), we can obtain the following relation.
□
Using proof by contradiction, if the above conclusion is not valid, there is a time variable . For any time , we have and . Based on Equations (2) and (3), the following system can be written as follows
Based on the above system, the following system will be obtained
The following conclusions can be inferred from the comparison theorem
Equation (39) has a positive periodic solution , which is globally asymptotically stable and . There’s a positive number , and for any , we have and . By the comparison theorem, there is a time variable , and we set to be positive. At any time , there are inequalities as follows
By combining Equations (2) and (3) with the relationship mentioned above we can obtain the following system
As and approach 0, the above inequality can be reduced to the following expression
Let , we set up the system as follows
The above system satisfies , . When and R0 > 1, there is a time variable As , and , we can draw the conclusions as follows
The above conclusion is in contradiction with the condition established previously. Therefore, Lemma 1 is proved.
Theorem 3.
There exists positive integer such that the solution verifies the system of inequalities as follows, when and
From Lemma 1, there are two possible situations when the malware continues to spread as follows:
- (a)
- When the time variable T is large enough, , ;
- (b)
- When the time variable T is large enough, and oscillate around .
If Scenario (a) is true, the persistence of malware transmission is obvious, and we will focus our discussion on Scenario (b). Inequalities (47) can be obtained from Lemma 1, and in the case of oscillation, the relationship exists as follows
Where , when , the relationship exists as follows
Thus available
Similarly, for , the relationship exists as follows
By combining Equations (48) and (50), we obtain
Let , and . Just because is bounded, cannot be infinitesimal. Thus, we can derive and . Similarly, for , there is also a positive number .
In this way, we can obtain the sequence , this sequence can be represented as follows
Let , for any , we have and . Therefore, Theorem 3 is proved.
5. Numerical Simulation
In this section, several numerical simulations are given to illustrate the correctness of the above theory. In fact, in order to reflect the characteristics and advantages of the pulse charging model, we make comparisons among the pulse charging model, the continuous charging model and the non-charging model. Among them, the model of continuous charging is derived from paper [21]. In Section 5.1, the malware-free T-period solution of SILS-P is obtained and verified, while the global stability of the other two charging models are presented. In Section 5.2, we analyze the impact of different variables on the threshold in different models. All of the simulations are based on DESKTOP-VEF0OI5 (Intel Core i5, 2.30 GHz) and MATLAB 2016a.
5.1. The Global Stability of the Disease-Free Equilibrium Solution
This subsection aims to verify Theorem 1 and Theorem 2 and compares three charging models when .
In reality, different distribution modes of nodes will affect the communication coverage area of nodes. The larger the communication coverage area is, the corresponding energy consumption will also increase [25]. However, the simulation in this section ignores the differences of communication mechanism and node distribution, and focuses on the change in the number of nodes. The number curve of nodes under the disease-free periodic solution can be realized by setting the relevant parameters in Table 2.

Table 2.
Description of the parameters.
In Section 2, we put forward the pulse charging strategy, which can keep WSNs running permanently under certain circumstances. Through numerical simulation, the change of the number of nodes can be intuitively reflected, and the number of high-energy nodes can reflect the operating state to some extent.
In Section 3, the stability of the periodic solution was proved. As t goes to infinity, there will be no spread of malware in WSNs, and the function of WSNs will depend on the number of remaining high-energy nodes. When t tends to infinity, the number of high-energy nodes can reflect the effect of charging strategy to some extent.
Here, we assume that some parts of the low-energy nodes are charged in a cycle and some nodes will be charged in the next cycle. In order to reflect the pulse charging strategy and obtain a sufficiently small duty cycle, we consider charging as an instantaneous behavior. In addition, the far-field charging efficiency is low [22], and for the sake of being closer to the real physical environment, the charging rate of nodes is set as a small constant.
The WSNs is assumed to have sensor nodes [26] and we suppose the following parameter and the initial condition , , , . Thus, when , whether R0 < 1 or , the whole number of sensor nodes is constant at 20 (i.e., ), comprising the initial value (i.e., ). It is assumed that is the threshold in the continuous charging model and is the threshold of the non-charging model.
From Equation (20) and the value of the previous parameters of SILS-P, we can calculate . From Theorem 2, the disease-free periodic solution (,0,0,0,) is globally stable, as presented in Figure 1. Moreover, it is noted that , ; , ; , ; , .
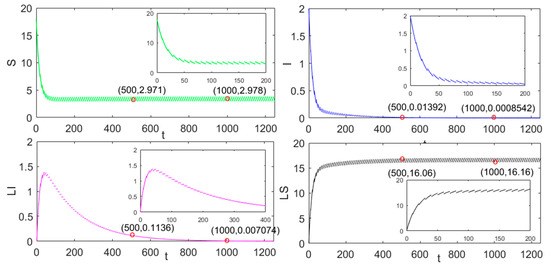
Figure 1.
The global stability of the disease-free periodic solution in the pulse charging model.
It is obvious that the values of S and LS nodes tend to be stable, this characteristic conforms to Equation (35) in Theorem 2. In the same way, the values of I and LI nodes almost disappear with the increase of t which conforms to Equation (29) in Theorem 2. Then, with the same value of parameters, the other two charging models are compared. It is noted that if and [21], we can obtain and .
As shown in Figure 2 and Figure 3, we discover that the number of nodes is 10.47 when tends to be stable in the continuous charging model. In the pulse charging model, the number of nodes is 2.978 when tends to be stable. When the non-charge policy is implemented, the number of nodes is 1.818. From Figure 2 and Figure 3, we can also find out the characteristics of the global stability in Theorem 3 in paper [21].
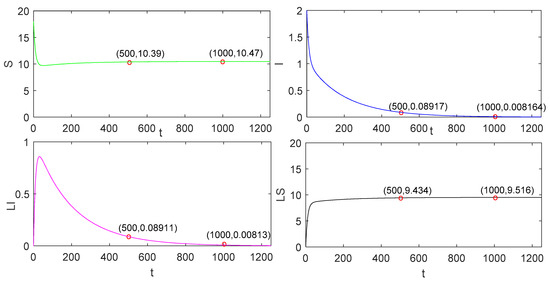
Figure 2.
The global stability of the disease-free equilibrium solution in the continuous charging model.
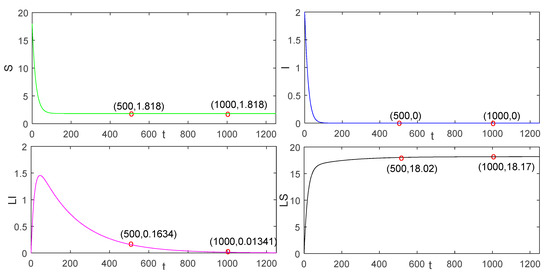
Figure 3.
The global stability of the disease-free equilibrium solution in the non-charging model.
Apparently, it is easy to recognise that the number of nodes is the largest in the continuous charging model, followed by the pulse charging model, and, finally, the non-charging model. Therefore, this phenomenon suggests that the continuous charging is the most efficient, followed by the pulse charging model, and, finally, the non-charging model. However, compared with the continuous charging model in [21], because of the short time slot of charging behavior, our model is more scientific and realistic. We observe that the time at which converges to zero with the pulse charging model is shorter than that with the traditional continuous charging model. In this respect, the advantage of the pulse charging model can be reflected.
5.2. Relations between the Threshold and Parameters
Accordingly, the effects of the parameters on , and will be discussed as follows.
In Figure 4a, the parameters are set as
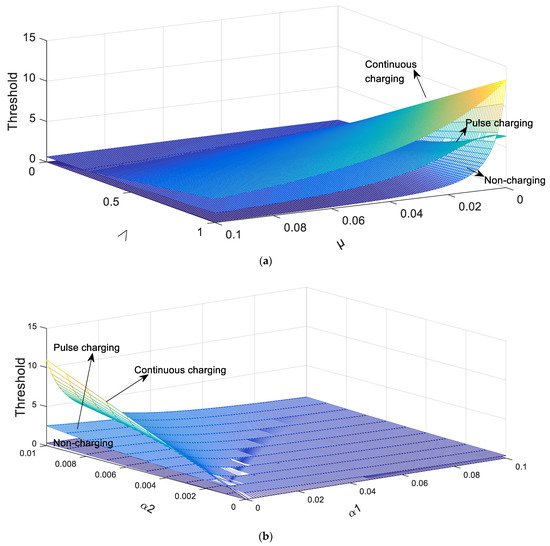
Figure 4.
The relations between the threshold and parameters in three charging models. (a) The effect of and on the threshold in three charging models. (b) The effect of and on the threshold in three charging models.
As shown in Figure 4a, it is obvious that the larger means the threshold larger and the larger means the threshold less. In addition, the value of the threshold in the pulse charging model is larger than that in the continuous charging model, but is smaller than that in the non-charging model in most cases.
Besides, it is assumed that in Figure 4b. It is indisputable that the increase of and the decrease of contribute to the growth of the threshold. Furthermore, it is clear to see that the influence of on the threshold is greater than that of .
In addition, it can be seen from the Figure 4a,b that with the change of parameters, the rate of change of threshold of the pulse charging model is generally smaller than that of the continuous charging model.
6. Conclusions and Future Work
Based on the existing SILS model [21], this paper proposes a pulse charging method, which is more scientific and realistic. Then, the paper analyzes the WSNs under pulse charging, obtains the malware-free T-period solution and carries out the stability analysis. In addition, the persistent spread of malware is also discussed and the persistence of the disease is demonstrated. By comparing the cases and , the dynamic of the malware spreading in WRSNs is revealed. The simulation results show that the malicious software will die out (malware-free T-period solution) or the malicious software will spread continuously (persistence of malware transmission). At the same time, the paper compares the relationship among the threshold and system parameters under three charging strategies: pulse charging, continuous charging and no charging.
In this paper, a pulse charging strategy is introduced in a homogeneous network. However, with the development of the Internet of Things (IOT) industry, heterogeneous network technology has become mainstream, and the pulse charging strategy for the heterogeneous network is one of our future research directions. Additonally, some impulsive models can be extended into depict the dynamics of infectious disease based on the security problem of WRSNs [15] in future.
Author Contributions
Conceptualization, G.L. and Z.L.; methodology, G.L., Z.H. and X.W.; software, Z.H. and X.W.; validation, Z.H. and X.W.; formal analysis, Z.H. and X.W.; investigation, G.L., Z.H., X.W., Z.L., F.H. and X.S.; writing—original draft preparation, X.W.; writing—review and editing, G.L., X.W. and Z.H. All authors have read and agreed to the published version of the manuscript.
Funding
The author acknowledges funding received from the following science foundations: The National Natural Science Foundation of China (61403089, 51975136, 51575116, U1601204, 52075109), The 2020 Department of Education of Guangdong Province Innovative and Strong School Project (Natural Sciences)-Young Innovators Project (Natural Sciences) under Grant 2020KQNCX054, National Key Research and Development Program of China (2018YFB200501), The Science and Technology Innovative Research Team Program in Higher Educational Universities of Guangdong Province (2017KCXTD025), The Innovative Academic Team Project of Guangdong Education System (1201610013), The Special Research Projects in the Key Fields of Guangdong Higher Educational Universities (2019KZDZX1009), The Science and Technology Research Project of Guangdong Province (2017A010102014,2016A010102022), and The Science and Technology Research Project of Guangzhou (201707010293) are all appreciated for supporting this work.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Huang, Y.H.; Zhu, Q.Y. A Differential Game Approach to Decentralized Virus-Resistant Weight Adaptation Policy over Complex Networks. IEEE Trans. Control Netw. Syst. 2020, 7, 944–955. [Google Scholar] [CrossRef] [Green Version]
- Xu, X.T.; Wang, G.C.; Hu, J.T.; Lu, Y.T. Study on Stochastic Differential Game Model in Network Attack and Defense. Secur. Commun. Netw. 2020, 2020, 3417039. [Google Scholar] [CrossRef]
- Wang, H.B.; Feng, L.P. Research on Wireless Sensor Network Security Location Based on Received Signal Strength Indicator Sybil Attack. Discret. Dyn. Nat. Soc. 2020, 2020, 1306084. [Google Scholar] [CrossRef]
- Shanmugavadivel, G.; Gomathy, B.; Ramesh, S.M. An Enhanced Data Security and Task Flow Scheduling in Cloud-enabled Wireless Body Area Network. Wirel. Pers. Commun. 2021. [Google Scholar] [CrossRef]
- Yang, L.; Lu, Y.Z.; Yang, S.M.X.; Guo, T.; Liang, Z.F. A Secure Clustering Protocol with Fuzzy Trust Evaluation and Outlier Detection for Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2021, 17, 4837–4847. [Google Scholar] [CrossRef]
- Khadr, M.H.; Elgala, H.; Rahaim, M.; Khreishah, A.; Ayyash, M.; Little, T. Machine learning-based security-aware spatial modulation for heterogeneous radio-optical networks. Proc. R. Soc. A-Math. Phys. Eng. Sci. 2021, 477. [Google Scholar] [CrossRef]
- Singh, A.; Nagar, J.; Sharma, S.; Kotiyal, V. A Gaussian process regression approach to predict the k-barrier coverage probability for intrusion detection in wireless sensor networks. Expert Syst. Appl. 2021, 172. [Google Scholar] [CrossRef]
- Singh, D.; Kumar, B.; Singh, S.; Chand, S. A Secure IoT-Based Mutual Authentication for Healthcare Applications in Wireless Sensor Networks Using ECC. Int. J. Healthc. Inf. Syst. Inform. 2021, 16, 21–48. [Google Scholar] [CrossRef]
- Sun, N.; Li, T.; Song, G.F.; Xia, H.R. Network Security Technology of Intelligent Information Terminal Based on Mobile Internet of Things. Mob. Inf. Syst. 2021, 2021, 9. [Google Scholar] [CrossRef]
- Reddy, D.L.; Puttamadappa, C.G.; Suresh, H.N.G. Hybrid optimization algorithm for security aware cluster head selection process to aid hierarchical routing in wireless sensor network. IET Commun. 2021. [Google Scholar] [CrossRef]
- Abidoye, A.P.; Kabaso, B. Lightweight models for detection of denial-of-service attack in wireless sensor networks. IET Netw. 2021. [Google Scholar] [CrossRef]
- Al-Saeed, Y.; Eldaydamony, E.; Atwan, A.; Elmogy, M.; Ouda, O. Efficient Key Agreement Algorithm for Wireless Body Area Networks Using Reusable ECG-Based Features. Electronics 2021, 10, 404. [Google Scholar] [CrossRef]
- Liu, B.; Zhou, W.L.; Gao, L.X.; Zhou, H.B.; Luan, T.H.; Wen, S. Malware Propagations in Wireless Ad Hoc Networks. IEEE Trans. Dependable Secur. Comput. 2018, 15, 1016–1026. [Google Scholar] [CrossRef]
- Wang, X.M.; He, Z.B.; Zhang, L.C. A Pulse Immunization Model for Inhibiting Malware Propagation in Mobile Wireless Sensor Networks. Chin. J. Electron. 2014, 23, 810–815. [Google Scholar]
- Liu, G.Y.; Peng, B.H.; Zhong, X.J. Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack-Defense Game Model. Sensors 2021, 21, 594. [Google Scholar] [CrossRef]
- Cao, Y.L.; He, Z.B.; Wang, X.M. Optimal Security Strategy for Malware Propagation in Mobile Wireless Sensor Networks. Acta Electron. Sin. 2016, 44. [Google Scholar] [CrossRef]
- Lin, C.; Guo, C.Y.; Dai, H.P.; Wang, L.; Wu, G.W.; Soc, I.C. Near Optimal Charging Scheduling for 3-D Wireless Rechargeable Sensor Networks with Energy Constraints. In Proceedings of the 2019 39th IEEE International Conference on Distributed Computing Systems, Dallas, TX, USA, 7–10 July 2019; pp. 624–633. [Google Scholar]
- Tian, M.; Jiao, W.; Chen, Y. A Joint Energy Replenishment and Data Collection Strategy in Heterogeneous Wireless Rechargeable Sensor Networks. Sensors 2021, 21, 2930. [Google Scholar] [CrossRef]
- Chawra, V.K.; Gupta, G.P. Hybrid meta-heuristic techniques based efficient charging scheduling scheme for multiple Mobile wireless chargers based wireless rechargeable sensor networks (Jan, 10.1007/s12083-020-01052-8, 2021). Peer-to-Peer Netw. Appl. 2021, 14, 1316. [Google Scholar] [CrossRef]
- Tony, T.; Soh, S.; Chin, K.W.; Lazarescu, M. Link Scheduling in Rechargeable Wireless Sensor Networks with Imperfect Battery and Memory Effects. IEEE Access 2021, 9, 17803–17819. [Google Scholar] [CrossRef]
- Liu, G.Y.; Peng, B.H.; Zhong, X.J. A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security. Sensors 2021, 21, 123. [Google Scholar] [CrossRef] [PubMed]
- Lu, X.; Wang, P.; Niyato, D.; Kim, D.I.; Han, Z. Wireless Charging Technologies: Fundamentals, Standards, and Network Applications. IEEE Commun. Surv. Tutor. 2016, 18, 1413–1452. [Google Scholar] [CrossRef] [Green Version]
- Yang, Y.P.; Xiao, Y.N. The effects of population dispersal and pulse vaccination on disease control. Math. Comput. Model. 2010, 52, 1591–1604. [Google Scholar] [CrossRef]
- Berhe, H.W.; Al-arydah, M. Computational modeling of human papillomavirus with impulsive vaccination. Nonlinear Dyn. 2021, 103, 925–946. [Google Scholar] [CrossRef]
- Zhuang, K.C.; Zhang, H.; Zhang, K.; Zhang, H. Analysis of Spreading Dynamics of Virus in Wireless Sensor Networks. Comput. Sci. 2013, 40, 187–191. [Google Scholar]
- Tang, S.S.; Mark, B.L. Analysis of Virus Spread in Wireless Sensor Networks: An Epidemic Model; IEEE: New York, NY, USA, 2009; pp. 86–91. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).