An Image Encryption Algorithm Using Logistic Map with Plaintext-Related Parameter Values
Abstract
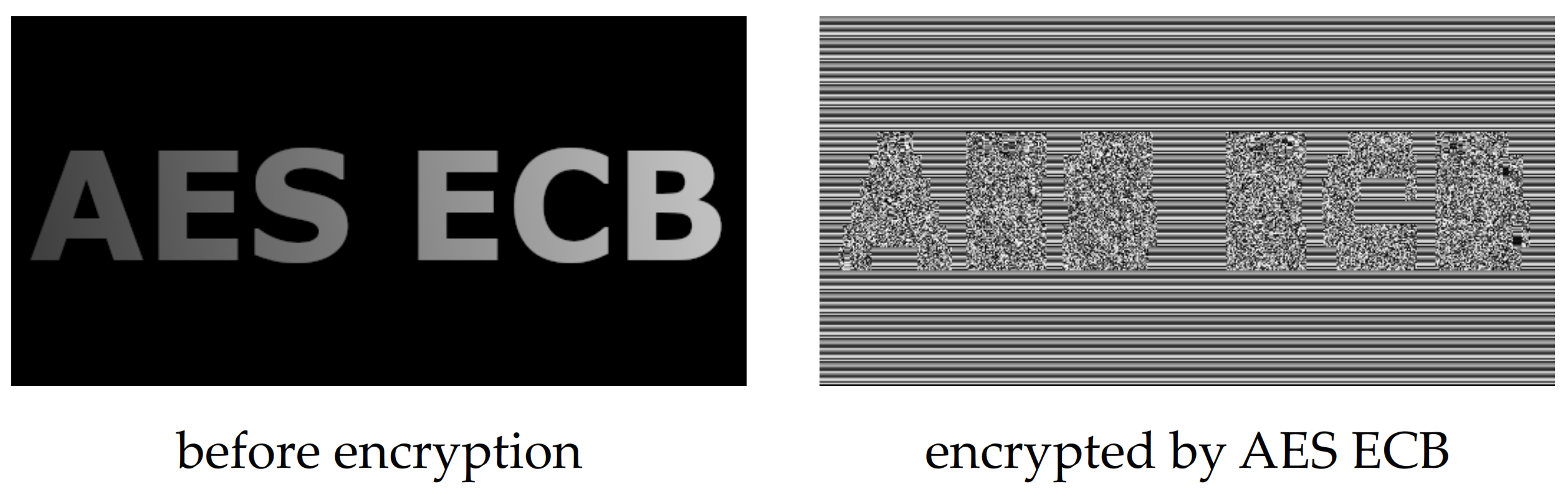
1. Introduction
2. Related Work
3. Proposed Solution
- the usage of a novel plaintext-related parameter modification scheme for LM;
- the whole encryption/decryption scheme is symmetric—these operations are able to extract the required values from either plain or encrypted images;
- it takes into account the knowledge about LM—previously reported drawbacks such as fixed points or periodic cycles [39,41] are suppressed by careful choice of parameter value intervals and alternation of parameter values during the generation of pseudo-random sequences. This could be viewed as a novelty since it is not common even for new proposals.
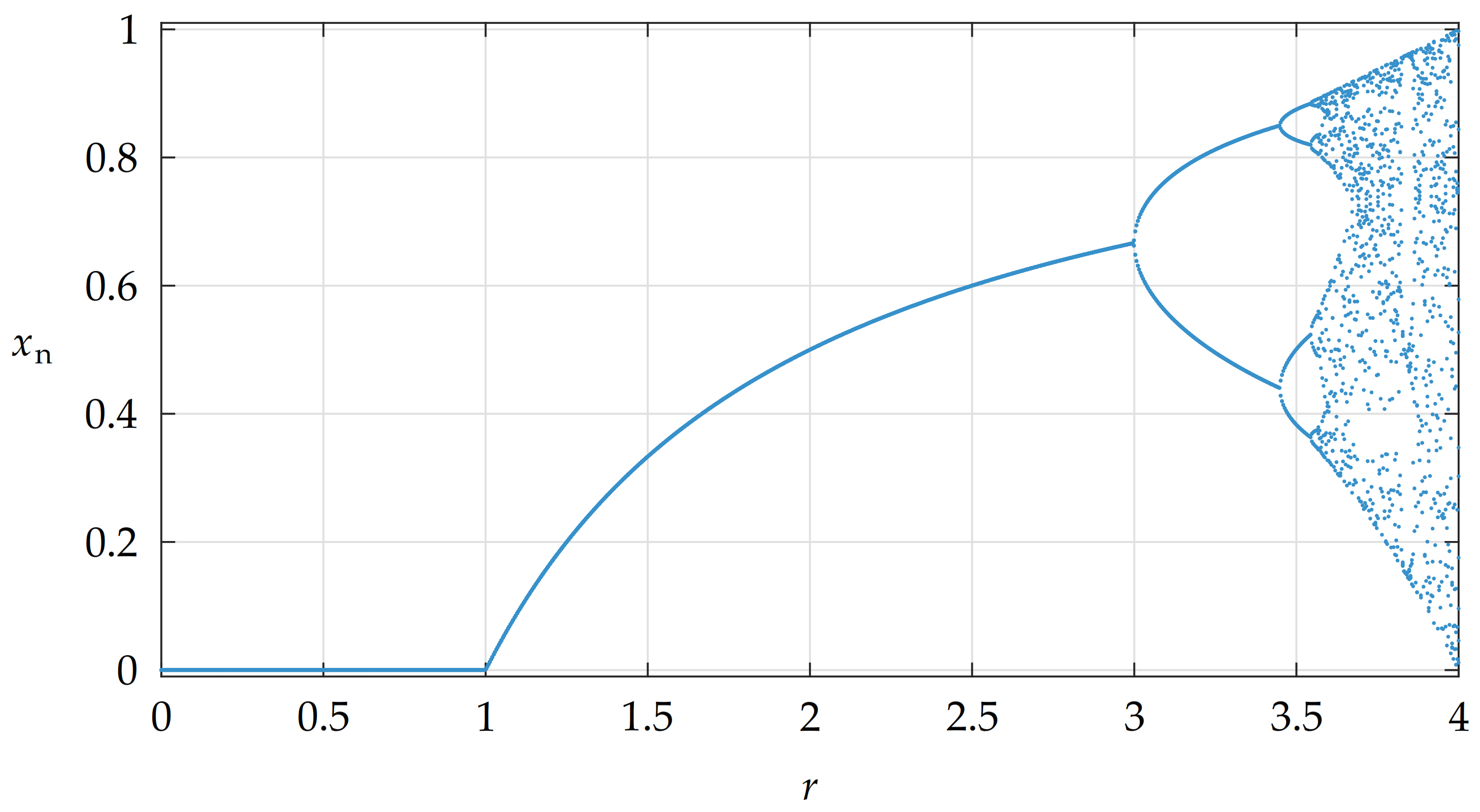
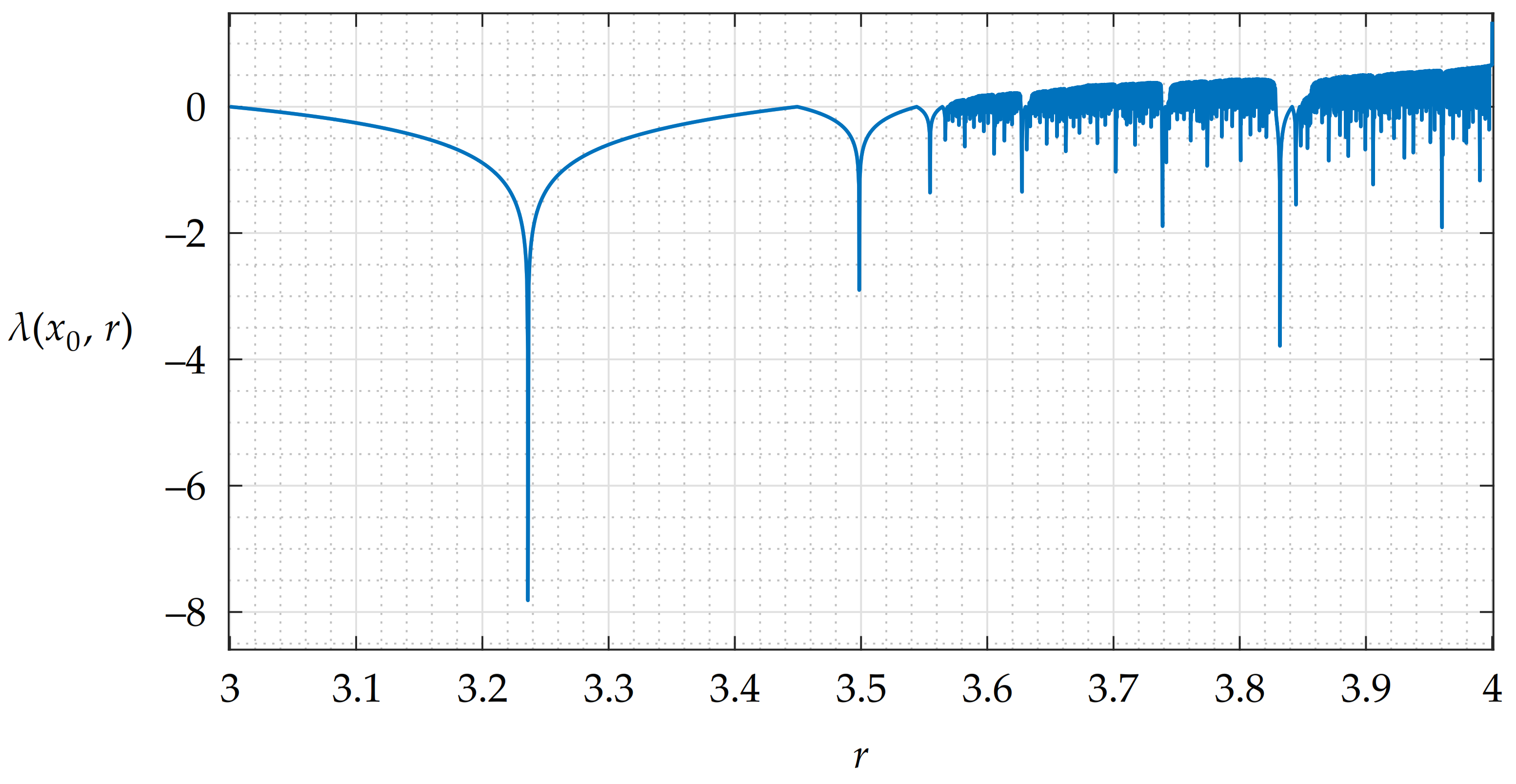
3.1. Logistic Map and Its Properties
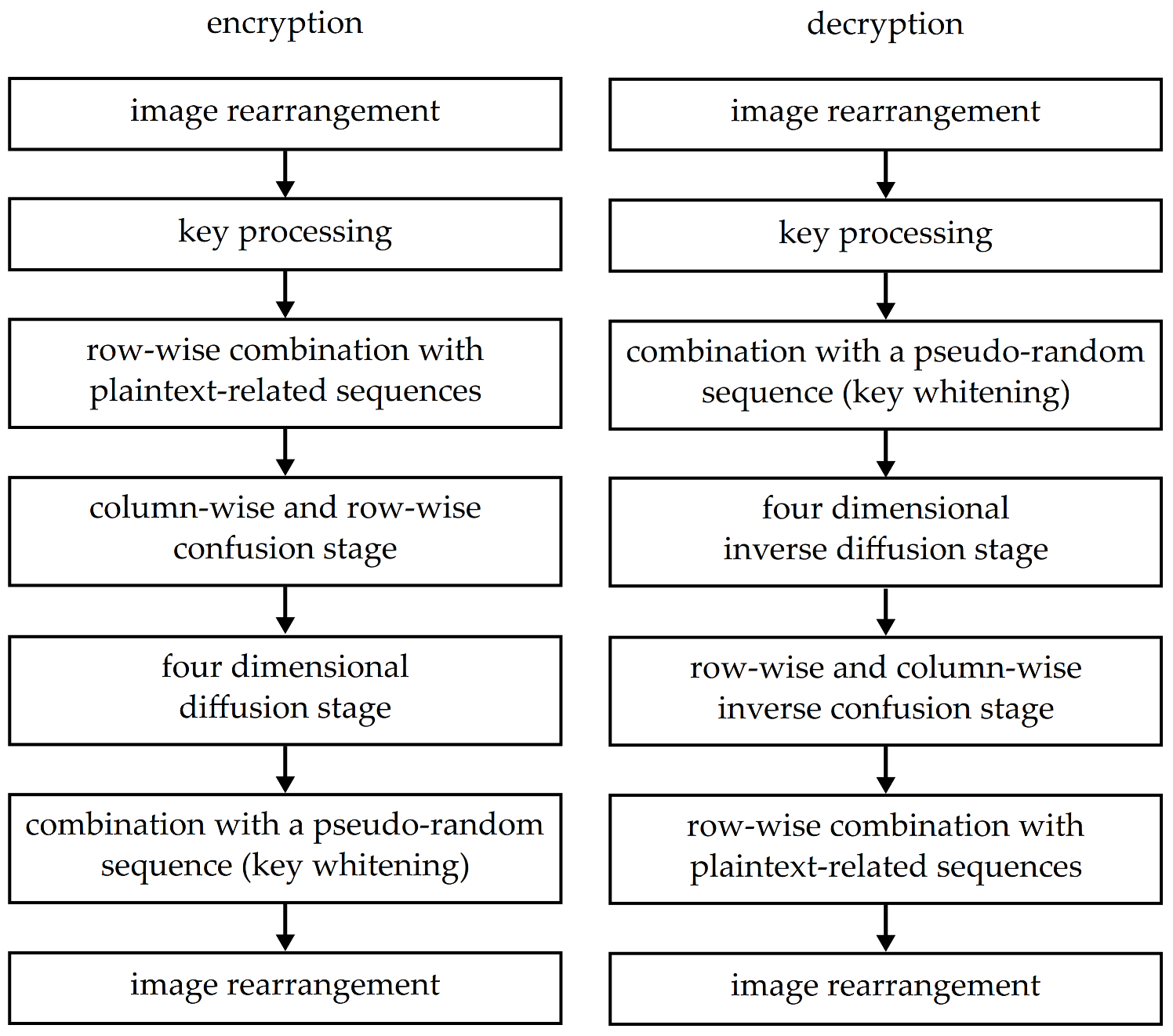
3.2. Encryption
3.3. Decryption
4. Experimental Results
4.1. Key Space Size and Key Sensitivity
4.2. Robustness against Image Modification
4.3. Statistical Properties of the Plaintext-Related Sequence
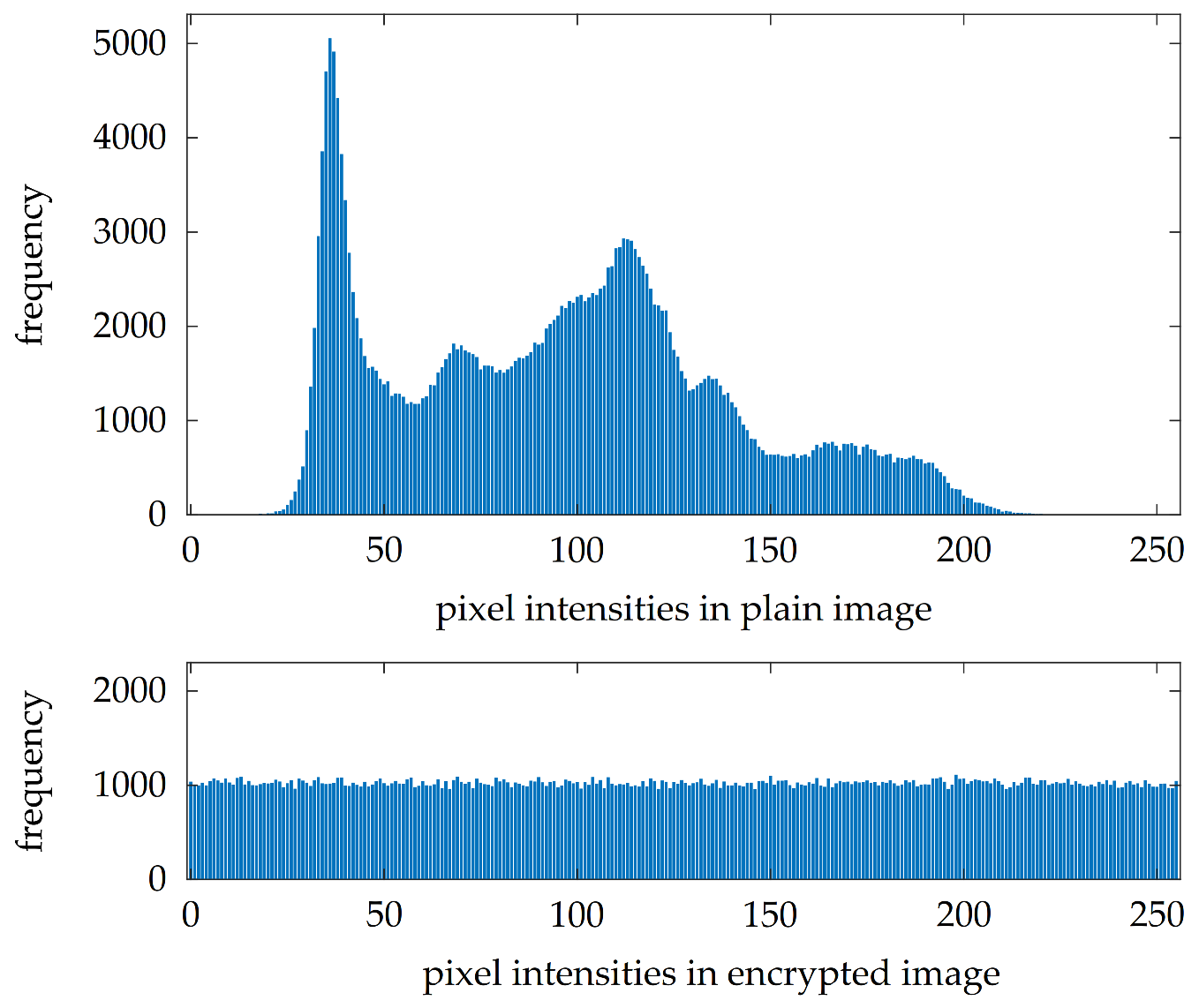
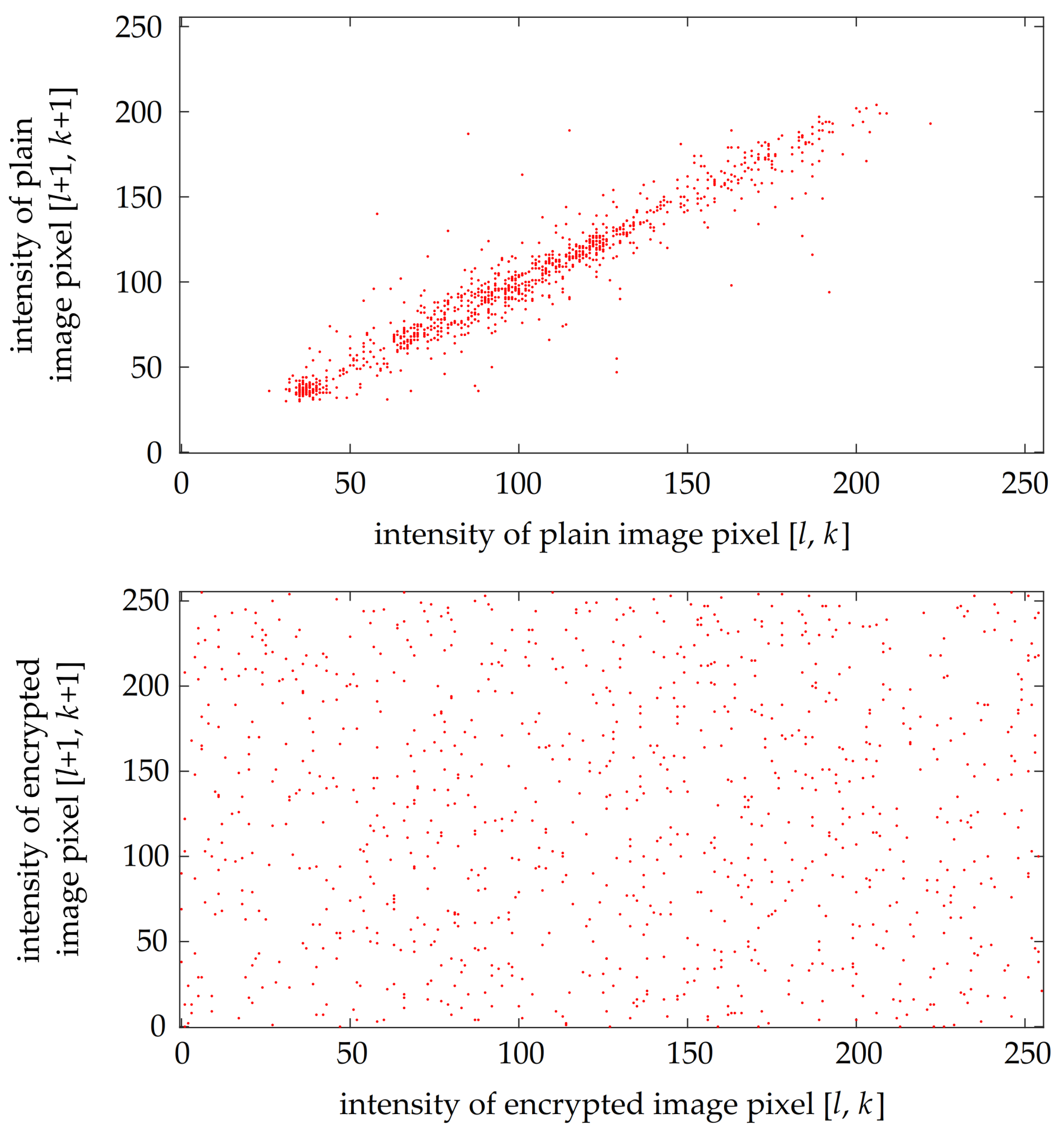
4.4. Properties Regarding Statistical Attacks
4.5. Properties Regarding Differential Attacks
4.6. Measurement of Computational Complexity
4.7. Discussion
4.8. Comparison with Similar Work
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| CPU | Central Processing Unit |
| ECB | Electronic CodeBook |
| LE | Lyapunov Exponent |
| LM | Logistic Map |
| NPCR | Number of Pixel Change Ratio |
| OS | Operating System |
| RAM | Random Access Memory |
| UACI | Unified Average Changing Intensity |
| XOR | eXclusive OR |
References
- Pichler, F.; Scharinger, J. Finite dimensional generalized baker dynamical systems for cryptographic applications. In Proceedings of the International Conference on EUROCAST 1995, Innsbruck, Austria, 22–26 May 1995; Springer: Berlin, Germany, 1995; pp. 465–476. [Google Scholar]
- Fridrich, J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 1998, 8, 1259–1284. [Google Scholar] [CrossRef]
- Gleick, J. Chaos: Making a New Science; Vintage Books: London, UK, 1998; 380p. [Google Scholar]
- Solak, E.; Cokal, C.; Yildiz, O.T.; Biyikoglu, T. Cryptanalysis of Fridrich’s chaotic image encryption. Int. J. Bifurc. Chaos 2010, 20, 1405–1413. [Google Scholar] [CrossRef]
- FIPS 197: ‘Advanced Encryption Standard (AES)’. Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197.pdf (accessed on 3 September 2021).
- Hajduk, V.; Broda, M.; Kovac, O.; Levicky, D. Image steganography with using QR code and cryptography. In Proceedings of the International Conference Radioelektronika 2016, Kosice, Slovakia, 19–20 April 2016; IEEE: Danvers, MA, USA, 2016; pp. 350–353. [Google Scholar]
- Oravec, J.; Turan, J. Substitution steganography with security improved by chaotic image encryption. In Proceedings of the International Conference Informatics 2017, Poprad, Slovakia, 14–16 November 2017; IEEE: Danvers, MA, USA, 2017; pp. 284–288. [Google Scholar]
- Fang, D.; Sun, S. A new scheme for image steganography based on hyper-chaotic map and DNA sequence. J. Inf. Hiding Multim. Signal Process. 2018, 9, 392–399. [Google Scholar]
- Chen, X.; Hu, C.-J. Adaptive medical image encryption algorithm based on multiple chaotic mapping. Saudi J. Biol. Sci. 2017, 24, 1821–1827. [Google Scholar] [CrossRef]
- Abundiz-Perez, F.; Cruz-Hernandez, C.; Murillo-Escobar, M.A.; Lopez-Gutierrez, R.M.; Arellano-Delgado, A. A fingerprint image encryption scheme based on hyperchaotic Rossler map. Math. Probl. Eng. 2016, 2016, 2670494. [Google Scholar] [CrossRef]
- Xie, E.Y.; Li, C.; Yu, S.; Lu, J. On the cryptanalysis of Fridrich’s chaotic image encryption scheme. Signal Process. 2017, 132, 150–154. [Google Scholar] [CrossRef]
- Preishuber, M.; Hutter, T.; Katzenbeisser, S.; Uhl, A. Depreciating motivation and empirical security analysis of chaos-based image and video encryption. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2137–2150. [Google Scholar] [CrossRef]
- Kovac, O.; Lukacs, P.; Gladisova, I. Textures classification based on DWT. In Proceedings of the International Conference Radioelektronika 2018, Prague, Czech Republic, 19–20 April 2018; IEEE: Danvers, MA, USA, 2018; pp. 1–5. [Google Scholar]
- Mihalik, J.; Gladisova, I. Color content descriptors of images by vector quantization. Adv. Electr. Electron. Eng. 2020, 18, 264–273. [Google Scholar]
- NIST SP 800-38A: ‘Recommendation for Block Cipher Modes of Operation: Methods and Techniques’. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-38a.pdf (accessed on 3 September 2021).
- Gueron, S. Intel® Advanced Encryption Standard (AES) New Instructions Set. Available online: https://www.intel.com/content/dam/doc/white-paper/advanced-encryption-standard-new-instructions-set-paper.pdf (accessed on 3 September 2021).
- Liu, L.; Miao, S. A new image encryption algorithm based on logistic chaotic map with varying parameter. SpringerPlus 2016, 5, 289–300. [Google Scholar] [CrossRef]
- Chai, X.; Zheng, X.; Gan, Z.; Chen, Y. Exploiting plaintext-related mechanism for secure color image encryption. Neural Comput. Appl. 2020, 32, 8065–8088. [Google Scholar] [CrossRef]
- Zheng, J.; Hu, H. A symmetric image encryption scheme based on hybrid analog-digital chaotic system and parameter selection mechanism. Multimed. Tools Appl. 2021, 80, 20883–20905. [Google Scholar] [CrossRef]
- Masood, F.; Ahmad, J.; Syed, A.S.; Jamal, S.S.; Hussain, I. A novel hybrid secure image encryption based on Julia set of fractals and 3D Lorenz chaotic map. Entropy 2020, 22, 274. [Google Scholar] [CrossRef]
- Masood, F.; Driss, M.; Boulila, W.; Ahmad, J.; Rehman, S.U.; Jan, S.U.; Qayyum, A.; Buchanan, W.J.A. lightweight chaos-based medical image encryption scheme using random shuffling and XOR operations. Wirel. Pers. Commun. 2021, 23, 1–28. [Google Scholar]
- Wu, Z.; Pan, P.; Sun, C.; Zhao, B. Plaintext-related dynamic key chaotic image encryption algorithm. Entropy 2021, 23, 1159. [Google Scholar] [CrossRef]
- Moussa, K.H.; El Naggary, A.I.; Mohamed, H.G. Non-linear hopped chaos parameters-based image encryption algorithm using histogram equalization. Entropy 2021, 23, 535. [Google Scholar] [CrossRef]
- Pourasad, Y.; Ranjbarzadeh, R.; Mardani, A. A new algorithm for digital image encryption based on chaos theory. Entropy 2021, 23, 341. [Google Scholar] [CrossRef]
- Kanso, A.; Ghebleh, M. A novel image encryption algorithm based on a 3D chaotic map. Commun. Nonlinear Sci. 2012, 17, 2943–2959. [Google Scholar] [CrossRef]
- Fu, C.; Hou, S.; Zhou, W.; Liu, W.; Wang, D. A chaos-based image encryption scheme with a plaintext related diffusion. In Proceedings of the 2013 9th International Conference on Information, Communications & Signal Processing, Tainan, Taiwan, 10–13 December 2013; IEEE: Danvers, MA, USA, 2013; pp. 1–5. [Google Scholar]
- Zhang, Y. A chaotic system based image encryption algorithm using plaintext-related confusion. Indones. J. Electr. Eng. Comput. Sci. 2014, 12, 7952–7962. [Google Scholar] [CrossRef]
- Norouzi, B.; Mirzakuchaki, S.; Seyedzadeh, S.M.; Mosavi, M.R. A simple, sensitive and secure image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Multimed. Tools Appl. 2014, 71, 1469–1497. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, D.; Wen, W.; Li, M. Breaking an image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Nonlinear Dyn. 2014, 76, 1645–1650. [Google Scholar] [CrossRef]
- Murillo-Escobar, M.A.; Cruz-Hernandez, C.; Abundiz-Perez, F.; Lopez-Gutierrez, R.M.; Acosta Del Campo, O.R. A RGB image encryption algorithm based on total plain image characteristics and chaos. Signal Process. 2015, 109, 119–131. [Google Scholar] [CrossRef]
- Fan, H.; Li, M.; Liu, D.; An, K. Cryptanalysis of a plaintext-related chaotic RGB image encryption scheme using total plain image characteristics. Multimed. Tools Appl. 2018, 77, 20103–20127. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Zhang, M. A fast chaos-based image encryption scheme with a novel plain image-related swapping block permutation and block diffusion. Multimed. Tools Appl. 2017, 76, 15561–15585. [Google Scholar] [CrossRef]
- Wang, X.; Zhu, X.; Wu, X.; Zhang, Y. Image encryption algorithm based on multiple mixed hash functions and cyclic shift. Opt. Lasers Eng. 2018, 107, 370–379. [Google Scholar] [CrossRef]
- Li, Z.; Peng, C.; Li, L.; Zhu, X. A novel plaintext-related image encryption scheme using hyper-chaotic system. Nonlinear Dyn. 2018, 94, 1319–1333. [Google Scholar] [CrossRef]
- Li, Z.; Peng, C.; Tan, W.; Li, L. A novel chaos-based image encryption scheme by using randomly DNA encode and plaintext related permutation. Appl. Sci. 2020, 10, 7469. [Google Scholar] [CrossRef]
- Sun, S.; Guo, Y.; Wu, R. A novel image encryption scheme based on 7D hyperchaotic system and row-column simultaneous swapping. IEEE Access 2019, 7, 28539–28547. [Google Scholar] [CrossRef]
- Zhang, Q.; Han, J. A novel color image encryption algorithm based on image hashing, 6D hyperchaotic and DNA coding. Multimed. Tools Appl. 2021, 80, 13841–13864. [Google Scholar] [CrossRef]
- Oravec, J.; Turan, J.; Ovsenik, L.; Ivaniga, T.; Solus, D.; Marton, M. Asymmetric image encryption approach with plaintext-related diffusion. Radioengineering 2018, 27, 281–288. [Google Scholar] [CrossRef]
- Oravec, J.; Turan, J.; Ovsenik, L.; Huszanik, T. A chaotic image encryption algorithm robust against the phase space reconstruction attacks. Acta Polytech. Hung. 2019, 16, 37–57. [Google Scholar]
- Ovsenik, L.; Turan, J.; Huszanik, T.; Oravec, J.; Kovac, O.; Oravec, M. Image encryption algorithm with plaintext related chaining. Comput. Inform. 2019, 38, 647–678. [Google Scholar] [CrossRef]
- Oravec, J.; Ovsenik, L.; Turan, J.; Huszanik, T. Mitigating drawbacks of logistic map for image encryption algorithms. Comput. Inform. 2020, 39, 1250–1281. [Google Scholar] [CrossRef]
- Oravec, J.; Ovsenik, L.; Papaj, J. An image encryption algorithm with a plaintext-related quantisation scheme. IET Image Process 2021, 15, 2039–2055. [Google Scholar] [CrossRef]
- Schneier, B. Applied Cryptography: Protocols, Algorithms, and Source Code in C; Wiley: New York, NY, USA, 1996; 1027p. [Google Scholar]
- May, R.R. Simple mathematical models with very complicated dynamics. Nature 2004, 261, 459–467. [Google Scholar] [CrossRef]
- Persohn, K.J.; Povinelli, R.J. Analyzing logistic map pseudorandom number generators for periodicity induced by finite precision floating-point representation. Chaos Solitons Fractals 2012, 45, 238–245. [Google Scholar] [CrossRef]
- Arroyo, D.; Alvarez, G.; Fernandez, V. On the inadequacy of the logistic map for cryptographic applications. In Proceedings of the 10th Spanish Meeting on Cryptology and Information Security, Salamanca, Spain, 2–5 September 2008; Universidad de Salamanca: Salamanca, Spain, 2008; pp. 77–82. [Google Scholar]
- Knuth, D.E. The Art of Computer Programming; Addison-Wesley: Boston, MA, USA, 2005; 1872p. [Google Scholar]
- Steingartner, W.; Eldojali, M.A.; Radakovic, D.; Dostal, J. Software support for course in semantics of programming languages. In Proceedings of the International Scientific Conference on Informatics 2017, Poprad, Slovakia, 14–16 November 2017; IEEE: Danvers, MA, USA, 2017; pp. 359–364. [Google Scholar]
- IEEE 754-2019: ‘IEEE Standard for Floating-Point Arithmetic’. Available online: https://ieeexplore.ieee.org/servlet/opac?punumber=8766227 (accessed on 3 September 2021).
- Steingartner, W.; Galinec, D. The role of categorical structures in infinitesimal calculus. J. Appl. Math. Comput. Mech. 2013, 12, 107–119. [Google Scholar] [CrossRef]
- Steingartner, W.; Polakova, A.; Praznak, P.; Novitzka, V. Linear logic in computer science. J. Appl. Math. Comput. Mech. 2015, 14, 91–100. [Google Scholar] [CrossRef][Green Version]
- The USC-SIPI Image Database. Available online: http://sipi.usc.edu/database/ (accessed on 3 September 2021).
- NIST SP 800-22 Rev. 1a: ‘A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications’. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-22r1a.pdf (accessed on 3 September 2021).
- Broda, M.; Hajduk, V.; Levicky, D. Universal statistical steganalytic method. J. Electr. Eng. 2017, 68, 117–124. [Google Scholar] [CrossRef]
- Wu, Y.; Noonan, J.P.; Agaian, S. NPCR and UACI randomness tests for image encryption. J. Sel. Areas Telecommun. 2011, 1, 31–38. [Google Scholar]
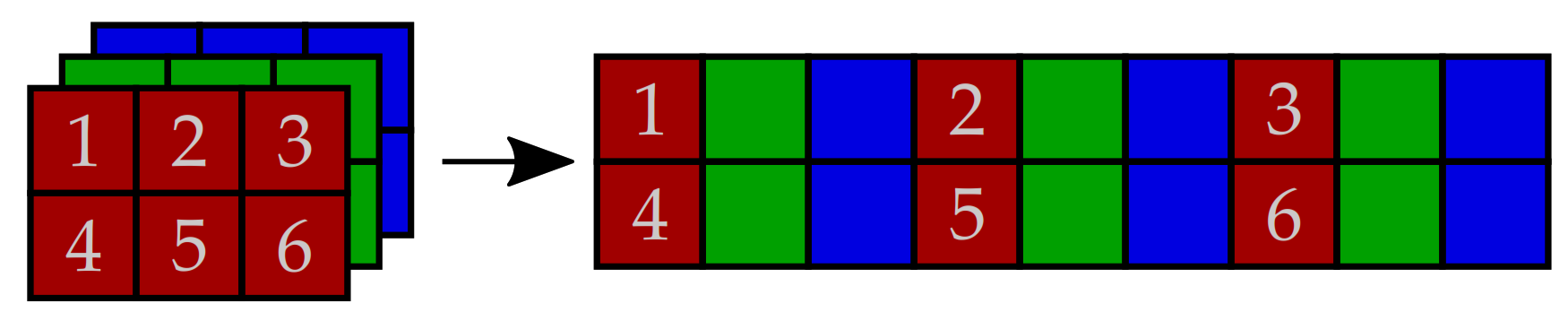
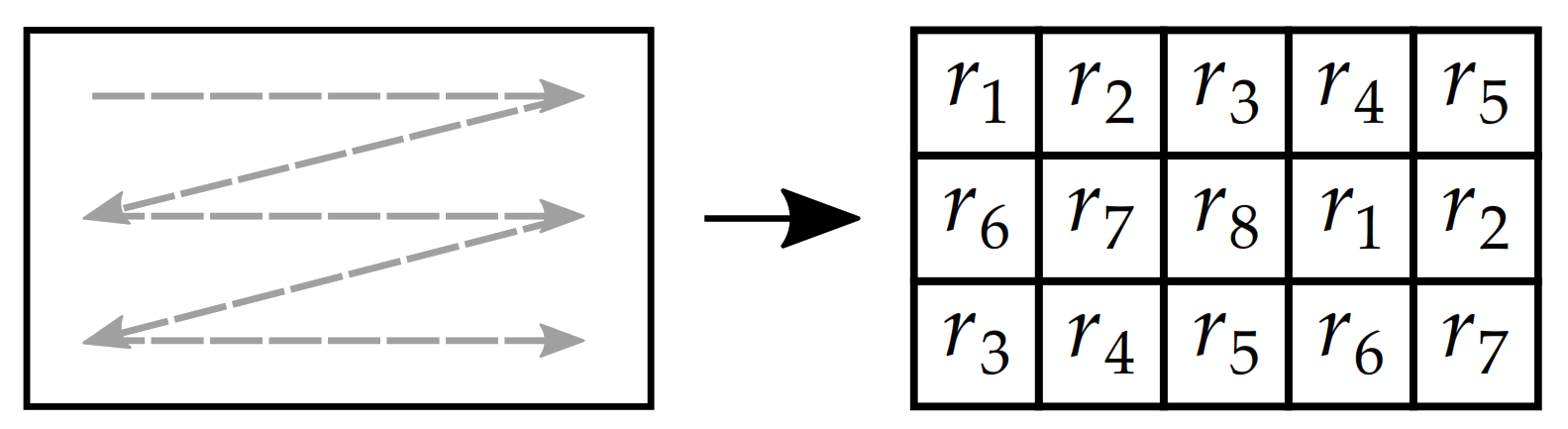
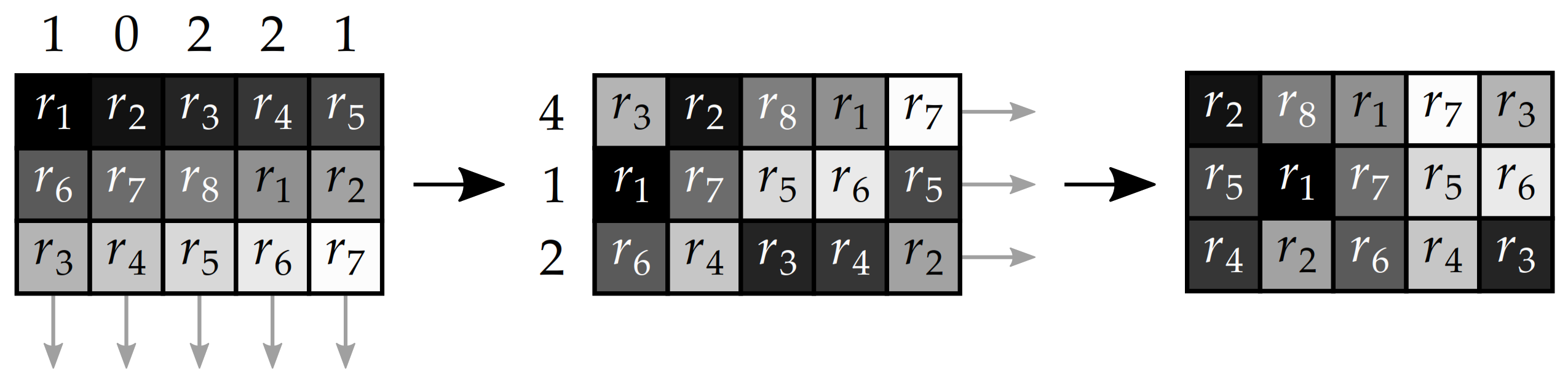



| Generated Sequence | Parameter Values Pattern | Sequence Length | Maximal Element Value Q | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| h | ||||||||||
| 255 | ||||||||||
| h | ||||||||||
| 255 | ||||||||||
| Scanning Direction | Scanning Order | Addition (Mod 256) | XOR | |
|---|---|---|---|---|
| Rows l | Columns k | |||
| top to bottom | : | |||
| left to right | : | |||
| bottom to top | : | |||
| right to left | : | |||
| Key | Value |
|---|---|
| 0× C9 0F DA A2 21 68 C2 34 C4 C6 62 8B 80 DC 1C D1 | |
| 0× C9 0F DA A2 21 68 C2 34 C5 C6 62 8B 80 DC 1C D1 | |
| 0× 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |
| Test | Required Pass Rate | Obtained Successful Results |
|---|---|---|
| Frequency (monobit) | 96/100 | 99/100 |
| Frequency within a block (M = 128 bits) | 96/100 | 98/100 |
| Runs | 96/100 | 96/100 |
| Longest run of ones in a block | 96/100 | 97/100 |
| Binary matrix rank | 96/100 | 98/100 |
| Discrete Fourier transform (spectral) | 96/100 | 98/100 |
| Non-overlapping template matching (m = 9 bits, first p-value) | 96/100 | 97/100 |
| Overlapping template matching (m = 9 bits) | 96/100 | 96/100 |
| Maurer’s universal statistic | 96/100 | 98/100 |
| Linear complexity (M = 500 bits) | 96/100 | 98/100 |
| Serial (m = 16 bits, first p-value) | 96/100 | 98/100 |
| Approximate entropy (m = 10 bits) | 96/100 | 96/100 |
| Cumulative sums (first p-value) | 96/100 | 99/100 |
| Random excursions (first p-value) | 60/63 | 62/63 |
| Random excursions variant (first p-value) | 60/63 | 63/63 |
| Image, Color Plane and Key | [-] | [-] | [-] | [-] | H [bits/px] | [%] | [%] | |
|---|---|---|---|---|---|---|---|---|
| R | 510,371 | 0.9723 | 0.9731 | 0.9535 | 7.5889 | not reported | ||
| G | 1,290,286 | 0.9734 | 0.9709 | 0.9531 | 7.106 | |||
| B | 1,908,534 | 0.9702 | 0.9733 | 0.9528 | 6.8147 | |||
| R | 1094 | −0.0019 | 0.002 | −0.0012 | 7.9992 | 99.6143 | 33.4857 | |
| G | 1003 | −0.0005 | −0.0018 | −0.0001 | 7.9993 | 99.6134 | 33.4805 | |
| B | 929 | −0.0014 | −0.001 | −0.0022 | 7.9994 | 99.6144 | 33.4811 | |
| R | 1064 | 0.0017 | 0.0008 | −0.0016 | 7.9993 | 99.6135 | 33.4816 | |
| G | 1046 | −0.001 | 0.0024 | 0.0021 | 7.9993 | 99.6142 | 33.4839 | |
| B | 1137 | 0.0002 | 0.0004 | −0.0014 | 7.9992 | 99.6145 | 33.4822 | |
| R | 1024 | −0.0029 | 0.0017 | 0.0011 | 7.9993 | 99.6151 | 33.486 | |
| G | 1007 | −0.0015 | 0.0012 | −0.0018 | 7.9993 | 99.6138 | 33.4823 | |
| B | 909 | −0.0027 | −0.0003 | 0.0007 | 7.9994 | 99.6157 | 33.4855 | |
| R | 852,749 | 0.9577 | 0.965 | 0.9477 | 7.3388 | not reported | ||
| G | 1,273,532 | 0.9609 | 0.9681 | 0.9558 | 7.4963 | |||
| B | 1,965,713 | 0.963 | 0.965 | 0.9523 | 7.0583 | |||
| R | 1012 | 0.0024 | −0.0004 | −0.0013 | 7.9993 | 99.614 | 33.4816 | |
| G | 988 | −0.0006 | 0.0017 | 0.0012 | 7.9993 | 99.6164 | 33.4832 | |
| B | 1099 | −0.0003 | 0.0028 | −0.001 | 7.9992 | 99.6154 | 33.4818 | |
| R | 878 | 0.0006 | 0.0014 | −0.0023 | 7.9994 | 99.6146 | 33.4818 | |
| G | 909 | 0.0014 | −0.0005 | 0.0007 | 7.9994 | 99.6132 | 33.4808 | |
| B | 841 | −0.0007 | −0.001 | 0.0025 | 7.9994 | 99.6166 | 33.4846 | |
| R | 1070 | 0.0017 | 0.0022 | −0.0004 | 7.9993 | 99.6158 | 33.4864 | |
| G | 947 | 0.0011 | 0.001 | −0.0009 | 7.9993 | 99.6157 | 33.4874 | |
| B | 1036 | −0.0006 | −0.0003 | 0.0023 | 7.9993 | 99.6147 | 33.483 | |
| - | 750,764 | 0.8435 | 0.7129 | 0.6758 | 7.3579 | not reported | ||
| 1123 | 0.0013 | 0.0014 | 0.0001 | 7.9992 | 99.6153 | 33.4807 | ||
| 1102 | −0.0009 | −0.0027 | 0.0014 | 7.9992 | 99.6142 | 33.4808 | ||
| 1046 | −0.0019 | −0.0013 | −0.0004 | 7.9993 | 99.6149 | 33.4856 | ||
| - | 1,039,126 | 0.9709 | 0.9765 | 0.9561 | 7.2344 | not reported | ||
| 993 | 0.0006 | −0.0015 | −0.0008 | 7.9993 | 99.6127 | 33.483 | ||
| 1046 | −0.0009 | 0.0029 | 0.0022 | 7.9993 | 99.6138 | 33.4836 | ||
| 995 | −0.0013 | 0.0026 | 0.0018 | 7.9993 | 99.6144 | 33.4847 | ||
| - | 478,900 | 0.9698 | 0.9767 | 0.9628 | 7.5943 | not reported | ||
| 1108 | 0.0013 | −0.0006 | −0.0012 | 7.9992 | 99.614 | 33.484 | ||
| 1075 | −0.002 | −0.0007 | −0.0016 | 7.9993 | 99.6132 | 33.4847 | ||
| 935 | 0.0007 | −0.0026 | 0.0004 | 7.9994 | 99.6137 | 33.4806 | ||
| - | 718,875 | 0.9748 | 0.9657 | 0.9538 | 7.4847 | not reported | ||
| 918 | 0.0011 | −0.0004 | −0.0016 | 7.9994 | 99.6135 | 33.4844 | ||
| 1042 | −0.0003 | −0.002 | 0.0014 | 7.9993 | 99.6154 | 33.4824 | ||
| 906 | 0.0019 | −0.0019 | −0.0003 | 7.9994 | 99.6148 | 33.4855 | ||
| Image and Key | [ms] | [ms] | [MB/s] | [MB/s] | [cycles/B] | [cycles/B] | |
|---|---|---|---|---|---|---|---|
| 493.0626 | 487.9469 | 1.5211 | 1.5371 | 1567.4 | 1551.14 | ||
| 490.6985 | 488.0388 | 1.5284 | 1.5368 | 1559.89 | 1551.43 | ||
| 493.014 | 487.4362 | 1.5211 | 1.5371 | 1567.25 | 1549.52 | ||
| 491.7683 | 488.2473 | 1.5251 | 1.5361 | 1563.29 | 1552.1 | ||
| 492.1848 | 490.5268 | 1.5238 | 1.529 | 1564.61 | 1559.34 | ||
| 491.2771 | 488.7079 | 1.5266 | 1.5347 | 1561.73 | 1553.56 | ||
| 149.4431 | 143.812 | 1.6729 | 1.7384 | 1425.2 | 1371.5 | ||
| 149.4405 | 143.4985 | 1.6729 | 1.7422 | 1425.18 | 1368.51 | ||
| 149.2358 | 143.409 | 1.6752 | 1.7433 | 1423.22 | 1367.65 | ||
| 149.4753 | 143.4511 | 1.6725 | 1.7428 | 1425.51 | 1368.06 | ||
| 149.3001 | 143.7227 | 1.6745 | 1.7395 | 1423.84 | 1370.65 | ||
| 149.5298 | 144.3434 | 1.6719 | 1.732 | 1426.03 | 1376.52 | ||
| 149.5122 | 143.768 | 1.6721 | 1.7389 | 1425.86 | 1371.08 | ||
| 149.4405 | 143.4985 | 1.6729 | 1.7422 | 1425.18 | 1368.51 | ||
| 149.2358 | 143.409 | 1.6752 | 1.7433 | 1423.22 | 1367.65 | ||
| 149.2376 | 143.7204 | 1.6752 | 1.7395 | 1423.24 | 1370.62 | ||
| 149.1357 | 143.3698 | 1.6763 | 1.7437 | 1422.27 | 1367.28 | ||
| 149.1004 | 143.4411 | 1.6767 | 1.7429 | 1421.93 | 1367.96 | ||
| Approach | [-] | [-] | [-] | H [bits/px] | [%] | [%] | [cycles/B] |
|---|---|---|---|---|---|---|---|
| Red color plane of true color image | |||||||
| proposed | −0.0019 | 0.002 | −0.0012 | 7.9992 | 99.6143 | 33.4857 | 1567.4 |
| [25] | −0.0029 | −0.015 | 0.0129 | 7.997 | 99.62 | 33.51 | ∼2270 |
| [30] | 0.0135 | - | 7.9974 | 99.63 | 33.31 | 648.53 | |
| Grayscale image | |||||||
| proposed | 0.0006 | −0.0015 | −0.0008 | 7.9993 | 99.6127 | 33.483 | 1425.51 |
| [19] | 0.0077 | 0.0053 | 0.0003 | 7.9993 | 99.606 | 33.4714 | 4205.32 |
| [27] | −0.0046 | −0.0511 | −0.0168 | 7.9993 | 99.6101 | 33.4679 | 8230.32 |
| [32] | 0.0044 | 0.0151 | 0.0012 | 7.9993 | 99.62 | 33.45 | 15,120.97 |
| [33] | −0.0037 | −0.0029 | 0.0047 | 7.9975 | 99.5956 | 33.5512 | 43,151.97 |
| [34] | 0.0013 | 0.0008 | 0.0066 | 7.9993 | 99.6107 | 33.436 | 5185.19 |
| [35] | 0.0003 | 0.0019 | 0.0003 | 7.9993 | 99.6159 | 33.4846 | 4945.37 |
| [37] | −0.0003 | −0.0024 | −0.0022 | 7.9994 | 99.6096 | 33.4599 | 72,452.57 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oravec, J.; Ovsenik, L.; Papaj, J. An Image Encryption Algorithm Using Logistic Map with Plaintext-Related Parameter Values. Entropy 2021, 23, 1373. https://doi.org/10.3390/e23111373
Oravec J, Ovsenik L, Papaj J. An Image Encryption Algorithm Using Logistic Map with Plaintext-Related Parameter Values. Entropy. 2021; 23(11):1373. https://doi.org/10.3390/e23111373
Chicago/Turabian StyleOravec, Jakub, Lubos Ovsenik, and Jan Papaj. 2021. "An Image Encryption Algorithm Using Logistic Map with Plaintext-Related Parameter Values" Entropy 23, no. 11: 1373. https://doi.org/10.3390/e23111373
APA StyleOravec, J., Ovsenik, L., & Papaj, J. (2021). An Image Encryption Algorithm Using Logistic Map with Plaintext-Related Parameter Values. Entropy, 23(11), 1373. https://doi.org/10.3390/e23111373







