1. Introduction
Quantum key distribution (QKD), which enables two remote legitimate parties (i.e., Alice and Bob) to share unconditional secret keys against a potential eavesdropper, is a major practical quantum cryptography technology in quantum information [
1]. There are mainly two categories of QKD protocols, namely discrete-variable (DV) protocols [
2,
3,
4,
5,
6] and continuous-variable (CV) protocols [
7,
8,
9,
10,
11], which, respectively, encode information on discrete variables (such as the polarization or the phase of single photons) and continuous variables (such as the quadratures of coherent states).
The DV-QKD needs a high-cost single-photon detector requiring cryogenic temperatures to measure the received quantum state, which presents a challenge for its widespread implementation. Compared to the DV-QKD, the CV-QKD takes the advantage of using a standard and cost-effective detector that is routinely deployed in standard telecom components working at room temperature. The security proof of CV-QKD against general attacks has been provided [
12,
13,
14,
15]. Many experiments of CV-QKD have been successfully implemented, especially the integrated silicon photonic chip for CV-QKD that offers new possibilities for low-cost and portable quantum communication [
16].
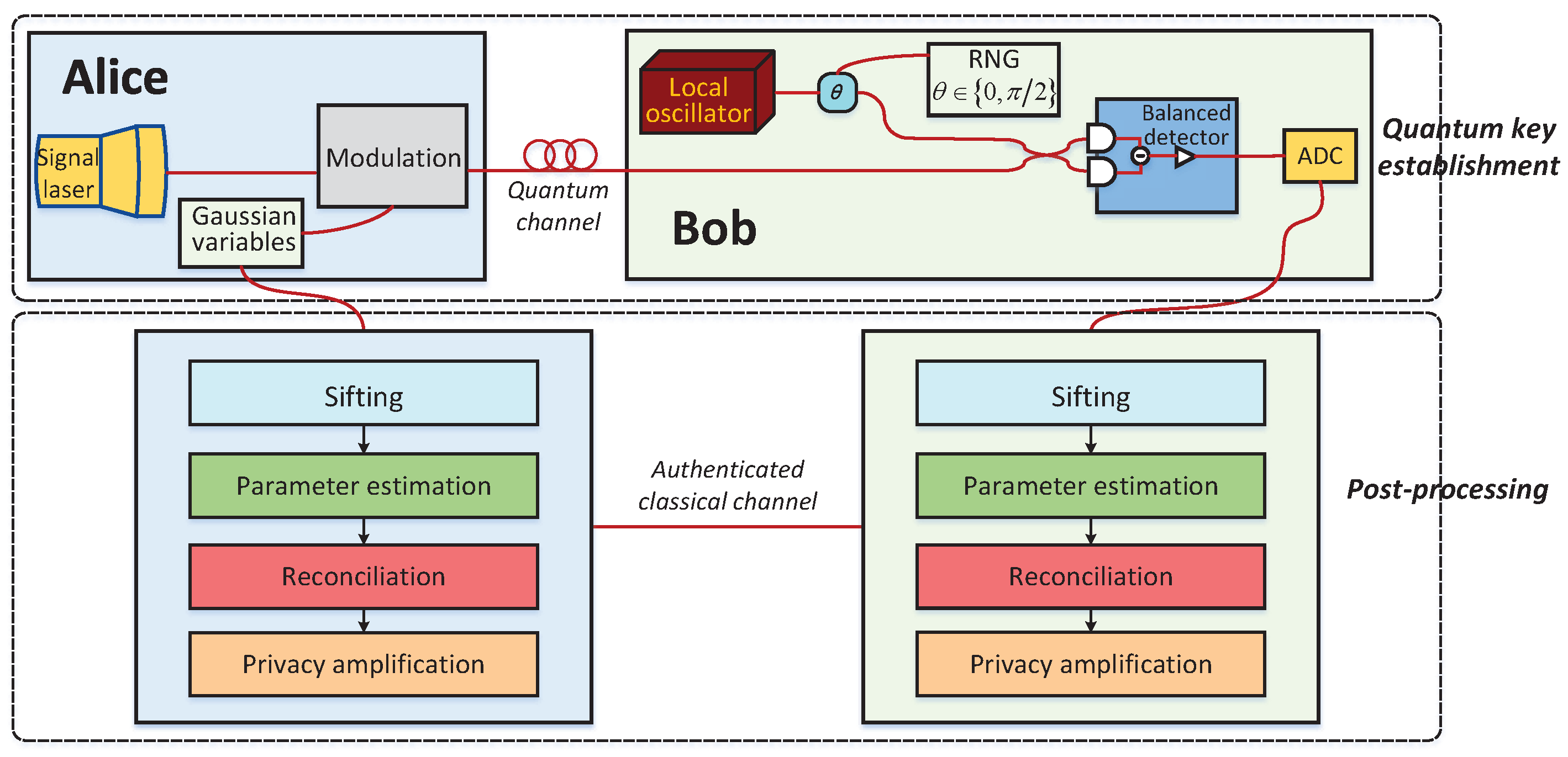
A CV-QKD system mainly includes two consecutive phases [
7,
8,
9]: the quantum key establishment phase and the classical post-processing phase, which are illustrated in
Figure 1. In the first phase, Alice prepares a coherent state using two Gaussian variables and sends it to Bob through the quantum channel. Then, Bob randomly chooses one of the two variables to measure his received coherent state and informs Alice of his choice. Owing to the physical noises or the existence of Eve [
17] in a quantum channel, the raw data of the legitimate parties obtained from the first phase are weakly correlated and weakly secure continuous variables.
To extract identical secret keys from their raw data, Alice and Bob subsequently perform a phase called post-processing, including four main stages: sifting, parameter estimation [
18,
19,
20], reconciliation [
21,
22,
23,
24,
25], and privacy amplification [
26,
27,
28]. Reconciliation is a crucial stage for CV-QKD, which allows the legitimate parties to distill the corrected keys from their raw data via an authentic classical channel. Its performance affects the secret key rate and the secure distance of the practical CV-QKD system [
29,
30,
31,
32].
Up to now, various reconciliation schemes have been proposed for reconciling the raw data of CV-QKD. Originally, C. Silberhorn et al. proposed sign reconciliation that first quantifies the raw data to bit string by using the sign and then corrects the error bits [
21]; however, its low reconciliation efficiency limits its application. Subsequently, V. Assche et al. proposed SEC, which chooses a set of quantization functions to convert a continuous variable into binary-value slices and then executes error correction on the quantized slices [
22,
23].
Soon after, many researchers apply code-modulated techniques, including multilevel coding (MLC) and multistage decoding (MSD) in SEC with Low Density Parity Check (LDPC) codes to improve the reconciliation performance at high SNRs [
33,
34]. The SEC scheme allows one to extract more than one bit of key from per pulse, especially at the high SNRs; however, its quantization performance is poor at the low SNR of long-distance CV-QKD, which limits its secure distance to about 30 km. Afterward multidimensional reconciliation was proposed by Anthony Leverrier et al. [
24], which extends the secure distance from 30 km to above 50 km. Since the code rate of multidimensional reconciliation is limited to 1 bit per pulse, its related research is mainly focused on improving the reconciliation efficiency with LDPC codes, and especially with Multi-edge type LDPC (MET-LDPC) codes at low SNRs [
35,
36,
37,
38,
39,
40,
41].
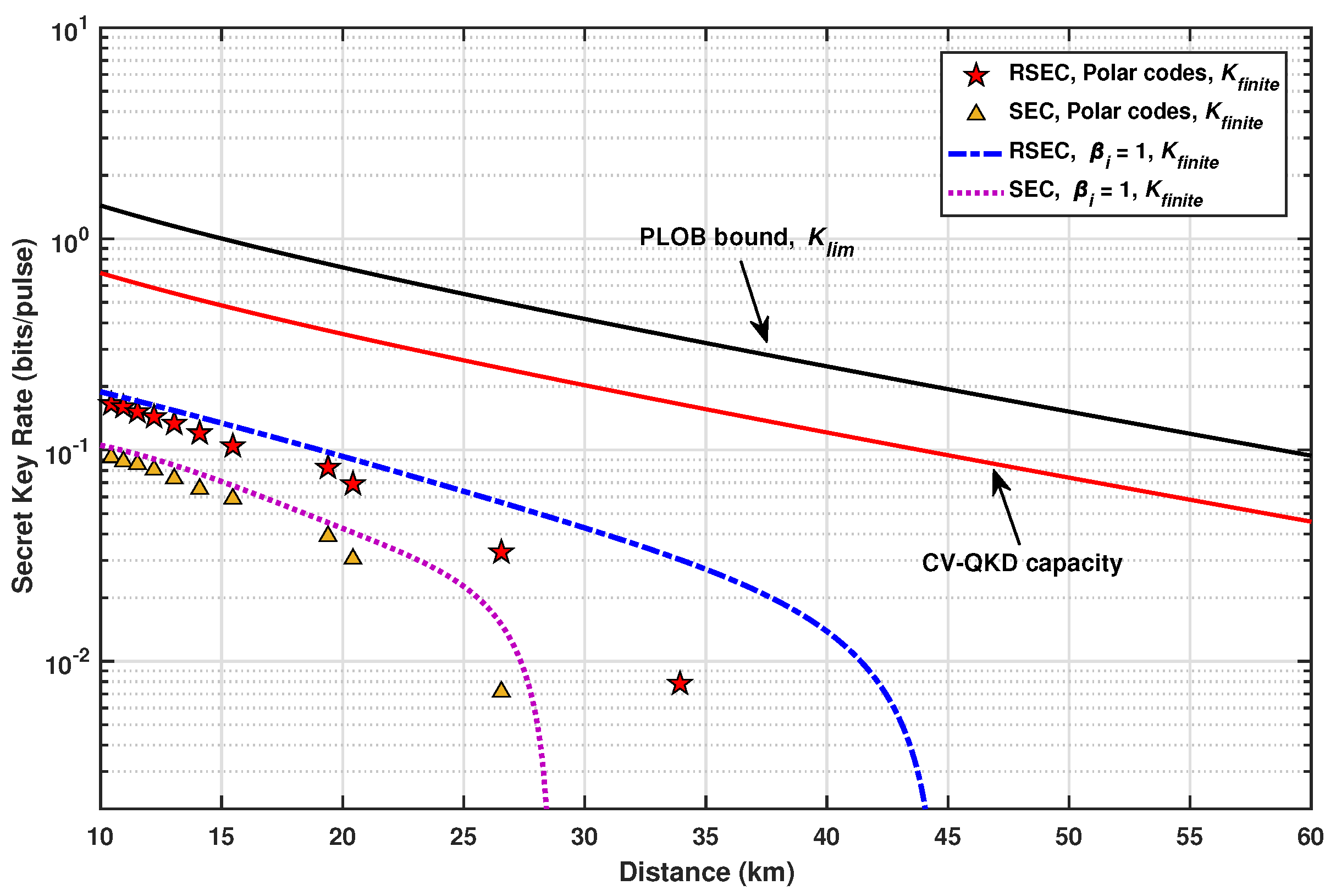
In summary, the existing research on reconciliation is mainly based on SEC and multidimensional reconciliation. These two schemes have their own advantages and disadvantages. Multidimensional reconciliation has a better quantization scenario than SEC reconciliation, and thus it can still achieve a high-efficiency reconciliation for a long-distance CV-QKD system with a noisy channel. However, its code rate is limited to 1 bit per pulse, which makes it more suitable for a long-distance CV-QKD system. Compared with multidimensional reconciliation, the SEC has advantages in extracting more than 1 bit of secret key per channel use.
Limited by its quantization performance, the SEC protocol is more suitable for the short-distance CV-QKD system. As is known, the secret key rate of a QKD system will decrease rapidly with the increase of distance [
29]. Due to the technology immaturity of the physical device, the key generation rate of the long-distance CV-QKD system is generally low [
32,
42], which obviously cannot satisfy the communication demand.
Therefore, to establish QKD networks [
43,
44,
45,
46] with the short-distance QKD system is a practical scheme to provide relatively high-speed keys for secure communication at present [
47]. In addition, the LDPC code is usually chosen to pursue a high reconciliation efficiency, but its matrix design is extremely difficult. By contrast, another common family of codes, polar codes, is relatively easier to construct and their recursive structure delivers excellent performance in practice.
In this research, our work focus on the improvement of the SEC protocol and the reconciliation of the data with polar codes. The main contributions of this paper are as follows: (i) We improve the SEC protocol by first performing a random orthogonal rotation on the raw data before slice quantization and then provide a novel estimator for the quantized slices. Compared with the SEC protocol, the improved protocol, named RSEC, has a higher quantization efficiency, which then increases the secret key rate and reconciliation efficiency. (ii) In order to accomplish the reconciliation of the correlated continuous variable in CV-QKD, we implement the RSEC protocol by combining the polar codes, achieving a high-efficiency reconciliation.
The rest of this paper is organized as follows: In
Section 2, the RSEC protocol is proposed to improve the SEC protocol. In
Section 3, the implementation of the RSEC protocol with polar codes is described. In
Section 4, the experimental results and analysis of RSEC are given. Finally, our conclusions are drawn in
Section 5.
2. Rotated Slice Error Correction (RSEC) Protocol
In this section, we briefly review the SEC reconciliation and then put forward RSEC to improve the current SEC. After the quantum key establishment phase of the Gaussian-modulated coherent state CV-QKD protocol, Alice and Bob share weakly correlated continuous-variable raw data due to the noises during the quantum transmission. The noises can safely be assumed to be Gaussian since they correspond to the case of the optimal attack for Eve [
12].
The correlated raw data are obtained by randomly measuring either the the amplitude and phase quadratures for each coherent state. Moreover, the information encoded on the two quadratures follow the same Gaussian distribution. For the convenience of description, let and correspond to the correlated Gaussian random variables of Alice and Bob, respectively. Then, the correlated raw data can be modeled as with , , where , and denote Alice’s modulation variance and the noise variance, respectively.
In the direct reconciliation scenario, Alice’s sequence is used as the target to correct Bob’s sequence. On the contrary, the reverse reconciliation scenario uses Bob’s sequence as the target to correct Alice’s sequence. Generally, the latter scenario can obtain a higher secret key rate [
35,
38]. Without loss of generality, we only consider the reverse reconciliation in this research.
2.1. Review of Slice Error Correction
In information reconciliation, Alice and Bob first perform an operation called quantization to convert the correlated values into binary sequences and then choose an error correction scheme to correct the binary sequence over an authenticated classical channel. SEC is a generic reconciliation protocol [
22]. Its underlying idea is to convert Alice’s and Bob’s values into bit strings with the slice function (i.e., quantization function) and then apply an error correction scheme as a primitive, taking advantage of all available information to minimize the number of exchanged reconciliation messages.
This works in two steps: First, Bob chooses a quantization function to map his raw data to m-slices binary digits, and informs Alice of the first t slices (usually t = 2 or 3), is a vector of slices ; then, Bob sequentially deals with the remaining slice k by sending a syndrome of to Alice so that Alice can recover with a high probability.
The quantization function is to divide the set of real numbers
into
intervals and then to assign different binary values to each of these intervals. There are two different schemes to construct the quantization function. The first construction scheme is to divide
with
equidistant points. The second construction scheme freely chooses
points to divide
, which performs better but has a much higher computational complexity. The previous work indicated that the second scheme does not improve as much as the quantization efficiency compared with the first scheme [
33]. Therefore, we use the first scheme to construct the quantization function in this research.
In addition, previous studies have shown that the best bit assignment method is to assign the least significant bit of the binary representation of
to the first slice
when
[
22]. The variables
divide the real numbers
into
intervals, where
,
,
. Then, each bit of
is subsequently assigned to the remaining slices. More specifically,
where
and
n is a nonnegative integer.
2.2. Improvement of Slice Error Correction
In the decoding process of SEC, the slice sequences are corrected in sequence; hence, the estimation of the current slice recursively depends on all previous slices. For this reason, the performance of SEC can be improved by reducing the bit error rate (BER) of the previously decoded slices, denotes the probability that Alice makes a wrong estimate of Bob’s slice value . According to the characteristics of quantization function , it is not hard to find that the last slice corresponds exactly to the sign of input variable x. Therefore, the quantization scheme of the last slice is similar to the multidimensional reconciliation, which uses the sign of the rotated data as the target sequence.
As is known, multidimensional reconciliation typically performs better than the SEC reconciliation in estimating the quantized values, especially at a low SNR [
24]. For each slice, although having obtained the first few slices, Alice still needs to infer Bob’s slice value in a certain number of intervals. Taking the case of
slices as an example, if Alice has the first two slices
, she needs to estimate Bob’s slice
among four intervals, i.e.,
,
,
,
to satisfy
. However, multidimensional reconciliation calculates the probabilities of Bob’s quantized value with the joint density function directly, which leads to more accurate estimations.
Consequently, to reduce the BER of the slice, we could execute a random orthogonal rotation on the raw data before the slice quantization and then infer the last slice
according to multidimensional reconciliation. After decoding the
m-th slice, Alice corrects the remaining slices in order. Assuming that Alice and Bob agree on the quantization function
and the dimension
d of the orthogonal matrix, the procedure of our improved protocol for reverse reconciliation is shown in
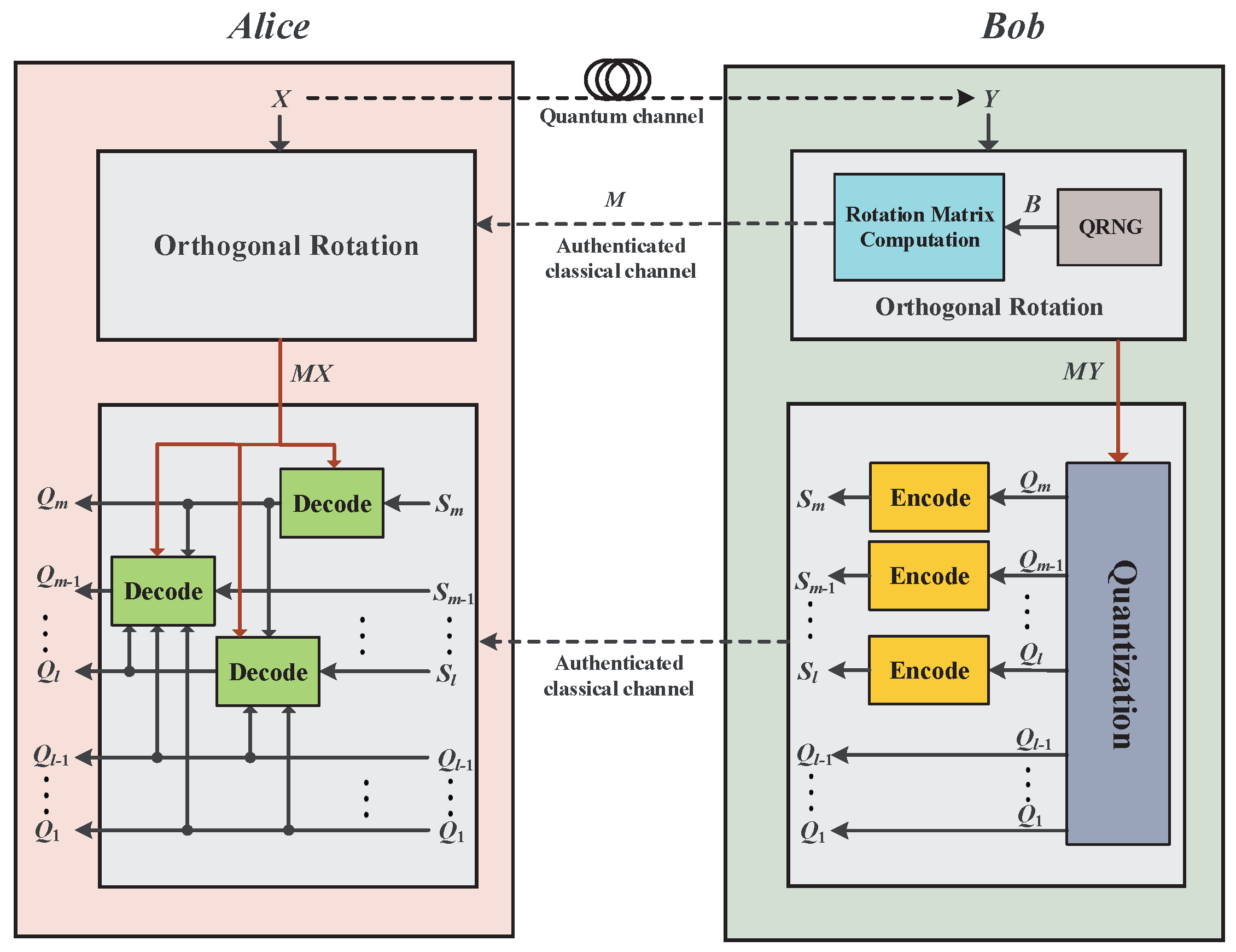
Figure 2. The detailed process is described as follows:
Step 1: Alice and Bob divide their raw data into d-dimensional vectors as , . Bob randomly generates a bit string and chooses a point on the unit sphere adjacent to the point . Then, he calculates an orthogonal matrix M satisfying for rotating Y to , and informs Alice of the matrix M, where , .
Step 2: After receiving Bob’s orthogonal matrix M, Alice performs the same rotation on X and has the rotated data .
Step 3: Bob quantizes his rotated data
into
m-slice bit vectors with the quantization function
, such as Equation (
1), and sends the quantized slice values of the
slices
to Alice, where
.
Step 4: Alice constructs a bit string
of the
m-th slice
from her rotated data
using the slice estimator
as Equation (
11) in
Section 2.3. Subsequently, Bob uses a chosen error correction codes to generate a syndrome
so that Alice aligns her bit string
on the sequence
.
Step 5: For each subsequent slice k, , Alice constructs a new string by applying the slice estimator to , and taking into account the disclosed slices and the previously corrected bit strings . Again, Alice aligns her bit string to Bob’s sequence using their chosen error correction codes and corresponding syndrome .
2.3. Slice Estimator of RSEC
In the decoding stage of the RSEC reconciliation, we need to use the side information to estimate Bob’s quantized slices first. Let us now detail the expressions we proposed. According to the decoding process, we first estimate the last slice
m of Bob. As is known,
where
is the rotation matrix, and
follows the Gaussian distribution,
.
As Gaussian variables have linear translation invariance—i.e., the linear combination of the independent Gaussian variables is still a Gaussian random variable—then
follows the following Gaussian distribution
It is known that
since
M is an orthogonal matrix. Therefore, the random variable
has the same probability distribution as
Z, i.e.,
where
. Similarly, Bob’s rotated data
follows the distribution
, and
follows the distribution
. In addition, according to the characteristics of the quantization function
, the bit string
corresponds to the sign of the rotated data
, i.e., if
,
, else,
. Here, we use
to denote the
k-th slice of
. Hence, we obtain the conditional probability of
as follows
where
,
K is the normalization factor
. By integrating the conditional probability into a parameter, we find the soft information called the log likelihood ratio (LLR), which is a very useful parameter for estimation, as follows
Given the transformation characteristics of the orthogonal rotation process, it is not difficult to deduce
. If estimating
with Equation (
6), Alice needs Bob to send his norm information
, which will lead to heavy communication traffic and storage resource requirements. Fortunately, we proposed a method that calculates the LLR without using the norm information of an encoder in our previous work [
40]. Therefore, our protocol uses this improved method to calculate the LLR of
as follows
where
is the SNR of the quantum channel, and
.
For the remaining slices
k , we derive their LLR with the corrected slices and the received
slices as prior information. According to the previous analysis, we find the joint density function of the rotated data
and
as Equation (
8). Hence, the random variables
and
follow the joint density function,
According to Equation (
8) and the characteristics of the quantization function Equation (
1), we derive that the conditional probability of
is expressed as
where
represents those quantization intervals satisfying
,
, i.e.,
,
0 or 1,
denotes the disclosed and corrected slices.
Accordingly, we find the initial LLR of
as Equation (
10) to preliminarily estimate the rotated results of the
k-th slice,
where
represents the quantization intervals that satisfy
, and
satisfies
, respectively.
Based on the derived LLRs of each slice, the estimator
of our RSEC reconciliation is constructed as follows
Then, Alice can use Equation (
11) to construct an initial estimation
for Bob’s slice value
.
2.4. Error Probability of Slice Estimator
In order to evaluate the accuracy of the proposed slice estimator, we theoretically analyze and compare the error probability of the SEC protocol and the RSEC protocol. The error probability of the slice estimator denotes the theoretical probability that Alice’s slice estimator yields a result different from Bob’s slice. For the SEC protocol, the error probability in slice
i can be expressed as
where
and
, the superscript
w characterize the variables of the SEC protocol. As the random variables
X and
Y follow the Gaussian distribution symmetrical about the coordinate axis, it is easy to obtain that
, and then
can be further written as
each of these terms can be expanded as
where
denotes the set in which
has a higher probability than
, and
,
.
In the RSEC protocol, the quantized values in slice
m are estimated and decoded first. According to the characteristics of the quantization function
, Bob’s last slice
when
and
otherwise. On the other side, Alice constructs an estimation of Bob’s quantized value
with Equations (
7) and (
11). The result in the last slice yielded by our estimator
corresponds to the sign of
x:
when
and
otherwise. Therefore, the error probability of the RSEC protocol in the last slice
m can be expressed as
the superscript
p characterize the variables of the RSEC protocol. By applying the probability distribution of
and
as analyzed in the previous section, we have
, and the
can be further calculated as follows
where
is given in Equation (
8), and the second equation in Equation (
15) is transformed by using the symmetry of the probability distribution of
and
.
Similar to the SEC protocol, the quantized values of the RSEC protocol in other slice
k are estimated by using the disclosed slices and the successfully decoded slices. Thus, the error probability of these slices can be calculated according to Equation (
13), where the last slice
is taken as additional information.
The error probabilities of the subsequent slices—which recursively depend on that of all the previous slices—are not simple to calculate [
22]. Here, we compare the estimation accuracy of RSEC protocol with the SEC protocol only by the error probability in the first decoded slice (i.e., the
l-th slice in SEC, the
m-th slice in RSEC). Using the Equations (
13) and (
15), we find the error probability in slice
of the SEC protocol and the error probability in slice
of RSEC protocol as shown in
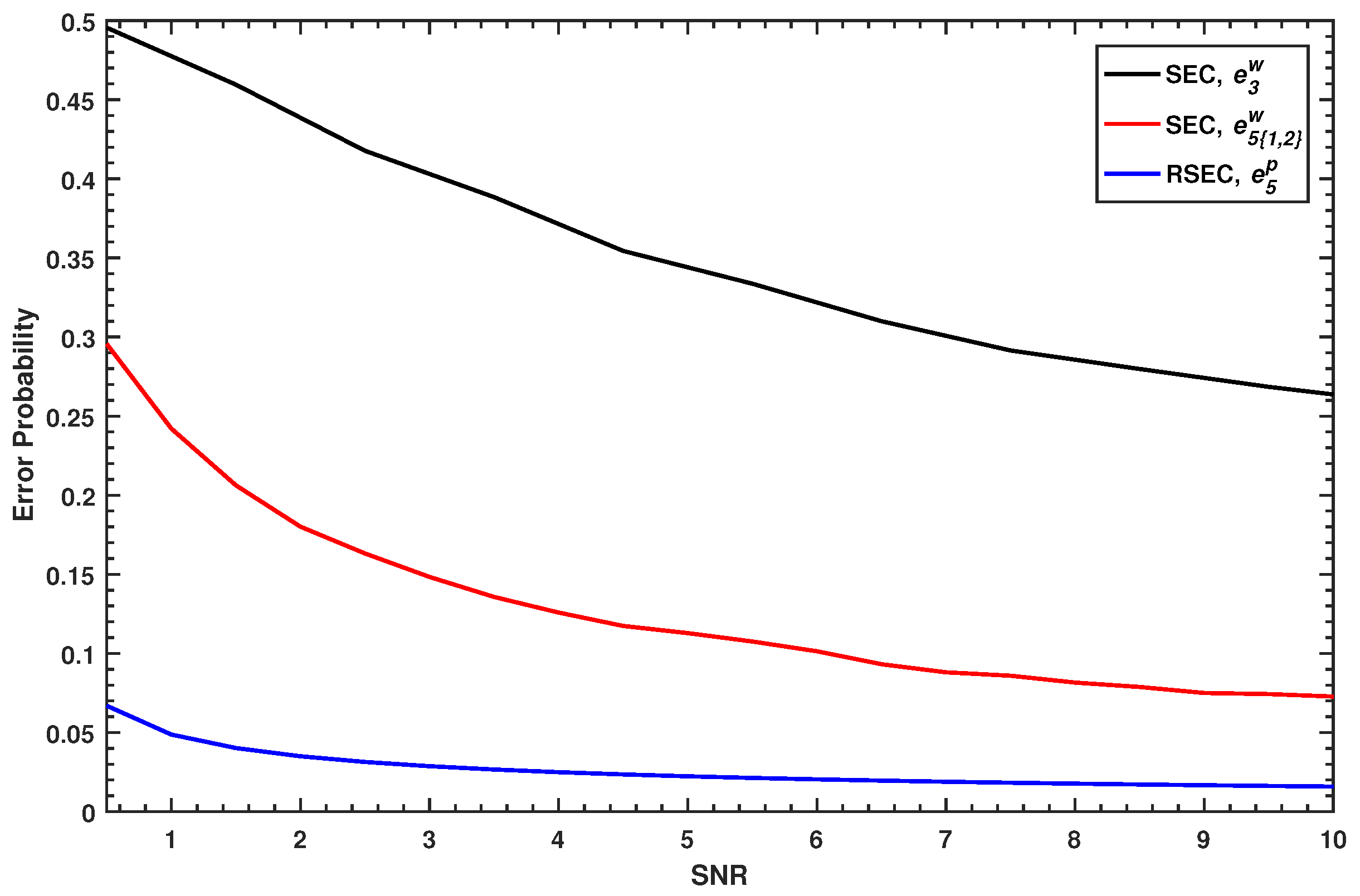
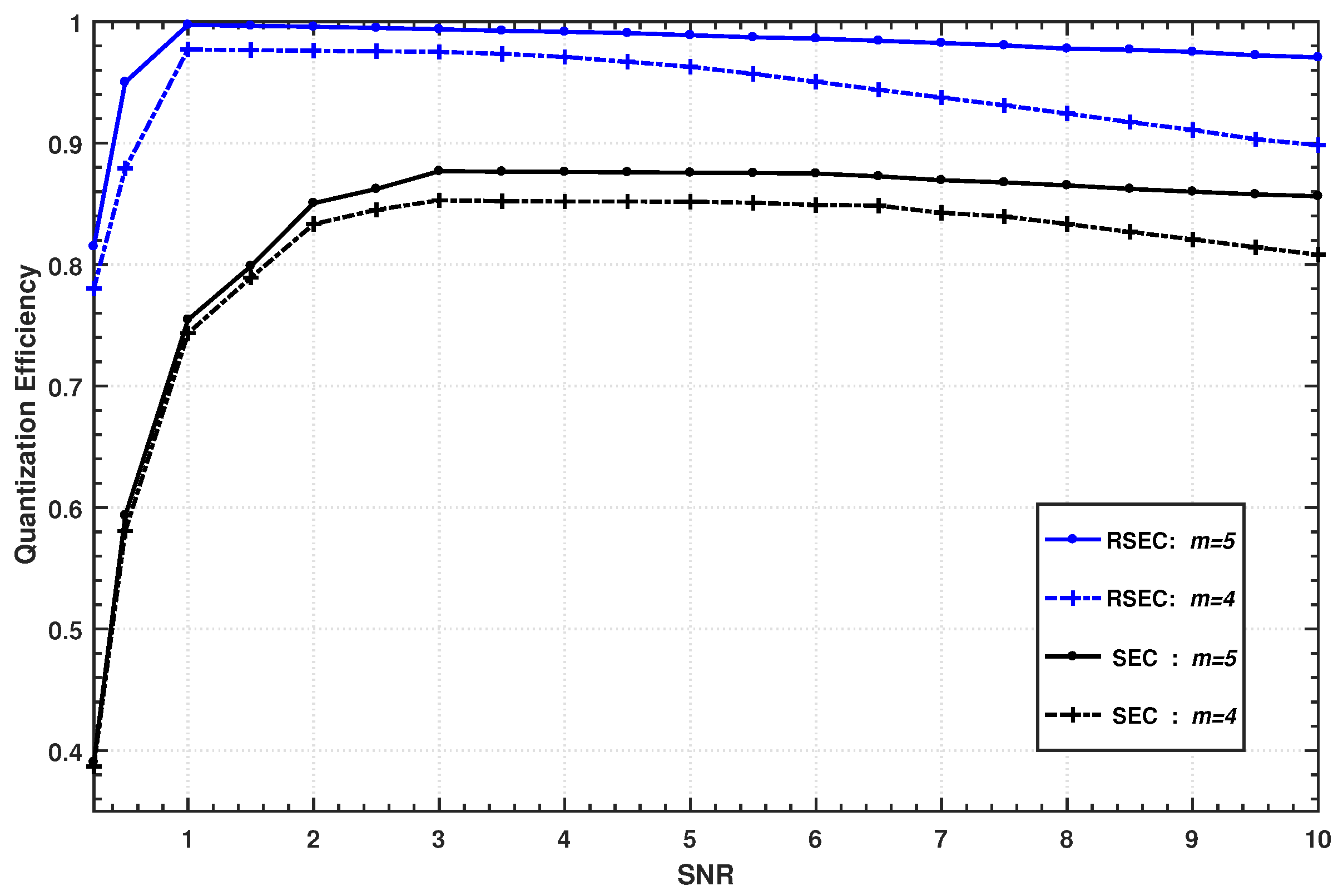
Figure 3, where the first two slices are disclosed and the quantization adopts the five-slices function.
corresponding to the blue curve is always smaller than
corresponding to the black curve, i.e., the estimator of RSEC in the first decoded slice always has a lower error probability than that of SEC. If the
m-th slice in the SEC protocol is estimated first, its error probability
corresponding to the red curve, of which the expression can be given by Equation (
16), also always performs worse than that of the RSEC protocol.
From the above analysis, it is indicated that the proposed estimator of RSEC protocol has much higher estimation accuracy in the quantization phase than the original estimator of the SEC protocol. Note that the error probability represents the theoretical case of the bit error rate, and the bit error rate of each slice needs to be estimated separately in the practical reconciliation.
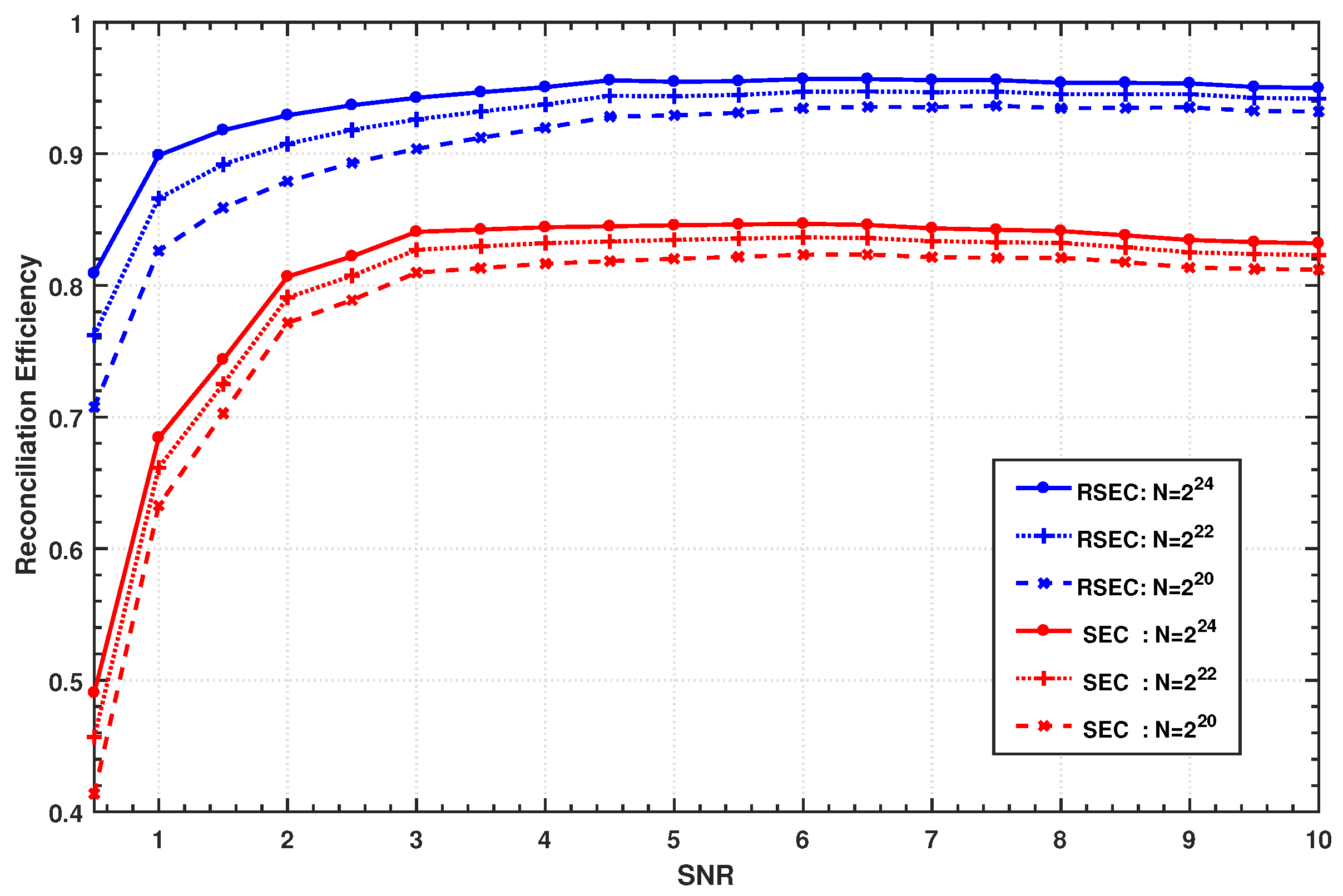
2.5. Reconciliation Efficiency
Let us now discuss the reconciliation efficiency of the proposed protocol, which is an important indicator for evaluating the performance of the reconciliation procedure. As is known, the random orthogonal rotation operation on raw data does not expose any information of the rotated results [
24]. According to the definition of efficiency in the slice reconciliation [
33], the reconciliation efficiency
of the RSEC protocol can be expressed as
where
is the classical capacity of the quantum channel for Gaussian variables,
m denotes the number of slices of quantization function, and
represents the code rate of the error correction scheme of the
i-th slice.
is the entropy of the slice sequences
, which can be calculated as follows
with
where
denotes the point dividing the real numbers
,
, and
,
.
and
represent Alice’s modulation variance and the noise variance, respectively.
Generally, the code rate of the first slices are equal to 0 since they are disclosed via the authentic classical channel.
3. Implementation of RSEC with Polar Codes
After quantizing the continuous variables into strings of bits with slice functions, the legitimate parties are needed to further apply a classical error correction code to complete the reconciliation of the correlated raw data. In this section, we will implement the RSEC protocol with polar codes to distill the correct keys from the correlating raw data.
3.1. Review of Polar Codes
The polar code is an error correction code that has been strictly proven to achieve the Shannon capacity [
48]. The recursive structure of its encoding and decoding gives them good practical performance. This is relatively easier to construct than another commonly used code, i.e., LDPC code. Therefore, we chose polar codes to implement the RSEC protocol in this research. The RSEC can also be implemented with other error correction codes. Now, we briefly review the encoding and decoding of polar codes in traditional communication.
3.1.1. Encoding
The central idea of polar codes is to convert the
N individual copies of the channel
W into two different types of channels, i.e., error-free channel and completely noisy channel, through an operation called channel polarization—channel combining and channel splitting. The information sender chooses the positions corresponding to the error-free channel to place her message bits (called information bits), and usually sets the remaining positions corresponding to the completely noisy channel as 0 (called frozen bits). The information bits and frozen bits together form a sequence
of
N bits. We use the notation
to denote a row vector of
n bits. The sender encodes the sequence
to a codeword
by
where
G is the generator matrix and defined as
,
means to perform the Kronecker product
n times on the matrix
, and
B is a permutation matrix for executing the bit-reversal operation [
48]. Obtaining the codeword
, the sender transmits it to the information receiver for decoding.
3.1.2. Decoding
After the codeword
is transmitted through the channel, the receiver obtains a sequence
, which is a noise version of
. Then, he uses successive cancellation (SC) or successive cancellation list (SCL) decoding algorithms to correct the error bits among
with the given frozen bits. We here describe the receiver’s decoding process with a SC decoding algorithm [
48]:
Initialize the received information
with channel transition probability
as
Calculate the likelihood ratio (LR) of
with the decoding results
of the previous
bits as follows
where
and
Generate the decision
of
as
where
is the position set of the frozen bits.
After getting the j-th bit by step (iii), the process returns to step (ii) to decode the -th bit.
3.2. Implementation Process
The reconciliation mode of CV-QKD is different from traditional communication. In traditional communication, the codeword is mixed with noises during the reconciliation. However, in a CV-QKD system, the two parties have already shared inconsistent data before the post-processing phase, in other words, the noise in the codeword appeared before the reconciliation. Therefore, in order to correct the slice sequences of RSEC, it is necessary to establish a virtual channel for Alice and Bob to deal with the noise.
The encoding of polar codes is reversible: Encoding an input sequence x twice, one can recover this sequence, i.e., . This property can be used to establish a virtual channel as: Bob encodes a slice sequence x to another sequence , and then sends the bits corresponding to the frozen indices to Alice. Since , the slice sequence x can be regarded as a polar codeword, Alice’s initial estimation of Bob’s slice value can be viewed as the received codeword, and corresponds to the frozen bits shared by the two parties. Therefore, a virtual channel can be established by using the above method.
Before launching the reconciliation with polar codes, Alice and Bob determine the code rate
of each slice according to the SNR and share the corresponding frozen index set
. The frozen index set can be selected by a construction algorithm with consideration to
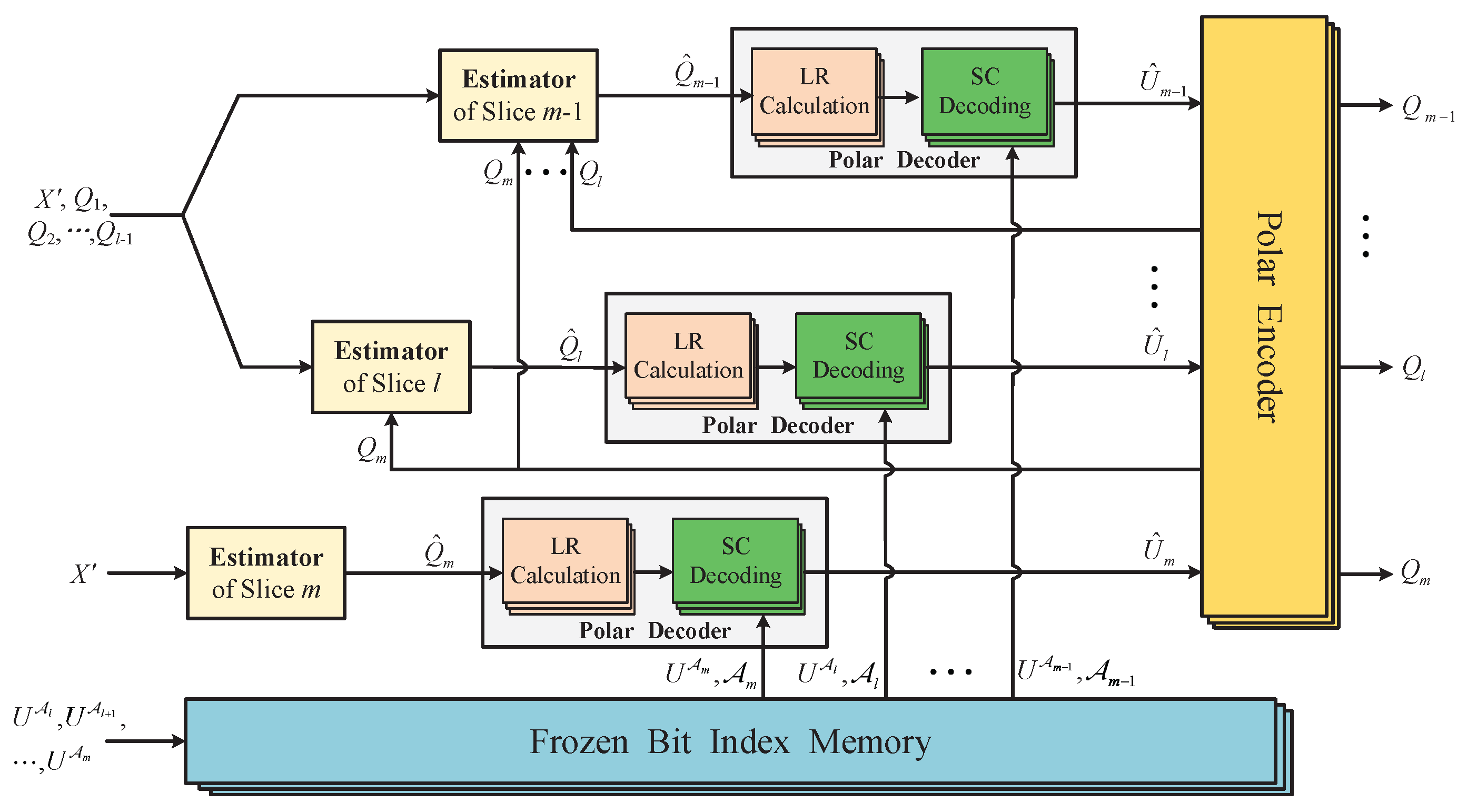
. Then, the logic structure of the RSEC reconciliation with polar codes is shown in
Figure 4, in which the detailed implementation process is described as follows:
Step 1: Alice and Bob convert their correlated data X, Y to another continuous-variable sequence noted as , with random orthogonal rotation according to RSEC. Bob then quantizes into m slice sequences with the slice function and sends the first slices to Alice. Afterward, they begin to reconcile the remaining slice sequences with polar codes in the order of slice.
Step 2: Alice uses the proposed estimator in Equation (
11) to construct a bit string
corresponding to Bob’s slice sequence
. Meanwhile, Bob encodes his slice sequence to
, and sends the bits
at the frozen positions to Alice.
Step 3: Alice calculates the initial LR
as Equation (
26),
, and then makes a decision
on
U after getting the final LR
in Equation (
27). Afterward, she can recover Bob’s sequence
with a high probability by executing an encoding operation on
.
where
is the initial LR corresponding to the
j-th bit of
U,
is the
j-th bit of
,
,
, the channel transition probability can be calculated as: if
,
, if
,
. The bit error rate
can be estimated in the stage of parameter estimation by executing the quantization operation on the extra raw data.
Moreover, Equation (
27) can evolve in a recursive manner as
if
j is odd, i.e.,
, then
if
j is even, i.e.,
, then
where
,
, we use
to denote the odd terms of
, and
denotes the even terms of
.
Alice can also use LLR as the soft information of polar codes for decoding. In this case, the initial LLR is calculated according to Equations (
7) and (
10).
In order to ensure that the equation holds with a high probability, Alice and Bob need to perform a cyclic redundancy check (CRC) to verify the decoding result . If fails to pass CRC check, Alice and Bob give up on this slice . Even if the decoding result passes the CRC check, undetected error bits may still exist. However, this situation rarely occurs and can be overlooked.
As the CRC values will leak the information about
, it is necessary to discard them. Therefore, the code rate
of each slice is calculated as follows
where
is the length of the CRC values.