1. Introduction
In modern wireless communication systems, physical layer security (PLS) is regarded as a critical aspect in providing confidential message transmission according to the characteristics of wireless channels. Differing from traditional encryption techniques, PLS can be proved and quantified without the risk of brute-force cracking. Shannon first proposed the notion of information-theoretic secrecy in his groundbreaking work [
1]. The more practical framework, named ‘the wiretap channel’, was established by Wyner in terms of a binary symmetric channel (BSC) [
2]. Another important contribution of Wyner was the designing of a secrecy coding scheme, in which the secrecy redundancy rate worked to confuse an eavesdropper. As extended versions, the wiretap channel has been considered in broadcast channels by Csiszar [
3] and in Gaussian channels by Leung-Yan-Cheong [
4].
On the basis of the above work, PLS has contributed to considerable progress, especially in performance optimization and signal processing. Secrecy capacity, which evaluates the effectiveness of secure transmission, has been defined as the maximum rate in each reliable and secure transmission [
5]. This metric has been adopted in the security analysis and optimization of 5G mmWave small cell networks [
6], co-operative non-orthogonal multiple access with proactive jamming [
7], artificial noise (AN)-aided multi-input multi-output (MIMO) Rician channels [
8] and so on. As the secrecy capacity may be less than target secrecy redundancy rate, the secrecy outage probability (SOP) has been applied to present a more comprehensive performance evaluation. For instance, [
9] discussed a security region with AN based on SOP, and [
10] minimized SOP in a D2D-enabled cellular network by access control. When a certain SOP constraint is required, secrecy throughput has widely been considered, especially in optimization problems where the transmission rate or power is adjusted for improved security [
11,
12]. On the other hand, signal processing-related methods have also been proposed, mainly including beamforming and precoding, AN, co-operative and relay and diversity technologies [
13,
14,
15,
16].
Recently, many excellent contributions have focused on the PLS of hybrid automatic repeat request (HARQ) methods capable of typical time diversity features. In HARQ with chase combining (HARQ-CC), the transmitter retransmits erroneous codewords (or their redundant versions) if the legitimate receiver fails to decode them. On the contrary, new transmissions are triggered when either the decoding is successful or the maximum transmission number is reached [
17]. Due to the increased comprehensive requirements, Makki et al. [
18] proposed a low-latency reliable HARQ protocol using finite blocklength codes. When a passive eavesdropper exists, it has been proven that retransmissions and combinations are capable of enhancing security, due to the diversity gain of the legitimate receiver [
19]. In order to efficiently design secure HARQ, Tang et al. [
20] discussed SOP, secrecy throughput and their asymptotic properties; Tomasin [
21] proposed a multiple-encoding HARQ scheme with statistics channel state information (CSI); Mheich et al. and Treust et al. [
22,
23] optimized secrecy throughput using multi-level feedback and rate adaption. However, most of them did not consider the influence of secrecy outage on secrecy throughput, which generally led to overestimated performance [
24]. Hence, in our previous work, we extended the effective secrecy throughput (EST) of a single transmission [
25] into a HARQ-CC system with a passive eavesdropper, and optimized secrecy redundancy rate for improved security [
26]. Nevertheless, another common scenario, which includes multiple eavesdroppers, rate adaption and limited latency, has not yet been analyzed.
Inspired by this problem, in this paper, we completed the optimization of both the code rate and secrecy redundancy rate to maximize EST in a general scenario with multiple eavesdroppers. At the same time, different latency requirements were also considered. The major contributions of our work include:
The closed-form expressions of COP, average transmission number and SOP in the HARQ-CC system with multiple eavesdroppers and different latencies are given. The corresponding approximations were also deduced, while EST was defined considering both reliable outage and secrecy outage.
With a given secrecy redundancy rate, the optimization problem of code rate to maximize the EST was discussed. This problem was solved with a parameterized closed-form solution, with and without the COP constraint.
When the code rate is given, the optimization problem of secrecy redundancy rate with EST criteria was also analyzed. We solved this problem by applying a fixed-point method, with and without the SOP constraint.
The joint optimization problem of the rate pair (i.e., code rate and secrecy redundancy rate), in order to maximize the EST, was discussed. To solve this problem, an iterative optimization algorithm was designed which involves the two methods mentioned above. COP and SOP constraints were also considered.
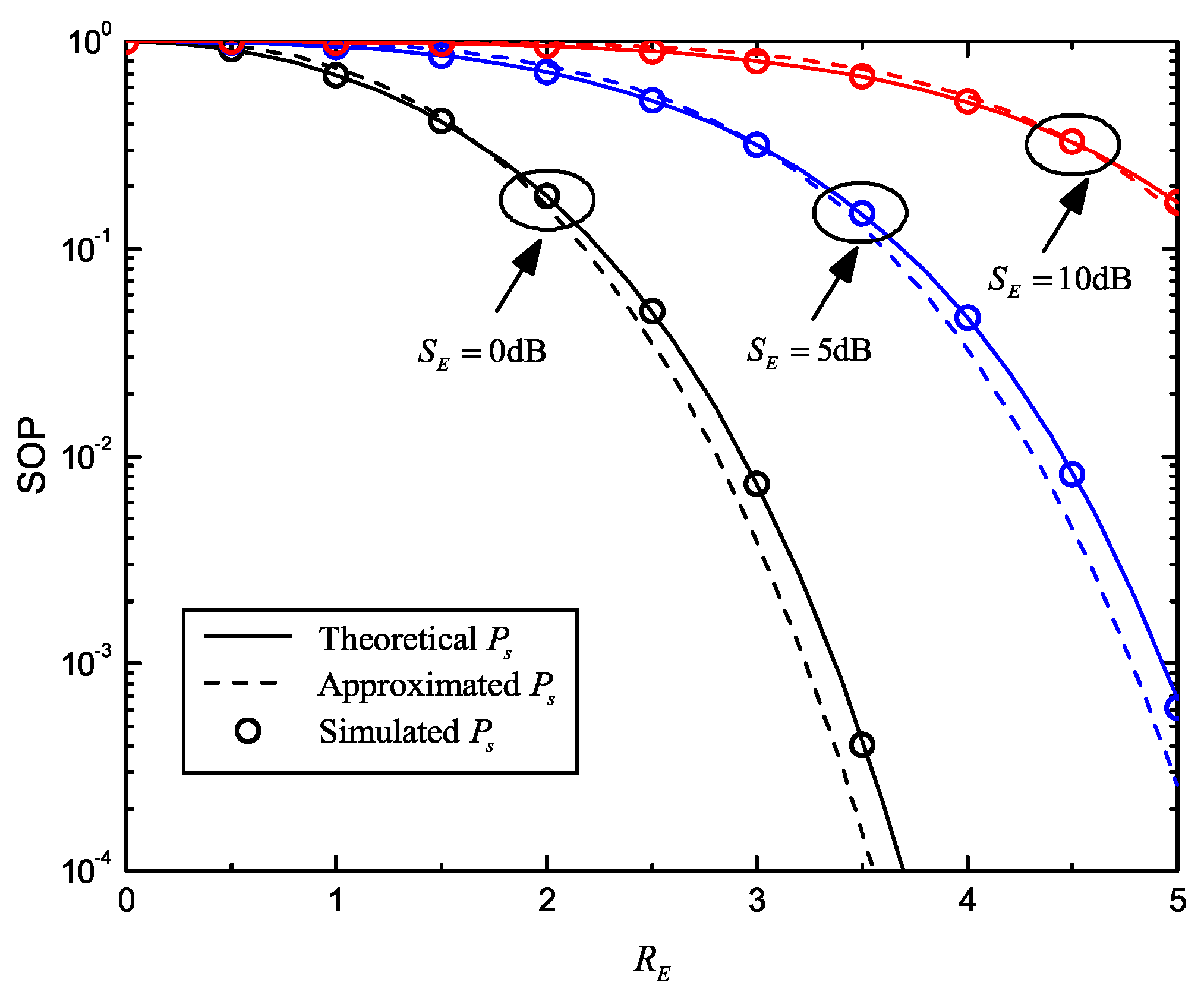
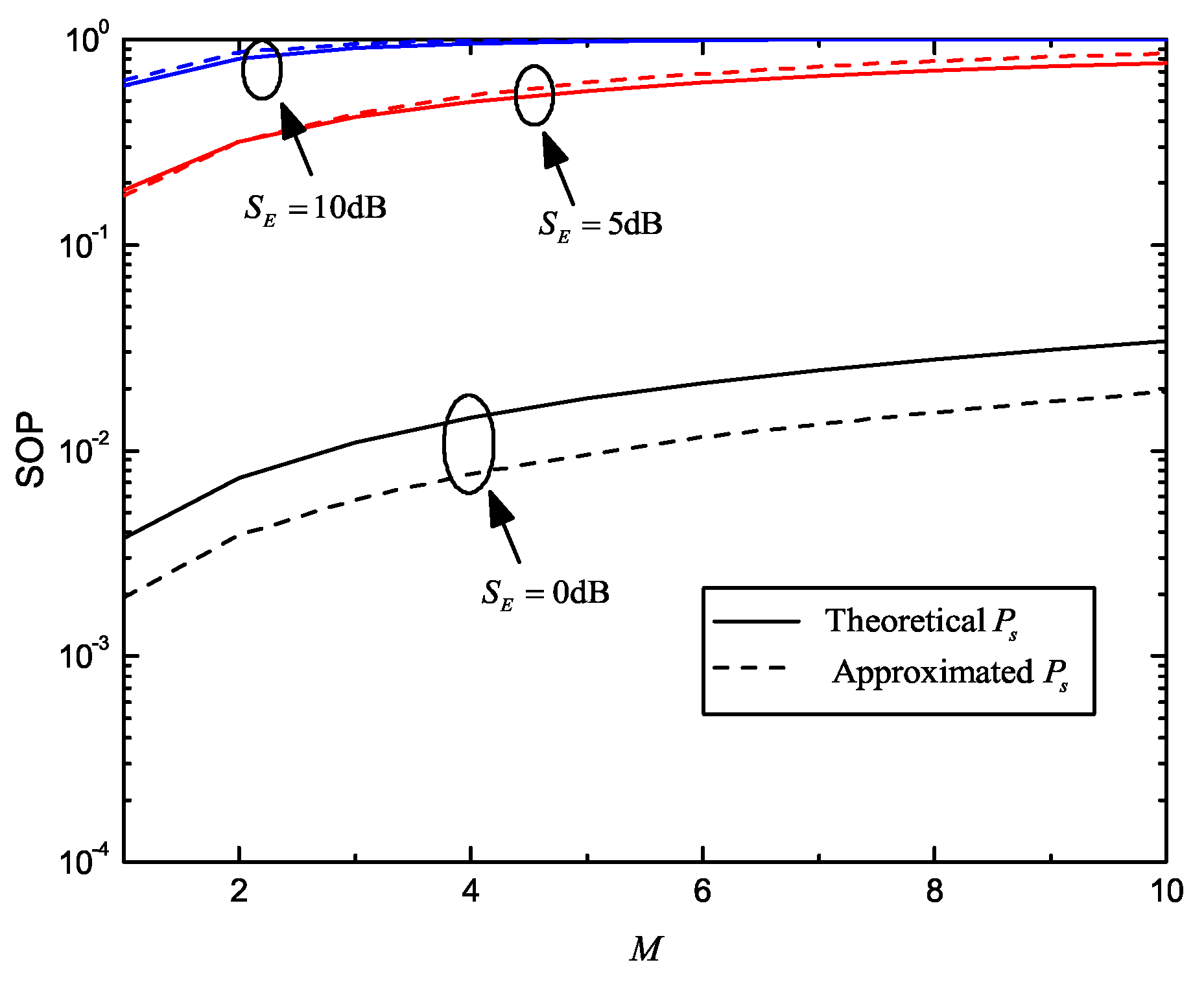
Numerical and simulated results confirm our expressions of critical secure performance metrics, as well as the proposed optimization methods, under different cases. We also found that secrecy performance inevitably deteriorates with an increasing number of eavesdroppers, due to more information leakage.
The rest of this paper is organized as follows: The overall system model and assumptions are described in
Section 2.
Section 3 expresses COP, average transmission number, SOP and its approximation, along with the definition of EST in a HARQ-CC system with multiple eavesdroppers.
Section 4 proposes the optimization of code rate, secrecy redundancy rate and both of them, in order to maximize EST under different constraints and the numerical and simulated results are presented in
Section 5.
Section 6 concludes our work.
Notation:
denotes the expectation operator. The function
is the upper incomplete gamma function,
is the gamma function,
and
are the regularized upper and lower incomplete gamma functions, respectively.
denotes a Gaussian distribution with mean
a and variance
b, respectively.
and
denote the probability density function (PDF) and the cumulative distribution function (CDF) of a random variate
X, respectively. The function
is the principal branch (
) of Lambert’s
W-function, defined through the implicit equation
[
27].
2. System Model of Secure HARQ-CC With Multi-Eavesdroppers
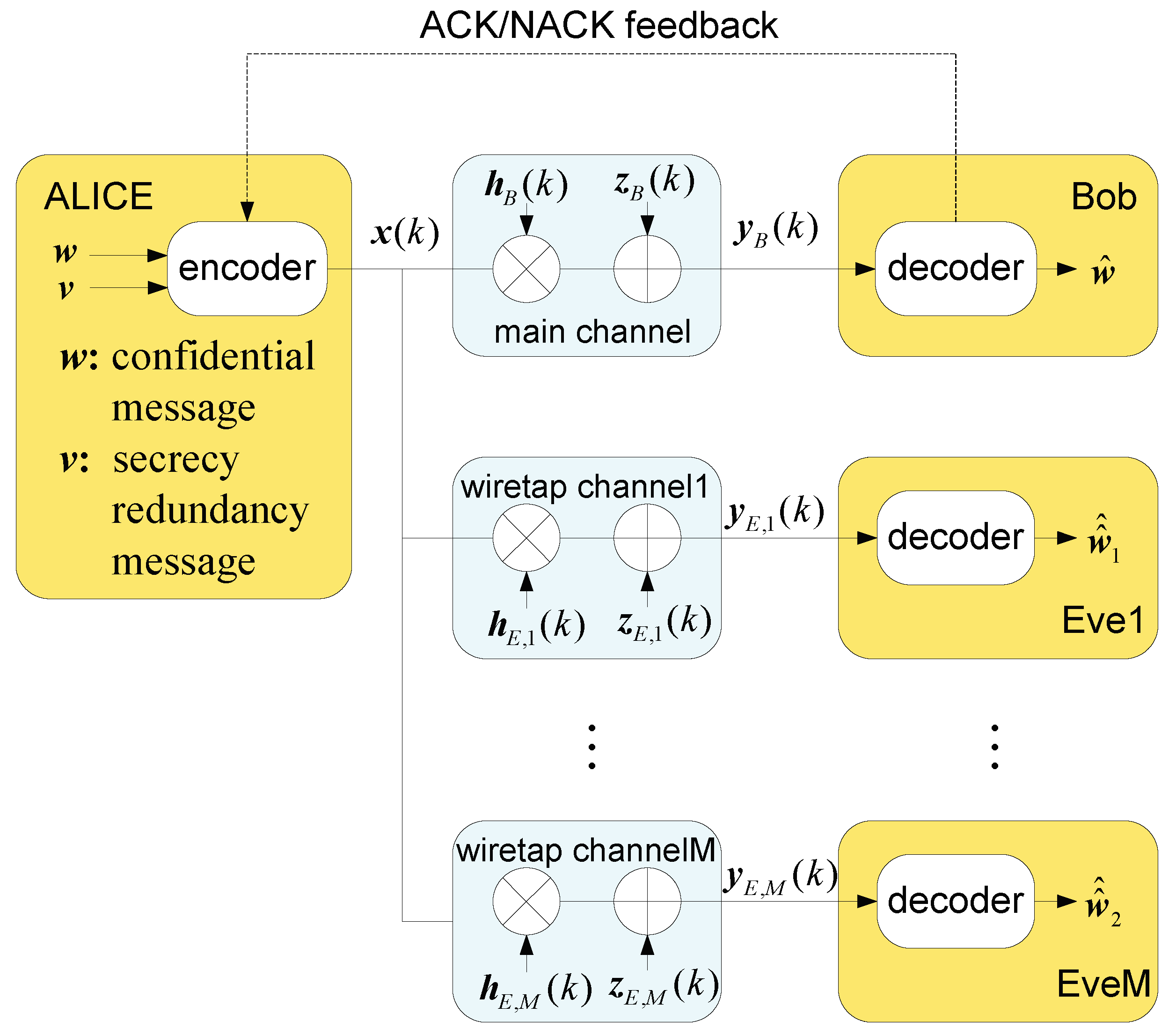
We considered a secure HARQ-CC transmission system with multiple eavesdroppers, as shown in
Figure 1. The transmitter (Alice) sends a confidential message
with a secrecy redundancy message
to the legitimate receiver (Bob) over the main channel, while several passive eavesdroppers (Eve1, …, EveM) intercept the transmission through
M wiretap channels. We assumed that the main and wiretap channels are independent Rayleigh block-fading channels. Retransmissions are triggered only by Bob, depending on his decoding failure. To avoid unexpected retransmissions, the maximum transmission number (
K) guarantees limited latency. A major security advantage of this protocol is that the erroneous codewords received by eavesdroppers may not be retransmitted by Alice, unless Bob had the same erroneous ones. Hence, there was much more diversity gain obtained by Bob than Eve1, …, EveM.
Alice encodes the confidential message
and the secrecy redundancy message
into the codeword
using the Wyner secrecy code [
2], where
k is the transmission number (1 ≤
k ≤
K). The code rate and secrecy redundancy rate are denoted by
and
, respectively. Thus, the secrecy rate is given by
. Assume that the transmission power is fixed at
P, and
. We denote the fading parameters of the main and wiretap channels by
and
, respectively, which are independently and identically distributed (i.i.d.) complex Gaussian random variables with zero mean and unit variance. We denote the additive Gaussian white noise by
and
, respectively. Their means are zero and their variances are, respectively,
and
. In each slot, the received signals of Bob and Eve1, …, EveM after
k transmissions are
For simplicity, we define
and
as the average received signal-to-noise ratio (SNR) through the main channel and the wiretap channels, respectively. After
k transmissions, Bob and Eve1, …, EveM uses the maximal ratio combining (MRC) before decoding. Their combined SNR becomes:
3. Security Performance Metrics
Based on the above secure HARQ-CC system model with multiple eavesdroppers, we analyzed some critical security performance metrics, including connection outage probability (COP), average transmission number, secrecy outage probability (SOP) and effective secrecy throughput (EST). Connection outage occurs when the legitimate receiver (Bob) cannot decode the transmitted codewords, and secrecy outage occurs when one or several of the eavesdroppers (Eve1, …, EveM) cannot be confused by secrecy redundancy after the transmission.
We first considered the COP after
k transmissions, denoted by
. The COP is defined as the probability that a connection outage occurs; that is, the mutual information after the
transmission,
, is less than the codeword rate
,
We know that the fading parameters are independent zero-mean unit-variance complex Gaussian random variables. Hence, the sum of their modular square is distributed according to the chi-squared distribution. Denote the decoding threshold of the main channel by
, then
where
is the cumulative distribution function (CDF) of a chi-squared random variable.
The average transmission number
is determined by the main channel, which is equal to the expectation of the actual transmission number,
N,
The SOP of HARQ-CC, denoted by
, is defined as the probability that a message transmitted by Alice can be decoded successfully by Eve1 or … or EveM after
k transmissions. As passive receivers, Eve1, …, EveM only receive messages when retransmissions are requested by Bob. When the number of transmissions in the main channel is
N,
where
is the mutual information of the wiretap channel,
is the probability that the
transmission occurs, and
. Assume that
M wiretap channels are i.i.d. Gaussian block fading channels,
,
. Denote the decoding threshold of a wiretap channel by
. Then we define
Hence, the SOP after
K transmissions becomes
It is well-known that an extremely small COP is the fundamental reliablity requirement in modern systems. We assume that under different latency requirements (i.e., different maximum transmission numbers
K), a small
has to be assured. Thus we have
, then
As
N is an integer,
is also
power of the complementary CDF (CCDF) of a Poisson random variable. With a given
, the PDF and CDF are both well-known as a log-concave function of
N. According to [
28], its CCDF is also log-concave. In other words,
is concave with respect to
N. Under the above assumption that a low
is assured under different
K,
. According to Jenson’s inequality, we have
where (
a) is true, based on the general mean inequality, and
and
are both positive. Thus,
Substituting Equation (
7) into Equation (
11), we approximate the SOP of the
transmission by its upper bound, as follows:
For simplicity, we define and , which means that the maximum transmission number of COP and SOP has been reached.
Most related works have not considered the influence of SOP in secrecy throughput, but this has been found to be inaccurate [
24]. Hence, we define the effective secrecy throughput (EST) of a secure HARQ-CC system as [
26]
where
indicates the maximum rate of each reliable and secure transmission,
is the average transmission number, and the COP and SOP are denoted by
and
, respectively. Based on the renewal–reward theorem [
29,
30],
in Equation (
13) expresses the average reliable and secure transmission rate of each transmission. As this metric demonstrates the secrecy performance more comprehensively, we adapted the code rate and secrecy redundancy rate to enhance the performance with this criteria in the following section.
4. Rate Adaption in Secure HARQ-CC System
In this section, in order to improve the performance of secure transmission when multiple eavesdroppers exist and latency is limited, we optimized the code rate and secrecy redundancy rate to maximize the EST of HARQ-CC. Three cases were considered: When is given, is optimized by a parameterized closed-form solution, with and without a COP constraint. When is given, is optimized by a fix-point method, with and without an SOP constraint. Combining the above methods, we then solved the joint optimization of the rate pair by an iterative algorithm with and without both COP and SOP constraints.
4.1. Optimization of Code Rate
In a secure HARQ-CC system, when the number of eavesdroppers is
M, the maximum transmission number is
K and the secrecy redundancy rate is given by
, we first considered the problem of how to determine the code rate which maximizes the EST:
where
,
and
are obtained by Equations (
4), (
12) and (
13), respectively. Now, we extended the parameterized closed-form solution [
17] to solve this problem. Several HARQ schemes tell us the standard solution is to solve the equation
for the (globally) optimal rate point
. Furthermore,
is required to guarantee a global maximum.
The basic idea of this solution method is to use the substitution for the rate in the numerator of the EST expression. only occurs in the numerator once; hence, instead of considering the rate , we focus on the threshold in the optimization.
The EST expression for secure HARQ-CC is first parameterized with respect to
, according to
where
, and
is also function of
, as
,
,
M and
K are given. Then, we take the derivative with respect to
,
Let
, where
is the optimal point, and divide both sides by
. Then, we have
where the
-terms and
-terms are separated into different sides of Equation (
17). We define
Then, Equation (
17) is given by
. From Equation (19), this relationship becomes
. Let
, which is rewritten to
, which is solved by
where
is the principal branch (
) of Lambert’s
W-function. Thus, we have
.
Then, we solve the problem in Equation (
14) by
where
. We see that all equations are expressed only in terms of the parameter
. With the given
, the optimal
and
can therefore be obtained.
As , defined in Equation (19), can be expanded by , we give the low and high SNR asymptotes as follows:
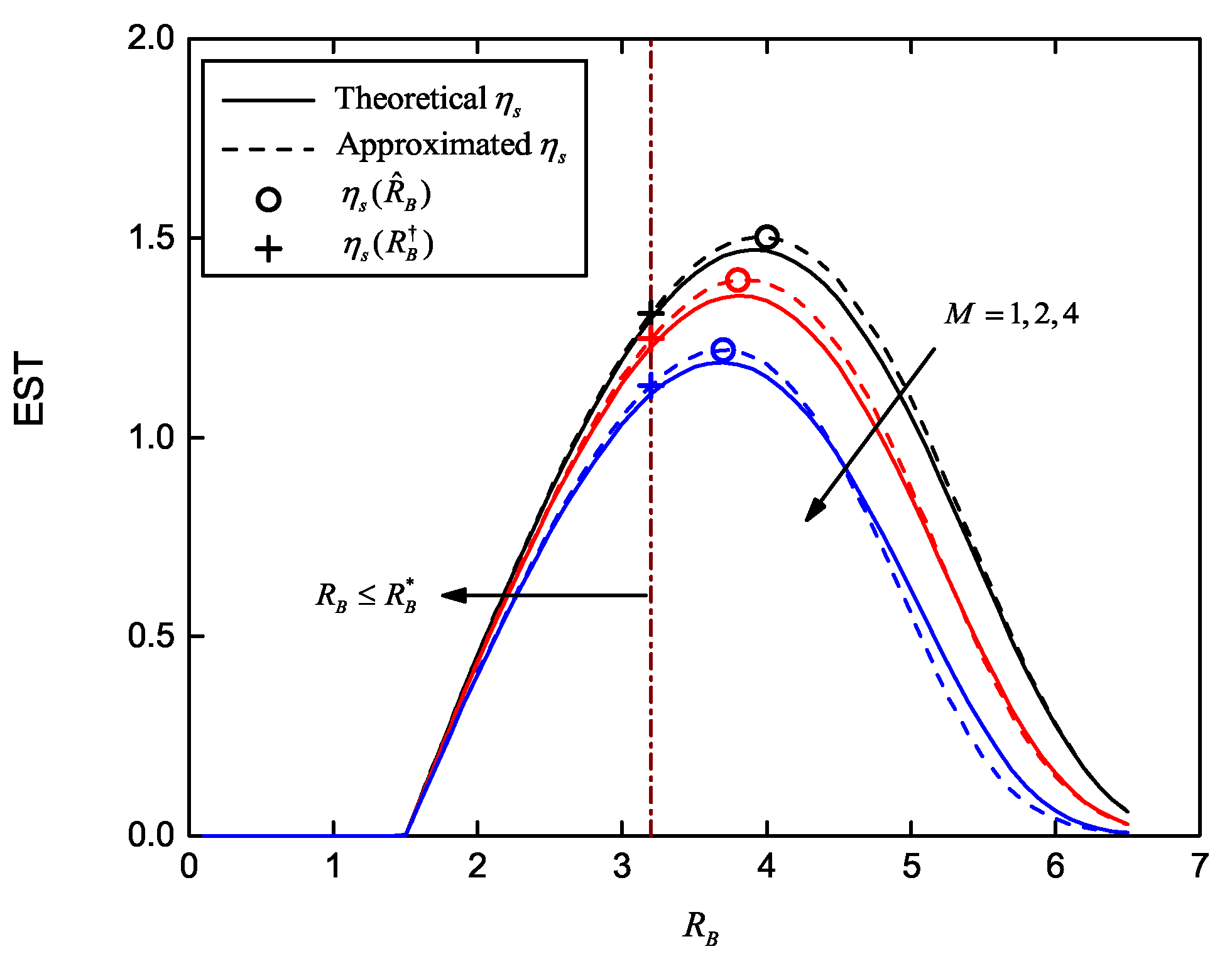
Remark 1. As for finite M, the problem in Equation (14) is solved bywhere . Proof. When , we have . By , , our solutions then become Equations (24)–(26), as , , and . □
Remark 2. As for finite M, the problem in Equation (14) is solved bywhere . Proof. When , . By , we have . Then, Equations (27)–(29) can be achieved. □
High reliability is the fundamental requirement in a modern wireless communication system. Hence, we continue to consider the problem in Equation (
14) with the following COP constraint:
where
denotes the target COP. According to Equation (
4),
increases monotonically with increasing
. Hence, we know the COP constraint requires
, where
in which
is the inverse function of the CDF of the chi-squared distribution.
As the solution of Equation (
14) requires
and
, (30) can be solved by:
where the optimal point
is always the maximum point in the feasible set of
.
4.2. Optimization of Secrecy Redundancy Rate
When the number of eavesdroppers is
M, the maximum transmission number is
K and code rate is given by
, we consider the problem of how to determine the secrecy redundancy rate which maximizes the EST:
where
is obtained by Equation (
13). With the given
, the decoding threshold of main channel becomes
. According to Equation (
4),
Thus, the EST of HARQ-CC becomes
where
and
are both determined, and
is given in Equation (
6) and approximated in Equation (
12).
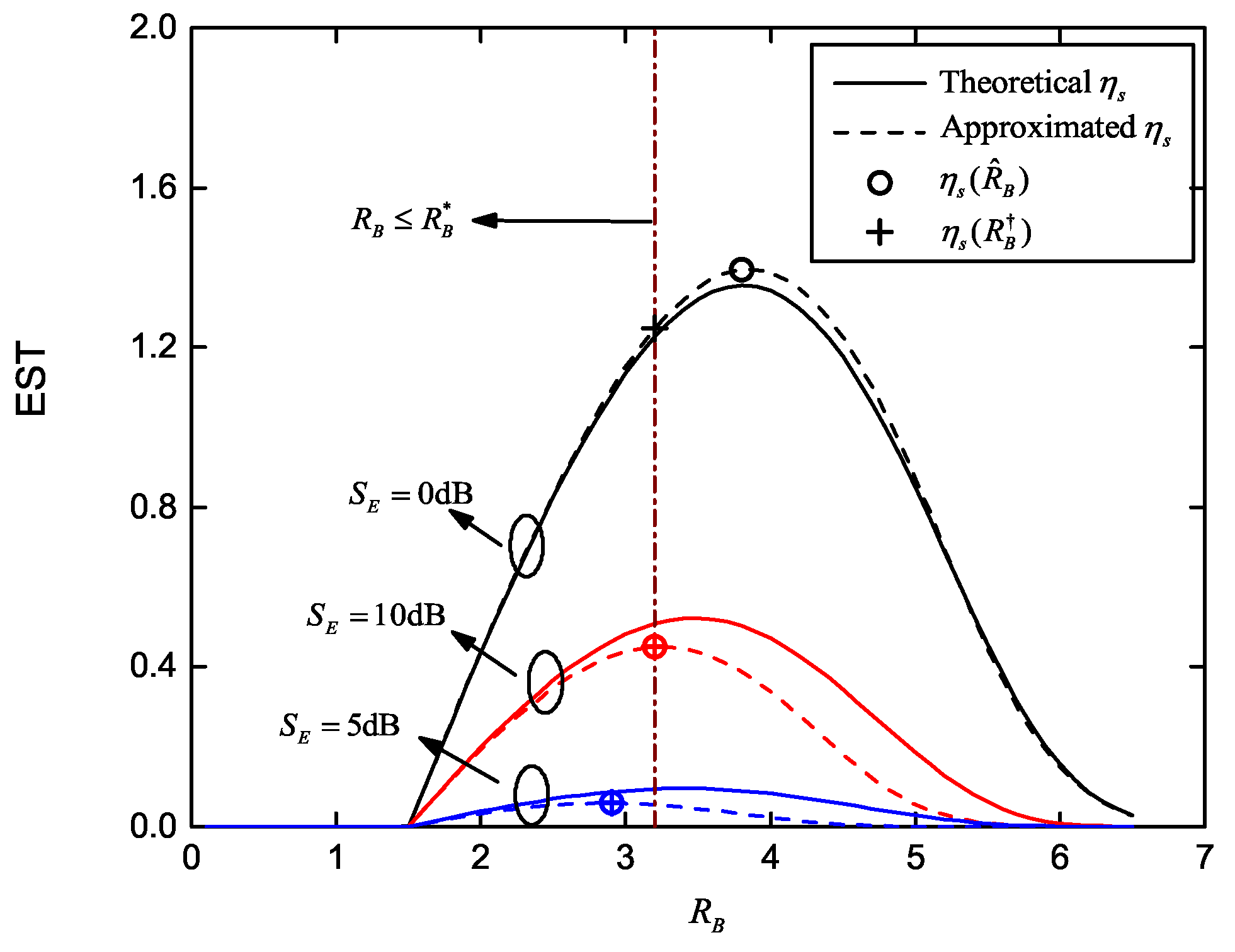
Proposition 1. is a log-concave function on , with existing maximum value.
Proof. Take the natural logarithm of both sides of Equation (
35),
where the first two parts in the RHS of Equation (
36) are determined. In the third part,
is a composition function
on
, and
.
is obviously concave. Based on the convexity-preserving properties,
is still concave on
. Finally, as
is the
power of the CDF of a chi-squared distribution, which is logarithmic concave,
is concave. Therefore,
is logarithmic concave with maximum value [
31]. □
Therefore, the log-concave optimization problem given in Equation (
33) can be converted to the following concave one:
Based on the above analysis, we know that if the optimal point
satisfies
, then
and
both have their maximum value at this value. From Equation (
35),
where
is approximated by Equation (
12) and its first derivative is
Substituting Equations (
12) and (
39) into Equation (
38) and letting
, we have the following fixed-point equation of the approximated
:
where
. Some classical techniques, such as the fixed-point iterative method, are suitable for solving the above equation.
Remark 3. As , we obtain .
Proof. Since
if
, when
, we have
. Hence, from Equation (
12),
and Equation (
35) become
It is easy to find that the maximum value of , , is obtained when . □
Remark 4. As , can be obtained by solving the fixed-point equation, Proof. If
,
. Applying
when
, we have
Substituting Equation (
43) into Equation (
40), Equation (
42) can be obtained. □
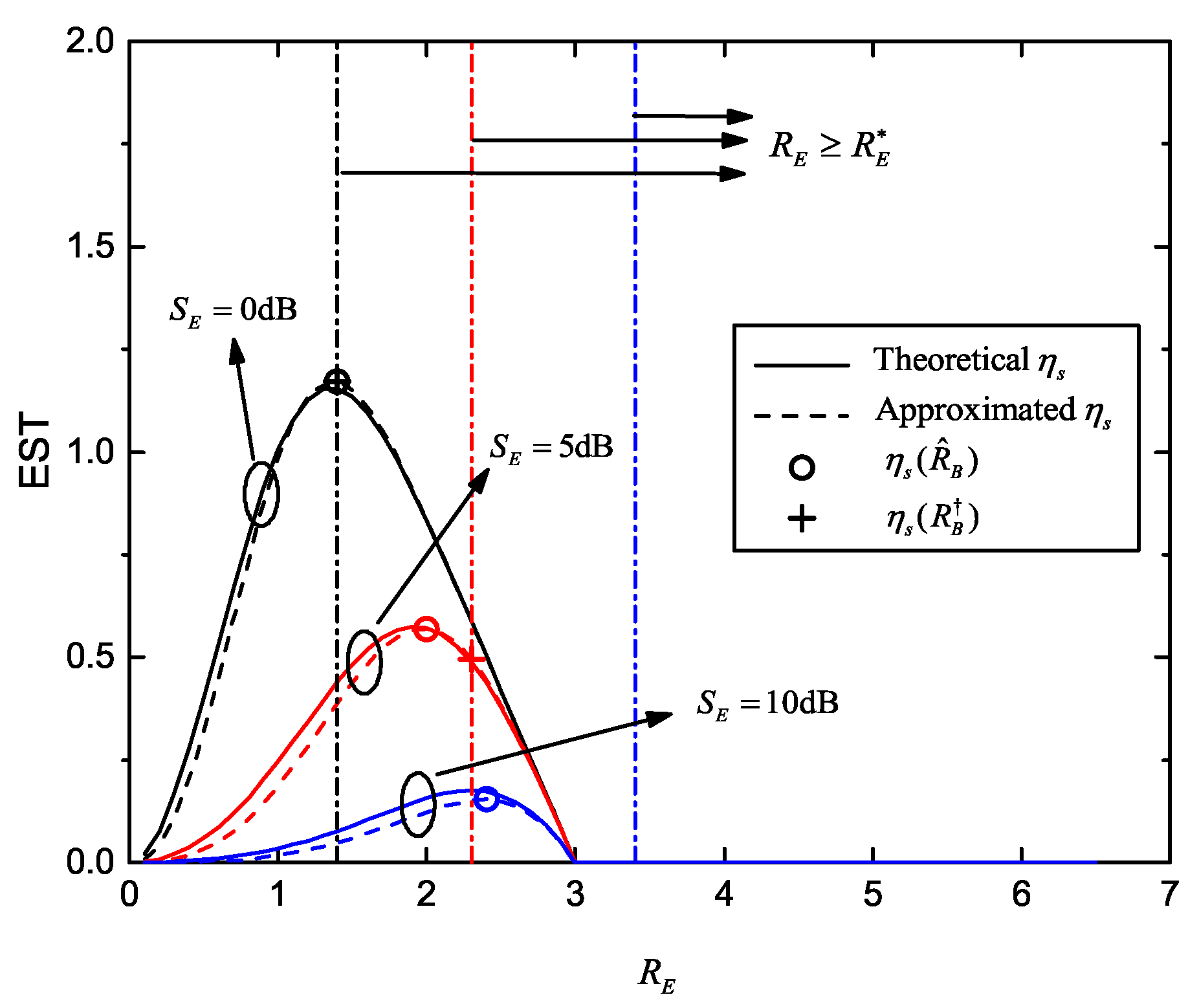
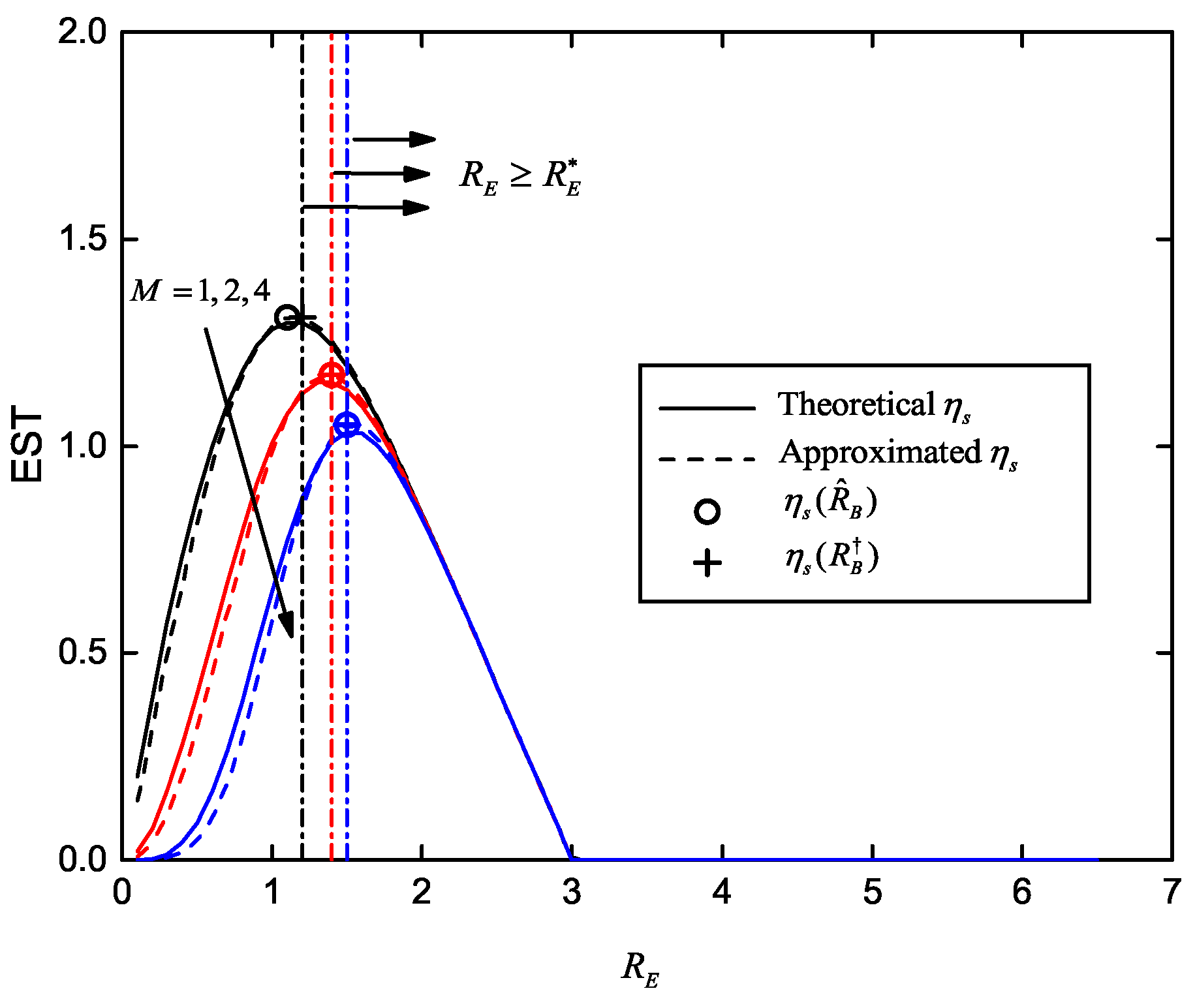
When the SOP constraint is required (e.g., in some special application scenarios), the optimization problem of secrecy redundancy rate aiming to enhance the EST becomes:
where
denotes the target SOP. According to Equation (
12),
decreases monotonically with increasing
. Hence, we know the SOP constraint requires
, and
where
is the same inverse function of the CDF of the chi-squared distribution as in Equation (
31).
Since EST in Equation (
35) has been proven to be log-concave on
and
, Equation (44) can be solved by
where the optimal point
is always the maximum point in the feasible set of
.
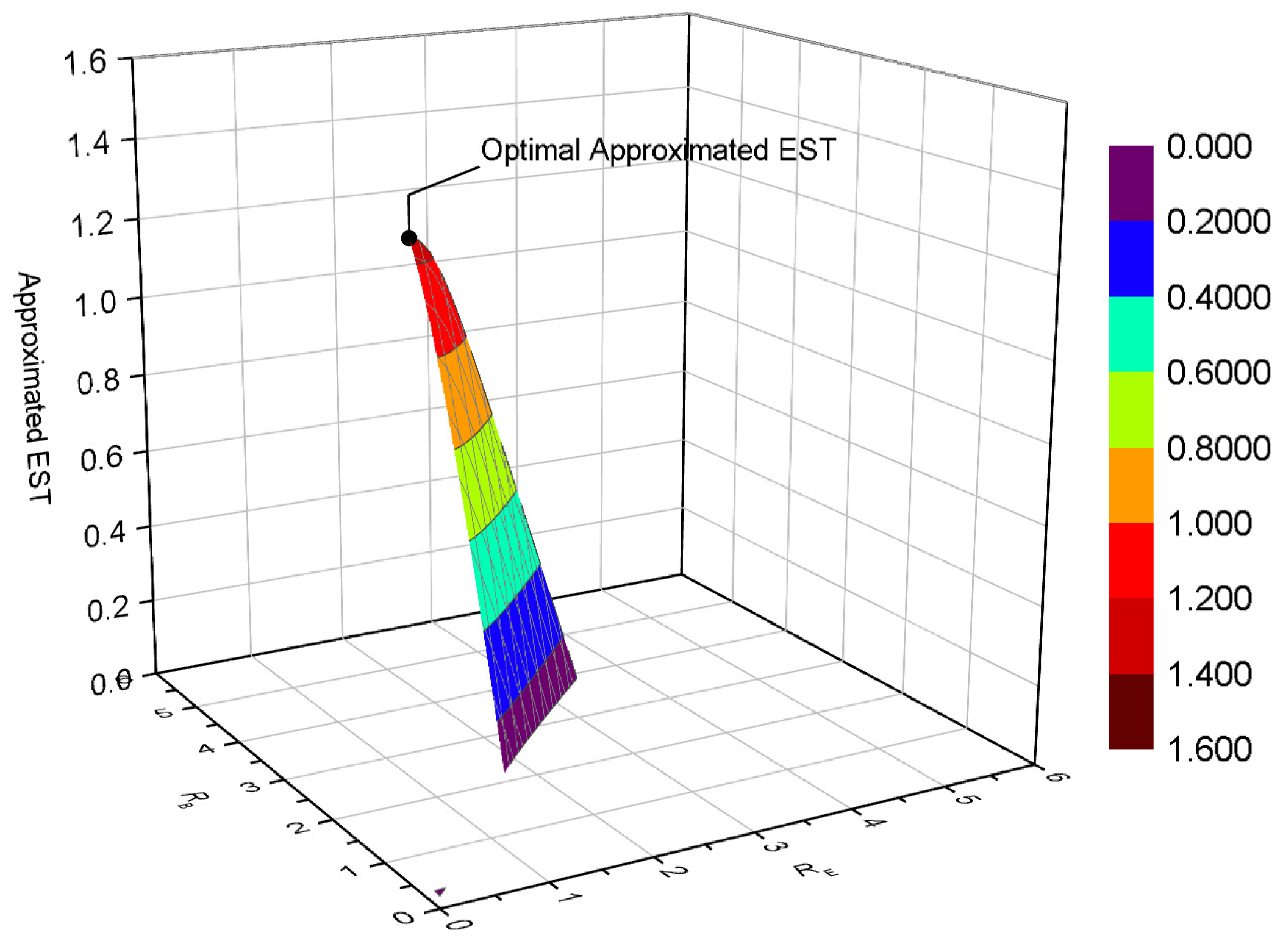
4.3. Optimization of the Rate Pair
In this part, we discuss a more general problem, which optimizes both the code rate and secrecy redundancy rate—that is, the rate pair (
)—with the EST criteria. When multiple eavesdroppers and limited retransmission number are still considered, this optimization problem is given by
where
is obtained by Equation (
13),
and
are given by Equations (
4) and (
12), respectively. As the expression of
is extremely complicated and its concavity is difficult to prove, we proposed an iterative algorithm to determine the rate pair (
,
).
In brief, the optimization problem in Equation (
47) can be tackled by iteratively adapting
and
separately until the EST gain denoted by
is no greater than
, where
is a preassigned small positive real number (e.g.,
). Specifically, it is first assumed that
, where
and
denote the optimal EST before and after each iteration, respectively. Here, we initialize them as
and
. The optimal rates are initialized as
and
. Next, using
, we solve the optimization of
in Equation (
14), while the optimal point
is obtained by Equations (21)–(23). Then, using
, we solve the optimization of
in Equation (
33), while the optimal point
is obtained by Equation (
40). After this iteration, we computed the maximum EST,
, by Equation (
13) and set
to evaluate the EST gain by
. Simultaneously,
is updated by
for next iteration. The iterations continue if
; otherwise, the optimal rate pair (
) is output. This algorithm giving the
-suboptimal solution is summarized in Algorithm 1.
| Algorithm 1 Iterative optimization of () for solving Equation (47). |
Input:, , , , ; - 1:
whiledo - 2:
; - 3:
Compute by Equations (21)–(23) - 4:
- 5:
Compute by Equation ( 40) - 6:
Compute by Equation ( 13) - 7:
- 8:
- 9:
- 10:
end while
Output:
(); |
Then, we reconsider Equation (
47) when COP and SOP constraints are both required. The optimization becomes:
where
and
denote the target COP and SOP, respectively. This problem can be solved by a modified version of Algorithm 1, in which
and
are replaced by
and
, computing Equations (
32) and (
46). In other words, the optimal rate pair should be selected among its feasible set.