1. Introduction
Owing to vast development in the modern digital era, the world has grown to be a worldwide community sharing private information. Because of this, people use images instead of long texts for sharing this kind of information securely and privately [
1]. Therefore, the protection of such images has become one of the vital concerns in medical, military, and many other areas. Recently, many cryptographic algorithms depending on chaotic systems have been used in image encryption [
2]. One of the recognized methods employed before image transmission is to convert an image into an unintelligible form, so that the transmitted message of the distorted image will not be discovered if it has reached an unsought end [
3,
4]. The encryption process is done with the help of a key, which produces variation on the pixel values of the image and destroys the apparent image attribute. Another encryption process is the scrambling image technique. In this technique, all pixel values are repositioned between different pixels of the image to be different from the original plain image, for example, Arnold transform, exponential transformation, geometry transform, and so on. These transformations have definite regularity, although the results of pixel distribution are different after scrambling, due to changes in only the position of pixels, without changing gray values. Arnold’s map has the property of periodicity. After running the algorithm for a certain number of times, the original image can be restored. Therefore, it has a weakness for the system [
5]. However, whilst [
6] demonstrated the powerful recovery of an image encryption system based on an Arnold map and Lü map, their encryption system was susceptible to several attacks, such as plaintext and chosen-text attacks when it depended on only the permutation of pixel values [
7]. As a result, these attack pixel values have to be rearranged and vary their position. Rearrangement of the values of pixels is called the confusion process, while changing the pixel values is known as the diffusion process. Chaos is a multi-disciplinary hypothesis which states that during the randomness of the chaotic complex technique, the chaotic system generates sequences due to its initial parameters’ sensitivity, periodic and pseudo randomness, and long-term volatility [
8], which encouraged us to employ the chaos theory in our new proposed scheme.
In recent years, several scientific papers have concentrated on researching chaotic image encryption. In 2015 [
9], S. S. Askar, A. A. Karawia et al. presented an image encryption system based on a chaotic economic map, and the simulation outputs a display so that the proposed algorithm can utilize the same secret keys to encrypt and decrypt the images successfully. The security analysis shows that the encrypted images have a good performance, but cannot resist noise attacks. After one year, Abbas proposed a new image encryption technique based on unconventional element analysis and Arnold’s Cat Map [
10], which was easily achieved and afforded an efficient and secure approach for image encryption. However, the algorithm depends on the encryption of square images only, so the domain of application is remarkably restricted. Later, in 2017, Shaikh, Chapaneri et al. [
11] proposed a color image encryption algorithm, which is a single round-based hyperchaotic system due to bi-directional pixel diffusion that contributes towards an increased security and improved efficiency. Recently, in 2019, Chenghai Li et al. used the “transforming-scrambling-diffusion” model to introduce a hyperchaotic color image encryption algorithm that depends on converting the pixel values into gray codes before scrambling [
12]. In the same year, Priya Ramasamy et al. suggested an improved logistical map while using a chaotic maps function and uncomplicated encryption techniques, such as block scrambling and modified zigzag transformation, for encryption phases [
13]. Recently, deoxyribonucleic acid (DNA) was applied to an image chaotic cryptosystem [
14,
15,
16,
17,
18,
19,
20,
21,
22], as a result of its numerous superior characteristics, such as its enormous parallelism, vast storage, small power consumption, etc. In 2016, Kulsoom et al. extracted the most significant bits and the least significant bits for each pixel of an image and performed DNA computing for them. Kulsoom et al.’s algorithm has a low robustness against noise because most digits of each pixel are not changed [
23]. After that, in 2018, Ran Wei et al. proposed an image cryptosystem that depends on the combination of DNA encoding and several chaotic maps [
24]. The performance analysis illustrated that the system could greatly enhance the sensitivity of plain images and secret keys, but the algorithm was complex and the necessities for hardware were comparatively high. In 2020, J. Wu, J. Shi, T. Li, proposed a novel image encryption algorithm based on a hyperchaotic system and variable kernels for the confusion stage and a DNA technique for the diffusion stage [
25].
Mitochondrial DNA (mtDNA) is a small part of the DNA of organelle cells within eukaryotic cells [
26]. Eukaryotic cells are organisms that have a nucleus enclosed within membranes that are used to transform chemical energy into a formula that cells can use [
27]. In humans, there are 16,569 base duos of mitochondrial DNA to code only 37 genes. The first major part of the human genome that can be sequenced is human mitochondrial DNA [
28]. mtDNA is congenital and uniquely from the mother in several organisms, including humans. Since animal mtDNA develops more rapidly than nuclear genetic symbols [
29,
30], it signifies a mainstay of phylogenetic and evolutionary biology. mtDNA allows inspection of the kinship of inhabitants. Therefore, it has become vital in molecular biology and biotechnology.
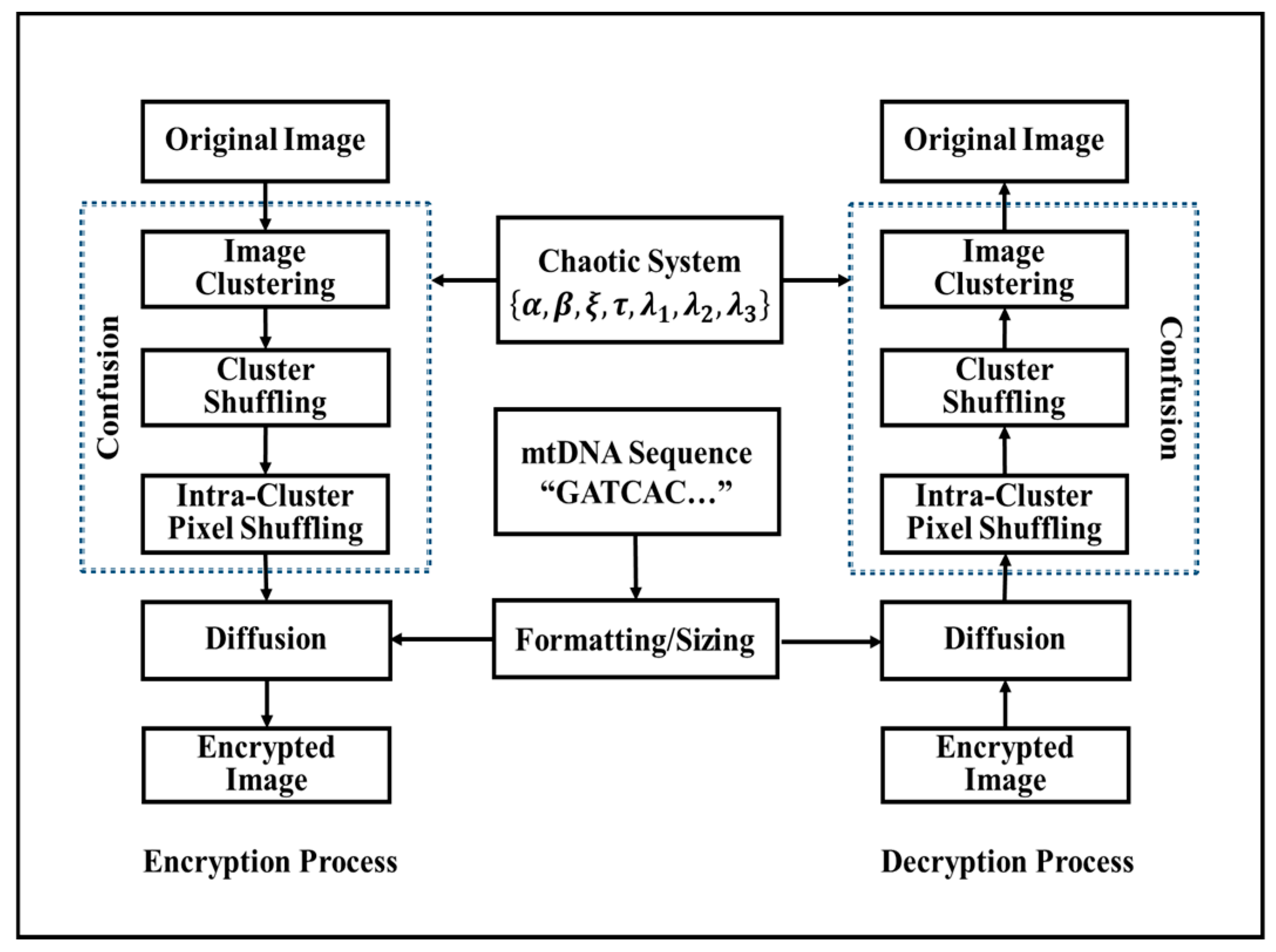
In this article, a new image cryptosystem is presented to encrypt a color image using identical encryption and decryption schemes. Both of these processes consist of confusion stages employing a hyperchaotic system, diffusion stage, and mtDNA. The proposed encryption algorithm was applied on three channels of a color plain image to increase uncertainty in the plain image. From the numerical analysis, the proposed algorithm was seen to be robust against various attacks, for example, chosen/known plain text attacks, brute force attacks, differential cipher image attacks, and entropy attacks. It has a large key space and is sensitive to minimal change in the chosen secret key. The encryption scheme was also compared with newly developed encryption techniques. The rest of the article is organized as follows.
Section 2 details a brief description of the hyperchaotic system, mtDNA, and DNA encoding. The explanation and argument of the proposed encryption/decryption algorithm are introduced in
Section 3.
Section 4 gives the numerical simulation results, while the security act of the proposed scheme is analyzed in
Section 5. Finally,
Section 6 concludes the article.
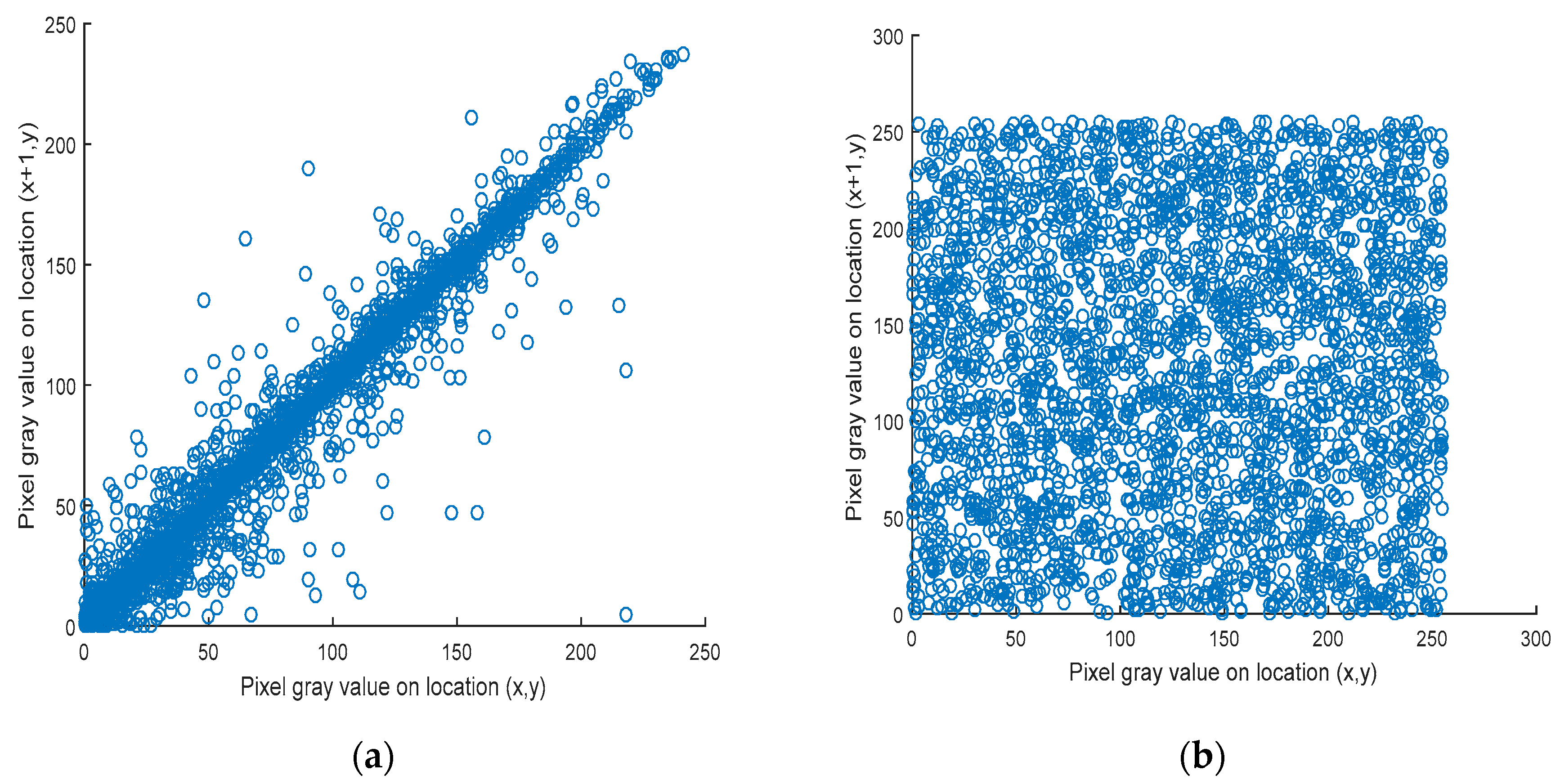
4. Simulation Results
Experimentation was carried out on Lena and baboon images. The Matlab (R2015a) software (MathWorks, Natick, MA, USA) was used to apply the proposed algorithm. In the hyperchaotic map, the control parameters
, and
were used to produce a chaotic sequence. The hyperchaotic sequences were arranged and the position of arranged sequences was used to split the plain image into n-clusters, shuffle the whole clusters, and scramble the pixels of each cluster. The utilized colored plain images were Lena, with dimensions of 256
× 256 pixels, as shown in
Figure 3a, and Baboon, with dimensions of 512 × 512 pixels, as shown in
Figure 3d. The corresponding cipher image was generated using the encryption algorithm and is shown in
Figure 3b,e. Then, we decrypted the cipher image, as presented in
Figure 3b,e, with correct undisclosed key
K to get the perfectly reconstructed image shown in
Figure 3c,f.