An Overview of Key Technologies in Physical Layer Security
Abstract
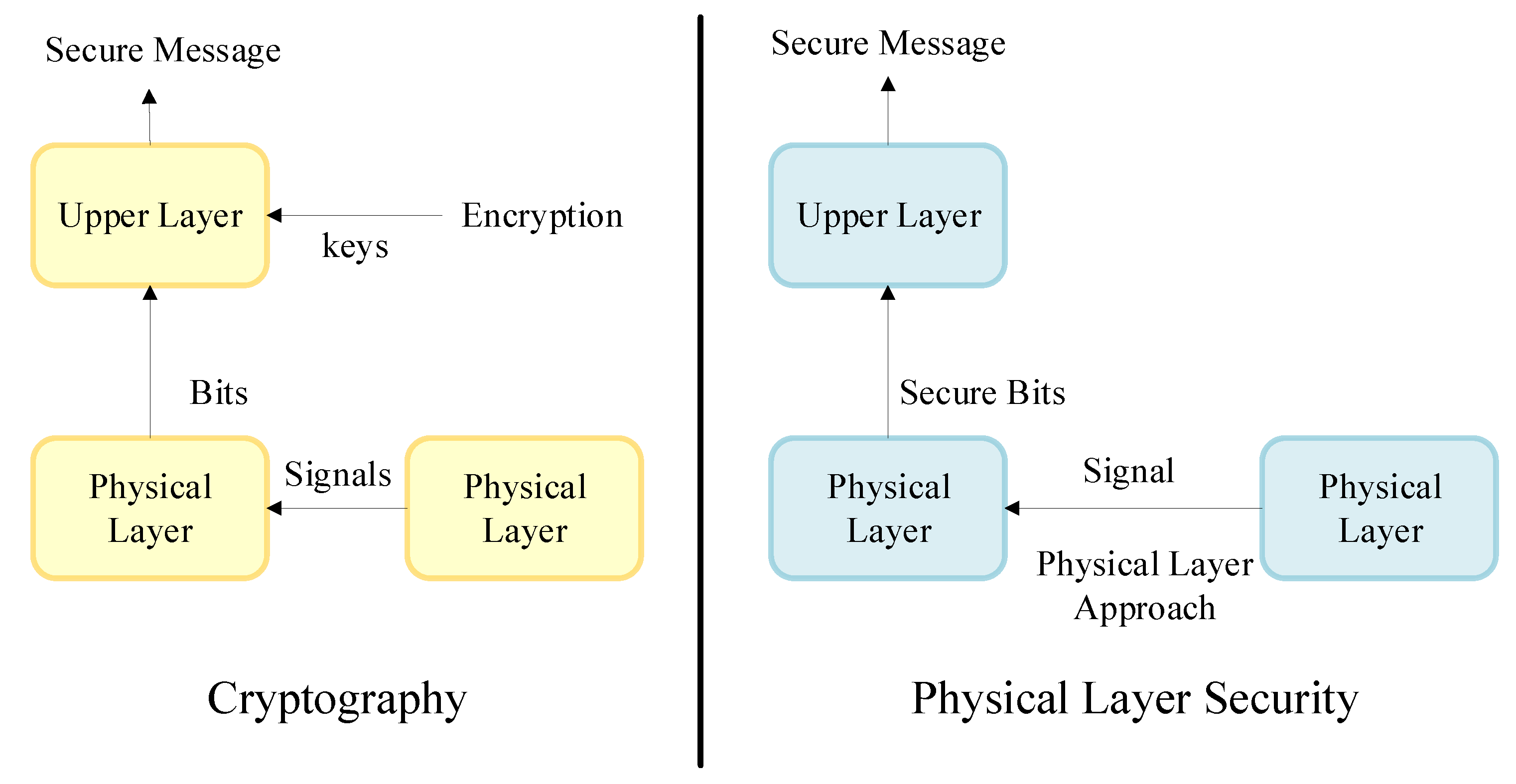
1. Introduction
1.1. Related Works
1.2. Overview of Cryptography and PLS
2. Background
2.1. Concept and Evolution of PLS
2.2. Motivation of PLS
2.3. Information-Theoretic Security
2.4. Performance Metrics in PLS
2.4.1. Secrecy Rate
2.4.2. Secrecy Outage Probability (SOP)
2.4.3. Quality of Service (QoS)-Related Metrics
2.5. Channel State Information (CSI)
2.6. Multiple-Input Multiple-Output (MIMO) Communication
3. Secure Multi-Antenna Techniques
3.1. Convex Optimization
3.2. Beamforming
3.3. Artificial Noise (AN) Precoding
3.4. Zero-Forcing (ZF) Precoding
3.5. Cooperative Jamming
3.6. Space-Time Coding (STC)
4. Challenges and Promising PLS Solutions
4.1. Challenges and Limitations in PLS
4.2. Promising PLS Solutions
4.2.1. Simultaneous Wireless Information and Power Transfer (SWIPT)
4.2.2. Machine Learning (ML)-Based Channel Estimation
4.2.3. Unmanned Aerial Vehicle (UAV)
4.2.4. Intelligent Reflecting Surface (IRS)
4.2.5. Visible Light Communication (VLC)
4.2.6. PLS in Satellite Communication
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| AN | Artificial noise |
| AWGN | Additive white Gaussian noise |
| BER | Bit error rate |
| CSI | Channel state information |
| IRS | Intelligent reflecting surface |
| ITU | International telecommunication Union |
| MIMO | Multiple-input multiple-output |
| OFDM | Orthogonal frequency division multiplexing |
| PLS | Physical layer security |
| QoS | Quality of service |
| SINR | Signal-to-interference-plus-noise ratio |
| STBC | Space-time block code |
| UAV | Unmanned aerial vehicle |
| URLLC | Ultra-reliable low latency communication |
| WIPT | Wireless information and power transfer |
| ZF | Zero-forcing |
References
- International Telecommunication Union. Statistics. Available online: https://www.itu.int/en/ITU-D/Statistics/Pages/stat/default.aspx (accessed on 13 November 2019).
- Steve. 2019 Official Annual Cybercrime Report. Technical Report. Available online: https://www.herjavecgroup.com/wp-content/uploads/2018/12/CV-HG-2019-Official-Annual-Cybercrime-Report.pdf (accessed on 13 November 2019).
- Zorgui, M. Wireless Physical Layer Security: On the Performance Limits of Secret-Key Agreement. Masters’s Thesis, King Abdullah University of Science and Technology, Thuwal, Saudi Arabia, 2015. [Google Scholar]
- Campagna, M.; Chen, A.L.; Dagdelen, Ö.; Darmstadt, T.U.; Ding, J.; Fernick, J.K.; Hayford, D.; Jennewein, T.; Lütkenhaus, N.; Mosca, M.; et al. Quantum Safe Cryptography and Security an Introduction, Benefits, Enablers and Challenges Quantum Safe Cryptography and Security Authors & Contributors Quantum Safe Cryptography and Security 2. Technical Report. 2015. Available online: https://www.etsi.org/images/files/ETSIWhitePapers/QuantumSafeWhitepaper.pdf (accessed on 12 November 2019).
- Li, H.; Wang, X. Physical-Layer Security Enhancement in Wireless Communication Systems Part of the Systems and Communications Commons Recommended Citation. Technical Report. 2013. Available online: https://core.ac.uk/download/pdf/61640146.pdf (accessed on 13 November 2019).
- Mukherjee, A.; Ali, S.; Fakoorian, A.; Huang, J.; Swindlehurst, A.L. Principles of Physical Layer Security in Multiuser Wireless Networks: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Wang, D.; Bai, B.; Member, S.; Zhao, W.; Han, Z. A Survey of Optimization Approaches for Wireless Physical Layer Security. IEEE Commun. Surv. Tutor. 2019, 21, 1878–1911. [Google Scholar] [CrossRef]
- Hamamreh, J.M.; Furqan, H.M.; Arslan, H. Classifications and Applications of Physical Layer Security Techniques for Confidentiality: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2019, 21, 1773–1828. [Google Scholar] [CrossRef]
- Wang, N.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical-Layer Security of 5G Wireless Networks for IoT: Challenges and Opportunities. IEEE Internet Things J. 2019, 6, 8169–8181. [Google Scholar] [CrossRef]
- Arfaoui, M.A.; Soltani, M.D.; Tavakkolnia, I.; Ghrayeb, A.; Safari, M.; Assi, C.; Haas, H. Physical Layer Security for Visible Light Communication Systems: A Survey. IEEE Commun. Surv. Tutor. 2020, 1. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Towards Smart and Reconfigurable Environment: Intelligent Reflecting Surface Aided Wireless Network. IEEE Commun. Mag. 2020, 58, 106–112. [Google Scholar] [CrossRef]
- Guan, X.; Wu, Q.; Zhang, R. Intelligent Reflecting Surface Assisted Secrecy Communication: Is Artificial Noise Helpful or Not? IEEE Wirel. Commun. Lett. 2020, 1. [Google Scholar] [CrossRef]
- Abeywickrama, S.; Zhang, R.; Wu, Q.; Yuen, C.; Zhang, R.; Wu, Q.; Yuen, C. Intelligent Reflecting Surface: Practical Phase Shift Model and Beamforming Optimization. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020. [Google Scholar]
- Shen, H.; Xu, W.; Gong, S.; He, Z.; Zhao, C. Secrecy Rate Maximization for Intelligent Reflecting Surface Assisted Multi-Antenna Communications. IEEE Commun. Lett. 2019, 23, 1488–1492. [Google Scholar] [CrossRef]
- Wu, Q.; Mei, W.; Zhang, R. Safeguarding wireless network with UAVs: A physical layer security perspective. IEEE Wirel. Commun. 2019, 26, 12–18. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Zhang, Y.; Guizani, M. Secure UAV communication networks over 5G. IEEE Wirel. Commun. 2019, 26, 114–120. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Zhang, Y. UAV communications for 5G and beyond: Recent advances and future trends. IEEE Internet Things J. 2019, 6, 2241–2263. [Google Scholar] [CrossRef]
- Vázquez, M.Á.; Pérez-Neira, A.; Christopoulos, D.; Chatzinotas, S.; Ottersten, B.; Arapoglou, P.D.; Ginesi, A.; Tarocco, G. Precoding in multibeam satellite communications: Present and future challenges. IEEE Wirel. Commun. 2016, 23, 88–95. [Google Scholar] [CrossRef]
- Radhakrishnan, R.; Edmonson, W.W.; Afghah, F.; Rodriguez-Osorio, R.M.; Pinto, F.; Burleigh, S.C. Survey of Inter-Satellite Communication for Small Satellite Systems: Physical Layer to Network Layer View. IEEE Commun. Surv. Tutor. 2016, 18, 2442–2473. [Google Scholar] [CrossRef]
- Boero, L.; Bruschi, R.; Davoli, F.; Marchese, M.; Patrone, F. Satellite Networking Integration in the 5G Ecosystem: Research Trends and Open Challenges. IEEE Netw. 2018, 32, 9–15. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Zhou, C.; Zhang, Y. Physical-Layer Security in Space Information Networks: A Survey. IEEE Internet Things J. 2020, 7, 33–52. [Google Scholar] [CrossRef]
- Gençoğlu, M.T. Importance of Cryptography in Information Security. IOSR J. Comput. Eng. 2019, 21, 65–68. [Google Scholar] [CrossRef]
- Shiu, Y.S.; Chang, S.Y.; Wu, H.C.; Huang, S.C.; Chen, H.H. Physical layer security in wireless networks: A tutorial. IEEE Wirel. Commun. 2011, 18, 66–74. [Google Scholar] [CrossRef]
- Siddiqi, M.A.; Yu, H.; Joung, J. 5G Ultra-Reliable Low-Latency Communication Implementation Challenges and Operational Issues with IoT Devices. Electronics 2019, 8, 981. [Google Scholar] [CrossRef]
- Sun, L.; Du, Q. A Review of Physical Layer Security Techniques for Internet of Things: Challenges and Solutions. Entropy 2018, 20, 730. [Google Scholar] [CrossRef]
- Wyner, A.D. The Wire-Tap Channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Li, J. A Critical Review of Physical Layer Security in Wireless Networking. Master’s Thesis, University College London, London, UK, 2015. [Google Scholar]
- Bassily, R.; Ekrem, E.; He, X.; Tekin, E.; Xie, J.; Bloch, M.R.; Ulukus, S.; Yener, A. Cooperative security at the physical layer: A summary of recent advances. IEEE Signal Process. Mag. 2013, 30, 16–28. [Google Scholar] [CrossRef]
- Wang, L. Physical Layer Security in Wireless Cooperative Networks; Wireless Networks; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J. Physical-layer Security: From Information Theory to Security Engineering; Cambridge University Press: Cambridge, UK, 2011; p. 329. [Google Scholar]
- Rohokale, V.M.; Prasad, N.R.; Prasad, R. Cooperative Wireless Communications and Physical Layer Security: State-of-the-Art. J. Cyber Secur. Mobil. 2012, 1, 227–249. [Google Scholar]
- Chen, Y.; Yang, Y.; Yi, W. A cross-layer strategy for cooperative diversity in wireless sensor networks. J. Electron. 2012, 29, 33–38. [Google Scholar] [CrossRef]
- Ryland, K.S.; Clancy, T.C.; Buehrer, R.M.; Dietrich, C.B. Software-Defined Radio Implementation of Two Physical Layer Security Techniques. Technical Report. 2017. Available online: https://vtechworks.lib.vt.edu/bitstream/handle/10919/82055/Ryland_KS_T_2018.pdf?sequence=1&isAllowed=y (accessed on 8 November 2019).
- Shannon, C.E. Communication Theory of Secrecy Systems. Technical Report. 1949. Available online: http://netlab.cs.ucla.edu/wiki/files/shannon1949.pdf (accessed on 14 November 2019).
- Wang, H.M.; Zheng, T.X. Physical Layer Security in Random Cellular Networks; Springer Briefs in Computer Science; Springer: Singapore, 2016. [Google Scholar] [CrossRef]
- Hyadi, A.; Rezki, Z.; Alouini, M.S. An Overview of Physical Layer Security in Wireless Communication Systems with CSIT Uncertainty. IEEE Access 2016, 4, 6121–6132. [Google Scholar] [CrossRef]
- Wei, Y.; Zeng, K.; Mohapatra, P. Adaptive wireless channel probing for shared key generation. In Proceedings of the IEEE INFOCOM, Shanghai, China, 30 July 2011; pp. 2165–2173. [Google Scholar] [CrossRef]
- Harrison, W.K.; Sarmento, D.; Vilela, J.P.; Gomes, M. Analysis of Short Blocklength Codes for Secrecy. Technical Report. Available online: https://jwcn-eurasipjournals.springeropen.com/articles/10.1186/s13638-018-1276-1 (accessed on 26 February 2020).
- Csiszar, I.; Kijrner, J. Broadcast Channels with Confidential Messages. IEEE Trans. Inf. Theory 1978, 24, 339–348. [Google Scholar] [CrossRef]
- Blahut, R.E.; Costello, D.J., Jr.; Maurer, U.; Mittelholzer, T. Communications and Cryptography: Two Sides of One Tapestry; Symposium on Communications, C; Kluwer Academic Publishers: Dordrecht, The Netherlands, 1994; pp. 270–285. [Google Scholar]
- Safavi-Naini, R.; Canetti, R. Advances in Cryptology—CRYPTO 2012. In Proceedings of the 32nd Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012; Springer: Berlin, Germany, 2012; p. 888. [Google Scholar]
- Zhou, X.S.; Song, L.; Zhang, Y. Physical Layer Security in Wireless Communications; CRC Press: Boca Raton, FL, USA, 2016; p. 295. [Google Scholar]
- Lin, P.H.; Jorswieck, E. Multiuser Channels with Statistical CSI at the Transmitter: Fading Channel Alignments and Stochastic Orders, an Overview. Entropy 2017, 19, 515. [Google Scholar] [CrossRef]
- Migliore, M.; Pinchera, D.; Lucido, M.; Schettino, F.; Panariello, G. MIMO Channel-State Estimation in the Presence of Partial Data and/or Intermittent Measurements. Electronics 2017, 6, 33. [Google Scholar] [CrossRef]
- What Are MIMO, MRC, Beamforming, STBC, and Spatial Multiplexing? WLAN Troubleshooting Guide—Huawei. Available online: https://support.huawei.com/enterprise/en/doc/EDOC1000060368/d9adbe5a/what-are-mimo-mrc-beamforming-stbc-and-spatial-multiplexing (accessed on 25 January 2020).
- Mohaisen, M.; Wang, Y.; Chang, K. Multiple Antenna Technologies. Technical Report. Available online: https://arxiv.org/ftp/arxiv/papers/0909/0909.3342.pdf (accessed on 8 November 2019).
- Björnson, E.; Sanguinetti, L.; Wymeersch, H.; Hoydis, J.; Marzetta, T.L. Massive MIMO is a Reality-What is Next? Five Promising Research Directions for Antenna Arrays. Digit. Signal Process. 2019, 94, 3–20. [Google Scholar] [CrossRef]
- Kapetanovi, D.; Zheng, G.; Rusek, F. Physical Layer Security for Massive MIMO: An Overview on Passive Eavesdropping and Active Attacks. IEEE Commun. Mag. 2015, 53, 21–27. [Google Scholar] [CrossRef]
- Yaacoub, E.; Al-Husseini, M. Achieving physical layer security with massive MIMO beamforming. In Proceedings of the 2017 11th European Conference Antennas Propagation, EUCAP 2017, Paris, France, 19–24 March 2017; pp. 1753–1757. [Google Scholar] [CrossRef]
- Romero-Zurita, N.; Ghogho, M.; McLernon, D. Physical layer security of MIMO-OFDM systems by beamforming and artificial noise generation. Phys. Commun. 2011, 4, 313–321. [Google Scholar] [CrossRef]
- Sheng, Z.; Tuan, H.D.; Sheng, Z.; Tuan, H.D.; Duong, T.Q.; Vincent Poor, H. Beamforming Optimization for Physical Layer Security in MISO Wireless Networks. IEEE Trans. Signal Process. 2018, 66, 3710–3723. [Google Scholar] [CrossRef]
- Björnson, E.; Bengtsson, M.; Ottersten, B. Optimal Multiuser Transmit Beamforming: A Difficult Problem with a Simple Solution Structure. IEEE Signal Process. Mag. 2014, 31, 142–148. [Google Scholar]
- SANKAR, K. Maximal Ratio Combining (MRC). 2008. Available online: http://www.dsplog.com/2008/09/28/maximal-ratio-combining/ (accessed on 27 January 2020).
- Mohammadkhani, R. Lecture 13: MIMO Transceivers Part II. Technical Report. 2017. Available online: https://eng.uok.ac.ir/mohammadkhani/courses/Array_MIMO/L13-MIMO%20Tx-Rx-part%20II.pdf (accessed on 29 January 2020).
- Sidiropoulos, N.D.; Member, S.; Davidson, T.N.; Luo, Z.Q. Transmit Beamforming for Physical-Layer Multicasting. IEEE Trans. SIGNAL Process. 2006, 54. [Google Scholar] [CrossRef]
- Ghogho, M.; Swami, A. Physical-layer secrecy of MIMO communications in the presence of a poisson random field of eavesdroppers. In Proceedings of the 2011 IEEE International Conference on Communications Workshops (ICC), Kyoto, Japan, 5–9 June 2011. [Google Scholar] [CrossRef]
- Khisti, A.; Wornell, G.W. Secure Transmission with Multiple Antennas II: The MIMOME Wiretap Channel. IEEE Trans. Inf. Theory 2010, 56, 5515–5532. [Google Scholar]
- Huang, Y.; Palomar, D.P. Rank-constrained separable semidefinite programming with applications to optimal beamforming. IEEE Trans. Signal Process. 2010, 58, 664–678. [Google Scholar] [CrossRef]
- Zhao, P.; Zhang, M.; Yu, H.; Luo, H.; Chen, W.; Member, S. Robust Beamforming Design for Sum Secrecy Rate Optimization in MU-MISO Networks. IEEE Trans. Inf. FORENSICS Secur. 2015, 10. [Google Scholar] [CrossRef]
- Nasir, A.A.; Tuan, H.D.; Duong, T.Q.; Poor, H.V.; Tuan, H.D.; Poor, H.V. Secure and Energy-Efficient Beamforming for Simultaneous Information and Energy Transfer. IEEE Trans. Wirel. Commun. 2017, 16, 7523–7537. [Google Scholar]
- Nghia, N.T.; Tuan, H.D.; Nghia, N.T.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. MIMO Beamforming for Secure and Energy-Efficient Wireless Communication. IEEE Signal Process. Lett. 2017, 24, 236–239. [Google Scholar] [CrossRef]
- Park, J.; Sung, Y.; Kim, D.; Vincent Poor, H. Outage probability and outage-based robust beamforming for MIMO interference channels with imperfect channel state information. IEEE Trans. Wirel. Commun. 2012, 11, 3561–3573. [Google Scholar] [CrossRef]
- Pu, W.; Xiao, J.; Zhang, T.; Luo, Z.Q. Overcoming DoF Limitation in Robust Beamforming: A Penalized Inequality-Constrained Approach. arXiv 2019, arXiv:1910.03365. [Google Scholar]
- Zhao, N.; Yu, F.R.; Sun, H. Adaptive energy-efficient power allocation in green interference-alignment-based wireless networks. IEEE Trans. Veh. Technol. 2015, 64, 4268–4281. [Google Scholar] [CrossRef]
- Cadambe, V.R.; Jafar, S.A. Interference alignment and degrees of freedom of the K-user interference channel. IEEE Trans. Inf. Theory 2008, 54, 3425–3441. [Google Scholar] [CrossRef]
- Maddah-Ali, M.A.; Motahari, A.S.; Khandani, A.K. Communication over MIMO X channels: Interference alignment, decomposition, and performance analysis. IEEE Trans. Inf. Theory 2008, 54, 3457–3470. [Google Scholar] [CrossRef]
- Lee, J.H.; Chae, S.H.; Choi, W. Opportunistic jammer selection for secure degrees of freedom. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 4862–4867. [Google Scholar] [CrossRef]
- Jing, X.; Mo, L.; Liu, H.; Zhang, C. Linear Space-Time Interference Alignment for K-User MIMO Interference Channels. IEEE Access 2018, 6, 3085–3095. [Google Scholar] [CrossRef]
- Rihan, M.; Huang, L.; Zhang, P. Joint interference alignment and power allocation for NOMA-based multi-user MIMO systems. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 217. [Google Scholar] [CrossRef]
- Negi, R.; Goel, S. Secret communication using artificial noise. In Proceedings of the VTC-2005-Fall, 2005 IEEE 62nd Vehicular Technology Conference, Dallas, TX, USA, 28 September 2005; Volume 3, pp. 1906–1910. [Google Scholar] [CrossRef]
- Liao, W.C.; Chang, T.H.; Ma, W.K.; Chi, C.Y. QoS-based transmit beamforming in the presence of eavesdroppers: An optimized artificial-aoise-aided approach. IEEE Trans. Signal Process. 2011, 59, 1202–1216. [Google Scholar] [CrossRef]
- Zhang, H.; Duan, L. Going beyond Secrecy Rate via Information Jamming. In Proceedings of the 2018 IEEE Global Communication Conference GLOBECOM 2018, Abu Dhabi, United Arab Emirates, 9–13 December 2018. [Google Scholar] [CrossRef]
- Goel, S.; Negi, R. Guaranteeing secrecy using artificial noise. IEEE Trans. Wirel. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- Liu, W.; Li, M.; Tian, X.; Wang, Z.; Liu, Q. Transmit Filter and Artificial Noise Design for Secure MIMO-OFDM Systems. arXiv 2017, arXiv:1704.08007. [Google Scholar]
- Reboredo, H.; Prabhu, V.; Rodrigues, M.R.; Xavier, J. Filter design with secrecy constraints: The multiple-input multiple-output Gaussian wiretap channel with zero forcing receive filters. In Proceedings of the ICASSP, IEEE International Conference Acoustics, Speech, and Signal Processing, Prague, Czechia, 22–27 May 2011; pp. 3440–3443. [Google Scholar] [CrossRef]
- Dong, L.; Han, Z.; Petropulu, A.P.; Poor, H.V. Cooperative jamming for wireless physical layer security. In Proceedings of the 2009 IEEE/SP 15th Workshop on Statistical Signal Processing, Cardiff, UK, 31 August–3 September 2009; pp. 417–420. [Google Scholar] [CrossRef]
- Cumanan, K.; Alexandropoulos, G.C.; Ding, Z.; Karagiannidis, G.K. Secure Communications with Cooperative Jamming: Optimal Power Allocation and Secrecy Outage Analysis. IEEE Trans. Veh. Technol. 2017, 66, 7495–7505. [Google Scholar] [CrossRef]
- Yang, M.; Zhang, B.; Huang, Y.; Yang, N.; Guo, D.; Gao, B. Secure Multiuser Communications in Wireless Sensor Networks with TAS and Cooperative Jamming. Sensors 2016, 16, 1908. [Google Scholar] [CrossRef]
- Hu, L.; Wen, H.; Wu, B.; Pan, F.; Liao, R.F.; Song, H.; Tang, J.; Wang, X. Cooperative Jamming for Physical Layer Security Enhancement in Internet of Things. IEEE Internet Things J. 2018, 5, 219–228. [Google Scholar] [CrossRef]
- Anjos, G.; Castanheira, D.; Silva, A.; Gameiro, A. Securing Non-Orthogonal Multiple Access Systems Against Simultaneous Eavesdropping Attacks Coming from Inside and Outside of the Network. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; Volume 2019. [Google Scholar] [CrossRef]
- Zhang, T.; Wen, H.; Jie, T.; Song, H.; Xie, F. Cooperative Jamming Secure Scheme for IWNs Random Mobile Users Aided by Edge Computing Intelligent Node Selection. IEEE Trans. Ind. Inform. 2020. [Google Scholar] [CrossRef]
- Zhong, Y.; Zhou, F.; Wang, Y.; Deng, X.; Al-Dhahir, N. Cooperative Jamming-Aided Secure Wireless Powered Communication Networks: A Game Theoretical Formulation. IEEE Commun. Lett. 2020, 24, 1081–1085. [Google Scholar] [CrossRef]
- Huo, Y.; Fan, X.; Ma, L.; Cheng, X.; Tian, Z.; Chen, D. Secure Communications in Tiered 5G Wireless Networks with Cooperative Jamming. IEEE Trans. Wirel. Commun. 2019, 18, 3265–3280. [Google Scholar] [CrossRef]
- Wang, Q.; Zhou, F.; Hu, R.Q.; Qian, Y. Energy-Efficient Beamforming and Cooperative Jamming in IRS-Assisted MISO Networks. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020. [Google Scholar] [CrossRef]
- Alamouti, S.M. A Simple Transmit Diversity Technique for Wireless Communications. IEEE J. Select. Areas Commun. 1998, 16, 1451–1458. [Google Scholar] [CrossRef]
- Sujatha, B. Space-Time Block Coding (STBC) for Wireless Networks. Int. J. Distrib. Parallel Syst. (IJDPS) 2012, 3. [Google Scholar] [CrossRef]
- Allen, T.; Cheng, J.; Al-Dhahir, N. Secure space-time block coding without transmitter CSI. IEEE Wirel. Commun. Lett. 2014, 3, 573–576. [Google Scholar] [CrossRef]
- Akuon, P.O.; Xu, H. Secure Signal and Space Alamouti Scheme. SAIEE Afr. Res. J. 2018, 107, 237–244. [Google Scholar] [CrossRef]
- Yang, N.; Yan, S.; Yuan, J.; Malaney, R.; Subramanian, R.; Land, I.; Yan, S.; Yuan, J.; Malaney, R. Artificial Noise: Transmission Optimization in Multi-Input Single-Output Wiretap Channels. IEEE Trans. Commun. 2015, 63, 1771–1783. [Google Scholar] [CrossRef]
- Liu, S.; Hong, Y.; Viterbo, E. Practical Secrecy using Artificial Noise. IEEE Commun. Lett. 2013, 17, 1483–1486. [Google Scholar]
- Zhang, R.; Ho, C.K. MIMO broadcasting for simultaneous wireless information and power transfer. IEEE Trans. Wirel. Commun. 2013, 12, 1989–2001. [Google Scholar] [CrossRef]
- Zhou, F.; Member, S.; Li, Z.; Member, S.; Cheng, J.; Li, Q.; Si, J.; Zhou, F.; Li, Z.; Si, J.; et al. Robust AN-Aided Beamforming and Power Splitting Design for Secure MISO Cognitive Radio With SWIPT. IEEE Trans. Wirel. Commun. 2016, 16, 2450–2464. [Google Scholar] [CrossRef]
- Boshkovska, E.; Wing, D.; Ng, K.; Zlatanov, N.; Koelpin, A.; Schober, R. Robust Resource Allocation for MIMO Wireless Powered Communication Networks Based on a Non-linear EH Model. IEEE Trans. Commun. 2017, 65, 1984–1999. [Google Scholar] [CrossRef]
- Chu, Z.; Johnston, M.; Le Goff, S. Simultaneous Wireless Information Power Transfer for MISO Secrecy Channel. IEEE Trans. Veh. Technol. 2015, 65, 6913–6925. [Google Scholar] [CrossRef]
- Zhu, Z.; Chu, Z.; Wang, Z.; Lee, I. Outage Constrained Robust Beamforming for Secure Broadcasting Systems with Energy Harvesting. IEEE Trans. Wirel. Commun. 2016, 15, 7610–7620. [Google Scholar] [CrossRef]
- Khandaker, M.R.; Wong, K.K. Masked beamforming in the presence of energy-harvesting eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2015, 10, 40–54. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Schober, R. Secure and Green SWIPT in Distributed Antenna Networks With Limited Backhaul Capacity. IEEE Trans. Wirel. Commun. 2015, 14, 5082–5097. [Google Scholar] [CrossRef]
- Kalamkar, S.S.; Banerjee, A. Secure Communication via a Wireless Energy Harvesting Untrusted Relay. IEEE Trans. Veh. Technol. 2017, 66, 2199–2213. [Google Scholar] [CrossRef]
- Nasir, A.A.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. Secrecy Rate Beamforming for Multicell Networks with Information and Energy Harvesting. IEEE Trans. Signal Process. 2017, 65, 677–689. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Chu, Z.; Zhang, Y. Secure Transmission for Heterogeneous Cellular Networks with Wireless Information and Power Transfer. IEEE Syst. J. 2018, 12, 3755–3766. [Google Scholar] [CrossRef]
- Jiang, C.; Zhang, H.; Ren, Y.; Han, Z.; Chen, K.C.; Hanzo, L. Machine Learning Paradigms for Next-Generation Wireless Networks. IEEE Wirel. Commun. 2017, 24, 98–105. [Google Scholar] [CrossRef]
- Soltani, M.; Pourahmadi, V.; Mirzaei, A.; Sheikhzadeh, H. Deep Learning-Based Channel Estimation. IEEE Commun. Lett. 2019, 23, 652–655. [Google Scholar] [CrossRef]
- Huang, H.; Guo, S.; Gui, G.; Yang, Z.; Zhang, J.; Sari, H.; Adachi, H. Deep Learning for Physical-Layer 5G Wireless Techniques: Opportunities, Challenges and Solutions. IEEE Wirel. Commun. 2019, 27, 214–222. [Google Scholar] [CrossRef]
- Mashhadi, B.; Gündüz, D. Deep Learning for Massive MIMO Channel State Acquisition and Feedback. J. Indian Inst. Sci. 2020, 100, 369–382. [Google Scholar] [CrossRef] [PubMed]
- Hamamreh, J. Physical Layer Security Against Eavesdropping in The Internet of Drones (IoD) Based Communication Systems. 2019. Available online: https://figshare.com/articles/Physical_Layer_Security_Against_Eavesdropping_in_The_Internet_of_Drones_IoD_Based_Communication_Systems/8362385 (accessed on 3 March 2020). [CrossRef]
- Wang, H.M.; Zhang, X.; Jiang, J.C. UAV-involved wireless physical-layer secure communications: Overview and research directions. IEEE Wirel. Commun. 2019, 26, 32–39. [Google Scholar] [CrossRef]
- Li, A.; Wu, Q.; Zhang, R. UAV-Enabled Cooperative Jamming for Improving Secrecy of Ground Wiretap Channel. IEEE Wirel. Commun. Lett. 2018, 8, 181–184. [Google Scholar] [CrossRef]
- Huang, C.; Hu, S.; Alexandropoulos, G.C.; Member, S.; Zappone, A.; Yuen, C.; Zhang, R.; Di Renzo, M.; Debbah, M. Holographic MIMO Surfaces for 6G Wireless Networks: Opportunities, Challenges, and Trends. IEEE Wirel. Commun. 2019. [Google Scholar] [CrossRef]
- Lu, X.; Hossain, E.; Shafique, T.; Feng, S.; Jiang, H.; Niyato, D. Intelligent Reflecting Surface (IRS)-Enabled Covert Communications in Wireless Networks. arXiv 2019, arXiv:1911.00986. [Google Scholar]
- Zhang, J.; Björnson, E.; Member, S.; Matthaiou, M.; Wing Kwan Ng, D.; Yang, H.; Love, D.J.; Zhang, J.; Björnson, E.; Matthaiou, M.; et al. Prospective Multiple Antenna Technologies for Beyond 5G. IEEE J. Select. Areas Commun. 2020, 38, 1637–1660. [Google Scholar] [CrossRef]
- Black, E.J.; Commware, P. Holographic Beam Forming and MIMO. Available online: https://pivotalcommware.com/wp-content/uploads/2017/12/Holographic-Beamforming-WP-v.6C-FINAL.pdf (accessed on 18 May 2020).
- Pathak, P.H.; Feng, X.; Hu, P.; Mohapatra, P. Visible Light Communication, Networking, and Sensing: A Survey, Potential and Challenges. IEEE Commun. Surv. Tutor. 2015, 17. [Google Scholar] [CrossRef]
- Ghassemlooy, Z.; Popoola, W.; Rajbhandari, S. Optical Wireless Communications: System and Channel Modelling with MATLAB®; CRC Press: Boca Raton, FL, USA, 2017; pp. 1–514. [Google Scholar] [CrossRef]
- Lu, W.; An, K.; Liang, T. Robust Beamforming Design for Sum Secrecy Rate Maximization in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2019, 55, 1568–1572. [Google Scholar] [CrossRef]
- Lei, J.; Han, Z.; Vázquez-Castro, M.A.; Hjørungnes, A. Secure Satellite Communication Systems Design with Individual Secrecy Rate Constraints. IEEE Trans. Inf. Forensics Secur. 2011, 6, 661–671. [Google Scholar] [CrossRef]
- Kalantari, A.; Zheng, G.; Gao, Z.; Han, Z.; Ottersten, B. Secrecy analysis on network coding in bidirectional multibeam satellite communications. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1862–1874. [Google Scholar] [CrossRef]






















Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sanenga, A.; Mapunda, G.A.; Jacob, T.M.L.; Marata, L.; Basutli, B.; Chuma, J.M. An Overview of Key Technologies in Physical Layer Security. Entropy 2020, 22, 1261. https://doi.org/10.3390/e22111261
Sanenga A, Mapunda GA, Jacob TML, Marata L, Basutli B, Chuma JM. An Overview of Key Technologies in Physical Layer Security. Entropy. 2020; 22(11):1261. https://doi.org/10.3390/e22111261
Chicago/Turabian StyleSanenga, Abraham, Galefang Allycan Mapunda, Tshepiso Merapelo Ludo Jacob, Leatile Marata, Bokamoso Basutli, and Joseph Monamati Chuma. 2020. "An Overview of Key Technologies in Physical Layer Security" Entropy 22, no. 11: 1261. https://doi.org/10.3390/e22111261
APA StyleSanenga, A., Mapunda, G. A., Jacob, T. M. L., Marata, L., Basutli, B., & Chuma, J. M. (2020). An Overview of Key Technologies in Physical Layer Security. Entropy, 22(11), 1261. https://doi.org/10.3390/e22111261





