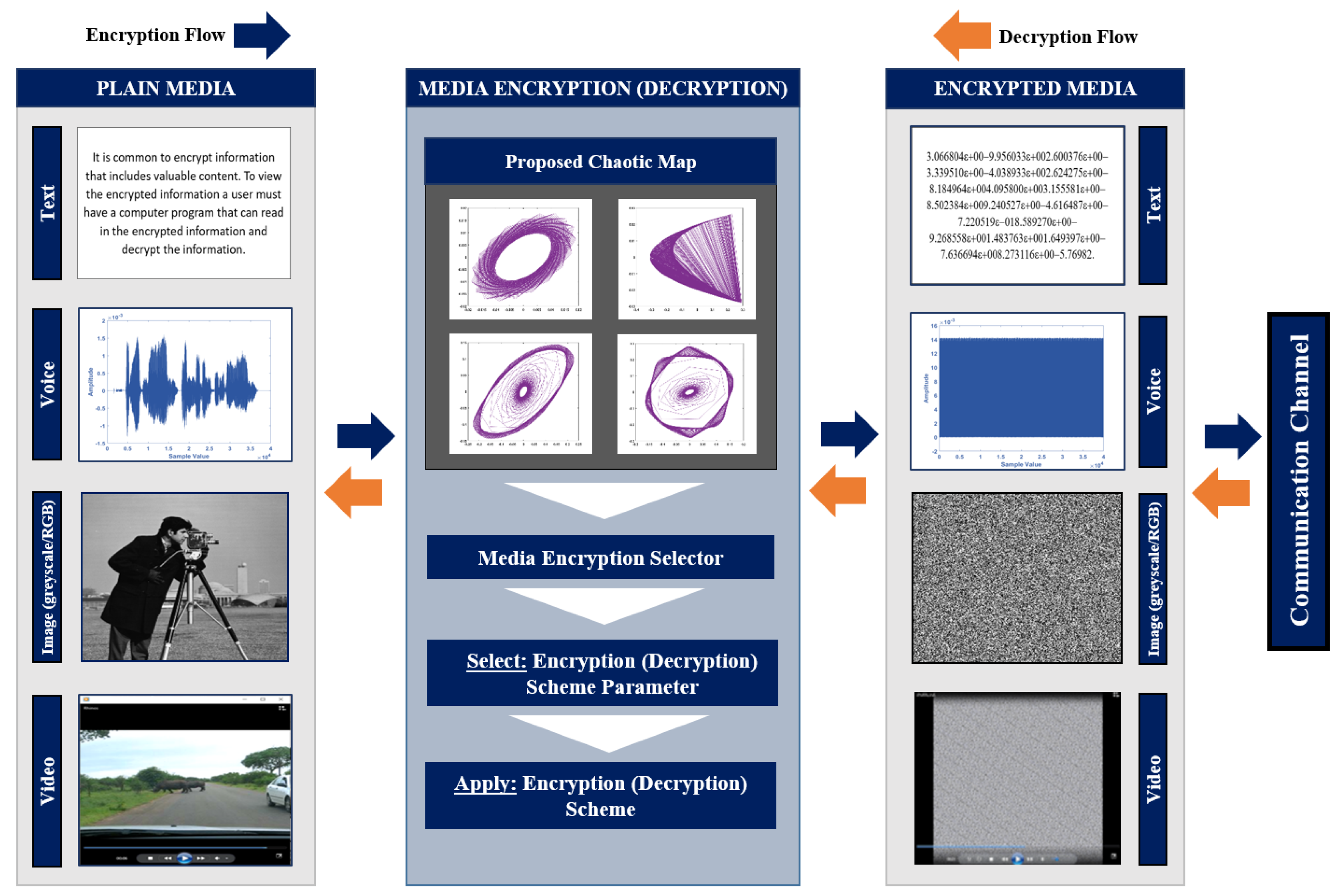
1. Introduction
Rapid and increased growing of multimedia data exchange over open networks and the Internet necessitates reliable and robust security means to provide confidentiality and to prevent unauthorized access to the transferred content. Among several solutions is the employment of data encryption [
1]. Encryption sachems are algorithms that modify data (such as text, image, sound, etc.) so that they are unreadable, invisible or impenetrable during transmission. Nowadays, data encryption plays an immense role in various applications and various encryption schemes have been developed with the ultimate goal to protect sensitive data by increasing its security and confidentiality [
2].
Most of the research work aims at providing improved encryption quality, less execution, and security robustness against attacks. Compared with traditional encryption schemes, chaos-based schemes have demonstrated outstanding performance with proven ability of increased security and privacy needed by utilizing variable keys [
3,
4,
5,
6,
7]. The basis is to use many components of chaos to decorate confusion and diffusion abilities of a given scheme [
8]. In literature, chaos-based encryptions span a wide spectrum of multimedia types, i.e., text, audio, image, and video. Next, an overview of the recent literature work on a chaotic maps-based multimedia encryption application is provided.
Chaotic maps have been utilized by several groups for textual content encryption. In particular, Ekhlas et al. [
9] proposed a textual content-encryption approach based on block cipher and chaotic maps. Their algorithm encrypted/decrypted an 8 × 8 bytes block primarily based on permutation and substitution the byte in S-box. Although their method employs large key space, it demonstrated low entropy and low security. A symmetric text cipher set of rules based totally on chaos was proposed by Murillo et al. [
10]. Their scheme combined a mystery key of 128-bit length, optimized logistic maps with pseudo-random sequences, plain text characteristics, and optimal permutation diffusion spherical. The method demonstrated fast encryption speed; however, it has a small parameter space. Volos et al. [
11] devised a textual content encryption process that is realized with a chaotic pseudorandom bit generator. The latter is based on two logistic maps with specific preliminary conditions and system parameters, running facet-by way of-side. The main advantage of the method in [
11] is its simple realization using the X-OR function in the bit sequences.
Speech cryptography literature has recently shown an increased utilization of chaos theory as well. For example, a speech cryptographic method -based on a combination of permutation and substitution of speech samples using a chaotic Zaslavsky map was developed by Yousif et al. [
12]. Their scheme demonstrated high-security features with low correlation. Jawad et al. [
13] presented a two-level chaotic verbal encryption exchange system. Namely, a chaotic scrambling and protecting. Their algorithm provided stronger encryption with a very long key space; however, the scheme complexity was very high. Mahdi et al. [
14] presented a voice chaotic-based protection model. Their technique utilized digital scrambling, using a duffing map, in which each speech sample is divided into eight bits. Similar to [
13], the algorithm has a longer key space, but it showed reduced security performances.
On the other hand, chaotic-based image encryption has been investigated thoroughly in literature. For example, Wang et al. [
15] offered a picture encryption technique utilizing hash function and cyclic shift. First, mask and diffusion operations were employed to exchange the pixel’s values. The final vicinity and value of pixels are altered by a bit cycle shift. Resistances to common attacks was the characteristic advantage of the method proposed in [
15]. Wu et al. [
16] introduced a photo encryption technique based totally on two-dimensional (2D) chaotic maps generated through the combining Henon and Sine maps. Amina et al. [
17] proposed a new chaotic cipher approach specialized for medical images. Their technique included two stages: pixel diffusion and chaotic confusion. Both the methods in [
16,
17] reported less encryption/decryption time; however, they also exhibit reduced compression capabilities. Another scheme was developed by Lou et al. [
18] to shield picture contents while transferred over the internet. Their approach utilized Deoxyribonucleic Acid (DNA) approach and a 2D Henon-Sine map (2D HSM) for pixels’ diffusion and permutation. Although their method demonstrated low entropy analysis, it was highly compressible. Alwadi et al. [
19] proposed a fast and hybrid system that cascades and combines chaotic maps. However, their method showed low robustness against some attacks. Yousif et al. [
6] developed an encryption framework that utilizes a bank of chaotic maps, from which a correlation-based criterion is employed to select the candidate map for encryption. Their correlation analysis used all image pixels compared with literature schemes, which randomly chose a predefined number of neighboring pixel pairs (≈1000). Due to the nature of the initial map selection, their approach is more efficient for image encryption.
Video encryption has been also explored by various researchers. Particularly, Ganeshkumar et al. [
20] provided a three-level chaos-video cryptosystem. They employed permutation and diffusion rounds, where the preliminary encryption parameters are obtained using a combination of logistic and tent (LTS) maps. Their method showed good time competency; however, compression reduction was its drawback. Valli et al. [
21] presented video encryption pipeline that utilized S-Box and has two alternative schemes. The first is a higher-dimensional (i.e., 12D) chaos structure, and the second uses the Ikeda Delay Differential Equation (DDE). The latter was designed for real-time video encryption. The main limitations of their method are the increased encryption time and key complexity.
The overview of the related work revealed that chaotic systems have been exploited for efficient for multimedia data encryption. Traditional chaos-based cryptographic systems may be effective for text data; however, they fail in providing the same security level for the voice data. This is mainly due to the high redundancy and bulk data capacity of voice signals. Also, some chaos-based image encryption methods have security liabilities, such as resistance to chosen–plaintext attack, sensitivity to chaotic secret keys, the first pixel in the cipher image cannot be correctly restored, and there are additional restrictions on parameters selection for the inverse rectangular transform system.
To partially overcome the above-stated limitations and security defects, the work presented in this manuscript proposes improved multimedia encryption algorithms utilizing 2D alteration models. The main contributions of this work are: (i) novel multiple chaotic maps that depict high chaotic behavior for all parameter settings (i.e., different control parameter selections will lead to optimal chaotic behavior as no single chaotic region outperforms the others); (ii) perturbation-based data encryption are employed in both the confusion and diffusion rounds to outdo deficiencies of traditional architectures; (iii) the proposed chaotic techniques have high sensitivity to any change in its initial conditions, in addition to the other properties such as random behavior, ergodicity, and the long periodicity; (iv) the proposed chaotic systems combine both faster and secure encryption/decryption compared to conventional literature systems; (v) our pipeline is a comprehensive multimedia (textual content, voice, image, and video) security system.
The remainder of this paper is prepared as follows. In
Section 2, the proposed scheme of multimedia security machine is clearly defined and the proposed chaotic maps of the cryptosystems are detailed. In
Section 3, quantitative performance measurements that are used for evaluation are provided. Experiments and the associated results of the proposed cryptosystem, the comparisons with other well-known approaches, and security analysis results are detailed and discussed in
Section 4. Eventually, the concluding remarks and venues for future research are given is
Section 5.
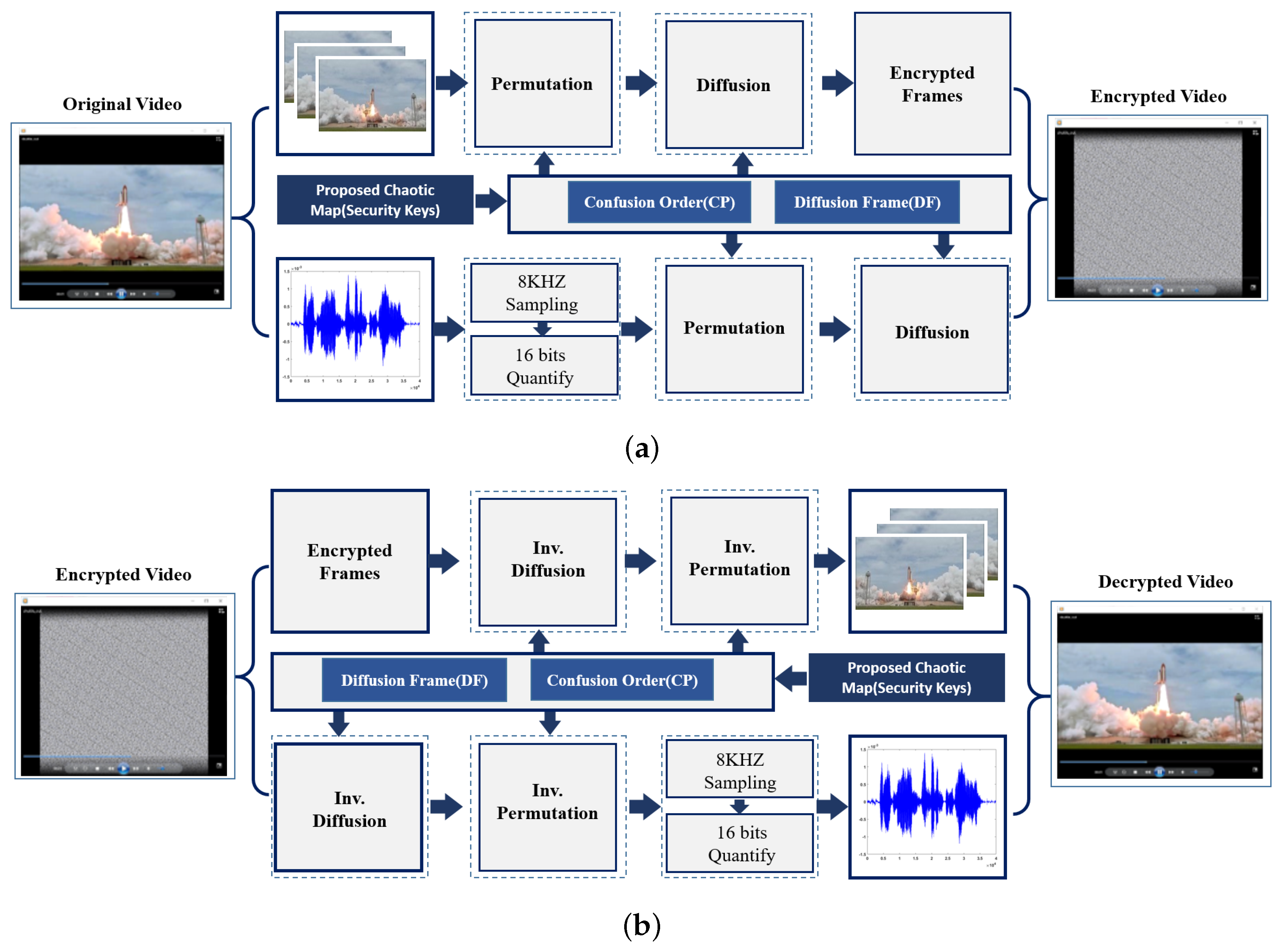
4. Experimental Results and Discussion
Most encryption schemes are evaluated using measurable examinations to quantify a relation between both encrypted and original media. All of our simulation experiments have been conducted using MATLAB R2017a programming environment running on a Windows 7 machine, with the following specification: core i5-2400, 4 GB RAM, and a 160 GB Hard Disk Drive (HDD). All simulations/tests have been conducted more than one time. Reported times represent the average elapsed time of all trials. Comparisons with other state-of-the-art literature schemes have been conducted and evaluation of the comparative results are assessed using the above-mentioned metrics.
4.1. Text Simulation Results
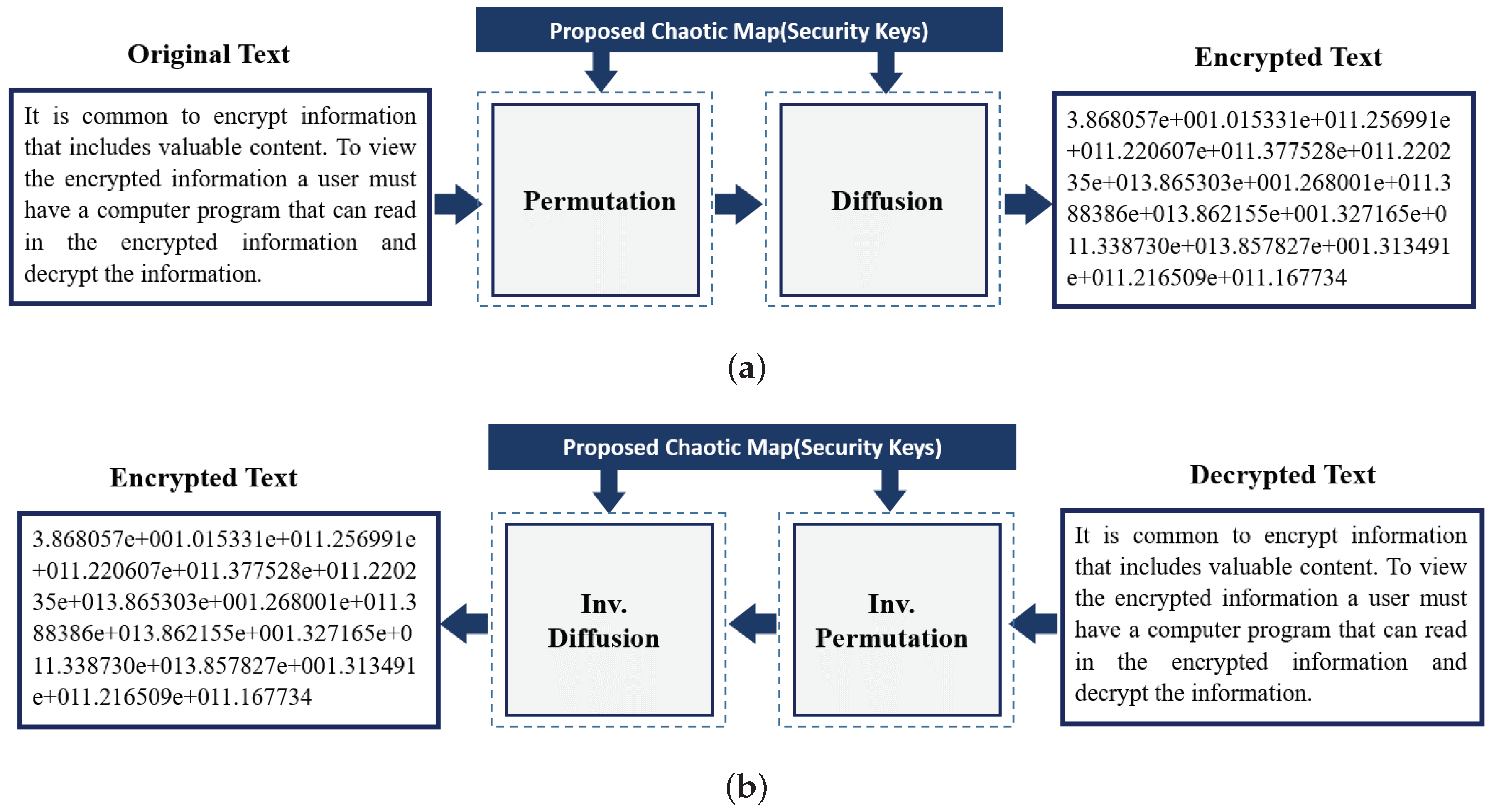
The encrypted text is obtained with the help of the nonlinear function presented in Algorithm 2 and it is sent to the communication channel. For the decryption, the data obtained from the communication channel is transferred to the chaos generator and the inverse of the nonlinear function. Correct decryption is achievable if the chaos generator used for both encryption and decryption is the same.
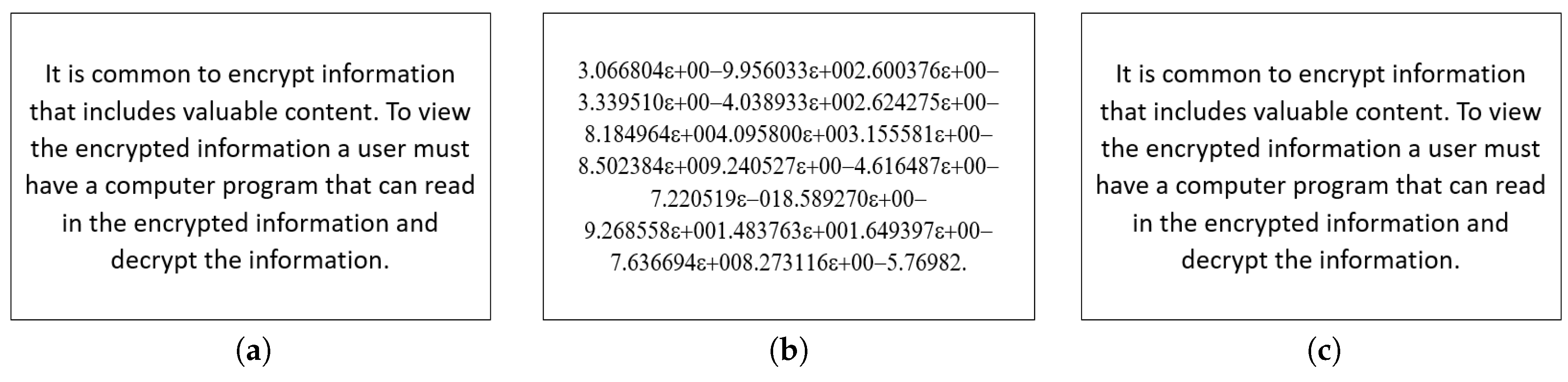
For the encryption, the plaintext in the
Figure 3 is used. In
Figure 7b, the encrypted text whose cipher is generated with the aid of the usage of proposed maps is shown. The decrypted text with the aid of inverting the nonlinear equation and with the assist of chaos generator is shown in
Figure 7c. It is worth mentioning that the average processing time for our text encryption/decryption scheme is 20 msec (1.6 MB/sec).
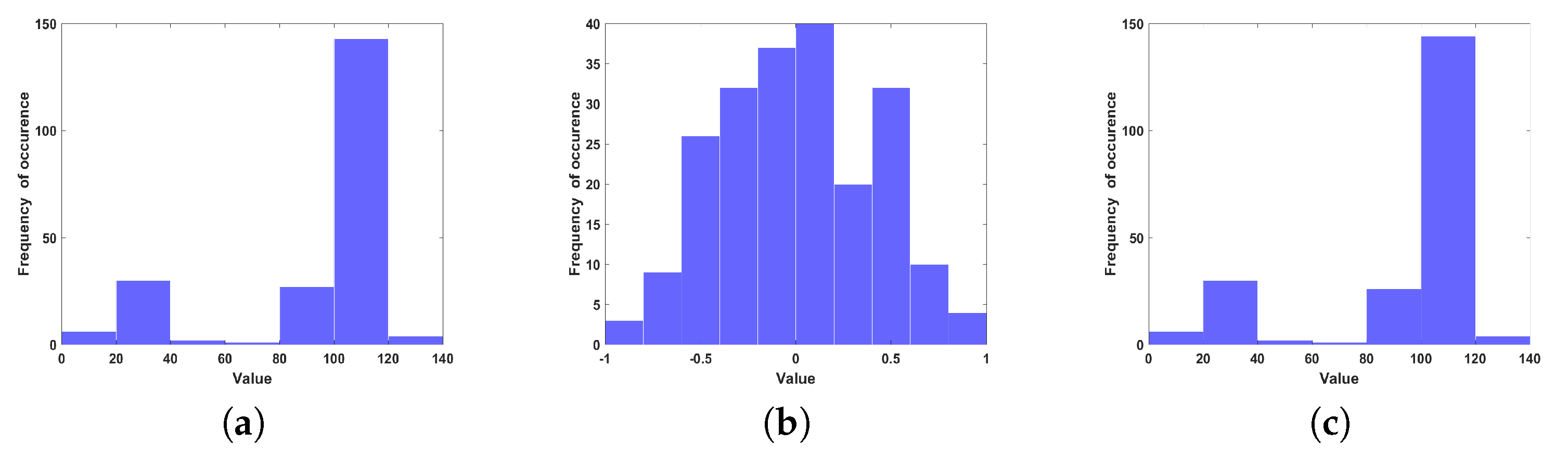
The statistical analysis of the plaintext and the encrypted version can be evaluated by histogram analysis. The histogram can offer information to find the plaintext, the secret key, or both. Just in case that the histogram content is reasonably equally circulated over the scale, no data about the plaintext can be accumulated through histogram examination. The histogram of the plaintext characters and the cipher text are shown in
Figure 8a,b, respectively. As can readily seen, the cipher text histogram is uniform, so the proposed scheme is powerful against histogram attacks in addition to frequency attacks.
In addition to visual evaluation using histogram analysis,
Table 1 summarizes the results of NPCR and UACI metrics for the proposed approach compared with other literature techniques. As demonstrated in the table, our scheme has achieved average values of 99.33%, and 33.42% for NPCR and UACI, respectively, which documents that the proposed algorithm is robust against differential attacks.
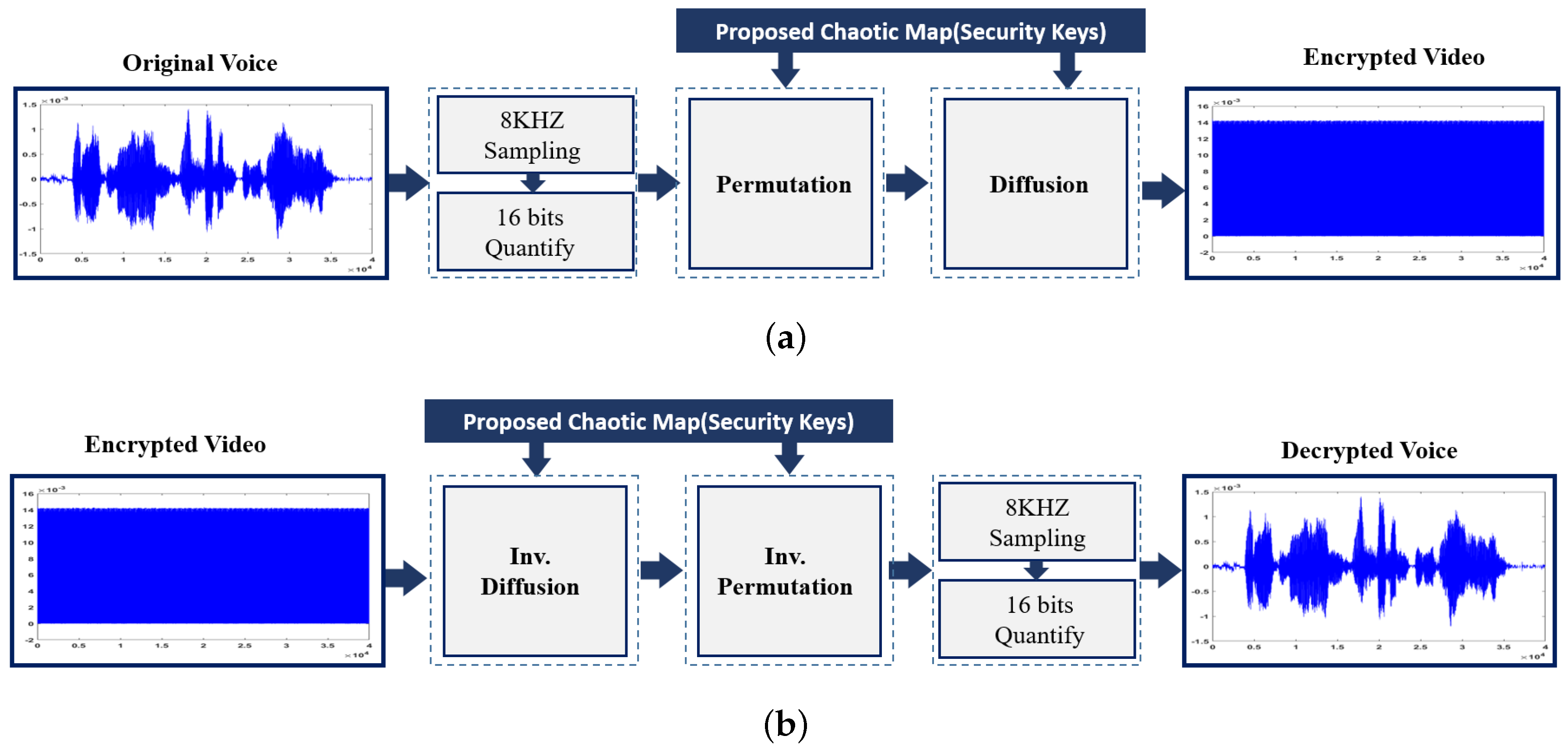
4.2. Voice Simulation Results
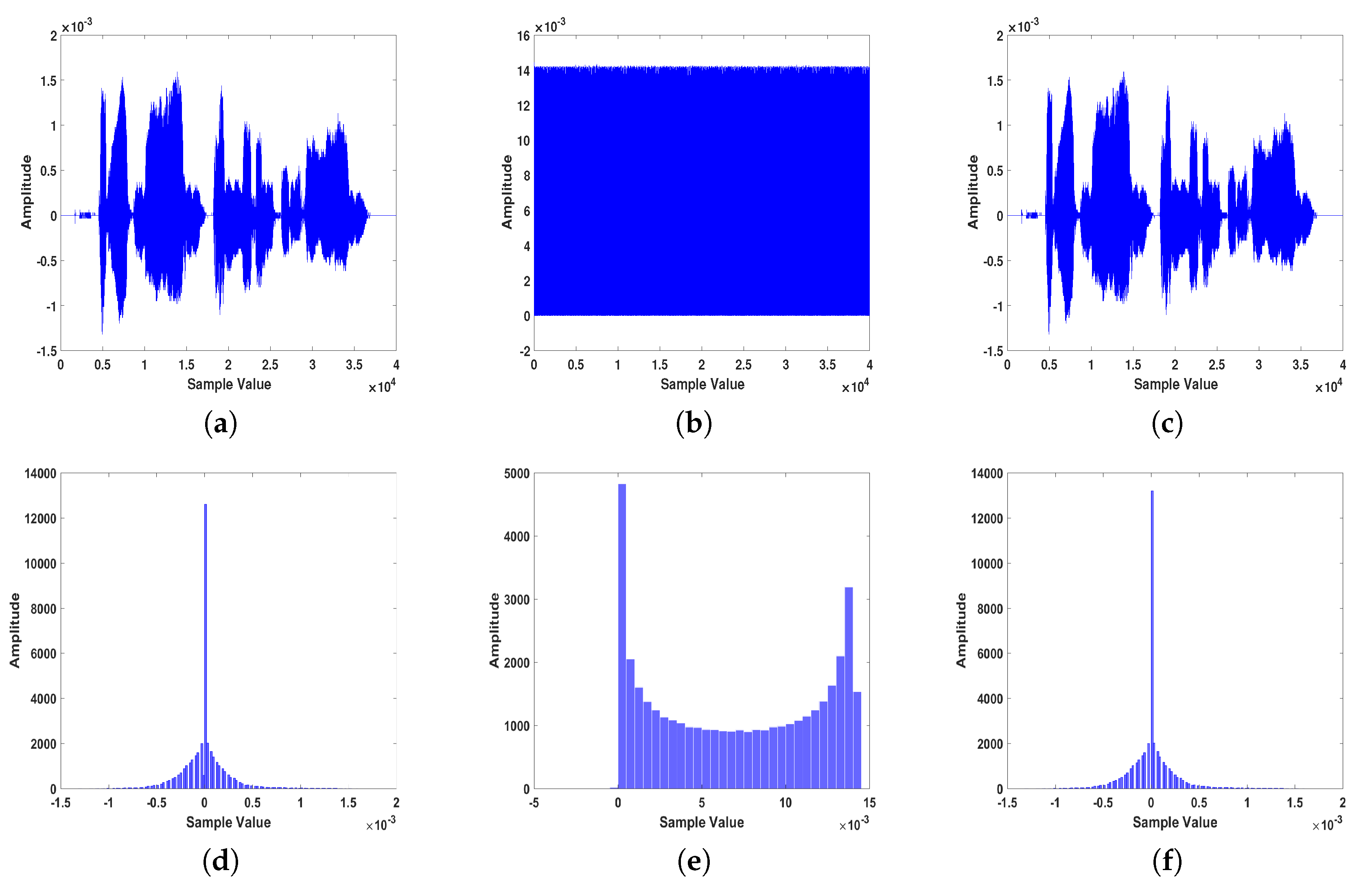
An example of voice simulation results using a voice block is shown in
Figure 9. The voice file used in this experiment has a total length of 5 sec with a sampling frequency of 8 KHz (i.e., 40,000 samples), and an 8-bit/sample. The performance of the proposed voice system is conducted using several metrics. For example, distributions of data histogram is one of the tools used in many different fields. In encryption practices, if the distributions of numbers that represent encrypted data are close, this means encryption has been performing well. Namely, the closer the encrypted data distributions are, the higher their encryption level. The second row in
Figure 9, shows the distribution versus sample value for our voice encryption approach. To statistically analyze our results, different measures that were described in
Section 3), are also used for quantitative evaluation.
Table 2 shows the average values of those metrics for the sample audio files analyzed using the proposed technique. In terms of processing time, the proposed scheme takes about 325 msec (2.16 MB/sec) for encryption or decryption stages.
Moreover,
Table 3 shows the quantitative comparison between the proposed scheme and state-of-the art literature voice encryption methods. As readily seen in the table, the encryption methods that use chaos outperform the traditional methods. In fact, the proposed two-level encryption scrambling scheme: scrambling and masking gives the best encryption results. The SSSNR of the main level (confused scrambling) is decreased by −7.028 dB (from 0.8823 to −6.1457) dB as contrasted with time-domain scrambling. In the subsequent level (chaotic diffusion), the SSSNR is diminished by −21.248 dB (from 0.8823 to −20.3657) dB. It additionally shows that when the two levels are consolidated, the general decrease is −26.1478 dB (from 0.8823 to −25.2655) dB. Furthermore, the key space of the proposed method is much greater than other traditional methods. The spectrograms in
Figure 10 of the original and encrypted speech signals show that these two signals are quite different from higher encryption quality.
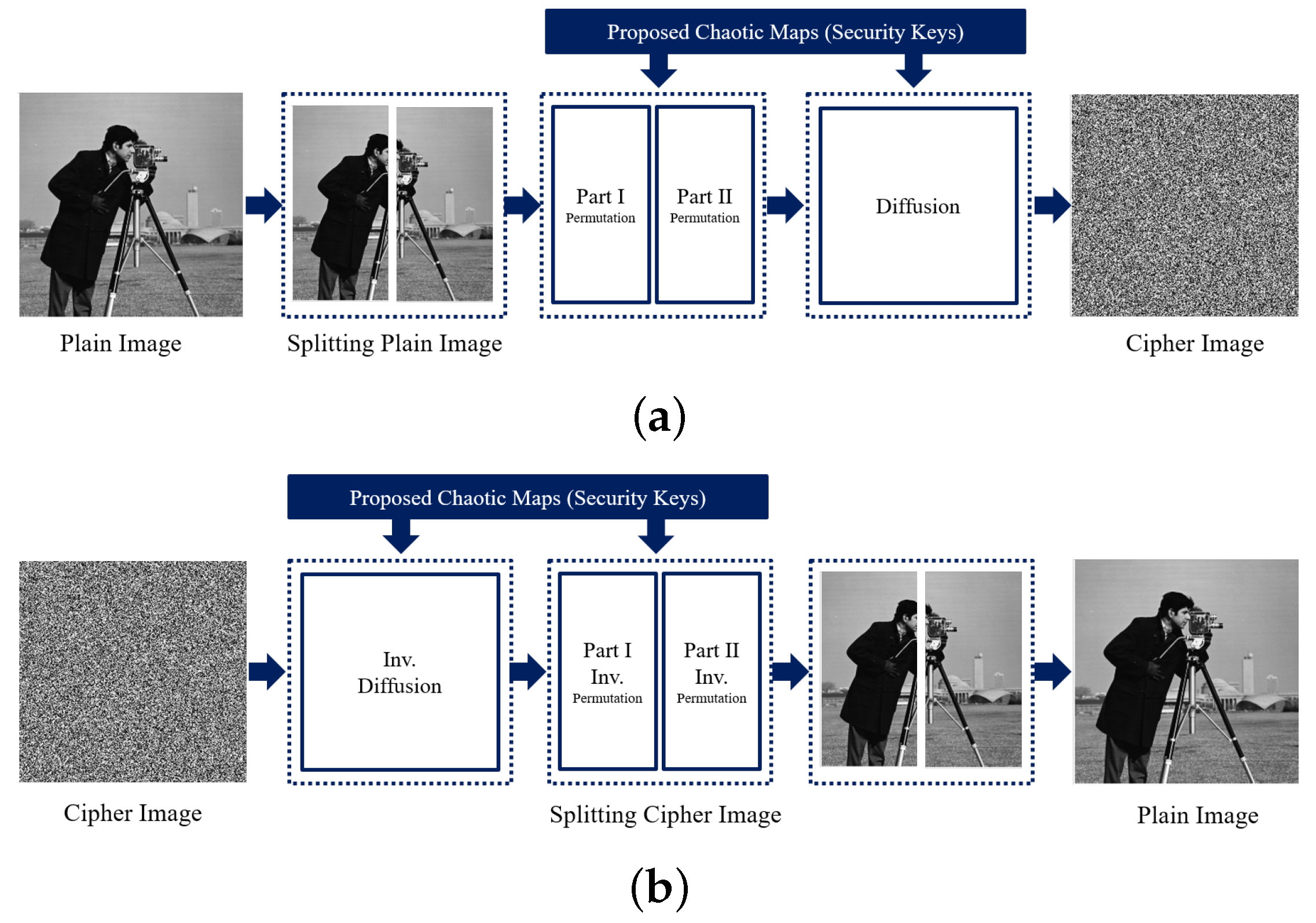
4.3. Image Simulation Results
Sample example of the image encryption and decoding processes are depicted in
Figure 11. Four reyscale images were utilized to test the proposed scheme: Lena, Cameraman, Baboon, and Pepper. The simulation results showed that the cipher images are so boisterous in a way that any data from them cannot be obtained.
Table 4 summarizes the evaluation metrics for all test images. To visually evaluate our image encryption scheme, the histogram analysis is conducted. As outlined above, the nearer the distribution numbers that represent encrypted data, the better the encryption level is. The histogram for a sample image is shown in the second row of
Figure 11.
The proposed encryption employments distinctive midpoints when scrambling individual input images. This, in turn, can remarkably increase the algorithm resistance to unknown or chosen attacks and differential assaults, which is a desired characteristic of cryptanalysis and secure encryption schemes. For an image encryption algorithm, NPCR bounded with UACI can measure its capacity of standing up to the differential attack. The security performance of the proposed algorithm has been conducted and compared with several state-of-the-art literature. The results can be observed in
Table 5. By differentiate, the UACI (>33%) and NPCR (>99%) values obtained by our approach are very close to the perfect standard, which proves the exceedingly sensitive for our scheme for resisting differential attacks. For decryption, utilizing the proper secret keys only can correctly restore plain images from the decoded ones. The simulation results also infer that small changes made to the plain image will produce completely different images even if there’s only one bit of change between the two plain images. Additional advantage of our method is that the encryption and decryption steps take about 242 msec (1.57 MB/sec).
In addition to histogram and differential attack analyses, other well-known security analyses can be performed to support the effectiveness of a given scheme. Those analyses can be applied to any data encryption schema, however, image encryption is the most common application. Thus, we have conducted other security tests for our image encryption algorithm: key space and sensitivity, and correlation analysis.
The key space defines all-out number of various keys, which can be utilized in the encryption scheme. The proposed calculation comprises two procedures; permutation and diffusion. For permutation step, the proposed four maps are exploited with autonomous factors , , a, b and for the split image and combination vector. For diffusion stage, the clench hand proposed map has independent variables , , a, b and . In the key identified with the plain content algorithm, we have a consistent whole number . Thus, the key space is . Since , , a, b and are two-fold accuracy numbers, their absolute number of various qualities is greater than 1014. Thus, the key space is bigger than = 280,375,465,082,880 combinations of secret keys. This huge key space is sufficient to resist brute-force attacks.
Key sensitivity is one of the most important features of chaos encryption. A small change in the key lead to different results during decryption, i.e., encrypted data cannot be decrypted even if only one parameter has been changed. It is also mandatory to know keys order, otherwise, the data cannot be decrypted without knowing all the keys as decryption does not happen in the correct order.
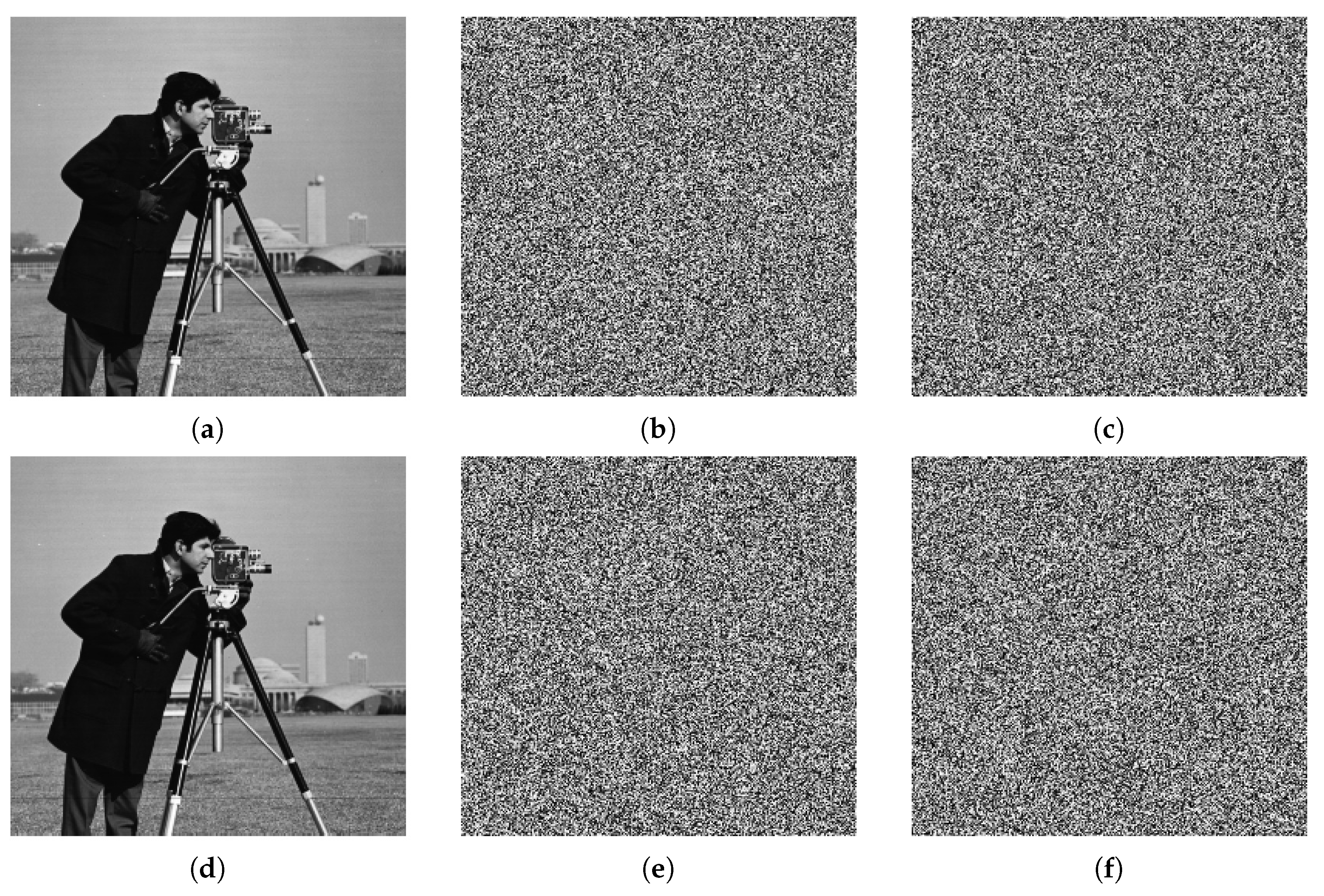
Figure 12 shows encrypted images using different encrypted keys. The second row of
Figure 12 demonstrates the decrypted images.
Figure 12d shows the decrypted image using the same keys of correct encrypted image in
Figure 12a. On the other hand,
Figure 12e,f show illegal decrypted images when error/wrong keys are used. The results document that the decrypted images are all unrecognized, i.e., the original image cannot be recovered unless the correct key is used. A small change will not produce correct decryption results. Therefore, the proposed encryption algorithm has a high key sensitivity.
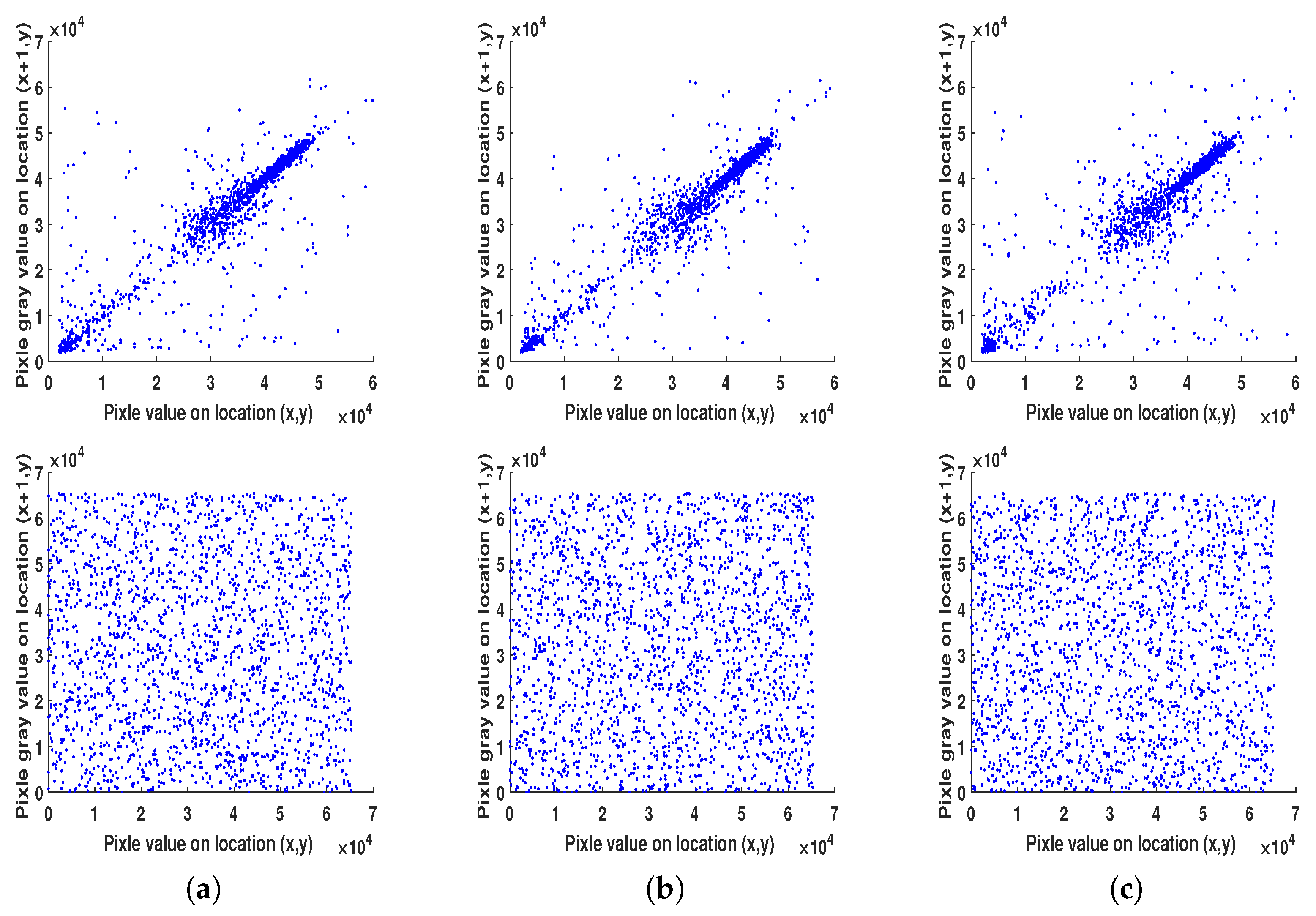
Another security evaluation is correlation analysis. This type of analysis visually shows the distribution between the adjacent pixels of both the original and encrypted images. Normally, plain images should exhibit strong correlations for its adjacent pixels, while the cipher images hardly have correlations for the adjacent pixels.
Figure 13 demonstrates the obtained correlations in horizontal, vertical and diagonal directions for both original and encrypted images. As expected, the correlations between the adjacent pixels are very high in the original image and very low in its encrypted version in all three directions. Numerically,
Table 6 summarizes the average correlation coefficients in all three directions for both plain and encrypted images. According to the results, our algorithm achieves good encryption in terms of the correlation degree of adjacent pixels (
R values of the plain images are closer to “1” while those of the cipher images are closer to “0”), thus documenting that the proposed encryption algorithm has good confusion and diffusion properties.
4.4. Video Simulation Results
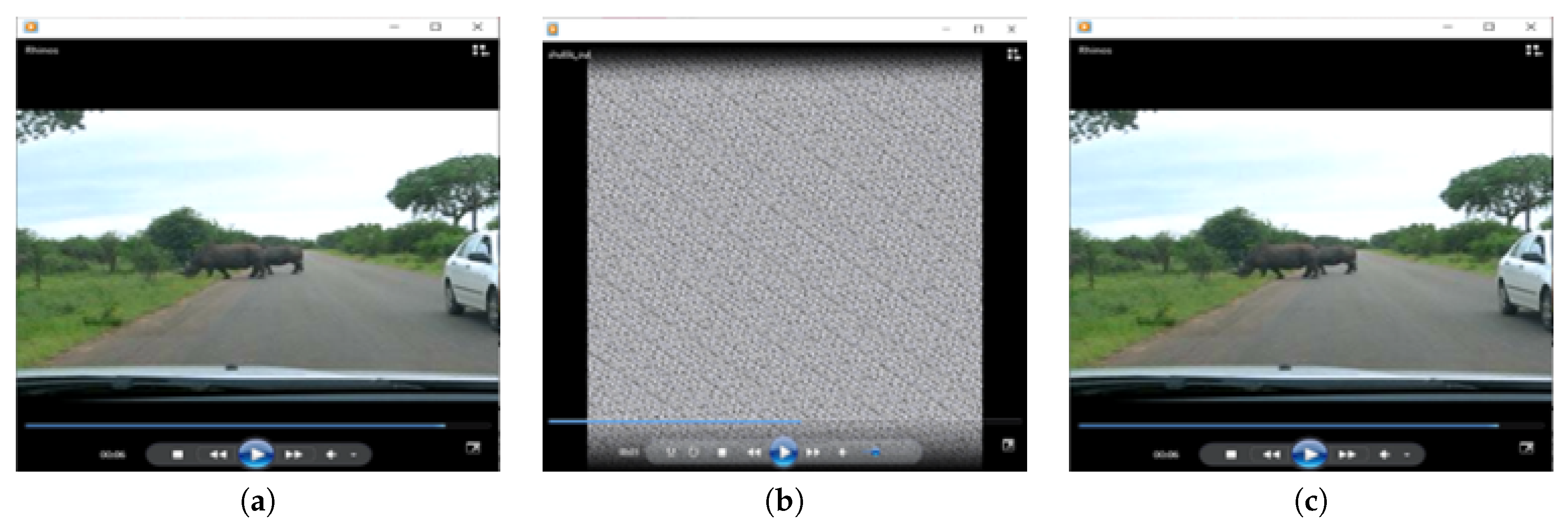
The proposed video encryption scheme is used to encrypt video data, frame by frame, without considering the selective region of interest. Input color videos considered are Rhino.avi, Flamingo.avi, Train.avi, and Viptrain.avi. A one-second test video consisting of 15 frames is chosen for testing the performance of the proposed video encryption scheme and the sample video frame is shown in
Figure 6. An encrypted video frame using Algorithm 5 is shown in
Figure 14, which shows that the encrypted frames are unintelligible, having good perceptual security.
Differential attack refers to the method of finding out a meaningful relationship between plain and encrypted video frames by making a slight change in the pixel value of the encrypted video frame and observing its effect. If a slight change in the plain video frame results in a significant change in the cipher frame with respect to diffusion, then this encryption scheme can resist differential attack effectively.
Table 7 measures the video simulation comparing the proposed approach with other literature methods.
In addition to NPCR and UACI quantitative measures, we also quantified our method based on encryption speed. In real-time the speed of encryption plays a vital role. If the time taken to encrypt/decrypt the data is high then the method may not be suitable for some applications like video conferencing, live streaming etc., The proposed method spends 1 second for creating the necessary parameters for the maps to be used and the time required to encrypt (decrypt) the test video data is about 408 msec (2.15 MB/sec). The time required to generate the keys is a one-time operation, so the proposed scheme provides a good competency as compared to its similar methods.
5. Conclusions
Multimedia encryption tools have become an integral part of secure and confidential data transfer over opened-nature wired or wireless communication channels. In this work, a hybrid-chaotic multimedia encryption/decryption pipeline has been proposed, which is based on novel 2D dynamical chaotic maps. The control parameters of both permutation and diffusion structure are generated by a combination of the proposed maps. Moreover, the ciphers are generated with different chaos generators for encryption and decryption and the performance analysis is conducted between these chaos generators. One of the advantages of the proposed system is its comprehensiveness in encoding all types of media (e.g., text, images, speech and video) compared with a single-secure data application. Other advantages of our system pertain to specific multimedia types. Particularly, we have presented a novel symmetric text encryption algorithm that uses plain text characteristics to resist a chosen or known plain text attack. Our proposed speech cryptosystem provided high-security features and low correlation between the original and encrypted speech signals. Moreover, the proposed image encryption/decryption scheme not only applicable for greyscale and color images but also it takes a very short time, which makes it suitable for today’s fast communication. Furthermore, the proposed video encryption possesses the ability to deal with more redundant data from the frame by frame, while providing good complexity and stability for secure encryption. In total, simulation experiments and evaluation statistics have shown that the proposed chaotic systems are faster and secure encryption/decryption of several data types with less computation as compared to conventional systems; practical in key handling; and can be implemented in real-time applications. Despite the advantages of our research, it is; however, limited in the availability of data making it difficult to process due to the limited hardware availability. Inter-operability, data processing, CPU management, memory and disk resources, and big data issues are still weaknesses in architectures that require a large number of heterogeneous devices such as Fog computing applications. There are a few research venues that are still open for future research and investigation. This includes the randomization of key choice handle, the expansion of the number of offers superimposed for increased layers’ of security; and the integration of other sorts of chaotic maps to improve the encryption handle. Another research avenue is the integration/utilization of the proposed schemes in fog applications. Generally, those applications are motivated by the desire for functionality and end-user requirements, while the security aspects are often ignored or considered as an afterthought. The impact of those security issues and possible solutions, providing future security-relevant directions will be determined for designing, developing, and maintaining fog systems.