Abstract
Herein, we focus on energy efficiency optimization for massive multiple-input multiple-output (MIMO) downlink secure multicast transmission exploiting statistical channel state information (CSI). Privacy engineering in the field of communication is a hot issue under study. The common signal transmitted by the base station is multicast transmitted to multiple legitimate user terminals in our system, but an eavesdropper might eavesdrop this signal. To achieve the energy efficiency utility–privacy trade-off of multicast transmission, we set up the problem of maximizing the energy efficiency which is defined as the ratio of the secure transmit rate to the power consumption. To simplify the formulated nonconvex problem, we use a lower bound of the secure multicast rate as the molecule of the design objective. We then obtain the eigenvector of the optimal transmit covariance matrix into a closed-form, simplifying the matrix-valued multicast transmission strategy problem into a power allocation problem in the beam domain. By utilizing the Minorize-Maximize method, an iterative algorithm is proposed to decompose the secure energy efficiency optimization problem into a sequence of iterative fractional programming subproblems. By using Dinkelbach’s transform, each subproblem becomes an iterative problem with the concave objective function, and it can be solved by classical convex optimization. We guarantee the convergence of the two-level iterative algorithm that we propose. Besides, we reduce the computational complexity of the algorithm by substituting the design objective with its deterministic equivalent. The numerical results show that the approach we propose performs well compared with the conventional methods.
1. Introduction
With the great development of network information technology and the continuous improvement of wireless communication technology, modern society puts forward higher requirements for the current communication transmission. With the extensive amount of research, there are a number of breakthrough technologies, such as the multiple-input multiple-output (MIMO) technology [1]. This technology has great potential to improve both the spectrum efficiency and the energy efficiency of the system, which is the development direction of future 5G/B5G wireless communication systems [2,3]. In the long-term evolution (LTE) standard, the wireless multicast transmission is also widely studied. In wireless multicast transmission, one base station (BS) sends public information to multiple user terminals (UTs). That is to say, that the BS can effectively transmit group-oriented signals by utilizing an evolved multimedia broadcast multicast service (eMBMS) [4,5,6,7,8]. As a mature technology, wireless multicast technology has certain advantages in improving the network traffic and reducing the communication cost. The combination of wireless multicast and massive MIMO is widely concerned with improving the quality of service (QoS), owing to its performance of effectively shaping the multicast transmission signals [9,10,11,12].
Due to the openness of the wireless propagation media, security issues are critical indicators in wireless transmissions of all fields. To ensure the security of transmission, many works traditionally use key-based enciphering. However, this method meets its challenge for secure wireless communications with additional control signaling and feedback channel management. Therefore, the security and privacy of physical layer security in wireless channels have a wide range of research [13,14,15], thanks to its great ability to work in a keyless scenarios. In previous works, the physical layer security of massive MIMO unicast transmission has been studied [16,17,18,19]. Meanwhile, in some existing works, the physical layer security of multicast transmission is also considered. For example, secure multicast precoding has been investigated [20,21,22]. Besides, some works have studied the security by introducing artificial noise into the multicast transmission, e.g., in [23,24].
Energy efficiency is another important indicator of performance in designing wireless transmission, which has been widely concerned by both academia and industry [25,26]. About 5% of the energy consumption of the whole world is produced by information and communication technologies, owing to its connected devices and infrastructure constantly being consumed [27]. In the future of 5G/B5G development, energy demand will soon become unmanageable. Therefore, a promising answer to this issue is to find considerable metrics which can limit energy consumptions but meet the needs of secure and reliable communication. However, most of the works on secure multicast transmission are limited to optimizing the secure rate, and almost no energy efficiency issues are considered. Some existing works have investigated the energy efficiency of unicast transmission instead of multicast transmission [28,29,30]. In some previous works, the energy efficiency multicast transmission was investigated [31,32], but the issues of security were not solved well.
In some works, it is assumed that the legitimate UTs’ instantaneous channel state information (CSI) is known [17,21,22,23,33]. However, due to CSI’s capture/feedback overhead in frequency division duplex MIMO systems, there are some difficulties in obtaining instantaneous CSI at the BS. It is the reason why most of the previous work has assumed this. On the other hand, statistical CSI has enormous advantages over instantaneous CSI for BS to obtain. Because of its slower change, BS can get statistical CSI accurately [34]. Therefore, statistical CSI is more suitable for wireless transmission design in high mobility scenarios. Besides, as a vast antenna array with high spatial resolution, massive MIMO channel typically exhibits new statistical characteristics [35,36].
We study the energy efficiency of massive MIMO secure multicast transmission with the assumption that only the statistical CSI of legal UTs and the eavesdropper can be obtained at the BS. We summarize the contributions of the current paper as follows.
- We first considered a secure multicast transmission scenario, in which the BS can only obtain the statistical CSI of the legitimate UTs and eavesdropper, and formulate our energy efficiency maximization problem. A tight lower bound rate of secure multicast is presented to simplify the optimization objective. Therefore, our problem is transformed into finding the optimal solution of this equivalent problem.
- Via making the transmit signaling directions into a closed-form, we simplify the energy efficiency optimization of matrix-valued strategy design to a beam domain power allocation problem, reducing the optimization variables significantly.
- By invoking the Minorize–Maximize (MM) method and Dinkelbach’s transform, we propose a two-level iterative algorithm to solve the equivalent problem. In the outer iteration, we decompose the original problem into several fractional programming subproblems, where the numerator is concave and the denominator is linear. In the inner iteration, we introduce related variables to remove the denominator and transform each subproblem into a common convex optimization problem to obtain the optimal solution of the equivalent problem. Our simulation results reveal that this solution is almost equal to the original problem.
- According to the large-dimensional random matrix theory, we use the deterministic equivalent of the secure transmit rate instead of massive sample averaging to reduce the computational complexity, which is proved to be almost the same as the original result.
The rest of this paper is arranged as follows. Section 2 presents the massive MIMO channel model. In Section 3, we divide the algorithm into three parts. The energy efficiency of secure multicast transmission is investigated. The optimal energy efficiency multicast transmit covariance matrix is decomposed into eigenvectors and eigenvalues as pretreatment. We propose an iterative algorithm for some fractional programming subproblems. Each subproblem is also solved by the inner iterative algorithm of sequential beam domain power allocation. The last part is to simplify the complexity of the problem. In Section 4, numerical simulation results are given. Finally, we summarize the full work in Section 5.
In our work, the use of symbols is also an important part. The main adopted symbols are as follows.
- denotes dimensional complex-valued vector space and denotes dimensional real-valued vector space.
- denotes the th element of matrix .
- det denotes the matrix determinant operation, tr denotes the matrix trace operation, and diag denotes the diagonalization of the matrix, respectively.
- denotes the expectation operation and denotes max.
- , , and denote the matrix transpose, conjugate, conjugate-transpose and inverse, respectively.
- ⊙ denotes the Hadamard product.
- denotes that is a positive semidefinite matrix.
2. Channel Model
We consider a massive MIMO secure multicast downlink transmission system, in which public messages sent by the BS are transmitted to the legitimate UTs. There is one BS with M antenna transmits and K UTs, each with antennas. The public messages are secret to the eavesdropper with antennas.
denotes the signal that is sent from the BS in multicast transmission. and , where denotes the transmit covariance matrix. We model the signals received by legitimate UT k and the eavesdropper as
respectively, where and are defined as the channel matrices of BS-UT k and BS-eavesdropper, respectively.
We consider our MIMO channel model to follow jointly spatially correlated Rayleigh fading, which means there are joint correlation characteristics between the transmitter and the receivers [37]. Thus, the channel matrices and in (1) and (2) can be expressed as
respectively, where and are random matrices with zero mean and independent elements, which are defined as the channel matrices of BS-UT k and BS-eavesdropper in the beam domain, respectively [34,38]. , , , and are unitary matrices of transmitter and receivers, respectively. The statistics of the beam domain channels can be described as
respectively. It can be proved that as the number of antennas in the BS, M, increases to infinity, the eigenvectors of the correlation matrices in (5) and (6) tend to be equal, which can be denoted by a deterministic unitary matrix [38]. is only effected by the topology of transmit array at the BS, which means the channel matrices can be rewritten as
respectively. It has been widely used in previous works and shows considerable accuracy for a finite number of BS antennas [35,36]. Thus, we adopt the channel models in (7) and (8) in this paper.
3. Energy Efficiency Optimization of Secure Multicast Transmission
We study the energy efficiency multicast optimization of secure massive MIMO in this section. We assume that the BS can only capture the statistical CSI of all legitimate UTs and the eavesdropper [34]. Besides, legitimate UTs and the eavesdropper can obtain the instantaneous CSI. Before constructing the energy efficiency model, we first analyze the secure transmit rate. The received signal transmission rate needs to be higher for any user terminal than that received by the eavesdropper. Focusing on delay-tolerant scenarios [39], the ergodic secure multicast rate can be expressed as
where the ergodic multicast rate is expressed as
and the ergodic rate for eavesdropper is expressed as
Meanwhile, we adopt a model of power consumption as follows. For large-scale MIMO systems, most of the power is consumed by the BS, we then focus mainly on the power consumption of the BS. Besides, the static and dynamic power consumption of the radio frequency chains is considered. Specifically, our power consumption model is adopted as
where denotes the transmit power of multicast transmission. Note that the coefficient is the reciprocal of the transmit amplifier drain efficiency, and are the static power consumption and the hardware dissipated power of the BS, respectively.
We denote W by the bandwidth of secure transmission, the energy efficiency of massive MIMO secure multicast transmission is formulated by the ratio of secure transmit rate to power consumption as follows,
Our aim is optimizing the transmit covariance matrix , leading to maximizing the of downlink secure multicast in (13). The problem is addressed as
where denotes the maximum multicast power budget at the transmitter.
in (11) can get its upper bound via using Jensen’s inequality, which is expressed as follows,
where denotes a function of matrix-valued form, which can output a diagonal matrix. Its ith diagonal element can be expressed as
For a vast region of signal-to-noise-ratio (SNR), the lower bound of secure multicast rate in (17) is very tight, and has little influence on the energy efficiency of the original problem, which can be seen in Section 4. Therefore, we can reduce the computational complexity while obtaining very approximate solutions of the original problem. The equivalent problem is approximately substituted for the original problem as follows,
The feasible solution leads the value of to zero. Therefore, all other feasible solutions leading to negative secure multicast rate are not the optimal solutions of the problem in (18). Besides, SNR is defined as in this paper. As a result, we omit the operator without loss of any optimality, leading the problem equivalent to follows,
We decompose the covariance matrix as . The columns of and diagonal elements of , respectively, denote the eigenvectors and the eigenvalues of , which indicates the multicast signaling directions and the powers allocation. We investigate the eigenvectors of the covariance matrix in Theorem 1.
Theorem 1.
Columns of are expressed as the eigenvectors of the transmit covariance matrix in (20) as follows,
Proof.
Please refer to the Appendix A. □
According to Theorem 1, we can indicate that the energy efficiency oriented secure multicast transmit signal directions are consistent with the eigenvector of the BS transmission correlation matrix. Therefore, the optimal problem for maximizing the system energy efficiency of secure downlink multicast transmission can be simplified into a beam domain power allocation problem. In particular, the precoding optimization problem of energy efficiency multicast transmission in (20) can be simplified to the following question without loss of optimality,
where
In (24), we adopt the minimum transmission rate received by legitimate users into our model to meet the requirement of confidentiality.
3.1. Minorize–Maximize Method
We note that function in (23) is the subtraction of two concave functions. The function is defined as the difference of convex functions (d.c.), which can not be solved by convex optimization directly. Via using the MM method, we adopt an iterative algorithm to deal with it [40,41]. The basic idea is to approximate by the first-order Taylor series expansion and transform it into a linear function. We can solve the subproblem with further algorithm and get the next iteration. The iterative subproblem is as follows,
where ℓ denotes the iteration index. Note that the gradient of over can be proved to be a diagonal matrix. We can get its kth diagonal element as follows,
where is by the MM method in (28), which can converge to a locally optimal solution of the original problem in (20) [42]. Therefore, our next step is to solve the subproblem of each iteration.
3.2. Dinkelbach’s Transform
At the ℓ th iteration of subproblem in (28), the fractional function of the objective is still difficult to solve with convex optimition directly. We have , which is a concave-minus-linear function. Thus, is a concave functions with respect to . Meanwhile, is a linear function. Dinkelbach’s transform is usually used to approach such concave-linear fractional program, whose advantage is that it does not have to include additional constraints. It has been proved that this algorithm possessed superlinear convergence [43,44]. Besides, Dinkelbach’s transform We express the powers allocation solved in (28) as . Via invoking Dinkelbach’s transform, we can solve the subproblem of each energy efficiency secure multicast optimization in (28) by iteratively solving the sequence of convex optimization problem as follows,
where t denotes the iteration index. is the solution of the ℓ th outer iteration of the MM method. Note that it is treated as a constant and will not update in the inner iteration in (30). denotes an auxiliary variable introduced by Dinkelbach’s transform, which can be updated as follows,
3.3. Deterministic Equivalent
Due to a large number of samples need to be averaged during the expectation operation in (30), the optimization complexity is still high, although each subproblem in (28) is a concave program. Thus, without using Monte Carlo averaging channel realizations, we calculate the deterministic equivalent of the secure transmit rate by adopting the large-dimensional random matrix theory, which can reduce the implementation complexity [45,46]. Note that the method of deterministic equivalent can keep the convexity of the transmission rate [47]. Therefore, the concave subproblem in (28) is given as
In (32), denotes the deterministic equivalent expression of , which is expressed as
where , , and can be obtained by solving the following three fixed-point equations,
where and are matrix-valued functions, which can output matrices in diagonal forms, the corresponding ith diagonal elements are respectively obtained by
Via the deterministic equivalent approach instead of exhaustive averaging, the expression is efficiently calculated by adopting the channel statistics in a small number of fixed-point iterations. As a result, the computational complexity to optimize the convex program in (28) can be reduced significantly.
3.4. Discussion
In the case of small numbers of antennas, the deterministic equivalent expression and are approximately equal [45,46]. Besides, with respect to , is still observed to be concave from (33). Thus, each subproblem in (32) does not change the convexity and still guarantees the convergence. Finally, we obtain our algorithm by two-level iteration. The optimal power allocation is obtained by the inner iteration and assigned to the outer iteration. Then, the initial power allocation of the inner layer is updated after the outer iteration. The proposed energy efficiency optimization algorithm of massive MIMO secure multicast transmission is described in detail in Algorithm 1.
| Algorithm 1 Energy Efficiency Optimization Algorithm for Secure Multicast Transmission |
| Input: The beam domain channel transmit statistics CSI and , initial power allocation , the threshold |
| Output: Optimal power allocation matrix |
| 1: Initialization: |
| 2: Calculate using (26), (27), and (33) |
| 3: repeat |
| 4: Update |
| 5: Initialization: , , using (31) |
| 6: repeat |
| 7: Update |
| 8: Calculate by using (30) with |
| 9: Update using (31) |
| 10: until |
| 11: Return |
| 12: until |
| 13: Return |
4. Simulation Results
To illustrate the performance of the energy efficiency optimization for massive MIMO secure multicast transmission with known statistical CSI. A series of assumptions about the simulation environment, transmission channel and antenna configuration are made in our work [48]. The major parameters related to simulation, such as the power consumption, are listed in Table 1.

Table 1.
Major simulation parameters of massive multiple-input multiple-output (MIMO) secure multicast transmission.
First of all, we evaluate our proposed algorithm convergence performance. In order to observe the convergence of the whole algorithm, we choose the outer iteration to draw Figure 1, which plots energy efficiency versus the number of iterations under different SNR. From Figure 1, it can be observed that our algorithm exhibits fast convergence performance. Besides, the lower the SNR regime is, the quicker the iteration converges. Thus, we can indicate that power allocation might perform better under the high SNR regime on optimizing secure multicast energy efficiency. In the regime of Figure 1, with the SNR increasing, the gain of energy efficiency increases faster, which shows that the secure multicast rate is growing rapidly.
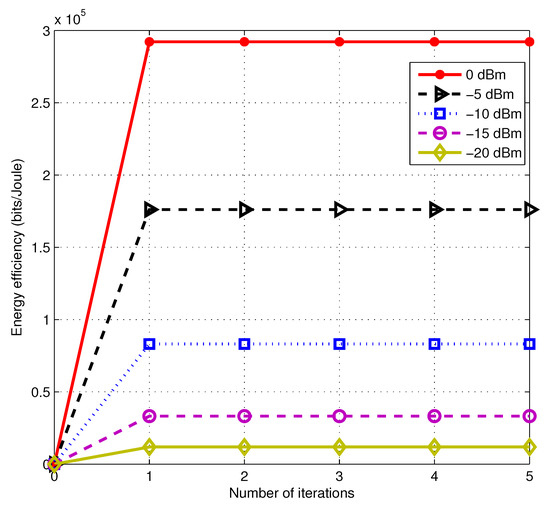
Figure 1.
The convergence performance of outer iteration of Algorithm 1 under different signal-to-noise-ratios (SNRs).
Next, we evaluate the energy efficiency performance of the proposed algorithm with a lower bound of secure multicast rate and the original optimization problem with the secure rate obtained by the Monte Carlo Method. It is shown in Figure 2 that the solutions of the two are quite tight. Therefore, we can handle the approximation problem to obtain the desired energy efficiency but significantly reduce the algorithm complexity. Then, we compare the energy efficiency performance optimized by the proposed algorithm with the traditional rate maximization one. In addition, the deterministic equivalent results are compared with those of the Monte Carlo method. According to Figure 2, it is not difficult to find that the gap between the deterministic equivalent and the Monte Carlo methods is almost zero. Besides, under the low transmit power regime, our proposed energy efficiency maximization and the traditional rate maximization algorithms have similar energy efficiency performance. It is also proved that the inference in Figure 1 is correct. However, under the high transmit power regime, the energy efficiency maximization algorithm is obviously superior to the traditional rate maximization one. It also shows that we can find a compromise power allocation to meet the two requirements at the same time in the goal of maximum rate and maximum energy efficiency for massive MIMO secure multicast transmission.
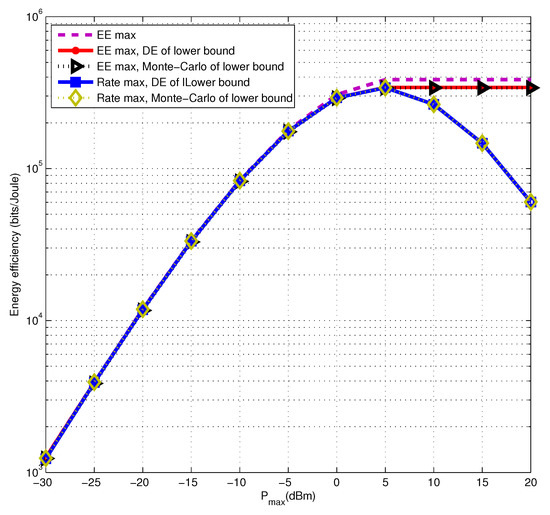
Figure 2.
The lower bound of energy efficiency by energy efficiency maximization and rate maximizations algorithm via using the deterministic equivalent and Monte Carlo methods, compared with the original energy efficiency.
Finally, we study the energy efficiency performance of our algorithm versus the numbers of antennas at the BS and show the results in Figure 3. With the number of BS antennas increasing, the change of energy efficiency performance tends to be flat, which shows that the power consumption dominates the performance of energy efficiency when the number of BS antennas is large. Besides, it can be indicated that we can find a suitable power allocation to meet our requirement of high energy efficiency. At the same time, we can also find that the energy efficiency does not increase with the number of antennas. This is because under large antennas and low power constraint, the secure rate changes faster than power consumption at the BS with the increase of the maximum power constraint, while the dynamic power consumption of the BS antennas increases rapidly under the high power constraint, leading the situation on the contrary. Finally, when the number of antennas increases, the system needs more power to reach better energy efficiency. Besides, the energy efficiency performance of the Monte Carlo method is quite close to the proposed one, which confirms the accuracy of the analysis.
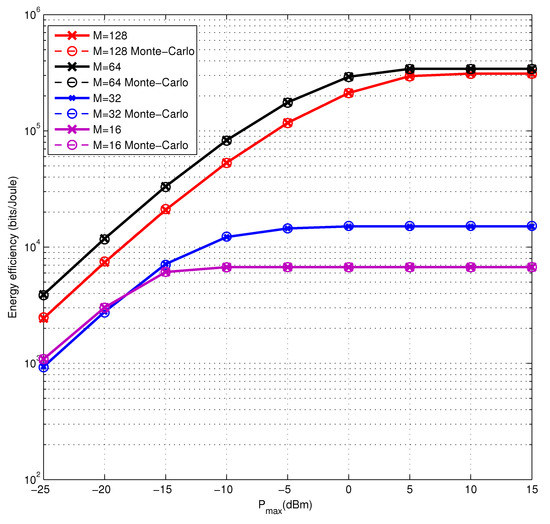
Figure 3.
The energy efficiency performance of the proposed algorithm and Monte Carlo method with the numbers of BS antennas varying from to .
5. Conclusions
We studied the energy efficiency optimization problem in downlink secure multicast transmission for massive MIMO with known statistical CSI in this paper. The energy efficiency maximization problem was formulated as maximizing the ratio of the secure multicast rate to the power consumption. We then obtained the secure multicast rate by introducing its lower bound to simplify the objective problem. Via making the transmit signaling directions into a closed-form, we simplified the energy efficiency optimization of matrix-valued strategy design to a beam domain power allocation problem. Next, we designed an algorithm including two-level iteration in the beam domain, and guaranteed the algorithm to converge to a locally optimal point based on the MM method and Dinkelbach’s transform. In addition, via substituting the multicast rate for its deterministic equivalent, the complexity of computational was significantly reduced. We made extensive simulations to verify the effectiveness of our algorithm. A large number of simulation results showed that the algorithm has fast convergence and low complexity. Compared with the rate maximization method, the proposed algorithm had more efficient and stable performance under the high transmission power constraint.
Author Contributions
Writing, B.J., L.Y., Y.H., and L.Q.; software, B.J. and L.Q. review and proofreading, Y.Z., L.Y., and W.W. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Natural Science Foundation of China under Grant 61761136016, in part by the Open Research fund of the Key Laboratory of Dynamic Cognitive System of Electromagnetic Spectrum Space, Ministry of Industry and Information Technology, Nanjing University of Aeronautics and Astronautics, under Grant KF20202107, and in part by the Fundamental Research Funds for the Central Universities.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Proof of Theorem 1
We can observe that the upper bound of the eavesdropper transmit rate in (15) is irrelevant to the off-diagonal elements of . Then, we define . The multicast rate of UTs in (20) can be expressed as follows,
Following a similar line of reasoning of the proof in [49], define as a diagonal matrix whose diagonal entries are all 1 except the th entry being . Please note that the matrix is an unitary matrix, which means has the same distribution as [49], thus
Here, is equal to expect for the off-diagonal entries in the rth row and the rth column, whose signs are reverse. We want to prove that nulling all the off-diagonal entries of in the r-th row and the r-th column will not decrease the transmit rate with respect to . We invoke Jensen’s inequality to prove it.
We repeat the r for 1 to , and find that the numerator of the problem is maximized when is diagonal. Meanwhile, the consumed power is irrelevant to the off-diagonal elements of . Thus, the objective problem in (20) is maximized when is diagonal. This concludes the proof.
References
- Larsson, E.G.; Edfors, O.; Tufvesson, F.; Marzetta, T.L. Massive MIMO for Next Generation Wireless Systems. IEEE Commun. Mag. 2014, 52, 186–195. [Google Scholar] [CrossRef]
- Guariglia, E. Harmonic Sierpinski Gasket and Applications. Entropy 2018, 20, 714. [Google Scholar] [CrossRef]
- Marzetta, T.L. Noncooperative cellular wireless with unlimited numbers of base station antennas. IEEE Trans. Wirel. Commun. 2010, 9, 3590–3600. [Google Scholar] [CrossRef]
- Lecompte, D.; Gabin, F. Evolved multimedia broadcast/multicast service (eMBMS) in LTE-advanced: Overview and Rel-11 enhancements. IEEE Commun. Mag. 2012, 50, 68–74. [Google Scholar] [CrossRef]
- Zhang, S.Q.; Wu, Q.Q.; Xu, S.G.; Li, G.Y. Fundamental Green Tradeoffs: Progresses, Challenges, and Impacts on 5G Networks. IEEE Commun. Surv. Tutor. 2017, 19, 33–56. [Google Scholar] [CrossRef]
- Wang, W.; Liu, A.; Zhang, Q.; You, L.; Gao, X.Q.; Zheng, G. Robust multigroup multicast transmission for frame-based multi-beam satellite systems. IEEE Access 2018, 6, 46074–46083. [Google Scholar] [CrossRef]
- Li, Y.; Liu, A.; Wang, W.; Gao, X.Q. Outage constrained robust multigroup multicast beamforming for multi-beam satellite communication systems. IEEE Wirel. Commun. Lett. 2018, 6, 46074–46083. [Google Scholar]
- Jiang, C.; Wu, W.; Ding, Z. LTE Multimedia Broadcast Multicast Service Provisioning Based on Robust Header Compression. IEEE Trans. Wirel. Commun. 2018, 17, 1161–1172. [Google Scholar] [CrossRef]
- Xiang, Z.; Tao, M.; Wang, X. Massive MIMO multicasting in noncooperative cellular networks. IEEE J. Sel. Areas Commun. 2014, 32, 1180–1193. [Google Scholar] [CrossRef]
- Sadeghi, M.; Björnson, E.; Larsson, E.G.; Yuen, C.; Marzetta, T.L. Max-min fair transmit precoding for multi-group multicasting in massive MIMO. IEEE Trans. Wirel. Commun. 2018, 17, 1358–1373. [Google Scholar] [CrossRef]
- Sadeghi, M.; Björnson, E.; Larsson, E.G.; Yuen, C.; Marzetta, T.L. Joint unicast and multi-group multicast transmission in massive MIMO systems. IEEE Trans. Wirel. Commun. 2018, 17, 6375–6388. [Google Scholar] [CrossRef]
- Zhang, X.; Sun, S.; Qi, F.; Bo, R.; Qian, Y. Massive MIMO Based Hybrid Unicast/Multicast Services for 5G. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016. [Google Scholar]
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Kapetanović, D.; Zheng, G.; Rusek, F. Physical layer security for massive MIMO: An overview on passive eavesdropping and active attacks. IEEE Commun. Mag. 2015, 53, 21–27. [Google Scholar] [CrossRef]
- Deepanramkumar, P.; Karuppiah, M.; Islam, S.K.H.; Obaidat, M.S. Secure cognitive radio-based synchronized transmission of 5G signals using massive MIMO. Int. J. Commun. Syst. 2018, 31, e3805.1–e3805.15. [Google Scholar]
- Wang, J.; Wang, J.; Lu, K.; Qian, Y.; Gu, N. On the Optimal Linear Network Coding Design for Information Theoretically Secure Unicast Streaming. IEEE Trans. Multimedia 2016, 18, 1149–1162. [Google Scholar] [CrossRef]
- Wu, Y.; Schober, R.; Ng, D.W.K.; Xiao, C.; Caire, G. Secure massive MIMO transmission with an active eavesdropper. IEEE Trans. Inf. Theory 2016, 62, 3880–3900. [Google Scholar] [CrossRef]
- Wu, W.; Gao, X.Q.; Wu, Y.; Xiao, C. Beam domain secure transmission for massive MIMO communications. IEEE Trans. Veh. Technol. 2018, 67, 7113–7127. [Google Scholar] [CrossRef]
- Lv, T.; Gao, H.; Yang, S. Secrecy transmit beamforming for heterogeneous networks. IEEE J. Sel. Areas Commun. 2015, 33, 1154–1170. [Google Scholar] [CrossRef]
- You, L.; Wang, J.; Wang, W.; Gao, X. Secure Multicast Transmission for Massive MIMO With Statistical Channel State Information. IEEE Signal Process. Lett. 2019, 26, 803–807. [Google Scholar] [CrossRef]
- Liu, X.; Gao, F.; Wang, G.; Wang, X. Joint beamforming and user selection in multicast downlink channel under secrecy-outage constraint. IEEE Commun. Lett. 2014, 18, 82–85. [Google Scholar] [CrossRef]
- Hanif, M.F.; Tran, L.N.; Juntti, M.; Glisic, S. On linear precoding strategies for secrecy rate maximization in multiuser multiantenna wireless networks. IEEE Trans. Signal Process. 2014, 62, 3536–3551. [Google Scholar] [CrossRef]
- Wang, B.; Mu, P. Artificial noise-aided secure multicasting design under secrecy outage constraint. IEEE Trans. Commun. 2017, 65, 5401–5414. [Google Scholar] [CrossRef]
- Hu, J.; Cai, Y.; Yang, N.; Zhou, X.; Yang, W. Artificial-Noise-Aided Secure Transmission Scheme With Limited Training and Feedback Overhead. IEEE Trans. Wirel. Commun. 2017, 16, 193–205. [Google Scholar] [CrossRef]
- Zappone, A.; Jorswieck, E. Energy efficiency in wireless networks via fractional programming theory. Found. Trends Commun. Inf. Theory 2015, 11, 185–296. [Google Scholar] [CrossRef]
- You, L.; Wang, W.; Gao, X. Energy-Efficient Multicast Precoding for Massive MIMO Transmission with Statistical CSI. Energies 2018, 11, 3175. [Google Scholar] [CrossRef]
- Auer, G.; Giannini, V.; Desset, C.; Godor, I.; Skillermark, P.; Olsson, M.; Imran, M.A.; Sabell, D.; Gonzalez, M.J.; Blume, O.; et al. How much energy is needed to run a wireless network? IEEE Wirel. Commun. 2012, 18, 40–49. [Google Scholar] [CrossRef]
- Ru, G.; Li, H.; Liu, L.; Hu, Z.; Gan, Y. Energy Efficiency of Hybrid Cellular With Heterogeneous QoS Provisions. IEEE Commun. Lett. 2014, 18, 1003–1006. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Lo, E.S.; Schober, R. Energy-Efficient Resource Allocation in OFDMA Systems with Large Numbers of Base Station Antennas. IEEE Trans. Wirel. Commun. 2012, 11, 3292–3304. [Google Scholar] [CrossRef]
- Björnson, E.; Sanguinetti, L.; Hoydis, J.; Debbah, M. Optimal Design of Energy-Efficient Multi-User MIMO Systems: Is Massive MIMO the Answer? IEEE Trans. Wirel. Commun. 2015, 14, 3059–3075. [Google Scholar] [CrossRef]
- He, S.; Huang, Y.; Jin, S.; Yang, L. Energy Efficient Coordinated Beamforming Design in Multi-Cell Multicast Networks. IEEE Commun. Lett. 2015, 19, 985–988. [Google Scholar] [CrossRef]
- Tervo, O.; Tran, L.; Pennanen, H.; Chatzinotas, S.; Ottersten, B.; Juntti, M. Energy-Efficient Multicell Multigroup Multicasting With Joint Beamforming and Antenna Selection. IEEE Trans. Signal Process. 2018, 66, 4904–4919. [Google Scholar] [CrossRef]
- Wang, J.; Lee, J.; Wang, F.; Quek, T.Q.S. Jamming-aided secure communication in massive MIMO Rician channels. IEEE Trans. Wirel. Commun. 2015, 14, 6854–6868. [Google Scholar] [CrossRef]
- Sun, C.; Gao, X.Q.; Jin, S.; Matthaiou, M.; Ding, Z.; Xiao, C. Beam division multiple access transmission for massive MIMO communications. IEEE Trans. Commun. 2015, 63, 2170–2184. [Google Scholar] [CrossRef]
- You, L.; Gao, X.Q.; Xia, X.G.; Ma, N.; Peng, Y. Pilot reuse for massive MIMO transmission over spatially correlated Rayleigh fading channels. IEEE Trans. Wirel. Commun. 2015, 14, 3352–3366. [Google Scholar] [CrossRef]
- You, L.; Gao, X.Q.; Swindlehurst, A.L.; Zhong, W. Channel acquisition for massive MIMO-OFDM with adjustable phase shift pilots. IEEE Trans. Signal Process. 2016, 64, 1461–1476. [Google Scholar] [CrossRef]
- Gao, X.Q.; Jiang, B.; Li, X.; Gershman, A.B.; McKay, M.R. Statistical eigenmode transmission over jointly correlated MIMO channels. IEEE Trans. Inf. Theory 2009, 55, 3735–3750. [Google Scholar] [CrossRef]
- You, L.; Gao, X.Q.; Li, G.Y.; Xia, X.G.; Ma, N. BDMA for millimeter-wave/Terahertz massive MIMO transmission with per-beam synchronization. IEEE J. Sel. Areas Commun. 2017, 35, 1550–1563. [Google Scholar] [CrossRef]
- Pei, M.; Swindlehurst, A.L.; Ma, D.; Wei, J. Adaptive limited feedback for MISO wiretap channels with cooperative jamming. IEEE Trans. Signal Process. 2014, 62, 993–1004. [Google Scholar] [CrossRef]
- Chouzenoux, E.; Moussaoui, S.; Idier, J. Majorize-minimize linesearch for inversion methods involving barrier function optimization. Inverse Probl. 2012, 28, 065011. [Google Scholar] [CrossRef]
- Sun, Y.; Babu, P.; Palomar, D.P. Majorization-Minimization Algorithms in Signal Processing, Communications, and Machine Learning. IEEE Trans. Signal Process. 2016, 65, 794–816. [Google Scholar] [CrossRef]
- Sriperumbudur, B.K.; Lanckriet, G.R.G. A proof of convergence of the concave-convex procedure using Zangwill’s theory. Neural Comput. 2012, 24, 1391–1407. [Google Scholar] [CrossRef] [PubMed]
- Dinkelbach, W. On Nonlinear Fractional Programming. Manag. Sci. 1967, 13, 492–498. [Google Scholar] [CrossRef]
- Zappone, A.; Bjornson, E.; Sanguinetti, L.; Jorswieck, E. Globally Optimal Energy-Efficient Power Control and Receiver Design in Wireless Networks. Trans. Sig. Proc. 2017, 65, 2844–2859. [Google Scholar] [CrossRef]
- Couillet, R.; Debbah, M. Random Matrix Methods for Wireless Communications; Cambridge Univ. Press: New York, NY, USA, 2011. [Google Scholar]
- Lu, A.A.; Gao, X.Q.; Xiao, C. Free deterministic equivalents for the analysis of MIMO multiple access channel. IEEE Trans. Inf. Theory 2016, 62, 4604–4629. [Google Scholar] [CrossRef]
- Wen, C.K.; Jin, S.; Wong, K.K. On the Sum-Rate of Multiuser MIMO Uplink Channels with Jointly-Correlated Rician Fading. IEEE Trans. Commun. 2011, 59, 2883–2895. [Google Scholar] [CrossRef]
- Salo, J.; Del Galdo, G.; Salmi, J.; Kyösti, P.; Milojevic, M.; Laselva, D.; Schneider, C. MATLAB Implementation of the 3GPP Spatial Channel Model (3GPP TR 25.996). January 2005. Available online: http://www.mweda.com/img/smqh/tongxin/tongxin-3300qsdyezswos.pdf (accessed on 10 October 2020).
- Lapidoth, A. The capacity of a MIMO Ricean channel is monotonic in the singular values of the mean. In Proceedings of the 5th International ITG Conference on Source and Channel Coding (SCC), Erlangen, Germany, 14–16 January 2004; pp. 1–5. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).