What Is the Entropy of a Social Organization?
Abstract
1. Introduction
2. Quantifying the Potentiality of a Social Organization
2.1. Network Representation of a Social Organization
2.2. Potentiality of a Social Organization
2.2.1. Potentiality and Constraints
2.2.2. How to Proxy Constraints
2.2.3. Network Ensembles and Their Probability Distribution
3. Introducing the Generalized Hypergeometric Ensembles
3.1. Obtaining
3.1.1. Parameters of a gHypEG
3.1.2. Calculating for Networks
3.1.3. Calculating for Networks
3.2. Tractability of the Entropy
3.2.1. Multinomial Entropy Approximation
3.2.2. Computing the Multinomial Entropy
3.3. Comparing Entropy Values
Normalizing Value Ranges
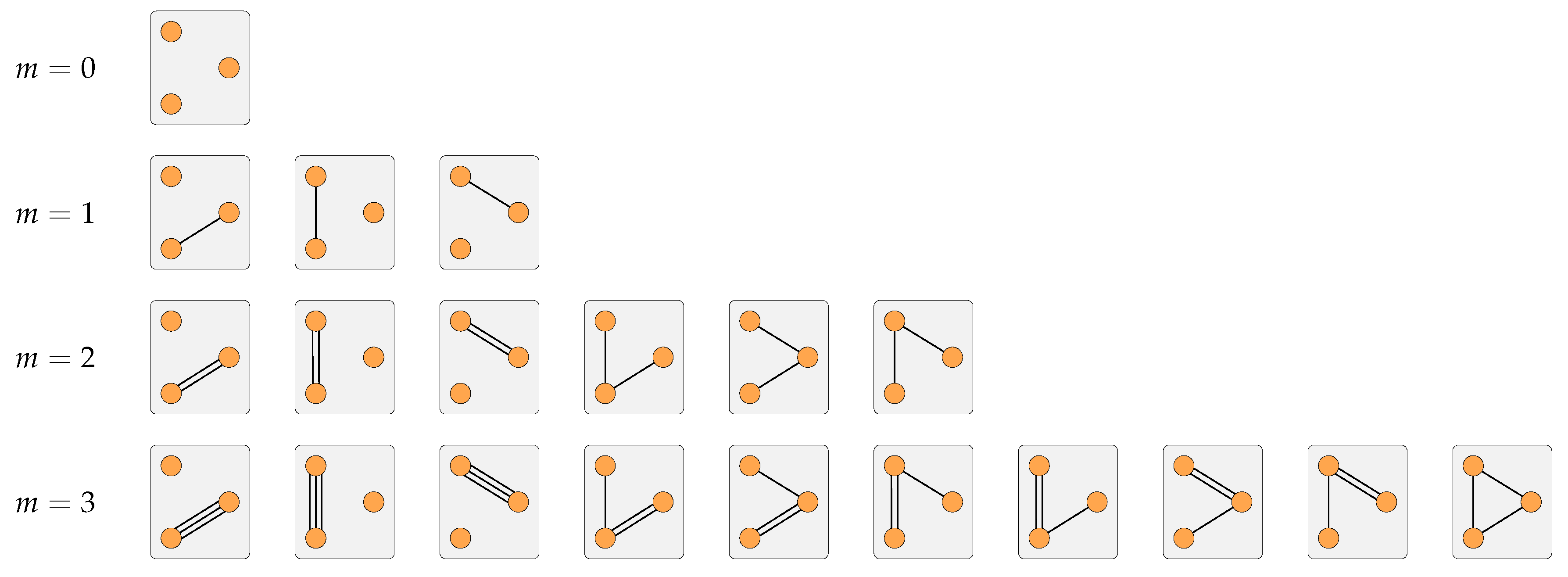
3.4. Examples for
3.4.1. Two Special Cases
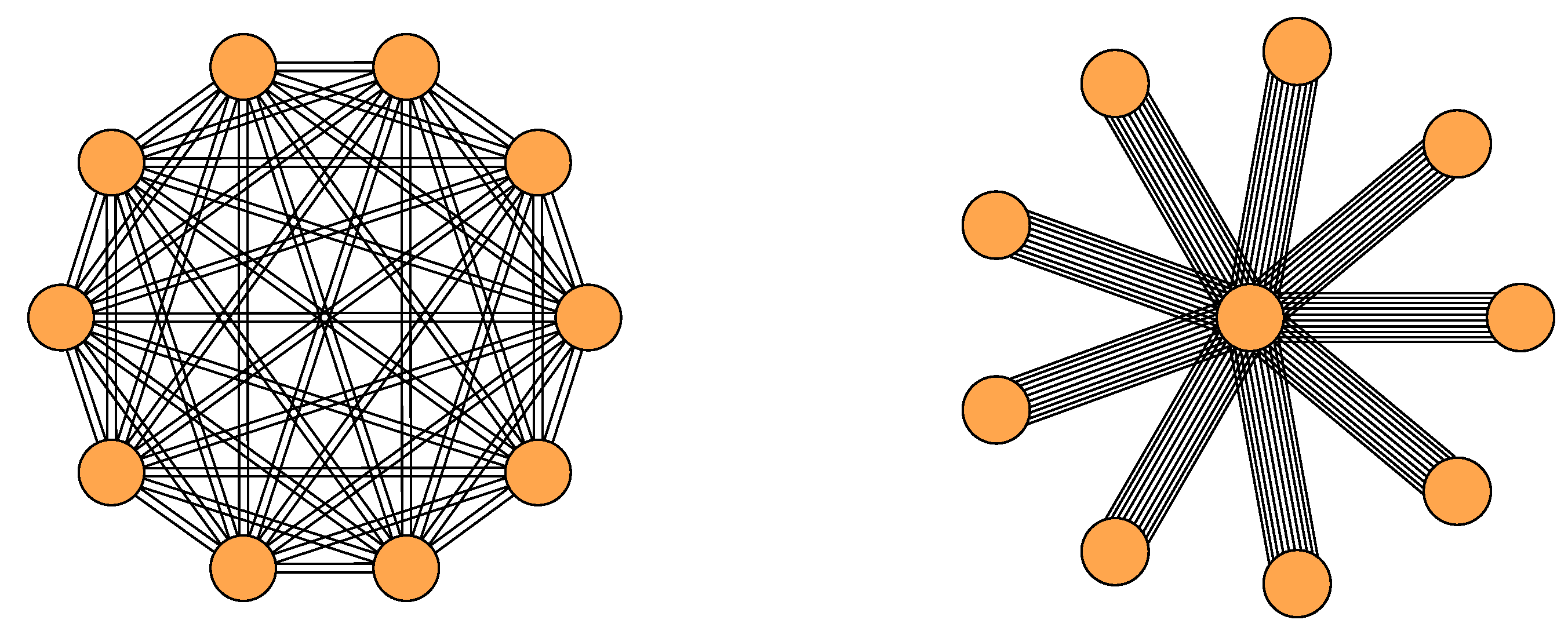
3.4.2. Complete Network
3.4.3. Star Network
4. Applications to Real-World Datasets
4.1. Examined Datasets
4.1.1. Southern Women Dataset
4.1.2. Karate Club Dataset
4.1.3. Conference Dataset
4.1.4. Network Overview
4.2. Potentiality of the Empirical Networks
4.2.1. Southern Women Network
4.2.2. Karate Club Network
4.2.3. Conference Networks
5. Conclusions
5.1. Fixed Numbers of Nodes and Edges
5.2. Large Number of Degrees of Freedom
5.3. Computability
Author Contributions
Funding
Conflicts of Interest
Appendix A. Fitting the Ξ Matrix for Undirected Networks Without Self-Loops
Appendix B. Convergence in Distribution of gHypEGs
Appendix C. Full Matrices for the Complete and the Star Network
References
- Schweitzer, F.; Nanumyan, V.; Tessone, C.J.; Xia, X. How do OSS projects change in number and size? A large-scale analysis to test a model of project growth. Adv. Complex Syst. 2014, 17, 1550008. [Google Scholar] [CrossRef]
- Zachary, W.W. An Information Flow Model for Conflict and Fission in Small Groups. J. Anthropol. Res. 1977, 33, 452–473. [Google Scholar] [CrossRef]
- Isella, L.; Stehlé, J.; Barrat, A.; Cattuto, C.; Pinton, J.F.; Van den Broeck, W. What’s in a crowd? Analysis of face-to-face behavioral networks. J. Theor. Biol. 2011, 271, 166–180. [Google Scholar] [CrossRef] [PubMed]
- Dorogovtsev, S.; Mendes, J. Evolution of Networks; Oxford University Press: Oxford, UK, 2003; Volume 57. [Google Scholar] [CrossRef]
- Newman, M.E.J. The Structure and Function of Complex Networks. SIAM Rev. 2003, 45, 167–256. [Google Scholar] [CrossRef]
- Ebeling, W.; Freund, J.; Schweitzer, F. Komplexe Strukturen: Entropie und Information; Vieweg+Teubner Verlag: Wiesbaden, Germany, 1998. [Google Scholar] [CrossRef]
- Zhao, K.; Karsai, M.; Bianconi, G. Entropy of dynamical social networks. PLoS ONE 2011, 6, e28116. [Google Scholar] [CrossRef] [PubMed]
- Kulisiewicz, M.; Kazienko, P.; Szymanski, B.K.; Michalski, R. Entropy Measures of Human Communication Dynamics. Sci. Rep. 2018, 8, 15697. [Google Scholar] [CrossRef] [PubMed]
- Santiago-Paz, J.; Torres-Roman, D.; Velarde-Alvarado, P. Detecting anomalies in network traffic using Entropy and Mahalanobis distance. In Proceedings of the CONIELECOMP 2012, 22nd International Conference on Electrical Communications and Computers, Puebla, Mexico, 27–29 February 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 86–91. [Google Scholar] [CrossRef]
- Rajaram, R.; Castellani, B. An entropy based measure for comparing distributions of complexity. Physica A 2016, 453, 35–43. [Google Scholar] [CrossRef]
- Hanel, R.; Thurner, S. A comprehensive classification of complex statistical systems and an axiomatic derivation of their entropy and distribution functions. Europhys. Lett. 2011, 93, 20006. [Google Scholar] [CrossRef]
- Bianconi, G. Entropy of network ensembles. Phys. Rev. E 2009, 79, 036114. [Google Scholar] [CrossRef]
- Coon, J.P.; Dettmann, C.P.; Georgiou, O. Entropy of spatial network ensembles. Phys. Rev. E 2018, 97, 042319. [Google Scholar] [CrossRef]
- Bianconi, G. The entropy of randomized network ensembles. Europhys. Lett. 2008, 81, 28005. [Google Scholar] [CrossRef]
- Casiraghi, G.; Nanumyan, V. Generalised hypergeometric ensembles of random graphs: The configuration model as an urn problem. arXiv 2018, arXiv:1810.06495. [Google Scholar]
- Bollobás, B. Modern Graph Theory. In Graduate Texts in Mathematics; Springer: New York, NY, USA, 1998; Volume 184. [Google Scholar] [CrossRef]
- Shannon, C.E. A Mathematical Theory of Communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Scholtes, I. When is a Network a Network? In Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining—KDD ’17, Halifax, NS, Canada, 13–17 August 2017; ACM Press: New York, NY, USA, 2017; pp. 1037–1046. [Google Scholar] [CrossRef]
- Vaccario, G.; Verginer, L.; Schweitzer, F. Reproducing scientists’ mobility: A data-driven model. arXiv 2018, arXiv:1811.07229. [Google Scholar] [CrossRef]
- Liben-Nowell, D.; Novak, J.; Kumar, R.; Raghavan, P.; Tomkins, A. Geographic routing in social networks. Proc. Natl. Acad. Sci. USA 2005, 102, 11623–11628. [Google Scholar] [CrossRef] [PubMed]
- Zanetti, M.S.; Scholtes, I.; Tessone, C.J.; Schweitzer, F. The rise and fall of a central contributor: Dynamics of social organization and performance in the GENTOO community. In Proceedings of the 2013 6th International Workshop on Cooperative and Human Aspects of Software Engineering, CHASE 2013, San Francisco, CA, USA, 25 May 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 49–56. [Google Scholar] [CrossRef]
- Scholtes, I.; Mavrodiev, P.; Schweitzer, F. From Aristotle to Ringelmann: A large-scale analysis of team productivity and coordination in Open Source Software projects. Empir. Softw. Eng. 2016, 21, 642–683. [Google Scholar] [CrossRef]
- Krivitsky, P.N.; Butts, C.T. Exponential-family Random Graph Models for Rank-order Relational Data. Sociol. Methodol. 2017, 47, 68–112. [Google Scholar] [CrossRef]
- Park, J.; Newman, M.E. Statistical mechanics of networks. Phys. Rev. E 2004, 70, 13. [Google Scholar] [CrossRef]
- Morris, M.; Handcock, M.S.; Hunter, D.R. Specification of Exponential-Family Random Graph Models: Terms and Computational Aspects. J. Stat. Softw. 2008, 24, 1548. [Google Scholar] [CrossRef]
- Fischer, R.; Leitão, J.C.; Peixoto, T.P.; Altmann, E.G. Sampling Motif-Constrained Ensembles of Networks. Phys. Rev. Lett. 2015, 115, 188701. [Google Scholar] [CrossRef]
- Casiraghi, G.; Nanumyan, V.; Scholtes, I.; Schweitzer, F. Generalized Hypergeometric Ensembles: Statistical Hypothesis Testing in Complex Networks. arXiv 2016, arXiv:1607.02441. [Google Scholar]
- Molloy, M.; Reed, B. A critical point for random graphs with a given degree sequence. Random Struct. Algorithms 1995, 6, 161–180. [Google Scholar] [CrossRef]
- Wallenius, K.T. Biased Sampling: The Noncentral Hypergeometric Probability Distribution. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 1963. [Google Scholar]
- SciPy: Open Source Scientific Tools for Python. 2001. Available online: http://www.scipy.org/ (accessed on 28 January 2019).
- Davis, A.; Gardner, B.B.; Gardner, M.R. Deep South: A Social Anthropological Study of Caste and Class; The University of Chicago Press: Chicago, IL, USA, 1941. [Google Scholar]
- Doreian, P. On the evolution of group and network structure. Soc. Netw. 1979, 2, 235–252. [Google Scholar] [CrossRef]

| Network | n | m | D | |||
|---|---|---|---|---|---|---|
| Southern Women | 18 | 322 | ||||
| Karate Club | 34 | 231 | ||||
| Conference | 113 | 6925 | ||||
| Conference | 113 | 7131 | ||||
| Conference | 113 | 6762 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zingg, C.; Casiraghi, G.; Vaccario, G.; Schweitzer, F. What Is the Entropy of a Social Organization? Entropy 2019, 21, 901. https://doi.org/10.3390/e21090901
Zingg C, Casiraghi G, Vaccario G, Schweitzer F. What Is the Entropy of a Social Organization? Entropy. 2019; 21(9):901. https://doi.org/10.3390/e21090901
Chicago/Turabian StyleZingg, Christian, Giona Casiraghi, Giacomo Vaccario, and Frank Schweitzer. 2019. "What Is the Entropy of a Social Organization?" Entropy 21, no. 9: 901. https://doi.org/10.3390/e21090901
APA StyleZingg, C., Casiraghi, G., Vaccario, G., & Schweitzer, F. (2019). What Is the Entropy of a Social Organization? Entropy, 21(9), 901. https://doi.org/10.3390/e21090901





