A New Quantum Blind Signature Scheme with BB84-State
Abstract
1. Introduction
2. Preliminary Theory
2.1. Properties of the Blind Signature
- Unforgeability: No one can generate an effective blind signature except the signer himself/herself. This is one of the most basic requirements.
- Non-repudiation: Once a signer has signed a message, he/she cannot deny his/her signature of the message.
- Blindness: Although a signer has signed a message, he/she cannot get the concrete content of the message.
- Unlinkability: Once the signature of the message is public, the signer cannot determine whether he/she has signed the message.
- Traceability: Once a dispute happens, the verifier can trace the signature.
2.2. Quantum Fingerprint
2.3. Improved QOTP Encryption
3. Quantum Blind Signature Scheme
3.1. BB84-State Encoding
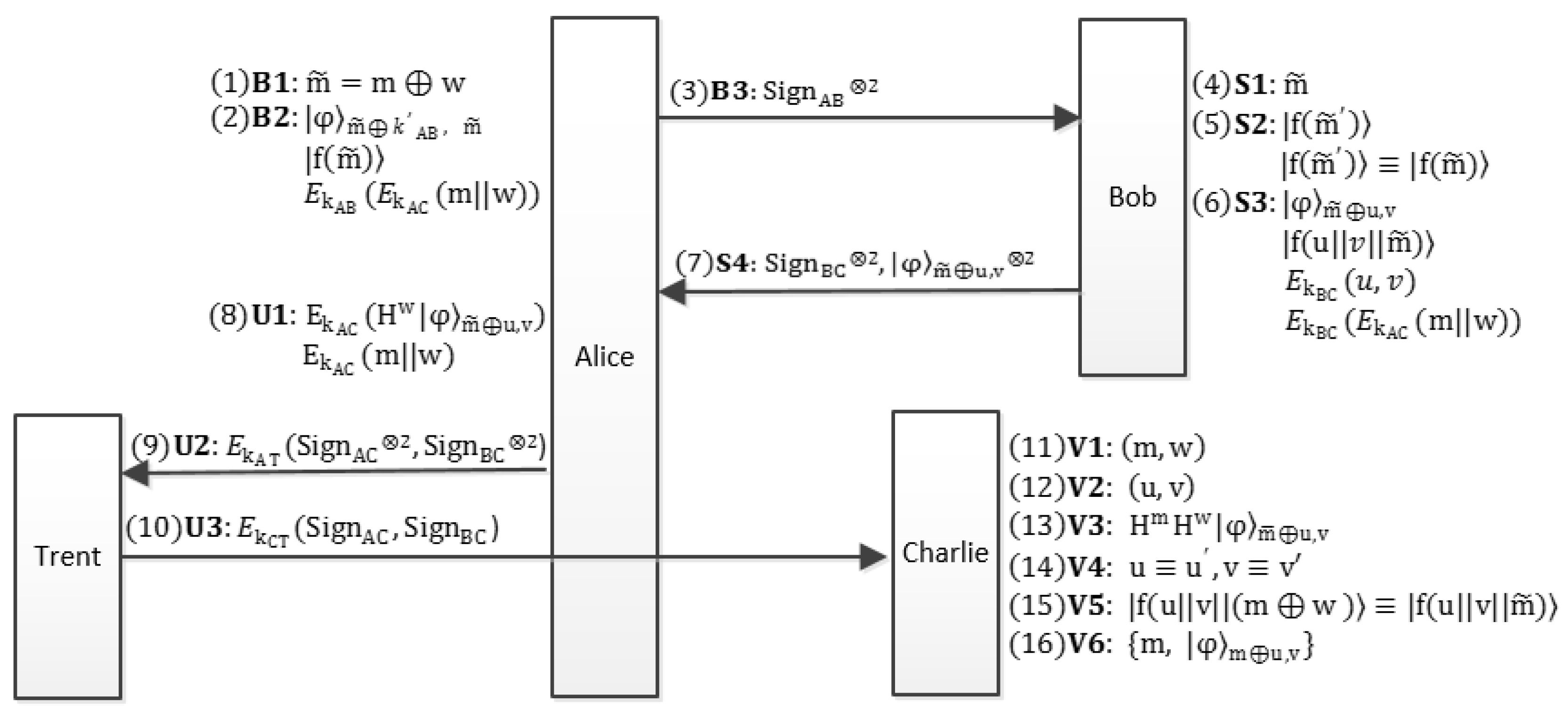
3.2. The Proposed Quantum Blind Signature Scheme
3.2.1. Initial Phase
3.2.2. Blinding Phase
3.2.3. Signing phase
3.2.4. Unblinding Phase
3.2.5. Verifying Phase
4. Security Analyses
4.1. Correctness
4.2. Against External Attack
4.3. Blindness
4.4. Unforgeability
4.5. Non-Repudiation
4.6. Unlinkability
4.7. Traceability
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Bennett, C.H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 1992, 68, 3121–3124. [Google Scholar] [CrossRef]
- Ekert, A.K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991, 67, 661–663. [Google Scholar] [CrossRef] [PubMed]
- Sasaki, T.; Yamamoto, Y.; Koashi, M. Practical quantum key distribution protocol without monitoring signal disturbance. Nature 2014, 509, 475–478. [Google Scholar] [CrossRef] [PubMed]
- Giovannetti, V.; Lloyd, S.; Maccone, L. Quantum private queries. Phys. Rev. Lett. 2008, 100, 230502. [Google Scholar] [CrossRef] [PubMed]
- Liu, B.; Gao, F.; Huang, W.; Wen, Q.Y. QKD-Based quantum private query without a failure probability. Sci. China-Phys. Mech. Astron. 2015, 58, 100301. [Google Scholar] [CrossRef]
- Wei, C.Y.; Cai, X.Q.; Liu, B.; Wang, T.-Y.; Gao, F. A Generic Construction of Quantum-Oblivious- Key-Transfer-Based Private Query with Ideal Database Security and Zero Failure. IEEE Trans. Comput. 2018, 67, 2–8. [Google Scholar] [CrossRef]
- Gottesman, D.; Chuang, I. Quantum digital signatures. arXiv, 2001; arXiv:quant-ph/0105032. [Google Scholar]
- Zeng, G.H.; Keitel, C.H. Arbitrated quantum-signature scheme. Phys. Rev. A 2002, 65, 042312. [Google Scholar] [CrossRef]
- Dunjko, V.; Wallden, P.; Andersson, E. Quantum digital signatures without quantum memory. Phys. Rev. Lett. 2014, 112, 040502. [Google Scholar] [CrossRef]
- Wallden, P.; Dunjko, V.; Kent, A.; Andersson, E. Quantum digital signatures with quantum key distribution components. Phys. Rev. A 2015, 91, 042304. [Google Scholar] [CrossRef]
- Amiri, R.; Wallden, P.; Kent, A.; Andersson, E. Secure quantum signatures using insecure quantum channels. Phys. Rev. A 2016, 93, 032325. [Google Scholar] [CrossRef]
- Lo, H.-K.; Curty, M.; Qi, B. Measurement-Device-Independent Quantum Key Distribution. Phy. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Puthoor, I.V.; Amiri, R.; Wallden, P.; Curty, M.; Andersson, E. Measurement-device-independent quantum digital signatures. Phy. Rev. A 2016, 94, 022328. [Google Scholar] [CrossRef]
- Yin, H.L.; Wang, W.L.; Tang, Y.L.; Zhao, Q.; Liu, H.; Sun, X.-X.; Zhang, W.-J.; Li, H.; Puthoor, I.V.; You, L.-X.; et al. Experimental measurement-device-independent quantum digital signatures over a metropolitan network. Phy. Rev. A 2017, 95, 042338. [Google Scholar] [CrossRef]
- Roberts, G.L.; Lucamarini, M.; Yuan, Z.L.; Dynes, J.F. Experimental measurement-device-independent quantum digital signatures. Nat. Comun. 2017, 8, 1098. [Google Scholar] [CrossRef] [PubMed]
- Chaum, D. Blind signature for untraceable payments. In Advances in Cryptology; Springer: Boston, MA, USA; pp. 199–203.
- Wen, X.; Niu, X.; Ji, L.; Tian, Y. A weak blind signature scheme based on quantum cryptography. Opt. Commun. 2009, 282, 666–669. [Google Scholar] [CrossRef]
- Qi, S.; Zheng, H.; Wen, Q.; Li, W. Quantum blind signature based on two-state vector formalism. Opt. Commun. 2010, 283, 4408–4410. [Google Scholar] [CrossRef]
- Yang, C.W.; Hwang, T.; Luo, Y.P. Enhancement on “quantum blind signature based on two-state vector formalism”. Quantum Inf. Process. 2012, 12, 109–117. [Google Scholar] [CrossRef]
- Zhang, M.; Xu, G.A.; Chen, X.B.; Yang, S.; Yang, Y.-X. Attack on the improved quantum blind signature protocol. Int. J. Theor. Phys. 2013, 52, 331–335. [Google Scholar] [CrossRef]
- Khodambashi, S.; Zakerolhosseini, A. A sessional blind signature based on quantum cryptography. Quantum Inf. Process. 2014, 13, 121–130. [Google Scholar] [CrossRef]
- Shi, W.M.; Zhang, J.B.; Zhou, Y.H.; Yang, Y.G. A new quantum blind signature with unlinkability. Quantum Inf. Process. 2015, 14, 3019–3030. [Google Scholar] [CrossRef]
- Luo, Y.P.; Tsai, S.L.; Hwang, T.; Kao, S.H. On “a new quantum blind signature with unlinkability”. Quantum Inf. Process. 2017, 16, 87. [Google Scholar] [CrossRef]
- Yin, X.; Ma, W.; Liu, W. A blind quantum signature scheme with χ-type entangled states. Int. J. Theor. Phys. 2012, 51, 455–461. [Google Scholar] [CrossRef]
- Wang, M.M.; Chen, X.B.; Yang, Y.X. A blind quantum signature protocol using the GHZ states. Sci. China Phys. Mech. Astron. 2013, 56, 1636–1641. [Google Scholar] [CrossRef]
- Zuo, H.J. Cryptanalysis of quantum blind signature scheme. Int. J. Theor. Phys. 2013, 52, 322–329. [Google Scholar] [CrossRef]
- Ribeiro, J.; Souto, A.; Mateus, P. Quantum blind signature with an offline repository. Int. J. Quantum Inf. 2015, 13, 1550016. [Google Scholar] [CrossRef]
- Lai, H.; Luo, M.X.; Pieprzyk, J.; Qu, Z.G.; Li, S.; Orgun, M.A. An efficient quantum blind digital signature scheme. Sci. China Inf. Sci. 2017, 60, 082501. [Google Scholar] [CrossRef]
- Wang, T.Y.; Wen, Q.Y. Fair quantum blind signatures. Chin. Phys. B 2010, 19, 0307. [Google Scholar]
- He, L.B.; Huang, L.S.; Yang, W.; Xu, R. Cryptanalysis of fair quantum blind signatures. Chin. Phys. B 2012, 21, 030306. [Google Scholar] [CrossRef]
- Zou, X.F.; Qiu, D.W. Attack and improvements of fair quantum blind signature schemes. Quantum Inf. Process. 2013, 12, 2071–2085. [Google Scholar] [CrossRef]
- Buhrman, H.; Cleve, R.; Watrous, J.; De, W.R. Quantum Fingerprinting. Phys. Rev. Lett. 2001, 87, 167902. [Google Scholar] [CrossRef] [PubMed]
- Zhang, K.J.; Zhang, W.W.; Li, D. Improving the security of arbitrated quantum signature against the forgery attack. Quantum Inf. Process. 2013, 12, 2655–2669. [Google Scholar] [CrossRef]
- Zhang, K.J.; Qin, S.J.; Sun, Y.; Song, T.T.; Su, Q. Reexamination of arbitrated quantum signature: the impossible and the possible. Quantum Inf. Process. 2013, 12, 3127–3141. [Google Scholar] [CrossRef]
- Boykin, P.; Roychowdhury, V. Optimal encryption of quantum bits. Phys. Rev. A 2003, 67, 042317. [Google Scholar] [CrossRef]
- Brassard, G. Quantum communication complexity (a survey). arXiv, 2001; arXiv:quant-ph/0101005. [Google Scholar]
- Buhrman, H.; Cleve, R.; Massar, S.; Wolf, R.D. Non-Locality and communication complexity. Rev. Mod. Phys. 2009, 82, 665–698. [Google Scholar] [CrossRef]
- Horn, R.T.; Babichev, S.A.; Marzlin, K.P.; Lvovsky, A.I.; Sanders, B.C. Single-Qubit optical quantum fingerprinting. Phys. Rev. Lett. 2005, 95, 150502. [Google Scholar] [CrossRef]
- Du, J.; Zou, P.; Peng, X.; Oi, D.K.L.; Kwek, L.C.; Oh, C.H.; Ekert, A. Experimental quantum multimeter and one-qubit fingerprinting. Phys. Rev. A 2006, 74, 042319. [Google Scholar] [CrossRef]
- Xu, F.; Miguel, A.J.; Wei, K.; Wang, W.; Palacios-Avila, P.; Feng, C.; Sajeed, S.; Lütkenhaus, L.; Lo, H.-K. Experimental quantum fingerprinting with weak coherent pulses. Nat. Commun. 2015, 6, 8735. [Google Scholar] [CrossRef] [PubMed]
- Arrazola, J.M.; Lutkenhaus, N. Quantum fingerprinting with coherent states and a constant mean number of photons. Phys. Rev. A 2014, 89, 062305. [Google Scholar] [CrossRef]
- Guan, J.Y.; Xu, F.; Yin, H.L.; Li, Y.; Zhang, Y.-J.; Chen, S.-J.; Yang, X.-Y.; Li, L.; You, L.-X.; Chen, T.-Y.; et al. Observation of Quantum Fingerprinting Beating the Classical Limit. Phys. Rev. Lett. 2016, 116, 240502. [Google Scholar] [CrossRef]
- Li, F.G.; Shi, J.H. An arbitrated quantum signature protocol based on the chained CNOT operations encryption. Quantum Inf. Process 2015, 14, 2171–2181. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, F.-L.; Wang, Z.-H.; Hu, Y.-M. A New Quantum Blind Signature Scheme with BB84-State. Entropy 2019, 21, 336. https://doi.org/10.3390/e21040336
Chen F-L, Wang Z-H, Hu Y-M. A New Quantum Blind Signature Scheme with BB84-State. Entropy. 2019; 21(4):336. https://doi.org/10.3390/e21040336
Chicago/Turabian StyleChen, Feng-Lin, Zhi-Hua Wang, and Yong-Mo Hu. 2019. "A New Quantum Blind Signature Scheme with BB84-State" Entropy 21, no. 4: 336. https://doi.org/10.3390/e21040336
APA StyleChen, F.-L., Wang, Z.-H., & Hu, Y.-M. (2019). A New Quantum Blind Signature Scheme with BB84-State. Entropy, 21(4), 336. https://doi.org/10.3390/e21040336



