Abstract
In this paper, we consider a cooperative multi-hop secured transmission protocol to underlay cognitive radio networks. In the proposed protocol, a secondary source attempts to transmit its data to a secondary destination with the assistance of multiple secondary relays. In addition, there exists a secondary eavesdropper who tries to overhear the source data. Under a maximum interference level required by a primary user, the secondary source and relay nodes must adjust their transmit power. We first formulate effective signal-to-interference-plus-noise ratio (SINR) as well as secrecy capacity under the constraints of the maximum transmit power, the interference threshold and the hardware impairment level. Furthermore, when the hardware impairment level is relaxed, we derive exact and asymptotic expressions of end-to-end secrecy outage probability over Rayleigh fading channels by using the recursive method. The derived expressions were verified by simulations, in which the proposed scheme outperformed the conventional multi-hop direct transmission protocol.
1. Introduction
Security is one of the most important issues in wireless communication because of the broadcast nature of wireless medium. Conventionally, encryption/decryption algorithms that generate public/private keys are used to guarantee the security [1,2]. Recently, a security framework for the physical layer, called the wiretap channel or physical-layer security (PLS) [3,4,5,6,7,8,9,10,11], has been introduced as a potential solution. In PLS, difference between Shannon capacity of the data link and that of the eavesdropping link, named secrecy capacity, is commonly used to evaluate secrecy performance such as average secrecy capacity (ASC), secrecy outage probability (SOP) and probability of non-zero secrecy capacity (PNSC). Hence, to enhance the secrecy performance for wireless systems, researchers proposed efficient communication methods to increase channel capacity of the data links, and/or decrease that of the eavesdropping links. Indeed, in [12,13,14], opportunistic relay selection protocols are considered to enhance the quality of the data channels in one-hop and dual-hop relaying networks. In [15,16,17,18], the authors considered cooperative jamming approaches to reduce the data rate received at the eavesdroppers. The authors of [19,20,21,22,23,24,25] considered the secrecy performance enhancement for underlay cognitive radio (UCR) networks in which transmit power of secondary users (SUs) is limited by maximum interference levels required by primary users (PUs). The authors of [26,27,28,29] proposed secure communication protocols for two-way relay networks. In [30,31,32,33], the end-to-end secrecy performance of multi-hop relaying systems is investigated.
Thus far, most published works related to performance evaluation assume that transceiver hardware of wireless terminals is perfect. However, in practice, it suffers from impairments due to phase noises, amplifier–amplitude non-linearity and in phase and quadrature imbalance (IQI) [34,35,36], which significantly degrade the performance of wireless communication systems. In [37,38], the authors proposed various relay selection methods to compensate the impact of the hardware imperfection. The authors of [39] studied the outage performance of partial relay selection and opportunistic relay selection schemes in the UCR networks under the joint of hardware imperfection and interference constraint.
To the best of our knowledge, several published works evaluate the secrecy performance under the impact of imperfect transceiver hardware. In [40], the authors first studied the impact of the hardware imperfection on the secrecy capacity. In particular, the work in [40] considers the effects of IQI in one-hop OFDMA communication systems. The authors of [41] designed a secure massive MIMO system in the presence of a passive multiple-antenna eavesdropper and the hardware impairments. Reference [42] provided a power-efficient resource allocation algorithm for secure wireless-powered communication networks with the hardware noises. Taking hardware imperfection into account, the authors of [43] proposed an optimal power allocation strategy to maximize the instantaneous secrecy rate of a cooperative amplify-and-forward (AF) relaying scheme. In [44], we calculated PNSC of multi-hop relay networks over Nakagami-m fading channels in presence of the hardware impairments. The results in [44] show that the hardware impairments significantly affect on the PNSC performance.
However, there is no published work related to cooperative multi-hop PLS in the UCR networks. This motivated us to propose such a scheme and evaluate its performance. In the proposed protocol, named Cooperative Multi-Hop Transmission Protocol (CMT), a secondary source sends its data to a secondary destination via multiple secondary relays. In addition, in the secondary network, a secondary eavesdropper overhears the source data transmitted by the source and relay nodes. In addition, the secondary transmitters must adjust the transmit power to satisfy the interference constraint required by a PU and a maximal power threshold. The operation of the proposed scheme can be realized via one or many orthogonal time slots. At each time slot, the current transmitter finds an intended receiver that is nearest to the destination, and can receive the data securely and successfully. If this receiver is the destination, the data transmission ends. Otherwise, the procedure is repeated with the new selected transmitter. We also design a cooperative MAC method at each time slot for reversing the channel as well as selecting the potential receiver. For performance measurement, we first formulate the secrecy capacity under joint constraint of the limited interference and the hardware imperfection. When the hardware impairments are relaxed, we derive exact and asymptotic expressions of the end-to-end SOP over Rayleigh fading channels by using a recursive expression. Computer simulations were realized to verify the theoretical derivations as well as to show the advantages of the CMT method. The results show that the proposed scheme outperformed the conventional multi-hop direct transmission (MDT) protocol, and parameters such as the imperfect CSI estimations, the number of intermediate relays, the hardware impairment level and the position of the eavesdropper significantly affected the end-to-end SOP.
The rest of this paper is organized as follows. System model of the proposed scheme is described in Section 2. In Section 3, exact and asymptotic expressions of the end-to-end SOP for the MDT and CMT protocols are derived. The simulation results are presented in Section 4. Section 5 presents our conclusions.
2. System Model
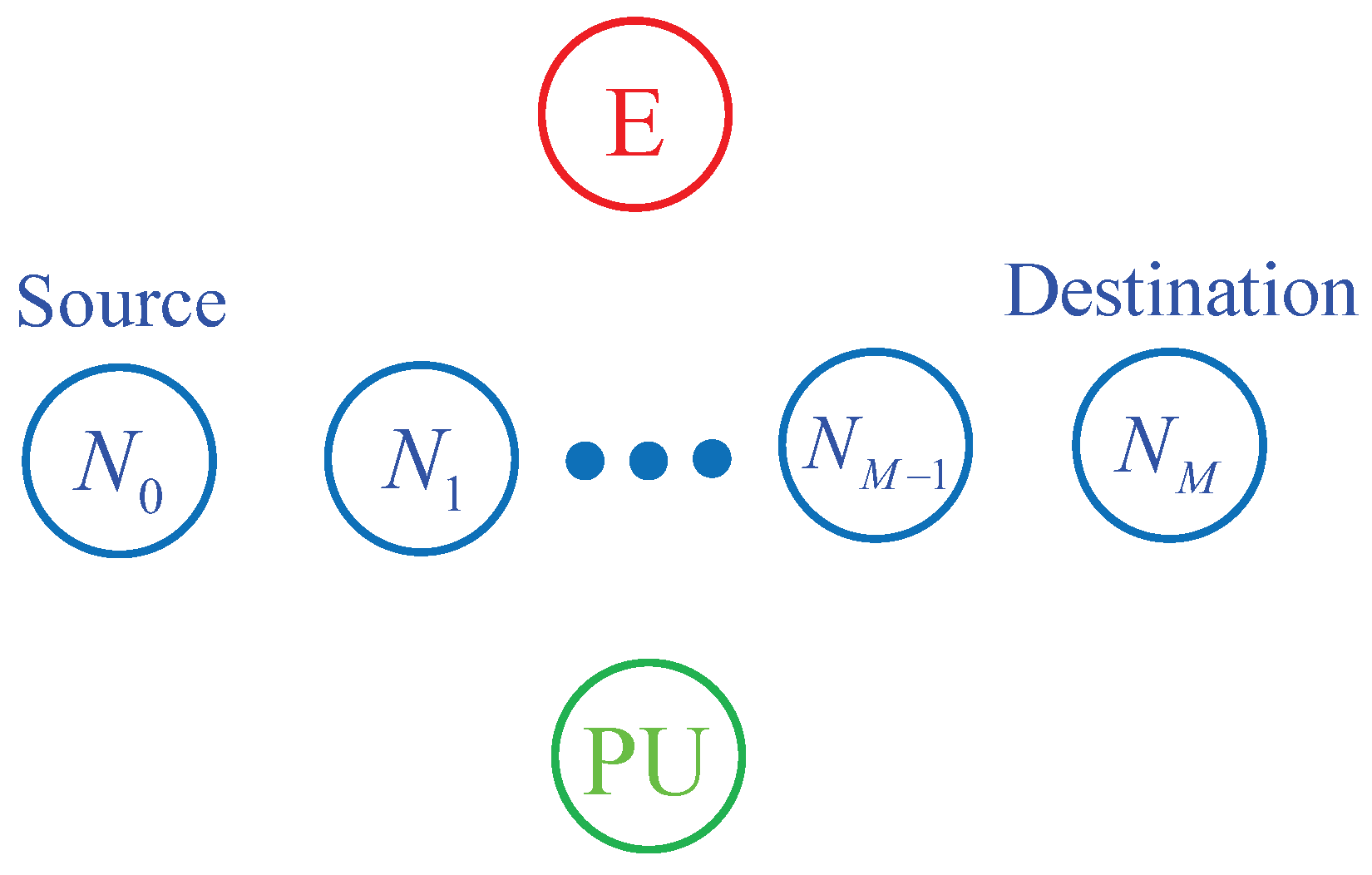
As illustrated in Figure 1, we consider an M-hop secondary network, where the source communicates with the destination via M− 1 relay nodes denoted by , , ..., . The relay nodes are numbered according to their distances to the destination, i.e., the relay is nearest and the relay is the furthest. In UCR, the source and the relay nodes must adapt the transmit power so that the co-channel interference levels caused by their transmission are below a threshold given by a primary user (PU). Moreover, the transmit power of the secondary transmitters is also limited by a maximum power . In addition, in the secondary network, the eavesdropper (E) attempts to overhear the source data transmitted by the secondary transmitters. Before describing the operation of the proposed protocol, we give assumptions used in this paper.
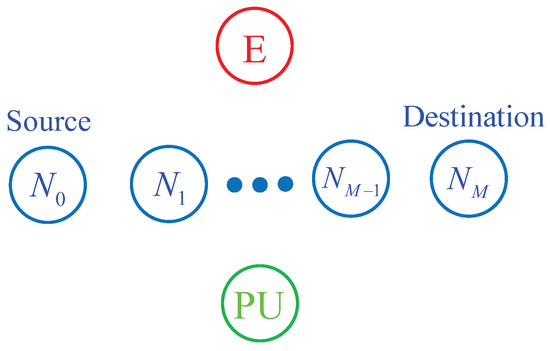
Figure 1.
System model of the proposed protocol.
We assume that all of the relays are in the radio range of the source and destination nodes. We assume that all of the nodes have a single antenna, and the data transmission is hence split into orthogonal time slots. For ease of presentation and analysis, it is assumed that all of the nodes have the same structure, and the impairment levels are the same. We also assume that the eavesdropper is an active node, and hence the secondary nodes can estimate channel state information (CSI) between themselves and the node E [45]. Next, the data transmission between two secondary nodes is considered to be secure and successful if the obtained secrecy capacity is higher than a positive threshold . Otherwise, the data are assumed to be intercepted, which is referred to as a secrecy outage event.
2.1. Channel and Hardware Impairment Models
Let , and denote distances of the , and links, respectively, where . We also denote , and as channel coefficients of , and links, respectively. Because the channels experience a Rayleigh fading distribution, the channel gains such as , and follow exponential distributions. To take path-loss into account, we can model the parameters of the random variables (RVs) and as [46]: , and , where is path-loss exponent.
Considering the data transmission between the transmitter X and the receiver Y (, ), the received data at Y is given as in [34,35,36]:
where is the source data, is the transmit power of X, is channel coefficient of the X-Y link, and are hardware noises at X and Y, respectively, and is Gaussian noise at Y.
Similar to the work in [34,35,36], , and are modeled as Gaussian random variables (RVs) with zero-mean and their variances are given, respectively, as
where and are levels of the hardware impairments at X and Y, respectively.
From Equations (1) and (2), the instantaneous signal-to-interference-plus-noise ratio (SINR) is formulated by
where is the total hardware impairment level.
Let us consider the transmit power of the node X in the underlay CR network. Firstly, is below the maximum transmit power, i.e., . Secondly, the interference caused at the PU due to the transmission of the node X must be below the interference threshold , i.e.,
Therefore, can be given as
where is assumed to be a constant.
From Equation (6), we can formulate the SINR for the and links, where , respectively, as
Moreover, when the transceiver hardware of all the nodes is perfect, i.e., , we can rewrite Equation (7) as
Hence, the secrecy capacity obtained at due to the transmission of is calculated as
where .
Moreover, as , we have
2.2. Operation of the Proposed Protocol
Next, we describe the operation of the proposed protocol, in which a MAC layer operation is designed to reverse the channel. Similar to the CoopMAC proposed in [47], in the first time slot, before transmitting the data, the source sends a request-to-send (RTS) message to the destination and all of the relays. By receiving this message, all of the nodes can estimate CSI between themselves and the source, calculate the instantaneous secrecy capacity by using Equation (9), and compare with . It is assumed that the source can exactly estimate the channel coefficients of the interference and eavesdropping links, and include these values into the RTS message. If the destination can receive the source data securely and successfully, i.e., , it will feedback a clear-to-send (CTS) message to inform. In this case, the source directly sends the data to the destination without using the relays. In the case where , the destination has to generate a non-CTS message to request the help of the relays. Now, let us denote as set of the potential relays which can receive the data securely and successfully, i.e., , where , , . To select the relay for the retransmission, we also propose a distributed relay selection method. Similar to the work in [48], the relay will set a timer given as
where A is a predetermined constant.
Then, the relay whose timer expires first will broadcast the CTS message, and it be selected to retransmit the data to the destination. We can observe from Equation (12) that the selected relay is nearest to the destination. It is worth noting that, if the set is empty (), no relay node can retransmit the data to the destination, and this case is considereda secrecy outage event. In the case where , the operation will be repeated with the new source.
Generally, at the kth time slot , assume that the current source is , and . Let denote set of relays from the node to the destination. Similarly, sends the RTS message to all of the nodes belonging to . Then, if , the destination generates the CTS message, and will directly transmit the data to . Otherwise, the potential relay which belongs to and is nearest to the destination will become the new source and repeat the process that did. Indeed, we denote as the set of the potential relays, i.e., , where , . In addition, let us denote as set of the nodes that cannot receive the data securely, where and . Then, assume that and , using the relay selection method described above, the relay will become the new source at the th time slot.
This process is only stopped when can securely and successfully receive the data or there is no relay between the current source and the destination that can securely and successfully receive the data. It is noted that, to avoid the eavesdropper and combine the received data with maximal ratio combining (MRC) technique, the source and the selected relays use randomize-and-forward (RF) method [49,50].
In the proposed protocol, to select the successful relay at each time slot correctly, the CSI estimations over the data, interference and eavesdropping links are assumed to be perfect. However, in practice, the estimations may not be correct due to the time variation of the channel, finite number of pilot symbols and noises. Hence, we will discuss this problem in the next sub-section.
2.3. Imperfect Channel Estimation
In this subsection, we consider the imperfect channel estimation at the transmitter and the receiver . From Equation (9), if wants to calculate the secrecy capacity , it has to estimate the channel coefficient correctly. In addition, has to estimate the channel coefficients and , which are then sent to through the RTS message.
Let , and denote the estimated CSIs of , and , respectively; the correlation between and ; and ; and and can be expressed, respectively as in [51]:
where , and are channel correlation factors, and , and are estimation errors. We can observe that if , all of the channel estimations are perfect. If , the channel estimations have errors, and the estimated secrecy capacity in Equation (9) is written by
where , and . Again, we note that the CSI estimation errors may lead to the incorrect relay selection, which would degrade the system performance.
2.4. Multi-Hop Direct Transmission Protocol
To show the advantages of the proposed protocol, we compared the secrecy performance of the proposed protocol with that of the conventional multi-hop direct transmission protocol (MDT) [44]. In the MDT scheme, the data are transmitted hop-by-hop from the source to the destination. Particularly, the data transmission is split into M orthogonal time slots. At the mth time slot, where , the node transmits the source data to the node . If the communication between and is secure and successful, will forward the data to the next hop in the next time slot. Otherwise, the data transmission is insecure and the secrecy outage event occurs. Similar to the MCT protocol, the source and relays in the MDT protocol use the RF technique.
3. Performance Analysis
Firstly, we can formulate SOP of the link as
where .
When the transceiver hardware is perfect , we can derive the exact closed-form expression for . At first, setting , conditioned on x can be given by
Due to the independence of and , we can write
Substituting probability density function (PDF) of the exponential RV , and the cumulative distribution function (CDF) of the exponential RV into Equation (18), after some manipulations, we obtain
Then, can be obtained from by
Furthermore, using the approximation in Equation (11), an asymptotic closed-form expression for at high P values can be provided by
3.1. Multi-hop Direct Transmission Protocol (MDT)
Because the transmission on each hop is independent, the end-to-end SOP of the MDT protocol can be given as
3.2. Cooperative Multi-Hop Transmission Protocol (CMT)
In the CMT protocol, the end-to-end SOP is expressed by a recursive expression as follows:
where is SOP at kth time slot, . Then, the end-to-end SOP of the CMT protocol is given as
Before calculating , we give an example with , where is expressed by
Equation (28) shows that there are 04 possible cases for the set , i.e., , , , . In Equation (28), the terms and can be calculated as in (32). Considering the term , which can be written by
In Equation (29), there are two possible cases for the set , i.e., , , and and are SOP at the second time slots. In addition, is calculated by Equation (32), while is expressed by
where, because the transmission between and is direct, Equation (21) is used to calculate .
Next, let us consider the term in Equation (28), where the relay will be selected for retransmitting the data to the destination. Similar to Equation (30), we have
Now, the recursive expression of is given as in Lemma 1.
Lemma 1.
When , can be expressed as
Proof.
At first, we set and , and conditioned on x and y can be given by
Then, is obtained from by
Let us consider the integral marked in Equation (34); combining the PDF and Equation (33), after some careful manipulations, we obtain
Next, substituting Equation (35) into Equation (34), and after some manipulations, we obtain Equation (32) and finish the proof.
4. Simulation Results
In this section, we present various Monte Carlo simulations to verify the theoretical results derived in Section 3. For the simulation environment, we considered a two-dimensional network in which the co-ordinate of the node , the primary user, and the eavesdropper are , and , respectively. To focus on investigating the impact of the important system parameters on the system performance, in all of the simulations, the path-loss exponent was fixed by 3.
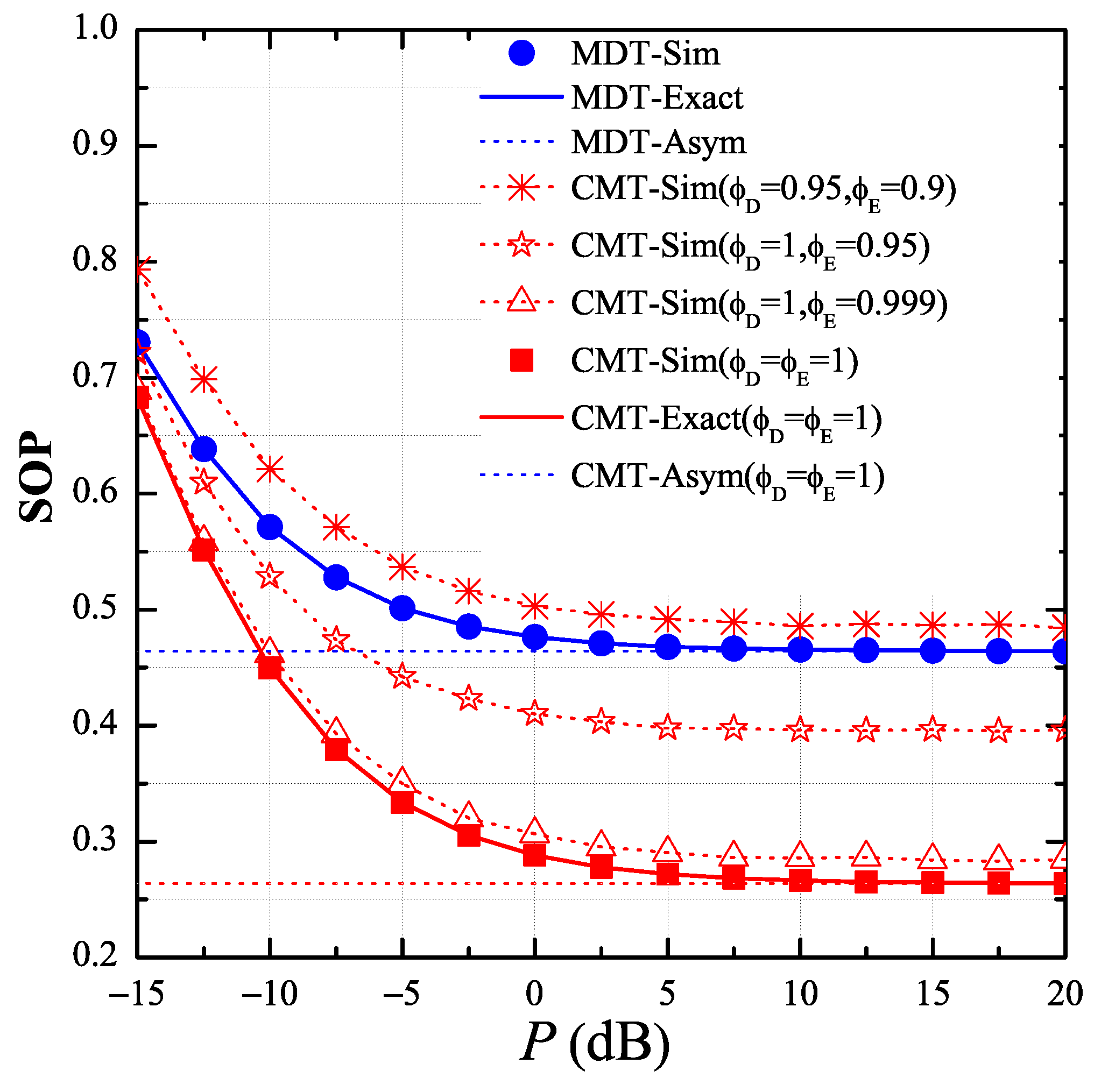
In Figure 2, we present the end-to-end SOP of the MDT and CMT protocols as a function of the transmit SNR in dB, and investigate the impact of the CSI estimation errors on the secrecy performance. In this simulation, we assumed the CSI estimations of the interference links are correct, i.e., , and the transceiver hardware is perfect, i.e., . We also set the simulation parameters as follows: the target rate , the ratio , and the number of hops M = 3. In addition, we placed the primary user and the eavesdropper at the positions and , respectively. As shown in Figure 2, when the estimations of the data and eavesdropping channels were correct, i.e., , the performance of the proposed protocol (CMT) was much better than that of the MDT protocol. However, the SOP performance of the CMT protocol significantly decreased with the CSI estimation errors. Moreover, when and , the MDT protocol outperformed the proposed protocol.
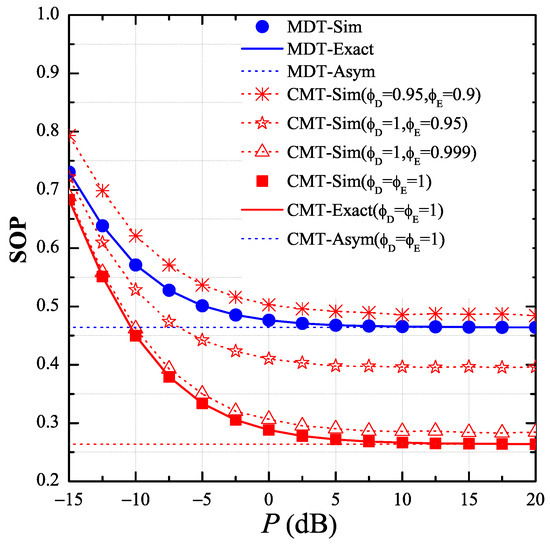
Figure 2.
End-to-end secrecy outage probability (SOP) as function of P in dB when , , , , , and .
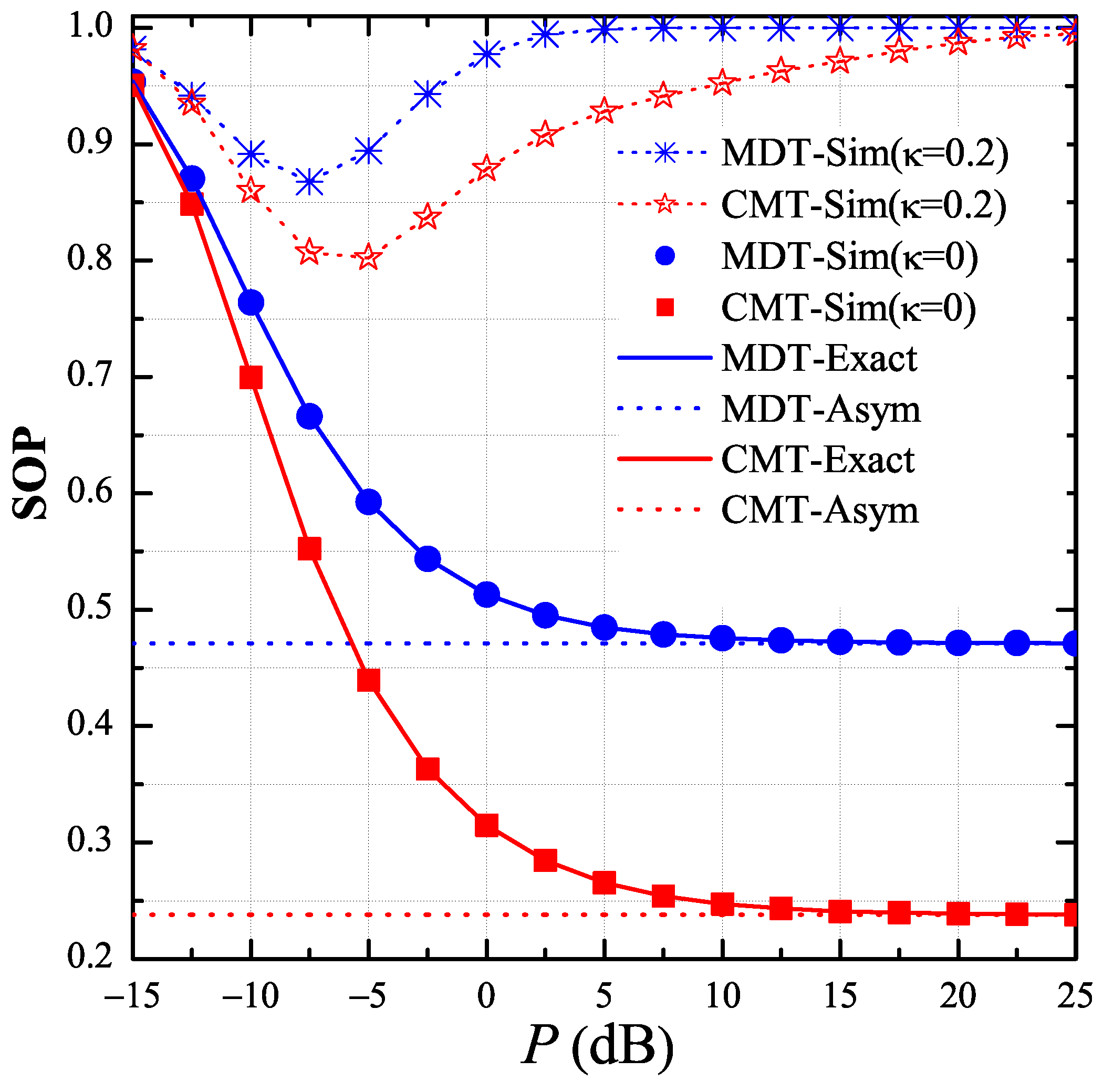
In Figure 3, we present the end-to-end SOP of the MDT and CMT protocols as a function of the transmit SNR in dB when all of the channel estimations are perfect, i.e., . As we can see, the proposed protocol (CMT) outperformed the MDT protocol for all the P values because the destination and the intermediate relays in the CMT protocol could obtain higher diversity gain as compared with those in the MDT protocol. As a result, the proposed protocol enhanced the channel capacity of the data links, which hence provided better secrecy performance. In addition, it was observed that, when the transceiver hardware was perfect , the secrecy performance of both protocols converged to the asymptotic results, which were independent of the P values. However, as , the values of SOP reached 1 at high region, which validated the statement in Section 3. Moreover, there existed a value of P at which the value of SOP was lowest. As shown in this figure, the optimal transmit SNRs in the CMT and MDT protocols were −5 dB and −7.5 dB, respectively. Finally, it is worth noting that the simulation results (Sim) match very well with the theoretical results (Exact), and, at high P regimes, the simulation results nicely converge to the asymptotic ones (Asym). These validate the correction of our derivations expressed in Section 3.
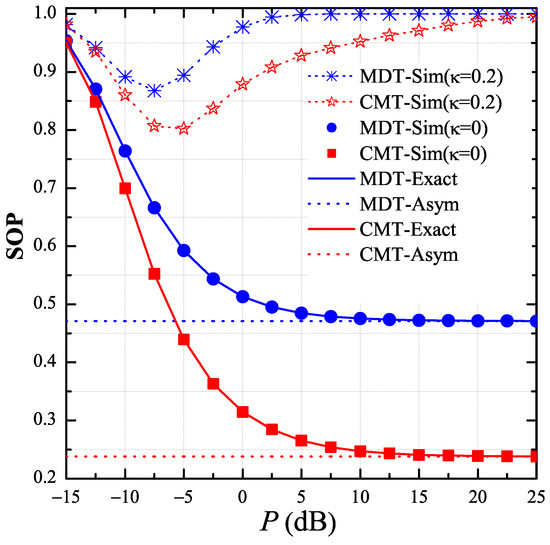
Figure 3.
End-to-end secrecy outage probability (SOP) as function of P in dB when , , , , , , and .
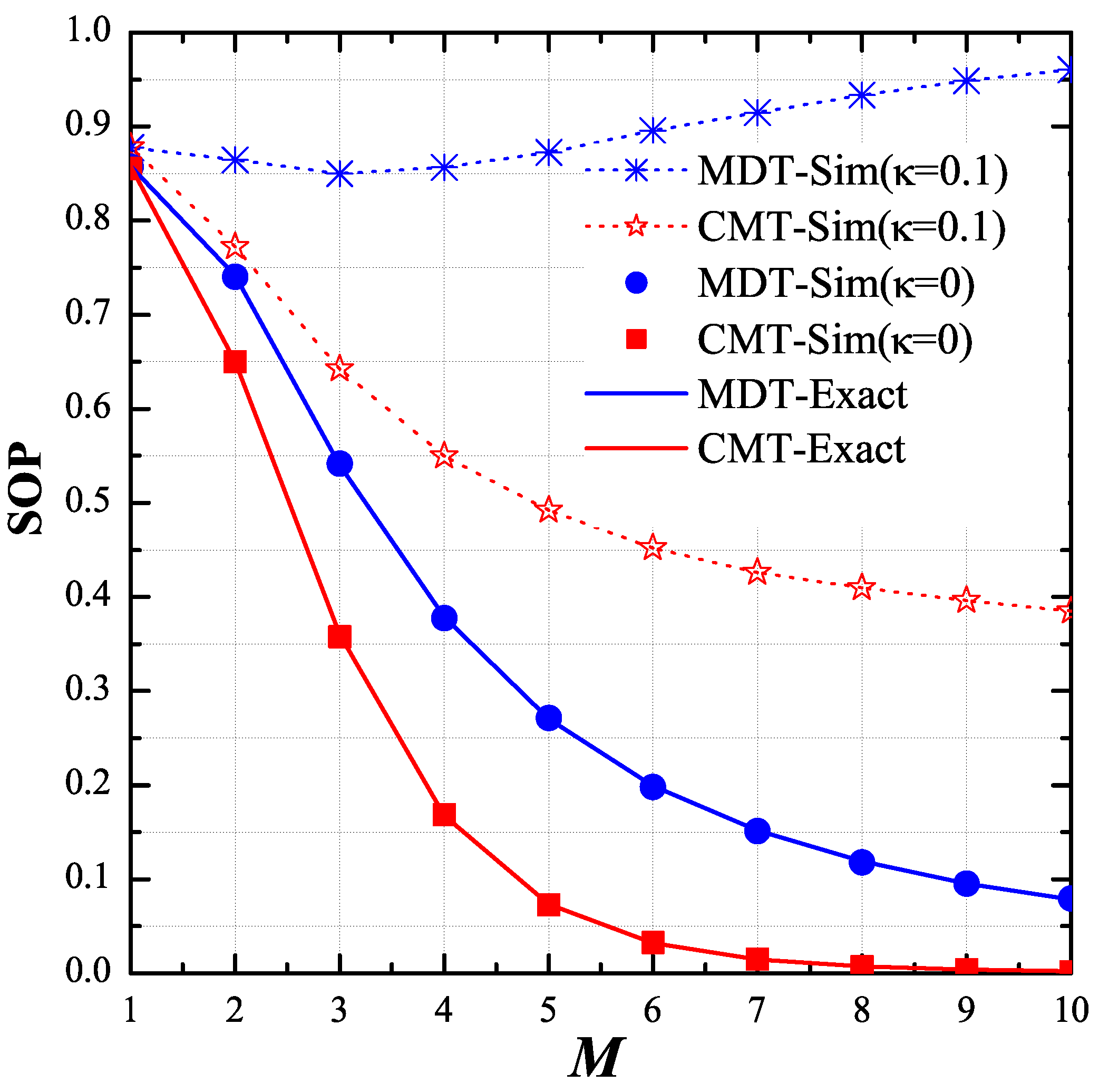
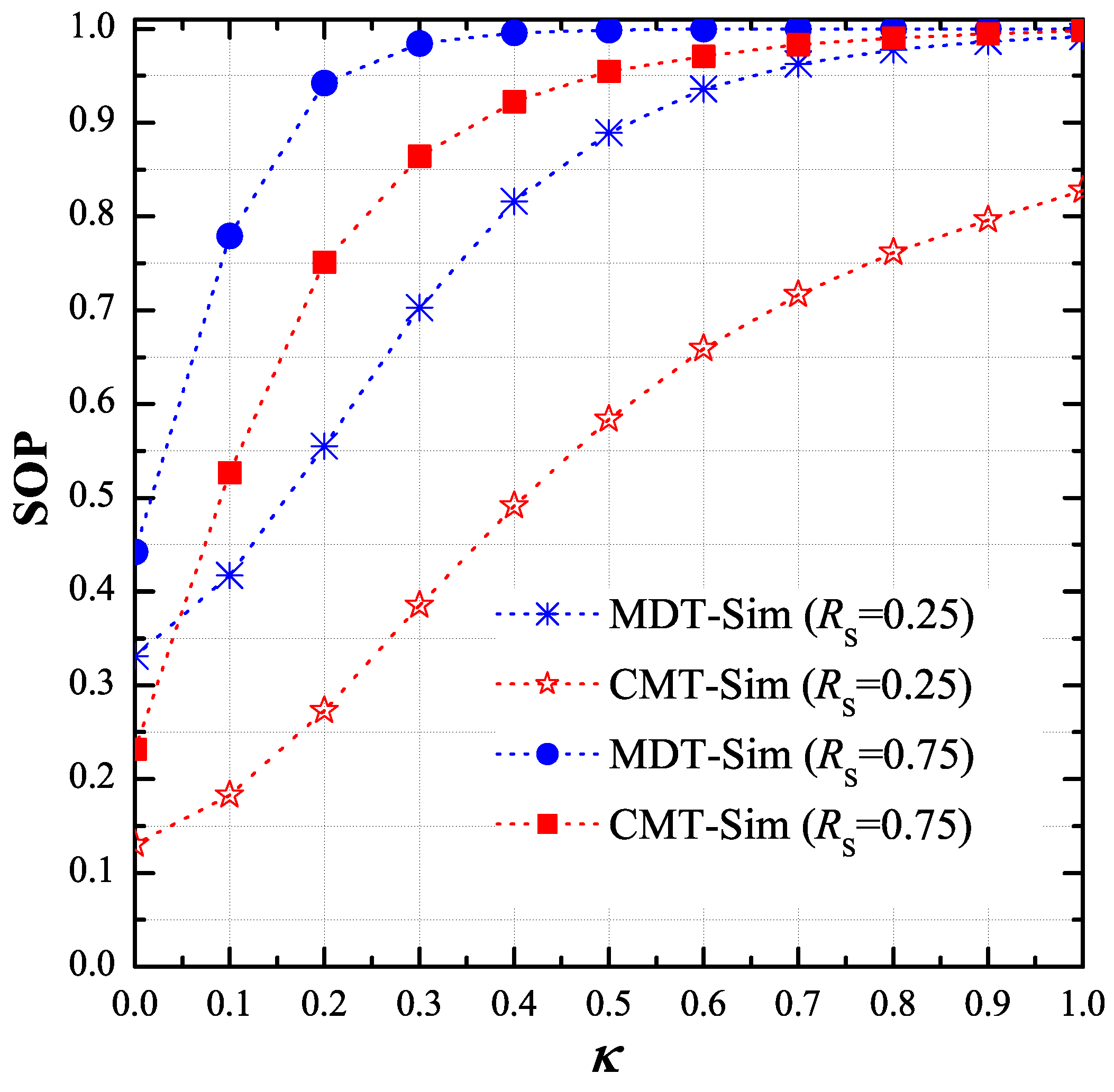
As shown in Figure 4, we changed the number of hops (M) and observed the variant of the end-to-end SOP. We assigned the values of P, , , , , , and as 5 dB, 1, 0.5, −0.5, −0.5, 0.5 and 0.5, respectively. As observed, with the perfect transceiver, the secrecy performance of the MDT and CMT protocols was better when the number of hops increased. For the CMT protocol, this result is still true with the presence of the hardware imperfection (), while the performance of the MDT protocol severely degraded with higher number of hops. Again, the results in this figure validate the theoretical results provided in the previous section.
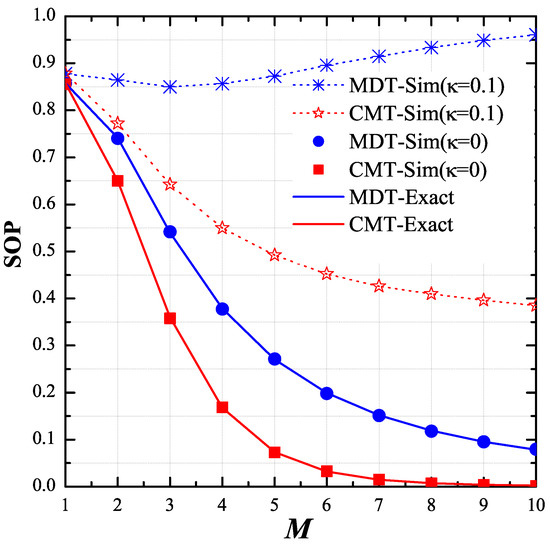
Figure 4.
End-to-end secrecy outage probability (SOP) as function of M when , , , , , , and .
Figure 5 presents the impact of the hardware impairment level on the secrecy performance of the CMT and MDT protocols when , and . Similarly, the proposed scheme obtained better performance, as compared the MDT scheme. It is also seen in Figure 5 that the SOP values rapidly increase as the value increases. In addition, the performance of the considered methods significantly enhanced with lower value of the target rate .
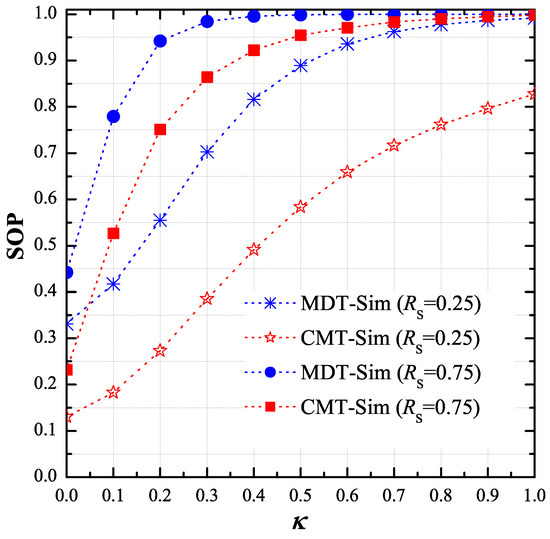
Figure 5.
End-to-end secrecy outage probability (SOP) as function of when , , , , , , and .
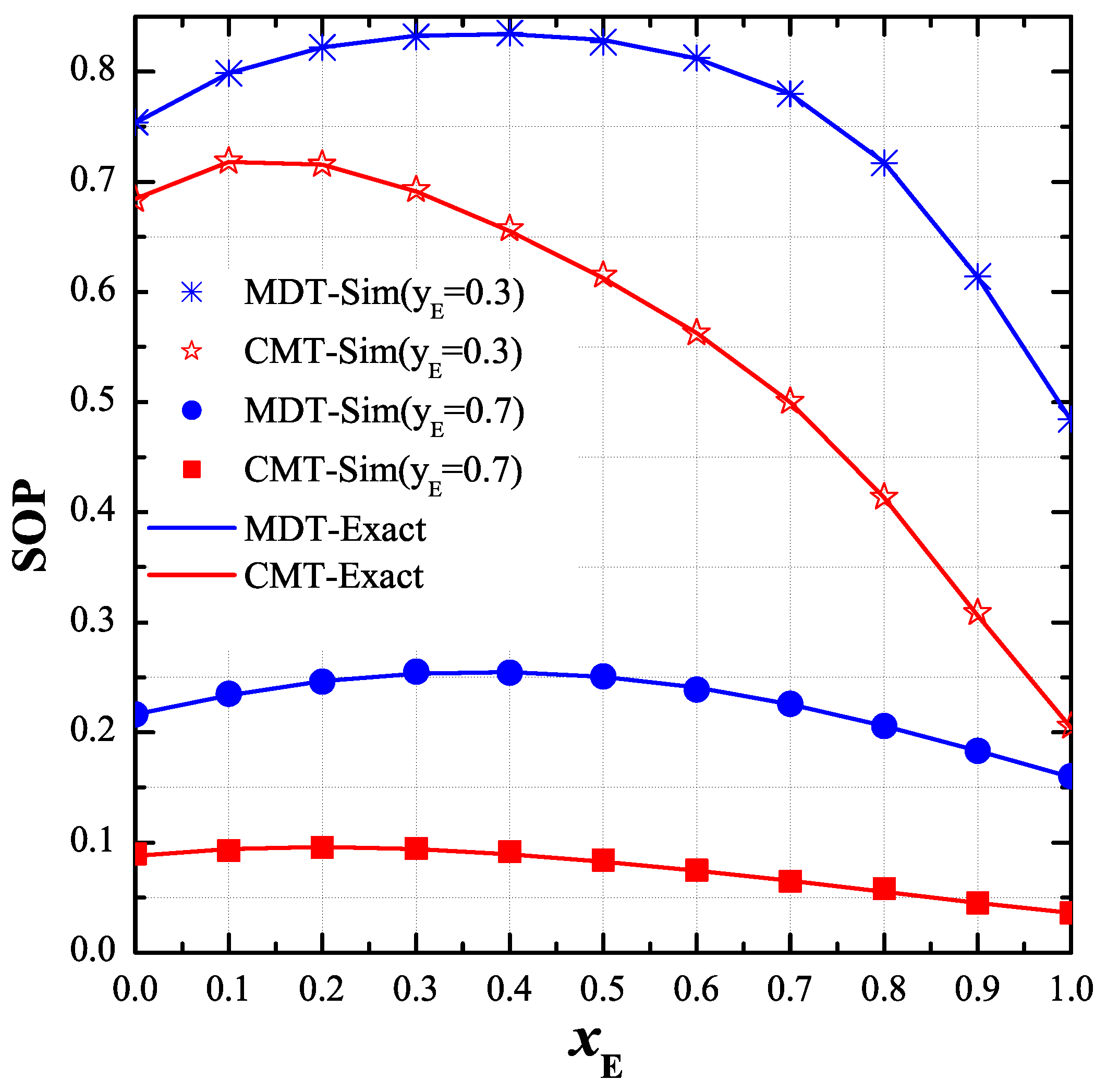
As shown in Figure 6, we studied the effect of the positions of the eavesdropper on the end-to-end SOP. In particular, we fixed the value of while changing from 0 to 1. The remaining parameters were set as: , , , , , and . It can be seen that the end-to-end SOP of the CMT protocol mostly decreased with the increasing of , while that of the MDT increased at small value and decreased at high region. We can see in this figure that the performance of the MDT protocol was worst when was about 0.4.
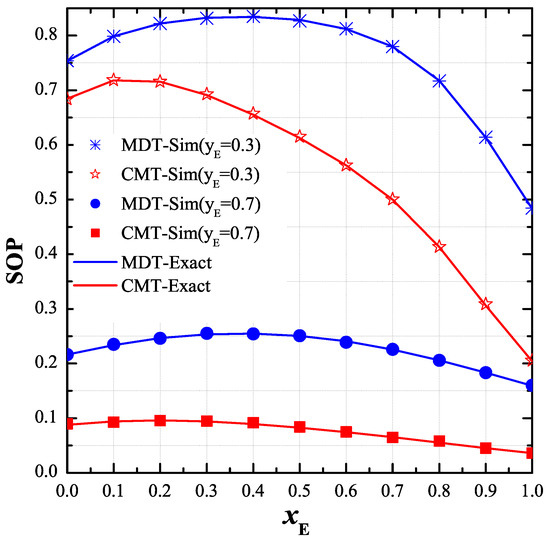
Figure 6.
End-to-end secrecy outage probability (SOP) as function of when , , , , , , and .
5. Conclusions
In this paper, we propose the cooperative multi-hop transmission protocol (CMT) in the UCR networks with the presence of an eavesdropper. Because the proposed scheme uses cooperative multi-hop transmission, it significantly outperforms the conventional multi-hop direct transmission protocol (MDT), in terms of the end-to-end secrecy outage probability (SOP). The interesting results obtained in this paper can be listed as follows:
- The secrecy performance of the proposed protocol was much better than that of the MDT protocol when the CSI estimations of the data, interference and eavesdropping links were perfect. Otherwise, the SOP performance significantly degraded due to the incorrect relay selection.
- When the transceiver hardware of the nodes was imperfect, the secrecy performance severely degraded. In particular, the value of the end-to-end SOP rapidly increased with higher transmit signal-to-noise ratio (SNR) and with higher impairment level.
- In the presence of the hardware noises, there existed an optimal value of the transmit SNR, at which the secrecy performance of the CMT and DMT schemes was best.
- The performance of the proposed protocol was better when the number of hops was higher.
- When the hardware impairments were relaxed, we derived exact and asymptotic expressions of the end-to-end SOP for the CMT and MDT protocols. We then performed computer simulations to verify the derived expressions.
Author Contributions
P.T.T., D.T.H. and T.N.N. created the main ideas and executed the performance evaluation by extensive simulations. T.T.D. and M.V. worked as the advisers of P.T.T., D.T.H. and T.N.N. to discuss, create, and advise the main ideas and performance evaluations together.
Acknowledgments
This research received support from the grant SGS reg. No. SP2019/41 conducted at VSB Technical University of Ostrava, Czech Republic and was partially funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2017.317.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ledwaba, L.P.I.; Hancke, G.P.; Venter, H.S.; Isaac, S.J. Performance Costs of Software Cryptography in Securing New-Generation Internet of Energy Endpoint Devices. IEEE Access 2018, 6, 9303–9323. [Google Scholar] [CrossRef]
- Liu, Z.; Choo, K.-K.R.; Grossschadl, J. Securing Edge Devices in the Post-Quantum Internet of Things Using Lattice-Based Cryptography. IEEE Commun. Mag. 2018, 56, 158–162. [Google Scholar] [CrossRef]
- Wyner, A.D. The Wire-tap Channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Csiszar, I.; Korner, J. Broadcast Channels With Confidential Messages. IEEE Trans. Inf. Theory 1978, 24, 339–348. [Google Scholar] [CrossRef]
- Gopala, P.K.; Lai, L.; Gamal, H.E. On the secrecy capacity of fading channels. IEEE Trans. Inf. Theory 2008, 54, 4687–4698. [Google Scholar] [CrossRef]
- Zhang, J.; Duong, T.Q.; Woods, R.; Marshall, A. Securing Wireless Communications of the Internet of Things from the Physical Layer, An Overview. Entropy 2017, 19, 420. [Google Scholar] [CrossRef]
- Chang, S.; Li, J.; Fu, X.; Zhang, L. Energy Harvesting for Physical Layer Security in Cooperative Networks Based on Compressed Sensing. Entropy 2017, 19, 462. [Google Scholar] [CrossRef]
- Sun, L.; Du, Q. A Review of Physical Layer Security Techniques for Internet of Things: Challenges and Solutions. Entropy 2018, 20, 730. [Google Scholar] [CrossRef]
- Wang, L.; Wong, K.-K.; Jin, S.; Zheng, G.; Heath, R.W. A New Look at Physical Layer Security, Caching, and Wireless Energy Harvesting for Heterogeneous Ultra-Dense Networks. IEEE Commun. Mag. 2018, 56, 49–55. [Google Scholar] [CrossRef]
- Kong, L.; Vuppala, S.; Kaddoum, G. Secrecy Analysis of Random MIMO Wireless Networks Over α-μ Fading Channels. IEEE Trans. Veh. Technol. 2018, 67, 11654–11666. [Google Scholar] [CrossRef]
- Jameel, F.; Wyne, S.; Kaddoum, G.; Duong, T.Q. A Comprehensive Survey on Cooperative Relaying and Jamming Strategies for Physical Layer Security. IEEE Commun. Surv. Tutor. 2018. [Google Scholar] [CrossRef]
- Krikidis, I. Opportunistic Relay Selection For Cooperative Networks With Secrecy Constraints. IET Commun. 2010, 4, 1787–1791. [Google Scholar] [CrossRef]
- Zhong, B.; Zhang, Z. Secure Full-Duplex Two-Way Relaying Networks With Optimal Relay Selection. IEEE Commun. Lett. 2017, 21, 1123–1126. [Google Scholar] [CrossRef]
- Kuhestani, A.; Mohammadi, A.; Mohammadi, M. Joint Relay Selection and Power Allocation in Large-Scale MIMO Systems With Untrusted Relays and Passive Eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2018, 13, 341–355. [Google Scholar] [CrossRef]
- Hu, L.; Wen, H.; Wu, B.; Pan, F.; Liao, R.-F.; Song, H.; Tang, J.; Wang, X. Cooperative Jamming for Physical Layer Security Enhancement in Internet of Things. IEEE Int. Things J. 2018, 5, 219–228. [Google Scholar] [CrossRef]
- Ma, H.; Cheng, J.; Wang, X.; Ma, P. Robust MISO Beamforming With Cooperative Jamming for Secure Transmission From Perspectives of QoS and Secrecy Rate. IEEE Trans. Commun. 2018, 66, 767–780. [Google Scholar] [CrossRef]
- Zhang, G.; Xu, J.; Wu, Q.; Cui, M.; Li, X.; Lin, F. Wireless Powered Cooperative Jamming for Secure OFDM System. IEEE Trans. Veh. Technol. 2018, 67, 1331–1346. [Google Scholar] [CrossRef]
- Hu, L.; Wen, H.; Wu, B.; Tang, J.; Pan, F.; Liao, R.-F. Cooperative-Jamming-Aided Secrecy Enhancement in Wireless Networks With Passive Eavesdroppers. IEEE Trans. Veh. Technol. 2018, 67, 2108–2117. [Google Scholar] [CrossRef]
- Singh, A.; Bhatnagar, M.R.; Mallik, R.K. Secrecy Outage of a Simultaneous Wireless Information and Power Transfer Cognitive Radio System. IEEE Wirel. Commun. Lett. 2016, 5, 288–291. [Google Scholar] [CrossRef]
- Lei, H.; Zhang, H.; Ansari, I.S.; Pan, G.; Qaraqe, K.A. Secrecy Outage Analysis for SIMO Underlay Cognitive Radio Networks over Generalized-K Fading Channels. IEEE Sig. Process. Lett. 2016, 23, 1106–1110. [Google Scholar] [CrossRef]
- Zhao, R.; Yuan, Y.; Fan, L.; He, Y.-C. Secrecy Performance Analysis of Cognitive Decode-and-Forward Relay Networks in Nakagami-m Fading Channels. IEEE Trans. Commun. 2017, 65, 549–563. [Google Scholar] [CrossRef]
- Chakraborty, P.; Prakriva, S. Secrecy Outage Performance of a Cooperative Cognitive Relay Network. IEEE Commun. Lett. 2017, 21, 326–329. [Google Scholar] [CrossRef]
- Al-Hraishawi, H.; Baduge, G.A.A.; Schaefer, R.F. Artificial Noise-Aided Physical Layer Security in Underlay Cognitive Massive MIMO Systems with Pilot Contamination. Entropy 2017, 19, 349. [Google Scholar] [CrossRef]
- Hung, T.; Georges, K.; Gagnon, F.; Louis, S. Cognitive Radio Network with Secrecy and Interference Constraints. Phys. Commun. 2017, 22, 32–41. [Google Scholar]
- Ping, X.; Ling, X.; Honghai, W.; Jung, T.S.; Ilsun, Y. Cooperative Jammer Selection for Secrecy Improvement in Cognitive Internet of Things. Sensors 2018, 18, 42–57. [Google Scholar]
- Feng, R.; Li, Q.; Zhang, Q.; Qin, J. Robust Secure Beamforming in MISO Full-Duplex Two-Way Secure Communications. IEEE Trans. Veh. Technol. 2016, 65, 408–414. [Google Scholar] [CrossRef]
- Sun, C.; Liu, K.; Zheng, D.; Ai, W. Secure Communication for Two-Way Relay Networks with Imperfect CSI. Entropy 2017, 19, 522. [Google Scholar] [CrossRef]
- Jameel, F.; Wyne, S.; Ding, Z. Secure Communications in Three-Step Two-Way Energy Harvesting DF Relaying. IEEE Commun. Lett. 2018, 22, 308–311. [Google Scholar] [CrossRef]
- Zhang, J.; Tao, X.; Wu, H.; Zhang, X. Secure Transmission in SWIPT-Powered Two-Way Untrusted Relay Networks. IEEE Access 2018, 6, 10508–10519. [Google Scholar] [CrossRef]
- Lee, J.-H.; Sohn, I.; Kim, Y.-H. Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks. Sensors 2016, 16, 1726. [Google Scholar] [CrossRef] [PubMed]
- Alotaibi, E.R.; Hamdi, K.A. Secure Relaying in Multihop Communication Systems. IEEE Commun. Lett. 2016, 20, 1120–1123. [Google Scholar] [CrossRef]
- Yao, J.; Liu, Y. Secrecy Rate Maximization With Outage Constraint in Multihop Relaying Networks. IEEE Commun. Lett. 2018, 22, 304–307. [Google Scholar] [CrossRef]
- Keshav, S.; Ku, M.-L.; Biswas, S.; Ratnarajah, T. Energy-Efficient Subcarrier Pairing and Power Allocation for DF Relay Networks with an Eavesdropper. Energies 2017, 10, 1953. [Google Scholar]
- Björnson, E.; Matthaiou, M.; Debbah, M. A new look at dual-hop relaying: Performance limits with hardware impairments. IEEE Trans. Commun. 2013, 61, 4512–4525. [Google Scholar] [CrossRef]
- Matthaiou, M.; Papadogiannis, A. Two-Way Relaying Under The Presence of Relay Transceiver Hardware Impairments. IEEE Commun. Lett. 2013, 17, 1136–1139. [Google Scholar] [CrossRef]
- Björnson, E.; Hoydis, J.; Kountouris, M.; Debbah, M. Massive MIMO Systems With Non-Ideal Hardware: Energy Efficiency, Estimation, and Capacity Limits. IEEE Trans. Inf. Theory 2014, 60, 7112–7139. [Google Scholar] [CrossRef]
- Guo, K.; Guo, D.; Zhang, B. Performance Analysis of Two-Way Multi-Antenna Multi-Relay Networks with Hardware Impairments. IEEE Access 2017, 5, 15971–15980. [Google Scholar] [CrossRef]
- Balti, E.; Guizani, M.; Hamdaoui, B.; Khalfi, B. Aggregate Hardware Impairments Over Mixed RF/FSO Relaying Systems With Outdated CSI. IEEE Trans. Commun. 2018, 66, 1110–1123. [Google Scholar] [CrossRef]
- Sharma, P.K.; Upadhyay, P.K. Cognitive relaying with transceiver hardware impairments under interference constraints. IEEE Commun. Lett. 2016, 20, 820–823. [Google Scholar] [CrossRef]
- Boulogeorgos, A.A.; Karas, D.S.; Karagiannidis, G.K. How Much Does I/Q Imbalance Affect Secrecy Capacity? IEEE Commun. Lett. 2016, 20, 1305–1308. [Google Scholar] [CrossRef]
- Zhu, J.; Ng, D.W.K.; Wang, N.; Schober, R.; Bhargava, V.K. Analysis and Design of Secure Massive MIMO Systems in the Presence of Hardware Impairments. IEEE Trans. Wirel. Commun. 2017, 16, 2001–2016. [Google Scholar] [CrossRef]
- Boshkovska, E.; Ng, D.W.K.; Dai, L.; Schober, R. Power-Efficient and Secure WPCNs with Hardware Impairments and Non-Linear EH Circuit. IEEE Trans. Commun. 2018, 66, 2642–2657. [Google Scholar] [CrossRef]
- Kuhestani, A.; Mohamadi, A.; Wong, K.-K.; Yeoh, P.L.; Moradikia, M.; Khandaker, M.R.A. Optimal Power Allocation by Imperfect Hardware Analysis in Untrusted Relaying Networks. IEEE Trans. Wirel. Commun. 2018, 17, 4302–4314. [Google Scholar] [CrossRef]
- Tin, P.T.; Hung, D.T.; Duy, T.T.; Voznak, M. Analysis of Probability of Non-zero Secrecy Capacity for Multi-hop Networks in Presence of Hardware Impairments over Nakagami-m Fading Channels. RadioEngineering 2016, 25, 774–782. [Google Scholar]
- Wang, L.; Kim, K.J.; Duong, T.Q.; Elkashlan, M.; Poor, H.V. Security Enhancement of Cooperative Single Carrier Systems. IEEE Trans. Inf. Forensics Secur. 2015, 10, 90–103. [Google Scholar] [CrossRef]
- Laneman, J.N.; Tse, D.N.C.; Wornell, G.W. Cooperative Diversity in Wireless Networks: Efficient Protocols and Outage Behavior. IEEE Trans. Inform. Theory 2004, 50, 3062–3080. [Google Scholar] [CrossRef]
- Liu, P.; Tao, Z.; Lin, Z.; Erkip, E.; Panwar, S. Cooperative Wireless Communications: A Cross-layer Approach. IEEE Wirel. Commun. 2006, 13, 84–92. [Google Scholar]
- Bletsas, A.; Khisti, A.; Reed, D.P.; Lippman, A. Simple Cooperative Diversity Method based on Network Path Selection. IEEE J. Sel. Areas Commun. 2006, 24, 659–672. [Google Scholar] [CrossRef]
- Mo, J.; Tao, M.; Liu, Y. Relay Placement for Physical Layer Security: A Secure Connection Perspective. IEEE Commun. Lett. 2012, 16, 878–881. [Google Scholar]
- Cai, C.; Cai, Y.; Yang, W.; Yang, W. Secure Connectivity Using Randomize-and-Forward Strategy in Cooperative Wireless Networks. IEEE Commun. Lett. 2013, 17, 1340–1343. [Google Scholar]
- Vo, N.Q.B.; Duong, T.Q.; Tellambura, C. On the Performance of Cognitive Underlay Multihop Networks with Imperfect Channel State Information. IEEE Trans. Commun. 2013, 61, 4864–4873. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).