Non-Volatile Memory Forensic Analysis in Windows 10 IoT Core
Abstract
:1. Introduction
1.1. Problem Discussed and Research Motivation
1.2. Contributions
- We study the current state of IoT forensics, explaining how the characteristics of the environment affect an investigation, and why traditional forensic techniques cannot provide a functional approach to be applied in this context.
- We present a review of the proposals from the community regarding IoT security and forensics.
- We conduct a forensic examination of the non-volatile memory of the Windows 10 IoT Core operating system. With this contribution, we address the study of a, forensically speaking, unknown operating system, thereby offering guidelines on how its analysis, acquisition, and evaluation should be carried out. This allows investigators to be able to rely on previous work when examining this system, easing the process.
- We list the relevant information that can be retrieved from the storage of Windows 10 IoT Core and which may be useful in a forensic investigation. This serves as a handbook to quickly observe what data can be extracted from the system and where it is located.
- We present a forensic tool to automatize the collection of these artifacts. This provides investigators with an IoT-specific program to properly study the non-volatile memory of Windows 10 IoT Core, instead of having to rely on general tools to perform this task.
2. Windows 10 IoT Core
- Startup application, namely Windows 10 IoT Core Default App, to graphically interact with the system.
- Secure Boot: UEFI located security feature to only allow the execution of trusted applications signed by known authorities.
- Bitlocker encryption.
- Device Guard: allows the execution of only trusted code, identifying the firmware, drivers and applications that should run on the device [7].
- Cortana (no longer available since version 1809).
- PowerShell.
- Windows Update.
- Bluetooth.
- Web, SSH, and FTP Server.
- Compatibility with Arduino boards.
- Miracast.
- WiFi Direct.
- Other hardware compatibility such as WiFi Adapters, Ethernet Adapters, Cameras, NFC, RFID, and multiple sensors.
3. Related Work
3.1. IoT Security
3.2. IoT Forensics
4. Analysis Method
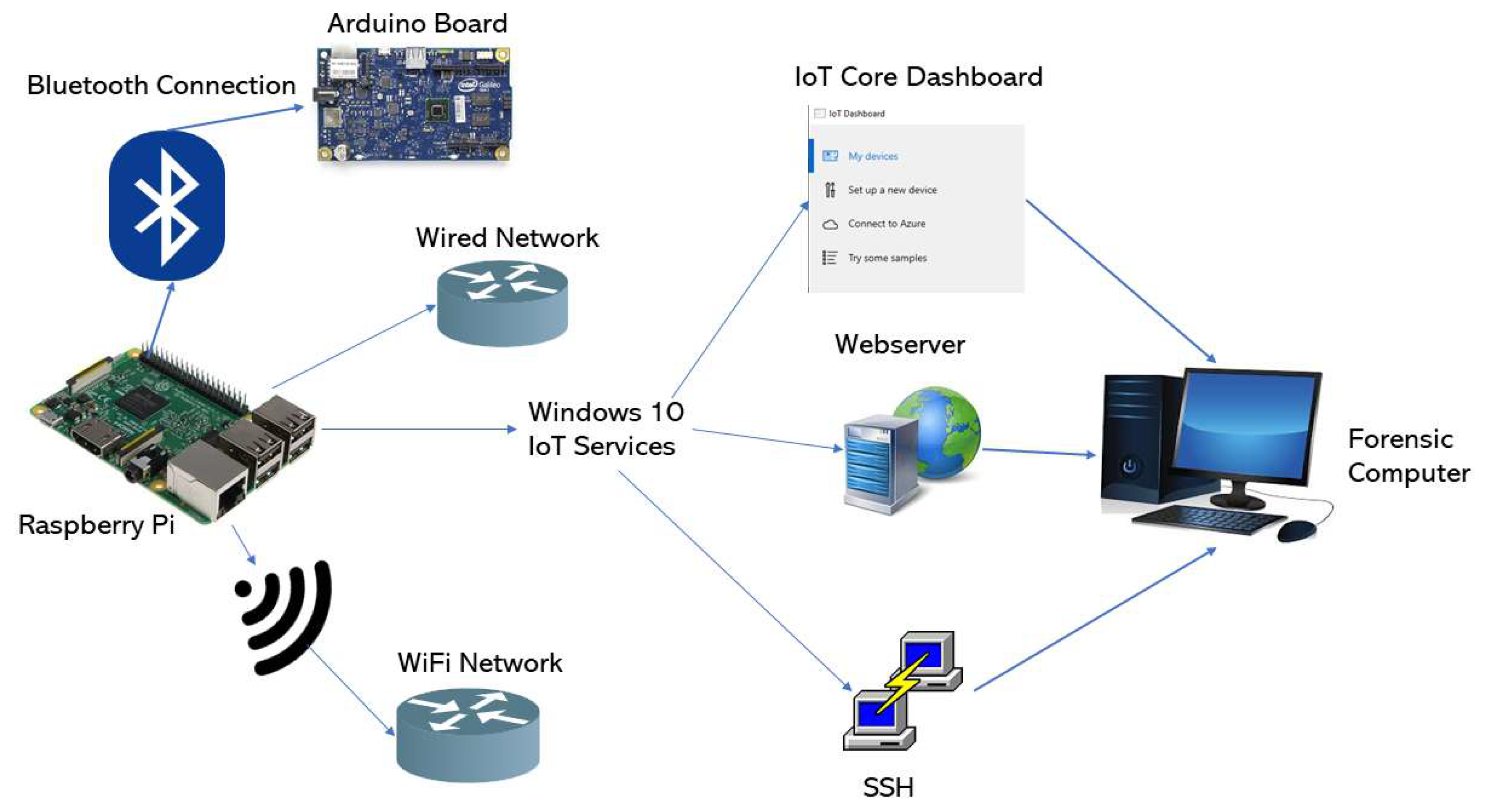
4.1. Test Environment
- Raspberry Pi Model 3 B: host of the Windows 10 IoT operating system.
- 32 Gigabyte microSD Card: non-volatile memory of the Raspberry Pi, as it does not include soldered storage.
- Windows IoT Core Build 17763: IoT version of Windows 10 released in February 2019.
- Desktop PC with Windows 10 and the Windows 10 IoT Core Dashboard application: acts as the forensic computer and it is also used to set up the Raspberry Pi and afterward connect to the device using the Windows 10 IoT Core Dashboard.
- Arduino board: used to test the connectivity of the system with other devices. To be specific, it is an Intel Galileo.
- Operative WiFi network: needed to study the effects of using a WiFi network on the device.
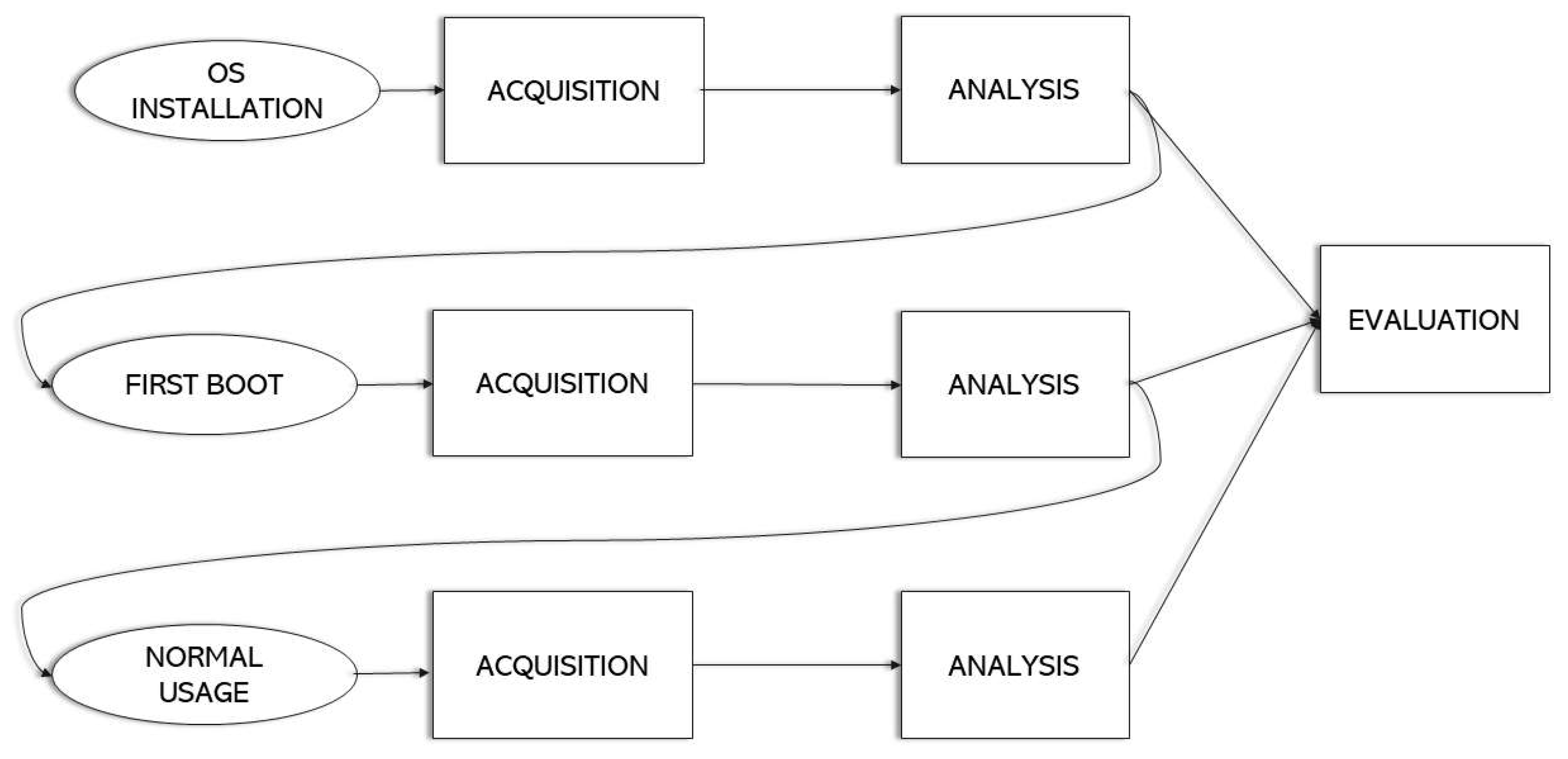
4.2. Methodology
- Pre-process: preparation work that is executed before the start of the investigation, such as tool set up or warrant obtention.
- Acquisition and Preservation: refers to the identification, acquisition, collection, transportation, storage and preservation of the data.
- Analysis: study of the acquired data to extract information and draw conclusions.
- Presentation: documentation of the findings obtained and submission of the report to the authorities or the requester of the investigation.
- Post-process: relates to the closing of the investigation. Actions such as the return of the evidence are carried out in this phase.
4.2.1. Pre-Process
- OS installation. This scenario allows us to study the system in its conception before any usage data is injected into it. The aim of this analysis is to comprehend how the data is distributed in the storage and to have a first contact with the operating system when it has not generated very much information. In addition, we examine what resources are used to configure the operating system in order to prepare for use. To create this scenario, after the microSD card has been sanitized, the “Windows 10 IoT Core Dashboard” program is launched, and the operating system is flashed into the storage. Once the installation process has finished, the microSD card is acquired and analyzed.
- First boot. In this case, we are trying to understand what information the operating system contains once it has been configured and is ready for the user to work with. Therefore, the system is studied when it is booted for the first time. All the terms are accepted, and the privacy settings are left at their default values. When the boot process has finished and the main screen is shown, the device is shut down and the non-volatile memory is acquired and analyzed.
- Normal usage. Lastly, the goal is to study the data generated by the operating system when the user has interacted with it. To achieve this, all the features of the system are explored: apps are installed and deployed, the settings are changed to fit the user preferences, a wired network and a wireless one are set up, connections with the IoT device are established using the Windows IoT Core Dashboard, services such as SSH and the web server are used, and the Arduino Board is paired via Bluetooth. After that, the storage is acquired and analyzed.
- FTK imager: used for the acquisition of the non-volatile memory and for analysis purposes, since it has browsing and mounting capabilities [36].
- Autopsy: allows the investigator to browse through the storage, apply filters and recover deleted files [37].
- QPhotorec: data carving tool to recover the deleted files from a filesystem [38].
- Registry explorer: analysis tool that enables the browsing of the Windows registry [39].
- RegRipper: extract and interprets the data stored in the Windows registry hives [40].
- MFTExplorer: graphical viewer to display the content of the master file table (MFT) [39].
- AnalyzeMFT: parser to extract information from the MFT file in an NTFS filesystem [41].
- ESEDatabaseView: utility to read the data inside an extensible storage engine (ESE) database [42].
4.2.2. Acquisition
- If the system is on, it is shut down. To do so, first, the system is turned off using the menu of the operating system, and then the Raspberry Pi is disconnected from the power supply. This guarantees that the storage does not suffer any damage or data loss.
- The microSD card is extracted from the board and inserted into a microSD to SD card adapter with write blockage capabilities.
- The adapter is then inserted into the forensic computer, making sure that the write blocker is on.
- The FTK Imager tool is launched and an image file of the storage is created.
- Once the image file is created, the hash value of the image is compared with that of the microSD card in order to guarantee that the data has not been altered.
- Finally, the image file is copied into a different storage location to ensure that at least one other copy is available in case the first one gets damaged.
4.2.3. Analysis
- Analysis of the existing partitions in the storage, determining their purpose and what directories they contain.
- Examination of the directories of the different partitions to understand the operating system structure. These first two tasks are performed using Autopsy and FTK Imager.
- Study of the purpose of the different directories and what possible sources of evidence can be found in them. In this case, multiple tools are used to browse through the storage and to read the different file types that it contains.
- Carving of the deleted files in the filesystem to determine whether any relevant file has been removed. To do so, the QPhotorec tool is used.
- Comparison of the files stored in the microSD card between the different acquisitions, obtaining the hash value for each of the files to understand how the information varies on each partition depending on the actions that are executed on the system.
4.2.4. Evaluation
5. Forensic Evidence in Windows 10 IoT Core
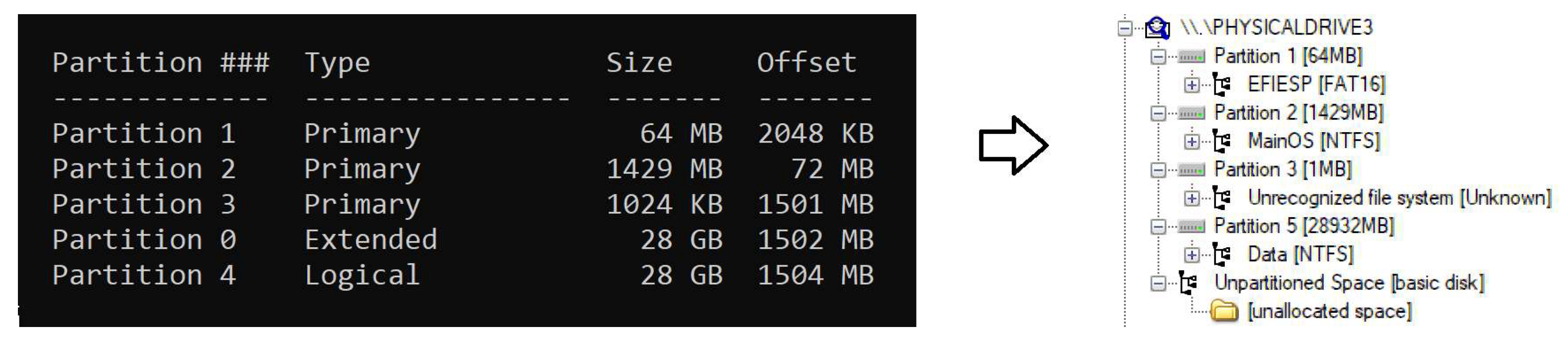
5.1. Partitions
- EFIESP: FAT 16 Extensible Firmware Interface system partition in charge of the booting process, in which boot loaders, applications and drivers that are launched by the UEFI firmware are stored. Its size is 63.7 Megabytes.
- MainOS: NTFS partition behaving as the system root directory that is launched by Windows Boot Loader when the device is turned on. Its size is 1.39 Gigabytes.
- Data: NTFS partition used by the system to store most of the information. It is the largest of all three available, and its size varies depending on the microSD card capacity since it takes all the space that is available after the creation of the “EFIESP” and “MainOS” partitions.
5.2. Directories
5.2.1. EFIESP
5.2.2. MainOS
5.2.3. Data
5.3. NTFS Filesystem
5.4. Registry
- System registry hives: they are located in Windows/System32/config.
- –
- COMPONENTS: holds data associated with Windows Update configuration and status [45].
- –
- DEFAULT: profile for the Local System account. Used by programs and services that run as Local System such as winlogon or logonui [46].
- –
- DRIVERS: stores the drivers installed on the machine and their dependencies.
- –
- SAM: contains information used by the Security Accounts Manager. Among other data, it contains usernames and passwords.
- –
- SECURITY: collects local security information used by the system and network.
- –
- SOFTWARE: stores program variables and settings that apply to all the device users.
- –
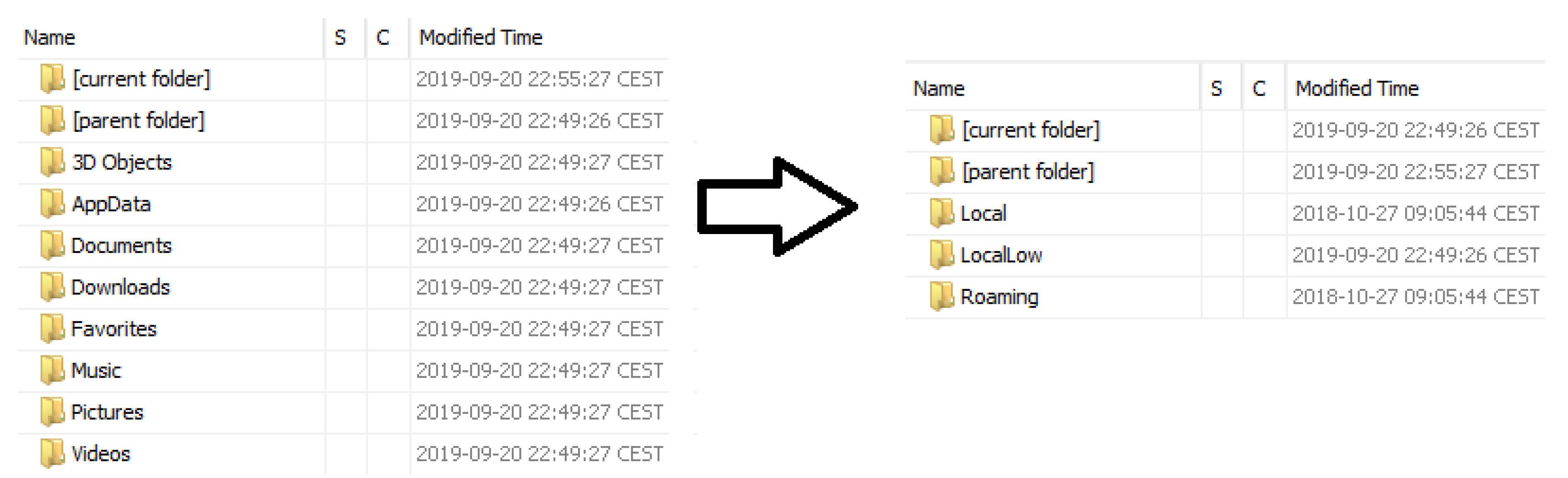
- User registry hives: stored in the corresponding user directory and in Users\∗user∗\AppDate\Local\Microsoft\Windows.
- Device details, such as number of cores, amount of storage and memory.
- Partitions on the system.
- Location of the Default Application, Temp, Program Files and Common Files paths, among others.
- Packages installed in the system.
- Digital certificates.
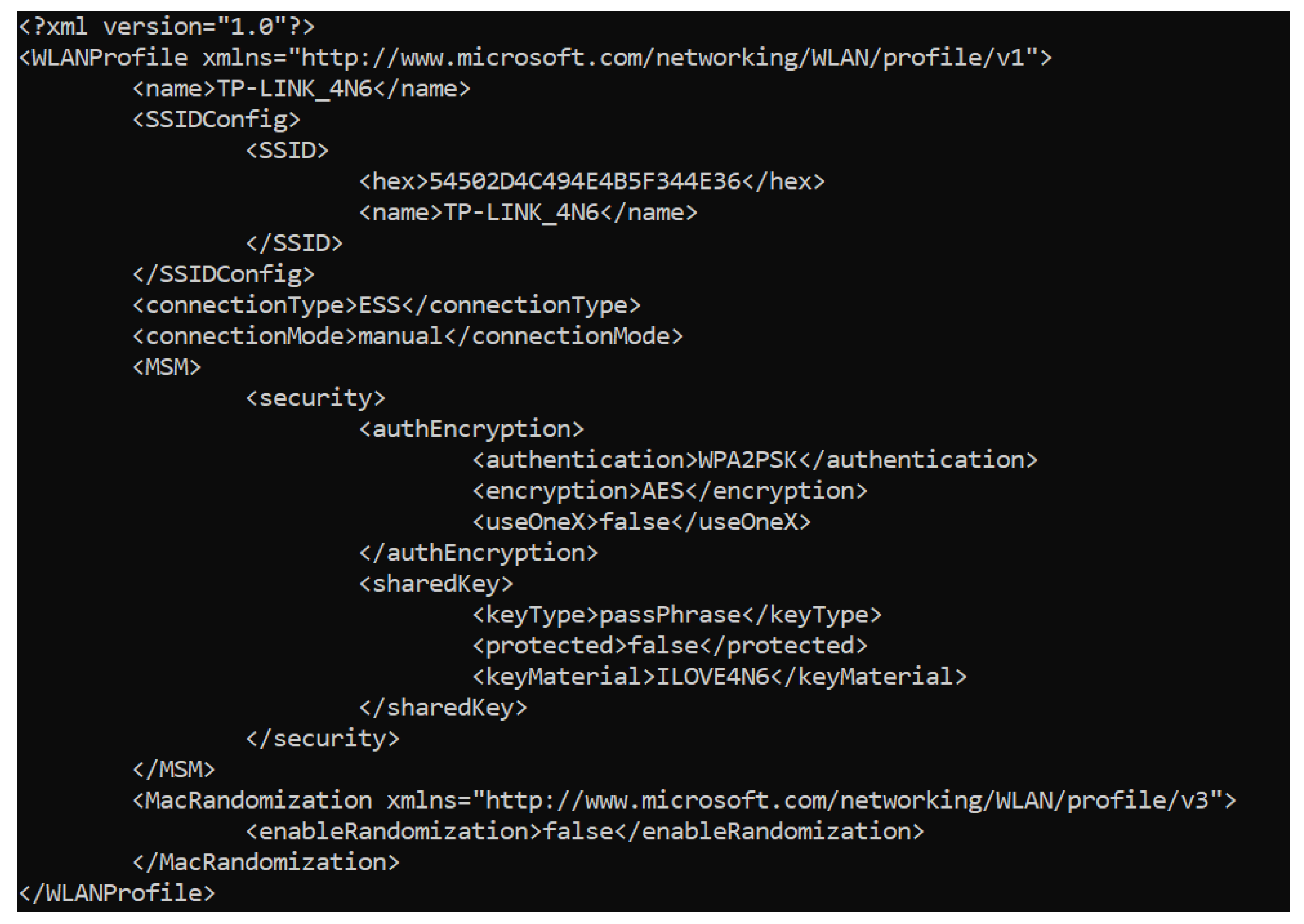
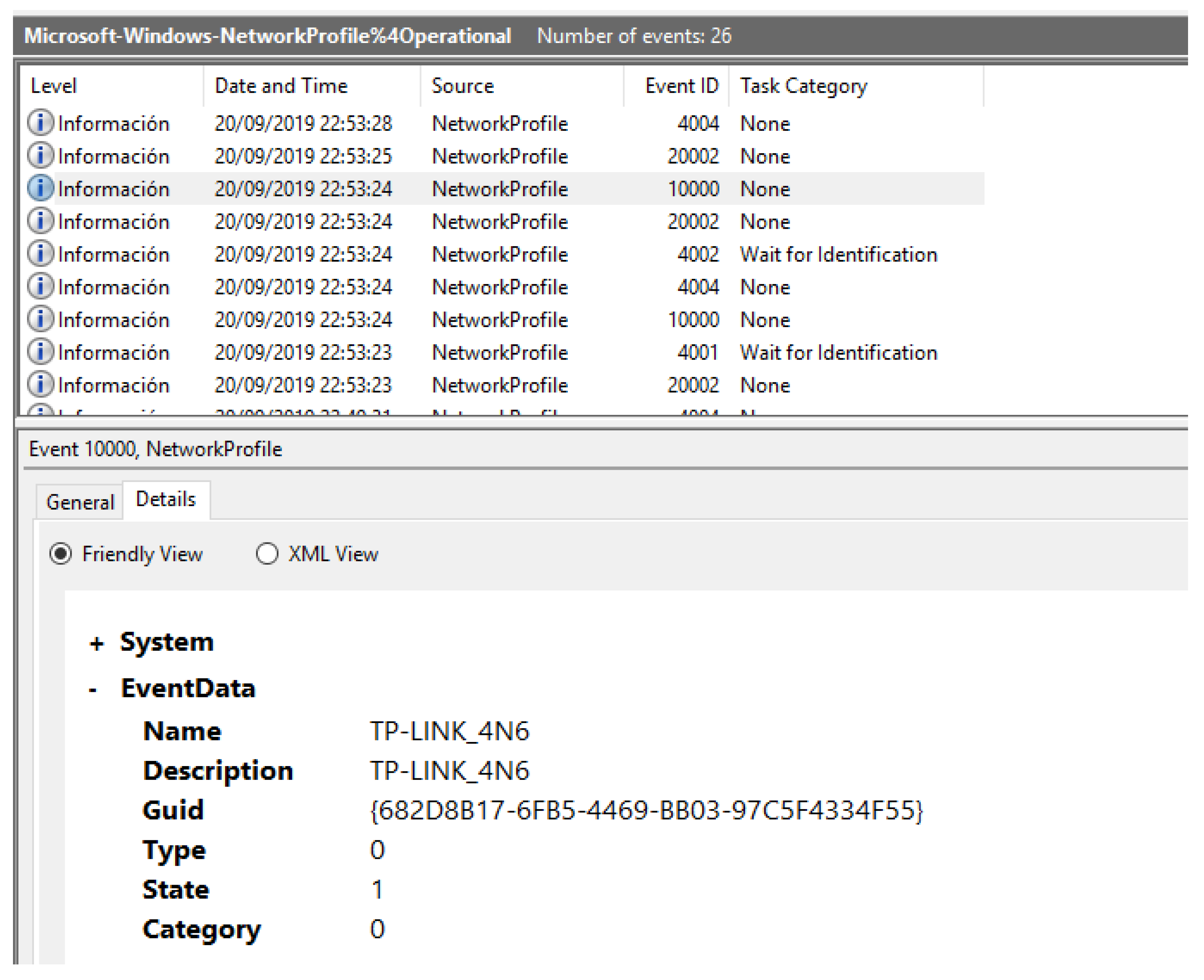
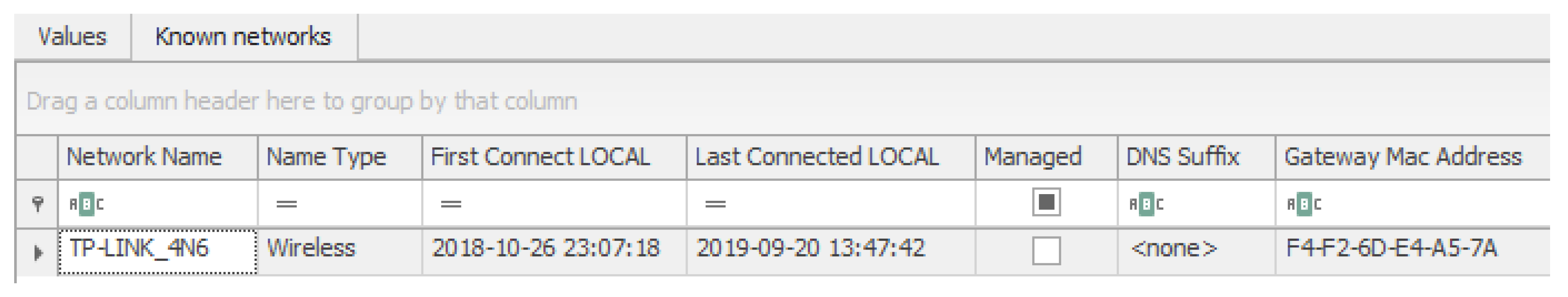
- Network profiles.
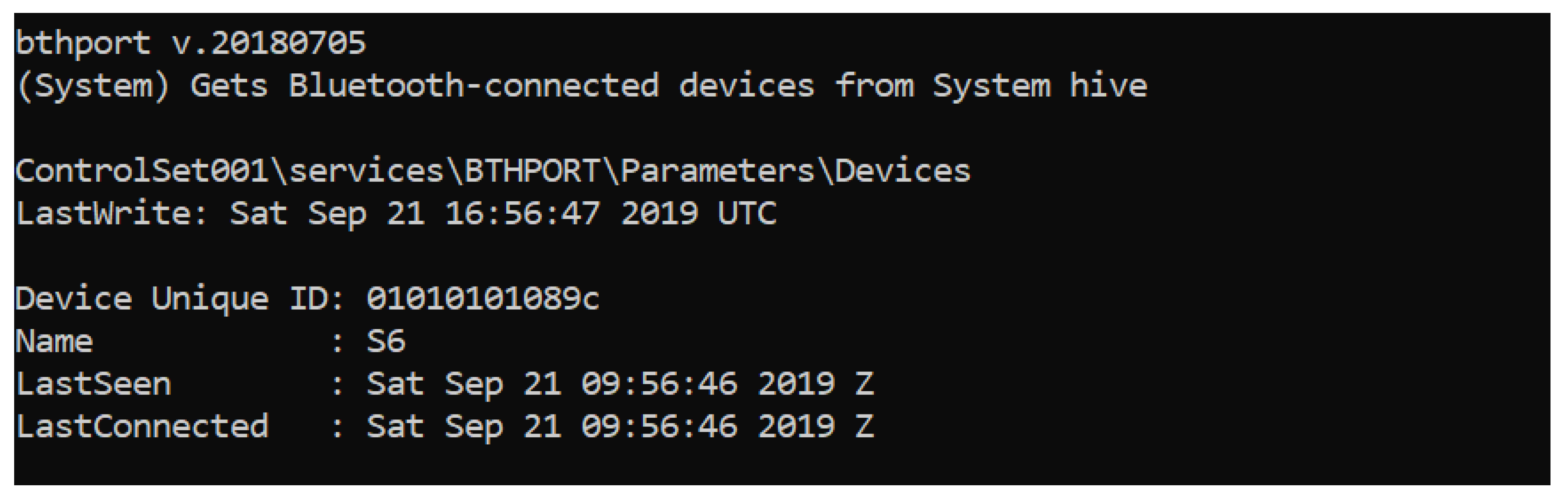
- Bluetooth devices paired.
- Mounted devices.
- USBs connected.
- Drivers installed.
- Browser history and settings.
5.5. System Events
- Application: activities regarding the software and components installed on the system.
- Security: data regarding the Windows system audit policies.
- Setup: data about the control of domains.
- OpenSSH: information about the log attempts, launch, and stop of the SSH server can be recovered.
- Network profile: data regarding the network and the connection type of the system, as well as information of when the system disconnected from it.
- Windows update: events are created when an update is found or downloaded.
- AppXDeploymentServer: information regarding the packages that have been installed and uninstalled on the system.
5.6. Users
- DefaultAccount: system managed account, member of the System Managed Accounts Group. This is the account used to log into the system every time that the operating system boots.
- DevToolsUser: account used to develop UWP applications.
- System: administrator account used by the system with maximum privileges to access all the data.
- Administrator: account for administering the computer protected by password, and set during the SD creation process. This is the user required by the Windows 10 IoT Core Dashboard application in order to connect to the system.
- Guest: restricted account for guests to access the system. Disabled by default.
- WDAGUtilityAccount: disabled account managed and used by the system for Windows Defender Application Guard scenarios.
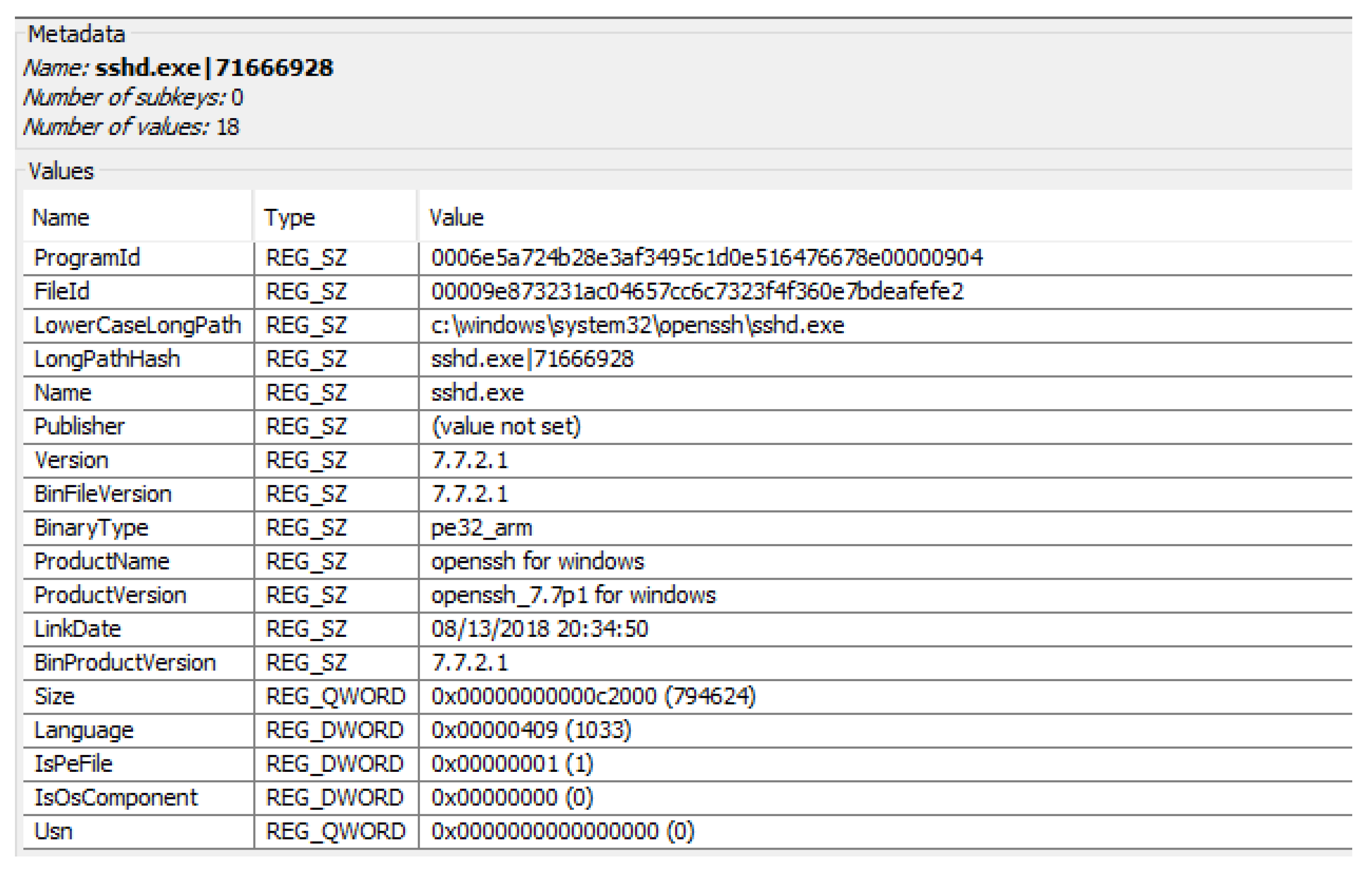
- sshd: non-privileged account that has no info about its purpose but, as its name shows, it is used by the system to manage the OpenSSH service.
5.7. Apps
- A directory is created for the app in \Programs\WindowsApp, where it will be installed.
- The packages needed for the app are stored in \ProgramData\Microsoft\Windows\AppRepository\Packages.
- The user information of the app is saved in their local directory: \Users\DefaultAccount\AppDate\Local\Packages\.
5.8. Browser
- Users\DefaultAccount\AppData\Local\Microsoft\Windows\WebCache.
- Users\DefaultAccount\AppData\Local\Microsoft\Windows\INetCache.
- Users\DefaultAccount\AppData\Local\Microsoft\Windows\INetCookies.
5.9. Bluetooth and WiFi Connections
5.10. Pagefile and Hiberfil
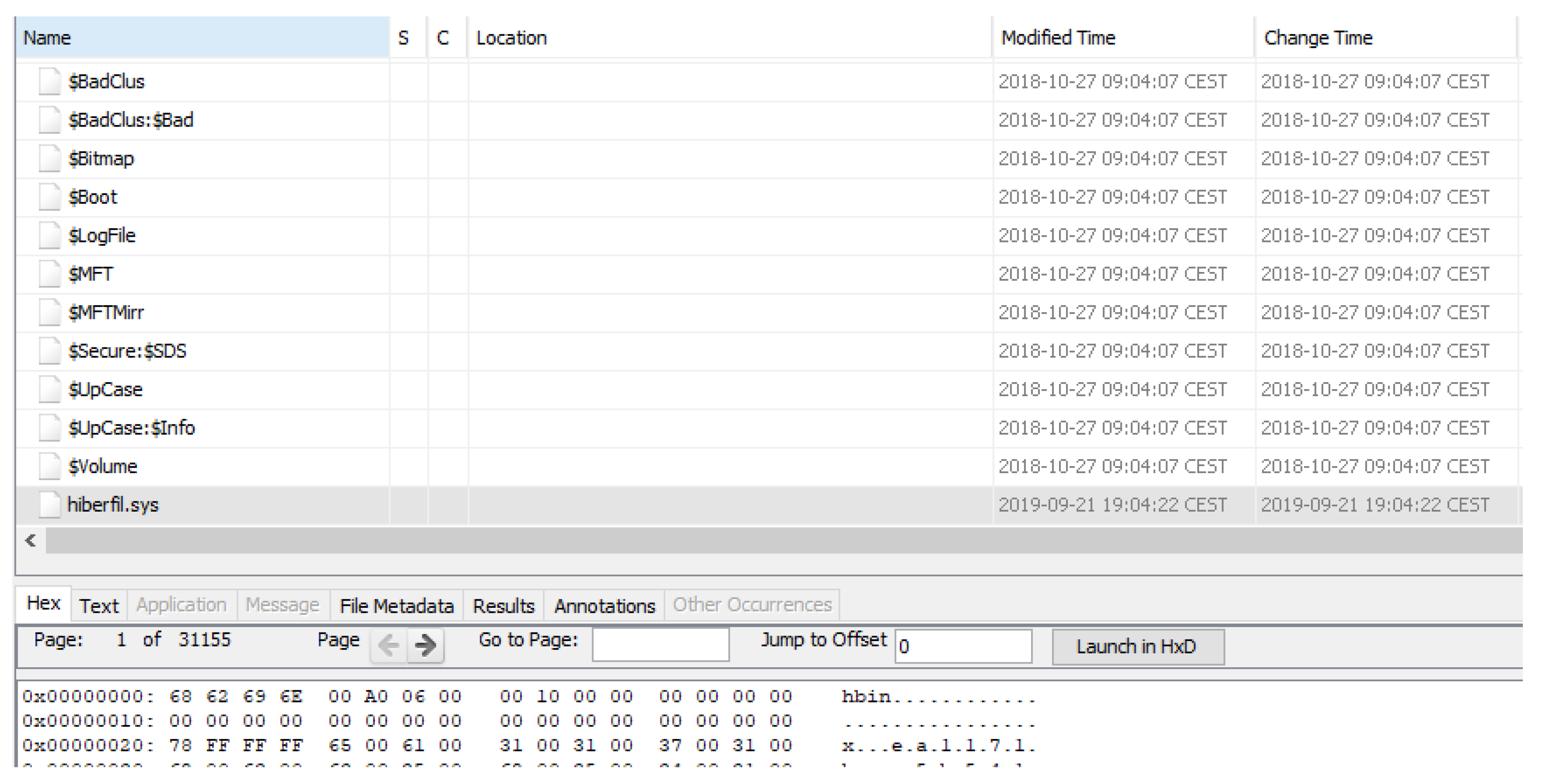
- Hiberfil: file used to save the state of the device when the system is put in hibernation mode. It contains data that, instead of being stored in RAM memory, is saved temporarily in the storage before shutting down the system, and then recovered when it restarts, such as user passwords, deleted files, connections established or information about running processes, among other data. As can be seen in Figure 14, after enabling the hibernation mode and putting the system in that state, the file is created.
- Pagefile: contains data temporarily exchanged between RAM memory and persistent storage. This occurs when the system needs more space available in physical memory, so virtual memory is created through paging, therefore storing a piece of information about RAM memory in the pagefile file. In order to analyze it, a tool such as Volatility [53] must be used to interpret the file content.
6. Proposed Tool for Evidence Retrieval from the Windows 10 IoT Core Non-volatile Memory
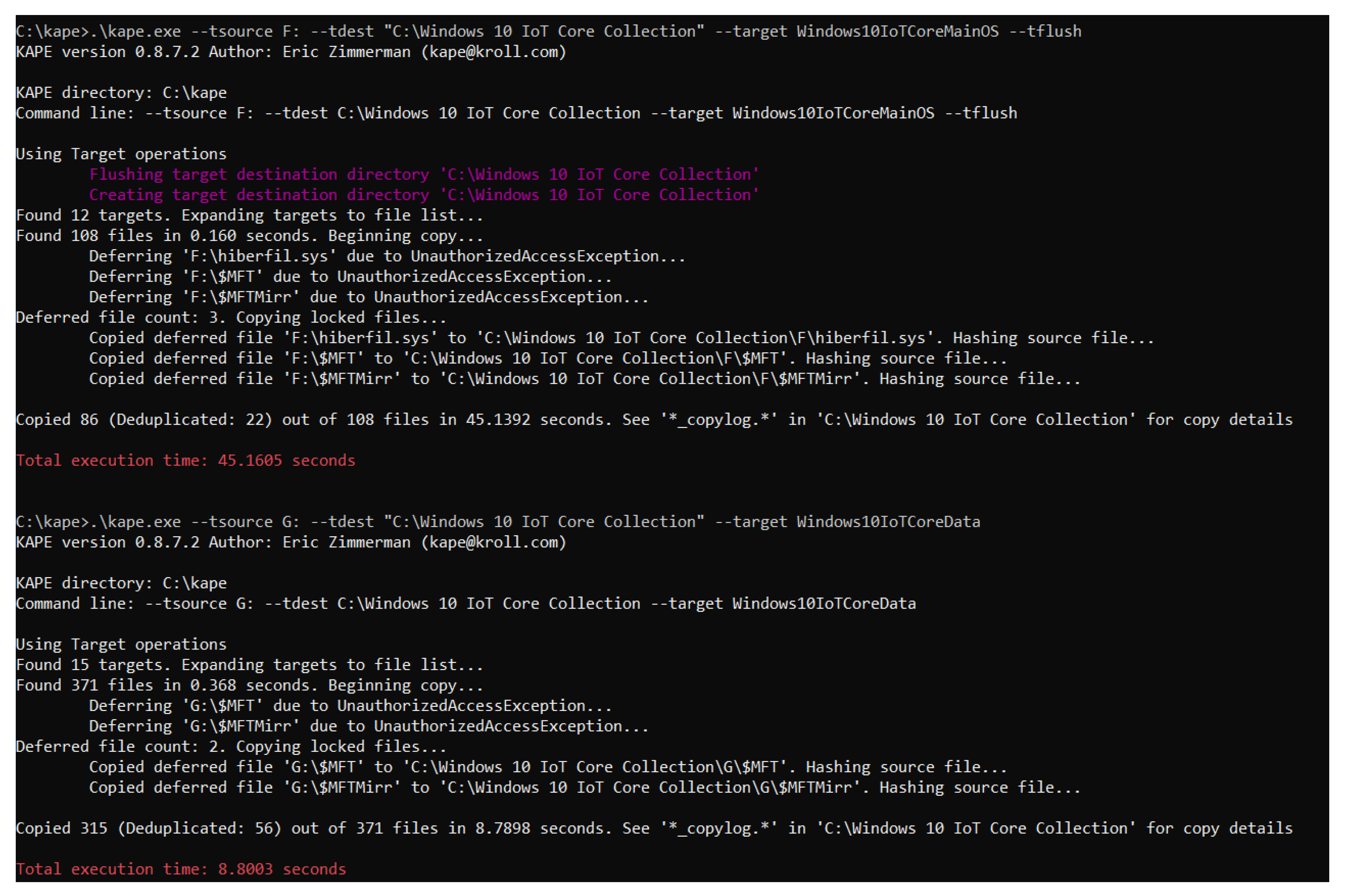
6.1. KAPE
- Targets: some examples of what data can be recovered by the tool are:
- –
- Evidence of execution, shortcut files and jump lists.
- –
- Metadata of the filesystem.
- –
- Antivirus logs.
- –
- User files.
- –
- Scheduled tasks.
- –
- Web browser data, such as history, bookmarks or cookies.
- –
- USB device log files.
- Modules: using the multiple forensic tools included in KAPE, these actions, among others, can be performed:
- –
- Event log parsing.
- –
- Registry information extraction.
- –
- Timeline creation.
- –
- File accessed listing.
- –
- Prefetch files processing.
- –
- Browsing history access.
- –
- Extraction of program execution data.
6.2. Target Developed for Windows 10 IoT Core
7. Conclusions
Future Work
- Extend the analysis of the Windows 10 IoT Core operating system, examining it from a dynamic perspective, focusing on studying the volatile memory and network traffic in order to have a complete understanding of what evidence is contained in it and how to collect it.
- Perform further research to study the similarities and differences among the different operating systems of the Windows 10 family, with the aim of discovering new possible evidence or techniques that can be applied in an IoT context.
- Continue the development of forensic tools to allow investigators to automatize the examination process, making them more efficient and simpler.
- Provide guidelines on how to analyze other IoT-based devices or systems, so that analysts can make use of other research when having to study them.
- Enlarge the scope of investigations with the goal of understanding the interaction between IoT devices and systems from a forensic viewpoint since connectivity is the main feature of this environment.
Author Contributions
Funding
Conflicts of Interest
Appendix A. Most Relevant Directories and Artifacts
| Partition | Evidence Description | Route |
|---|---|---|
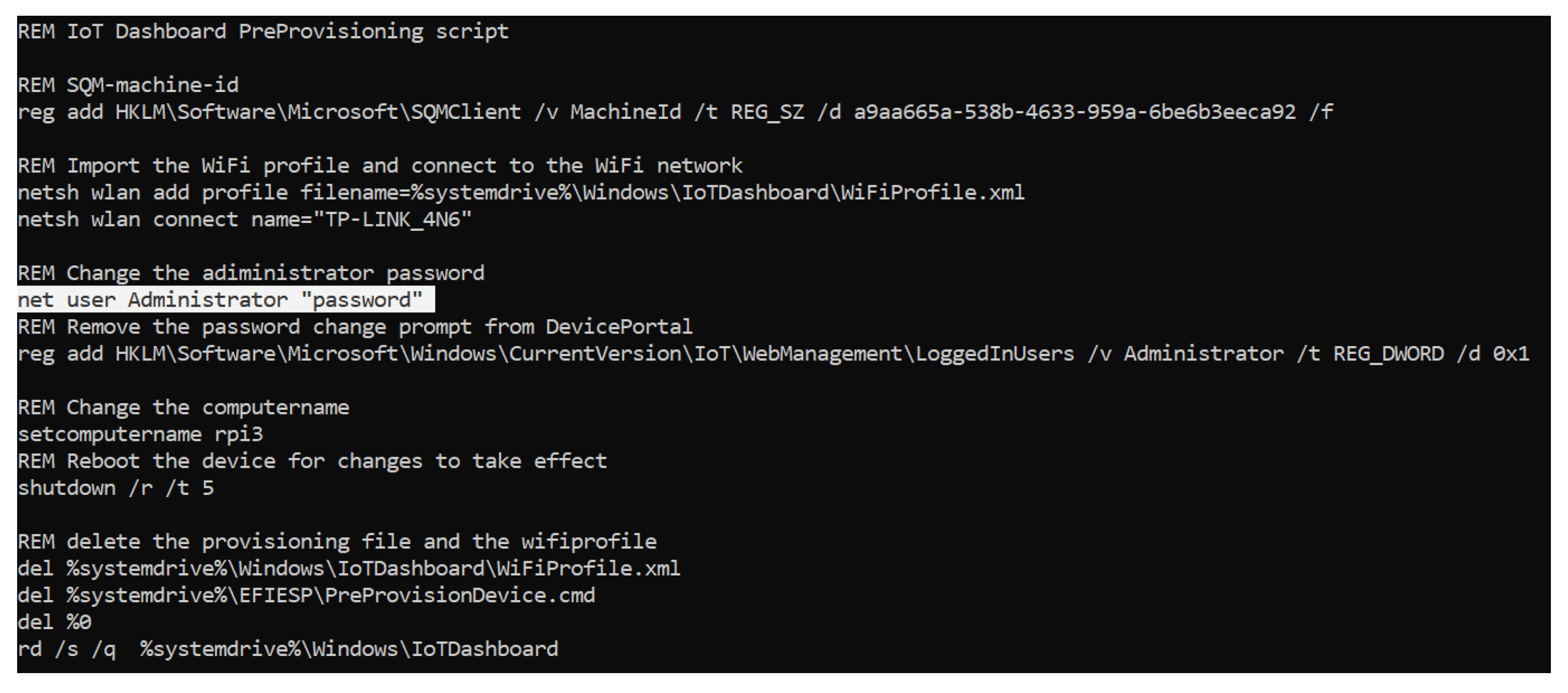
| MainOS | Preprovisoning script created during the set up process and used to configure the system when it boots for the first time. | Windows\IoTDashboard\PreProvisionDevice.cmd |
| MainOS | WiFi profile information file created during the set up process and used to configure the WiFi connection when it boots for the first time. | Windows\IoTDashboard\WiFiProfile.xml |
| MainOS | System Event Logs. Relevant actions occurred in the system classified into the form of events. | Windows\System32\winevt\Logs |
| MainOS | Amcache is a registry file that provides information regarding the executed applications. | Windows\AppCompat\Programs\Amcache.hve |
| MainOS | System registry files. Contain data of system configurations, hardware devices or applications installed. | Windows\System32\config |
| MainOS | Data temporarily exchanged between RAM memory and persistent storage. | pagefile.sys |
| MainOS | File used to save the state of the device when the system is put in hibernation mode. | hiberfil.sys |
| MainOS | Logs of the connections made to the webserver | Windows\system32\LogFiles\HTTPERR\httperr1.log |
| MainOS and Data | Most important NTFS filesystem metadata files. | $MFT, $MFTMirr, $LogFile, $I30, $Volume, $Boot |
| Data | NTUSER.dat user registry file. Stores personal files, preferences and settings for each user. | Users\∗user∗\NTUSER.dat |
| Data | UsrClass.dat user registry file. Information from user processes that do not have write permission to the standard registry hives. | Users\∗user∗\AppData\Local\Microsoft\Windows\UsrClass.dat |
| Data | Personal directories of the users in the system | Users\∗user\Downloads, Documents, Desktop |
| Data | Folder used to store information regarding the user application’s personal configuration. | Users\∗user∗\AppData |
| Data | Applications installed on the system. | Programs\WindowsApp |
| Data | Packages of the applications installed. | ProgramData\Microsoft\Windows\AppRepository\Packages |
| Data | User information about the apps installed. | Users\∗user∗\AppData\Local\Packages\ |
| Data | Browser history and cookies. | Users\∗user∗\AppData\Local\Microsoft\Windows\WebCache |
| Data | Internet cache stored from web browsing. | Users\∗user∗\AppData\Local\Microsoft\Windows\INetCache\IE |
| Data | Internet cookies stored from web browsing. | Users\∗user∗\AppData\Local\Microsoft\Windows\INetCookies |
References
- Gartner Inc. Gartner Says 8.4 Billion Connected “Things” Will Be in Use in 2017, Up 31 Percent from 2016. Available online: https://www.gartner.com/en/newsroom/press-releases/2017-02-07-gartner-says-8-billion-connected-things-will-be-in-use-in-2017-up-31-percent-from-2016 (accessed on 18 July 2019).
- Kuzin, M.; Shmelev, Y.; Kuskov, V. New Trends in the World of IoT Threats-Securelist. Available online: https://securelist.com/new-trends-in-the-world-of-iot-threats/87991/ (accessed on 18 July 2019).
- Makrushin, D. Is Mirai Really as Black as It’s Being Painted?—Securelist. Available online: https://securelist.com/is-mirai-really-as-black-as-its-being-painted/76954/ (accessed on 19 July 2019).
- Cimpanu, C. New Silex Malware is Bricking IoT Devices, Has Scary Plans-ZDNet. Available online: https://www.zdnet.com/google-amp/article/new-silex-malware-is-bricking-iot-devices-has-scary-plans/ (accessed on 19 July 2019).
- Hall, C. Survey Shows Linux the Top OS for Internet of Things Devices. Available online: https://www.itprotoday.com/iot/survey-shows-linux-top-operating-system-internet-things-devices (accessed on 23 September 2019).
- Windows Dev Center. Overview of Windows 10 IoT Core-Windows IoT- Microsoft Docs. Available online: https://docs.microsoft.com/es-es/windows/iot-core/windows-iot-core (accessed on 15 July 2019).
- Windows Dev Center. Enabling Secure Boot, BitLocker, and Device Guard on Windows 10 IoT Core-Windows IoT-Microsoft Docs. Available online: https://docs.microsoft.com/es-es/windows/iot-core/secure-your-device/securebootandbitlocker (accessed on 15 July 2019).
- Zhao, K.; Ge, L. A Survey on the Internet of Things Security. In Proceedings of the Ninth International Conference on Computational Intelligence and Security, Leshan, China, 14–15 December 2013; pp. 663–667. [Google Scholar] [CrossRef]
- Riahi, A.; Challal, Y.; Natalizio, E.; Chtourou, Z.; Bouabdallah, A. A Systemic Approach for IoT Security. In Proceedings of the IEEE International Conference on Distributed Computing in Sensor Systems, Cambridge, MA, USA, 20–23 May 2013; pp. 351–355. [Google Scholar] [CrossRef]
- Zhang, Z.; Cho, M.C.Y.; Wang, C.; Hsu, C.; Chen, C.; Shieh, S. IoT Security: Ongoing Challenges and Research Opportunities. In Proceedings of the IEEE 7th International Conference on Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014; pp. 230–234. [Google Scholar]
- Xu, T.; Wendt, J.B.; Potkonjak, M. Security of IoT systems: Design challenges and opportunities. In Proceedings of the IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, CA, USA, 2–6 November 2014; pp. 417–423. [Google Scholar] [CrossRef]
- U Farooq, M.; Waseem, M.; Khairi, A.; Sadia Mazhar, P. A Critical Analysis on the Security Concerns of Internet of Things (IoT). Int. J. Comput. Appl. 2015, 111, 1–6. [Google Scholar]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015; pp. 336–341. [Google Scholar]
- Ukil, A.; Sen, J.; Koilakonda, S. Embedded Security for Internet of Things. In Proceedings of the 2nd National Conference on Emerging Trends and Applications in Computer Science, Shillong, India, 4–5 March 2011. [Google Scholar]
- Chze, P.L.R.; Leong, K.S. A secure multi-hop routing for IoT communication. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 428–432. [Google Scholar]
- Miettinen, M.; Marchal, S.; Hafeez, I.; Asokan, N.; Sadeghi, A.; Tarkoma, S. IoT SENTINEL: Automated Device-Type Identification for Security Enforcement in IoT. In Proceedings of the IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2177–2184. [Google Scholar] [CrossRef]
- Wurm, J.; Hoang, K.; Arias, O.; Sadeghi, A.; Jin, Y. Security analysis on consumer and industrial IoT devices. In Proceedings of the 21st Asia and South Pacific Design Automation Conference (ASP-DAC), Macau, China, 25–28 January 2016; pp. 519–524. [Google Scholar] [CrossRef]
- Han, J.; Jeon, Y.; Kim, J. Security considerations for secure and trustworthy smart home system in the IoT environment. In Proceedings of the 2015 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 28–30 October 2015; pp. 1116–1118. [Google Scholar]
- Lillis, D.; Becker, B.; O’Sullivan, T.; Scanlon, M. Current Challenges and Future Research Areas for Digital Forensic Investigation. arXiv 2016, arXiv:1604.03850. [Google Scholar]
- Oriwoh, E.; Jazani, D.; Epiphaniou, G.; Sant, P. Internet of Things Forensics: Challenges and Approaches. In Proceedings of the 9th IEEE International Conference on Collaborative Computing: Networking, Applications and Worksharing, Austin, TX, USA, 20–23 October 2013. [Google Scholar]
- MacDermott, A.; Baker, T.; Shi, Q. Iot Forensics: Challenges for the Ioa Era. In Proceedings of the 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–5. [Google Scholar]
- Yaqoob, I.; Hashem, I.A.T.; Ahmed, A.; Kazmi, S.A.; Hong, C.S. Internet of things forensics: Recent advances, taxonomy, requirements, and open challenges. Future Gener. Comput. Syst. 2019, 92, 265–275. [Google Scholar] [CrossRef]
- Oriwoh, E.; Sant, P. The Forensics Edge Management System: A Concept and Design. In Proceedings of the IEEE 10th International Conference on Ubiquitous Intelligence and Computing and 2013 IEEE 10th International Conference on Autonomic and Trusted Computing, Vietri sul Mere, Italy, 18–21 December 2013; pp. 544–550. [Google Scholar] [CrossRef]
- Van Baar, R.; van Beek, H.; van Eijk, E. Digital Forensics as a Service: A game changer. Digit. Investig. 2014, 11, S54–S62. [Google Scholar] [CrossRef]
- Perumal, S.; Norwawi, N.M.; Raman, V. Internet of Things(IoT) digital forensic investigation model: Top-down forensic approach methodology. In Proceedings of the Fifth International Conference on Digital Information Processing and Communications (ICDIPC), Sierre, Switzerland, 7–9 October 2015; pp. 19–23. [Google Scholar] [CrossRef]
- Bouchaud, F.; Grimaud, G.; Vantroys, T. IoT Forensic: Identification and Classification of Evidence in Criminal Investigations. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; ACM: New York, NY, USA, 2018; pp. 60:1–60:9. [Google Scholar]
- Al Sharif, S.; Al Ali, M.; Al Reqabi, N.; Iqbal, F.; Baker, T.; Marrington, A. Magec: An Image Searching Tool for Detecting Forged Images in Forensic Investigation. In Proceedings of the 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Larnaca, Cyprus, 21–23 November 2016; pp. 1–6. [Google Scholar]
- Sutherland, I.; Read, H.; Xynos, K. Forensic analysis of smart TV: A current issue and call to arms. Digit. Investig. 2014, 11, 175–178. [Google Scholar] [CrossRef]
- Hadgkiss, M.; Morris, S.; Paget, S. Sifting through the ashes: Amazon Fire TV stick acquisition and analysis. Digit. Investig. 2019, 28, 112–118. [Google Scholar] [CrossRef]
- Baggili, I.; Oduro, J.; Anthony, K.; Breitinger, F.; McGee, G. Watch What You Wear: Preliminary Forensic Analysis of Smart Watches. In Proceedings of the 10th International Conference on Availability, Reliability and Security, Toulouse, France, 24–27 August 2015; pp. 303–311. [Google Scholar]
- Feng, X.; Dawam, E.S.; Amin, S. A New Digital Forensics Model of Smart City Automated Vehicles. In Proceedings of the IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Exeter, UK, 21–23 June 2017; pp. 274–279. [Google Scholar]
- Hossain, M.; Hasan, R.; Zawoad, S. Trust-IoV: A Trustworthy Forensic Investigation Framework for the Internet of Vehicles (IoV). In Proceedings of the IEEE International Congress on Internet of Things (ICIOT), Honolulu, HI, USA, 25–30 June 2017; pp. 25–32. [Google Scholar]
- Servida, F.; Casey, E. IoT forensic challenges and opportunities for digital traces. Digit. Investig. 2019, 28, S22–S29. [Google Scholar] [CrossRef]
- Chung, H.; Park, J.; Lee, S. Digital forensic approaches for Amazon Alexa ecosystem. Digit. Investig. 2017, 22, S15–S25. [Google Scholar] [CrossRef]
- Yusoff, Y.; Ismail, R.; Hassan, Z. Common Phases of Computer Forensics Investigation Models. Int. J. Comput. Sci. Inf. Technol. 2011, 3. [Google Scholar] [CrossRef]
- AccessData Corp. FTK Imager version 4.2.1. Available online: https://accessdata.com/product-download/ftk-imager-version-4-2-1 (accessed on 9 August 2019).
- Carrier, B. Autopsy—The Sleuth Kit. Sleuthkit.org. Available online: http://www.sleuthkit.org/autopsy/ (accessed on 9 August 2019).
- CGSecurity. PhotoRec ES—CGSecurity. CGSecurity.org. Available online: http://www.cgsecurity.org/wiki/PhotoRec_ES (accessed on 9 August 2019).
- Zimmerman, E. Eric Zimmerman’s Tools. Github.com. Available online: https://ericzimmerman.github.io/ (accessed on 12 August 2019).
- Carvey, H. RegRipper. Github.com. Available online: https://github.com/keydet89/RegRipper2.8 (accessed on 12 August 2019).
- dkovar. Analyze MFT. Github.com. Available online: https://github.com/dkovar/analyzeMFT (accessed on 13 August 2019).
- Nir Sofer. ESEDatabaseView—View/Open ESE Database Files (Jet Blue/.edb files). Available online: https://www.nirsoft.net/utils/ese_database_view.html (accessed on 15 August 2019).
- Torres Álvarez, J.B. Detección Antiforense Open Source. Master’s Thesis, Universidad Internacional de La Rioja, Logroño, Spain, 2016. [Google Scholar]
- Matt, B. A Journey into NTFS. Available online: https://medium.com/@bromiley/a-journey-into-ntfs-part-1-e2ac6a6367ec (accessed on 26 August 2019).
- Niemiro–Sysnative Forums. Restoring a Backup of the COMPONENTS Hive—What are the Issues? Available online: https://www.sysnative.com/forums/threads/restoring-a-backup-of-the-components-hive-what-are-the-issues.11691/ (accessed on 21 August 2019).
- Chen, R. The Default User is Not the Default User—The Old New Thing. Available online: https://devblogs.microsoft.com/oldnewthing/20070302-00/?p=27783 (accessed on 22 August 2019).
- Wong, L.W. Forensic Analysis of the Windows Registry—ForensicFocus.com. Available online: https://www.forensicfocus.com/Content/pid=73/page=1/ (accessed on 22 August 2019).
- Windows Dev Center. Predefined Keys—Windows Applications—Microsoft Docs. Available online: https://docs.microsoft.com/en-us/windows/desktop/sysinfo/predefined-keys (accessed on 23 August 2019).
- Understanding NTUser.dat in Windows 10—Windows Enterprise Desktop. Available online: https://searchenterprisedesktop.techtarget.com/blog/Windows-Enterprise-Desktop/Understanding-NTUserdat-in-Windows-10 (accessed on 23 August 2019).
- Tilbury, C. SANS Digital Forensics and Incident Response Blog-Computer Forensic Artifacts: Windows 7 Shellbags—SANS Institute. Available online: https://digital-forensics.sans.org/blog/2011/07/05/shellbags (accessed on 23 August 2019).
- Rouse, M. What is Windows Event Log?—Definition from WhatIs.com. Available online: https://searchwindowsserver.techtarget.com/definition/Windows-event-log (accessed on 26 August 2019).
- Hoffman, C. What Is the Windows Event Viewer, and How Can I Use It? Available online: https://www.howtogeek.com/123646/htg-explains-what-the-windows-event-viewer-is-and-how-you-can-use-it/ (accessed on 26 August 2019).
- Volatility Foundation. Releases—Volatilityfoundation. An Advanced Memory Forensics Framework. Available online: https://www.volatilityfoundation.org/releases (accessed on 2 September 2019).
- Zimmerman, E. Kroll Artifact Parser and Extractor—KAPE. Available online: https://www.kroll.com/en/insights/publications/cyber/kroll-artifact-parser-extractor-kape (accessed on 5 September 2019).


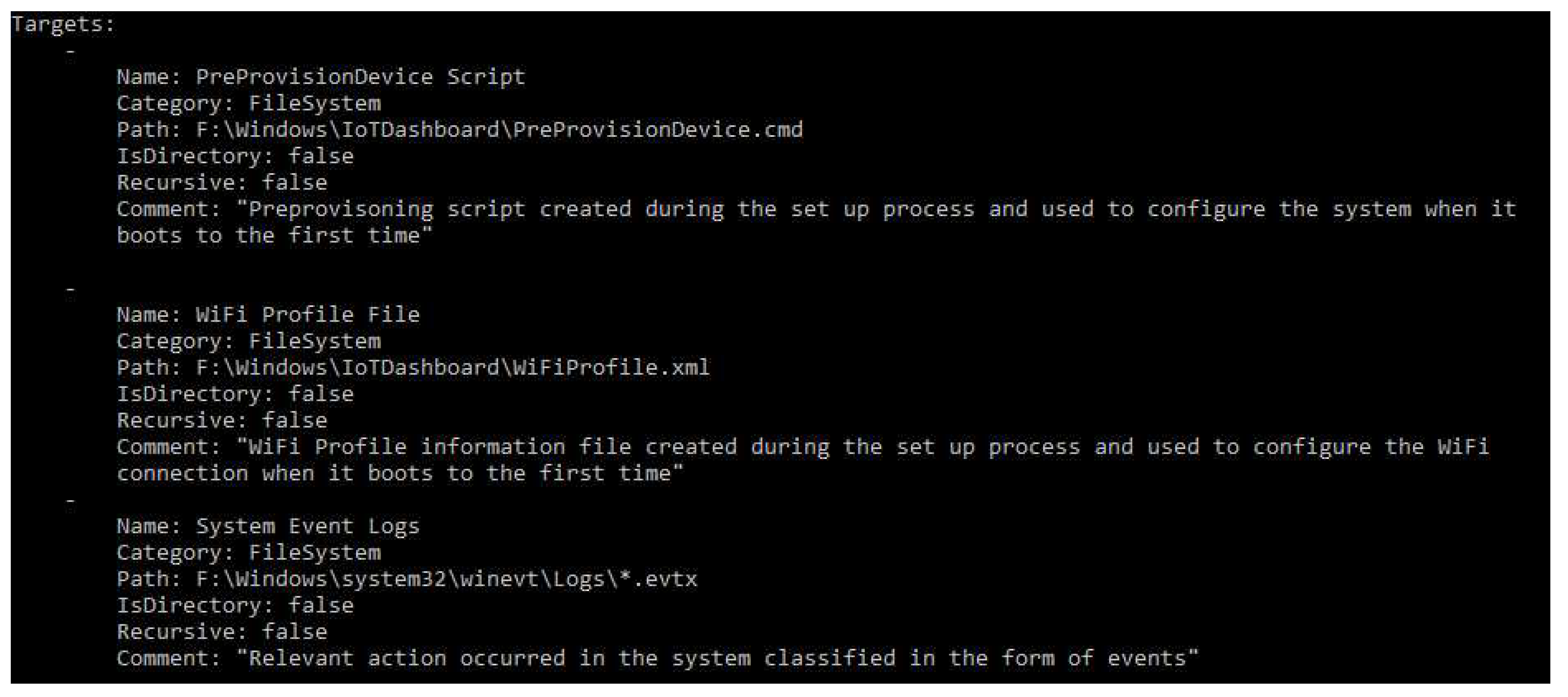
| Directory | Description |
|---|---|
| boot | Installation boot files. |
| EFI | Contains the booting information and settings for the operating system startup process. We can find the bootloader for the ARM architecture and the boot configuration data. |
| System Volume Information | Folder used by the system to store its information and the restore points. |
| Users | Directory in which information about the system’s users is stored. Here we can find that a user account under the name “default” exists, but no relevant material is found in it, including the NTUSER registry. This user profile is used as a template when creating new users, which will be built based on the “default” profile. |
| Windows | Typical Windows system structure directory. Information about specific IoT and ARM packages can be found, but nothing relevant as no usage information is stored in this partition. |
| Directory | Description |
|---|---|
| $Extend | Folder that contains metadata and optional extensions regarding the NTFS filesystem. |
| Data | It is a symbolic link to the Data partition, known in NTFS as a junction point. |
| Program Files | Directory to store the information of the programs that are installed on the system. This folder is not used for this purpose in this operating system, as the programs are installed on the “Data” partition. |
| ProgramData | Folder used for application data that is not user-specific, that is to say, the information is available for every account in the system, so all the information of the programs that are shared between the users is stored in this directory. It has no forensic value as the “ProgramData” directory on the “data” partition stores most of the information. |
| PROGRAMS | Folder typically used on Windows 10 Mobile to store the preloaded apps in the system, although there is no information stored in it in the IoT operating system. We can find the folder used to update the system,“UpdateOS”. |
| System Volume Information | Folder used by the system to store its information and the restore points. |
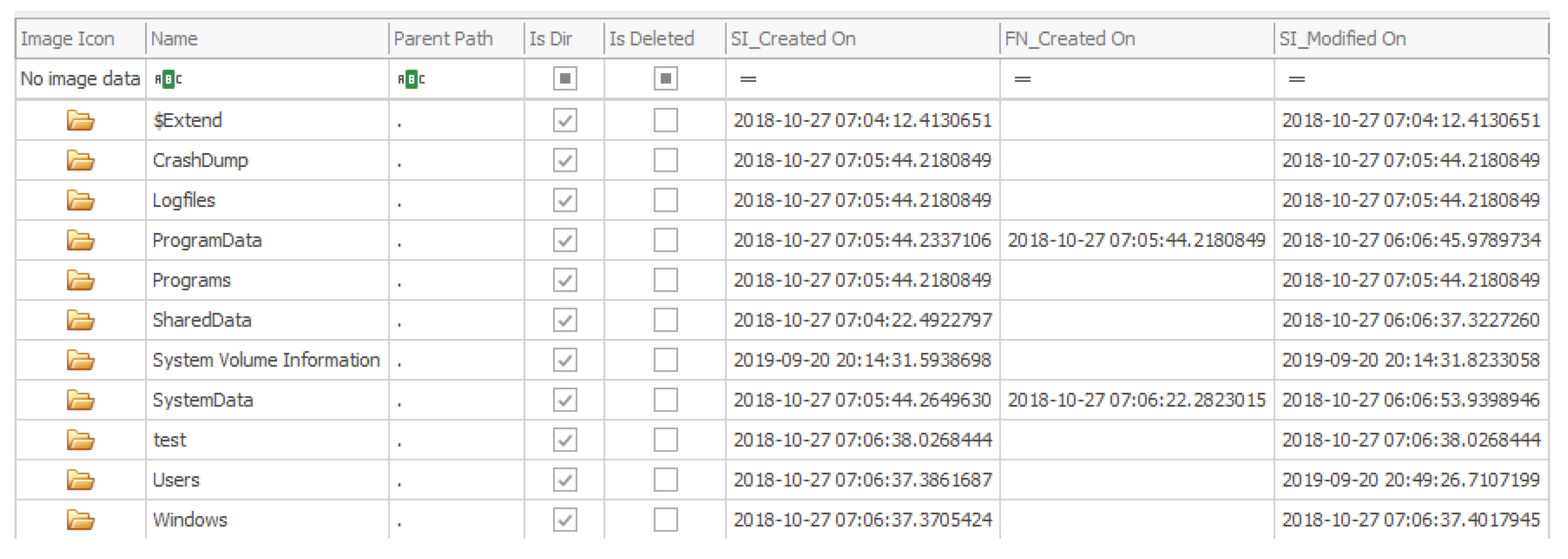
| SystemData | Contains a directory named “Temp” with no information in it. |
| Users | Local information of the users can be found here. There is a “default” user used for the start menu and tiles design, and a “public” directory for the namesake user, but they are empty. |
| Windows | As this partition behaves as the system directory, the Windows folder contains information about the packages installed, drivers, executables, libraries and relevant forensic artifacts such as the system registry hives and the system event logs, among other data. There is also a directory in “System32” named “LogFiles” in which a log about the connections made to the webserver can be found. |
| Directory | Description |
|---|---|
| $Extend | Folder that contains metadata and optional extensions regarding the NTFS filesystem. |
| CrashDump | Keeps the information stored in memory when the system or an application crashes. |
| Logfiles | Directory in which the logs from different applications are stored. Complements the namesake directory that is available in the “MainOS” partition, although in this analysis only information about the Windows Management Instrumentation (WMI) has been found. |
| ProgramData | Same purpose as the directory in the system root partition. In this folder there is more information than in the aforementioned one, and the data regarding the SSH service is especially relevant. Also, the packages that have been installed for the different applications in the system can be found here. |
| Programs | Contains directories for the different applications that have been installed on the system as well as a folder with the deleted ones. Each folder contains the resources needed for that application to run. |
| SharedData | Folder designed for shared storage. |
| System Volume Information | Folder used by the system to store its information and the restore points. |
| SystemData | Contains a directory for the Event Tracing for Windows (ETW) logs, a different one for the non-ETW ones and a “Temp” folder. |
| test | Used for the Windows Driver Test Framework (WDTF) for developing and running tests on the system. |
| Users | Local information for the users of the system are stored in this directory. The most relevant user is the “administrator” as this is the one that is logged on automatically when the system boots, therefore being the one who executes all the actions that are performed by a user on the device. |
| Windows | Little data can be found in this directory, as the relevant “Windows” folder is the one stored in the “MainOS” partition. Some packages are stored in this partition as well as the system registry files, which are almost empty. |
| File | Description |
|---|---|
| $AttrDef | Describes the attributes supported on the volume. It is essential for the filesystem, since a file is a representation of these attributes. |
| $BadClus | Informs of the clusters that contain bad sectors. |
| $Bitmap | Contains the status of the clusters in the filesystem. |
| $Boot | Provides data with respect to the booting process such as the boot sector. |
| $I30 | Representation of the $INDEX_ROOT, $INDEX_ALLOCATION and $BITMAP attributes. They present information regarding the filenames and directories stored in a specific directory. |
| $LogFile | Stores the transactions that have been performed in the system to allow their recovery after a failure. |
| $MFT | Most important file of all, as it is a table that contains information for every file and directory that has been stored in the filesystem. It is extremely useful in forensic investigations as it logs all the activities that have occurred, providing information regarding timestamps, attributes, names or how it was created, among other data. |
| $MFTMirr | File to allow the recovery of the MFT. |
| $Secure | Lists the security descriptors for the volume. |
| $TFX_DATA | Contains transactional data. Corresponds to the $LOGGED_UTILITY_STREAM, attribute, but some tools such as FTK Imager represents it as an independent file [43]. |
| $UpCase | Used to compare and sort filenames. |
| $Volume | Describes the characteristics of the volume, such as its identifier, label or version [44]. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Castelo Gómez, J.M.; Roldán Gómez, J.; Carrillo Mondéjar, J.; Martínez Martínez, J.L. Non-Volatile Memory Forensic Analysis in Windows 10 IoT Core. Entropy 2019, 21, 1141. https://doi.org/10.3390/e21121141
Castelo Gómez JM, Roldán Gómez J, Carrillo Mondéjar J, Martínez Martínez JL. Non-Volatile Memory Forensic Analysis in Windows 10 IoT Core. Entropy. 2019; 21(12):1141. https://doi.org/10.3390/e21121141
Chicago/Turabian StyleCastelo Gómez, Juan Manuel, José Roldán Gómez, Javier Carrillo Mondéjar, and José Luis Martínez Martínez. 2019. "Non-Volatile Memory Forensic Analysis in Windows 10 IoT Core" Entropy 21, no. 12: 1141. https://doi.org/10.3390/e21121141
APA StyleCastelo Gómez, J. M., Roldán Gómez, J., Carrillo Mondéjar, J., & Martínez Martínez, J. L. (2019). Non-Volatile Memory Forensic Analysis in Windows 10 IoT Core. Entropy, 21(12), 1141. https://doi.org/10.3390/e21121141





