A Framework to Secure the Development and Auditing of SSL Pinning in Mobile Applications: The Case of Android Devices
Abstract
:1. Introduction
2. Background
2.1. OWASP Mobile
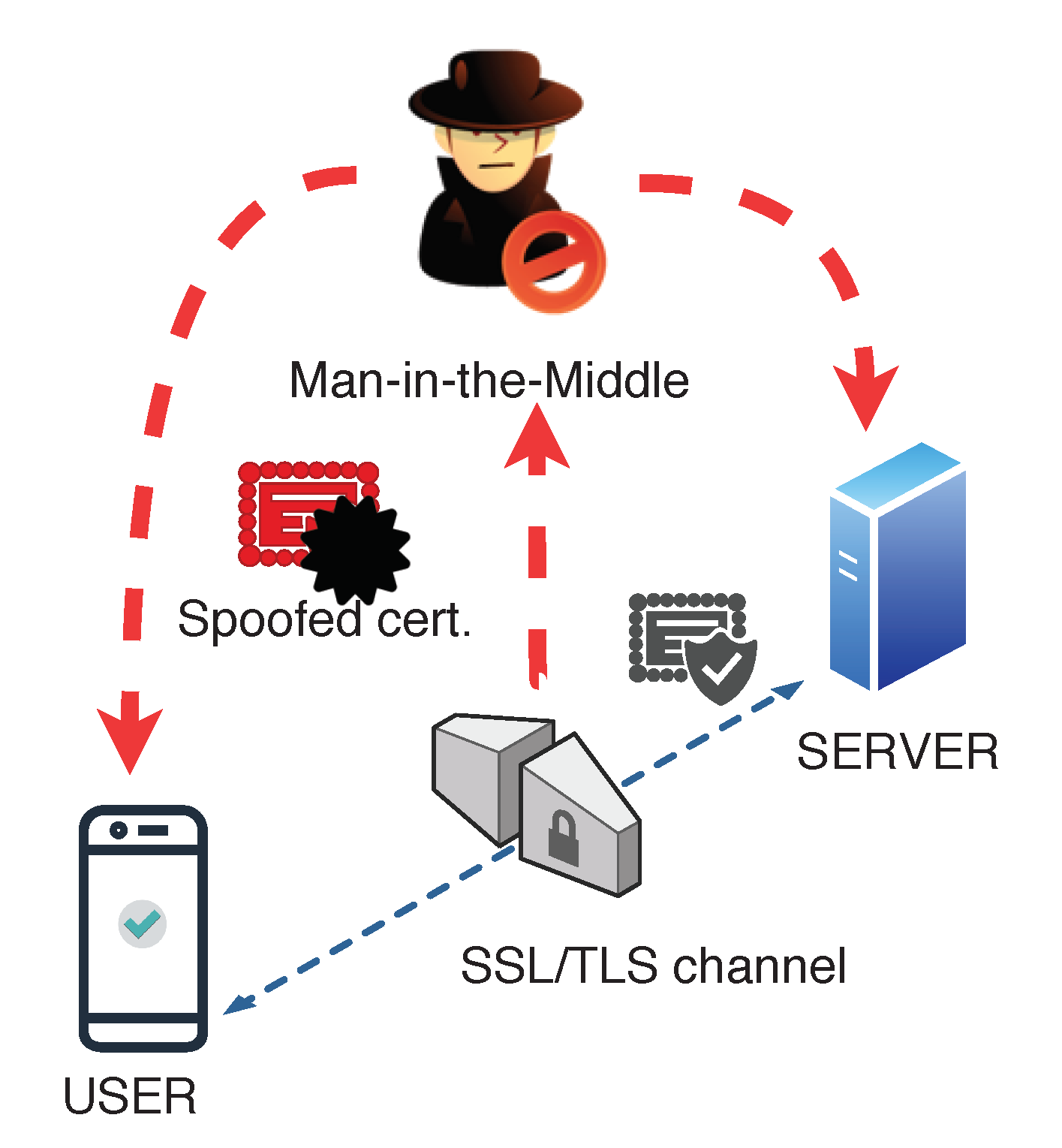
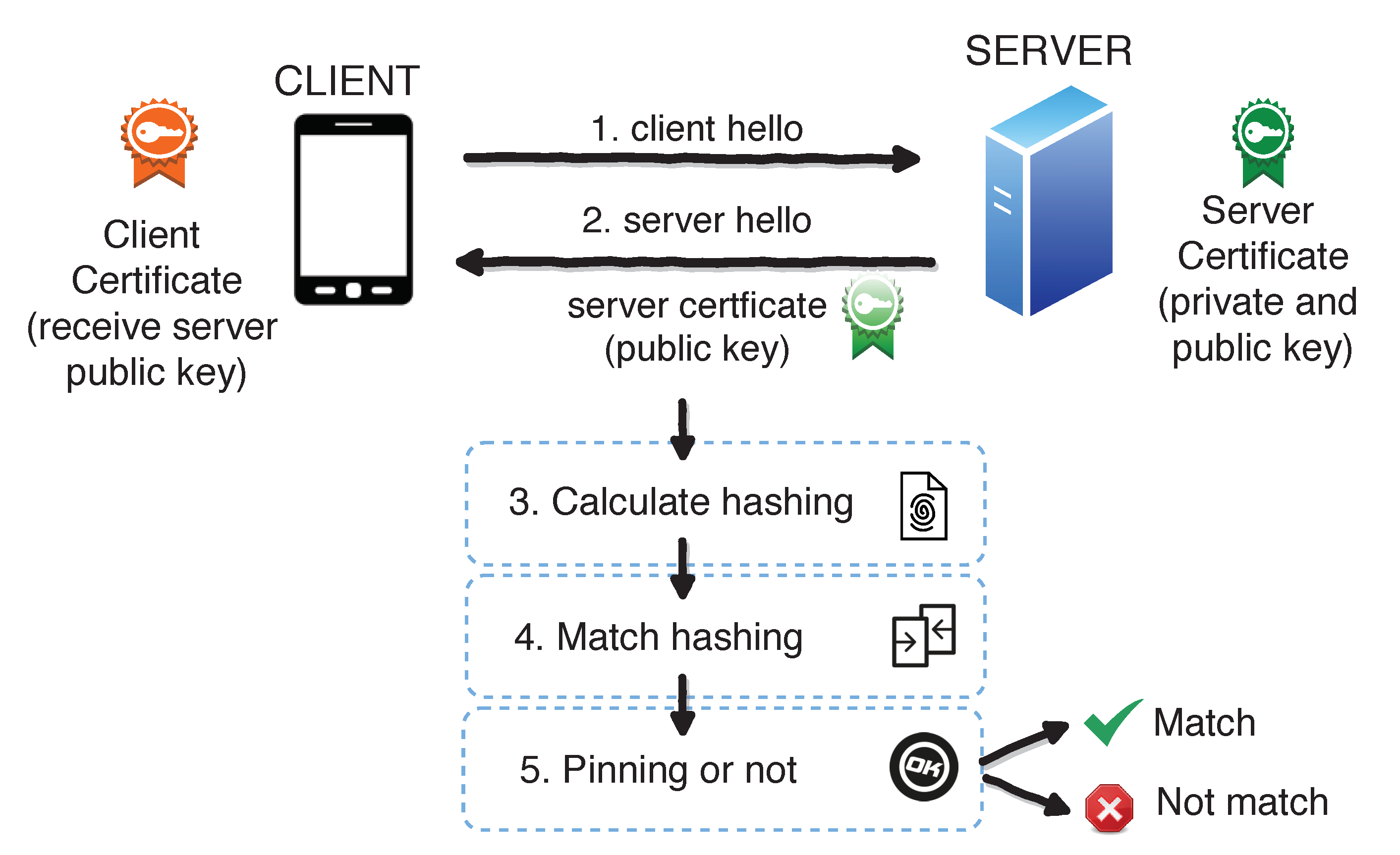
2.2. SSL and SSL Pinning
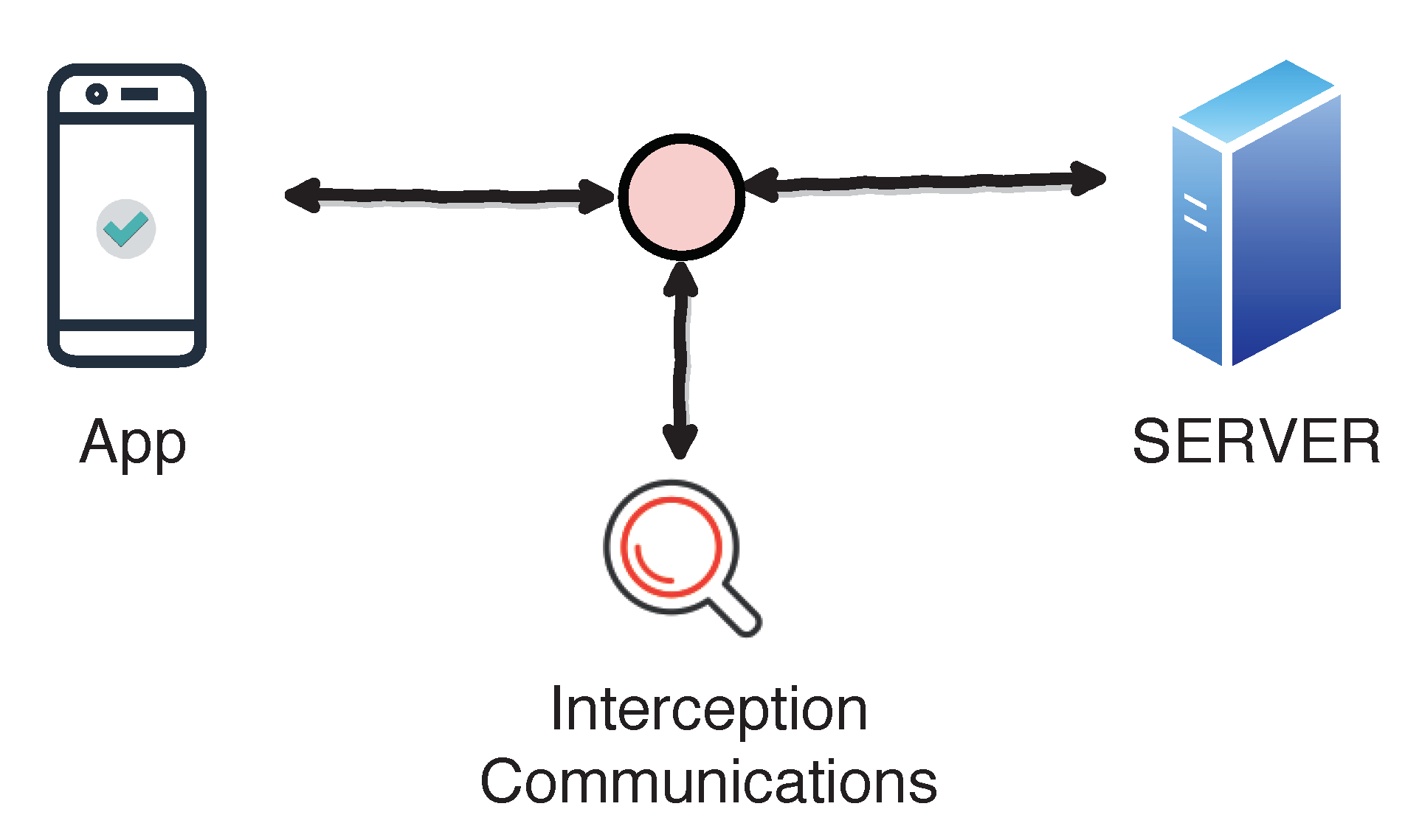
2.3. Bypassing SSL Pinning
- Dynamic analysis of code. The code that is being executed in memory is extracted and its behaviour is low-level analysed, evaluating registers, the data that are loaded in memory and functions, among others. An example of a dynamic analysis tool is SSL Unpinning by Xposed framework. This tool takes advantage of the fact that the code that implements SSL Pinning is known. In general, pinning developers use a well-known or common template. In this case, an attacker may guess this and use SSL Unpinning to bypass SSL Pinning in the pinning stage. In addition, tools such as Frida or Cycript enable the modification of some functions of pinning at runtime.
- Static analysis of code. It consists in extracting and analysing the app code when not at runtime. As we explain in Section 3, if pinning does not implement anti-tampering or exceptions for the modification of pinning, SSL Pinning functions can be replaced to bypass the pinning process.
3. Security Controls to Protect against Bypassing SSL Pinning
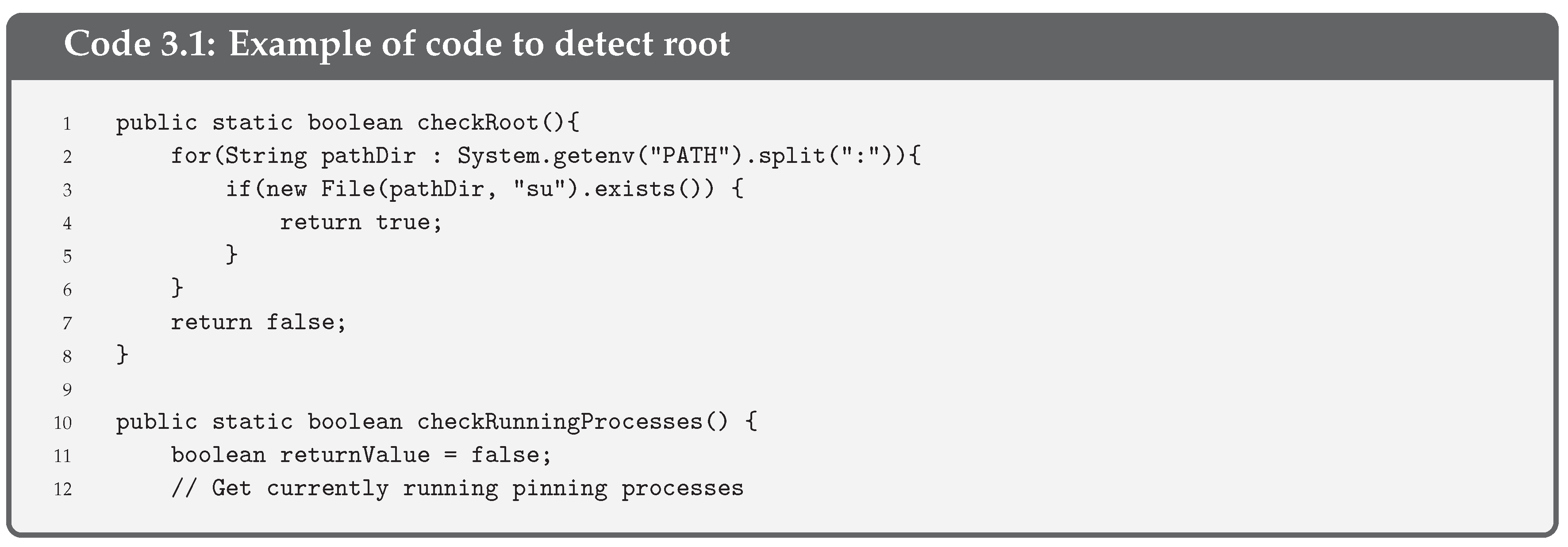
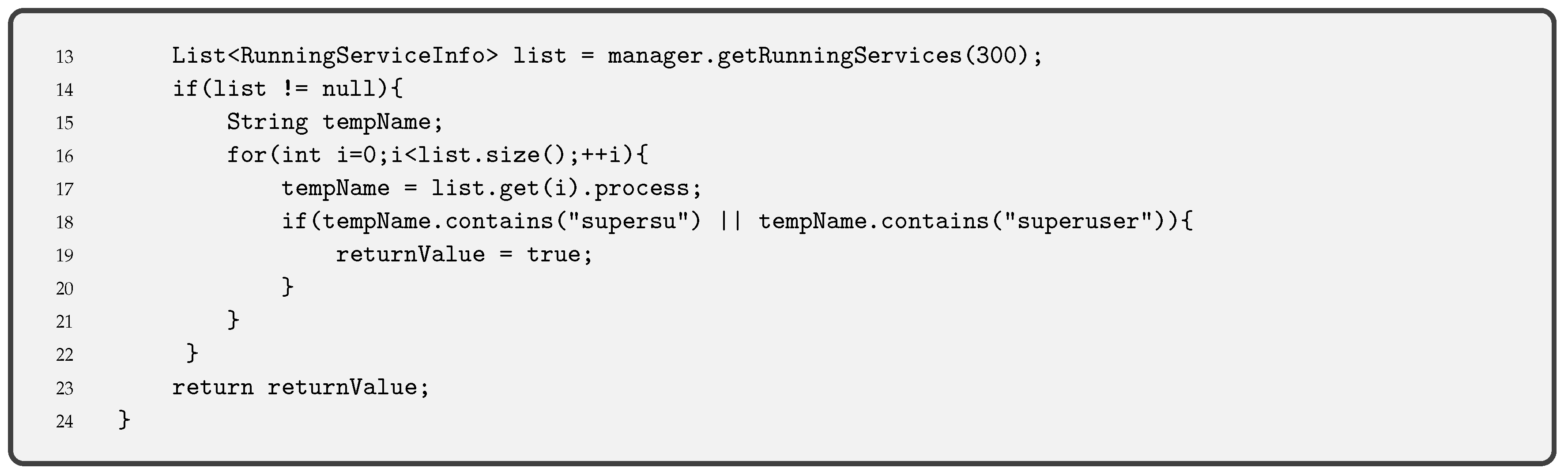
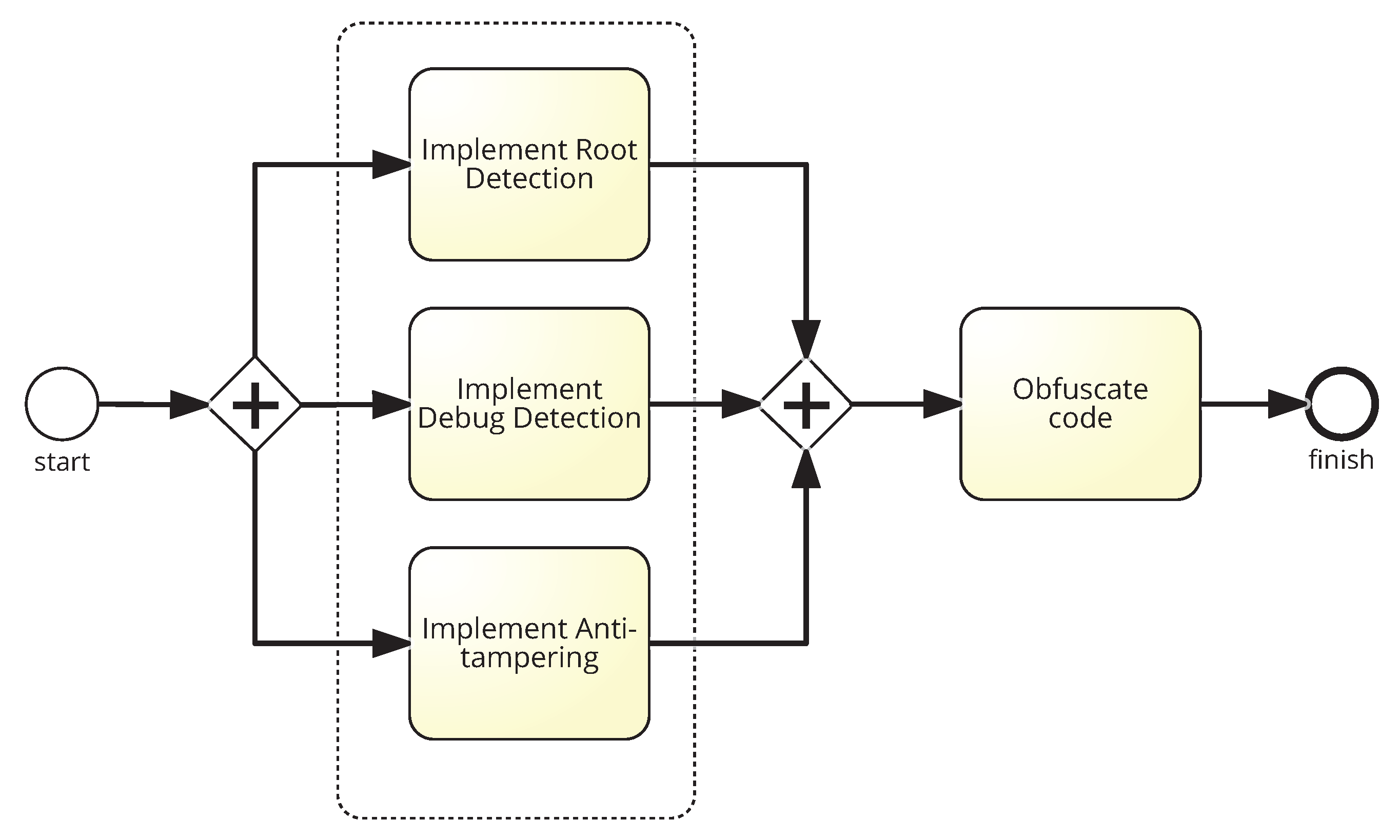
- Root Detection is a security control consisting of checking the blocks of the execution code that turn the pinning into the supervisor mode. Thus, root detection helps prevent the execution of code in supervisor mode. This control improves the effectiveness of reverse engineering and anti-tampering processes.There are several ways to detect root [32] but the most common one is checking some files (i.e., binaries and apk files) that are present on a rooted device, such as or . A piece of the code used to check the root execution on the pinning is given in Code 3.1.
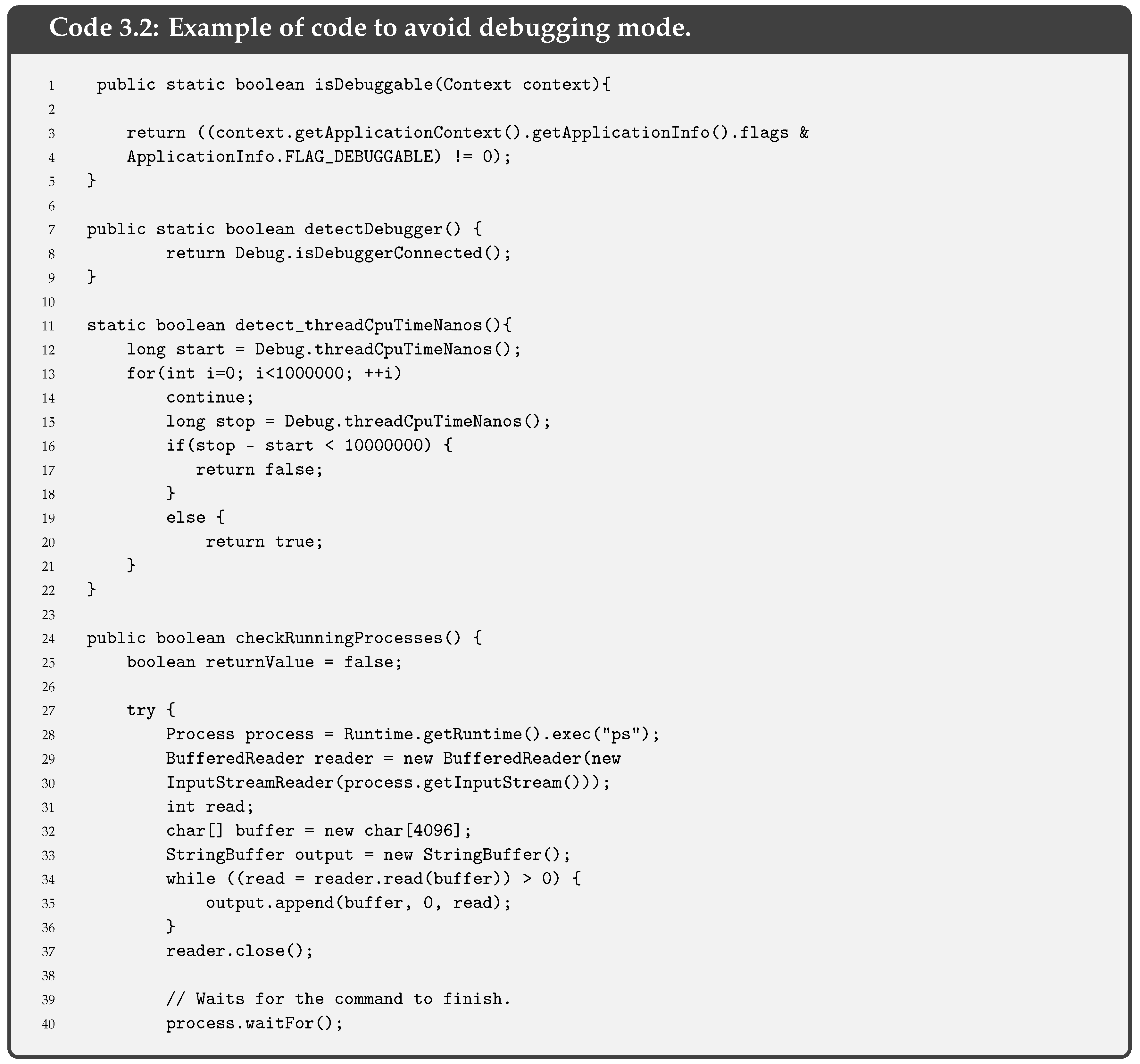
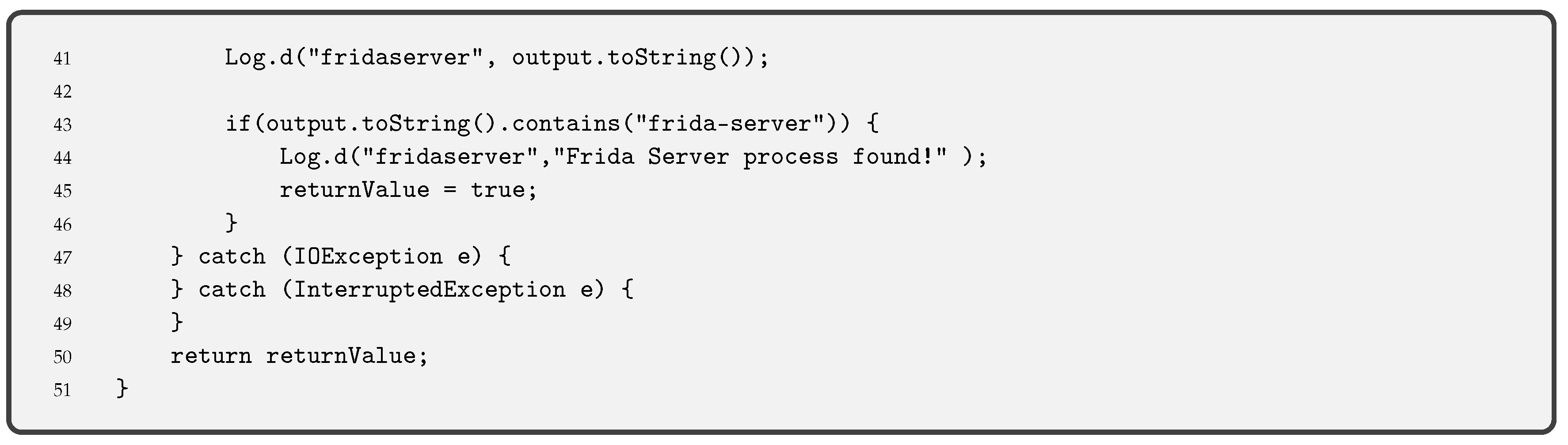
- Debug Detection is used to prevent the app code from being controlled. If a device in debug mode is detected, the execution of the pinning is stopped. This measure stops an attacker from seeing the step-by-step behaviour of our code. Together with the obfuscation of code, described below, it allows hiding the internal functioning of the pinning. Functions such as the one we provide in Code 3.2 are used for Android applications. This piece of code is an adaptation of the guidelines OWASP for debug detection, although there are other ways to detect the debug mode.Indeed, it is always possible to compile an app in debug mode (i.e., changing the Android Manifest file and modifying the corresponding label). In this case, the entire device is not in debug mode, but the app. Code 3.2 detects debugging mode with different functions: finding the Debugger flag, detecting debugger, detecting if execution has stopped because of debugging and checking running processes.
- Anti-tampering solution is an important option since any attacker may decompile an application and recompile it. Modifying some parts of the application [32], as previously explained in the SSL pinning bypass process, an attacker could skip the SSL pinning, and thus make the application invalid.Code 3.3 gives an example of the code that can be included in an Android application, particularly in the onCreate function within MainActivity. In this case, the signature of the application is checked only when the app is started. In iOS, the mechanism is similar, as indicated in the Apple Security Transforms Programming Guide [33].
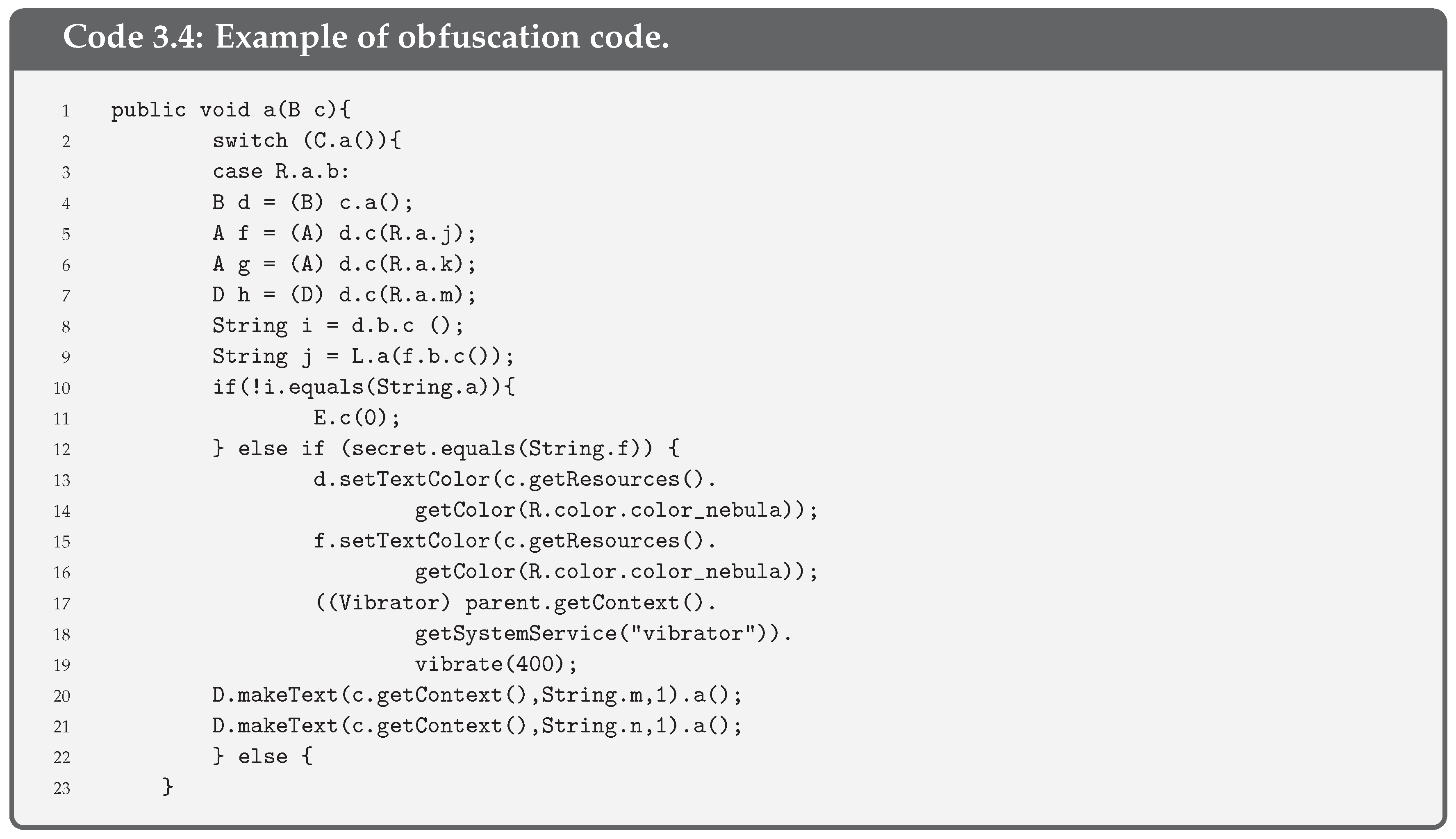
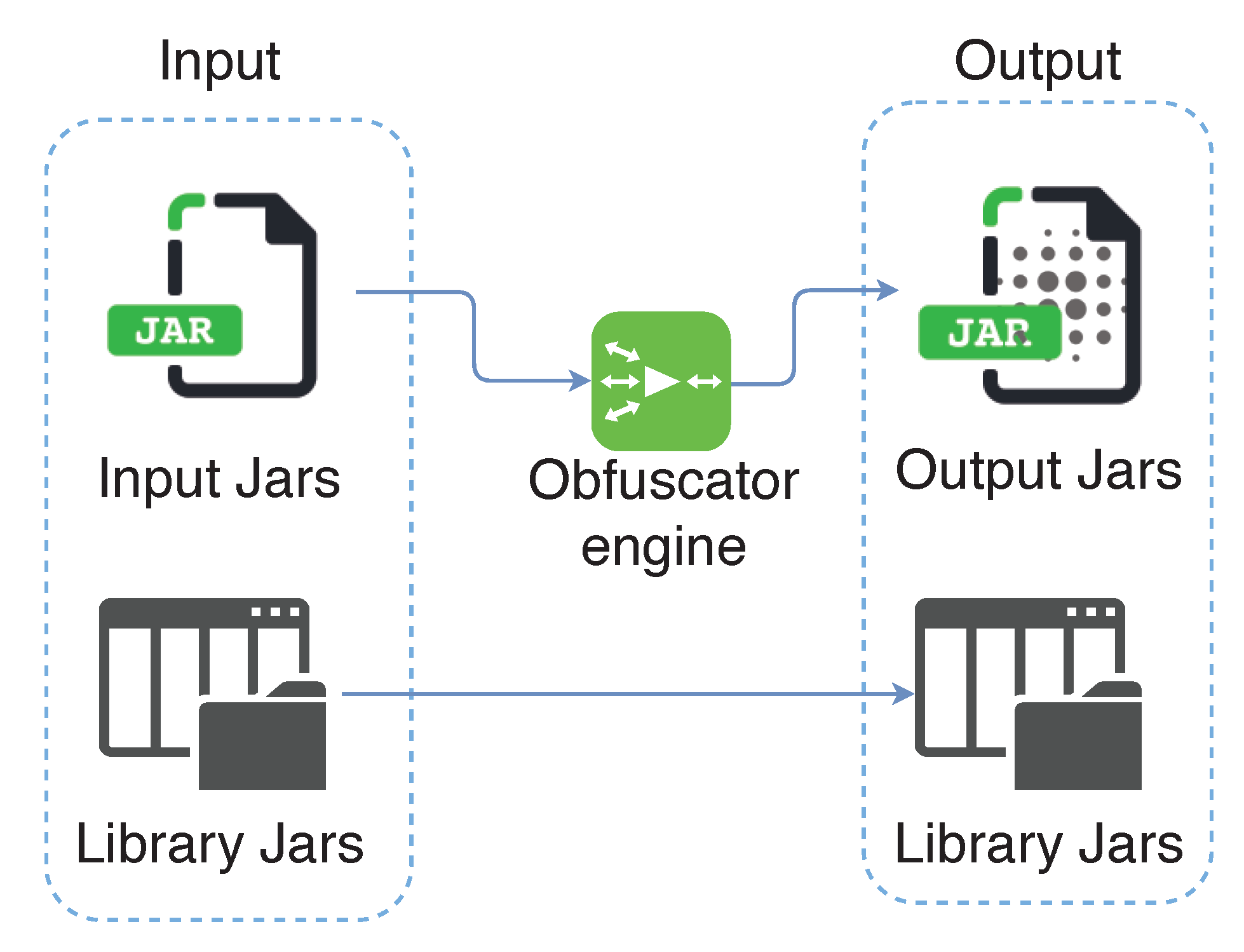
- Obfuscate code. All the measures above do not make sense without preventing any attacker from knowing the code of the app. This way, the analysis of SSL Pinning functions or any of the previous ones that we have presented is more difficult. For this reason, code obfuscation is necessary. There are code obfuscators that convert the existing code into a more illegible one, as seen in Figure 4. Therefore, it is more difficult to detect which are the critical functions of the code for an attacker.As may be seen, replacing variables and function names for letters and numbers makes it more difficult to guess what a function does. An example of obfuscation is shown in Code 3.4, where names of variables and functions are hidden.
4. Experiment Setup
4.1. Threat Scenario
4.2. Current Bypassing Methods
- Method 1: Change common name (CM) in certificate. It is similar to the MiTM attack described in Section 2.3, with the proxy changing the CA-signed certificate dynamically.
- Method 2: Insert CA in the application. This method modifies the CA signature that is stored inside the application.
- Method 3: Use SSL Unpinning. Root access is necessary in this case. Tools such as Xposed in Android or SSL Kill Switch are used for SSL bypassing. They take advantage of the fact that the code that implements SSL Pinning is known. App developers use a well-known template, so that an attacker may guess it and use these tools to bypass SSL Pinning in the app.
- Method 4: Debugging app. If the app does not implement anti-tampering or exceptions for the modification of the app, SSL Pinning functions can be replaced to bypass the pinning process.
- Method 5: Modify app executable to avoid the SSL pinning process. The modified version of the app is copied to the device to permanently bypass SSL/TLS pinning.
4.3. New SSL Pinning Bypassing Methods
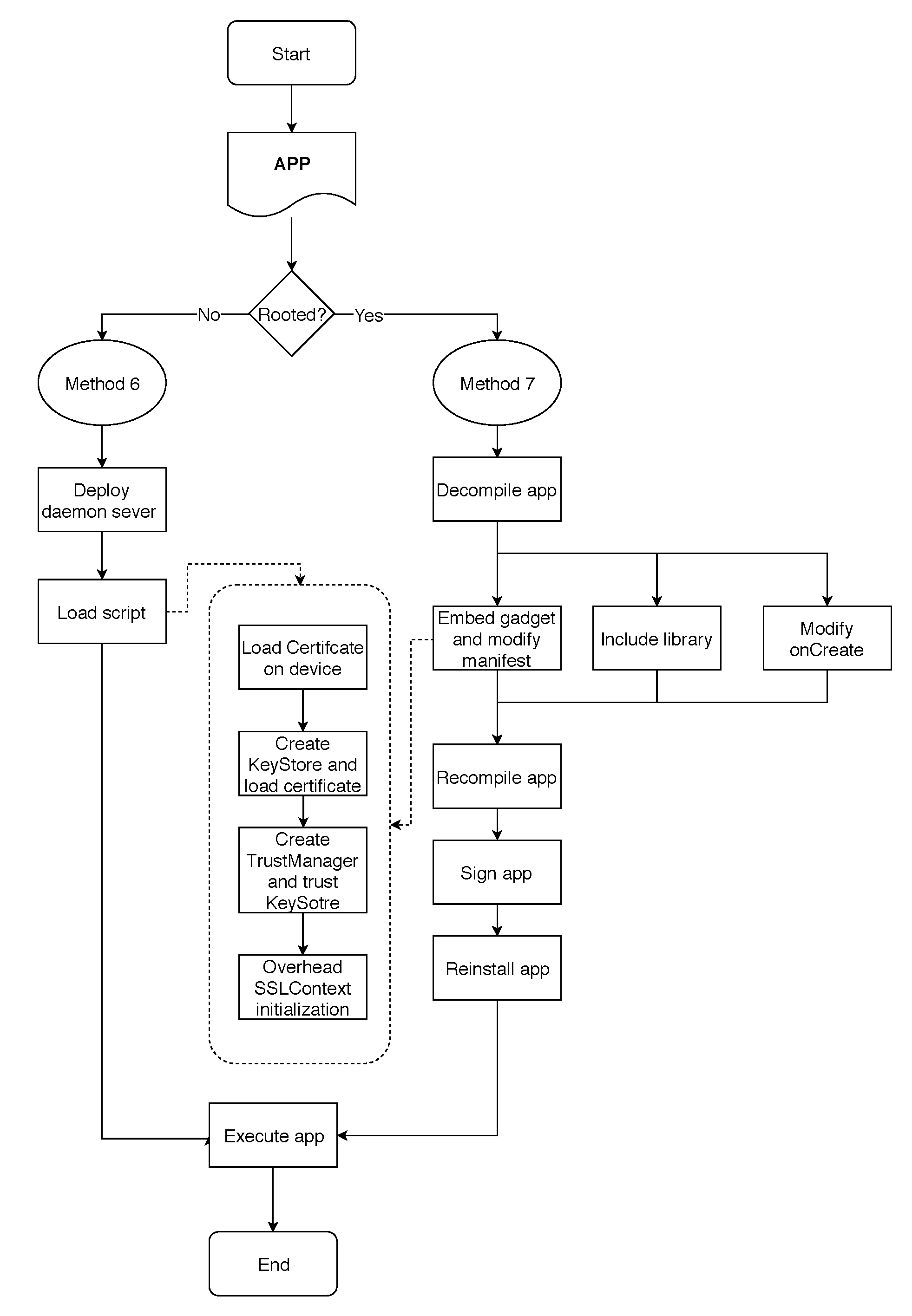
4.3.1. Method 6: Dynamic Debugging of the App in Rooted Devices
- The mobile phone must execute a server that acts as a dynamic code interpreter. The server acts as a daemon and it enables interacting dynamically with the physical memory of the device to manipulate and change the behaviour of the executing apps. Thus, the aim of the server is to manipulate or change the expected behaviour of the SSL pinning process. In our case, we used Frida server with the following command:
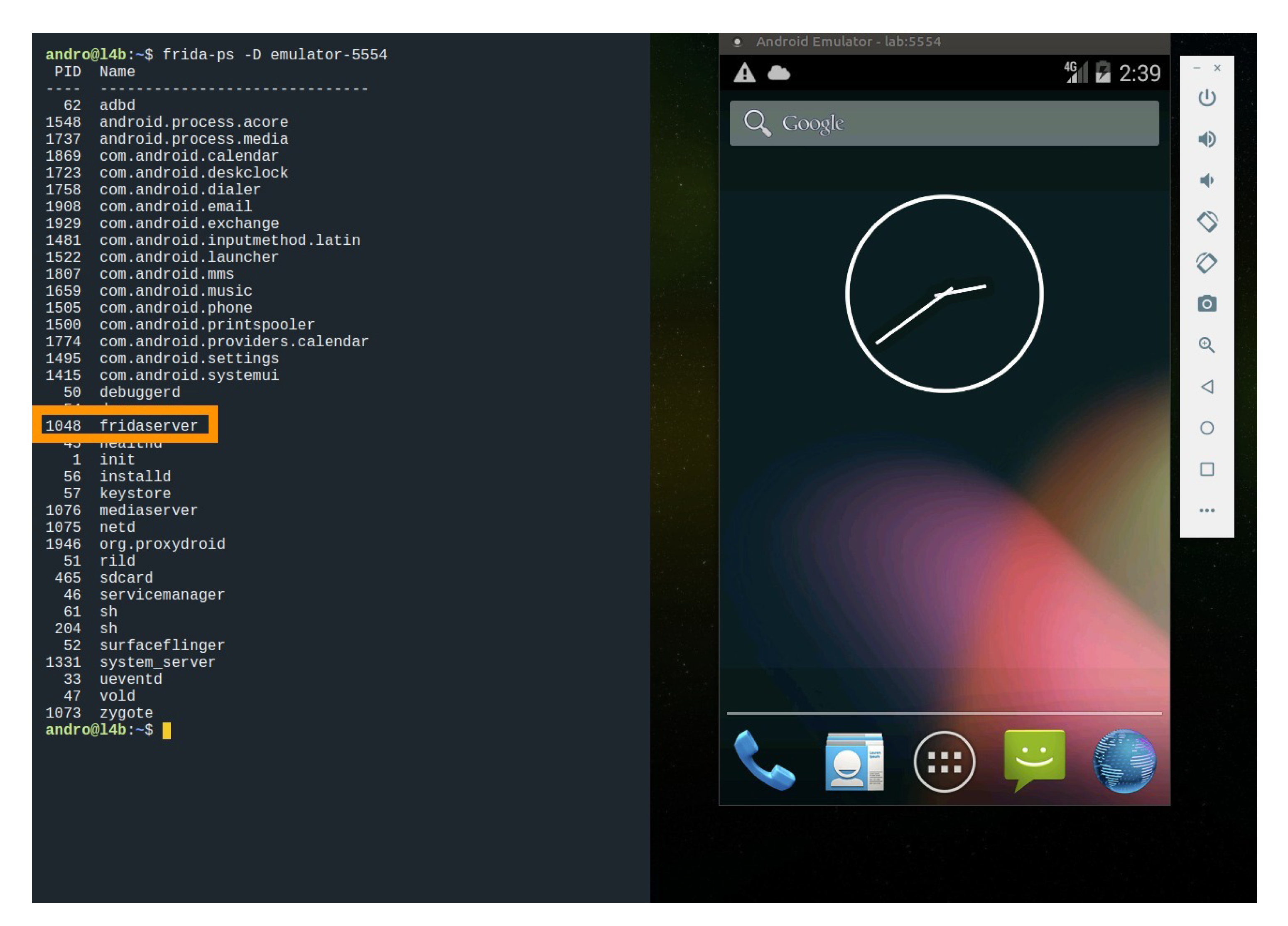
- It should be confirmed that the daemon server is running and has enough permissions to read and manipulate the memory of the device. With this aim, Frida framework can be used by means of the following command:Figure 6 shows how a Frida server is running in a mobile emulator.
- Once the daemon server is running on the device, this fact enables the access to the physical memory of the device. This way, we are able to make the appropriate changes in memory to circumvent SSL Pinning measures. It is necessary to indicate which part of the app code must be dynamically modified in memory. To do that, a script must run on the server. In the following, we describe the steps of a script which modifies dynamically in the memory the code. Thus, the target app must be executed on the mobile together with the script to modify its code dynamically. There are several scripts (https://codeshare.frida.re/@pcipolloni/universal-android-ssl-pinning-bypass-with-frida/) that may be used. In our case, the script loads our certificate, creates a KeyStore containing our certificate and generates a TrustManager that trusts the certificate inside our KeyStore. When the app initialises its SSLContext, the parameter TrustManager in the SSLContext.init() method is swapped with the one we had created before.
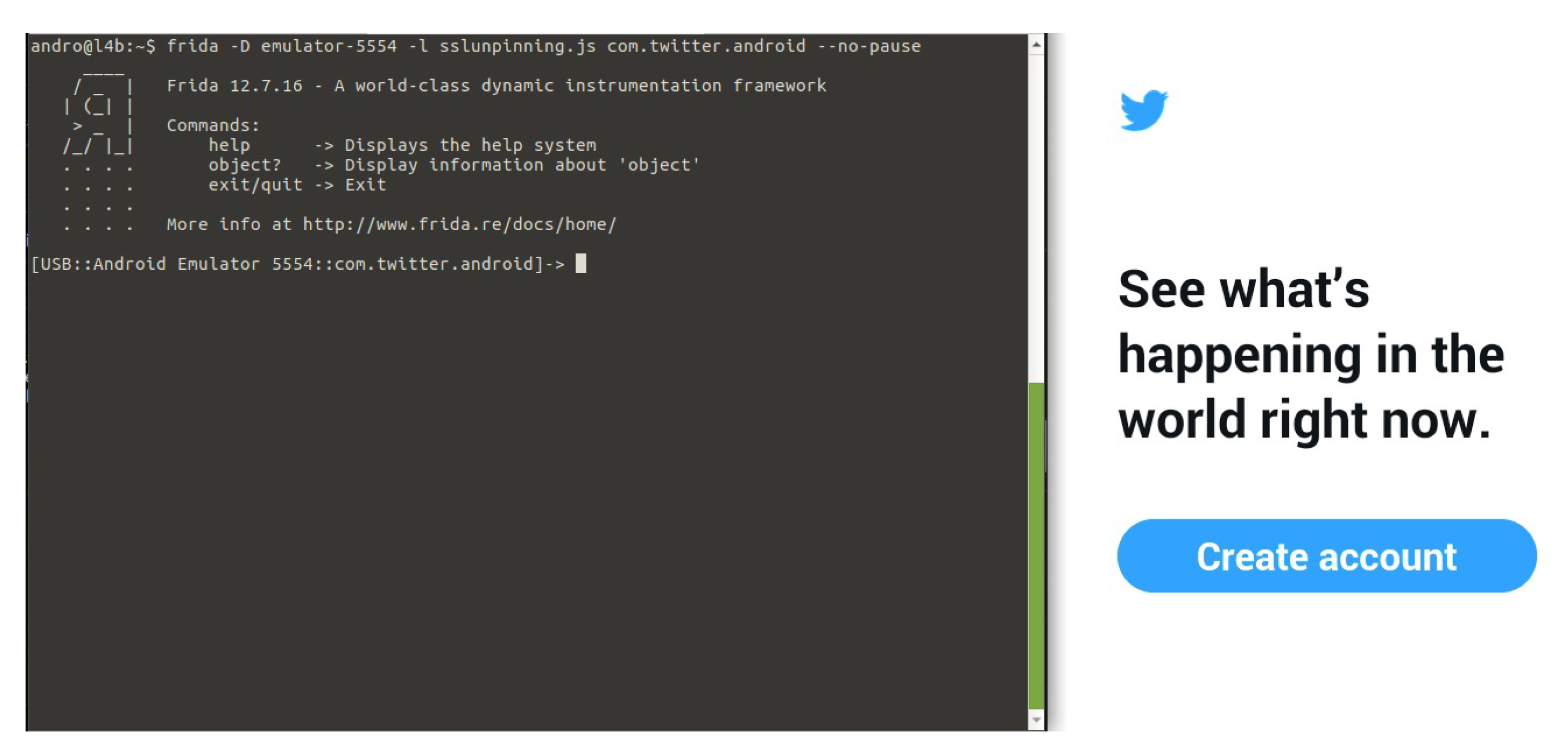
- It must be checked that there are not any restrictions that prevent the SSL handshake of the connection. If so, the connection is established. Finally, it must be confirmed that the target app works properly and SSL pinning was disabled. Figure 7 shows an example of how the execution of the Twitter app is intercepted by Frida.
4.3.2. Method 7: Dynamic Debugging of the App in Non-Rooted Devices
- The target app code must be decompiled. For instance, apktool may be used.
- A daemon must be embedded inside the target app. In our case, the daemon is Frida gadget. The function of the daemon is similar to Step 1 in Method 6.
- a.
- To put in the Frida gadget, an internet permission must be added to the Android manifest. Thereafter, Frida is able to open a socket.
- b.
- The file containing Frida libraries must be included to the app’s library folder.
- c.
- The method in the main activity of the target app must be modified to force the daemon to be run when the target app starts.
- The modified app must be re-installed, launched, and its functioning must be checked.
- From here, Steps 2–4 of Method 6 are executed.
4.4. Experiment Design
5. Analysis of Results
5.1. SSL Pinning and Security Controls
5.2. SSL Pinning Bypassing Methods
5.3. Framework of Applicability
- Root detection disables Methods 3 and 6 when it is implemented. This fact occurs as the device needs to be rooted in some of the steps taken in the application of the methods.
- Anti-tampering security control disables the application of Methods 2, 5 and 7. This fact occurs as it is necessary to modify statically the app code to bypass the SSL pinning checks. This step requires to recompile the app and sign it. However, as we do not have access to the original certificate of the app, it is detected by the anti-tampering control.
- Anti-debugging security control stops Mmethods 3, 4, 6 and 7. As previously mentioned, a device in debug mode is detected, so the execution of the pinning is stopped since this measure stops step-by-step execution of the app code.
- Code obfuscation avoids Method 5 since obfuscation prevents the search of the functions that check the SSL Pinning.
- Method 2 can be tackled using the anti-tampering security control.
- Method 3 can be stopped using root detection or anti-debugging controls.
- Method 4 can be prevented with the anti-debugging control.
- Method 5 can be stopped with the utilisation of anti-tampering or code obfuscation.
- Method 6 can be held with the root detection and anti debugging security controls.
- Method 7 can be denied with the anti-tampering and anti debugging controls.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Disclaimer
References
- Li, D.; Guo, B.; Shen, Y.; Li, J.; Huang, Y. The evolution of open-source mobile applications: An empirical study. J. Softw. Evol. Process. 2017, 29, e1855. [Google Scholar] [CrossRef]
- Unal, P.; Temizel, T.T.; Eren, P.E. What installed mobile applications tell about their owners and how they affect users’ download behavior. Telemat. Inform. 2017, 34, 1153–1165. [Google Scholar] [CrossRef]
- Kumar, R.; Perti, A. Security issues with self-signed SSL certificates. Int. J. Innov. Technol. Explor. Eng. (IJITEE) 2019, 8, 7S2. [Google Scholar]
- Lindgren, A.; Lindoff, B. On Estimating the Number of Worldwide LTE Cell-IDs and WiFi Aps. 2018. Available online: https://combain.com/uploads/Whitepaper_WorldWide_LTE_CellID_and_WiFi_APs_A.pdf (accessed on 3 September 2019).
- Anthi, E.; Theodorakopoulos, G. Sensitive data in Smartphone Applications: Where does it go? Can it be intercepted? In International Conference on Security and Privacy in Communication Systems; Springer: Berlin/Heidelberg, Germany, 2017; pp. 301–319. [Google Scholar]
- Khan, J.; Abbas, H.; Al-Muhtadi, J. Survey on mobile user’s data privacy threats and defense mechanisms. In Proceedings of the 12th Iberian Conference on Information Systems Technolo-Gies (CISTI), Lisbon, Portugal, 14–17 June 2017. No. 7975981. [Google Scholar]
- D’Orazio, C.J.; Choo, K.-K.R. A technique to circumvent SSL/TLS validations on iOS devices. Future Gener. Comput. Syst. 2017, 74, 366–374. [Google Scholar]
- Razaghpanah, A.; Sundaresan, S.; Niaki, A.A.; Amann, J.; Vallina-Rodriguez, N.; Gill, P. Studying TLS usage in Android apps. In Proceedings of the 13th International Conference on Emerging Technologies (CoNEXT 2017), Ingeon, Korea, 12–15 December 2017; pp. 350–362. [Google Scholar]
- Fahl, S.; Harbach, M.; Perl, H.; Koetter, M.; Smith, M. Rethinking SSL development in an appified world. In Proceedings of the ACM SIGSAG Conference on Computer & Communications Security (CCS 2013), Berlin, Germany, 4–8 November 2013; pp. 49–60. [Google Scholar]
- De los Santos, S.; Torres, J. Analysing HSTS and HPKP implementation in both browsers and servers. IET Inf. Secur. 2017, 12, 275–284. [Google Scholar] [CrossRef]
- Mueller, B.; Schleier, S. OWASP Mobile Application Security Verification Standard v 1.1.4. Available online: https://www.owasp.org/index.php/OWASP_Mobile_Security_Testing_Guide (accessed on 21 November 2019).
- Dhawale, C.A.; Misra, S.; Jambhekar, N.D.; Thakur, S.U. Mobile computing security threats and solution. Int. J. Pharm. Technol. 2016, 8, 23075–23086. [Google Scholar]
- OWASP Mobile Top 10. 2016. Available online: https://www.owasp.org/index.php/Mobile_Top_10_2016-Top_10 (accessed on 22 February 2017).
- Kim, S.; Han, H.; Shin, D.; Jeun, I.; Jeong, H. A study of International Trend Analysis on Web Service Vulnerabilities in OWASP and WASC. In Proceedings of the 3rd International Conference on Information Security and Assurance (ISA 2009), Seoul, Korea, 25–27 June 2009; Springer: Heidelberg, Germany; Volume 5576, pp. 788–796. [Google Scholar]
- Szczepanik, M.; Jozwiak, I. Security of mobile banking applications. Adv. Intell. Syst. Comput. 2018, 635, 412–419. [Google Scholar]
- Hickman, K. The SSL Protocol; Netscape Communications Corp: Mountain View, CA, USA, 1995. [Google Scholar]
- Dierks, T.; Rescorla, E. The TLS Protocol Version 1.2. RFC 5246. Available online: https://tools.ietf.org/html/rfc5246 (accessed on 21 November 2019).
- Gu, X.; Gu, X. On the detection of fake certificates via attribute correlation. Entropy 2015, 17, 3806–3837. [Google Scholar] [CrossRef]
- Varela-Vaca, A.J.; Gasca, R.M. Towards the automatic and optimal selection of risk treatments for business processes using a constraint programming approach. Inf. Softw. Technol. 2013, 55, 1948–1973. [Google Scholar] [CrossRef]
- Oracle—Java Secure Socket Extension (JSSE) Reference Guide. 2018. Available online: https://docs.oracle.com/javase/8/docs/technotes/guides/security/jsse/JSSERefGuide.html (accessed on 3 September 2019).
- OpenSSL. Available online: https://www.openssl.org/ (accessed on 3 September 2019).
- LibreSSL. Available online: http://www.libressl.org/ (accessed on 3 September 2019).
- GNUTLS. Available online: https://www.gnutls.org/ (accessed on 3 September 2019).
- Al-Qershi, F.; Al-Qurishi, M.; Md Mizanur Rahman, S.; Al-Amri, A. Android vs. iOS: The security battle. In Proceedings of the 2014 World Congress on Computer Applications and Information Systems (WCCAIS), Hammamet, Tunisia, 17–19 January 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Onwuzurike, L.; de Cristofaro, E. Danger is my middle name: Experimenting with SSL vulnerabilities in Android apps. In Proceedings of the 8th ACM Conference on Security & Privacy in Wireless and Mobile Networks (WiSec’ 15), New York, NY, USA, 22–26 June 2015; ACM: New York, NY, USA, 2015. [Google Scholar] [CrossRef]
- Fahl, S.; Harbach, M.; Muders, T.; Baumgärtner, L.; Freisleben, B.; Smith, M. Why eve and mallory love android: An analysis of android SSL (in)security. In Proceedings of the 2012 ACM conference on Computer and Communications Security (CCS’ 12), Raleigh, NC, USA, 16–18 October 2012; ACM: New York, NY, USA, 2012; pp. 50–61. [Google Scholar] [CrossRef]
- Tendulkar, V.; Enck, W. An Application Package Configuration Approach to Mitigating Android SSL Vulnerabilities. arXiv 2014, arXiv:1410.7745. [Google Scholar]
- Moonsamy, V.; Batten, L. Mitigating Man-In-the-Middle Attacks on Smartphones—A Discussion of SSL Pinning and DNSSec. In Proceedings of the 12th Australian Information Security Management Conference; Edith Cowan University: Perth, Australia, 2014. [Google Scholar]
- Graves, J. SSL Pinning for Increased App Security. 2013. Available online: https://possiblemobile.com/2013/03/ssl-pinning-forincreased-app-security/ (accessed on 18 October 2019).
- Andzakovic, D. Bypassing SSL Pinning on Android via Reverse Engineering. 2014. Available online: https://security-assessment.com/files/documents/whitepapers/BypassingSSLPinningonAndroidviaReverseEngineering.pdf (accessed on 16 September 2019).
- Sierra, F.; Ramirez, A. Defending your android app. In Proceedings of the ACM Conference on Research in Information Technology, Chicago, IL, USA, 30 September–3 October 2015; pp. 29–34. [Google Scholar]
- OWASP—Mobile Security Testing Guide—Android Anti-Reversing Defenses. Available online: https://mobile-security.gitbook.io/mobile-security-testing-guide/android-testing-guide/0x05j-testing-resiliency-against-reverse-engineering (accessed on 16 September 2019).
- Apple Inc. Security Transforms Programming Guide. Available online: https://developer.apple.com/library/content/documentation/Security/Conceptual/SecTransformPG/SigningandVerifying/SigningandVerifying.html (accessed on 3 September 2019).
- ProGuard. Available online: https://www.guardsquare.com/en/proguard (accessed on 3 September 2019).
- iXGuard. Available online: https://www.guardsquare.com/en/ixguard (accessed on 3 September 2019).
- APKtool. Available online: https://ibotpeaches.github.io/Apktool (accessed on 3 September 2019).
- Penetration Testing Tool: Dex2jar Package. Available online: https://tools.kali.org/reverse-engineering/dex2jar (accessed on 3 September 2019).
- Android Developer: Logcat. Available online: https://developer.android.com/studio/command-line/logcat (accessed on 3 September 2019).
- SSLUnpinning—Certificate Pinning Bypass. Available online: https://repo.xposed.info/module/mobi.acpm.sslunpinning (accessed on 16 September 2019).
- Frida. Available online: https://www.frida.re/ (accessed on 3 September 2019).
- Objection. Available online: https://github.com/sensepost/objection (accessed on 3 September 2019).
| Category | Name |
|---|---|
| M1 | Improper Platform Usage |
| M2 | Insecure Data Storage |
| M3 | Insecure Communication |
| M4 | Insecure Authentication |
| M5 | Insufficient Cryptography |
| M6 | Insecure Authorisation |
| M7 | Client Code Quality |
| M8 | Code Tampering |
| M9 | Reverse Engineering |
| M10 | Extraneous Functionality |
| Control | Description |
|---|---|
| 5.1 | Data are encrypted on the network using TLS. The secure channel is used consistently throughout the app |
| 5.2 | The TLS settings are in line with current best practices, or as close as possible if the mobile operating system does not support the recommended standards |
| 5.3 | The app verifies the X.509 certificate of the remote endpoint when the secure channel is established. Only certificates signed by a trusted CA are accepted |
| 5.4 | The app uses its own certificate store, or pins the endpoint certificate or public key, and subsequently does not establish the connection with endpoints that offer a different certificate or key, even if signed by a trusted CA |
| 5.5 | The app does not rely on a single insecure communication channel (email or SMS) for critical operations, such as enrollments and account recovery |
| App | Principal Method | ||||
|---|---|---|---|---|---|
| Method 1 | Method 2 | Method 3 | Method 4 | Method 5 | |
| - | - | - | ✓ | ✓ | |
| NAB Bank app | - | - | - | ✓ | ✓ |
| Dropbox | - | - | ✓ | ✓ | ✓ |
| - | - | ✓ | ✓ | ✓ | |
| Bank of America | - | - | - | ✓ | ✓ |
| ✓ | ✓ | - | ✓ | ✓ | |
| ANZ GoMoney | - | - | - | ✓ | ✓ |
| PayPal | ✓ | - | - | ✓ | ✓ |
| MEGA | - | - | - | ✓ | ✓ |
| CopyApp | ✓ | ✓ | - | ✓ | ✓ |
| Name App | SSL Pinning | Root Detection | Tamper Detection | Debug Detection | Obfuscated |
|---|---|---|---|---|---|
| ✓ | - | - | - | ✓ | |
| NAB Bank app | ✓ | ✓ | ✓ | ✓ | ✓ |
| Dropbox | ✓ | - | - | - | ✓ |
| ✓ | ✓ | ✓ | ✓ | ✓ | |
| Bank of America | ✓ | ✓ | ✓ | ✓ | ✓ |
| ✓ | ✓ | ✓ | ✓ | - | |
| Outlook | ✓ | ✓ | ✓ | - | - |
| PayPal | ✓ | - | - | - | - |
| MEGA | ✓ | - | - | - | - |
| ✓ | ✓ | ✓ | ✓ | - |
| App | Principal Method | New Methods | |||||
|---|---|---|---|---|---|---|---|
| Method 1 | Method 2 | Method 3 | Method 4 | Method 5 | Method 6 | Method 7 | |
| - | - | - | ✓ | ✓ | - | ✓ | |
| NAB Bank app | - | - | - | - | - | - | - |
| Dropbox | - | - | ✓ | ✓ | ✓ | ✓ | ✓ |
| - | - | - | - | - | - | - | |
| Bank of America | - | - | - | - | - | - | - |
| - | - | - | - | ✓ | - | - | |
| Outlook | - | - | - | ✓ | ✓ | - | ✓ |
| PayPal | - | - | - | ✓ | ✓ | ✓ | ✓ |
| MEGA | - | - | - | ✓ | ✓ | ✓ | ✓ |
| - | - | - | - | ✓ | - | - | |
| Method 1 | Method 2 | Method 3 | Method 4 | Method 5 | Method 6 | Method 7 | |
|---|---|---|---|---|---|---|---|
| Root Detection | ⇌ | ⇌ | |||||
| Anti tampering | ⇌ | ⇌ | ⇌ | ||||
| Anti debugging | ⇌ | ⇌ | ⇌ | ⇌ | |||
| Obfuscation | ⇌ |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ramírez-López, F.J.; Varela-Vaca, Á.J.; Ropero, J.; Luque, J.; Carrasco, A. A Framework to Secure the Development and Auditing of SSL Pinning in Mobile Applications: The Case of Android Devices. Entropy 2019, 21, 1136. https://doi.org/10.3390/e21121136
Ramírez-López FJ, Varela-Vaca ÁJ, Ropero J, Luque J, Carrasco A. A Framework to Secure the Development and Auditing of SSL Pinning in Mobile Applications: The Case of Android Devices. Entropy. 2019; 21(12):1136. https://doi.org/10.3390/e21121136
Chicago/Turabian StyleRamírez-López, Francisco José, Ángel Jesús Varela-Vaca, Jorge Ropero, Joaquín Luque, and Alejandro Carrasco. 2019. "A Framework to Secure the Development and Auditing of SSL Pinning in Mobile Applications: The Case of Android Devices" Entropy 21, no. 12: 1136. https://doi.org/10.3390/e21121136
APA StyleRamírez-López, F. J., Varela-Vaca, Á. J., Ropero, J., Luque, J., & Carrasco, A. (2019). A Framework to Secure the Development and Auditing of SSL Pinning in Mobile Applications: The Case of Android Devices. Entropy, 21(12), 1136. https://doi.org/10.3390/e21121136