1. Introduction
With the rapid development of communication technology and the wide use of the Internet and mobile networks, people pay more and more attention to information security. The primary reference source for protecting data is cryptology [
1]. Because of its high performance, the chaotic system has attracted a lot of attention from researchers [
2].
There is an interesting relationship between chaos and cryptography. According to this relationship, many characteristics of chaotic systems such as the sensitivity of initial value/system parameters, ergodicity, deterministic dynamics, and structural complexity are considered to be the diffusion and confusion of keys [
3,
4,
5,
6]. Compared with traditional encryption systems, they have certain randomness [
7,
8]. As a result of this close relationship, several chaos-based cryptosystems have been put forward since 1990 [
9].
On the one hand, the extreme sensitivity of chaotic systems to initial conditions makes chaotic systems very attractive for cryptographic applications, especially for pseudo-random number generators (PRNGs) [
7,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21]. Several chaotic systems have been successfully used [
8] and play an important role in many applications such as numerical simulations, the game industry, communication and stochastic computation [
22]. On the other hand, PRNG is an important module in the development of cryptosystems to be robust against different types of security attacks. Some PRNGs have been implemented in personal computers and in embedded systems [
4,
23]. A PRNG is defined as an algorithm that can produce random number sequences whose main advantage is the rapidity and repeatability of a generating process, which is one of the most important components in stream cryptography [
20]. In practical applications, the generation is not trivial, and the randomness of generated sequences is the key to the selection of applications [
7].
Logistic map is one of the most commonly used chaotic map in chaotic cryptography for it is one of the simplest and most studied nonlinear systems [
24] and has been widely used in block ciphers, stream ciphers and hash functions. In 1947, Ulam and von Neumann proposed a PRNG based on the logistics map [
25]. Oishi and Inoue designed a PRNG by using chaos first order nonlinear difference equation in 1982 as well as construct a uniform random number generator with arbitrary Kolmogorov entropy [
17]. In 1999, Gonzalez and Pino put forward a truly unpredictable random function to help generate real random numbers by extending logistic map [
18]. Wang et al. realized the binary sequence of chaotic orbit with limited computational accuracy which was based on z-logistic mapping in 2006 [
19]. In 2009, Patidar [
9] and Patidar et al. [
7] proposed a novel pseudo-random bit generator based on two chaotic logistic maps and two chaotic standard maps, respectively. The chaotic maps are running side-by-side and starting from random independent initial conditions. Their schemes were studied for the NIST (National Institute of Science and Technology) and DIEHARD tests suites, which are considered the most stringent statistical tests suites for randomness [
26]. In 2013, François M et al. presented a PRNG algorithm based on mixing three chaotic maps produced from an input initial vector [
13] which uses the standard chaos function and linear congruence to calculate and index the arranged position and passes the test of the NIST test suite. In the raised schemes, many researchers have proposed similar feedback approaches [
9,
27,
28] such as Patidar achieved the continuous operation of PRNGs by using the value generated by the previous chaotic system as the initial value of the next iteration of chaotic systems [
9]. In 2016, Xu D et al. proposed separate chaotic mapping from linear feedback shift register (LFSR), where the results of chaotic iteration are quantified after the binary bit sequence is reached, xor is performed with the m sequence outputted by the LFSR to realize the disturbance, and finally the disturbance result is returned to the input of the chaotic iterative system for the next round of iterative operations [
14]. In the PRNG based on the piecewise logistic chaotic system proposed by Wang et al., the parameter m is used to limit the system parameters of a chaotic system and adjust its next iteration to remedy the randomness problem [
20].
At the present stage, the research of PRNG based on chaos focuses on the complexity of random bit extraction which attaches importance to reduce the possibility of extracting chaotic information by improving the complexity of the algorithm. Because all chaotic systems are deterministic systems, chaotic behavior can be identified by some methods in chaos theory [
22] which means it is not safe to design PRNG with fixed system parameters. The idea of feedback is used to realize the continuous output of pseudo-random numbers, but the correlation between the previous and next is the key to security. An algorithm is proposed on the basis of the logistic chaotic system, which can realize the iteration of the pre-and-post chaotic system and the independence of the pre-and-post iteration. The change of parameters of the chaotic system in the algorithm has no statistical regularity, then realizes the generation of the pseudo-random sequence would be safe enough from the point of view of the chaotic system. After the analysis, it was found that it had good randomness and no obvious statistical information.
2. Pseudo-Random Sequence Generator Algorithm
The process of the PRNG’s generation in this paper can be divided into initial state and normal state. Seed parameters need to be selected manually in the initial state [
29], while seed parameters need not be selected manually in the normal state. The selection of normal seed parameters is related to the generation of antecedent pseudo-random sequences.
2.1. Generation of Initial Pseudo-Random Sequences
Select the initial seed parameters , where is the system parameter, is the initial value and is the number of iterations. is the value range of , is the value range of , more than 1000 is required to improve the randomness of the sequence . The value of the initial seed parameter is arbitrary.
According to logistic chaos equation, we can get 16 floating point numbers by iterating for times.
Discarding the integer part of could get a 15-decimal number, respectively arbitrary select 3 digits to form a 3-decimal number, 4 digits to form a 4-decimal number, 5 digits to form a 5-decimal number, all the way up to 15 digits to make up a 15-decimal number. A whole numerical sequence is obtained by taking each decimal number module 256 and converting it into a binary sequence, which is a pseudo-random sequence generated at the initial state. Also, 104 numbers of pseudo-random sequences can be generated by one chaotic iteration.
2.2. Generation of Normal Pseudo-Random Sequences (Taking the Nth Times as an Example)
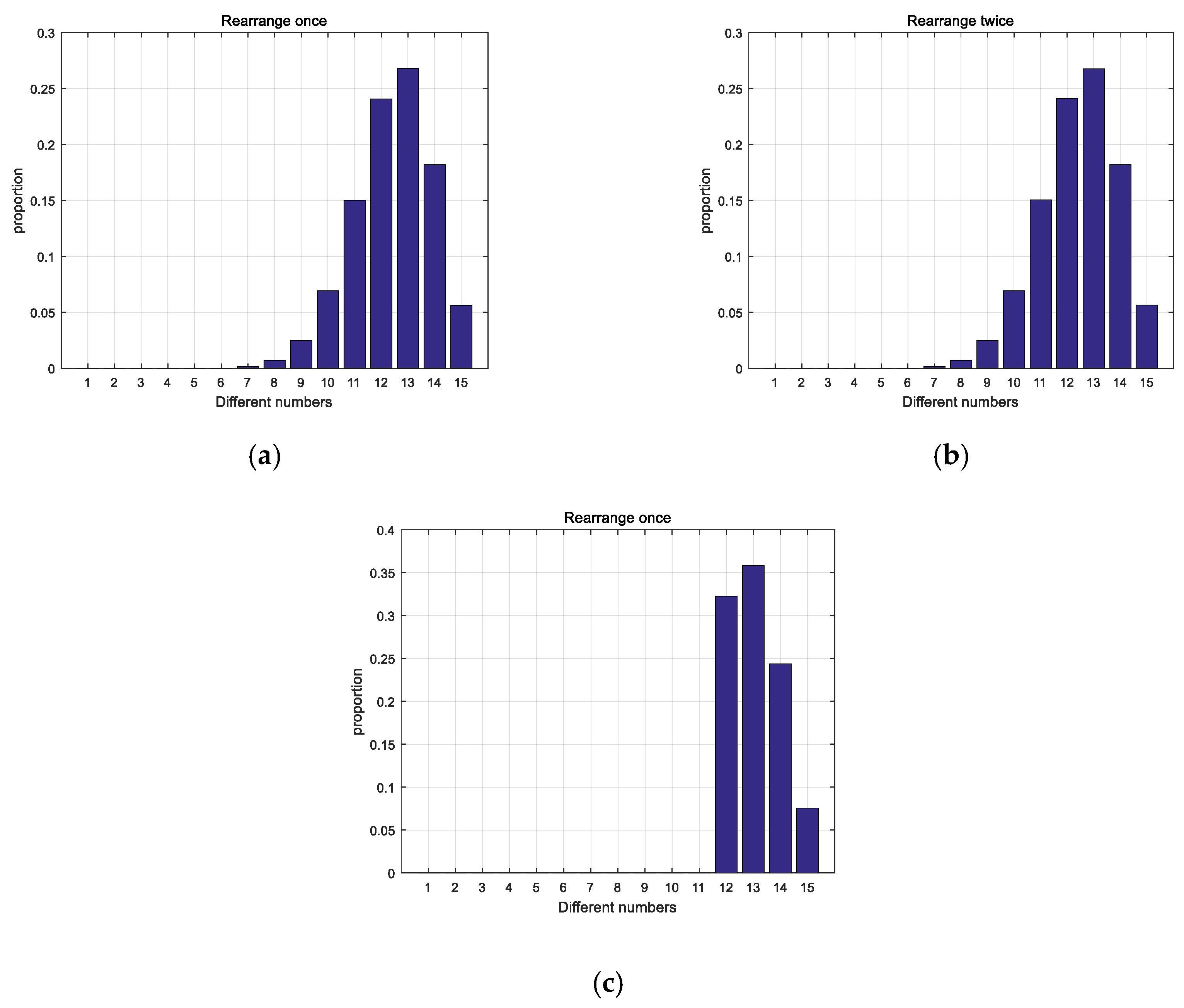
Retain the fractional part of the floating point number generated at the th, thus a 15 decimal number can be got and then rearrange it for once time. If the different number of positions after rearranging between the previous and next time is less than 12, it will be rearranged again until the condition is met. The 1st, 5th, 9th and 13th numbers are taken to form the decimal part with the integer part 0 as the initial value of the chaotic system.
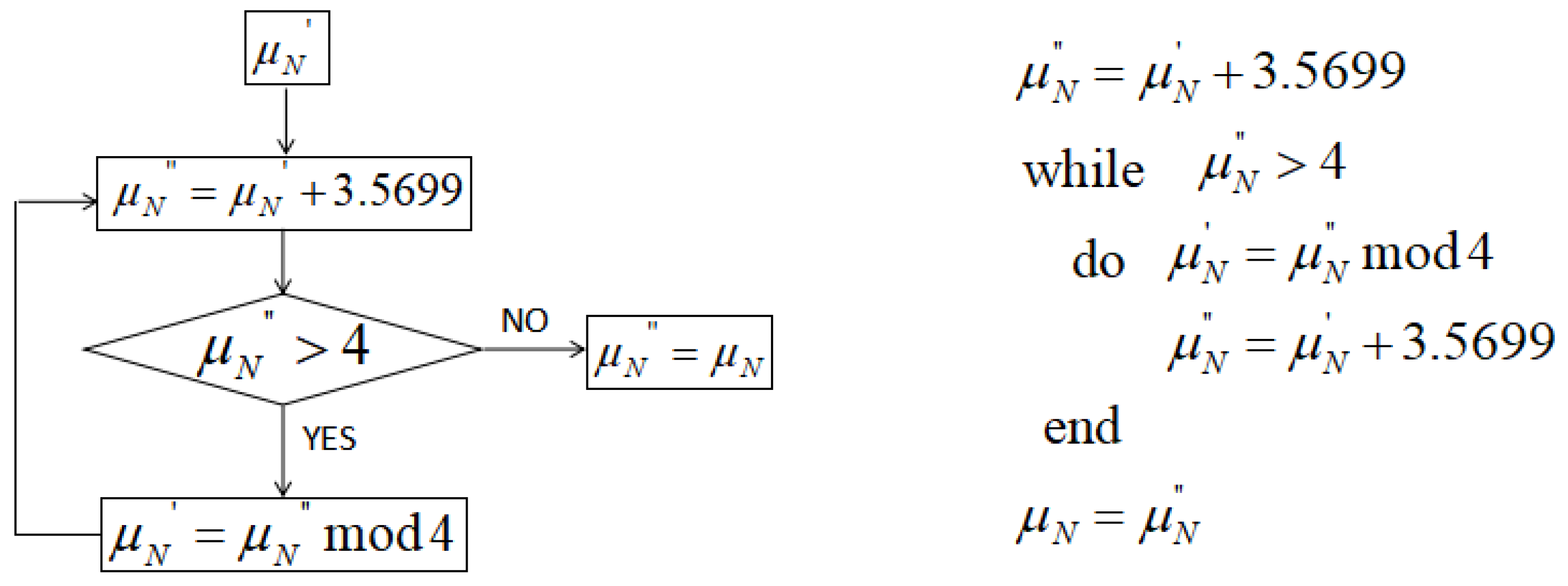
The 2nd, 6th, 10th, and 14th digits are taken as the preparatory system parameter
of the chaotic system. The flow chart of the generation of
is shown in
Figure 1. The algorithm description is also given together.
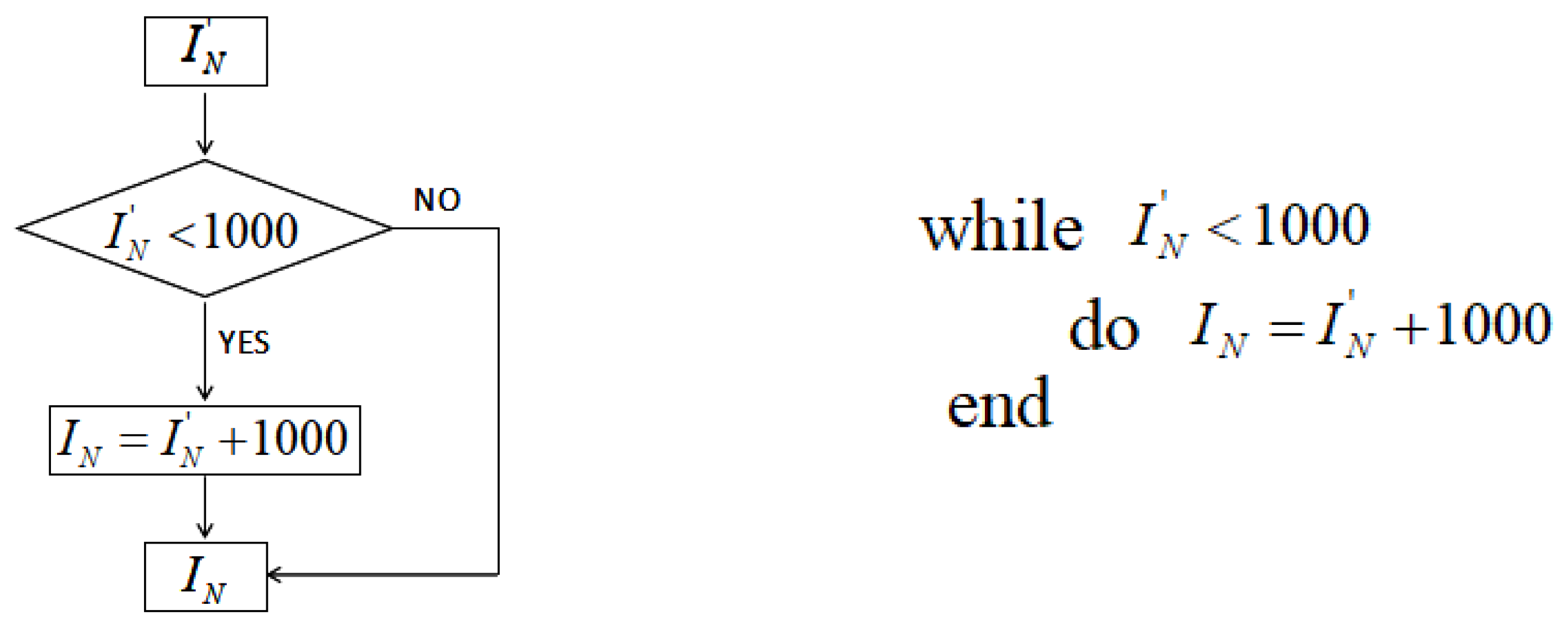
The 3rd, 7th, 11th, and 15th digits are taken to form the 4-bit integeral
. To be within a better range, the flow chart of the iteration number
’s generation is shown in
Figure 2. The algorithm description is also given.
4. Conclusions
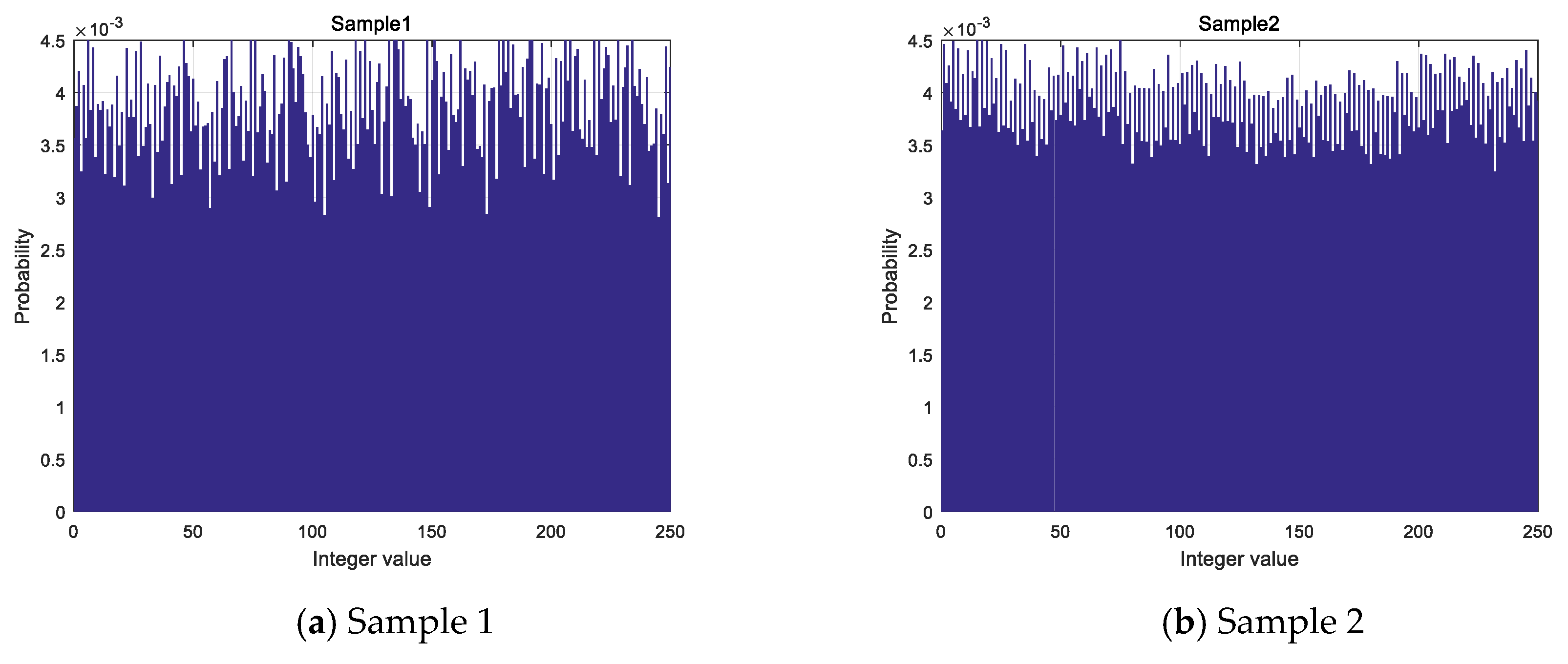
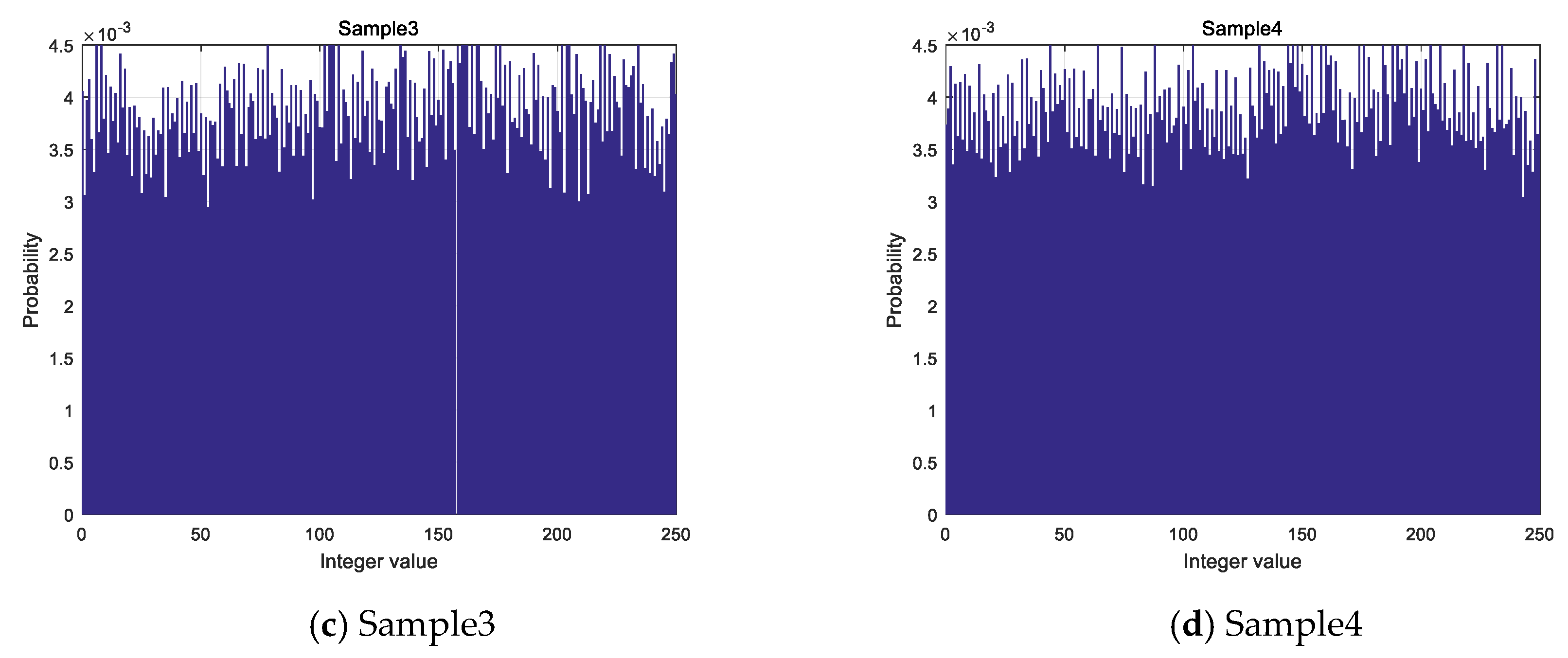
This paper proposes a PRNG based on a logistic chaotic system. Aiming at the security of chaotic system parameters in the process of generating pseudo-random number sequences, the floating point numbers generated by initial state chaotic systems are rearranged and extracted. The system parameters of the next chaotic system are generated on this basis. The next chaotic system’s system parameters are extracted from the 15 number sequences generated by the previous time. The rearrangement increases the key space, which makes the system parameters of the chaotic system uncontrollable and has no statistical properties, and key space after increasing makes it difficult for exhaustive attacks. On the one hand, the pseudo-random sequence can be output infinitely, which is strong enough to meet all kinds of encryption needs. On the other hand, due to the perfect performance of the logistic chaotic system, the security of the output sequence is strong. The analysis of the characteristics of the logistic chaotic system and integer value sequence shows that the generated pseudo-random sequence has good randomness and independence from the aspects of the histogram, information entropy, numerical calculation, and proportional value.