Abstract
We investigate the secure degrees of freedom (s.d.o.f.) of three new channel models: broadcast channel with combating helpers, interference channel with selfish users, and multiple access wiretap channel with deviating users. The goal of introducing these channel models is to investigate various malicious interactions that arise in networks, including active adversaries. That is in contrast with the common assumption in the literature that the users follow a certain protocol altruistically and transmit both message-carrying and cooperative jamming signals in an optimum manner. In the first model, over a classical broadcast channel with confidential messages (BCCM), there are two helpers, each associated with one of the receivers. In the second model, over a classical interference channel with confidential messages (ICCM), there is a helper and users are selfish. By casting each problem as an extensive-form game and applying recursive real interference alignment, we show that, for the first model, the combating intentions of the helpers are neutralized and the full s.d.o.f. is retained; for the second model, selfishness precludes secure communication and no s.d.o.f. is achieved. In the third model, we consider the multiple access wiretap channel (MAC-WTC), where multiple legitimate users wish to have secure communication with a legitimate receiver in the presence of an eavesdropper. We consider the case when a subset of users deviate from the optimum protocol that attains the exact s.d.o.f. of this channel. We consider two kinds of deviation: when some of the users stop transmitting cooperative jamming signals, and when a user starts sending intentional jamming signals. For the first scenario, we investigate possible responses of the remaining users to counteract such deviation. For the second scenario, we use an extensive-form game formulation for the interactions of the deviating and well-behaving users. We prove that a deviating user can drive the s.d.o.f. to zero; however, the remaining users can exploit its intentional jamming signals as cooperative jamming signals against the eavesdropper and achieve an optimum s.d.o.f.
1. Introduction
Physical layer security techniques allow secure transmission of information (in absolute sense) without the need for encryption keys [1]. Consequently, the problems of exchanging encryption keys across open wireless networks are mitigated. In the seminal work [2], Wyner showed that secure communication through a degraded wiretap channel is possible by exploiting the noisy nature of the channel. The problem was extended to general wiretap channel, which may not be necessarily degraded by Csiszar and Korner in [3]. The physical layer security framework was then extended to various multiuser settings such as: the multiple access wiretap channel (MAC-WTC) [4], broadcast channel with confidential messages (BCCM) [5,6,7,8,9], interference channel with confidential messages (ICCM) [5], multireceiver wiretap channels [10,11], and relay-eavesdropper channels [12]. In the absence of exact secrecy rates, secure degrees of freedom (s.d.o.f.) provide a first order approximation to the secrecy rate by giving their scaling with , where P is the total average transmitted power. The s.d.o.f. have been considered in the literature in many multiuser channel models, such as helper wiretap channel [13,14], multiple-access wiretap channel [13,15,16,17], interference channel [13,17,18,19,20,21,22], X-channel [23,24], half-duplex relay channel [25], compound wiretap channel [26], diamond channel [27], MIMO wiretap Y channel [28], multiuser channel models under imperfect CSIT [29,30,31,32,33]. An investigation of the intercept probability in the presence of eavesdropping attack and interference can be found in [34].
In this work, we investigate extended versions of BCCM, ICCM, and MAC-WTC channel models. Information-theoretic security for discrete memoryless interference and broadcast channels with confidential messages were studied in [5]. BCCM consists of a transmitter and two receivers. The transmitter has two messages, each directed to one of the receivers and needing to be kept secure from the other receiver. The s.d.o.f. of Gaussian BCCM is zero for each user [13]. However, with an altruistic system helper, each user in the BCCM can have an s.d.o.f. of [13]. ICCM consists of two transmitters and two receivers. Each transmitter has a message that needs to be conveyed reliably to one of the receivers and needs to be kept secret from the other receiver. The s.d.o.f. of Gaussian ICCM is for each user [13]. With an altruistic system helper, each user in the ICCM can have an s.d.o.f. of [13]. In both of these systems, this eventual s.d.o.f. per user requires perfect coordination between the transmitters and the helper, even if that obliges the transmitters to jam their own receivers as in the case of ICCM.
In MAC-WTC, which was introduced in [4,35], multiple legitimate users wish to have secure communication with a legitimate receiver in the presence of an eavesdropper. The secrecy capacity region of the MAC-WTC is still unknown, even in the simple Gaussian setting [4,13,15,17,35,36,37]. Recently, [13] and [17] determined the exact sum s.d.o.f. and the entire s.d.o.f. region, respectively, of the MAC-WTC. The exact sum s.d.o.f. of a K-user MAC-WTC is [13]. The achievability of this sum s.d.o.f. requires all users to send signals in a certain optimum manner. The main tools in the achievability are: structured signaling, channel prefixing, cooperative jamming, and interference alignment. In the optimum scheme, each user sends streams of message-carrying signals and 1 stream of cooperative jamming signal. The signals are simultaneously aligned at the two receivers: At the eavesdropper, all message-carrying signals are aligned with a cooperative jamming signal, which ensures that the information leakage to the eavesdropper is zero in the s.d.o.f. sense; at the legitimate receiver, all cooperative jamming signals are aligned in a single dimension occupying the smallest space, thereby leaving the largest space for message-carrying signals. The total number of dimensions created at the legitimate receiver is , and one dimension is lost for the cooperative jamming signals, hence achieving a sum s.d.o.f. of .
All these works assume that all nodes are altruistic and follow a prescribed transmission policy in order to maximize the sum secure rate of the entire system. In this paper, we investigate BCCM, ICCM, and MAC-WTC channel models in the case of selfish and malicious behavior, where the users/helpers do not perform the system-wide-optimal altruistic behavior but apply a selfish strategy and/or take sides by aiming to help one user and potentially hurt the other. These new models are extensions of the ones studied in [4,5,13] and are a step forward in studying channel models with active adversaries. We use s.d.o.f. metric to quantify the effects of these malicious behaviors. For BCCM and ICCM channel models, we note a self-enforcing property: Even with the excessive capabilities of the helpers/users (infinite power and all-knowing entities), these capabilities are naturally restricted in these channel models due to the users’/helpers’ interest in reliable communication to/with their own receivers. That is, no entity can use infinite powered Gaussian jamming signals which would wipe out the communication for everybody. This self-enforcing property necessitates users to apply selective jamming via interference alignment. This motivates studying such jamming techniques and analyzing their effect on the s.d.o.f. of the users. In addition, a careful look at the achievable scheme for the MAC-WTC in [13] reveals that the cooperative jamming signal of each user protects parts of the message-carrying signals of the other users; and that no user can protect its own signals. This creates an interesting ecosystem where each user strictly depends on the rest of the users for its own security. The fact that a user’s cooperative jamming transmission does not contribute to its own security but at the same time uses up its own transmit power may motivate some selfish users not to send cooperative jamming signals. In this work, we investigate the effects of such (and worse) deviations from the optimum signaling scheme on the system s.d.o.f., and the actions that the rest of the users can take to compensate for such behavior.
In the first model, which is the BCCM with combating helpers, there are two helpers, where each helper takes the side of one of the receivers and at the same time aims to hurt the secure communication to the other receiver. The two helpers have contradicting objectives and hence are combating. Helpers in this model do not coordinate with the transmitter as in [13]. We use a stringent objective function for each helper: Each helper minimizes the s.d.o.f. of the other receiver, while not decreasing the s.d.o.f. of its own receiver by its action. We formulate the problem as an extensive-form game [38], which is a sequential strategic game, where every player (node) acts according to its information about the other nodes’ actions in previous transmission frames. We investigate achievable schemes that use real interference alignment [39] in a recursive way. We prove that under this stringent objective function and recursive real interference alignment, the malicious behaviors of the two combating helpers are neutralized, and the s.d.o.f. for each user converges to the optimal s.d.o.f. of per user [13], as if both helpers are altruistic.
In the second model, which is the ICCM with selfish users, there is an external system helper. In this model, the users do not coordinate as in the optimal strategy in [13] instructs. The users are selfish and want to hurt the other receiver; each transmitter’s goal is to maximize the difference of the s.d.o.f. between the two receivers. This permits each user to jam its own receiver if this hurts the other receiver more, making self-jamming more natural here than the optimum scheme in [13]. There is a neutral helper in this system which aims to maximize the s.d.o.f. of the system. Using the extensive-form game formulation and recursive real interference alignment, we show that the selfishness of the users precludes any secure communication and drives the s.d.o.f. of both users to zero, despite the existence of a mediating helper.
In the third model, which is the MAC-WTC with deviating users, we first consider the case where M out of K users deviate by not transmitting cooperative jamming signals. We start by evaluating the achievable sum s.d.o.f. when the remaining users do not change their original optimum strategies. We show that the sum s.d.o.f. of the system decreases, and deviating users do not benefit from their actions. Then, we consider two possible counterstrategies by the remaining users: In the first strategy, all users decrease their rates to ensure that all message-carrying signals are protected by the remaining cooperative jamming signals, and leakage s.d.o.f. is zero. We show that, in this case, the individual s.d.o.f. of the deviating users increase. Hence, deviating users gain at the expense of well-behaving users. In the second strategy, we allow the leakage s.d.o.f. to be nonzero but constrain leakage in a single dimension. We show that, although the sum s.d.o.f. of the system is lower than in the case of the first counterstrategy, this strategy decreases the individual s.d.o.f. of the deviating users and increases the s.d.o.f. of well-behaving users. Next, we consider a more severe form of deviation by considering one user turning malicious and sending intentional jamming signals. As this deviating user has infinite power, it can wipe out all communication, secure or otherwise, if it sends Gaussian signals. For the sake of a meaningful formulation, we restrict the strategy set of this deviating user to be of structured signaling and alignment type. Under this restriction, we formulate the problem as an extensive-form game [38]. We show that this deviating user can drive the s.d.o.f. of the system to zero. We then show that, interestingly, the remaining users can utilize these intentional (malicious) jamming signals to protect more message-carrying signals at the eavesdropper, achieving a sum s.d.o.f. of . We prove that this sum s.d.o.f. matches the sum s.d.o.f. of a user MAC-WTC with 1 external altruistic helper, thereby showing that the system turns a malicious jammer into an altruistic helper, i.e., the deviating user benefits the system against its intentions.
Organization: In Section 2, we focus on the BCCM with combating helpers. In Section 3, we consider the ICCM with selfish users. Finally, in Section 4, we consider the MAC-WTC with deviating users. For each model, we first give the formal description of the channel model, then we present our proposed achievable schemes.
2. BCCM with Combating Helpers
2.1. System Model and Assumptions
In BCCM, the transmitter has two private messages and picked from the message sets uniformly with rates , , respectively, where , where n is the length of the codeword. Each message should be received reliably by the ith receiver, while being kept secure from the jth receiver, :
where is the mutual information between the random variables, X and Y, and is the estimate of at the ith receiver. The s.d.o.f. is defined as , where P is the transmitter power constraint .
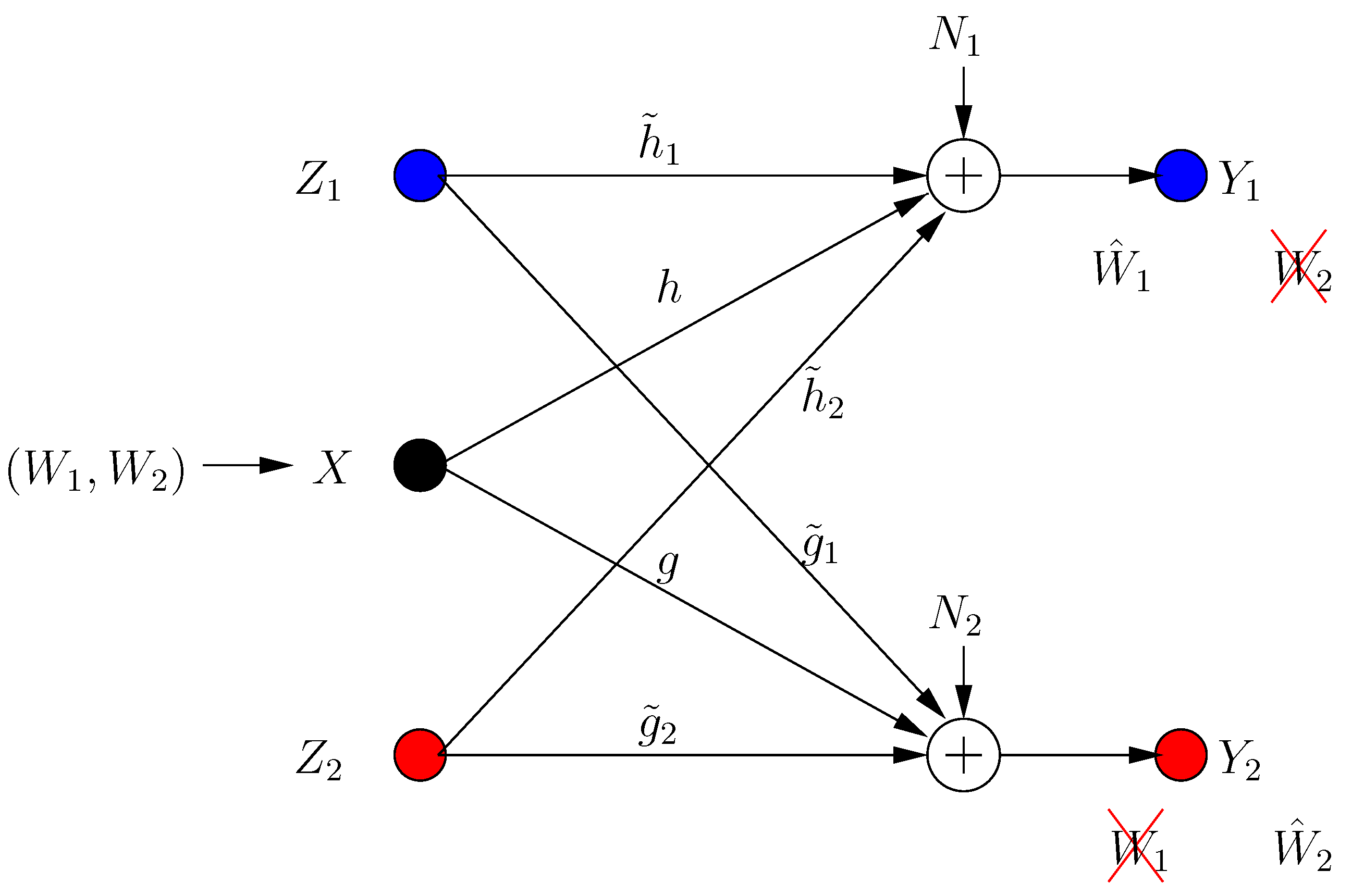
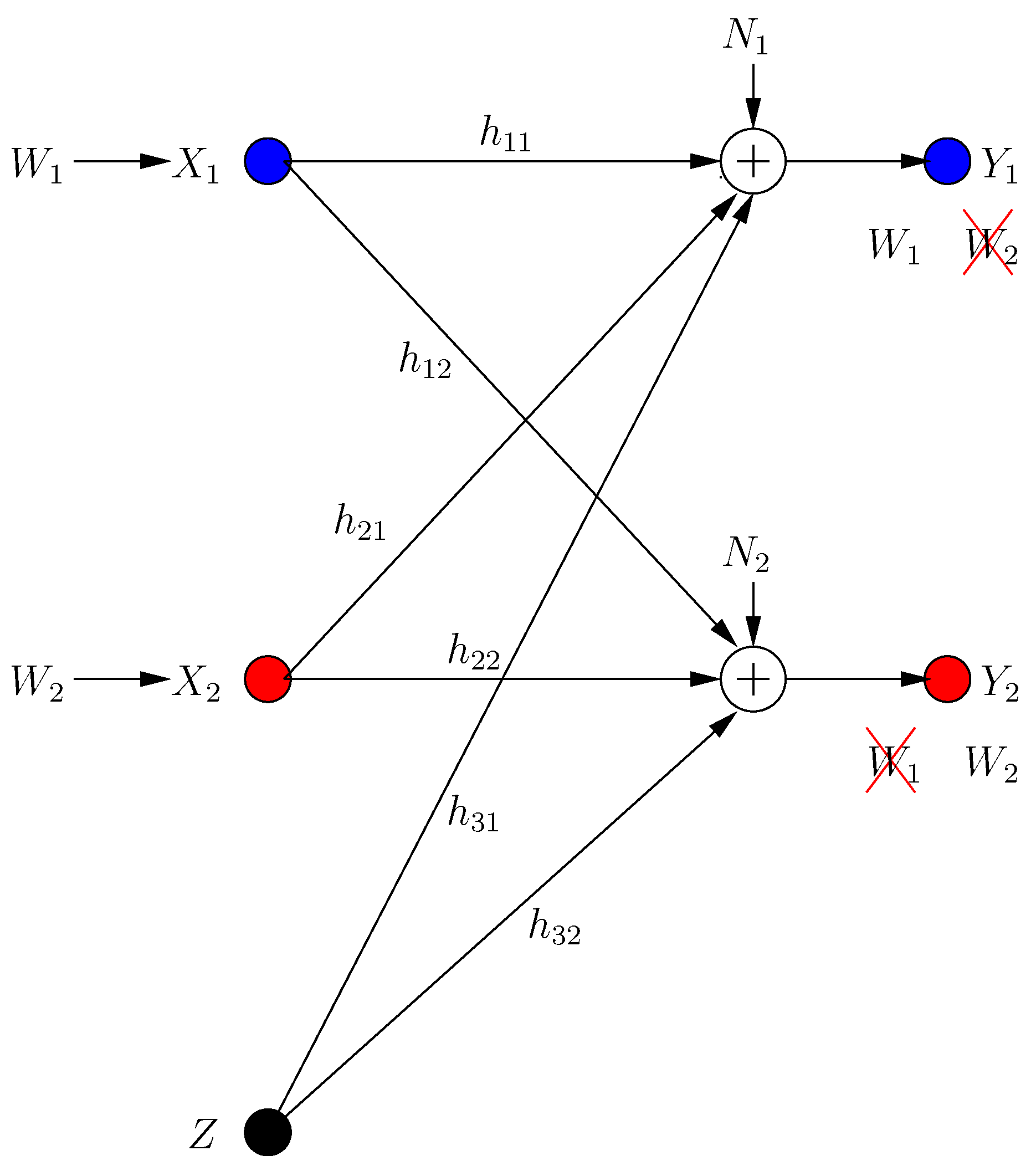
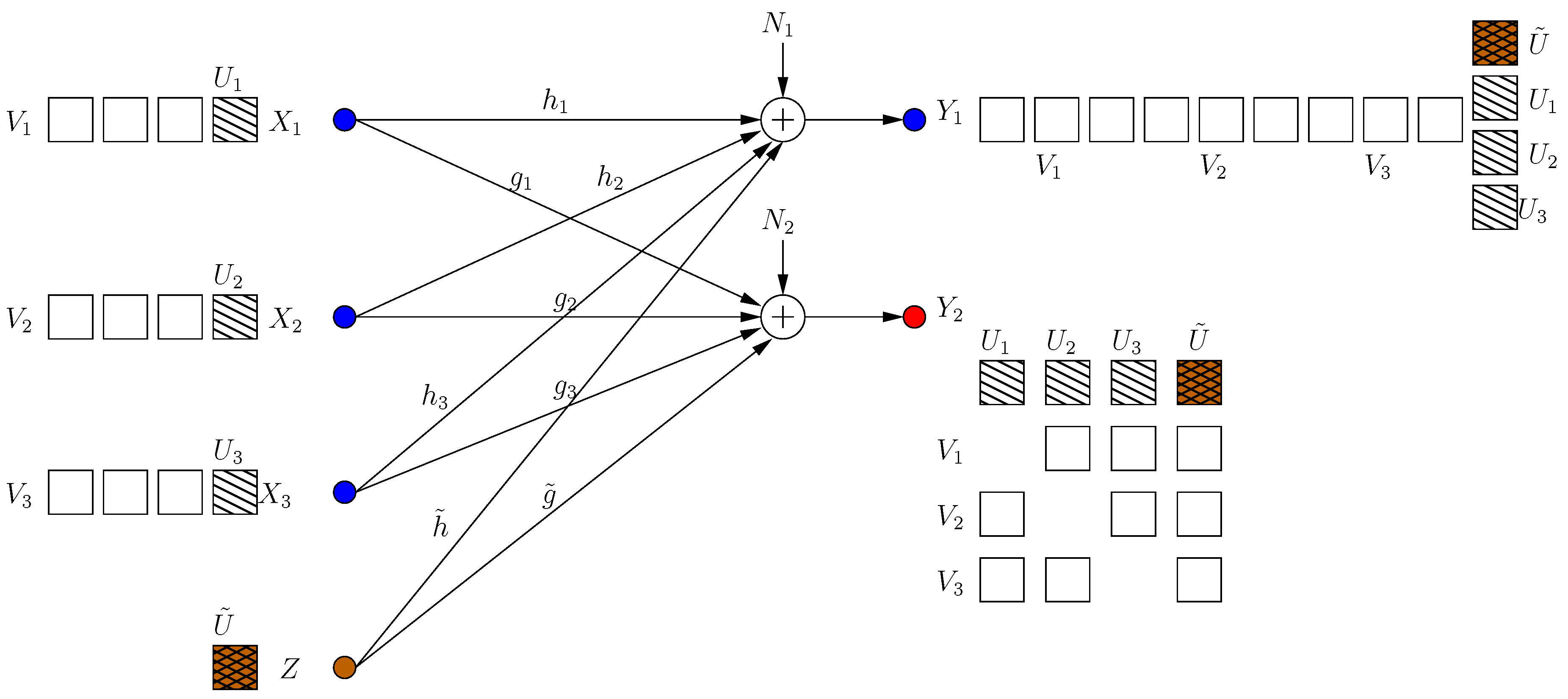
The system has two helpers with inputs and , with the power constraints . Each helper assists secure transmission to one of the receivers. The input/output relations for the BCCM with combating helpers (see Figure 1) are:
where is the received signal at the ith receiver in the kth transmission frame, h, g are the channel gains from the transmitter to receivers 1, 2, respectively, and , are the channel gains from helper i to receivers 1, 2, respectively.
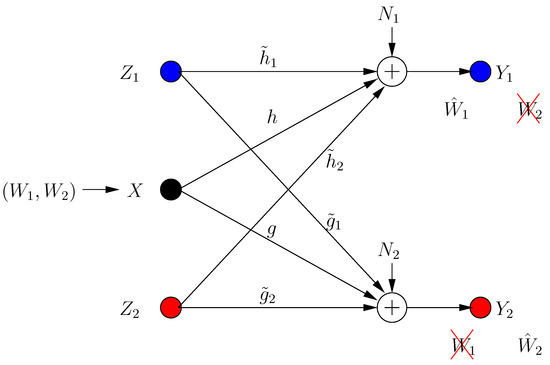
Figure 1.
Broadcast channel with confidential messages (BCCM) with combating helpers.
The helpers are combating as they maximize the s.d.o.f. of one user only, while hurting the other user by sending jamming signals. The transmitter acts in even transmission frames, and helpers respond in odd frames. Each node has perfect channel state information (CSI) and knows the actions of others at the end of every frame. We require that the action of a helper does not hurt its own receiver (in terms of s.d.o.f.) if no new jamming signals are produced by the other helper. Consequently, we formalize the role of the ith helper as:
where and is the s.d.o.f. of the jth user in the kth transmission frame, where k is odd. On the other hand, the transmitter does not take the side of any of the users and maximizes the sum s.d.o.f. of the system, i.e., transmitter’s role in even encoding frames is:
2.2. Achievable Scheme: Recursive Real Interference Alignment as Extensive-Form Game
We use recursive real interference alignment as the achievable strategy for our model. At encoding frame k, all secure and jamming signals are picked from PAM constellation set , where is the minimum distance between any two points in the constellation and is the number of points.
2.2.1. For Frames ,
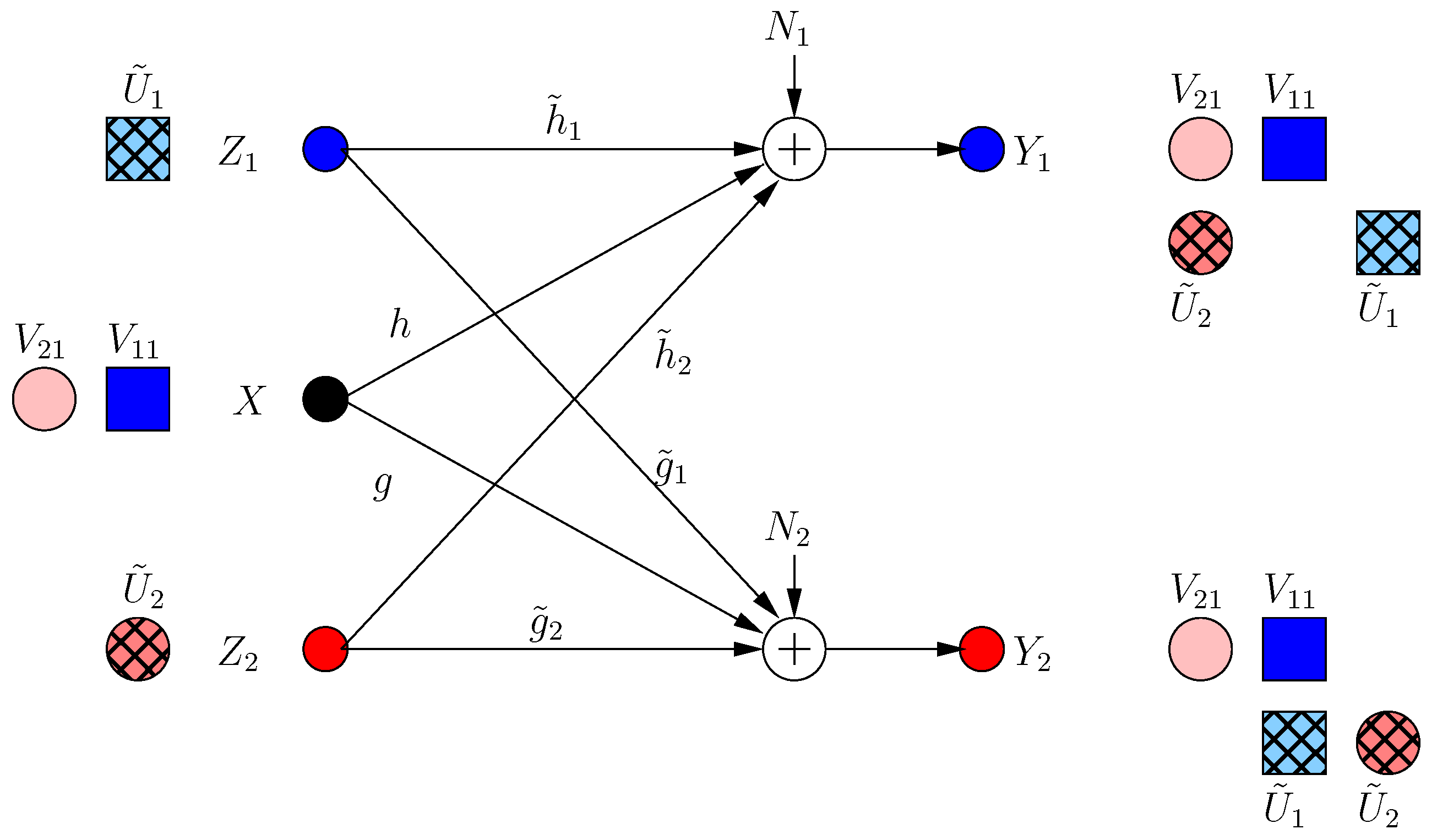
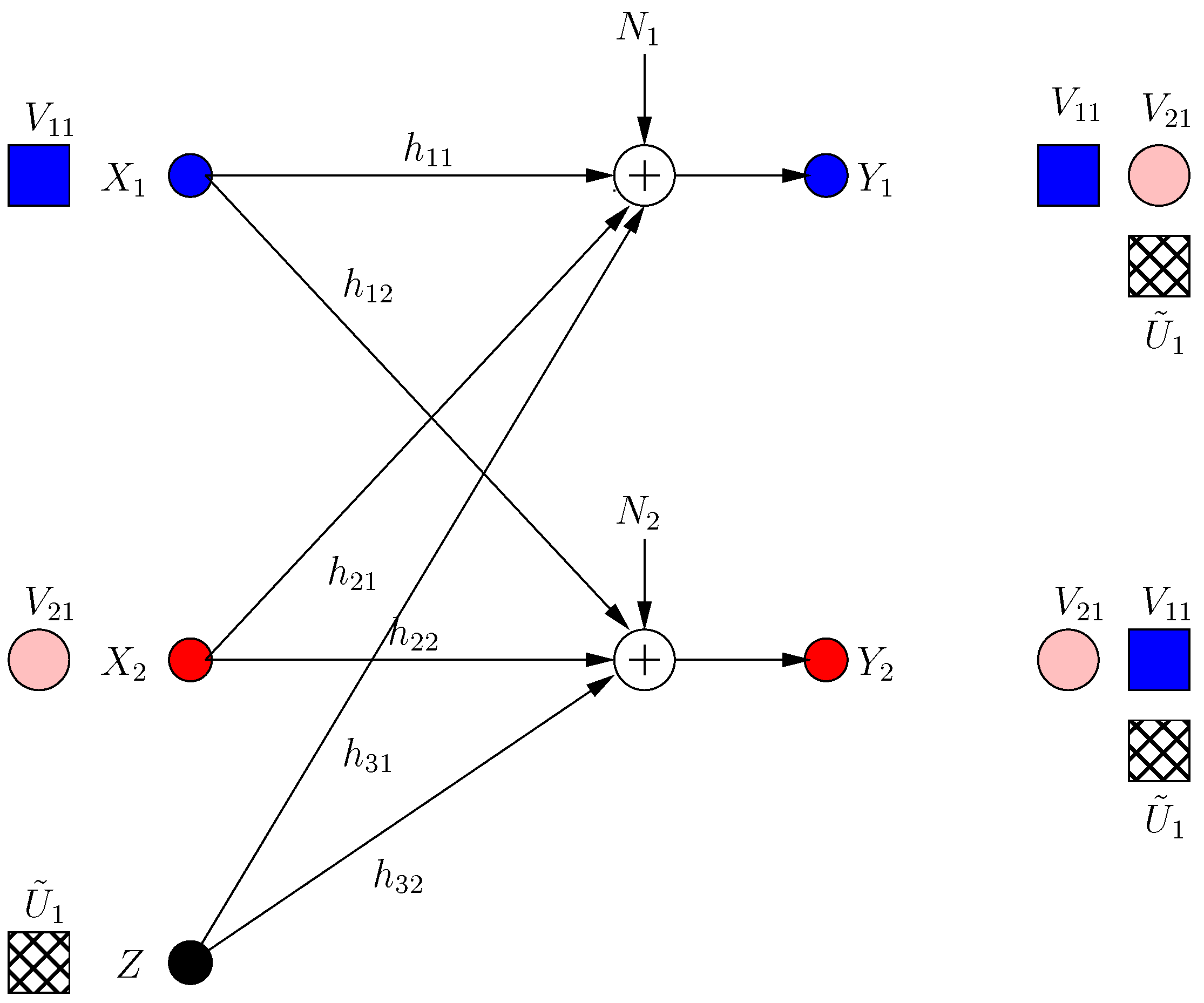
Frames 0 and 1 are considered transient frames. For frame 0, the transmitter performs the optimal strategy in the presence of helpers [13] and sends two signal components , in two irrational dimensions:
where , are rationally independent scalars. These message-carrying signals are not secured. None of the helpers expects the other helper to jam its own receiver; thus, each helper needs to protect the message of its own receiver at the other receiver. Hence, at , the ith helper sends a structured jamming signal in the irrational dimension where its message-carrying signal lies at the other receiver as:
Then, the received signals are:
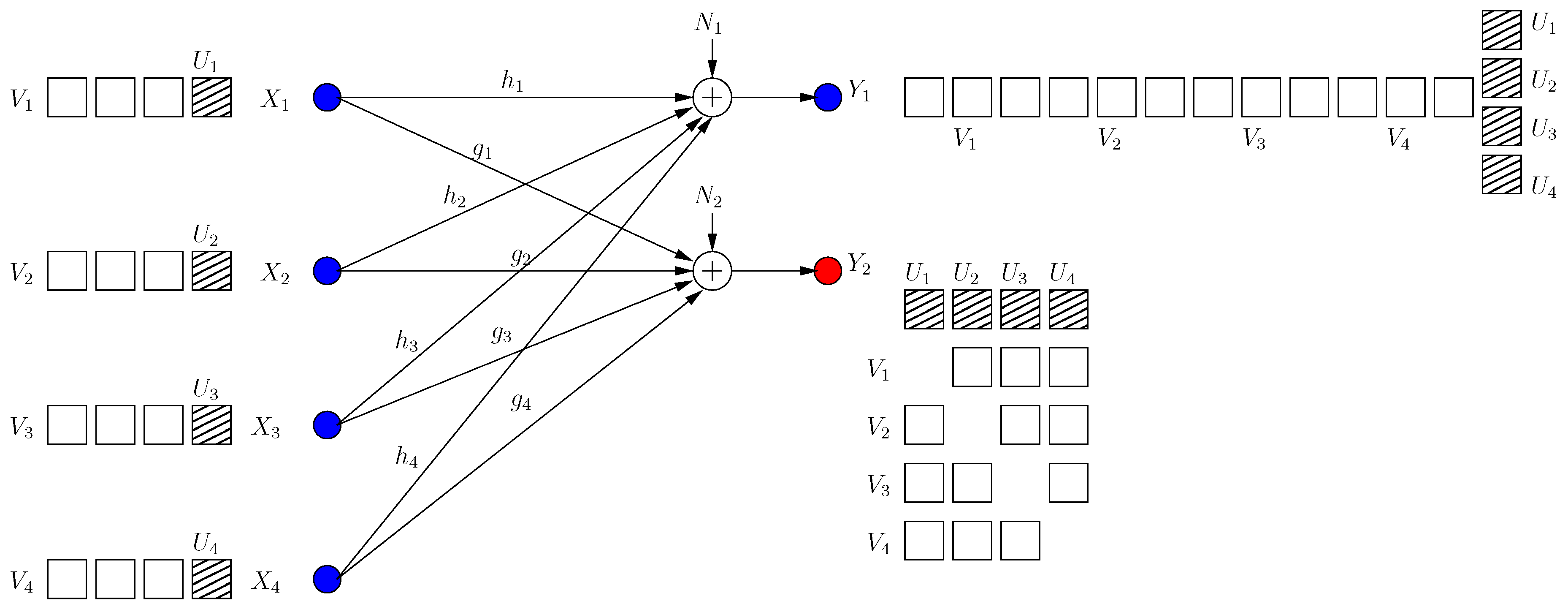
Although , are now secure, this results in a new irrational dimension at each receiver as in Figure 2. Hence, for each user as we show formally in Section 2.3 (instead of in BCCM with coordinating helpers).
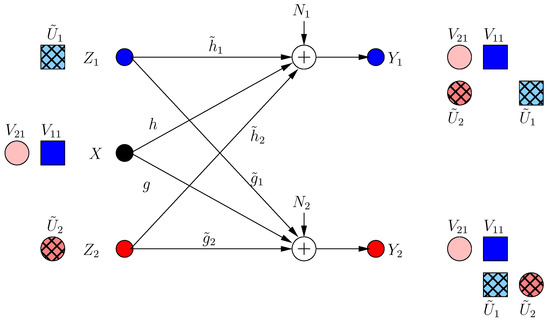
Figure 2.
BCCM frame . Pink circle and blue square denote user signals, and the hatched circles/squares denote corresponding helper jamming signals.
2.2.2. For Frame
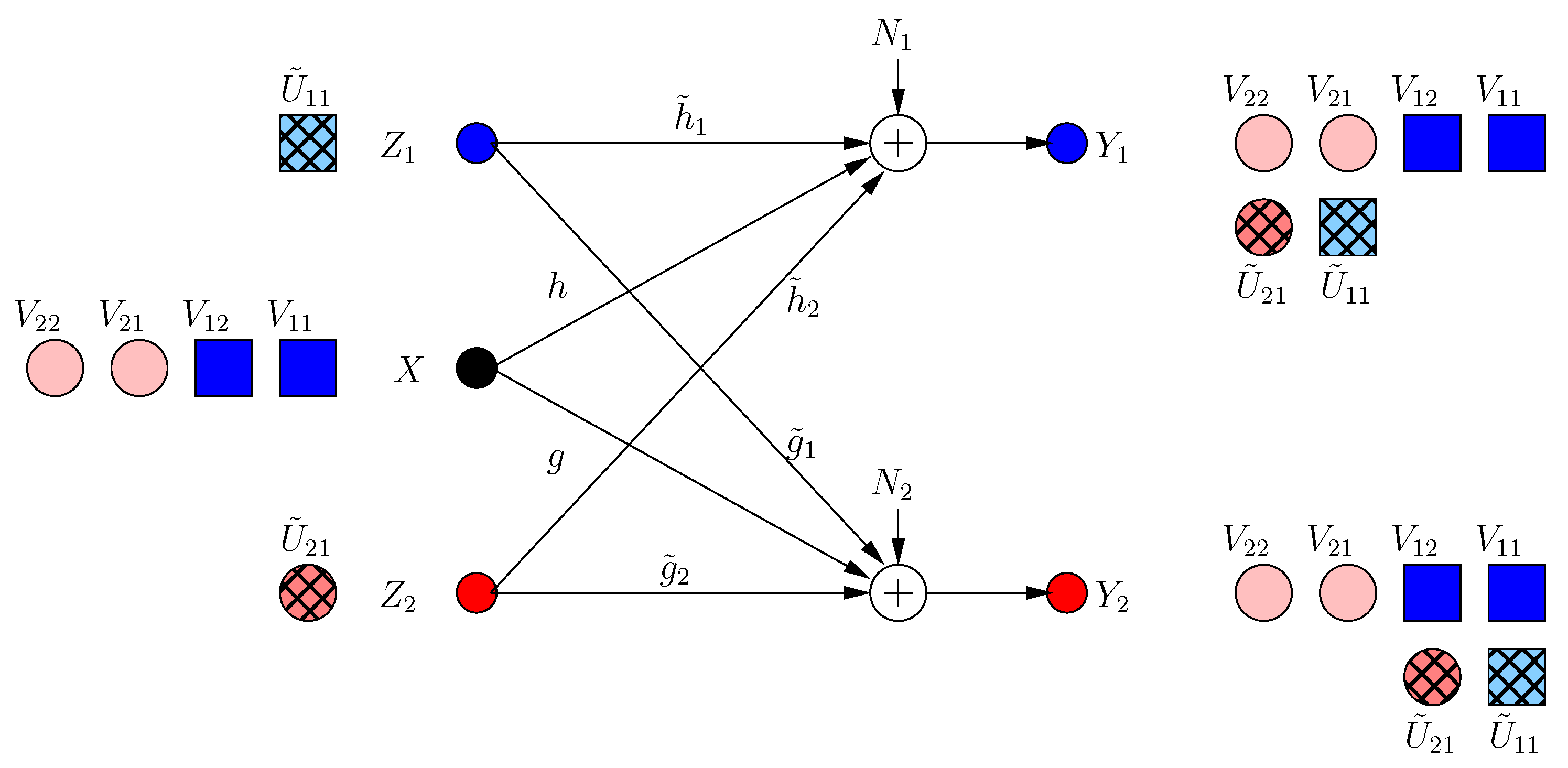
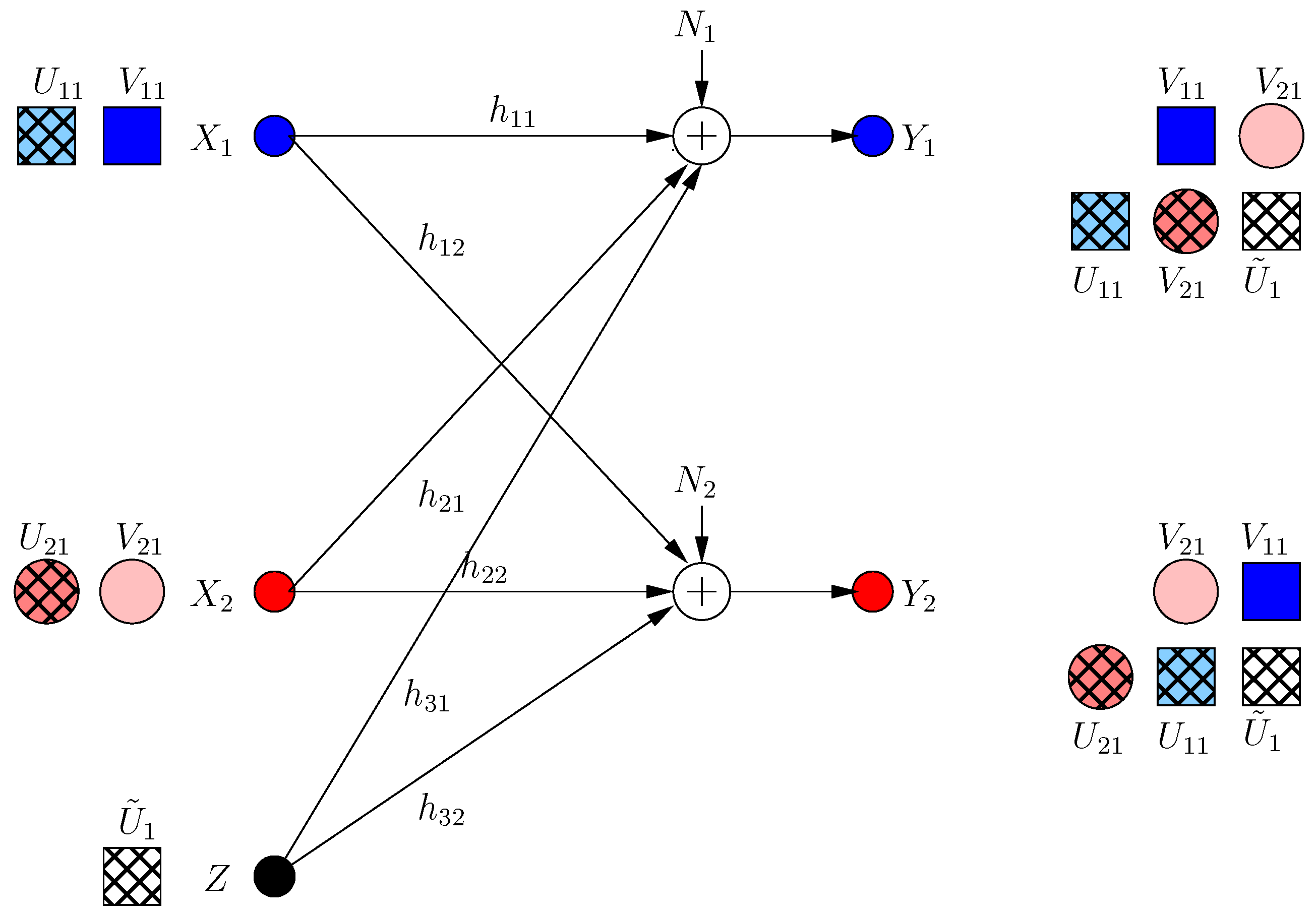
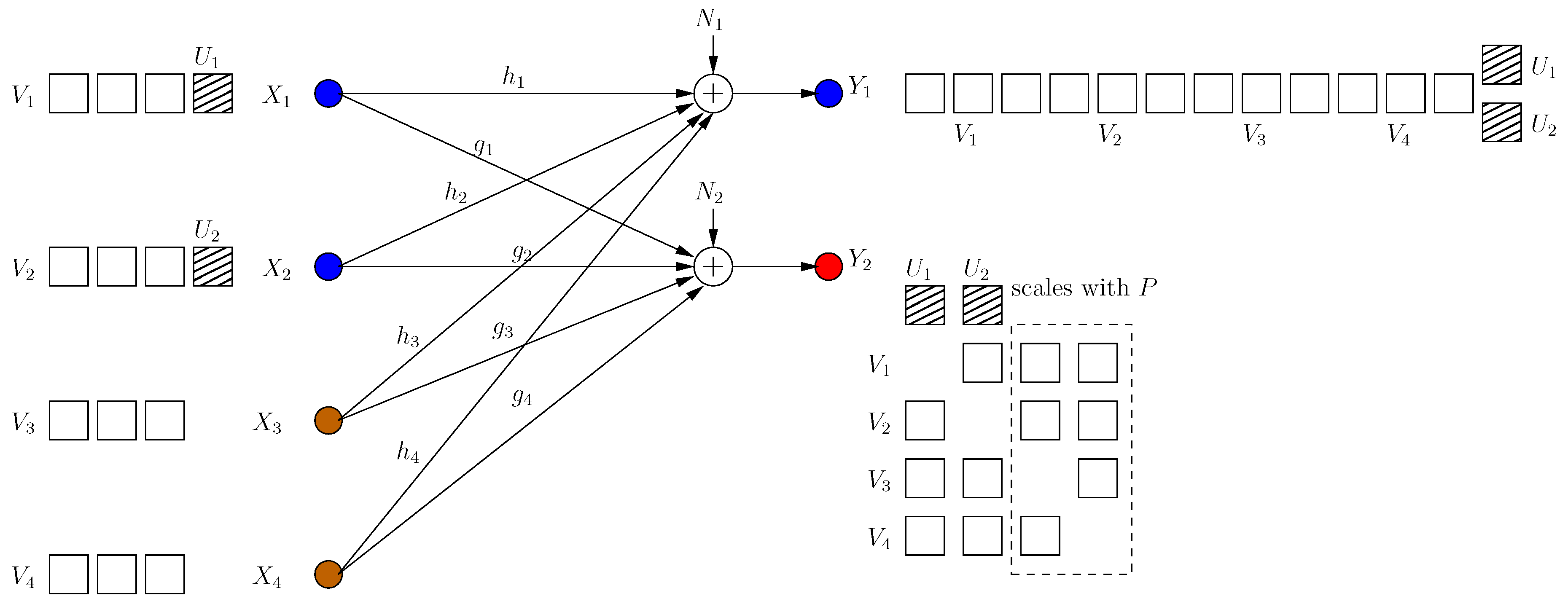
The transmitter knows that a new irrational dimension is generated within frame . The transmitter uses this dimension in its favor, as it can protect more message-carrying signals. It produces two new message-carrying signal components , to be aligned with the generated jamming dimensions in frame as:
That is, the transmitter appends its last frame transmission with two new signal components in rationally independent dimensions , (see Figure 3). The received signals are:
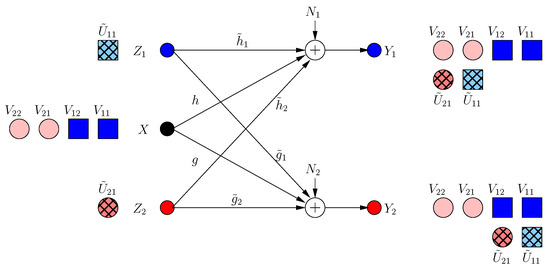
Figure 3.
BCCM frame .
Consequently, the system retains full s.d.o.f. ().
2.2.3. For Frame
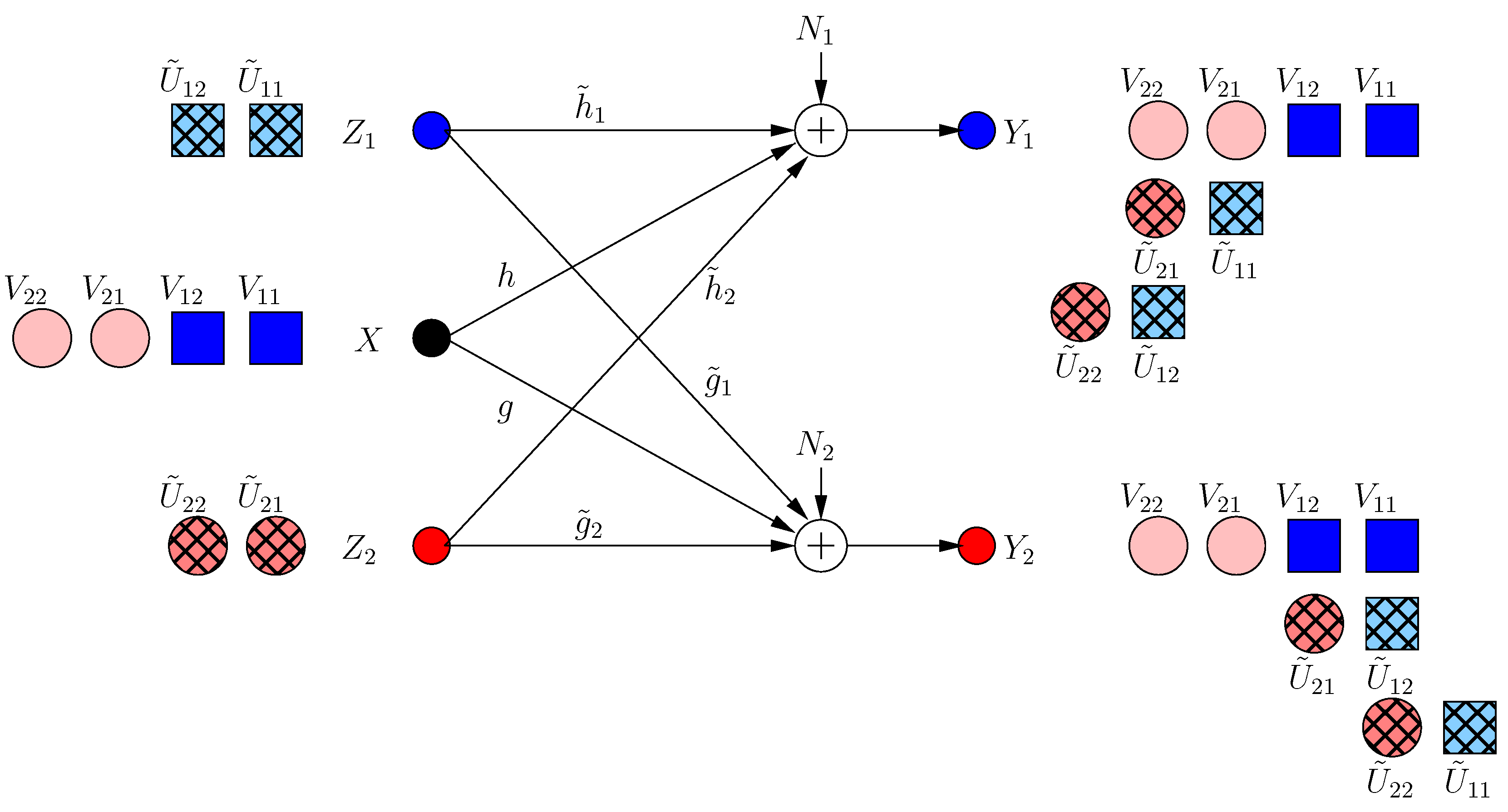
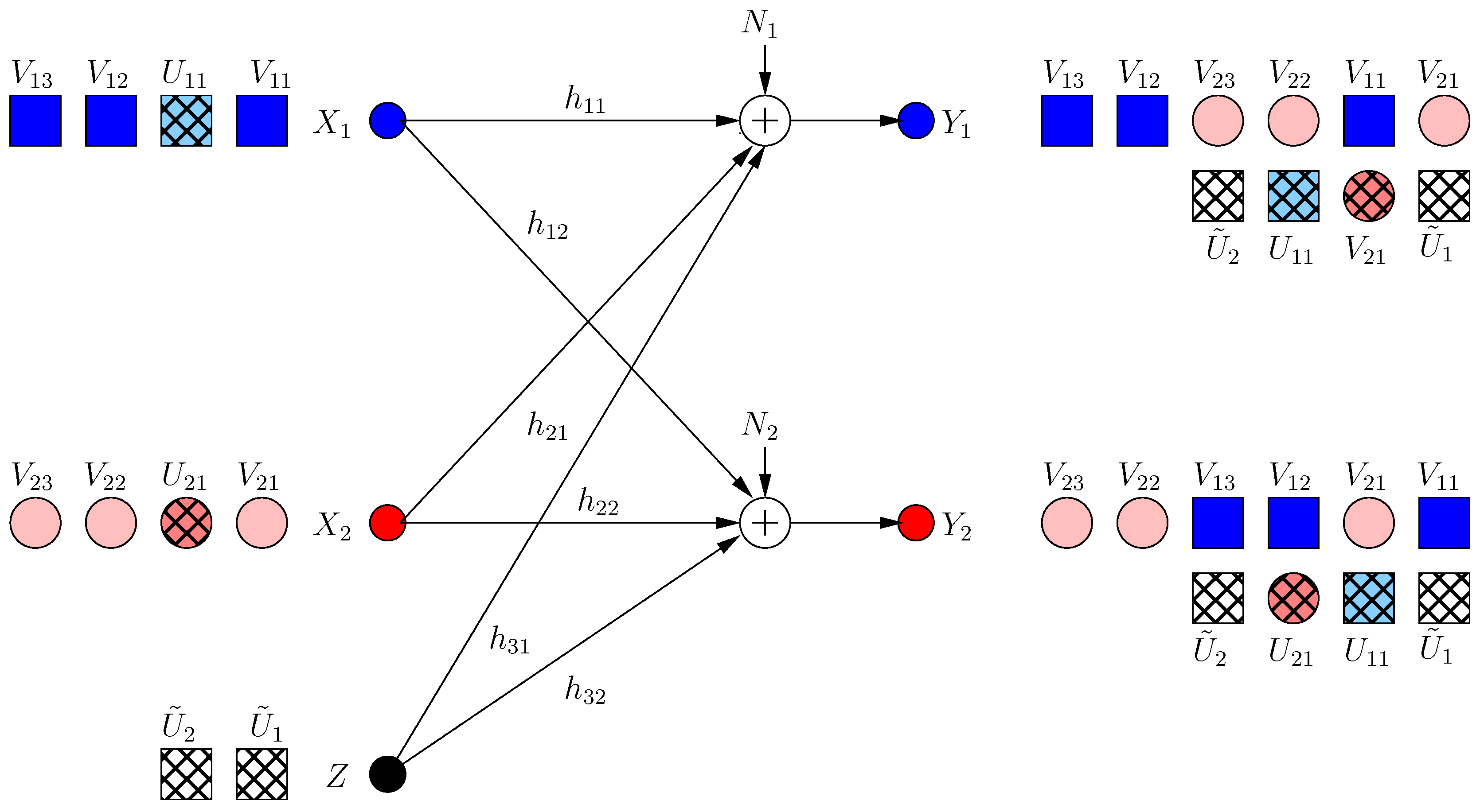
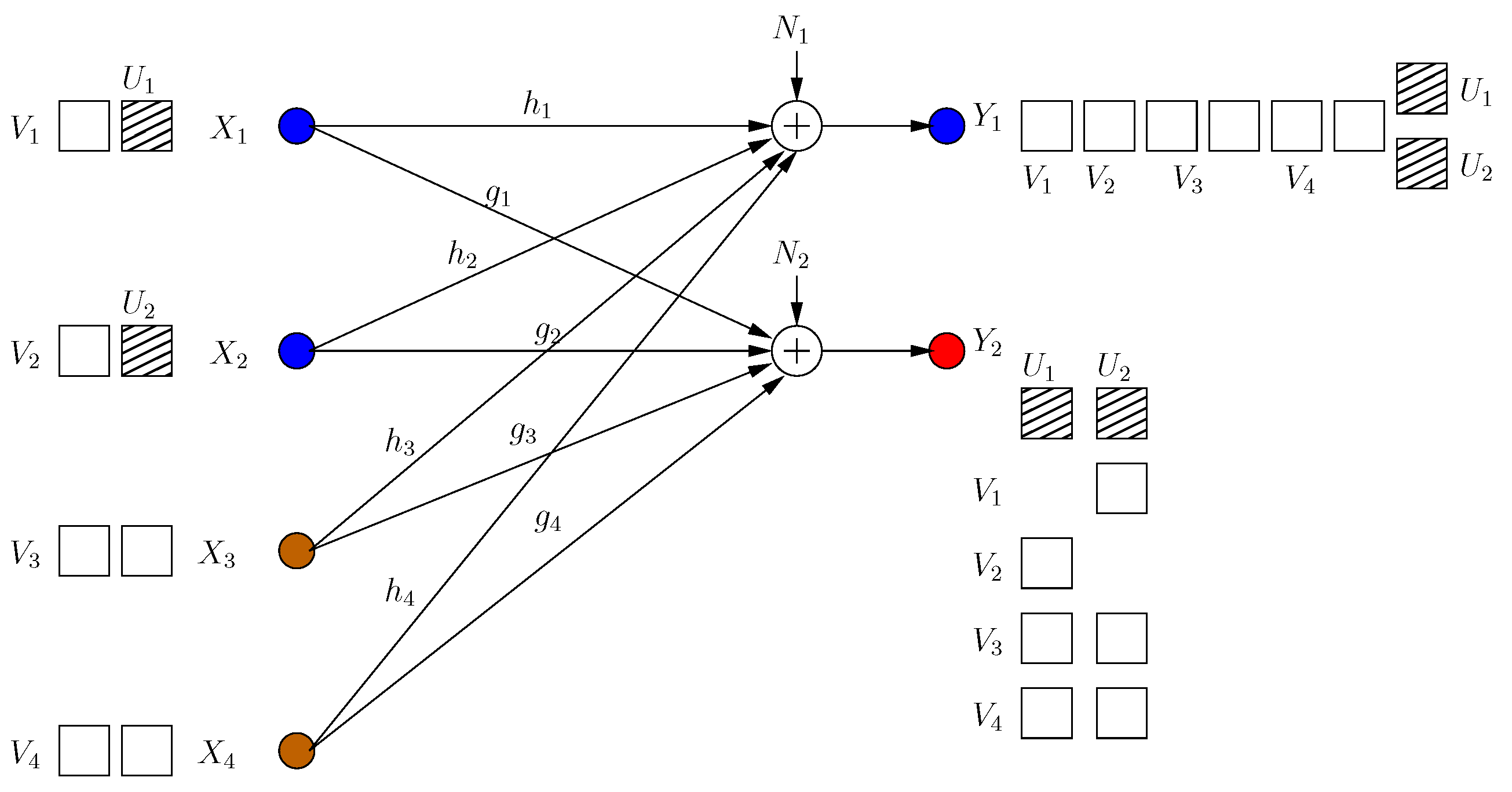
Now, each helper minimizes the s.d.o.f. of the other user by sending a jamming signal. However, due to the strong constraint , no helper jams the other receiver directly, as this would create a new jamming dimension at the side of its own receiver, decreasing its own s.d.o.f. Instead, it transmits a jamming signal which aligns with the already jammed dimension at its own receiver as:
Consequently, the received signals are:
Since the dimension is already jammed, the first helper does not create a new irrational dimension. Hence, it does not hurt its own receiver. However, it creates a new jamming dimension at the second receiver, which decreases the resultant s.d.o.f. From the symmetry, the second helper applies the same strategy, and hence, the resulting s.d.o.f. is as in Figure 4. Note that neither of the helpers can hold back its original jamming signal (i.e., each helper should append its previous signaling with new jamming signals), because if not, its previous message-carrying signals are compromised.
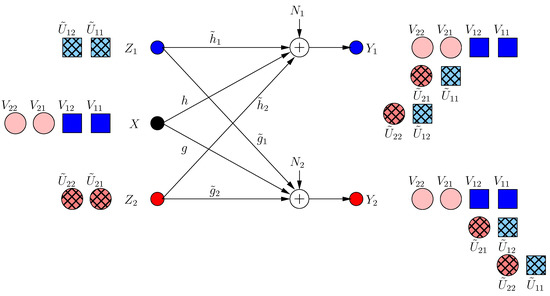
Figure 4.
BCCM frame .
2.2.4. For General kth Frame
If k is odd, the helpers produce one extra jamming component aligned with the last generated jamming signal of the other helper. If k is even, the transmitter makes use of this jamming signal and provides two extra secure signals, achieving the maximum possible s.d.o.f. (, k is even).
2.3. Calculation of the Secure Degrees of Freedom
To calculate the s.d.o.f., we need the following lemma.
Lemma 1.
If every message-carrying signal is protected by a cooperative jamming signal, then the s.d.o.f. is given by:
where is the number of irrational dimensions needed to receive the message-carrying signal of user i at the kth frame and is the total number of irrational dimensions.
Proof.
From [5], the following rate expression is achievable for the BCCM:
Let denote the total number of irrational dimensions used in the kth frame at receiver 1, and denote the number of dimensions used to receive at receiver 1 (without loss of generality, due to symmetry). Then, by choosing and , the average power constraint is satisfied for all nodes, and the probability of error is upper bounded using the Khintchine–Groshev theorem of Diophantine approximation in number theory as in [39] as:
where is constant that does not depend on P. Hence, the probability of error converges to zero as . Then, using Fano’s inequality and the data processing inequality of , we lower bound as follows:
Since we designed the coding scheme at each frame so that is completely hidden for some , we can upper bound the second term as:
where is a diagonal matrix which corresponds to the irrational-dimension gains. The last step follows from carefully designing the jamming vector , so that it aligns with each component of . By taking limit as , we have . □
Now, we are ready to formally calculate the resulting s.d.o.f. from the recursive real interference alignment in the following theorem.
Theorem 1.
For BCCM with combating helpers under the constraint of not decreasing the s.d.o.f. of their own receivers due to helper actions, the s.d.o.f. of each user evolves as:
i.e., the combating behavior is asymptotically neutralized.
Proof.
Using Lemma 1, we have . We complete the proof by calculating the dimensions , . We prove this by induction on k. For the base step , we have and which conforms with (29). For , we have and , and hence, .
For the induction step, assume that k is odd and . Then, in the th frame, the transmitter can always add two extra message-carrying signals to have . Thus, and . This is because the transmitter uses the extra irrational dimension produced by jamming in odd frames in its favor, hence adding one extra dimension corresponding to the new message-carrying signal. This results in the following simultaneous equations:
Solving these two equations gives and . Then, and . In the next frame transmission, each helper produces an extra jamming component aligned with a already jammed dimension. This increases by one at the other receiver without changing . Consequently, , which converges to . □
3. ICCM with Selfish Users
3.1. System Model and Assumptions
In ICCM, each transmitter has a message picked from the message set uniformly with rate for . Message should be received reliably by the ith receiver, while being kept secure from the jth receiver, . The system has an external helper with channel input Z. Inputs satisfy power constraints and . The ICCM model depicted in Figure 5 is given by:
where is the received signal at the ith receiver in the kth transmission frame, and is the channel gain from transmitter (transmitter 3 is the helper) to receiver .
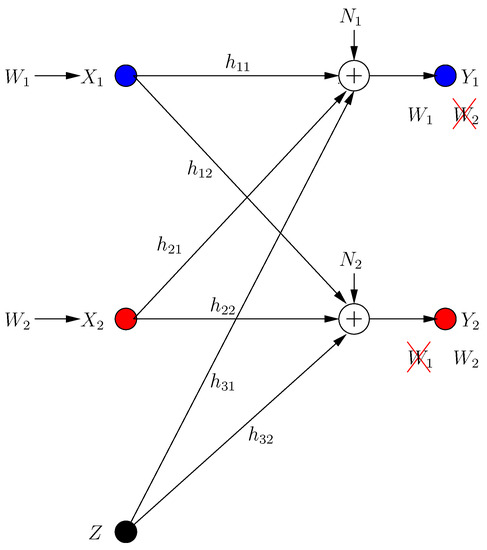
Figure 5.
Interference channel with confidential messages (ICCM) with selfish users.
The users are selfish and malicious. User i maximizes the individual s.d.o.f. at receiver , while maximally hurting the second user. Formally, the ith user’s role is:
where . The role of the users here is less stringent than in the BCCM model, since in the ICCM model, we allow the users to hurt their own receivers if they hurt the other receiver more. On the other hand, the system helper does not take the side of any of the users and maximizes the sum s.d.o.f. of the system:
3.2. Achievable Scheme: Recursive Real Interference Alignment as Extensive Form Game
Similar to the BCCM, we propose using recursive interference alignment using the PAM constellation .
3.2.1. For Frame
All nodes perform the optimal selfless strategy as in [13]. The transmitted signals are:
The received signals at both receivers are (as in Figure 6):
which implies that the achievable s.d.o.f. .
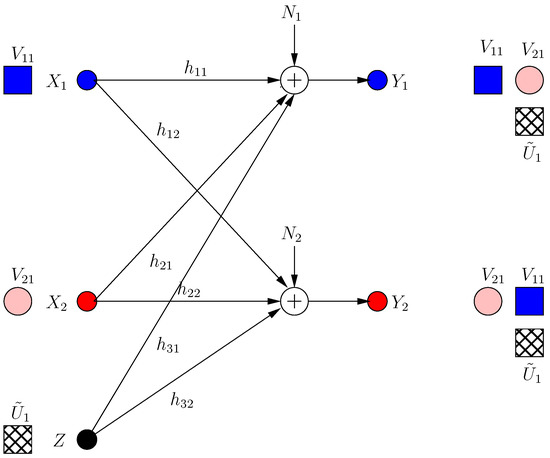
Figure 6.
ICCM frame . Pink circle and blue square denote user signals, and the hatched squares denote jamming signals.
3.2.2. For Frame
User i maximizes assuming that user j keeps its strategy as in frame 0. Each user prefers to jam the other user directly, even if it results in partial decrease of its own s.d.o.f. (by creating an extra dimension at its receiver), since in this case, it can drive the s.d.o.f. of the other user to zero and maximize the s.d.o.f. difference. Thus:
Hence, the received signals in this case are:
which implies that all secure signals are jammed and communication is driven to zero s.d.o.f. as in Figure 7.
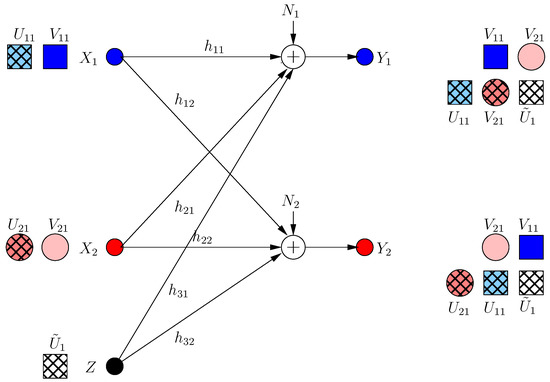
Figure 7.
ICCM frame .
3.2.3. For Frame
Both users know that their communication links are jammed during frame . Therefore, the problem of maximizing the s.d.o.f. difference reduces to maximizing s.d.o.f. of each individual user, since the s.d.o.f. of the other user is zero. Each user benefits from the extra jamming dimension created by the other user to protect extra message-carrying component. Moreover, the helper produces an extra jamming component in a new irrational dimension, which allows each user to produce extra secure signal. Thus:
where is an irrational number independent from all channel gains. Hence, the received signals are:
Consequently, as shown in Figure 8.
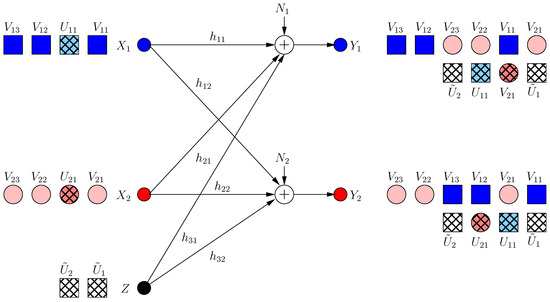
Figure 8.
ICCM frame .
3.2.4. For General kth Frame
The s.d.o.f. differs based on whether k is odd/even. If k is odd, each user chooses to jam all dimensions of the other user’s secure signals. This choice leads to for all odd frames. If k is even, each user takes advantage of the generated jamming by the other user plus the extra jamming signal from the system helper to protect more signals.
3.3. Calculation of the Secure Degrees of Freedom
Theorem 2.
For the ICCM with selfish users in the presence of a system helper, assuming that users maximize the s.d.o.f. difference for every transmission frame, the s.d.o.f. evolves as:
i.e., selfishness eventually precludes secure communication.
Proof.
From [5], the rates given in (19) are achievable for the ICCM. Then, from Lemma 1, we have . Next, we count when k is even. This follows by induction: For , the number of secure dimensions is 1. Now, assume that the relation holds for any even . Then, . Then, since user i jams all secure dimensions of user j in frame , it creates new dimensions. These dimensions are used by user i in frame k to protect new secure signals. The helper produces an extra jamming component, allowing protection of one extra signal. Then, .
We use this result in proving s.d.o.f. by induction: For , and , which leads to . For , and , which leads to . Now, assume that k is even and expression (47) is true, then, . Then, from the above, we have . Hence, . The total dimensions at any receiver is increased over the frame by , since the increase is caused by the new secure dimensions for the two users, which are symmetric. Therefore, the s.d.o.f. for even k is:
If k is odd, users make s.d.o.f. zero, completing the proof. □
Remark 1.
Although the previous channel models are different, they have critical similarities: In both models, there is a central node, transmitter in BCCM, and helper in ICCM, which altruistically want to maximize the sum s.d.o.f.; however, the transmitter in BCCM can send useful signals, but the helper ICCM can only jam. In both models, there are two adversarial/selfish transmitters, helpers in BCCM, and users in ICCM; however, helpers in BCCM can only jam, but users in ICCM can send useful signals and/or jam. We observe that this difference in roles drives systems to opposite end results of full s.d.o.f. in BCCM and zero s.d.o.f. in ICCM.
4. Multiple Access Wiretap Channel with Deviating Users
4.1. System Model and Assumptions
The K-user Gaussian MAC-WTC is given by (see Figure 9):
where are the channel outputs at the legitimate receiver and the eavesdropper, respectively, and are the channel gains from user i to the receiver and the eavesdropper, respectively. User i has a message picked uniformly from the message set , with a rate , and sends it in n channel uses using reliably and securely, i.e.,
where , and are the estimates of the messages at the legitimate receiver. The transmitters are subject to power constraints . The sum s.d.o.f. is given by .
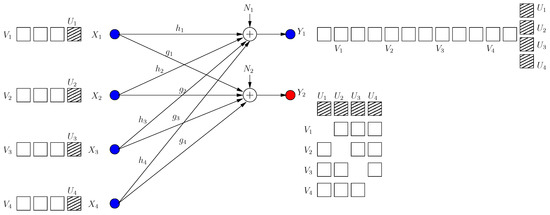
Figure 9.
Optimal achievable scheme for a user multiple access wiretap channel (MAC-WTC).
In the second part of the section, we consider a severe form of deviation where one user transmits intentional jamming signals. To distinguish that user and its jamming signal, we denote its channel input as Z, which is also subject to the power constraint , and we designate it as the Kth user without loss of generality, see Figure 13. The malicious user and the remaining users respond to each other in multiple coding frames. The channel inputs/outputs for this model in frame k are:
where are the channel gains from the malicious user to the legitimate receiver and the eavesdropper, respectively.
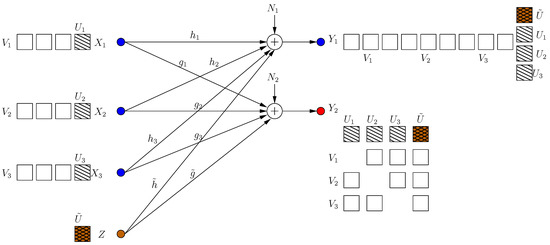
Figure 13.
A malicious jamming user: users’ response.
4.2. S.d.o.f. When Remaining Users Do Not Respond
Consider that M users have deviated from the optimum strategy in [13] (see Figure 9) by not sending cooperative jamming signals and that the remaining users have kept their originally optimum strategies, i.e., have not responded to the deviating users (see Figure 10). That is, the user signals are [13]:
where are picked uniformly from PAM constellation set [13]. The constants are chosen as [13]:
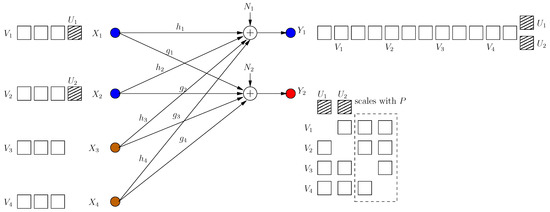
Figure 10.
The remaining users keep their originally optimum schemes.
Let . From [13,15], the following secure rates are achievable:
For the first term : We note that the components of vector are received in different rational dimensions, and hence, we have separable constellation points, while the cooperative jamming signal components are aligned in the same rational dimension, i.e., constellation points. From data processing and Fano’s inequalities:
For the second term : We note that we have dimensions, in which message-carrying signals are aligned with cooperative jamming signals, while M dimensions lack cooperative jamming signals, i.e., we have constellation points. Hence:
Substituting (62) and (67) into (59), and taking the limit as , the achievable sum s.d.o.f. is:
That is, the sum s.d.o.f. decreases by from the optimal in [13]. This affects all users, including the deviating users; hence, they do not benefit from their deviation.
4.3. S.d.o.f. When Remaining Users Respond
In this section, we consider two achievable schemes resulting from two different responses of the remaining users.
4.3.1. Reducing the Secure Rate for Zero Leakage Rate
In this achievable scheme, all users decrease their secure rates, i.e., decrease the number of message-carrying signal components to ensure that all of them are aligned with cooperative jamming signals. Specifically, the first users send message-carrying signals and 1 cooperative jamming signal, while the rest of the users, i.e., the deviating users, send message-carrying signals and no cooperative jamming signals, see Figure 11. Note that the deviating users are motivated to decrease their message-carrying signals from to , as otherwise, some of their message-carrying signals would not be protected. The transmitted signals are:
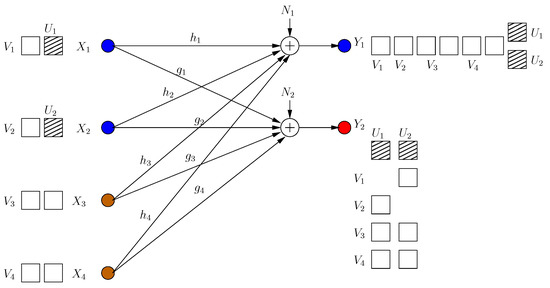
Figure 11.
All users reduce rates to have zero leakage secure degrees of freedom (s.d.o.f.)
Let . We evaluate the secrecy rates using (59), after choosing:
The components of are received in different dimensions, and hence, we have separable constellation points, while the cooperative jamming signals are aligned in the same dimension, i.e., constellation points. Thus:
Since all message-carrying signals are jammed by cooperative jamming signals, we have dimensions with overlapping constellation points. Thus:
Substituting (75) and (79) into (59), and taking the limit as , the achievable sum s.d.o.f. is:
The resultant sum s.d.o.f. is less than the optimal in [13]. However, interestingly, the individual s.d.o.f. of each deviating user is , which is larger than its s.d.o.f. without deviation , so long as , i.e., if at least one user sticks to the optimal strategy in [13].
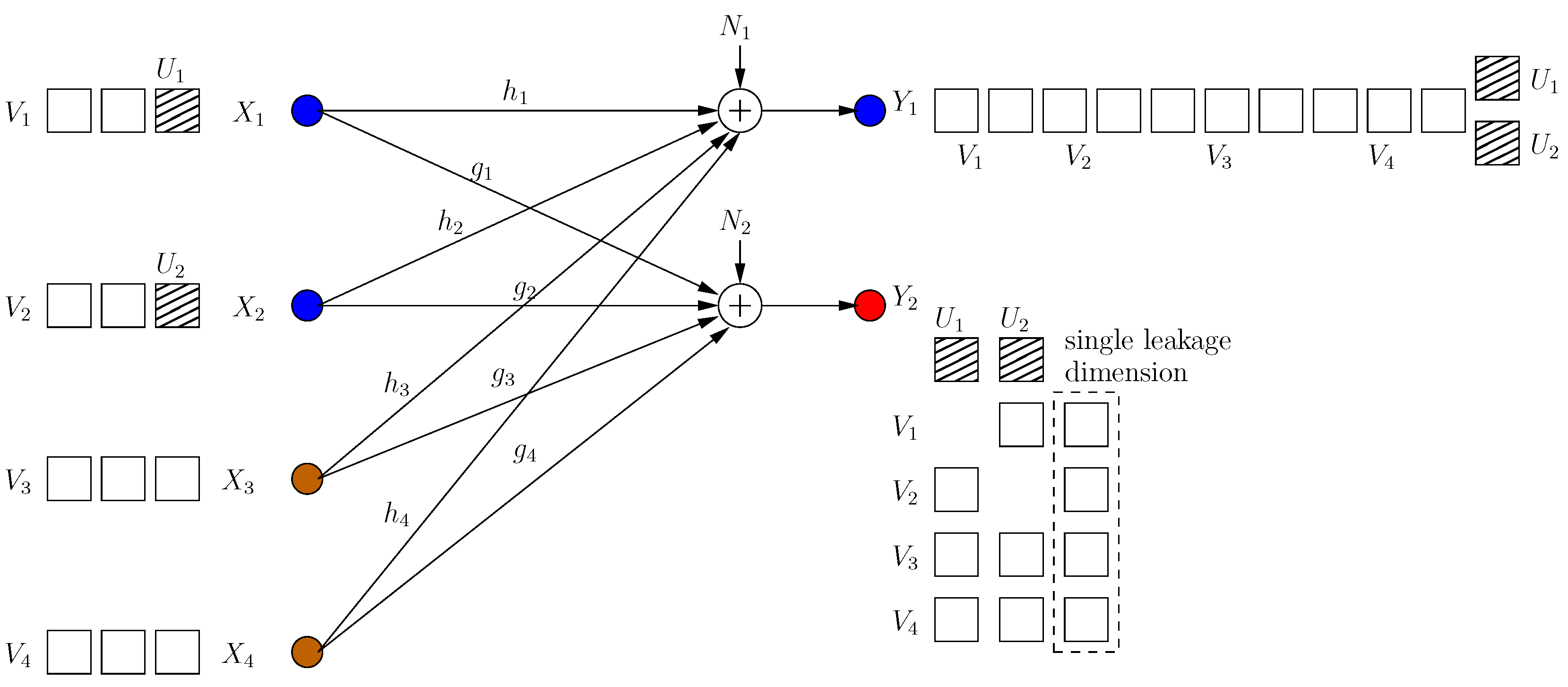
4.3.2. Reducing the Leakage to a Single Dimension
In this achievable scheme, we allow one rational dimension to be leaked. This dimension is not secured by a cooperative jamming signal. This results in the ability of injecting an extra message-carrying signal component for each user. All these extra signals are aligned in the same rational dimension at the eavesdropper. The transmitted signals are (see Figure 12):
where is rationally independent from all channel gains. The received signals are shown in Figure 12. Through similar steps, we have the following s.d.o.f. for this scheme:
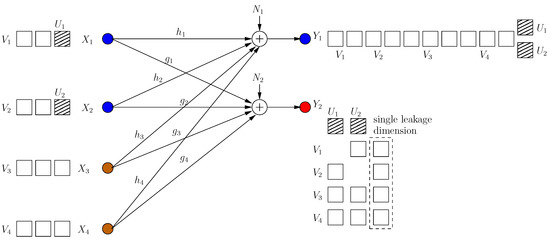
Figure 12.
All users reduce the leakage dimension to 1.
4.4. Malicious Deviation: Intentional Jamming
In this section, we consider a more severe form of deviation, where a user (say the Kth user) sends intentional jamming signals. The deviating (malicious) user is restricted to using structured signals. In this section, we show that, when the malicious user acts, it can drive the sum s.d.o.f. to zero. However, when the remaining users respond, the sum s.d.o.f. is raised to , which is the sum s.d.o.f. of a user MAC-WTC with an external altruistic helper.
4.4.1. When the Jammer Responds to the Users
In any encoding frame, each user sends its message-carrying signals on N rationally independent dimensions as:
Then, the jammer designs structured jamming signals as a response to users’ signals as:
Consequently, the received signal at the legitimate receiver is:
Hence, each message-carrying signal is aligned with a jamming signal. Let to be a vectorization of all secure signal components. Then, the secure rate is upper bounded as:
Hence, , i.e., whenever the jammer knows the signaling scheme of the users, it nulls the communication by jamming.
4.4.2. When the Users Respond to the Jammer
Since structured jamming signaling suffices to jam the system, the jammer sends structured signals in N dimensions:
Users make use of the generated jamming signals to hide extra secure signals from the eavesdropper. Users send:
where are the message-carrying signals which are protected by cooperative jamming signals generated by other users, and the jamming signals generated by the malicious user, respectively. Then, the received signal at receiver 1 is:
i.e., users’ jamming signals use the same dimensions as the external jammer to inject extra cooperative jamming signals. The received signal at the eavesdropper is:
i.e., all message-carrying signals are protected from the eavesdropper, as in Figure 13, with , .
We note that the received signals at receiver consist of constellation points in dimensions. Each user is transmitting using PAM constellation . By choosing and , we have:
Further, since every message-carrying signal is protected by a cooperative jamming signal, . Thus, the achievable sum s.d.o.f. with one malicious jammer when users respond is . Finally, in the Appendix A, we determine the sum s.d.o.f. of a K-user MAC-WTC with M external altruistic helpers, as a result on its own. We note that this is in fact equal to the sum s.d.o.f. of a user MAC-WTC with one external helper, concluding that the users’ action to the jammer is optimal, as they achieve the s.d.o.f. of the case of an altruistic helper with a malicious jammer.
5. Conclusions
We introduced three new channel models, namely, BCCM with combating helpers, ICCM with selfish users, and MAC-WTC with deviating users. These new models aimed at studying the effects of selfishness and malicious behavior on the secure rate in networks. We investigated the achievable s.d.o.f. in these models. The presented schemes are only achievable; new role-based converse arguments are needed.
For the BCCM with combating helpers, we formulated the problem as an extensive-form game. We assumed that each helper wants to minimize the s.d.o.f. of the other receiver without sacrificing the s.d.o.f. of its receiver and analyzed schemes that employ recursive real interference alignment. In this case, we showed that the malicious behaviors of the combating helpers are neutralized and the s.d.o.f. of both users converge to , as in the case of altruistic helpers.
For the ICCM with selfish users, we changed the objective function of the users to maximizing the difference of the s.d.o.f. between the two users. By similar analysis to BCCM, we showed that the selfishness precludes any secure communication, and the s.d.o.f. of two users converge to zero.
Finally, for the MAC-WTC with deviating users, we considered two types of deviation: First, in the case when some of the users stop transmitting cooperative jamming signals as required by the optimal scheme, we evaluated the corresponding s.d.o.f. and proposed counterstrategies to respond to the deviation. Second, we investigated an extreme form of deviation, where a user sends intentional jamming signals. We showed that although a deviating user can drive the sum s.d.o.f. to zero, the jamming signals can be exploited as cooperative jamming signals against the eavesdropper to achieve an optimum s.d.o.f.
Author Contributions
Conceptualization, K.B. and S.U.; Formal analysis, K.B. and S.U.; Investigation, K.B. and S.U.; Methodology, K.B. and S.U.; Validation, K.B. and S.U.; Visualization, K.B. and S.U.; Writing–original draft, K.B. and S.U.; Writing–review and editing, K.B. and S.U.
Funding
This work was supported by NSF Grants CNS 13-14733, CCF 14-22111, CCF 14-22129, and CNS 15-26608, and was presented in part at ISIT conference, Barcelona, Spain, July 2016.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. K-User MAC-WTC with M External Helpers
In this Appendix, we present the exact s.d.o.f. for a MAC-WTC with K users in the presence of M external helpers. In the context of user-misbehavior, the s.d.o.f. of this model serves as an upper bound for the MAC-WTC when the users respond to the intentional jamming when the number of users is and the number of helpers is 1, i.e., we upper bound the s.d.o.f. in this case by replacing the jammer by an altruistic helper.
Theorem A1.
The s.d.o.f. of the K-user Gaussian MAC-WTC with M-external helpers is given by .
Proof.
For the achievability, each user sends message-carrying signals and one cooperative jamming signal to secure the other users. Each helper sends one cooperative jamming signal. The cooperative jamming signals are aligned in the same rational dimension at the receiver.
For the converse, we rely on the techniques in [13]. The received signals at legitimate and eavesdropper receivers of the K-user Gaussian MAC with M external helpers are given by:
where are the channel gains from the ith user to the legitimate receiver and the eavesdropper, respectively, and are channel gains from the jth helper to the legitimate receiver and the eavesdropper, respectively. are input signals from the ith user and the jth helper, respectively. We denote all n-lettered signals by bold vector notation, e.g., let be expressed as .
First, we have the following upper bound which represents the secrecy penalty due to the secrecy constraint on the eavesdropper:
where corresponds to messages 1 through K, and similarly, represent input signals 1 through K from the users and input signals 1 through M from the helpers, respectively. Inequality (A5) follows from applying the secrecy constraint, (A6) follows from Fano’s inequality due to reliability requirements, and (A10) follows from conditioning over helpers’ input signals. We define Gaussian-perturbed input signals for the users and the helpers to not deal with mixed probability measures as , where is i.i.d. Gaussian noise with variance and similarly, for . We introduce these channel inputs in our bound as:
where (A16) follows from the fact that are reconstructable up to finite variance Gaussian noise given and applying the independence upper bound for the first term. The differential entropy of the received observations at the eavesdropper can be lower bounded as:
for some . Consequently, we can write (A16) as the following upper bound which represents the secrecy penalty due to the secrecy constraint imposed on
Next, we have the role of the external helper(s), i.e., upper bounding the differential entropy of the external helpers to ensure decodability of all messages at the legitimate receiver. The sum rate is upper bounded as:
where (A30) follows from Fano’s inequality and (A31) follows from the data processing inequality. Therefore, we can upper bound the differential entropy of the jth external helper as:
The above argument holds for every external helper, i.e., . By adding the corresponding upper bounds of the M helpers, we have the following role of the external helpers upper bound:
Next, by considering the rates of all users except one for the users, we have the role of the internal helper(s). Since each user affects the decodability of other users, by upper bounding the message entropy of all users except one, we can obtain an upper bound on the differential entropy of the signaling scheme employed by each user. Let be all messages from all users except user l:
Hence, we have the following upper bound on the differential entropy of each user:
Applying the above upper bound for the users starting from user 2 to user K, we have the following role of the users upper bound:
Now, we combine all these bounds together. From the upper bounds (A28) and (A36), we substitute in (A20) to have:
We rearrange and simplify (A37) as:
Noting that (A20) still holds for penalizing any of the users’ rate, then by changing role of users and adding the K bounds, we have:
where we used the fact that Gaussian maximizes differential entropy under an average power constraint. By normalizing by and taking limits as , we have the following upper bound on the sum s.d.o.f. for the -user MAC with M external helpers as:
concluding the proof of the theorem. □
Note that this result is related to the s.d.o.f. region result in [17] for the user MAC-WTC, when we focus on the hyperplane corresponding to zero s.d.o.f. for M of the users; these M users essentially serve as helpers.
References
- Liang, Y.; Poor, H.V.; Shamai, S. Information theoretic security. Found. Trends Commun. Inf. Theory 2009, 5, 355–580. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Labs Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Csiszar, I.; Korner, J. Broadcast channels with confidential messages. IEEE Trans. Inf. Theory 1978, 24, 339–348. [Google Scholar] [CrossRef]
- Tekin, E.; Yener, A. The Gaussian Multiple Access Wire-Tap Channel. IEEE Trans. Inf. Theory 2008, 54, 5747–5755. [Google Scholar] [CrossRef]
- Liu, R.; Maric, I.; Spasojevic, P.; Yates, R.D. Discrete Memoryless Interference and Broadcast Channels With Confidential Messages: Secrecy Rate Regions. IEEE Trans. Inf. Theory 2008, 54, 2493–2507. [Google Scholar] [CrossRef]
- Chong, H.F.; Liang, Y.C. Secrecy capacity region of a class of two-user Gaussian MIMO BC with degraded message sets. In Proceedings of the IEEE International Symposium on Information Theory, Istanbul, Turkey, 7–12 July 2013. [Google Scholar]
- Liu, R.; Liu, T.; Poor, H.V.; Shamai, S. Multiple-Input Multiple-Output Gaussian Broadcast Channels With Confidential Messages. IEEE Trans. Inf. Theory 2010, 56, 4215–4227. [Google Scholar]
- Khina, A.; Kochman, Y.; Khisti, A. The confidential MIMO broadcast capacity: A simple derivation. In Proceedings of the IEEE International Symposium on Information Theory, Hong Kong, China, 14–19 June 2015. [Google Scholar]
- Goldfeld, Z.; Permuter, H. MIMO Gaussian Broadcast Channels with Common, Private and Confidential Messages. arXiv 2016, arXiv:1608.06057. [Google Scholar]
- Khisti, A.; Tchamkerten, A.; Wornell, G.W. Secure Broadcasting Over Fading Channels. IEEE Trans. Inf. Theory 2008, 54, 2453–2469. [Google Scholar] [CrossRef]
- Ekrem, E.; Ulukus, S. The Secrecy Capacity Region of the Gaussian MIMO Multi-Receiver Wiretap Channel. IEEE Trans. Inf. Theory 2011, 57, 2083–2114. [Google Scholar] [CrossRef]
- Lai, L.; Gamal, H.E. The Relay-Eavesdropper Channel: Cooperation for Secrecy. IEEE Trans. Inf. Theory 2008, 54, 4005–4019. [Google Scholar] [CrossRef]
- Xie, J.; Ulukus, S. Secure Degrees of Freedom of One-Hop Wireless Networks. IEEE Trans. Inf. Theory 2014, 60, 3359–3378. [Google Scholar] [CrossRef]
- Nafea, M.; Yener, A. Secure Degrees of Freedom for the MIMO Wire-Tap Channel With a Multi-Antenna Cooperative Jammer. IEEE Trans. Inf. Theory 2017, 63, 7420–7441. [Google Scholar] [CrossRef]
- Bagherikaram, G.; Motahari, A.S.; Khandani, A.K. On the secure DoF of the single-antenna MAC. In Proceedings of the IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010. [Google Scholar]
- He, X.; Khisti, A.; Yener, A. MIMO Multiple Access Channel With an Arbitrarily Varying Eavesdropper: Secrecy Degrees of Freedom. IEEE Trans. Inf. Theory 2013, 59, 4733–4745. [Google Scholar]
- Xie, J.; Ulukus, S. Secure Degrees of Freedom Regions of Multiple Access and Interference Channels: The Polytope Structure. IEEE Trans. Inf. Theory 2016, 62, 2044–2069. [Google Scholar] [CrossRef]
- Koyluoglu, O.O.; Gamal, H.E.; Lai, L.; Poor, H.V. On the secure degrees of freedom in the K-user Gaussian interference channel. In Proceedings of the IEEE International Symposium on Information Theory, Toronto, ON, Canada, 6–11 July 2008. [Google Scholar]
- He, X.; Yener, A. K-user interference channels: Achievable secrecy rate and degrees of freedom. In Proceedings of the IEEE Information Theory Workshop on Networking and Information Theory, Volos, Greece, 10–12 June 2009. [Google Scholar]
- He, X.; Yener, A. Secure Degrees of Freedom for Gaussian Channels with Interference: Structured Codes Outperform Gaussian Signaling. In Proceedings of the GLOBECOM IEEE Global Telecommunications Conference, Honolulu, HI, USA, 30 November–4 December 2009. [Google Scholar]
- Xie, J.; Ulukus, S. Secure Degrees of Freedom of K-User Gaussian Interference Channels: A Unified View. IEEE Trans. Inf. Theory 2015, 61, 2647–2661. [Google Scholar] [CrossRef]
- Banawan, K.; Ulukus, S. Secure Degrees of Freedom Region of Static and Time-Varying Gaussian MIMO Interference Channel. IEEE Trans. Inf. Theory 2019, 65, 444–461. [Google Scholar] [CrossRef]
- Gou, T.; Jafar, S.A. On the secure degrees of freedom of wireless X networks. In Proceedings of the 46th Annual Allerton Conference on Communication, Control, and Computing, Urbana-Champaign, IL, USA, 23–26 September 2008. [Google Scholar]
- Wang, Z.; Xiao, M.; Skoglund, M.; Poor, H.V. Secure Degrees of Freedom of Wireless X Networks Using Artificial Noise Alignment. IEEE Trans. Commun. 2015, 63, 2632–2646. [Google Scholar] [CrossRef]
- Kim, T.T.; Poor, H.V. On the Secure Degrees of Freedom of Relaying With Half-Duplex Feedback. IEEE Trans. Inf. Theory 2011, 57, 291–302. [Google Scholar] [CrossRef]
- Khisti, A. Interference Alignment for the Multiantenna Compound Wiretap Channel. IEEE Trans. Inf. Theory 2011, 57, 2976–2993. [Google Scholar] [CrossRef]
- Lee, S.H.; Zhao, W.; Khisti, A. Secure Degrees of Freedom of the Gaussian Diamond-Wiretap Channel. IEEE Trans. Inf. Theory 2017, 63, 496–508. [Google Scholar] [CrossRef]
- Fan, Y.; Liao, X.; Vasilakos, A.V. Physical Layer Security Based on Interference Alignment in K-User MIMO Y Wiretap Channels. IEEE Access 2017, 5, 5747–5759. [Google Scholar] [CrossRef]
- Tandon, R.; Mohajer, S.; Poor, H.V.; Shamai, S. Degrees of Freedom Region of the MIMO Interference Channel With Output Feedback and Delayed CSIT. IEEE Trans. Inf. Theory 2013, 59, 1444–1457. [Google Scholar] [CrossRef]
- Yang, S.; Kobayashi, M.; Piantanida, P.; Shamai, S. Secrecy Degrees of Freedom of MIMO Broadcast Channels With Delayed CSIT. IEEE Trans. Inf. Theory 2013, 59, 5244–5256. [Google Scholar] [CrossRef]
- Zaidi, A.; Awan, Z.H.; Shamai, S.; Vandendorpe, L. Secure Degrees of Freedom of MIMO X-Channels With Output Feedback and Delayed CSIT. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1760–1774. [Google Scholar] [CrossRef]
- Mukherjee, P.; Xie, J.; Ulukus, S. Secure Degrees of Freedom of One-Hop Wireless Networks With No Eavesdropper CSIT. IEEE Trans. Inf. Theory 2017, 63, 1898–1922. [Google Scholar] [CrossRef]
- Mukherjee, P.; Tandon, R.; Ulukus, S. Secure Degrees of Freedom Region of the Two-User MISO Broadcast Channel With Alternating CSIT. IEEE Trans. Inf. Theory 2017, 63, 3823–3853. [Google Scholar] [CrossRef]
- Moualeu, J.M.; Hamouda, W.; Takawira, F. Intercept Probability Analysis of Wireless Networks in the Presence of Eavesdropping Attack With Co-Channel Interference. IEEE Access 2018, 6, 41490–41503. [Google Scholar] [CrossRef]
- Tekin, E.; Yener, A. The General Gaussian Multiple-Access and Two-Way Wiretap Channels: Achievable Rates and Cooperative Jamming. IEEE Trans. Inf. Theory 2008, 54, 2735–2751. [Google Scholar] [CrossRef]
- Ekrem, E.; Ulukus, S. On the secrecy of multiple access wiretap channel. In Proceedings of the 46th Annual Allerton Conference on Communication, Control, and Computing, Urbana-Champaign, IL, USA, 23–26 September 2008. [Google Scholar]
- Ge, H.; Xu, R.; Berry, R.A. Secure signaling games for Gaussian multiple access wiretap channels. In Proceedings of the IEEE International Symposium on Information Theory, Hong Kong, China, 14–19 June 2015. [Google Scholar]
- Tadelis, S. Game Theory: An Introduction; Princeton University Press: Princeton, NJ, USA, 2013. [Google Scholar]
- Motahari, A.S.; Oveis-Gharan, S.; Maddah-Ali, M.A.; Khandani, A.K. Real Interference Alignment: Exploiting the Potential of Single Antenna Systems. IEEE Trans. Inf. Theory 2014, 60, 4799–4810. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).