Abstract
The problem of multilevel diversity coding with secure regeneration (MDC-SR) is considered, which includes the problems of multilevel diversity coding with regeneration (MDC-R) and secure regenerating code (SRC) as special cases. Two outer bounds are established, showing that separate coding can achieve the minimum-bandwidth-regeneration (MBR) point of the achievable normalized storage-capacity repair-bandwidth trade-off regions for the general MDC-SR problem. The core of the new converse results is an exchange lemma, which can be established using Han’s subset inequality.
1. Introduction
Diversity coding and node repair are two fundamental ingredients of reliable distributed storage systems. While the study of diversity coding has been in the literature for decades [1,2,3,4,5,6], systematic studies of node repair mechanisms were started only recently by Dimakis et al. in their pioneering work [7]. A particular model, which was first introduced in [7] and has since received a significant amount of attention in the literature [8,9,10,11,12,13,14,15,16,17,18,19,20], is the so-called (exact-repair) regenerating code (RC) problem.
More specifically, in an RC problem, a file of size B is to be encoded in a total of n distributed storage nodes, each of capacity . The encoding needs to ensure that the file can be perfectly recovered by having full access to any k out of the total n storage nodes. In addition, when node failures occur and there are only d remaining nodes in the system, it is required that the data originally stored in any failed node can be recovered by downloading data of size from each one of the d remaining nodes. An interesting technical challenge is to characterize the optimal trade-offs between the node capacity and the download bandwidth in satisfying both the file-recovery and node-repair requirements, which was studied in [8,9,10,11,12,13,14,15,16,17,18,19,20]. However, despite intensive research efforts that have yielded many interesting and highly non-trivial partial results including a precise characterization of the minimum-storage-regenerating (MSR) and the minimum-bandwidth-regenerating (MBR) rate points, the optimal trade-offs between the node capacity and the download bandwidth have not been fully understood for the general RC problem.
More recently, two extensions of the RC problem, namely multilevel diversity coding with regeneration (MDC-R) and secure regenerating code (SRC), have also been studied in the literature. The problem of MDC-R was first introduced by Tian and Liu [21]. In an MDC-R problem, a total of d independent files of size , respectively, are to be stored in n distributed storage nodes, each of capacity . The encoding needs to ensure that the file can be perfectly recovered by having full access to any j out of the total n storage nodes for any . In addition, when node failures occur and there are only d remaining nodes in the system, it is required that the data originally stored in any failed node can be recovered by downloading data of size from each one of the d remaining nodes.
Clearly, an RC problem can be viewed as an MDC-R problem with degenerate messages (i.e., for all ). Therefore, from the code construction perspective, it is natural to consider the so-called separate coding scheme, i.e., to construct a code for the MDC-R problem, we can simply use an RC to encode the file for each , and the coded messages for each file remain separate when stored in the storage nodes and during the repair processes. However, despite being a natural scheme, it was shown in [21] that separate coding is in general suboptimal in achieving the optimal trade-offs between the normalized storage-capacity and repair-bandwidth. On the other hand, it has been shown that separate coding can, in fact, achieve both the MSR [21] and the MBR [22] points of the achievable normalized storage-capacity and repair-bandwidth trade-off region for the general MDC-R problem.
The problem of SRC is an extension of the RC problem that further requires security guarantees during the repair processes. More specifically, the SRC problem that we consider is the RC problem [7,8,9,10,11,12,13,14,15,16], with the additional constraint that the file needs to be kept information-theoretically secure against an eavesdropper, which can access the data downloaded to regenerate a total of ℓ different failed nodes under all possible repair groups. Obviously, this is only possible when . Furthermore, when , the secrecy requirement degenerates, and the SRC problem reduces to the RC problem without any repair secrecy requirement.
Under the additional require secrecy requirement (), the optimal trade-offs between the node capacity and repair bandwidth have been studied in [23,24,25,26,27,28,29,30]. In particular, Shah, Rashmi and Kumar [25] showed that a particular trade-off point (referred to as the SRK point as the three first letters of the authors’ names) can be achieved by extending an MBR code based on the product-matrix construction proposed in [8]. Later, it was shown [30] that, for any given pair, there is a lower bound on ℓ, denoted by , such that, when , the SRK point is the only corner point of the trade-off region for the SRC problem. On the other hand, when , it is possible that the trade-off region features multiple corner points, even though a precise characterization of the trade-off region, including both the MSR and the MBR points, remains missing in general.
In this paper, we introduce the problem of multilevel diversity coding with secure regeneration (MDC-SR) (The problem of secure multilevel diversity coding without any node regeneration requirement has been considered in [6,31].), which includes the problems of MDC-R and SRC as two special cases. In this model, multiple files are to be stored distributed in several storage nodes, like what in the Multilevel Diversity Coding problem. The system requires that, if a user can fully access some of the nodes, then the user can recover the corresponding part of the original files. Meanwhile, if any storage node failed, it can be regenerated by downloading messages from other nodes within a certain bandwidth limit. Additionally, if some nodes and repairing messages are leaked to an eavesdropper, the original files can still be information that is theoretically secure. The detailed definition of this model can be found in the next section. Similar to the MDC-R problem, it is natural to consider the separate coding scheme for the MDC-SR problem as well. Our main contribution consisted of three parts. Firstly, we established two nontrivial outer bounds for the MDC-SR problem. The secrecy constraint in the MDC-SR problem makes the outer bounding its trade-off region, not a simple extension of the bounding technic of the MDC-R problem in [22]. Secondly, we addressed a coding scheme with a separate coding structure that can achieve the intersection of the two outer bounds that we established, hence we can show that the optimality of separate coding in terms of achieving the MBR point of the achievable normalized storage-capacity and repair-bandwidth trade-off region extends more generally from the MDC-R problem to the MDC-SR problem. Last but not the least, during the process of establishing the two outer bounds, we proposed a lemma called Exchange Lemma, which we believe can be used widely in other similar or even more generalized problems. We need to mention that our system model and main results can be degenerated to some unknown results. For example, when specialized to the SRC problem, our result shows that the SRK point [25] is, in fact, the MBR point of the achievable normalized storage-capacity and repair-bandwidth trade-off region, regardless of the number of corner points of the trade-off region.
From the technical viewpoint, this is mainly accomplished by establishing two outer bounds (one of them must be “horizontal”, i.e., on the normalized repair-bandwidth only) on the achievable normalized storage-capacity and repair-bandwidth trade-off region, which intersect precisely at the superposition of the SRK points. The core of the new converse results is an exchange lemma, which we establish by exploiting the built-in symmetry of the problem via Han’s subset inequality [32]. The meaning of “exchange” will be clear from the statement of the lemma. The lemma only relies on the functional dependencies for the repair processes and might be useful for solving some other related problems as well.
The rest of the paper is organized as follows. In Section 2, we formally introduce the problem of MDC-SR and the separate coding scheme. The main results of the paper are then presented in Section 3. In Section 4, we introduce the exchange lemma and use it to establish the main results of the paper. Finally, we conclude the paper in Section 5.
Notation and Remarks. Sets and random variables will be written in calligraphic and sans-serif fonts respectively, to differentiate from the real numbers written in normal math fonts. For any two integers , we shall denote the set of consecutive integers by . The use of the brackets will be supressed otherwise.
Though many remarkable previous works are mentioned in this introduction, some of them, in fact, are more related to our work, such as [15,25,29]. We list them for the best convenience of our readers.
2. The MDC-SR Problem
Let be a tuple of positive integers such that . Formally, an code consists of:
- for each , a message-encoding function ;
- for each , a message-decoding function ;
- for each , , and , a repair-encoding function ;
- for each and , a repair-decoding function .
For each , let be a message that is uniformly distributed over . The messages are assumed to be mutually independent. Let be a random key that is uniformly distributed over and independent of the messages . For each , let be the data stored at the ith storage node, and for each , , and , let be the data downloaded from the th storage node in order to regenerate the data originally stored at the ith storage node under the context of repair group . Obviously,
represent the message sizes, storage capacity, and repair bandwidth, respectively.
A normalized message-rate storage-capacity repair-bandwidth tuple is said to be achievable for the MDC-SR problem if an code (i.e., for all ) can be found such that:
- (rate normalization)for any ;
- (message recovery)for any ;
- (node regeneration)for any and ;
- (repair secrecy)for any such that , where is the collection of data that can be downloaded from the other nodes to regenerate node i.
The closure of all achievable tuples is the achievable normalized message-rate storage-capacity repair-bandwidth trade-off region for the MDC-SR problem. For a fixed normalized message-rate tuple , the achievable normalized storage-capacity repair-bandwidth trade-off region is the collection of all normalized storage-capacity repair-bandwidth pairs such that and is denoted by .
Based on the above problem formulation, it should be clear that the MDC-SR problem includes several open problems of recent interest:
- (1)
- the achievable normalized storage-capacity repair-bandwidth trade-off region of the MDC-R problem is simply for any given normalized message-rate tuple ,
- (2)
- the achievable normalized storage-capacity repair-bandwidth trade-off region of the SRC problem is simply ,
- (3)
- the achievable normalized storage-capacity repair-bandwidth trade-off region of the RC problem is simply or, equivalently, .
Given these connections, our problem formulation can be viewed as providing a unified framework to investigate these closely-related problems.
A simple and natural strategy for constructing a code for the MDC-SR problem is to use to an SRC to encode the message separately for each . Since the coded data are kept separate during the encoding, decoding and repair processes, we have
Thus, for the general MDC-SR problem, the separate coding normalized storage-capacity repair-bandwidth trade-off region for a fixed normalized message-rate tuple is given by:
As mentioned previously, when , the repair secrecy requirement (4) degenerates, and the MDC-SR problem reduces to the MDC-R problem. In this case, it was shown in [22] that any achievable normalized message-rate storage-capacity repair-bandwidth tuple must satisfy:
where . When set as equalities, the intersection of (6) and (7) is given by:
For any , the MBR point for the RC problem can be written as [8]
We may thus conclude immediately from (5) (with ) that separate coding can achieve the MBR point for the general MDC-R problem.
Figure 1 shows the optimal trade-off curve between the normalized storage-capacity and repair-bandwidth and the best possible trade-offs that can be achieved by separate coding for the MDC-R problem with [21]. Clearly, for this example, separate coding is strictly suboptimal when . On the other hand, when or , separate coding can, in fact, achieve the optimal trade-offs. In particular, separate encoding can achieve the MSR point and the MBR point . In the same figure, the outer bounds (6) and (7) have also been plotted. As illustrated, they intersect precisely at the MBR point . Notice that, for this example at least, the outer bound (7) is tight only at the MBR point.
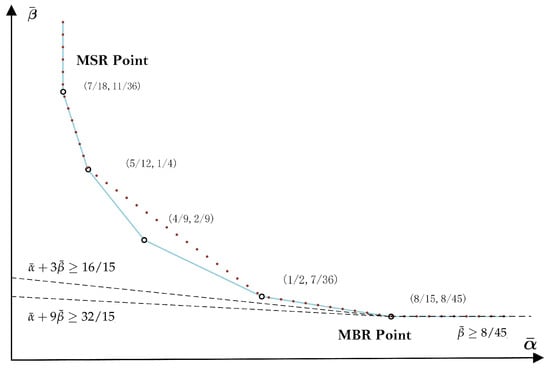
Figure 1.
The optimal trade-off curve between the normalized storage-capacity and repair-bandwidth (the solid line) and the best possible trade-offs that can be achieved by separate coding (dashed line) for the multilevel diversity coding with regeneration (MDC-R) problem with (adapted from [21]). The outer bounds (6), (7) and (14) are evaluated as , , and , respectively. When set as equalities, they intersect precisely at the MBR point .
3. Main Results
Our main result of the paper is to show that the optimality of separate coding in terms of achieving the MBR point of the normalized storage-capacity repair-bandwidth trade-off region extends more generally from the MDC-R problem to the MDC-SR problem. The results are summarized in the following theorem.
Theorem 1.
For the general MDC-SR problem, any achievable normalized message-rate storage-capacity repair-bandwidth tuple must satisfy:
where . When set as equalities, the intersection of (9) and (10) is given by:
For any , the SRK point for the SRC problem can be written as [25]:
We may thus conclude immediately from (5) that separate coding can achieve the MBR point for the general MDC-SR problem.
The following corollary follows immediately from Theorem 1 by setting for all .
Corollary 1.
For the general SRC problem, any achievable normalized storage-capacity repair-bandwidth tuple must satisfy:
While the outer bound (12) is known [23,24,30], the outer bound (13) is new. Figure 2 shows the optimal trade-off curve between the normalized storage-capacity and repair-bandwidth for the SRC problem. Notice that, for this example, the SRK point is, in fact, the MBR point even though the trade-off region has two corner points. In the same figure, the outer bunds (12) and (13) have also been plotted. As illustrated, when set as equalities, they intersect precisely at the MBR/SRK point . Notice that for this example at least, the outer bound (13) is tight only at the MBR/SRK point.
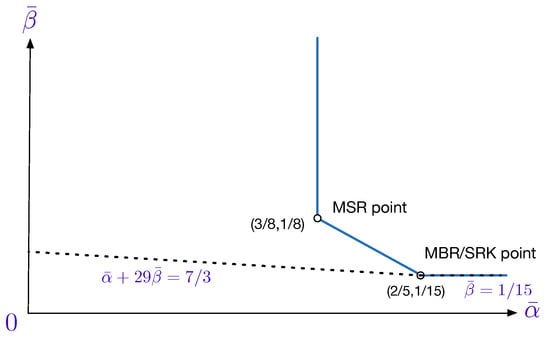
As a final remark, we mention here that when , the outer bound (9) is reduced to (6) for the MDC-R problem by the fact that . However, when , the outer bound (10) is reduced to:
which is weaker than the outer bound (7) by the fact that . Figure 1 shows the outer bound (14) for the MDC-R problem with . As illustrated, (14) is weaker than (7), and both are only tight at the MBR point .
4. Proof of the Main Results
- (1)
- Total number of nodes. To prove the outer bounds (9) and (10), let us first note that these bounds are independent of the total number of storage nodes n in the system. Therefore, in our proof, we only need to consider the cases where —for the cases where , since any subsystem consisting of out of the total n storage nodes must give rise to a MDC-SR problem. Therefore, these outer bounds must apply as well. When , any repair group of size d is uniquely determined by the node j to be repaired, i.e., , and hence can be dropped from the notation without causing any confusion.
- (2)
- (3)
- Key collections of random variables. Focusing on the symmetrical codes, the following collections of random variables play a key role in our proof:These collections of random variables have also been used in [22,30].
An important part of the proof is to understand the relations between the collections of random variables defined above, and to use them to derive the desired converse results. We shall discuss this next.
4.1. Technical Lemmas
Lemma 1.
Proof of Lemma 1.
Fix and . Let us first note that is a function of . As a result, is a function of . It thus follows immediately from the node regeneration requirement (3) that is a function of . Similarly and inductively, it can be shown that is a function of for all . This completes the proof of the lemma. ☐
The above lemma demonstrates the “compactness” of and has a number of direct consequences. For example, for any fixed , it is clear from Lemma 1 that is a function of and hence for any .
The following lemma plays the key role in proving the outer bounds (6) and (7). The proof is rather long and is deferred to the Appendix to enhance the flow of the paper.
Lemma 2 (Exchange lemma).
For any symmetrical code that satisfies the node regeneration requirement (3), we have
for any , , , and .
Corollary 2.
For any symmetrical code that satisfies the node regeneration requirement (3), we have
for any and .
Proof of Corollary 2.
Corollary 3.
For any symmetrical code that satisfies the node regeneration requirement (3), we have
for any and .
4.2. The Proof
Consider a symmetrical regenerating code that satisfies the rate normalization requirement (1), the message recovery requirement (2), the node regeneration requirement (3), and the repair secrecy requirement (4). Let us first prove a few intermediate results. The outer bounds (9) and (10) will then follow immediately.
Proposition 1.
for any . Consequently,
Proof of Proposition 1.
To see (22), consider proof by induction. For the base case with , we have
where follows from the fact that is a function of , which is a function of by Lemma 1; follows from the chain rule for entropy; follows from the fact that ; and follows from the fact that . Assuming that (22) holds for some , we have
where follows from the induction assumption; follows from Corollary 2; follows from the fact that is a function of , which is a function of by Lemma 1; follows from the chain rule for entropy; and follows from the facts that is independent of and that . This completes the induction step and hence the proof of (22).
Proposition 2.
Proof of Proposition 2.
First note that, for any , we have
where follows from the fact that due to the symmetrical code that we consider, and follows from the submodularity of the entropy function. Add (27) over and cancel from both sides. We have
It follows that
where follows from (28); follows from the fact that and that ; and follows from the fact that and that by the union bound on entropy. This completes the proof of the proposition. ☐
Proposition 3.
for any . Consequently,
Proof of Proposition 3.
To see (29), note that, for any , we have
where follows from (22) of Proposition 1; follows from Corollary 3; and follows from the fact that due to the repair secrecy requirement (4). Adding to both sides and using the facts that
and that
complete the proof of (29). Here, and are due to the facts that is a function of , which is a function of both and by Lemma 1.
Note that
Furthermore,
where follows from the fact that is a function of , which is a function of by Lemma 1; follows from the chain rule for entropy; follows from the fact that ; follows from the fact that is a function of and hence a function of ; follows from the fact that due to the symmetrical code that we consider; and follows from the fact that due to the repair secrecy requirement (4).
Proof of Theorem 1.
We are now ready to prove the outer bounds (9) and (10). To prove (9), note that
where follows from the fact that ; follows from the union bound on entropy; and follows from (23) of Proposition 1. Cancelling from both sides of the inequality and normalizing both sides by complete the proof of (9).
To prove (10), note that
where follows from the fact that ; follows from the fact that is a function of ; follows from the fact that due to the submodularity of the entropy function; follows from Proposition 2; follows from the fact that due to the symmetrical code that we consider; follows from (23) of Proposition 1 and (30) of Proposition 3; and follows from the fact that . Cancelling from both sides of the inequality and normalizing both sides by complete the proof of (10). ☐
5. Conclusions
This paper considered the problem of MDC-SR, which includes the problems of MDC-R and SRC as special cases. Two outer bounds were established, showing that separate coding can achieve the MBR point of the achievable normalized storage-capacity repair-bandwidth trade-off regions for the general MDC-SR problem. When specialized to the SRC problem, it was shown that the SRK point [25] is the MBR point of the achievable normalized storage-capacity repair-bandwidth trade-off regions for the general SRC problem. The core of the new converse results is an exchange lemma, which we established by using Han’s subset inequality [32]. The exchange lemma only relies on the functional dependencies for the repair processes and might be useful for solving some other related problems as well.
Note that separate encoding can also achieve the MSR point of the achievable normalized storage-capacity repair-bandwidth trade-off regions for the general MDC-R problem [22]. We suspect that this also generalizes to the MDC-SR problem. To prove such this result, however, we shall need new converse results as well as new code constructions for the general SRC problem, both of which are currently under our investigations.
Author Contributions
T.L. and C.T. proposed the idea of this paper, S.S. was responsible for the technical proof of the paper and all for authors worked on writing, revising and editing this manuscript.
Funding
The work of T.L. was supported in part by the National Science Foundation under Grants CCF-17-19017; the work of C.T. was supported in part by CCF-18-32309; and the work of C.S. was supported in part by the National Natural Science Foundation of China under Grant 61631017.
Acknowledgments
S.S. is grateful to Fangwei Ye for giving opinions to our early version on Arxiv.
Conflicts of Interest
The authors declare no conflict of interest. The founding sponsors had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, and in the decision to publish the results.
Appendix A. Proof of the Exchange Lemma
Proof of the Exchange Lemma.
This lemma is proved in an iterative way. The to be “exchanged” random variable sets are partitioned in a designed way, and every time after a small partition of the set is exchanged, we can establish an inequality. In our proof, we use not only the submodularity of the entropy function but also the properties of regeneration code, namely Lemma 1 as well.
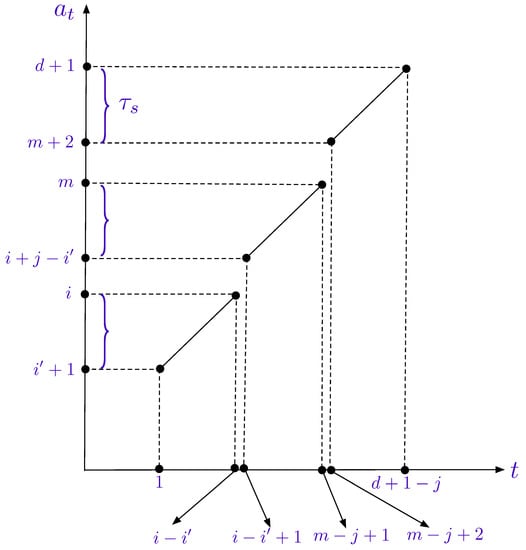
Fix , , , and . Let us first note that, if , we must have , and in this case the inequality (15) holds trivially with an equality. Therefore, for the remaining proof, we shall assume that . Now that , we may write for some integer and . Furthermore, let
As illustrated in Figure A1, is monotonically increasing with t. Finally, let and
for any . It is straightforward to verify that:
- for any ,
- ,
- .

Figure A1.
as a function of t. The sets form a partition of the set .
Consider a symmetrical code that satisfies the node regeneration requirement (3). Let us show by induction that for any , we have
To prove the base case of , first note that
where follows from the fact that is a function of by Lemma 1, and follows from the fact that is a function of . Furthermore,
where follows from the fact that is a function of by Lemma 1, and and follow from the symmetrical code that we consider. It follows that
where follows from the submodularity of the entropy function. This completes the proof of the base case of .
Assume that (A1) holds for some . We have
Note that both and are functions of , which is in turn a function of by Lemma 1. We thus have
Furthermore, by the symmetrical code that we consider, we have
It follows that
where follows from the submodularity of the entropy function. Substituting (A3) into (A2) gives
which completes the induction step and hence the proof of (A1).
Setting in (A1), we have
By the symmetrical codes that we consider, we have
and
for any subset such that . By Han’s subset inequality [32], we have
where follows from the fact that is a function of by Lemma 1. Substituting (A5) and (A6) into (A4) gives:
which is equivalent to (15) by noting that
This completes the proof of the exchange lemma. ☐
References
- Singleton, R.C. Maximum distance q-nary codes. IEEE Trans. Inf. Theory 1964, 10, 116–118. [Google Scholar] [CrossRef]
- Roche, J.R. Distributed Information Storage. Ph.D. Dissertation, Stanford University, Stanford, CA, USA, 1992. [Google Scholar]
- Roche, J.R.; Yeung, R.W.; Hau, K.P. Symmetrical multilevel diversity coding. IEEE Trans. Inf. Theory 1997, 43, 1059–1064. [Google Scholar] [CrossRef]
- Yeung, R.W.; Zhang, Z. On symmetrical multilevel diversity coding. IEEE Trans. Inf. Theory 1999, 45, 609–621. [Google Scholar] [CrossRef]
- Mohajer, S.; Tian, C.; Diggavi, S.N. Asymmetric multilevel diversity coding and asymmetric Gaussian multiple descriptions. IEEE Trans. Inf. Theory 2010, 56, 4367–4387. [Google Scholar] [CrossRef]
- Jiang, J.; Marukala, N.; Liu, T. Symmetrical multilevel diversity coding and subset entropy inequalities. IEEE Trans. Inf. Theory 2014, 60, 84–103. [Google Scholar] [CrossRef]
- Dimakis, A.G.; Godfrey, P.B.; Wu, Y.; Wainwright, M.; Ramchandran, K. Network coding for distributed storage systems. IEEE Trans. Inf. Theory 2010, 56, 4539–4551. [Google Scholar] [CrossRef]
- Rashmi, K.V.; Shah, N.B.; Kumar, P.V. Optimal exact-regenerating codes for distributed storage at the MSR and MBR points via a product-matrix construction. IEEE Trans. Inf. Theory 2011, 57, 5227–5239. [Google Scholar] [CrossRef]
- Cadambe, V.R.; Jafar, S.A.; Maleki, H.; Ramchandran, K.; Suh, C. Asymptotic interference alignment for optimal repair of MDS codes in distributed storage. IEEE Trans. Inf. Theory 2013, 59, 2974–2987. [Google Scholar] [CrossRef]
- Tian, C. Characterizing the rate region of the (4,3,3) exact-repair regenerating codes. IEEE J. Sel. Areas Commun. 2014, 32, 967–975. [Google Scholar] [CrossRef]
- Goparaju, S.; El Rouayheb, S.; Calderbank, R. New codes and inner bounds for exact repair in distributed storage systems. In Proceedings of the 2014 IEEE International Symposium on Information Theory (ISIT), Honolulu, HI, USA, 29 June–4 July 2014; pp. 1036–1040. [Google Scholar]
- Duursma, I.M. Outer bounds for exact repair codes. Arxiv, 2014; arXiv:1406.4852. [Google Scholar]
- Prakash, N.; Krishnan, M.N. The storage-repair-bandwidth trade-off of exact repair linear regenerating codes for the case d = k = n − 1. In Proceedings of the 2015 IEEE International Symposium on Information Theory (ISIT), Hong Kong, China, 14–19 June 2015; pp. 859–863. [Google Scholar]
- Elyasi, M.; Mohajer, S.; Tandon, R. Linear exact repair rate region of (k + 1,k,k) distributed storage systems: A new approach. In Proceedings of the 2015 IEEE International Symposium on Information Theory (ISIT), Hong Kong, China, 14–19 June 2015; pp. 2061–2065. [Google Scholar]
- Tian, C.; Sasidharan, B.; Aggarwal, V.; Vaishampayan, V.A.; Kumar, P.V. Layered exact-repair regenerating codes via embedded error correction and block designs. IEEE Trans. Inf. Theory 2015, 61, 1933–1947. [Google Scholar] [CrossRef]
- Ye, M.; Barg, A. Explicit constructions of high-rate MDS array codes with optimal repair bandwidth. IEEE Trans. Inf. Theory 2017, 63, 2001–2014. [Google Scholar] [CrossRef]
- Kralevska, K.; Gligoroski, D. An Explicit Construction of Systematic MDS Codes with Small Sub-packetization for All-Node Repair. Arxiv, 2018; arXiv:1806.03103. [Google Scholar]
- Goparaju, S.; Fazeli, A.; Vardy, A. Minimum storage regenerating codes for all parameters. IEEE Trans. Inf. Theory 2017, 63, 6318–6328. [Google Scholar] [CrossRef]
- Kralevska, K.; Gligoroski, D.; Jensen, R.E.; Overby, H. Hashtag erasure codes: From theory to practice. IEEE Trans. Big Data 2017, 1. [Google Scholar] [CrossRef]
- Kralevska, K.; Gligoroski, D.; Øverby, H. General Sub-packetized Access Optimal Regenerating Codes. IEEE Commun. Lett. 2016, 20, 1281–1284. [Google Scholar] [CrossRef]
- Tian, C.; Liu, T. Multilevel diversity coding with regeneration. IEEE Trans. Inf. Theory 2016, 62, 4833–4847. [Google Scholar] [CrossRef]
- Shao, S.; Liu, T.; Tian, C. Multilevel diversity coding with regeneration: Separate coding achieves the MBR point. In Proceedings of the 2016 Annual Conference on Information Science and Systems (CISS), Princeton, NJ, USA, 16–18 March 2016; pp. 602–607. [Google Scholar]
- Pawar, S.; El Rouayheb, S.; Ramchandran, K. On secure distributed data storage under repair dynamics. In Proceedings of the 2010 IEEE International Symposium on Information Theory (ISIT), Austin, TX, USA, 13–18 June 2010; pp. 2543–2547. [Google Scholar]
- Pawar, S.; El Rouayheb, S.; Ramchandran, K. Securing dynamic distributed storage systems against eavesdropping and adversarial Attacks. IEEE Trans. Inf. Theory 2011, 57, 6734–6753. [Google Scholar] [CrossRef]
- Shah, N.B.; Rashmi, K.V.; Kumar, P.V. Information-theoretically secure regenerating codes for distributed storage. In Proceedings of the 2011 IEEE Global Telecommunications Conference (GLOBECOM), Kathmandu, Nepal, 5–9 December 2011; pp. 1–5. [Google Scholar]
- Goparaju, S.; El Rouayheb, S.; Calderbank, R.; Poor, H.V. Data secrecy in distributed storage systems under exact repair. In Proceedings of the 2013 International Symposium on Network Coding (NetCod), Calgary, AB, Canada, 7–9 June 2013; pp. 1–6. [Google Scholar]
- Rawat, A.S.; Koyluoglu, O.O.; Silberstein, N.; Vishwanath, S. Optimal locally repairable and secure codes for distributed storage systems. IEEE Trans. Inf. Theory 2014, 60, 212–236. [Google Scholar] [CrossRef]
- Tandon, R.; Amuru, S.; Clancy, T.C.; Buehrer, R.M. Towards optimal secure distributed storage systems with exact repair. IEEE Trans. Inf. Theory 2016, 62, 3477–3492. [Google Scholar] [CrossRef]
- Ye, F.; Shum, K.W.; Yeung, R.W. The rate region of secure exact-repair regenerating codes for 5 nodes. In Proceedings of the 2016 IEEE International Symposium on Information Theory (ISIT), Barcelona, Spain, 10–15 July 2016; pp. 1406–1410. [Google Scholar]
- Shao, S.; Liu, T.; Tian, C.; Shen, C. On the trade-off region of secure exact-repair regenerating codes. IEEE Trans. Inf. Theory 2017, 63, 7253–7266. [Google Scholar] [CrossRef]
- Balasubramanian, A.; Ly, H.D.; Li, S.; Liu, T.; Miller, S.L. Secure symmetrical multilevel diversity coding. IEEE Trans. Inf. Theory 2013, 59, 3572–3581. [Google Scholar] [CrossRef]
- Han, T.S. Nonnegative entropy measures of multivariate symmetric correlations. Inf. Control 1978, 36, 133–156. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).