Benefit-Cost Analysis of Security Systems for Multiple Protected Assets Based on Information Entropy
Abstract
:1. Introduction
2. Benefit-Cost Estimation of Security Systems Based on Information Entropy

2.1. Identify Assets, Security Unit and Intrusion Path
- (1)
- Attackers start from the outside and treat one of protected assets as a target of attack;
- (2)
- There exists at least one path can get to the protected asset;
- (3)
- All units in the path have protection capability values; the attacker needs to pay a cost to pass through the security unit.
2.2. Security Unit Effectiveness Assessment
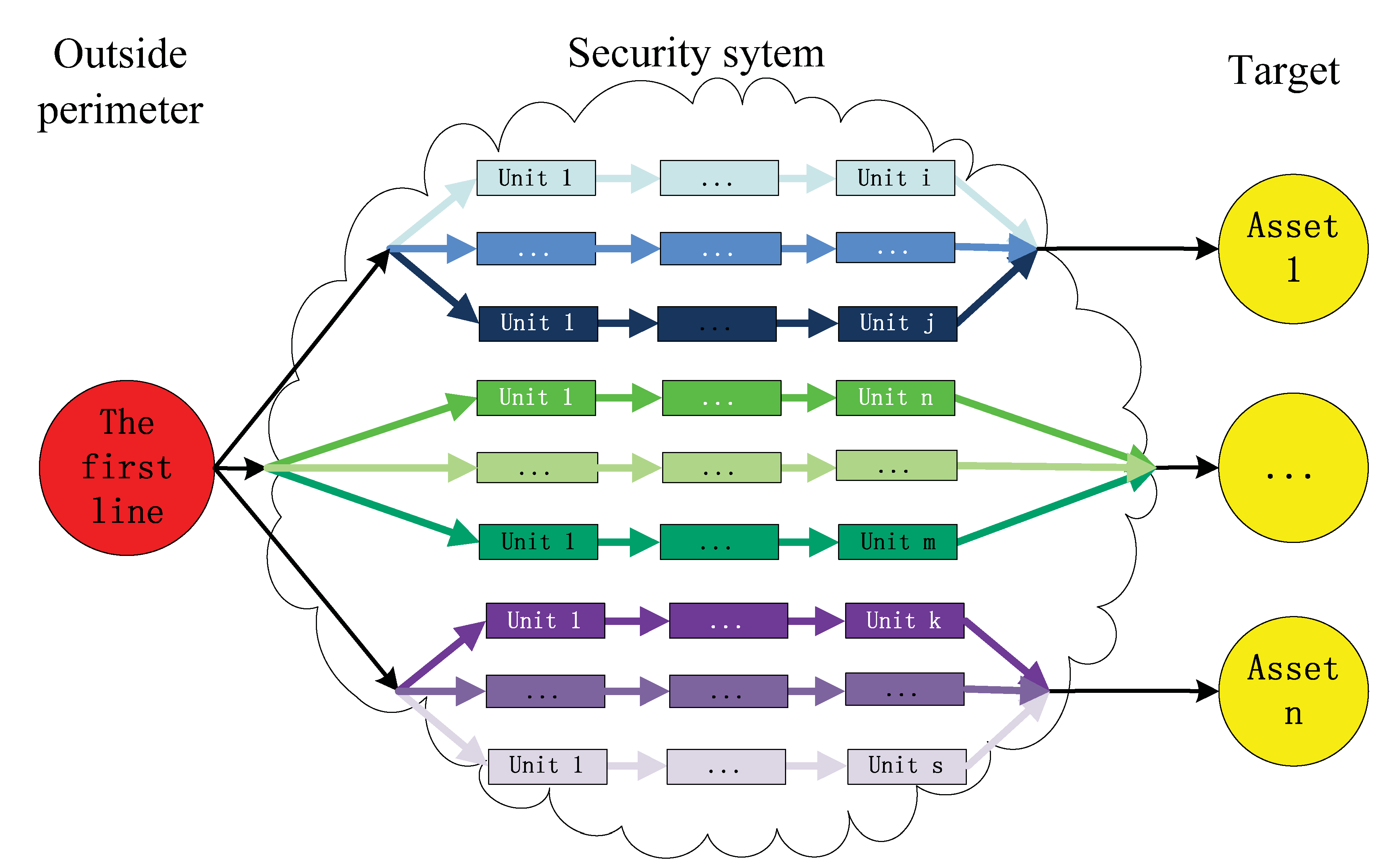
2.3. Intrusion Path Effectiveness Assessment
2.4. Security System Risk Assessment
2.5. Benefit-Cost Estimation
3. An Application of a Museum Scenario
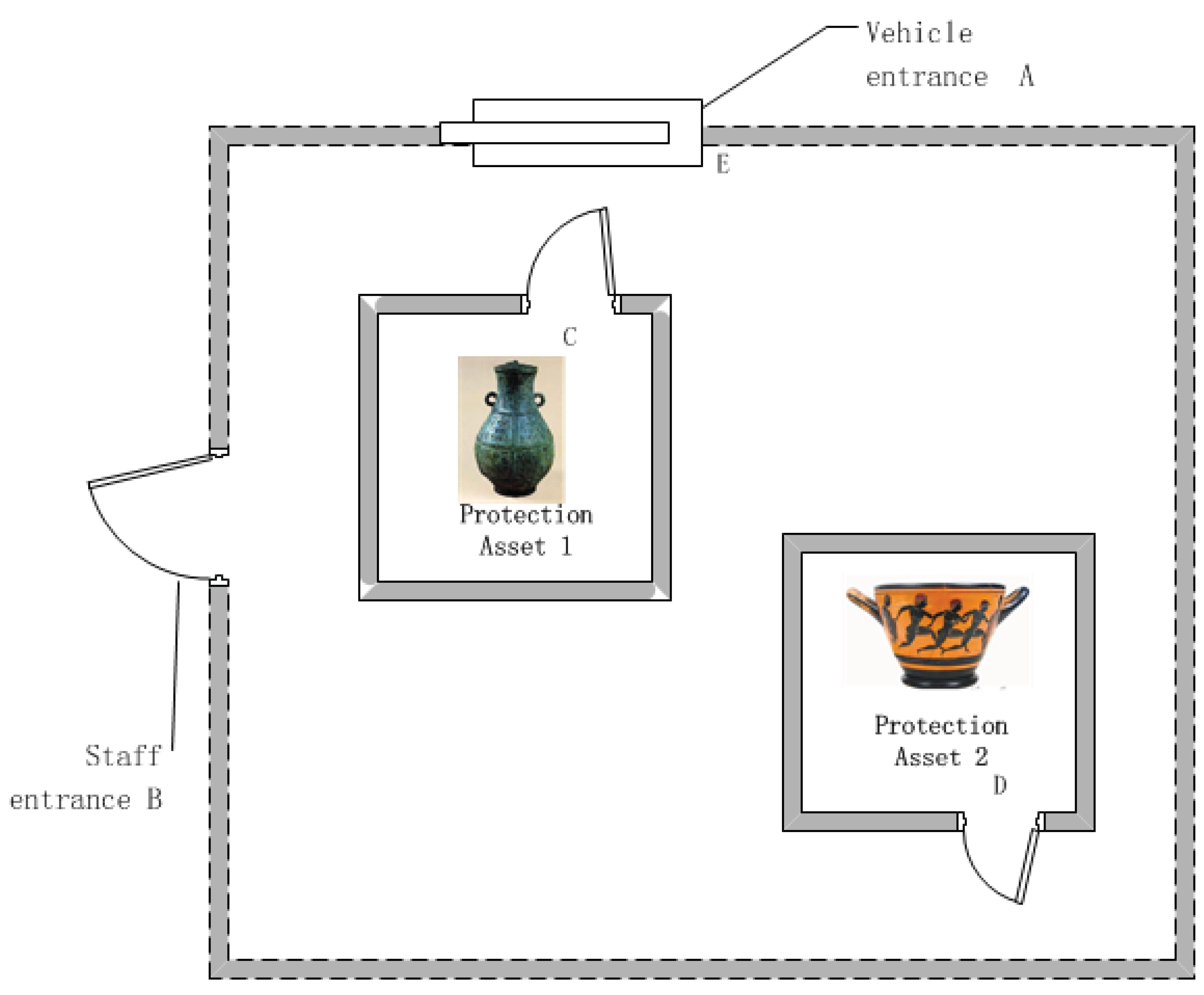
3.1. Identify Assets, Security Unit and Intrusion Path
| Intrusion Path | Protection element of Unit 1 | Protection element of Unit 2 |
|---|---|---|
| Path 1 for asset 1 | Vehicle entrance A | Door C |
| Path 2 for asset 1 | Staff entrance B | Door C |
| Path 1 for asset 2 | Vehicle entrance A | Door D |
| Path 2 for asset 2 | Staff entrance B | Door D |
3.2. The Protection Effectiveness of Security Unit
| Unit | Detection | Delay | Response | Effectiveness |
|---|---|---|---|---|
| Vehicle entrance A | 0.7 | 0.8 | 0.9 | 0.74 |
| Staff entrance B | 0.8 | 0.8 | 0.6 | 0.60 |
| Door C | 0.9 | 0.6 | 0.8 | 0.70 |
| Door D | 0.7 | 0.6 | 0.9 | 0.64 |
3.3. The Protection Effectiveness of an Intrusion Path
| Intrusion Path | Effectiveness |
|---|---|
| Path 1 for asset 1 | 1.44 |
| Path 2 for asset 2 | 1.30 |
| Path 1 for asset 1 | 1.38 |
| Path 2 for asset 2 | 1.24 |
3.4. The Risk Assessment of the Security System
| Parameter | i = 1 | i = 2 |
|---|---|---|
| 1.30 | 1.24 | |
| 0.6 | 0.4 | |
| 100,000 | 200,000 | |
| 1.6 × 104 | 2.32 × 104 |
3.5. Benefit-Cost Estimation
| Strategy | Risk Reduction Value | Benefit-Cost Value |
|---|---|---|
| 1 | 3 × 103 | 30 |
| 2 | 3 × 103 | 30 |
| 3 | 1.4 × 103 | 1.4 × 102 |
4. Conclusions
Acknowledgments
References and Notes
- Graves, G.H. Analytical foundations of physical security system assessment. Ph.D. Thesis, Texas A&M University, College Station, TX, USA, August 2006. [Google Scholar]
- US Department of Homeland Security. National infrastructure protection plan. Available online: http://www.dhs.gov/xlibrary/assets/NIPP_Plan.pdf (accessed on 20 February 2009).
- Chen, Z.H. Research and practice of effectiveness evaluation of security system (in Chinese). China Security & Protection 2007, 11, 16–20. [Google Scholar]
- Sun, Y.-H.; Li, S.-J.; Li, B. Quantitative assessment of physical protection system for nuclear power plant (in Chinese). Nuclear Power Engineering 2009, 30, 20–25. [Google Scholar]
- Wu, Q.; Yan, L.L. The risk assessment model for enterprise security (in Chinese). Safety & Security Technology 2010, 10, 10–14. [Google Scholar]
- Li, J.-S. Inquiry on the design of museum building security prevention system (in Chinese). Shanxi Architecture 2011, 37, 29. [Google Scholar]
- Bennett, H.A. The EASI approach to physical security evaluation; SAND76-0500; Sandia Labs.: Albuquerque, NM, USA, 1 January 1977; pp. 1–35. [Google Scholar]
- Chapman, L.D.; Harlan, C.P. EASI estimate of adversary sequence interruption on an IBM PC; SAND-85-1105; Sandia Labs.: Albuquerque, NM, USA, 1 October 1985; pp. 1–66. [Google Scholar]
- Matter, J.C. SAVI: APC-based vulnerability assessment program; SAND 88-1279; Sandia Labs.: Albuquerque, NM, USA, 1 July 1988; pp. 1–19. [Google Scholar]
- Garcia, M.L. Design and Evaluation of Physical Protection Systems; Butterworth-Heinemann: Burlington, MA, USA, 2007. [Google Scholar]
- Hicks, M.J.; Snell, M.S.; Sandoval, J.S.; Potter, C.S. Physical protection systems—Cost and performance analysis: A case study. IEEE Aero. Electron. Syst. Mag. 1999, 14, 9–13. [Google Scholar] [CrossRef]
- Fischer, R.J.; Green, G. Introduction to Security, 7th ed.; Elsevier: Boston, MA, USA, 2004. [Google Scholar]
- Shen, N. Design and development of physical protection system. Master Thesis, China Institute of Atomic Energy, Beijing, China, July 2003. [Google Scholar]
- Cummings, M.C.; Mcgarvey, D.C.; Vinch, P.M. Homeland security risk assessment. Volume II. Methods, techniques, and tools; RP05-024-01a; Homeland Security Institute: Arlington, VA, USA, 16 June 2006; pp. 1–160. [Google Scholar]
- Keeney, R.L. Modeling values for anti-terrorism analysis. Risk Anal. 2007, 27, 585–596. [Google Scholar] [CrossRef] [PubMed]
- Nikoofal, M.; Zhuang, J. Robust allocation of a defensive budget considering an attacker’s private information. Risk Anal. 2011. [Google Scholar] [CrossRef] [PubMed]
- Golalikhani, M.; Zhuang, J. Modeling arbitrary layers of continuous level defenses in facing with a strategic attacker. Risk Anal. 2011, 31, 533–547. [Google Scholar] [CrossRef] [PubMed]
- Zhuang, J.; Bier, V.M. Balancing terrorism and natural disasters—Defensive strategy with endogenous attack effort. Oper. Res. 2007, 55, 976–991. [Google Scholar] [CrossRef]
- Zhuang, J.; Bier, V.M.; Alagoz, O. Modeling secrecy and deception in a multiple-period attacker-defender signaling game. Eur. J. Oper. Res. 2010, 203, 409–418. [Google Scholar] [CrossRef]
- Hausken, K.; Zhuang, J. The timing and deterrence of terrorist attacks due to exogenous dynamics. Eur. J. Oper. Res. 2011. [Google Scholar] [CrossRef]
- Hao, M.; Jin, S.; Zhuang, J. Robustness of optimal defensive resource allocations in the face of less than fully rational attackers. In Proceedings of the 2009 Industrial Engineering Research Conference, Miami, FL, USA, 30 May–3 June 2009; pp. 886–891.
- Fisscher, R.J.; Green, G. Introduction to Security, 7th ed.; Elsevier: Burlington, MA, USA, 2004. [Google Scholar]
- Clausius, R. The Mechanical Theory of Heat—With Its Applications to the Steam Engine and to Physical Properties of Bodies; John van Voorst: London, UK, 1986. [Google Scholar]
- Sandler, S.I. Chemical and Engineering Thermodynamics, 3rd ed.; Wiley: New York, NY, USA, 1999. [Google Scholar]
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Golan, A.; Maasoumi, E. Information theoretic and entropy methods: An overview. Economet. Rev. 2008, 27, 317–328. [Google Scholar] [CrossRef]
- Davies, S.J.; Minion, R.R. Security Supervision: Theory and Practice of Asset Protection, 3rd ed.; Butterworth-Heinemann: Jordan Hill, Oxford, UK, 2008. [Google Scholar]
- Rico, G.; Beasley, J.S. Physical protection systems: Concepts, analysis, and practice in the ET classroom. Available online: http://spacegrant.nmsu.edu/NMSU/2006/rico.pdf (accessed on 27 September 2006).
© 2012 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Dai, J.; Hu, R.; Chen, J.; Cai, Q. Benefit-Cost Analysis of Security Systems for Multiple Protected Assets Based on Information Entropy. Entropy 2012, 14, 571-580. https://doi.org/10.3390/e14030571
Dai J, Hu R, Chen J, Cai Q. Benefit-Cost Analysis of Security Systems for Multiple Protected Assets Based on Information Entropy. Entropy. 2012; 14(3):571-580. https://doi.org/10.3390/e14030571
Chicago/Turabian StyleDai, Jingjing, Ruimin Hu, Jun Chen, and Qing Cai. 2012. "Benefit-Cost Analysis of Security Systems for Multiple Protected Assets Based on Information Entropy" Entropy 14, no. 3: 571-580. https://doi.org/10.3390/e14030571
APA StyleDai, J., Hu, R., Chen, J., & Cai, Q. (2012). Benefit-Cost Analysis of Security Systems for Multiple Protected Assets Based on Information Entropy. Entropy, 14(3), 571-580. https://doi.org/10.3390/e14030571




