Authorized and Unauthorized Consumption of SVOD Content: Modeling Determinants of Demand and Measuring Effects of Enforcing Access Control
Abstract
1. Introduction
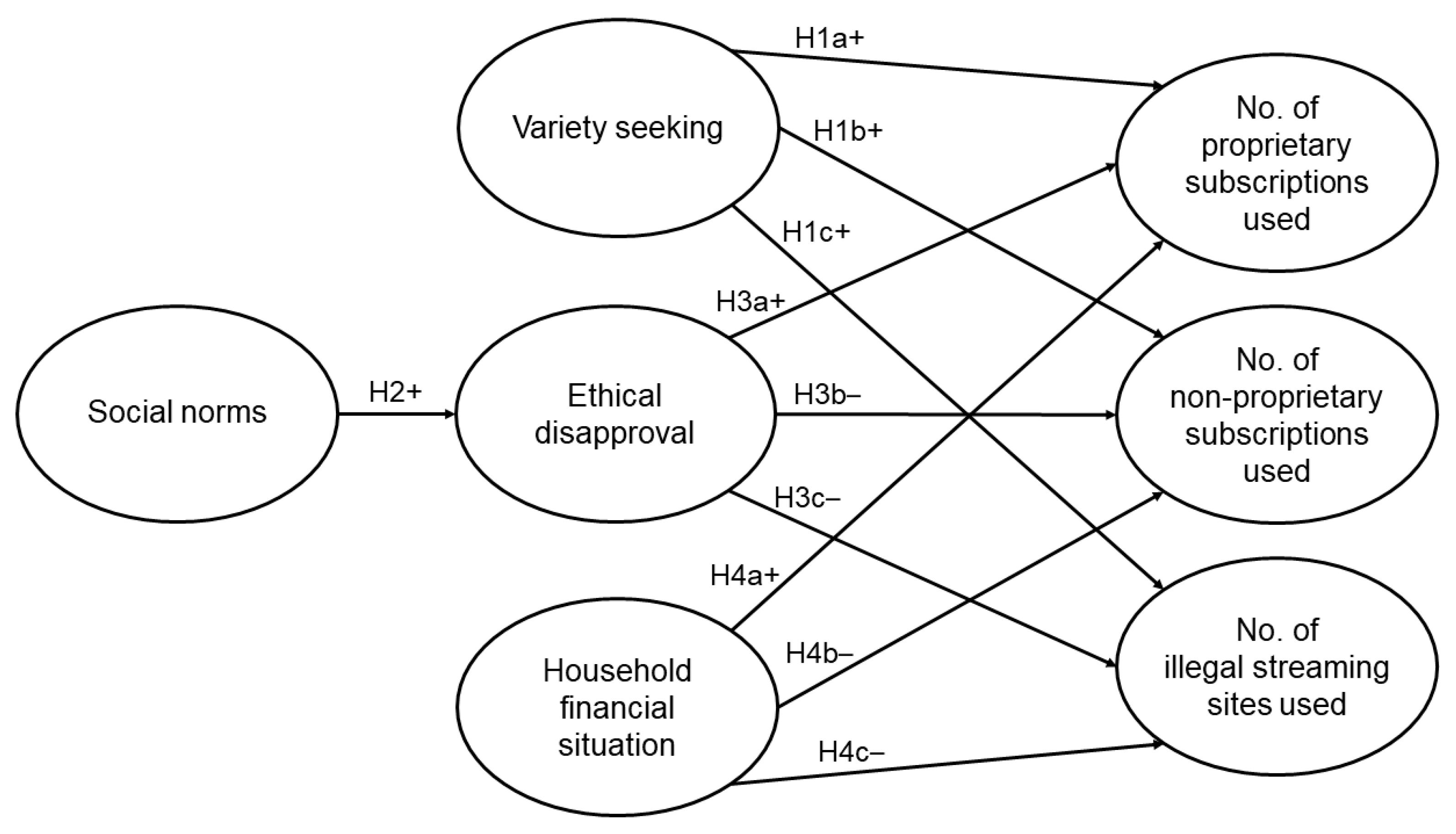
2. Hypothesis Development
2.1. Baseline Model
2.2. Effects of Access Control Enforcement
2.3. Change Model
3. Methodology
3.1. Survey Development
3.2. Variables
3.3. Statistical Analyses
4. Results
4.1. Baseline Model
4.2. Effects of Access Control Enforcement
4.3. Change Model
5. Discussion
5.1. Theoretical Implications
5.2. Managerial Implications
5.3. Limitations
5.4. Future Research Directions
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A. Suggested Use of SVOD Platforms and Illegal Streaming Sites
Appendix B. Alternative Versions of the Warning
References
- Palomba, A. Do SVOD Product Attribute Trade-Offs Predict SVOD Subscriptions and SVOD Account Access? Using Utility Constant Sums to Predict SVOD Subscriptions and SVOD Account Access. Int. J. Media Manag. 2020, 22, 168–190. [Google Scholar] [CrossRef]
- Schauerte, R.; Feiereisen, S.; Malter, A.J. What Does It Take to Survive in a Digital World? Resource-Based Theory and Strategic Change in the TV Industry. J. Cult. Econ. 2021, 45, 263–293. [Google Scholar] [CrossRef]
- Weinberg, C.B.; Otten, C.; Orbach, B.; McKenzie, J.; Gil, R.; Chisholm, D.C.; Basuroy, S. Technological Change and Managerial Challenges in the Movie Theater Industry. J. Cult. Econ. 2021, 45, 239–262. [Google Scholar] [CrossRef]
- Chalaby, J.K. The Streaming Industry and the Platform Economy: An Analysis. Media Cult. Soc. 2023, 01634437231210439. [Google Scholar] [CrossRef]
- Leichtman Research Group. 83% of U.S. Households Have an SVOD Service; Leichtman Research Group: Durham, NH, USA, 2023; Available online: https://leichtmanresearch.com/83-of-u-s-households-have-an-svod-service/ (accessed on 8 September 2023).
- Nagaraj, S.; Singh, S.; Yasa, V.R. Factors Affecting Consumers’ Willingness to Subscribe to over-the-Top (OTT) Video Streaming Services in India. Technol. Soc. 2021, 65, 101534. [Google Scholar] [CrossRef]
- Chakraborty, D.; Siddiqui, M.; Siddiqui, A.; Paul, J.; Dash, G.; Mas, F.D. Watching Is Valuable: Consumer Views—Content Consumption on OTT Platforms. J. Retail. Consum. Serv. 2023, 70, 103148. [Google Scholar] [CrossRef]
- Yoon, J.H.; Kim, H.K. Why Do Consumers Continue to Use OTT Services? Electron. Commer. Res. Appl. 2023, 60, 101285. [Google Scholar] [CrossRef]
- Sahu, G.; Gaur, L.; Singh, G. Applying Niche and Gratification Theory Approach to Examine the Users’ Indulgence towards over-the-Top Platforms and Conventional TV. Telemat. Inform. 2021, 65, 101713. [Google Scholar] [CrossRef]
- Menon, D. Purchase and Continuation Intentions of over -the -Top (OTT) Video Streaming Platform Subscriptions: A Uses and Gratification Theory Perspective. Telemat. Inform. Rep. 2022, 5, 100006. [Google Scholar] [CrossRef]
- Soren, A.A.; Chakraborty, S. Adoption, Satisfaction, Trust, and Commitment of over-the-Top Platforms: An Integrated Approach. J. Retail. Consum. Serv. 2024, 76, 103574. [Google Scholar] [CrossRef]
- Lee, P.; Stanton, B.; Sharma, R. Digital Consumer Trends 2023; Deloitte: London, UK, 2023; Available online: https://www2.deloitte.com/content/dam/Deloitte/uk/Documents/technology-media-telecommunications/deloitte-uk-digital-consumer-trends-2023-deck.pdf (accessed on 8 September 2023).
- Chatterley, A. The Film and TV Piracy Report 2022: Unlocking the Value of Digital Piracy Data for the Film & TV Industries; MUSO: London, UK, 2023; Available online: https://www.muso.com/2022-muso-piracy-film-and-tv-report (accessed on 15 September 2023).
- Redondo, I.; Serrano, D. Giants with Feet of Clay? An Inquiry into User Payment Patterns for Subscription Video-on-Demand Services. Adm. Sci. 2023, 13, 122. [Google Scholar] [CrossRef]
- McAlister, L.; Pessemier, E. Variety Seeking Behavior: An Interdisciplinary Review. J. Consum. Res. 1982, 9, 311–322. [Google Scholar] [CrossRef]
- Steenkamp, J.-B.E.M.; Baumgartner, H. The Role of Optimum Stimulation Level in Exploratory Consumer Behavior. J. Consum. Res. 1992, 19, 434–448. [Google Scholar] [CrossRef]
- Gu, R.; Oh, L.-B.; Wang, K. Multi-Homing on SNSs: The Role of Optimum Stimulation Level and Perceived Complementarity in Need Gratification. Inf. Manag. 2016, 53, 752–766. [Google Scholar] [CrossRef]
- Vakeel, K.A.; Fudurić, M.; Malthouse, E.C. Extending Variety Seeking to Multi-Sided Platforms: Impact of New Retailer Listing. J. Retail. Consum. Serv. 2021, 59, 102382. [Google Scholar] [CrossRef]
- Hu, Y.; Zhao, L.; Luo, X.; Gupta, S.; He, X. Trialing or Combining? Understanding Consumer Partial Switching in Mobile Application Usage from the Variety Seeking Perspective. Internet Res. 2021, 31, 1769–1802. [Google Scholar] [CrossRef]
- Sinha, R.K.; Mandel, N. Preventing Digital Music Piracy: The Carrot or the Stick? J. Marketing 2008, 72, 1–15. [Google Scholar] [CrossRef]
- Raju, P.S. Optimum Stimulation Level: Its Relationship to Personality, Demographics, and Exploratory Behavior. J. Consum. Res. 1980, 7, 272–282. [Google Scholar] [CrossRef]
- Fishbein, M.; Ajzen, I. Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research; Addison-Wesley Publishing Company: Reading, MA, USA, 1975. [Google Scholar]
- Bandura, A. Social Foundations of Thought and Action: A Social Cognitive Theory; Prentice Hall: Englewood Cliffs, NJ, USA, 1986. [Google Scholar]
- Liao, C.; Lin, H.-N.; Liu, Y.-P. Predicting the Use of Pirated Software: A Contingency Model Integrating Perceived Risk with the Theory of Planned Behavior. J. Bus. Ethics 2010, 91, 237–252. [Google Scholar] [CrossRef]
- Sardanelli, D.; Vollero, A.; Siano, A.; Bottoni, G. Lowering the Pirate Flag: A TPB Study of the Factors Influencing the Intention to Pay for Movie Streaming Services. Electron. Commer. Res. 2019, 19, 549–574. [Google Scholar] [CrossRef]
- Aarts, H.; Verplanken, B.; van Knippenberg, A. Predicting Behavior from Actions in the Past: Repeated Decision Making or a Matter of Habit? J. Appl. Soc. Psychol. 1998, 28, 1355–1374. [Google Scholar] [CrossRef]
- Ouellette, J.A.; Wood, W. Habit and Intention in Everyday Life: The Multiple Processes by Which Past Behavior Predicts Future Behavior. Psychol. Bull. 1998, 124, 54–74. [Google Scholar] [CrossRef]
- Phau, I.; Lim, A.; Liang, J.; Lwin, M. Engaging in Digital Piracy of Movies: A Theory of Planned Behaviour Approach. Internet Res. 2014, 24, 246–266. [Google Scholar] [CrossRef]
- Phau, I.; Liang, J. Downloading Digital Video Games: Predictors, Moderators and Consequences. Mark. Intell. Plan. 2012, 30, 740–756. [Google Scholar] [CrossRef]
- Siponen, M.; Vance, A.; Willison, R. New Insights into the Problem of Software Piracy: The Effects of Neutralization, Shame, and Moral Beliefs. Inf. Manag. 2012, 49, 334–341. [Google Scholar] [CrossRef]
- Akbulut, Y. Exploration of the Antecedents of Digital Piracy through a Structural Equation Model. Comput. Educ. 2014, 78, 294–305. [Google Scholar] [CrossRef]
- Coyle, J.R.; Gould, S.J.; Gupta, P.; Gupta, R. “To Buy or to Pirate”: The Matrix of Music Consumers’ Acquisition-Mode Decision-Making. J. Bus. Res. 2009, 62, 1031–1037. [Google Scholar] [CrossRef]
- Nanda, A.P.; Banerjee, R. Consumer’s Subjective Financial Well-Being: A Systematic Review and Research Agenda. Int. J. Consum. Stud. 2021, 45, 750–776. [Google Scholar] [CrossRef]
- De La Rosa, W.; Tully, S.M. The Impact of Payment Frequency on Consumer Spending and Subjective Wealth Perceptions. J. Consum. Res. 2022, 48, 991–1009. [Google Scholar] [CrossRef]
- Gunson, N.; Marshall, D.; Morton, H.; Jack, M. User Perceptions of Security and Usability of Single-Factor and Two-Factor Authentication in Automated Telephone Banking. Comput. Secur. 2011, 30, 208–220. [Google Scholar] [CrossRef]
- Krol, K.; Philippou, E.; De Cristofaro, E.; Sasse, M.A. “They Brought in the Horrible Key Ring Thing!” Analysing the Usability of Two-Factor Authentication in UK Online Banking. arXiv 2015, arXiv:1501.04434. [Google Scholar] [CrossRef]
- Brehm, J.W. A Theory of Psychological Reactance; Academic Press: New York, NY, USA, 1966. [Google Scholar]
- Brehm, S.S.; Brehm, J.W. Psychological Reactance: A Theory of Freedom and Control; Academic Press: New York, NY, USA, 1981. [Google Scholar]
- Lowry, P.B.; Moody, G.D. Proposing the Control-Reactance Compliance Model (CRCM) to Explain Opposing Motivations to Comply with Organisational Information Security Policies. Inf. Syst. J. 2015, 25, 433–463. [Google Scholar] [CrossRef]
- Dutson, J.; Allen, D.; Eggett, D.; Seamons, K. Don’t Punish All of Us: Measuring User Attitudes about Two-Factor Authentication. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Stockholm, Sweden, 17–19 June 2019; pp. 119–128. [Google Scholar] [CrossRef]
- Colnago, J.; Devlin, S.; Oates, M.; Swoopes, C.; Bauer, L.; Cranor, L.; Christin, N. “It’s Not Actually That Horrible”: Exploring Adoption of Two-Factor Authentication at a University. In Proceedings of the 2018 CHI Conference on Human Factors in Computing Systems, Montreal, QC, Canada, 21–26 April 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 1–11. [Google Scholar] [CrossRef]
- Folger, R.G.; Cropanzano, R. Organizational Justice and Human Resource Management; SAGE Publications: Thousand Oaks, CA, USA, 1998. [Google Scholar]
- Folger, R.G.; Cropanzano, R. Fairness Theory: Justice as Accountability. In Advances in Organizational Justice; Stanford University Press: Stanford, CA, USA, 2002. [Google Scholar]
- Lowry, P.B.; Posey, C.; Bennett, R.J.; Roberts, T.L. Leveraging Fairness and Reactance Theories to Deter Reactive Computer Abuse Following Enhanced Organisational Information Security Policies: An Empirical Study of the Influence of Counterfactual Reasoning and Organisational Trust. Inf. Syst. J. 2015, 25, 193–273. [Google Scholar] [CrossRef]
- Richards, A.S.; Bessarabova, E.; Banas, J.A.; Larsen, M. Freedom-Prompting Reactance Mitigation Strategies Function Differently across Levels of Trait Reactance. Commun. Q. 2021, 69, 238–258. [Google Scholar] [CrossRef]
- Bin-Nashwan, S.A.; Al-Hamedi, A.M.; Marimuthu, M.; Al-Harethi, A. Study on System Fairness Dimensions and Tax Compliance in the Middle East Context. Probl. Perspect. Manag. 2020, 18, 181–191. [Google Scholar] [CrossRef]
- Varet, F.; Granié, M.-A.; Carnis, L.; Martinez, F.; Pelé, M.; Piermattéo, A. The Role of Perceived Legitimacy in Understanding Traffic Rule Compliance: A Scoping Review. Accid. Anal. Prev. 2021, 159, 106299. [Google Scholar] [CrossRef] [PubMed]
- Halliday, S.; Finch, N.; Meers, J.; Tomlinson, J.; Wilberforce, M. Why the UK Complied with COVID-19 Lockdown Law. King’s Law J. 2022, 33, 386–410. [Google Scholar] [CrossRef]
- Steenkamp, J.-B.E.M.; Baumgartner, H. Development and Cross-Cultural Validation of a Short Form of CSI as a Measure of Optimum Stimulation Level. Int. J. Res. Mark. 1995, 12, 97–104. [Google Scholar] [CrossRef]
- López-Mosquera, N. Gender Differences, Theory of Planned Behavior and Willingness to Pay. J. Environ. Psychol. 2016, 45, 165–175. [Google Scholar] [CrossRef]
- Munerah, S.; Koay, K.Y.; Thambiah, S. Factors Influencing Non-Green Consumers’ Purchase Intention: A Partial Least Squares Structural Equation Modelling (PLS-SEM) Approach. J. Clean. Prod. 2021, 280, 124192. [Google Scholar] [CrossRef]
- Yoon, C. Theory of Planned Behavior and Ethics Theory in Digital Piracy: An Integrated Model. J. Bus. Ethics 2011, 100, 405–417. [Google Scholar] [CrossRef]
- Bayuk, J.; Altobello, S.A. Can Gamification Improve Financial Behavior? The Moderating Role of App Expertise. Int. J. Bank Mark. 2019, 37, 951–975. [Google Scholar] [CrossRef]
- Roll, S.; Kondratjeva, O.; Bufe, S.; Grinstein-Weiss, M.; Skees, S. Assessing the Short-Term Stability of Financial Well-Being in Low- and Moderate-Income Households. J. Fam. Econ. Issues 2022, 43, 100–127. [Google Scholar] [CrossRef]
- Redondo, I.; Aznar, G. Whitelist or Leave Our Website! Advances in the Understanding of User Response to Anti-Ad-Blockers. Informatics 2023, 10, 30. [Google Scholar] [CrossRef]
- Shen, L.; Dillard, J.P. Psychometric Properties of the Hong Psychological Reactance Scale. J. Personal. Assess. 2005, 85, 74–81. [Google Scholar] [CrossRef]
- Hair, J.; Hult, G.T.M.; Ringle, C.M.; Sarstedt, M. A Primer on Partial Least Squares Structural Equation Modeling, 3rd ed.; SAGE Publications: Los Angeles, CA, USA, 2021. [Google Scholar]
- Ringle, C.M.; Wende, S.; Becker, J.-M. SmartPLS Software, version 4; SmartPLS GmbH: Monheim am Rhein, Germany, 2022. Available online: https://www.smartpls.com (accessed on 15 September 2023).
- Redondo, I.; Serrano, D. Authorized and Unauthorized Consumption of SVOD Content: Modeling Determinants of Demand and Measuring Effects of Enforcing Access Control. 2024. [Data File]. Available online: https://doi.org/10.6084/m9.figshare.24559096 (accessed on 28 November 2023).

| Variables | Categories | No. of Subjects (n = 503) | Sample Percentage |
|---|---|---|---|
| Gender | Males | 219 | 43.5 |
| Females | 284 | 56.5 | |
| Age | 16–30 | 115 | 22.9 |
| 31–40 | 127 | 25.2 | |
| 41–50 | 137 | 27.2 | |
| 51 or more | 124 | 24.7 | |
| Education | Primary | 54 | 10.7 |
| Secondary | 191 | 38.0 | |
| Tertiary | 258 | 51.3 | |
| Warning version | First | 126 | 25.0 |
| Second | 127 | 25.2 | |
| Third | 126 | 25.0 | |
| Fourth | 124 | 24.7 | |
| Use of illegal streaming sites | Yes | 126 | 25.0 |
| No | 377 | 75.0 |
| Latent Variables | Items | Outer Loadings |
|---|---|---|
| Variety seeking (AVE = 0.681; CR = 0.845) | I like to experience novelty and change in my daily routine | 0.832 |
| I am continually seeking new ideas and experiences | 0.872 | |
| I like to continually change activities | 0.806 | |
| When things get boring, I like to find some new and unfamiliar experiences | 0.789 | |
| Social norms (AVE = 0.774; CR = 0.902) | Many friends and relatives would disapprove if I used an SVOD platform without paying its full cost | 0.908 |
| People important to me think it illicit to use an SVOD platform without paying its full cost | 0.887 | |
| Many close people recommend that I not use SVOD platforms if I do not pay all their costs | 0.831 | |
| The people I appreciate the most would never use SVOD platforms without paying all their costs | 0.891 | |
| Ethical disapproval (AVE = 0.835; CR = 0.934) | Using an SVOD platform without paying its full cost goes against my principles | 0.928 |
| Using an SVOD platform without paying its full cost is ethically unacceptable | 0.941 | |
| Using an SVOD platform without paying its full cost is a practice that should be prosecuted | 0.905 | |
| Using an SVOD platform without paying its full cost is a practice that one should feel guilty about | 0.880 | |
| Household financial situation (AVE = 0.720; CR = 0.868) | At home we could handle a major unexpected expense | 0.881 |
| At home we have money left over at the end of the month | 0.889 | |
| At home we can afford extra expenses | 0.867 | |
| At home we are optimistic about our financial future | 0.750 |
| Latent Variable | (1) | (2) | (3) | (4) |
|---|---|---|---|---|
| (1) Variety seeking | 0.825 | |||
| (2) Social norms | 0.254 | 0.880 | ||
| (3) Ethical disapproval | 0.228 | 0.804 | 0.914 | |
| (4) Household financial situation | 0.256 | 0.178 | 0.154 | 0.848 |
| Hypothesized Relationships | Path Coeff. | t Values | Sig. | f2 | q2 |
|---|---|---|---|---|---|
| H1a: Variety seeking → No. of proprietary subscriptions used | 0.142 | 3.334 | p < 0.01 | 0.020 | 0.016 |
| H1b: Variety seeking → No. of non-proprietary subscriptions used | 0.059 | 1.419 | 0.156 | 0.003 | –0.001 |
| H1c: Variety seeking → No. of illegal streaming sites used | 0.130 | 2.920 | p < 0.01 | 0.016 | 0.010 |
| H2: Social norms → Ethical disapproval | 0.804 | 43.231 | p < 0.001 | 1.822 | 1.808 |
| H3a: Ethical disapproval → No. of proprietary subscriptions used | 0.036 | 0.825 | 0.410 | 0.001 | –0.003 |
| H3b: Ethical disapproval → No. of non-proprietary subscriptions used | –0.246 | 5.405 | p < 0.001 | 0.061 | 0.028 |
| H3c: Ethical disapproval → No. of illegal streaming sites used | –0.116 | 2.728 | p < 0.01 | 0.013 | 0.002 |
| H4a: Household financial situation → No. of proprietary subscriptions used | 0.212 | 5.326 | p < 0.001 | 0.046 | 0.041 |
| H4b: Household financial situation → No. of non-proprietary subscriptions used | –0.065 | 1.353 | 0.176 | 0.004 | –0.001 |
| H4c: Household financial situation → No. of illegal streaming sites used | 0.067 | 1.307 | 0.191 | 0.004 | –0.001 |
| After the Warning | ||||||
|---|---|---|---|---|---|---|
| Before the Warning | (1) | (2) | (3) | (4) | Platforms No Longer Used | Total |
| (1) Fully paid proprietary subscriptions | 950 | 26 | 12 | 1 | 65 | 1054 |
| (2) Cost-sharing proprietary subscriptions | 50 | 56 | 22 | 1 | 29 | 158 |
| (3) Cost-sharing non-proprietary subscriptions | 13 | 10 | 19 | 4 | 33 | 79 |
| (4) Unpaid non-proprietary subscriptions | 14 | 6 | 5 | 18 | 25 | 68 |
| Total | 1027 | 98 | 58 | 24 | 152 | 1359 |
| Latent Variables | Items | Outer Loadings |
|---|---|---|
| Trait reactance (AVE = 0.531; CR = 0.851) | I become angry when my freedom of choice is restricted | 0.903 |
| I become frustrated when I am unable to make free and independent decisions | 0.569 | |
| I am content only when I am acting on my own free will | 0.616 | |
| I resist the attempts of others to influence me | 0.777 | |
| Perceived fairness (AVE = 0.802; CR = 0.920) | For me, the new user authentication system is inadequate to adequate | 0.889 |
| For me, the new user authentication system is abusive to moderate | 0.898 | |
| For me, the new user authentication system is unjustifiable to justifiable | 0.892 | |
| For me, the new user authentication system is unbearable to bearable | 0.905 |
| Hypothesized Relationships | Path Coeff. | t Values | Sig. | f2 | q2 |
|---|---|---|---|---|---|
| H8: Trait reactance → Perceived fairness | –0.149 | 2.716 | p < 0.01 | 0.023 | 0.015 |
| H9a: Perceived fairness → Change in No. of proprietary subscriptions used | 0.296 | 7.205 | p < 0.001 | 0.096 | 0.003 |
| H9b: Perceived fairness → Change in No. of non-proprietary subscriptions used | –0.141 | 2.957 | p < 0.01 | 0.020 | 0.001 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Redondo, I.; Serrano, D. Authorized and Unauthorized Consumption of SVOD Content: Modeling Determinants of Demand and Measuring Effects of Enforcing Access Control. J. Theor. Appl. Electron. Commer. Res. 2024, 19, 467-485. https://doi.org/10.3390/jtaer19010025
Redondo I, Serrano D. Authorized and Unauthorized Consumption of SVOD Content: Modeling Determinants of Demand and Measuring Effects of Enforcing Access Control. Journal of Theoretical and Applied Electronic Commerce Research. 2024; 19(1):467-485. https://doi.org/10.3390/jtaer19010025
Chicago/Turabian StyleRedondo, Ignacio, and Diana Serrano. 2024. "Authorized and Unauthorized Consumption of SVOD Content: Modeling Determinants of Demand and Measuring Effects of Enforcing Access Control" Journal of Theoretical and Applied Electronic Commerce Research 19, no. 1: 467-485. https://doi.org/10.3390/jtaer19010025
APA StyleRedondo, I., & Serrano, D. (2024). Authorized and Unauthorized Consumption of SVOD Content: Modeling Determinants of Demand and Measuring Effects of Enforcing Access Control. Journal of Theoretical and Applied Electronic Commerce Research, 19(1), 467-485. https://doi.org/10.3390/jtaer19010025







