1. Introduction
In the 6G era [
1], ultra-reliable low-latency communication (URLLC) scenarios impose stringent delay constraints, encompassing applications such as autonomous driving and industrial automation. The principal objective of URLLC, which is to ensure real-time requirements with hard delay constraints, has attracted widespread attention in academia [
2]. It is worth noting that finite blocklength coding with a short-frame structure exhibits an excellent low-latency performance [
3]. Accordingly, this work proposes a variable-length finite blocklength coding scheme to satisfy the hard latency constraint over time-varying wireless channel fading. Meanwhile, we customize the corresponding dynamic framing and power allocation to suit the variable-length channel coding.
Hard delay constraints play a crucial role in URLLC scenarios, as they ensure timely and reliable data delivery [
2]. In light of this, academia has embarked on comprehensive studies of both transmission designs and network structures relevant to hard delay constraints. Most research has primarily targeted transmission designs, such as [
4,
5,
6,
7,
8,
9,
10,
11,
12]. For instance, Ref. [
4] explored network communications under stringent timeliness constraints, demonstrating the superior performance of network coding over routing in delay-constrained unicast settings. The authors of [
5] addressed the challenges of delay-constrained scheduling for point-to-point communications over time-varying channels using a channel-threshold policy. Ref. [
6] ensured adherence to hard delay constraints by exploiting frequency and spatial diversity techniques. The authors of [
7] proposed an optimal power control policy to minimize the probability of violating delay bounds. In [
8], an optimal dynamic coding-window selection policy was proposed for delay-constrained communications. Kumar investigated a framework of hard delay constraints for real-time communication from a queueing perspective in [
9,
10]. The authors of [
11] consider the delay-constrained scheduling problem of point-to-point communication, while the authors of [
12] consider the hard deadline constraints of multichannel systems in a cognitive radio scenario. Subsequent works have investigated many network structures, such as [
13,
14,
15,
16]. For instance, the authors of [
13] explored optimal forwarding for real-time communication over multi-hop wireless lossy networks under strict latency constraints. In [
14], the scheduling of delay constrained transmissions were investigated for coded caching. Ref. [
15] optimized user offloading and resource allocation in a mobile cloud computing system with delay constraints. Likewise, Ref. [
16] focused on maximizing delay-constrained coverage in vehicular networks through optimal base station deployment.
The maximal achievable coding rate of finite blocklength coding was investigated in [
17], which provided significant insights into how low latency requirements can be effectively met using a short frame structure. Consequently, academia has pursued research concerning the maximal achievable coding rate of finite blocklength coding and its applicable network structures. Most of this research has primarily focused on the maximal achievable coding rate, as seen in [
18,
19,
20,
21]. For instance, the authors in [
18] characterized the maximal achievable rate in block fading channels using the channel-side information at the receiver (CSIR). The authors of [
19] investigated the maximal achievable rate over quasi-static multiple-input multiple-output fading channels. Ref. [
20] investigated the finite blocklength limits in multi-antenna AWGN channels, shedding light on channel dispersion and its impact on coding delay and optimal coding schemes. The maximal achievable rate was investigated in parallel complex AWGN channels in [
21]. Subsequent studies have investigated applicable network structures, such as [
3,
22,
23,
24]. The study in [
3] reviewed the advances in information theory related to finite blocklength coding in short-packet transmissions system. The authors in [
22] re-evaluated frame design principles involving finite blocklength coding in cellular wireless systems. In [
23], the scheduling of downlink non-orthogonal multiple access (NOMA) was examined in the context of short-packet communications. The work in [
24] proposed a fast HARQ protocol, substantially improving throughput, delay, and error probability with finite blocklength coding.
Numerous studies have implemented finite blocklength coding in low-latency communication systems. As demonstrated in [
25], there exists a significant disparity between the current channel coding for URLLC and the standard approximation of finite blocklength coding [
26]. Extensive research efforts have examined the design of low-latency transmission using finite blocklength coding in single-user systems. For instance, Ref. [
27] proposed an adaptive blocklength transmission framework and two novel schemes to optimize the end-to-end delay in 6G networks. Refs. [
28,
29] have investigated finite blocklength coding in low-latency transmission systems. The exploration of low-latency transmission design using finite blocklength coding has extended to multiple access systems as well. A multi-access transmission design utilizing finite blocklength coding has been examined in low-latency vehicular communications, rate-splitting multiple access, and Internet of Things systems [
30,
31,
32,
33,
34]. Furthermore, the authors in [
35,
36] have investigated the variable coding policy used in low-latency communications.
The aforementioned work [
4,
5,
6,
7,
8,
13,
14,
15,
16] adopts an common assumption that the transmission power and rate analysis is based on the classical Shannon capacity formula. This assumption is valid only when the channel coding adopts an extremely long blocklength [
17]. Nonetheless, the future 6G system is expected to support a wide range of services for emerging applications, such as autonomous driving and industrial automation, where the blocklength is short and sometimes subject to hard delay and reliability constraints [
3]. This implies that the long codewords required by the Shannon capacity formula may become impractical. Consequently, the previous designs in [
4,
5,
6,
7,
8,
13,
14,
15,
16] are unsuitable for these 6G applications. In the previously mentioned research [
3,
22,
23,
24], although finite blocklength coding is utilized, its application to the scheduling of communications with stringent delay constraints is not considered. While [
25,
26,
27,
28,
29,
30,
31,
32,
33,
34,
35,
36] have investigated the use of finite blocklength coding in low-latency communications, they do not adequately address the enforcement of hard delay constraints. These oversights render the aforementioned studies ill-suited for real-time communication systems.
In our previous work [
37], we focused on optimizing the average delay in short-packet transmission systems. However, in URLLC, we not only consider the average delay but also ensure that all data packets do not exceed a hard delay constraint [
38]. Therefore, in this paper, we delve into hard-delay-constrained communication in short-packet transmission systems, utilizing variable-length coding. In conventional URLLC systems, the focus has primarily been placed on minimizing the average delay or outage probability. However, these studies have not addressed the issues pertaining to hard delay constraints and finite blocklength coding. To this end, we propose a cross-layer design policy tailored to short-packet transmission systems with hard delay constraints. In particular, we encode randomly arriving packets via variable-length coding and transmit the encoded symbols by truncated channel inversion over parallel channels, with the channel-side information at the transmitter (CSIT). Furthermore, we model the data queue and symbol queue as a two-dimensional Markov chain. By adopting the embedded Markov chain and focusing on instances when the symbol queue is empty, we simplify our derived Markov chain into a one-dimensional Markov chain, with the data queue length being the system state. We investigate the analytic expression of average power consumption per slot in the embedded Markov chain. To derive the hard-delay-constrained policy, two heuristic algorithms are proposed. We utilize gradient descent, based on the policies obtained from these heuristic algorithms, to achieve an enhanced hard-delay-constrained policy that effectively strikes a balance between delay constraint and power consumption. Through simulations, we have also verified that our presented policy outperforms the traditional on-demand transmission policy and CSIR policy.
The rest of this paper is organized as follows:
Section 2 illustrates the system model. The finite blocklength coding with a cross-layer approach is investigated in
Section 3. In
Section 4, a heuristic algorithm is proposed to obtain the hard delay constraint policy. Numerical results and concluding remarks are presented in
Section 5 and
Section 6, respectively. The research flow chart of this paper is shown in
Figure 1.
2. System Model
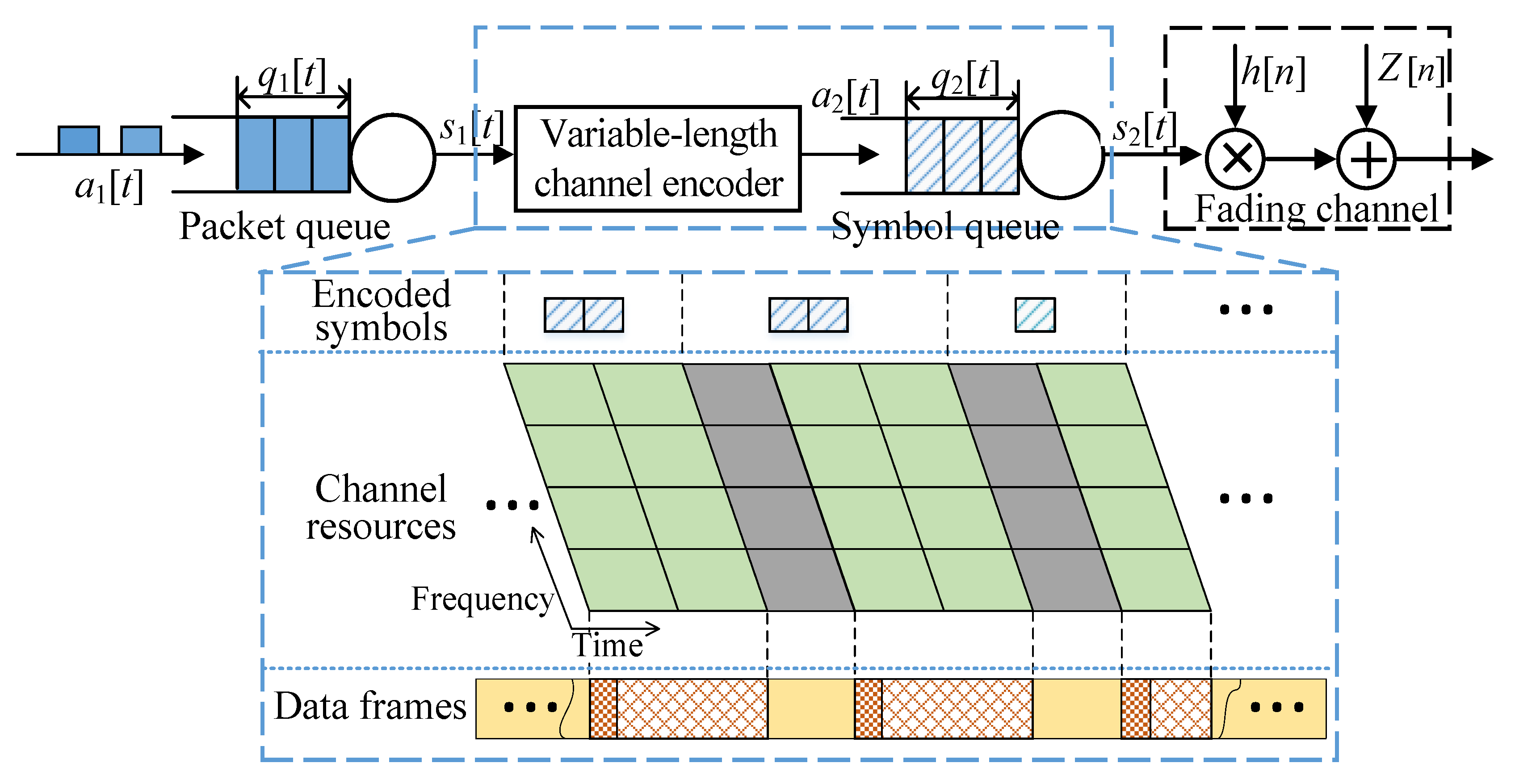
This paper considers a real-time transmission system, such as that depicted in
Figure 2. Specifically, the system is designed to transmit packets via parallel fading channels within a hard delay constraint. Time is discretized into time slots, with each slot spanning a duration of
T seconds. Meanwhile, we suppose that the transmitter has perfect knowledge of the channel state information. This assumption facilitates transmit power adaptation, which partially mitigates the detrimental impact of channel fades.
2.1. Physical Layer of the Channel Model
In the physical layer, we denote the transmitted signal during the
t-th time slot as
, while the corresponding received signal at the receiver is denoted as
. Let
denote the channel coefficient. The relationship between the transmitted and received signals is expressed as
Herein,
denotes an additive white Gaussian noise process with a noise spectral density of
. Meanwhile,
denotes the channel gain.
In practical systems with limited transmit power, the deep fading phenomena inherent to wireless channels pose significant challenges for achieving the low latency and high reliability requirements of URLLC. To address these challenges, we propose the use of parallel channels to ensure more reliable transmission. For the convenience of our theoretical analysis, we adopt a transmission scheme that selects the best among these parallel channels. However, to achieve hard delay constraints, it is necessary to employ parallel channels to enhance reliability.
Let M denote the number of parallel channels, with the channel gain denoted as . We assume that these parallel channels follow an independent and identically distributed () Rayleigh distribution over time. That is, the probability density function () of the channel gain is . Furthermore, the cumulative distribution function () of the channel gain is denoted as .
In the interest of analytical representation, we turn to utilize the maximal channel gain, expressed as
The
corresponding to this maximal channel gain
is given by
Subsequently,
associated with the maximal channel gain
is derived as
It is worth noting that our framework remains accommodating to diverse channel distribution and multiplexing schemes. The emphasis on maximal channel gain is strictly a matter of analytical convenience. The system model we propose is suitable for various wireless communication systems that require meeting hard delay constraints, where factors like interference and mobility can be normalized into the channel gain. Our proposed approach is applicable to different channel models.
2.2. Finite Blocklength Coding in the Physical Layer
In practice, a short frame structure is utilized to achieve ultra-low-latency transmission. Thus, the system is obligated to implement channel coding with a finite blocklength over parallel channels. The coding rate and the blocklength for finite blocklength coding are denoted by
and
, respectively. Given the block error probability
and the received signal to noise ratio
, we know that [
17]
where
is the inverse of the Gaussian Q-function. Adjusting the coding rate is similar to adaptive modulation and coding in information theory. However, in finite blocklength coding, new challenges arise. The coding length is finite, and the codewords generated together need to be transmitted at a constant signal-to-noise ratio.
In the finite blocklength coding regime, maintaining a consistent signal-to-noise ratio across the
symbols that are collectively encoded is critical. Thus, power adaptation should ensure a consistent signal-to-noise ratio
over the
symbols, where
B and
denote the channel bandwidth and the power consumption, respectively. To mitigate the high levels of power consumption caused by poor channel conditions, we considered implementing truncated channel inversion. To ensure a constant signal-to-noise ratio at the receiver, the power consumption at the transmitter is
Our objective is to optimize the threshold of the truncated channel inversion
in order to minimize the average power consumption while achieving a hard delay constraint in the system.
2.3. The Queueing Model in the Network Layer
As shown in
Figure 2, we characterize the packet transmission dynamics in the network layer using a packet queuing model. Queuing effects arise due to the fact that the coding’s blocklength may require multiple time slots for transmission. Consequently, the transmission process is conceptualized as the symbol queue. The packet queue and symbol queue together form a tandem queue.
To begin with, let us introduce the packet queue. Suppose that data packets of size
A bits arrive deterministically at the transmitter in each time slot. We define queue length,
, in terms of the number of packets waiting in the queue. In particular,
evolves as
where
, and
K is the maximum queue length constrained by the buffer size. Moreover,
denotes the service rate in terms of the number of data packets transmitted in time slot
t.
Considering Equation (
5), the achievable channel coding rate in finite blocklength coding increases with the coding blocklength. Consequently, it is more power-efficient to accumulate a sufficient number of packets before the coding process. We propose a greedy framing policy, where all packets in the packet queue undergo finite blocklength coding when the symbol queue is empty. Consequently, the service rate of the packet queue is given by
Subsequently, a detailed introduction to the symbol queue is provided. Throughout the finite blocklength coding process, the data packets transmitted by the packet queue
, each encompassing
A bits, are encoded into
symbols. The relationship between the service rate of the packet queue
and the coding blocklength
is given by
The encoded symbols are buffered in a symbol queue and transmitted over a time-varying fading channel across multiple time slots. The symbol queue’s length
is defined as the number of symbol blocks backlogged in the symbol queue in the
t-th time slot. Each symbol block spans
T s and
B Hz in the time and spectral domains, respectively. Subsequently, the arrival rate of the symbol queue
is defined as the number of symbol blocks that arrive. The service rate of the symbol queue
is defined as the number of symbol blocks transmitted in the
t-th time slot. Consequently, the evolution of the symbol queue
is defined as
During the encoding process, the data packets can be encoded into multiple symbols. The number of symbols that can be transmitted in each time slot is generally multiple and contingent upon the available channel resources. When the system is allocated
T s and
B Hz as its channel resources, we set
. Subsequently, the coding blocklength
can be quantified as the number of symbol blocks
. Then,
is formulated as
The ceiling function has been utilized in Equation (
11) to account for the symbol blocks being discrete units. The use of variable-length coding introduces variability in the transmission time. The constructed symbol queue is designed to indicate the transmission process of symbols. Consequently, communication signalling based on the symbol queue can prompt the receiver to commence decoding.
2.4. The Hard-Delay Constraint
In this real-time transmission system, the delay of data packets in the system consists of two components: the queueing delay of the packet queue and the transmission delay of the symbol queue. The maximum waiting time of a data packet in the system, defined as
W, is given by
where
and
represent the maximum queueing delay in the packet queue and the maximum transmission delay in the symbol queue, respectively. To satisfy the hard delay constraint, it is necessary to limit the waiting time of data packets within the system. This indicates that the waiting time of the data packets in both the packet queue and the symbol queue should be limited. In the following, we separately consider the maximum waiting time of the data packets in these two queues.
In light of Equation (
7), the hard delay constraint in the packet queue is characterized by an integer
K. Notably,
K represents the maximal number of time slots that a packet is allowed to be backlogged in the packet queue, with
. The nature of the deterministic packet arrival process leads us to the fact that if
, it indicates that the earliest
packets have been in the queue for more than
K time slots. Consequently, these initial
packets violate the hard delay constraint and should be dropped. In real-time communication systems, it is necessary to design policies to ensure that all data packets are transmitted within their designated time limits to achieve a packet loss rate of zero.
The delay-violation probability is defined as the proportion of data packets that violate the hard delay constraint. We use
to denote the delay-violation probability, which is given by
As long as the packet queue does not exceed the maximum queue length, the symbol queue will necessarily have the maximum length, according to Equations (
8)–(
10). Therefore, as long as the overflow of the packet queue is constrained, this tandem queuing system will not experience overflow. Then, we do not need to incorporate the symbol dropping mechanism. Therefore, the condition
implies that all packets obey the hard delay constraint.
For the symbol queue, it is also necessary to restrict the maximum waiting time of the symbol blocks. In the next section, we will provide a detailed explanation of how to limit the maximum waiting time in the symbol queue using embedded Markov chains.
Our aim is to obtain a variable-length coding policy that minimizes the transmission power while ensuring the hard delay constraint. The explicit design of our variable-length coding policy is addressed in the next section.
3. Cross-Layer Design for Finite Blocklength Coding
In this section, we generate a variable-length coding policy to satisfy the hard delay constraint. In particular, we consider implementing truncated channel inversion to determine the service rate. Based on this, we prove that the hard delay constraint can be satisfied with finite average power. Then, we formulate the system as an embedded Markov chain. Based on this, we consider the packet queue length as the only system state, while the evolution of the symbol queue length is embedded into the transition probabilities. Moreover, we demonstrate that the variable-length coding policy is capable of achieving this hard delay constraint by guaranteeing a limitation on both the maximum queuing delay and transmission delay.
3.1. Achieving the Hard Delay Constraint with Finite Average Power
We use
to denote the number of symbol blocks corresponding to
data packets. Subsequently, we have
under conditions where
and
. Let
k and
l represent the number of time slots and the number of symbol blocks that have been successfully transmitted after a finite blocklength coding process, respectively. Then, we have
Considering that the transmission in a deep fading channel requires infinite power, we should suspend symbol transmission during deep fading to save power, particularly when the remaining number of symbol blocks is less than the number of the remaining time slots. To satisfy the hard delay constraint, it is necessary to transmit the symbol block when the remaining number of symbol blocks is equal to the remaining number of time slots, regardless of the channel quality. As such, the service rate of the symbol queue is given by
In each time slot, the threshold of the truncated channel inversion is intrinsically related to three parameters:
, defined as the number of data packets concurrently encoded;
k; and
l. For a more concise expression, we abbreviate
to
.
Let
denote the fixed receiver power. The average power for
in a single time slot is defined as
The average power consumption of the system is given by
Based on Equations (
4) and (
17), the average power for
in a single time slot is defined as
We assume
in this equation without a loss of generality. To facilitate the computation of Equation (
19), we propose the following two lemmas.
Lemma 1. The integral expression satisfieswhere we have Proof. Firstly, we consider the following integral expression:
Secondly, we prove the convergence of Equation (
22) by considering two cases, i.e.,
and
. For the case when
,
which proves there is convergence. When
, we have
Therefore, the lemma is proved. ☐
Lemma 2. The following equality holds, i.e.,Here, is an arbitrary function of i. Proof. In this proof, we consider the following expression, which is equivalent to Equation (
25):
Therefore, the lemma is proved. ☐
Theorem 1. The average power across the optimal subchannel of parallel fading channels is expressed asRemarkably, even when . Proof. Initially, we employ integration by parts to reshape the integral subject. Following this, the higher-order polynomial is expanded through the implementation of the binomial theorem, thereby facilitating its integration. Subsequently, Lemma 1 is invoked to substitute the associated integral expression. The ensuing expression post-integration is simplified utilizing Lemma 2. Finally, we utilize Lemma 1 to prove the convergence of Theorem 1.
Leveraging Equation (
19), the average power over the optimal subchannel of parallel fading channels is expressed as
Next, we employ Lemma 2, where we define
In this way, we have
According to Lemma 1, we prove the convergence of Equation (
30). At this point, the theorem is proved. ☐
By using Lemmas 1 and 2, the average power consumption is given in Theorem 1, which demonstrates that the average power consumption of a parallel fading channel is finite. Then, using Theorem 1, we show that the system can meet the hard delay constraint with finite power consumption with a Markov chain.
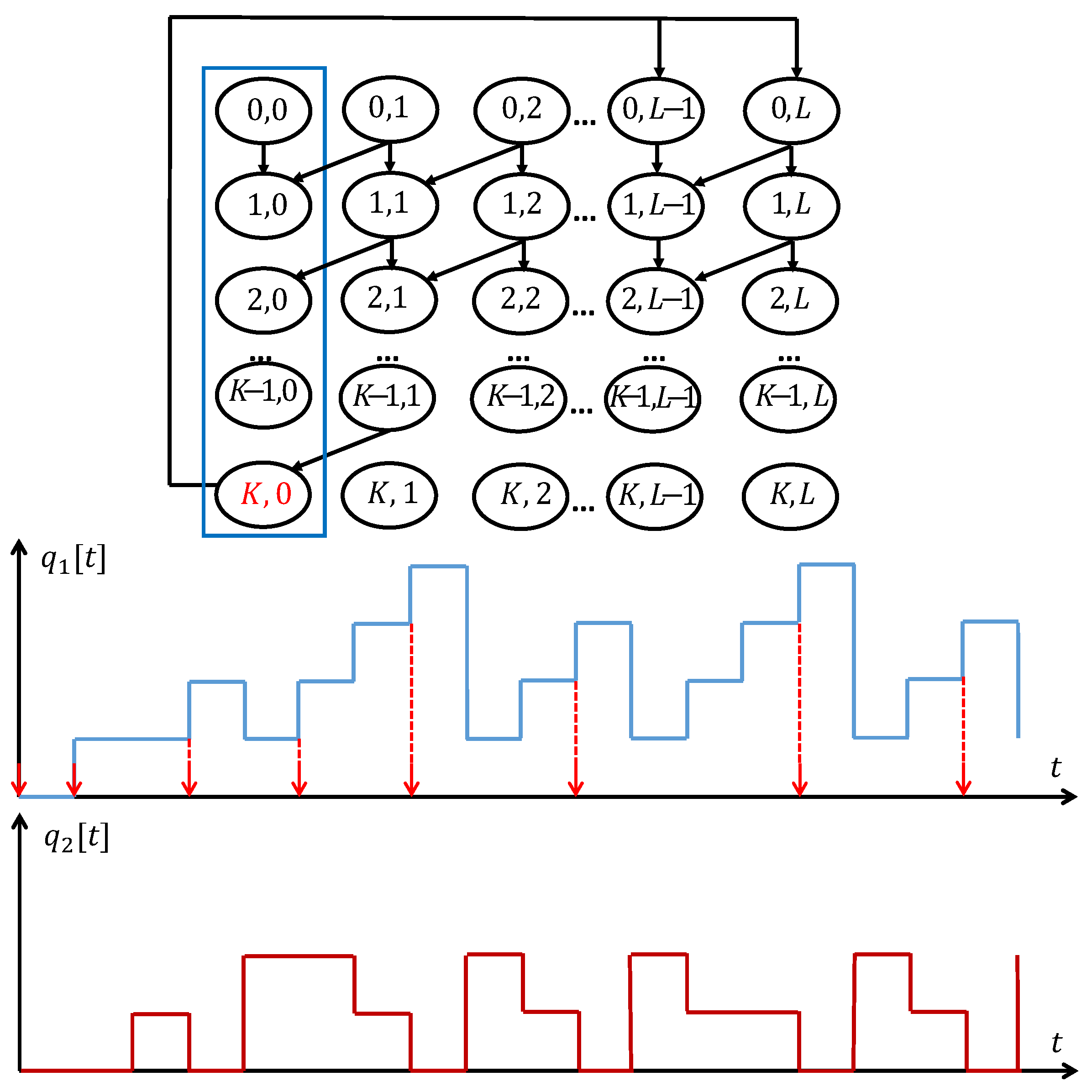
3.2. Embedded Markov Chain Model
In this finite blocklength coding system, we model the packet and symbol queues as a two-dimensional Markov chain, denoting the system state as
. The transition probability of the two-dimensional Markov chain is derived from Equations (
7) and (
10). Fortunately, we observe that the evolution of the symbol queue, i.e., the transmission process of encoded symbols, is determined by the packet queue length, i.e.,
, when a new variable-length encoding process starts. Consequently, the two-dimensional Markov chain is transformed into an embedded Markov chain. In this embedded Markov chain, the packet queue length at the beginning of an encoding process becomes the sole system state, with the transmission process of encoded symbols embedded into the transition probabilities. In our previous work [
37], we utilized a two-dimensional Markov chain as it was necessary to calculate the average delay of the system. However, in a system with a hard delay constraint, we only need to ensure that the maximum delay does not exceed the threshold. Therefore, we utilized a one-dimensional embedded Markov chain.
To facilitate understanding,
Figure 3 illustrates the process of the embedded Markov chain. From a global perspective, incorporating all time slots, the system operates in a two-dimensional paradigm, constituted by the packet queue and the symbol queue. In
Figure 3, the blue line represents the change in the packet queue, while the red line represents the change in the symbol queue. However, our focus is selectively directed towards time slots where the symbol queue is empty, as indicated by the red arrow. Then, we treat the packet queue as an embedded Markov chain. With the derived one-dimensional Markov chain, we can significantly reduce the complexity for the steady-state analysis and system performance optimization.
Theorem 2. The packet queue having a maximum queue length and a delay-violation probability is a necessary and sufficient condition for satisfying the hard delay constraint in the system, defined as .
Proof. Firstly, we demonstrate the sufficiency of the theorem. The given maximum length K of the packet queue and the delay-violation probability ensure that data packets can wait for at most K time slots in the packet queue. Additionally, the condition in the packet queue guarantees the transmission of symbols in the symbol queue within the specified delay constraint. Consequently, the hard delay constraint is satisfied, affirming the sufficiency of the theorem.
Subsequently, we establish the necessity of this through a proof by contradiction. To derive a contradiction, let us assume that the transmission of the symbol queue requires time slots while adhering to the hard delay constraint D. In this scenario, the accumulation of data packets in the packet queue surpasses the prescribed maximum length K, resulting in packet loss and a violation of the hard delay constraint. This contradiction highlights the necessity of the theorem. Therefore, the theorem is proved. ☐
Given the policy
, we have
. The steady-state distribution of this Markov chain is denoted as
, which is expressed as
To ensure the normalization condition, the following equation holds:
where
signifies the steady-state probability distribution of the embedded Markov chain and
represents a
-dimensional vector with all entries equal to one. Subsequently, we will derive the balance equation.
Lemma 3. At the beginning of the k-th time slot, the probability distribution of the number of symbol blocks already transmitted, denoted by l, which are coded by ζ packets, is expressed aswhere we haveAdditionally, is defined as the set that contains all vectors obtained by selecting l positions in a k-dimensional all-zero vector and setting them to 1. Proof. This proof is conducted through induction on k. The primary approach involves deriving the probability distribution for each time slot sequentially, followed by mathematical induction to establish a general expression.
We define
as the transmission probability in the
k-th time slot, which represents the probability of successfully transmitting
l symbols before the
k-th time slot. These symbols are encoded from a set of
data packets. The transmission probability is given by
We now proceed by induction. In the first time slot, we have
In the second time slot, we have
In the third time slot, we have
We define
as the set that contains all vectors obtained by selecting
l positions in a
k-dimensional all-zero vector and setting them to 1, assuming the following equation holds for
:
Based on Equation (
42), we can derive the following expression
At this point, the mathematical induction proof is complete. As such, this lemma is proved. ☐
Theorem 3. The transition probability is defined asThen, the transition probability is calculated as Proof. In a finite blocklength coding system, data packets are encoded into symbol blocks. The probability of having transmitted symbol blocks within time slots is expressed as . The probability of transmitting the last symbol block in the -th time slot is expressed as . By multiplying these two probabilities, the lemma is then proven. ☐
Based on the transition probability presented in Theorem 3, we can derive the corresponding balance equation for the packet queue state
. Thus, we obtain
where
represents the transition matrix.
Our objective is to minimize the average power consumption of the system while adhering to hard delay constraints. To achieve this, we introduce the following theorem, which derives the average power consumption from the perspective of an embedded Markov chain.
Theorem 4. The average power in the finite blocklength coding system is Proof. The average power consumption on the embedded Markov chain is given by
The average number of packets that appear on the embedded Markov chain is expressed as
In this finite blocklength coding system, there is one packet per time slot. Consequently, the average power consumption per packet is equal to the average power consumption per time slot. Through the division of the average power consumption across the embedded Markov chain by the corresponding average number of packets in this chain, we derive the average power consumption per time slot. ☐
In this section, we demonstrated the feasibility of achieving hard delay constraints with limited power. The embedded Markov chain is utilized to ensure the hard delay constraints are met. Furthermore, we also present the average power consumption.
5. Simulation Results
This section presents both theoretical and simulation results to validate our theoretical analysis and emphasize the effectiveness of the proposed policy for hard-delay-constrained communication. We examine a practical scenario in URLLC that leverages finite blocklength coding. For this scenario, we set the packet size to bits, the block error probability to , the power consumption per symbol to W, the channel bandwidth to Hz, the coherence time to s, and the noise spectral density of the Gaussian noise process to dBm.
Figure 4 illustrates the changes in average power consumption corresponding to the changes in the hard delay constraints. The red line represents the policy of Algorithm 1, which integrates both heuristic algorithms and gradient descent. The blue line corresponds to the first heuristic algorithm, while the pink line depicts the second heuristic algorithm. The black line signifies the maximum coding blocklength policy, which selectively initiates transmissions that are in proximity to the hard delay constraint, thereby maximizing the coding blocklength. The on-demand transmission policy, with a channel threshold set to zero, is denoted by the grey line. Both the heuristic algorithms and the maximum coding blocklength policy display non-smooth characteristics owing to inaccuracies in symbol block quantization. Notably, Algorithm 1 exhibits the best performance, substantiating the superiority of our proposed policy over baseline policies. Additionally, the excellent match between the theoretical and simulation results in the figure is noteworthy. It is important to highlight that as the hard delay constraint increases gradually, the average power consumption decreases. This is attributed to a larger hard delay constraint providing more flexibility in selecting transmission opportunities, allowing for the identification of time slots with superior channel quality for transmission and consequently leading to reduced power consumption.
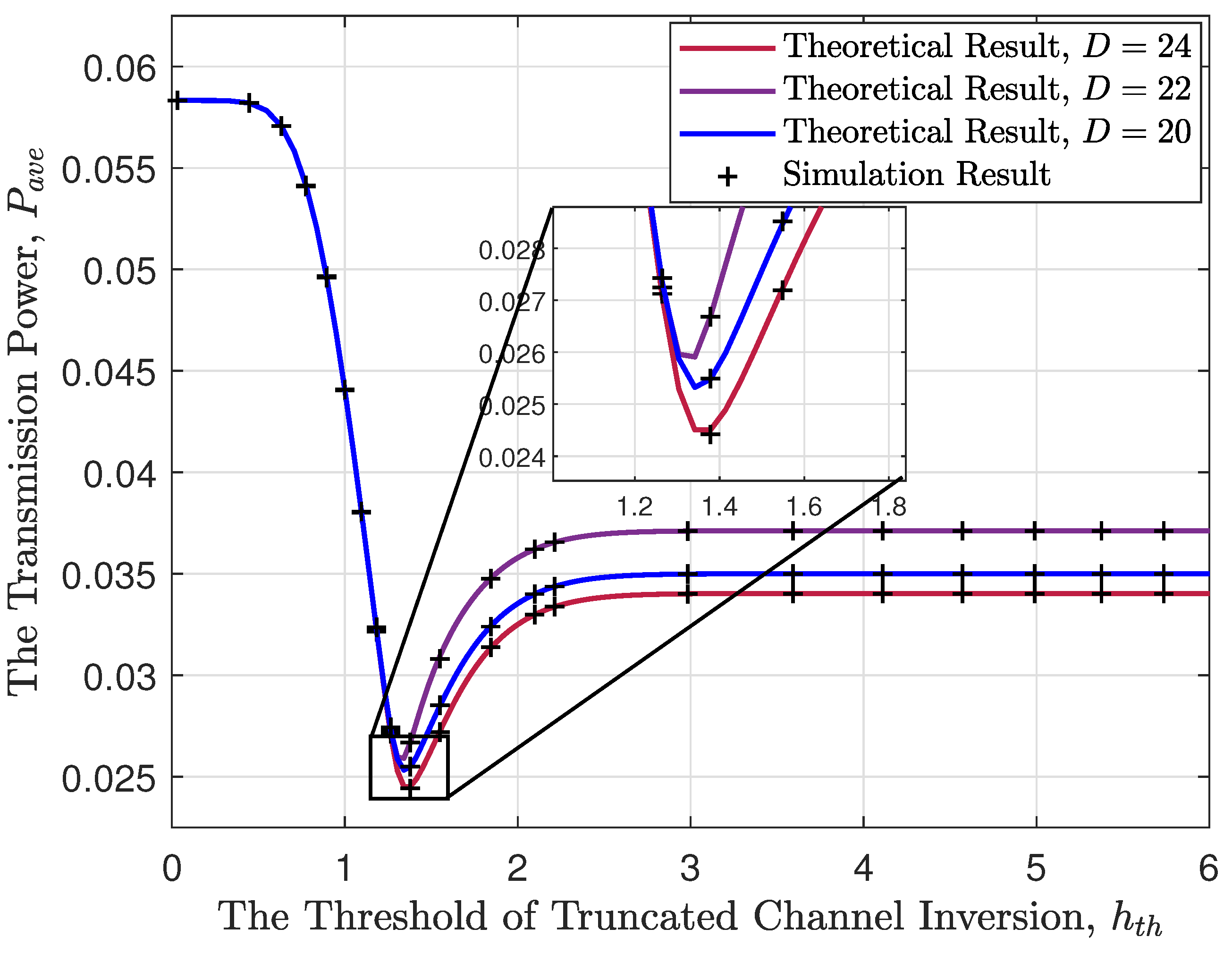
Figure 5 delineates the power consumption trend, using the first heuristic algorithm as the channel gain varies. We observe that as the channel gain threshold increases, the average power consumption first decreases and then increases. The declining trend arises as an increasing channel gain threshold in poor-quality channels allows for the avoidance of transmission, consequently saving power. However, as the channel gain threshold increases, the symbol block is eventually forced to transmit through any channel when reaching the upper limit of the hard delay constraint, disregarding channel quality. It is noteworthy that power consumption at a channel threshold of zero is higher than when the channel threshold is extremely high. A channel threshold equal to zero implies immediate transmission once symbols are encoded, resulting in a shorter coding blocklength. On the contrary, a high channel threshold demands waiting, potentially until the upper limit imposed by the hard delay constraint, before initiating transmission. In such cases, the coding blocklength is longer. Therefore, based on Equation (
5), the power consumption at a zero channel threshold is higher than that at an extremely high channel threshold.
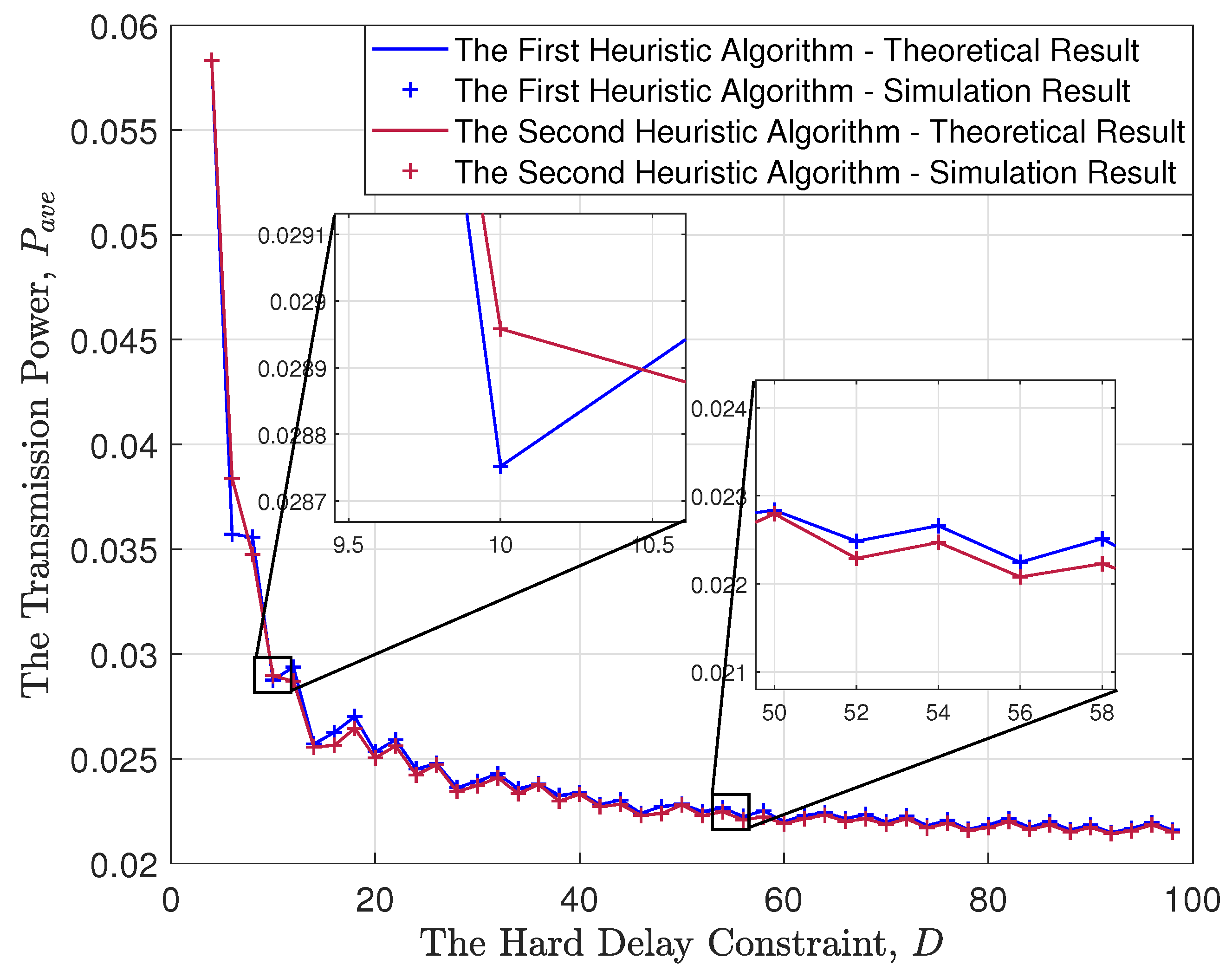
Figure 6 illustrates the performance of two heuristic algorithms as the upper limit of the hard delay constraint varies. With an increase in the hard delay constraint, the number of system states also increases, thereby slowing down the convergence of the gradient descent method. Thus, only the results of the heuristic algorithms are displayed. As observed, when the upper limit of the hard delay constraint increases, the average power consumption decreases. This phenomenon can be explained from two perspectives. Firstly, a higher hard delay constraint provides more time slots for transmission, enabling the selection of better-quality channels and, consequently, reducing power consumption. Secondly, with a high hard delay constraint, more data packets can be accumulated for transmission, resulting in a longer coding blocklength, further contributing to the reduction in power consumption.
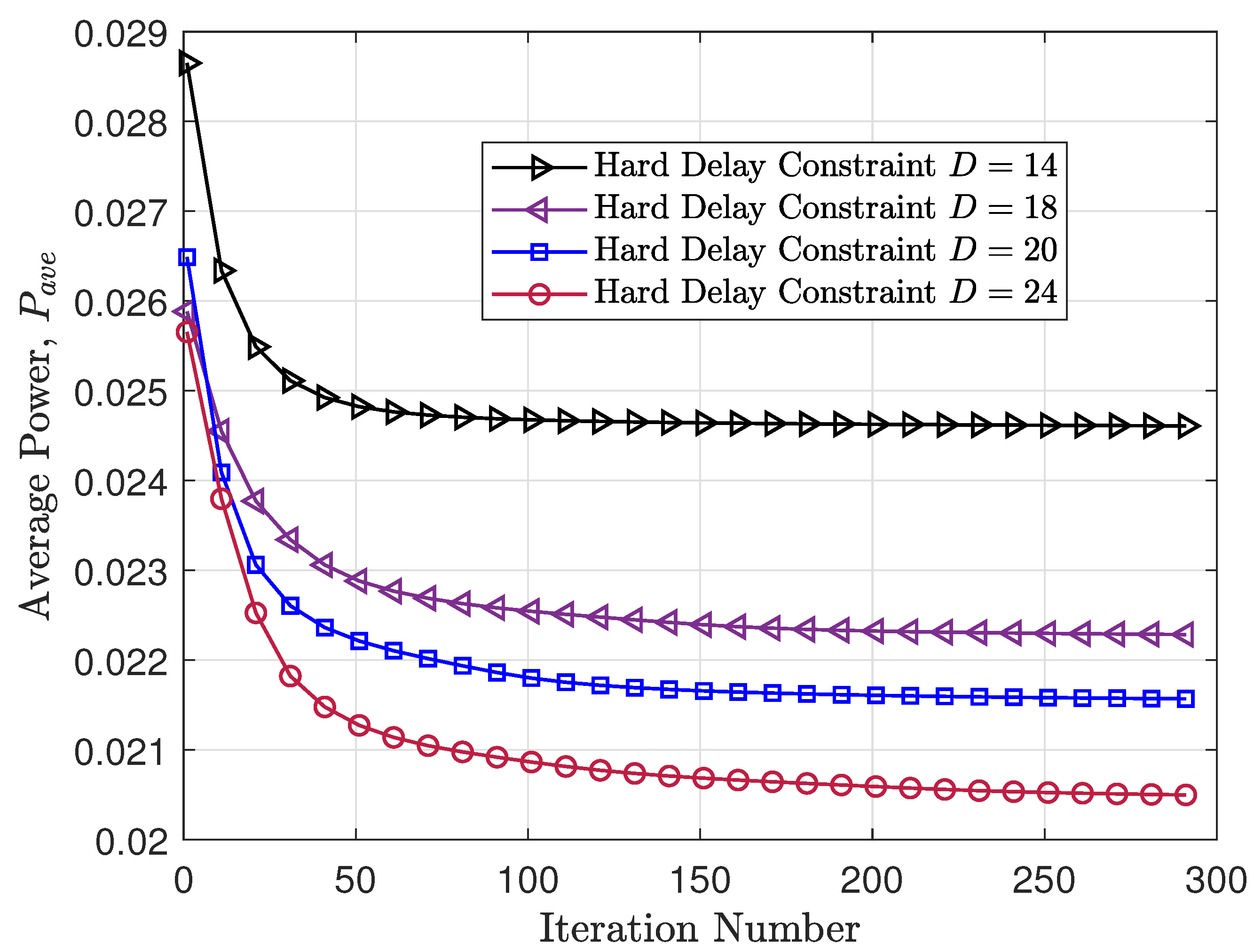
Figure 7 depicts the change in average power consumption as a function of the iteration number of the gradient descent policy. As the iteration number increases, a deceleration in descent speed is observed, pointing to an eventual convergence. Notably, the rate of convergence of the gradient descent policy slows down with increases in the hard delay constraint. This slowdown can be attributed to the scale of the Markov chain states and the scale of the channel truncation threshold parameters. The increased number of parameters leads to a slower convergence rate. Consistent with the observations in
Figure 4,
Figure 7 also illustrates a gradual decrease in average power consumption with an increase in the hard delay constraint.
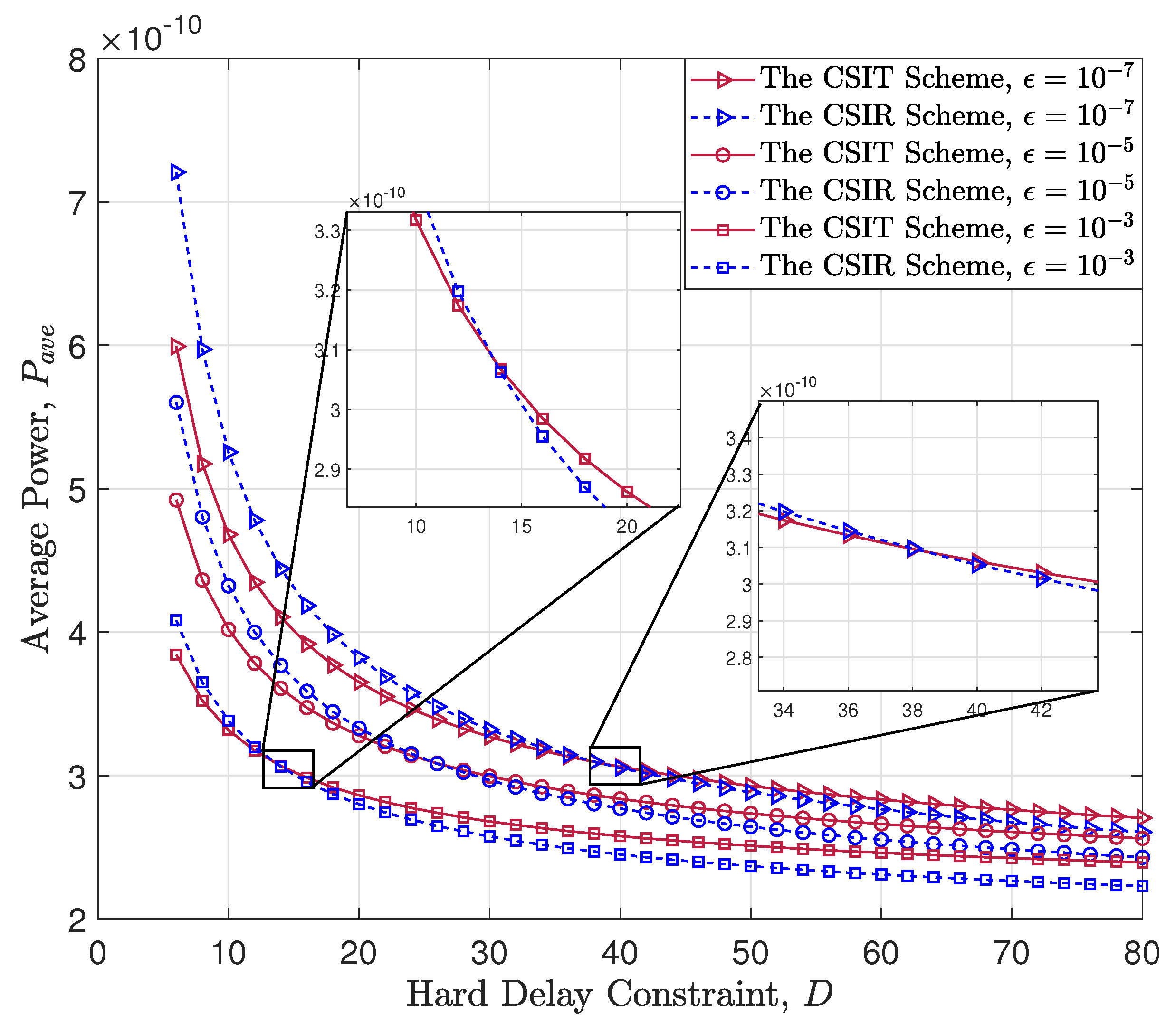
Figure 8 illustrates the comparison of our presented scheme with the CSIT and the CSIR scheme in [
18]. To clearly demonstrate the comparison between the two policies, we modified some simulation parameters. Here, we set the packet size to
bits, the channel bandwidth to
Hz, and the coherence time to
s. Additionally, we showcase the performance of the CSIT scheme and the CSIR scheme under different block error probabilities. It is worth noting that in the CSIR scheme, channel inversion truncation is not required. Therefore, in this simulation, we set the maximum queue length equal to the maximum coding blocklength. In
Figure 8, we observe that our presented CSIT scheme performs better when the hard delay constraint is relatively small. For instance, when the block error probability
and the hard delay constraint
, our presented CSIT scheme outperforms the CSIR scheme. Similarly, when the block error probability
and the hard delay constraint
, our presented CSIT scheme outperforms the CSIR scheme. Therefore, we find that as the block error probability decreases, the advantage interval of our presented CSIT scheme increases.