Transnational Cyber Governance for Risk Management in the Gas Sector: Exploring the Potential of G7 Cooperation
Abstract
1. Introduction
2. Ghost in the Pipeline: Natural Gas Security Dynamics, Energy-Cyber Power Balances, and Cyberthreats
3. The Path to Transnational Governance: An Institutional Analysis Design Approach
3.1. Institutional Analysis Design
3.2. Data
4. Assessing National Capabilities for Cyber Risk Management
4.1. Cyber Risk Management
- Develop cyber security processes: the organisation should develop cyber capabilities to identify, protect, detect, respond, and recover;
- Education and training staff for cyber security for risk analysis and risk evaluation;
- Upgrade and maintain a system to mitigate cyber risk;
- Create a cyber security culture to raise awareness and encourage proactive behaviour;
- Draft resilience by design through sectoral methodologies and system approaches for interconnected critical energy infrastructures [77].
4.2. National Cyber Governance Capabilities2
4.3. The Partnership Approach to Risk Management
5. A Cyber Governance Alliance? Navigating CEI Interdependence and G7 Cyber Governance
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
| 1 | For the principles of UN Charter and Cyber Operations see UNGA (2013), Group of Governmental Experts on Developments in the Field of Information and Telecommunications in the Context of International Security, 24 June 2013, UN Doc A/68/98, paras 19–20; UNGA (2015), Report of the Group of Government Experts on Developments in the Field of Information and Telecommunications in the Context of International Security, A/70/174, 22 July 2015, para 28(b). The 2015 UN GGE also agreed 11 voluntary and non-binding norms, rules, and principles of responsible state behaviour in the ICT environment. UN Doc A/68/98, paras 19–20; UNGA (2015), Report of the Group of Government Experts on Developments in the Field of Information and Telecommunications in the Context of International Security, A/70/174, 22 July 2015, para 28(b). The 2015 UN GGE also agreed 11 voluntary and non-binding norms, rules and principles of responsible state behaviour in the ICT environment. |
| 2 | For study purposes, the overview of national cyber capabilities in this section is based on the Cyber Capabilities and National Power: Net Assessment [76]. |
| 3 | For more on the Canadian strategy to protect Critical Infrastructures. URL: https://www.securitepublique.gc.ca/cnt/trnsprnc/brfng-mtrls/prlmntry-bndrs/20240614/19-en.aspx (accessed on 28 June 2024). |
References
- Williams, P.; Molnar, N.; Springer, G. Northeast Ohio Impact of Global Tech Outage Extends to Utilities, Hospitals, Government. 2024. Available online: https://eu.beaconjournal.com/story/news/local/2024/07/19/crowdstrike-outage-imacts-some-akron-services/74467780007/ (accessed on 21 July 2024).
- IBM. X-Force Threat Intelligence Index 2024; IBM: Armonk, NY, USA, 2024. [Google Scholar]
- Greig, J. G7 Countries Vow to Establish Collective Cybersecurity Framework for Operational Tech. 2024. Available online: https://therecord.media/countries-vow-to-establish-cyber-collective (accessed on 8 July 2024).
- Rosenzweig, P. International Governance Framework for Cybersecurity. Can.-United States Law J. 2012, 37, 405–432. [Google Scholar]
- Lee, I. Cybersecurity: Risk management framework and investment cost analysis. Busines Horiz. 2021, 64, 659–671. [Google Scholar] [CrossRef]
- Mizrak, F. Integrating Cybersecurity Risk Management into Strategic Management: A Comprehensive Literature Review. Res. J. Bus. Manag. 2023, 10, 98–108. [Google Scholar] [CrossRef]
- KPMG. Top Risks 2023: The Bottom Line for Business. 2023. Available online: https://assets.kpmg.com/content/dam/kpmg/xx/pdf/2023/02/top-risks-thought-leadership.pdf (accessed on 25 July 2024).
- Alcamo, I. The Energy Security Dynamics Around the Israel-Hamas War and Their Implications for the Future of the Gaza Marine Gas Field. 2024. Available online: https://iari.site/2024/06/11/the-energy-security-dynamics-around-the-israel-hamas-war-and-their-implications-for-the-future-of-the-gaza-marine-gas-field/ (accessed on 18 June 2024).
- Sabin, S. Hackers Make Their Mark in Israel-Hamas Conflict. 2023. Available online: https://www.axios.com/2023/10/10/hackers-ddos-israel-hamas-conflict (accessed on 4 June 2024).
- Bouhdada, J. Digital Transformation: Building Cyber Resilience in the Oil and Gas Industry. 2023. Available online: https://www.worldoil.com/magazine/2023/december-2023/features/digital-transformation-building-cyber-resilience-in-the-oil-and-gas-industry/ (accessed on 8 July 2024).
- Council on Foreign Relations. What Does the G7 Do? 2024. Available online: https://www.cfr.org/backgrounder/what-does-g7-do#chapter-title-0-6 (accessed on 18 July 2024).
- Pastukhova, M. Over-Reliance on Gas Delays G7 Transition to Net-Zero Power. 2024. Available online: https://www.politico.eu/sponsored-content/over-reliance-on-gas-delays-g7-transition-to-net-zero-power/ (accessed on 8 July 2024).
- Observatory of Economic Complexity. Natural Gas Liquified-Latest Trends. 2023. Available online: https://oec.world/en/profile/bilateral-product/natural-gas-liquefied/reporter/are/ (accessed on 8 July 2024).
- U.S. Energy Information Administration. Japan’s Energy Overview. 2023. Available online: https://www.eia.gov/international/content/analysis/countries_long/Japan/#:~:text=Because%20it%20has%20no%20international,crude%20oil%20to%20meet%20demand.&text=Japan%20was%20the%20world’s%20fifth%2Dhighest%20energy%20consumer%20in%202021 (accessed on 8 July 2024).
- Wolff, G.; Gritz, A. Gas and energy security in Germany and central and Eastern Europe. 2023. Available online: https://dgap.org/en/research/publications/gas-and-energy-security-germany-and-central-and-eastern-europe-0 (accessed on 9 July 2024).
- Waldholz, R.; Wehrmann, B.; Wettengel, J. Ukraine War Pushes Germany to Build LNG Terminals. 2023. Available online: https://www.cleanenergywire.org/factsheets/liquefied-gas-does-lng-have-place-germanys-energy-future (accessed on 9 July 2024).
- Onyango, D. EastMed Pipeline Remains on EU’s New List of Common Interest Projects. 2023. Available online: https://www.pipeline-journal.net/news/eastmed-pipeline-remains-eus-new-list-common-interest-projects (accessed on 2 July 2024).
- Mikkelsen, D. Oil and Gas-How the EastMed Pipeline Strengthens European Energy Security. 2023. Available online: https://www.oilandgasmiddleeast.com/business/insights/how-the-eastmed-pipeline-strengthens-european-energy-security (accessed on 1 July 2024).
- Hamre, J.J.; Cha, V.; Benson, E.; Bergmann, M.; Murphy, E.L.; Welsh, C. “Bending the Architecture”—Reimagining the G7. 2024. Available online: https://www.csis.org/analysis/bending-architecture-reimagining-g7 (accessed on 2 July 2024).
- Corriere della Sera. Missione Sicurezza. 2019. Available online: https://specialistudio.corriere.it/leonardo-si1/cyber-security-chieti/ (accessed on 3 December 2022).
- Leonardo. Training. 2022. Available online: https://www.leonardo.com/en/news-and-stories-detail/-/detail/leonardo-ecosystem-sole24ore (accessed on 9 November 2022).
- Voo, J.; Hemani, I.; Cassidy, D. National Cyber Power Index 2022; Belfer Center: Cambridge, MA, USA, 2022. [Google Scholar]
- Lowy Institute. Asia Power Index 2023-Cybercapabilities. 2023. Available online: https://power.lowyinstitute.org/data/military-capability/signature-capabilities/cyber-capabilities/ (accessed on 8 July 2024).
- Haan, K.; Aditham, K. What Is The Five Eyes Alliance? Forbes, 4 June 2024. Available online: https://www.forbes.com/advisor/business/what-is-five-eyes/ (accessed on 25 July 2024).
- Antoniuk, D. Germany to Launch Cyber Military Branch to Combat Russian Threats. 2024. Available online: https://therecord.media/germany-to-launch-cyber-military-unit-russia (accessed on 8 July 2024).
- Zan, T.D.; Giacomello, G.; Martino, L. Italy’s Cybersecurity Architecture and Critical Infrastructure. In Routledge Companion to Global Cyber-Security Strategy; Manjikian, M., Ed.; Routledge: London, UK, 2021; pp. 121–131. [Google Scholar]
- DeCode39. First G7 Cyber Group Agrees on Info-Sharing to Defend Democracies. 2024. Available online: https://decode39.com/9058/first-g7-cyber-group-agrees-on-info-sharing-to-defend-democracies/ (accessed on 1 July 2024).
- Feld, S.D.L. Germany, Austria, Italy to Develop the Southern Hydrogen Corridor. Simson: “Key project for decarbonization”. 2024. Available online: https://www.eunews.it/en/2024/05/30/germany-austria-italy-to-develop-the-southern-hydrogen-corridor-simson-key-project-for-decarbonization/ (accessed on 12 June 2024).
- Weatherby, C. EastWestCenter-Next Steps for US-Japan Collaboration on Energy Infrastructure. 2020. Available online: https://www.eastwestcenter.org/sites/default/files/private/ewc_api-n145_final.pdf (accessed on 12 June 2024).
- Raszewski, S. When One Door Closes, Another Opens: How the Failure of the Turkey—Austria Natural Gas Pipeline Project Has Led to Recovery, Resilience and Scalability of Successor Projects. Energy Policy 2022, 167, 112978. [Google Scholar] [CrossRef]
- Aalto, P.; Temel, D.K. European Energy Security: Natural Gas and the Integration Process. J. Common Mark. Stud. 2014, 52, 758–774. [Google Scholar] [CrossRef]
- Sassi, F. LinkedIN-Francesco Sassi’s Post. 2024. Available online: https://www.linkedin.com/posts/sassi-francesco_norway-france-are-planning-a-major-activity-7217120596197842945-I2I5?utm_source=share&utm_medium=member_ios (accessed on 14 July 2024).
- Lafrance, C.; Wehrmann, B. EnergyPost.Eu-Russia’s War Has Exposed France and Germany’s Energy Policy Differences. Can It Also Bring Them Together? 2023. Available online: https://energypost.eu/russias-war-has-exposed-france-and-germanys-energy-policy-differences-can-it-also-bring-them-together/ (accessed on 10 June 2024).
- Zhou, C.; Zhu, B.; Halff, A.; Davis, S.J.; Liu, Z.; Bowring, S.; Arous, S.B.; Ciais, P. Europe’s Adaptation to the Energy Crisis: Reshaped Gas Supply; Transmission-Consumption Structures and Driving Factors from 2022 to 2024. 2024. Available online: https://essd.copernicus.org/preprints/essd-2024-173/essd-2024-173.pdf (accessed on 16 July 2024).
- International Energy Agency. World Energy Investment 2024. 2024. Available online: https://iea.blob.core.windows.net/assets/60fcd1dd-d112-469b-87de-20d39227df3d/WorldEnergyInvestment2024.pdf (accessed on 9 July 2024).
- Energy Security Sentinel. An Interactive Study of Geopolitical Risk and Energy Prices. 2024. Available online: https://storymaps.arcgis.com/stories/6e44901bfd7e421ca06cacc7c6e9ea1d (accessed on 4 June 2024).
- European Commission. Eighth Report on the State of the Energy Union. 2024. Available online: https://energy.ec.europa.eu/topics/energy-strategy/energy-union/eighth-report-state-energy-union_en# (accessed on 4 June 2024).
- Bowden, M. The Atlantic ‘The Most Consequential Act of Sabotage in Modern Times: The Destruction of the Nord Stream Pipeline Curtailed Europe’s Reliance on Russian Gas. But Who Was Responsible? 2023. Available online: https://www.theatlantic.com/international/archive/2023/12/nord-stream-pipeline-attack-theories-suspects-investigation/676320/ (accessed on 25 July 2024).
- Hecking, H.; Schulte, S.; Vatansever, A.; Raszewski, S. Options for Gas Supply Diversification for the EU and Germany in the Next Two Decades, Cologne; EWI-EUCRS: London, UK, 2016. [Google Scholar]
- Sassi, F. Stop ai Nuovi Terminal di Gnl Negli Usa: Quali Implicazioni per la Sicurezza Energetica Europea, Rome: Il Senato. 2024. Available online: https://www.researchgate.net/publication/382762146_Stop_ai_nuovi_terminal_di_gnl_negli_Usa_quali_implicazioni_per_la_sicurezza_energetica_europea (accessed on 24 July 2024).
- Münchmeyer, M.; Raimondi, P.P. Between Security and Transition: Prospects for German-Italian Energy Cooperation. IAI Comment. 2023, 23–66, 1–7. [Google Scholar]
- LaBelle, M.C. Breaking the era of energy interdependence in Europe: A multidimensional reframing of energy security, sovereignty, and solidarity. Energy Strategy Rev. 2024, 52, 101314. [Google Scholar] [CrossRef]
- Jensen, E.T. Cyber Attacks: Proportionality and Precautions in Attack. Int. Law Stud. 2013, 89, 198–2017. [Google Scholar] [CrossRef][Green Version]
- Franzese, P.W. Sovereignty in Cyberspace: Can It Exist? 2009. Available online: https://go.gale.com/ps/i.do?id=GALE%7CA212035708&sid=googleScholar&v=2.1&it=r&linkaccess=abs&issn=00948381&p=AONE&sw=w&userGroupName=anon%7Ed5434b46&aty=open-web-entry (accessed on 18 June 2024).
- Nyman, M. Cyber Attacks as Armed Attacks? The Right of Self-Defence When a Cyber Attack Occurs. 2022. Available online: https://www.diva-portal.org/smash/get/diva2:1751329/FULLTEXT01.pdf (accessed on 18 June 2024).
- Oorspronga, F.; Ducheine, P.; Pijpers, P. Cyber-attacks and the right of self-defense: A case study of the Netherlands. Policy Des. Pract. 2023, 6, 217–239. [Google Scholar] [CrossRef]
- Baezner, M.; Robin, P. Cyber Sovereignty; ETHZürich: Zürich, Switzerland, 2018. [Google Scholar]
- Davis, D. 5 Big Cyberattacks in Oil and Gas. 2022. Available online: https://www.oilandgasiq.com/digital-transformation/articles/5-big-cyber-security-attacks-in-oil-and-gas (accessed on 2 July 2024).
- Caversan, F. Mind the Gap: Bridging the Gap Between Information Technology and Operational Technology. 2024. Available online: https://www.forbes.com/sites/forbestechcouncil/2024/02/23/mind-the-gap-bridging-the-gap-between-information-technology-and-operational-technology/ (accessed on 5 June 2024).
- CISA. The Attack on Colonial Pipeline: What We’ve Learned and What We’ve Done over the Past Two Years. 2023. Available online: https://www.cisa.gov/news-events/news/attack-colonial-pipeline-what-weve-learned-what-weve-done-over-past-two-years (accessed on 5 June 2024).
- Klimburg, A.; Beato, F.; Kolaczkowski, M. Why the Energy Sector’s Latest Cyberattack in Europe Matters. 2022. Available online: https://www.weforum.org/agenda/2022/02/cyberattack-amsterdam-rotterdam-antwerp-energy-sector/ (accessed on 5 June 2024).
- Dragos. Global Oil and Gas Cyber Threat Perspective. 2019. Available online: https://www.dragos.com/wp-content/uploads/Dragos-Oil-and-Gas-Threat-Perspective-2019.pdf (accessed on 5 June 2024).
- Industrial Cyber. Dragos Detects Escalation in Adversarial Capabilities, As Pipedream Threat Group Widens Attack Competence. 2023. Available online: https://industrialcyber.co/news/dragos-detects-escalation-in-adversarial-capabilities-as-pipedream-threat-group-widens-attack-competence/ (accessed on 26 July 2024).
- Israel National Cyber Directorate. Cyber Defense Doctrine Managing the Risk: Full Applied Guide to Organizational Cyber Defense; ICND: Tel Aviv, Israel, 2021.
- Smith, D.C. Cybersecurity in the energy sector: Are we really prepared? J. Energy Nat. Resour. Law 2021, 39, 265–270. [Google Scholar] [CrossRef]
- Parfomak, P.W. Liquefied Natural Gas (LNG)Infrastructure Security: Issues for Congress. In Liquefied Natural Gas: Security and Hazards; Keller, B.W., Ed.; Nova Science Publishers, Inc.: New York, UK, 2009; pp. 49–85. [Google Scholar]
- Wadhawan, Y.; Neuman, C. Evaluating Resilience of Gas Pipeline Systems Under Cyber-Physical Attacks: A Function-Based Methodology. In Proceedings of the 2nd ACM Workshop on Cyber-Physical Systems Security and Privacy, Vienna, Austria, 28 October 2016. [Google Scholar]
- Wang, Z.; Zhao, B.; Blum, R.S. An Overview of Cybersecurity for Natural Gas Networks: Attacks, Attack Assessment, and Attack Detection. In Security in Cyber-Physical Systems Foundations and Applications; Fink, G.A., Song, H., Jeschke, S., Eds.; Springer: London, UK, 2021; pp. 256–268. [Google Scholar]
- Nurse, J.R.C.; Creese, S.; Goldsmith, M.; Lamberts, K. Trustworthy and Effective Communication of Cybersecurity Risks: A Review. The 1st Workshop on Socio-Technical Aspects in Security and Trust (STAST 2011). In Proceedings of the The 5th International Conference on Network and System Security (NSS 2011), Milan, Italy, 8 September 2011. [Google Scholar]
- Giannopoulos, G.; Jungwirth, R.; Hadjisavvas, C. Fortifying Defence: Strengthening Critical Energy Infrastructure against Hybrid Threats; EDA: Brussels, Belgium, 2023.
- Hadjistassou, C.; Bratskas, R.; Koutras, N.; Kyriakides, A.; Charalambous, E.; Hadjiantonis, A.M. Safeguarding critical infrastructures from cyber attacks: A case study for offshore natural gas assets. J. Pol. Saf. Reliab. Assoc. Summer Saf. Reliab. Semin. 2015, 6, 115–124. [Google Scholar]
- Kilovaty, I. Cybersecuring the Pipeline. House Law Rev. 2023, 60, 605. [Google Scholar]
- Greco, E.; Marconi, F. Technological Innovation and Cybersecurity: The Role of the G7. IAI Comment. 2024, 24, 1–6. [Google Scholar]
- European Central Bank. G7 Fundamental Elements of Cybersecurity for the Financial Sector. 2016. Available online: https://www.ecb.europa.eu/paym/pol/shared/pdf/G7_Fundamental_Elements_Oct_2016.pdf (accessed on 27 July 2024).
- ENISA. Public Private Partnerships (PPP) Cooperative Models; ENISA: Brussels, Belgium, 2017.
- Polski, M.M.; Ostrom, E. An Institutional Framework for Policy Analysis and Design. 1999. Available online: https://ostromworkshop.indiana.edu/pdf/teaching/iad-for-policy-applications.pdf (accessed on 24 July 2024).
- Skarbek, D. Qualitative research methods for institutional analysis. J. Institutional Econ. 2020, 16, 409–422. [Google Scholar] [CrossRef]
- Vanhoonacker, S. The Institutional Framework. In International Relations and the European Union; Hill, C., Smith, M., Eds.; Oxford University Press: Oxford, UK, 2011; pp. 76–100. [Google Scholar]
- Andonova, L. Governance Entrepreneurs; Cambridge University Press: Cambridge, MA, USA, 2017. [Google Scholar]
- DiMaggio, P.J.; Walter, P. The iron cage revisited” institutional isomorphism and collective rationality in organizational fields. Am. Sociol. Rev. 1983, 48, 147–160. [Google Scholar] [CrossRef]
- Powell, W.I.; Maggio, P.D. Introduction. In The New Institutionalism in Organizational Analysis; Powell, W.W., DiMaggio, P.J., Eds.; The University of Chicago Press: Chicago, IL, USA, 1991; pp. 7–61. [Google Scholar]
- Newhouse, W.; Long, J.; Weitzel David Warren, J.; Thompson, M.; Yates, C.; Tran, H.; Mink, A.; Herriott, A.; Cottle, T. Cybersecurity Framework Profile for Liquefied Natural Gas; US National Institute of Standards and Technology: Washington, DC, USA, 2023.
- Luiijf, E.; Besseling, K. Nineteen national cyber security strategies. Int. J. Crit. Infrastruct. 2013, 9, 3–31. [Google Scholar] [CrossRef]
- NATO CCDCOE. NATO CCD COE National Cyber Security Strategy Guidelines. 2013. Available online: https://ccdcoe.org/uploads/2018/10/NCSS-Guidelines_2013.pdf (accessed on 4 June 2024).
- Park, C.; Shi, W.; Zhang, W.; Kontovas, C.; Chang, C.H. Cybersecurity in the maritime industry: A literature review. In Proceedings of the International Association of Maritime Universities (IAMU) Conference, the 20th Commemorative Annual General Assembly, Tokyo, Japan, 30 October–1 November 2019. [Google Scholar]
- European Commission and HR FASP. Joint Communication To The European Parliament And The EU’s Cybersecurity Strategy for the Digital Decade. 2020. Available online: https://digital-strategy.ec.europa.eu/en/policies/cybersecurity-strategy (accessed on 4 June 2024).
- European Defence Agency. Protection of Critical Energy Infrastructure (PCEI) Conceptual Paper. 2017. Available online: https://eda.europa.eu/docs/default-source/events/eden/phase-i/information-sheets/cf-sedss---protection-of-critical-energy-infrastructure-conceptual-paper.pdf (accessed on 3 July 2024).
- Bundesministerium des Innern für Bau und Heimat. Cybersicherheitsstrategie für Deutschland 2021. 2021. Available online: https://www.cio.bund.de/SharedDocs/downloads/Webs/CIO/DE/it-sicherheit-und-netze/it-sicherheit/cybersicherheitsstrategie-fuer-deutschland/cybersicherheitsstrategie-fuer-deutschland2021.pdf;jsessionid=3A70E0CBE8BA58D4304BB64CCD5EC4C0.live881?__blob=public (accessed on 10 June 2024).
- International Telecommunication Union. Global Cybersecurity Index 2020; International Telecommunication Union: Geneva, Switzerland, 2020. [Google Scholar]
- Raath, S. Cybersecurity Spending: How Much Are Countries Investing in Their Digital Defenses? 2024. Available online: https://www.expressvpn.com/blog/cybersecurity-spending/#20 (accessed on 6 June 2024).
- IISS. Cyber Capabilities and National Power: Net Assessment; INSS: London, UK, 2020; Volume 1. [Google Scholar]
- Blooshi, B.A.; Eksteen, A. Cyber Governance in the EU. In European Cybersecurity in!Context A Policy-Oriented Comparative Analysis, Technoseries Paper 3; Martino, L., Gamal, N., Eds.; European Liberal Forum: Brussels, Belgium, 2022; pp. 19–27. [Google Scholar]
- G20 Research Group. 2019 G20 Osaka Summit Interim Compliance Report; University of Toronto: Toronto, ON, Canada, 2019. [Google Scholar]
- Pollet, M. France Launches “Cyber Campus” to Boost Cybersecurity Strategy. 2022. Available online: https://www.euractiv.com/section/cybersecurity/news/france-launches-new-cyber-campus-to-boost-cybersecurity-strategy/ (accessed on 1 July 2024).
- Agenzia Cybersicurezza Nazionale. National Cybersecurity Strategy 2022–2026. 2022. Available online: https://www.acn.gov.it/portale/en/strategia-nazionale-di-cybersicurezza (accessed on 11 July 2024).
- Hathaway, M.; Spidalieri, F. Italy Cyber Readiness at a Glance; Potomac Institute for Policy Studies: Arlington, VA, USA, 2016. [Google Scholar]
- HM Government. National Cyber Strategy 2022 Pioneering a Cyber Future with the Whole of the UK. 2022. Available online: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/1053023/national-cyber-strategy-amend.pdf (accessed on 10 June 2024).
- The Whitehouse. US National Cybersecurity Strategy. 2023. Available online: https://www.whitehouse.gov/wp-content/uploads/2023/03/National-Cybersecurity-Strategy-2023.pdf (accessed on 4 June 2024).
- Andonova, L. Globalization, Agency, and Institutional Innovation: The Rise of Public-Private Partnerships in Global Governance. Colby-Work. Pap. Econ. 2006, 3, 1–62. [Google Scholar]
- Manley, M. Cyberspace’s Dynamic Duo: Forging a Cybersecurity Public-Private Partnership. J. Strateg. Secur. 2015, 8, 85–98. [Google Scholar] [CrossRef]
- Carr, M. Public–Private Partnerships in National Cyber-Security Strategies. 2016. Available online: https://www.chathamhouse.org/sites/default/files/publications/ia/INTA92_1_03_Carr.pdf (accessed on 14 January 2022).
- The European Parliament and the Council. Directive 2022/2555 of The European Parliament and of The Council of 14 December 2022 on measures for a high common level of cybersecurity across the Union, amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and repealing Directive (EU) 2016/1148 (NIS 2 Directive) (Text with EEA relevance). Off. J. Eur. Union 2022, L333, 80–152. [Google Scholar]
- Busch, N.E.; Givens, A.D. Public-Private Partnerships in Homeland Security: Opportunities and Challenges. Homel. Secur. Aff. 2012, 8, 1–24. [Google Scholar]
- Christensen, K.K.; Petersen, K.L. Public–private partnerships on cyber security: A practice of loyalty. Int. Aff. 2017, 93, 1435–1452. [Google Scholar] [CrossRef]
- US Department of Energy. Natural Gas. 2015. Available online: https://www.energy.gov/sites/prod/files/2015/06/f22/Appendix%20B-%20Natural%20Gas_1.pdf (accessed on 3 June 2024).
- Menashri, H.; Baram, G. Critical Infrastructures and Their Interdependence in a Cyber Attack—The Case of the U.S. 2015. Available online: https://www.inss.org.il/wp-content/uploads/systemfiles/5_Menashri_Baram.pdf (accessed on 21 March 2023).
- Rinaldi, S.M.; Peerenboom, J.P.; Kelly, T.K. Identifying, Understanding, and Analyzing Critical Infratsructures Interdependencies. Control. Syst. Mag. 2002, 21, 11–25. [Google Scholar] [CrossRef]
- Portante, E.C.; Kavicky, J.A.; Craig, B.A.; Talaber, L.E.; Folga, S.M. Modeling Electric Power and Natural Gas System Interdependencies. J. Infrastruct. Syst. 2017, 23, 1–18. [Google Scholar] [CrossRef]
- Bureau of Policy and Research. Ten Years After Sandy Barriers to Resilience; Bureau of Policy and Research: New York, NY, USA, 2022.
- Hokstad, P.; Utne, I.B.; Vatn, J. (Eds.) Interdependency Modelling in Risk Analysis. In Risks and Interdependencies in Critical Infrastructures; Norwegian University of Science and Technology: Trodenheim, Norway, 2012; pp. 45–101. [Google Scholar]
- Pawlak, P.; Géry, A. Why the World Needs a New Cyber Treaty for Critical Infrastructure. 2024. Available online: https://carnegieendowment.org/research/2024/03/why-the-world-needs-a-new-cyber-treaty-for-critical-infrastructure?lang=en¢er=europe (accessed on 8 June 2024).
- Settanni, G.; Skopik, F.; Shovgenya, Y.; Fiedler, R.; Carolan, M.; Conroy, D.; Boettinger, K.; Gall, M.; Brost, G.; Ponchel, C.; et al. A collaborative cyber incident management system for European interconnected critical infrastructures. J. Inf. Secur. Appl. 2017, 34, 166–182. [Google Scholar] [CrossRef]
- Sonesson, T.R.; Johansson, J.; Cedergren, A. Governance and interdependencies of critical infrastructures: Exploring mechanisms for cross-sector resilience. Saf. Sci. 2021, 142, 105383. [Google Scholar] [CrossRef]
- Fägersten, B.; Fiott, D.; Kleberg, C. Navigating the Euro-Atlantic Defence Innovation Landscape; Politea: Stockholm, Sweden, 2023. [Google Scholar]
- Group of Eight. G8 Principles for Protecting Critical Information Infrastructures. 2003. Available online: http://www.cybersecuritycooperation.org/documents/G8_CIIP_Principles.pdf (accessed on 8 June 2024).
- Global Cyber Security Capacity Centre. Cybersecurity Capacity Maturity Model for Nations (CMM). 2016. Available online: https://gcscc.web.ox.ac.uk/files/cmmrevisededition090220171pdf (accessed on 8 June 2024).
- UNODA. Canada’s Proposal for the Work of the 2021-25 United Nations Open-Ended Working Group on “Developments in the Field of Information and Telecommunications in the Context of International Security” (UNCLASSIFIED). 2021. Available online: https://documents.unoda.org/wp-content/uploads/2021/12/Canadian-position-paper-2021-25-OEWG-final-Dec-6_Annex-Gender-Considerations.pdf (accessed on 8 June 2024).
- OSCE. 10 Years of OSCE Cyber/ICT Security Confidence-Building Measures. 2023. Available online: https://www.osce.org/files/f/documents/f/7/555999_1.pdf (accessed on 10 June 2024).
- Martino, L. Give Diplomacy a Chance: OSCE’s Red Lines in Cyberspace. 2018. Available online: https://www.cssii.unifi.it/upload/sub/Pubblicazioni/2018_Martino_Luigi.pdf (accessed on 3 June 2024).
- Home Treasury. About the G7 Cyber Expert Group (CEG). 2023. Available online: https://home.treasury.gov/policy-issues/international/g-7-and-g-20/g7-cyber-expert-group (accessed on 8 June 2024).
- Abbott, K.W.; Genschel, P.; Snidal, D.; Zangl, B. Two Logics of Indirect Governance: Delegation and Orchestration. Br. J. Political Sci. 2016, 46, 719–729. [Google Scholar] [CrossRef]
- Klijn, E.H. Public Private Partnerships: Deciphering meaning, message and phenomenon. In International Handbook of PPP; Hodge, G.A., Greve, C., Boardman, A.E., Eds.; Edgar Elgar: Cheltenham, UK, 2010; pp. 68–80. [Google Scholar]
- Rosenau, J. Governance in the Twenty-first Century. Glob. Gov. 1995, 1, 13–43. [Google Scholar] [CrossRef]
- Rosenau, J. Governing the ungovernable: The challenge of a global disaggregation of authority. Regul. Gov. 2007, 1, 88–97. [Google Scholar] [CrossRef]
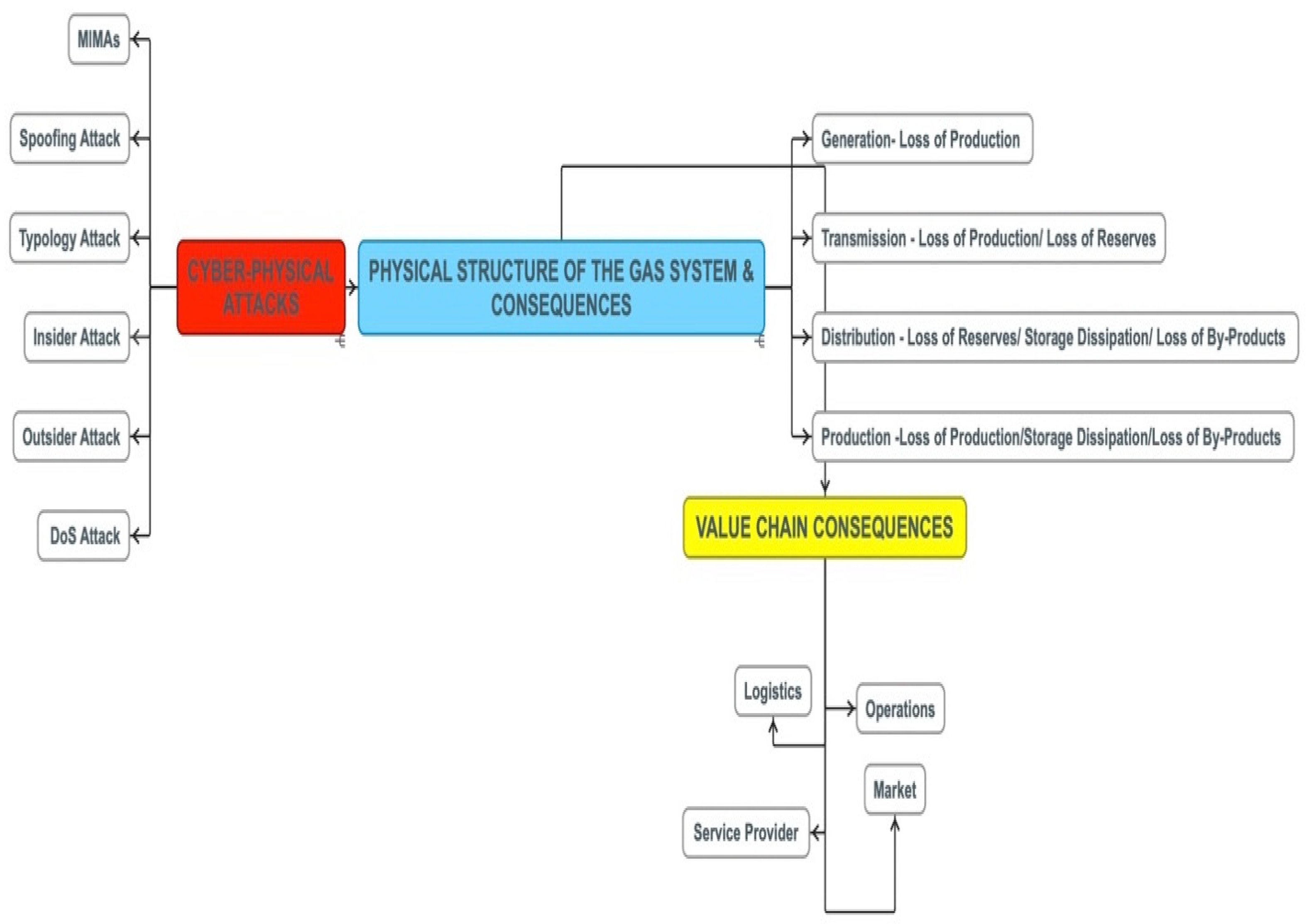
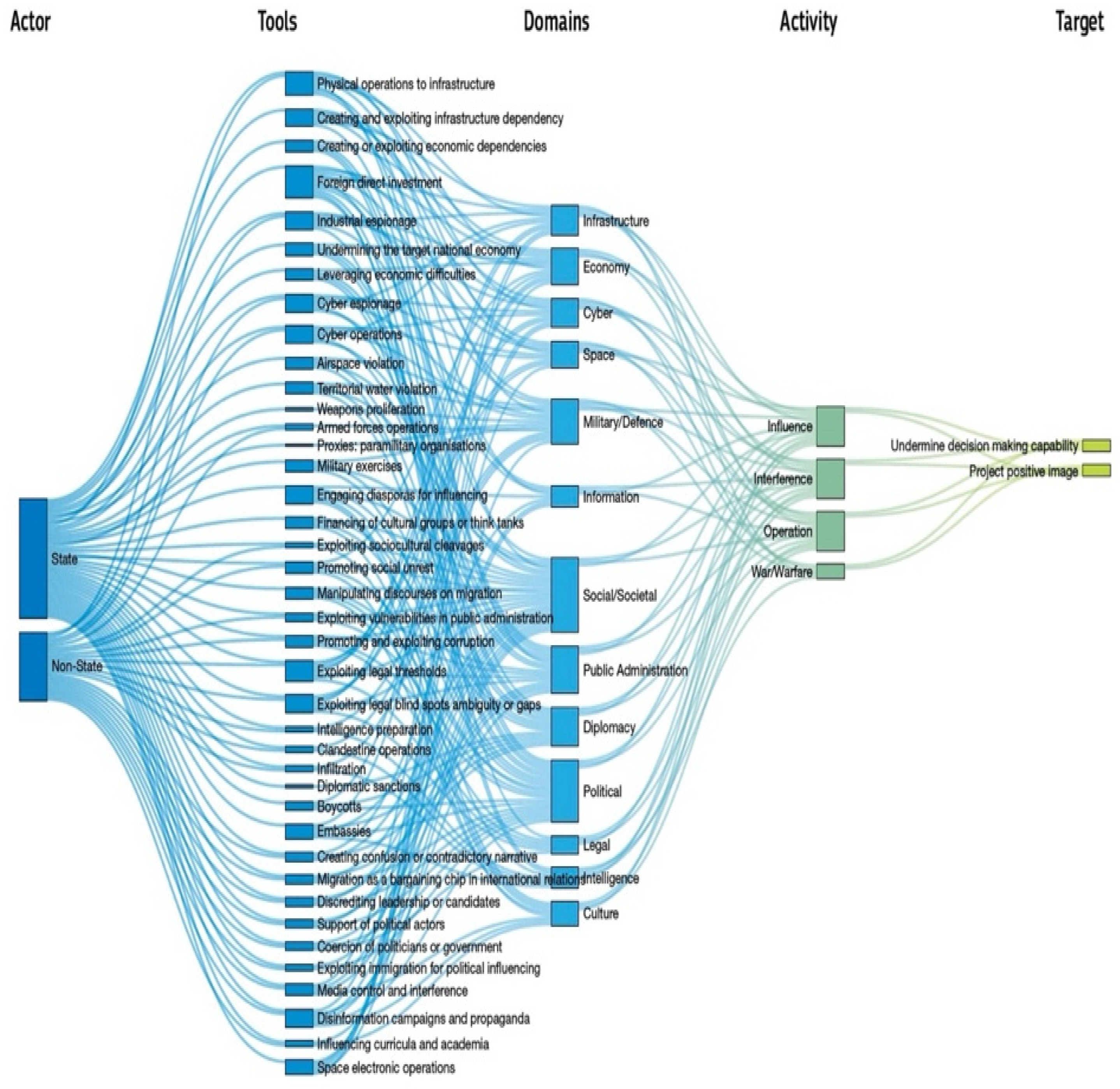

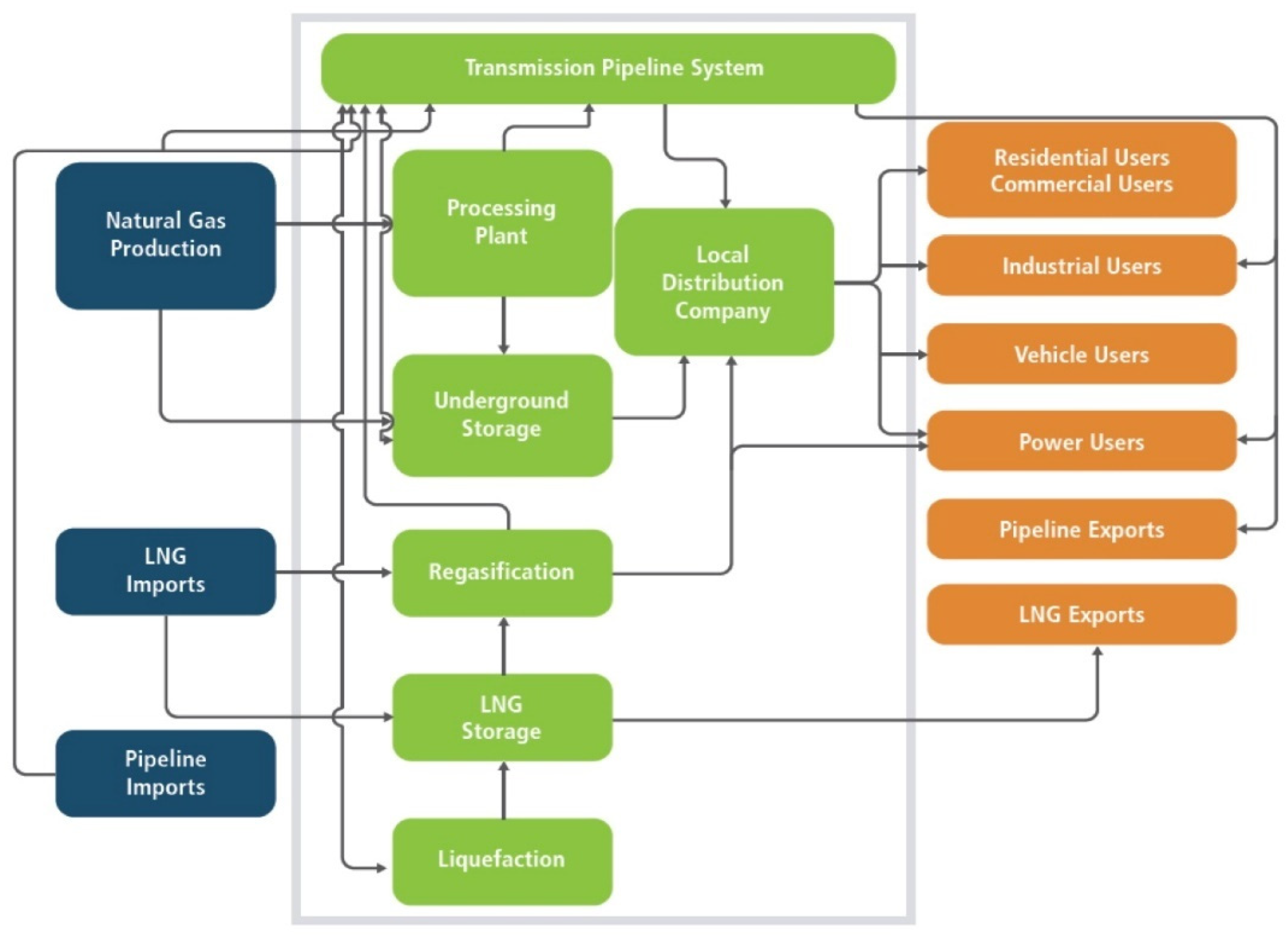
| Risks | Characteristics | Examples |
|---|---|---|
| Communication [59] | Relates to the risk message | Difficulty in understanding and transmitting the message Inaccurate information that affects decision making Media have also been shown to cause problems through a lack of care in interpreting and reporting |
| Risk source | ||
| Message receiver | ||
| Escalation phases [60] | Targeting (decision making) Destabilisation (multiple operations) Coercion (hybrid warfare) | Creating and exploiting infrastructure dependency: cyber espionage, exploiting legal rules and institutions Infiltrations, water space violation Paramilitary organisations attack |
| Cyberweapons [60,61] | Computer; worm; trojan back-door; modular virus, modular malware; remote attacks; | Industrial system damage; cyber espionage in the energy sector; covert intelligence monitoring |
| Cyber attacks that propagate from cyber to the gas pipeline physical domain [57] | Before SCADA responds Preventing SCADA response | A failure of a cyber node controlling power grid functionality propagates from cyber to power to gas pipeline systems |
| Others | Theft of core intellectual property; disruption or destruction of a physical plant; biased communications by leadership |
| Source of Threat | Motivation | Goals | Consequences | Risk Impact—TBD |
|---|---|---|---|---|
| Government/Proxies Criminal Actors Non-state Actors Illiterate users Business competitors | Espionage/Military Espionage Pre-mission Intelligence Sabotage Economic Profit Revenge | Reputation Damage IP Theft/Corruption Money Extortion Leak of sensitive information Services Disruption | Human Lives IP Theft Destruction of Critical Energy Infrastructure Sanctions Disinvestment | Insignificant Minor Major Critical Catastrophic |
| Country | Important Governance Structures | Strategic Documents | Budget 2024 (USD Billion) | Global Cybersecurity Index Ranking (2020) | Membership |
|---|---|---|---|---|---|
| United States | National Security Council Department of Defence Intelligence agencies Private Sector Universities US Cyber Army Command Cyber industry | National Cybersecurity Strategy 2023 DoD Cyber Strategy 2023 International Cyberspace and Digital Policy Strategy, 2024 | 78.3 | 1 | NATO FVEY |
| United Kingdom | National Cyber Security Service National Cyber Security Centre National Cyber Force CERT Cyber industry | National Cyber Strategy 2022 Government Cyber Security Strategy 2022 to 2030 | 10.6 | 2 | NATO FVEY |
| Canada | Communications Security Establishment Canadian Armed Forces Canadian Security Intelligence Service Joint Force Cyber Command Canadian Centre for Cyber Security National CERT Cyber industry | Enterprise Cyber Security Strategy 2024 National Cyber Security Action Plan 2019–2024 | 3.68 | 3 | NATO FVEY |
| Japan | Cyber Security Strategic Headquarters National Center of Incident Readiness& Strategy for Cybersecurity Defence Intelligence Headquarters Directorate for Signals Intelligence National CERT Military C4 Systems Command Japan Self-Defence Forces | Cybersecurity Strategy 2018 National Security Strategy 2022 National Defence Strategy 2022 Individual Partnership and Cooperation Programme in 2020 | 10.1 | 7 | FVEY ally |
| France | Defence and National Security Council, ComCyber, Cyber Defence Executive Committee General Directorate for External Security National cyber-security Campus Private Sector National CERT | National Security Strategy 2022 Strategic Review of Cyber Defence | 5.5 | 9 | NATO EU FVEY ally |
| Germany | Federal Min Interior Centre for Digitization & Capability Development Federal Office for Information Security Citizen-CERT Implementation Plan for Critical Infrastructure Military Cyber Branch Private Sector Cyber industry | White Paper 2016 National Cyber Security Strategy 2021 | 7.9 | 13 | NATO EU |
| Italy | Interministerial Committee for the Security of Republic National Cybersecurity Agency Technical CISR, Cyber Security Unit Leonardo Cybersecurity Academy NATO-Leonardo Security Operation Centre IT-CERT National Cybersecurity Authority Public-private collaboration Cyber industry | Quadro Strategico Nazionale National Cybersecurity Strategy 2022–2026 Italy’s Cloud Strategy | 2.6 | 20 | NATO EU |
| IAD Domain | G7 |
|---|---|
| Policy Analysis Objective & Analytic Approach | Analysis Objective: Transnational Cybergovernance in Energy Analytic Approach: Cybergovernance capabilities of each G7 member Multistakeholder approach to cybergovernance at national level Exploring international engagements in Cybergovernance of G7 members Energy & Cyber power balances Energy security domain of interest for G7 members |
| Physical World | Most industrialised economies Strength of cyber capabilities: Tier 1 (US, UK, Canada, France). Tier 2 (Japan), and Tier 3 (Italy, Germany) Cyber risk management national frameworks between innovation and technology Cyber culture of the state Approach to safeguard national critical energy infrastructures Energy sovereignty depends on cyber sovereignty Top gas exporters: US, Canada Top gas importers: UK, Japan, France EU gas transit hub: Italy and Germany Defence innovativeness |
| Community | Security Community-amalgamated and integrated characterised by political communications Members are bound by their allianceships Shared strategic and economic interests |
| Rules-in-use | National regulatory frameworks State-level agencies Methodologies for cyber risk management in the public and private sectors Offensive and defensive operations in France are clearly divided so the rules of engagements Decision-making is with state-level institutions, national cyber agencies and high-level leadership Some G7 countries have a military cyber command, others not. |
| Action arena | Integration of cyber units within government entities Public-private engagement is a preferred actor in the cyber governance. Industry forums |
| Patterns of interaction | Some countries have national cyber forums or campuses where private and public engage NATO structures EU structures OSCE Five Eyes Alliance Bilateral agreements Regional initiatives Informal and formal networks of cyber security communities Partnerships between state-level institutions and industry at NATO/EU level |
| Outcomes | The trust might be an issue amongst G7 governments for greater control over critical energy infrastructures Optimisation of cyber resources Greater expertise in cyber issues Governments agree on objectives and norms of cooperation Use transnational public-private partnerships to compensate the gap in cybergovernance Increase of clusters of transnational epistemic networks on cyber governance |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pengili, M.; Raszewski, S. Transnational Cyber Governance for Risk Management in the Gas Sector: Exploring the Potential of G7 Cooperation. Gases 2024, 4, 327-350. https://doi.org/10.3390/gases4040019
Pengili M, Raszewski S. Transnational Cyber Governance for Risk Management in the Gas Sector: Exploring the Potential of G7 Cooperation. Gases. 2024; 4(4):327-350. https://doi.org/10.3390/gases4040019
Chicago/Turabian StylePengili, Megghi, and Slawomir Raszewski. 2024. "Transnational Cyber Governance for Risk Management in the Gas Sector: Exploring the Potential of G7 Cooperation" Gases 4, no. 4: 327-350. https://doi.org/10.3390/gases4040019
APA StylePengili, M., & Raszewski, S. (2024). Transnational Cyber Governance for Risk Management in the Gas Sector: Exploring the Potential of G7 Cooperation. Gases, 4(4), 327-350. https://doi.org/10.3390/gases4040019





