Abstract
Cyber situational awareness is the result of both the analysis of cyber security and situational awareness studies and the line of research that uses artificial intelligence methods in the field of cybersecurity. It covers both methods of automatic detection of cyber threats in the network and methods of providing information to an analyst for further risk analysis and decision making to protect of the assets of the facility. Investigations of cyber situational awareness in the energy sector have become pertinent resulting from both the concept of the digital transformation of energy and the consideration of energy facilities and systems as cyber-physical systems. The problems of ensuring cybersecurity and raising awareness about the cyber environment of an energy facility are compounded by their high significance for the economies of countries. In this regard, such facilities are considered as critical infrastructure. The first part of this article discusses the basic concepts of cyber situational awareness, some knowledge representation models and some existing security metrics. The second part considers the use of frame, production and network models of knowledge representation in the analysis of the cyber situational awareness of energy facilities and the software components that implement them.
1. Introduction
Cyber situational awareness (CSA) studies are accompanied by planning strategies and the implementation of protection measures. These studies are not limited to searching for vulnerabilities, cyber threats in the cyber environment, tracking incidents or anomalies. Such studies include the activities of an analyst with a large amount of data, their analysis and the preparatory stages for decision making. This article describes methods and developed software tools to support decision making in the analysis of the CSA of energy facilities, although the classical model of cyber situational awareness presented by Mica Endsley [1] does not include the decision-making process.
1.1. Aspects of Cyber Situational Awareness
Cyber situational awareness includes awareness of any suspicious or atypical activities occurring in a cyber environment, where a cyber environment comprises any activities related to a computer network [2]. Cyber situational awareness is considered from both a technical and cognitive point of view.
The technical component is of great importance at the operational level of security incident management, which is characterized by some security elements. These include vulnerability management, patch management, event management, incident management, malware detection, asset management, configuration management, network management, license management and information management [3].
The cognitive component of cyber situational awareness concerns a person’s ability to understand the technical implications and draw conclusions to make informed decisions [2]. Decision making plays an important role both on a tactical level and on a strategic level. The former is aimed at assessing the impact of the current state of the cyber environment on the normal functioning of the facility. The latter is related to identifying trends in malicious attacks and building effective protection plans.
Most of the existing security analysis tools are focused on detecting attacks [4]. Such tools are usually considered within the framework of the technical component of CSA. Safety assessments and decisions on the provision of safety measures refer to the prediction of what may happen in the future, which is closely related to the cognitive component of CSA. Observation of the current situation and its constituent factors is possible if there is an absence of security [5]. The assessment of the security of the cyber environment is accompanied by the choice and calculation of security metrics.
1.2. Security Metrics
Metrics are understood as “tools designed to facilitate decision making and improve performance and accountability through collection, analysis, and reporting of relevant performance-related data” [6]. Flater D. in [5,7] discusses the good and bad characteristics of security metrics. The main characteristics of bad metrics include the interpretation of safety as a quantity that can be measured; incorrect use of scales and the use of erroneous scales, the choice of which can mislead and lead to unreasonable or false conclusions; false precision of the assessment of the operability of products and technologies, in which the uncertainty of the measurement is ignored; combining disparate measures without substantiating how this gives a reliable measurement; and naive use of human input which ignores subjective factors.
Ref. [4] provides corporate network security metrics, where a scale of parameters and a method for calculating the indicator are defined for each metric. The remaining operability of a cyber asset after an attack or hack, the average length of attack paths and the percentage of compromised hosts at time t are some examples of such metrics. In [8], metrics are divided into calculating the metrics from the viewpoint of attacks, malefactors, network topologies and the cost characteristics of attacks and countermeasures, as well as the possibility of zero-day vulnerabilities. Paper [9] provides an extensive classification of model-based quantitative network security metrics and research papers that use them. The paper concludes that the development of metrics and models is aimed at supporting decision making, rather than forming an ideal conception of the level of network security.
The transition from awareness of the state of the cyber environment to decision making can be accomplished through the use of semantic modeling methods.
1.3. Semantic Modeling Methods and Some Their Challenges
Semantic modeling methods are used to analyze and model the behavior of systems, objects and situations that have a number of characteristics such as [10] (i) difficulties in formal description and accurate prediction of their behavior; (ii) absence or incompleteness of data; (iii) measurement of elements (factors) describing the behavior of systems, objects and situations cannot be performed with sufficient accuracy. Semantic models include ontologies, Bayesian belief networks and cognitive and event models [11]. Semantic models are subjective models, the construction of which is aimed at formalizing human (expert) knowledge in a certain problem area. Methods related to the formalization of human knowledge depend on such aspects as [12] (i) assumptions about the adequacy of knowledge accepted in theoretical models and (ii) the ability of analysts and experts to carry out adequate formalization in terms of the accepted theoretical model.
The problem of the subjectivity of expert assessments is also relevant in the development of security metrics. As mentioned in Section 1.2, one of the problems in building a good security metric is taking into account the human factor when evaluating security. In [13], three approaches to taking into account the subjective factor are described. These approaches actually relate to the construction of cognitive models; however, they can also be applied within the framework of constructing the causal topology of a Bayesian belief network.
- The construction of collective casual maps, including the commonality of construction goals and the unity of decision-making strategies. Such an approach may be accompanied by the problem of mutual understanding of the parties involved in the modeling and the problem of differences in the key concepts of experts.
- An approach for conflict situations, according to which the knowledge model includes several semantic models (cognitive maps) built by different experts with different goals and interests.
- An approach to analyzing the validity of managerial decisions based on reflexive cognitive maps, aimed at assessing the adequacy of managerial decisions to find bottlenecks based on semantic models constructed by various experts with their own views but with a common goal.
The collective method of matching knowledge bases for various fields of science and education regarding the example of building ontologies is considered in [14]. Special attention is paid to the Cognitive Ergonomic Metric, the purpose of which is to evaluate two aspects: (i) correctness and depth of reflection of the subject area and (ii) the ergonomic aspect of the ontology representation from the point of view of the quality and speed of human perception.
The problem of the subjectivity of expert assessments arises both in the construction of semantic models and in the formation of probability distributions on the nodes of the Bayesian belief network. On the one hand, the subjectivity of a priori expert-derived probabilities can be partially offset by the use of publicly available statistical reports, and on the other hand, collective methods can lead to a consensus [15] in determining probabilistic characteristics. With the appearance of the necessary statistical data, it is possible to update the probability value to a plausible value for vulnerabilities and threats which are within a cyber environment. For instance, these include threats of cyber negligence and threats associated with the use of social engineering.
Models based on the Bayesian paradigm are widely used to solve predictive tasks of risk analysis. The purpose of this analysis is to provide decision support [16]. This paradigm fits into the context of the analysis of CSA in the application to cybersecurity.
The interpretation of large volumes of received data is a rather difficult task that requires a highly experienced analyst despite the intellectualization of security software in a computer network. The paper proposes to use frame, production and semantic models in the analysis of the CSA of an energy facility, which allows one to formalize expert knowledge and to replicate it in the future.
2. Analysis of Cyber Situational Awareness of Energy Facilities
The current research focuses on the cognitive component of CSA relying on existing systems for security incident detection, intrusion detection and anomaly detection in the network. A CSA analysis of an energy facility is proposed to be carried out in three stages:
- Environment and situation analyses, including an analysis of detected vulnerabilities and threats.
- Modeling of states and events in the cyber environment by constructing threat vectors in the cyber environment of an energy facility based on a Bayesian belief network.
- Risk assessment in the cyber environment using the results of network reasoning.
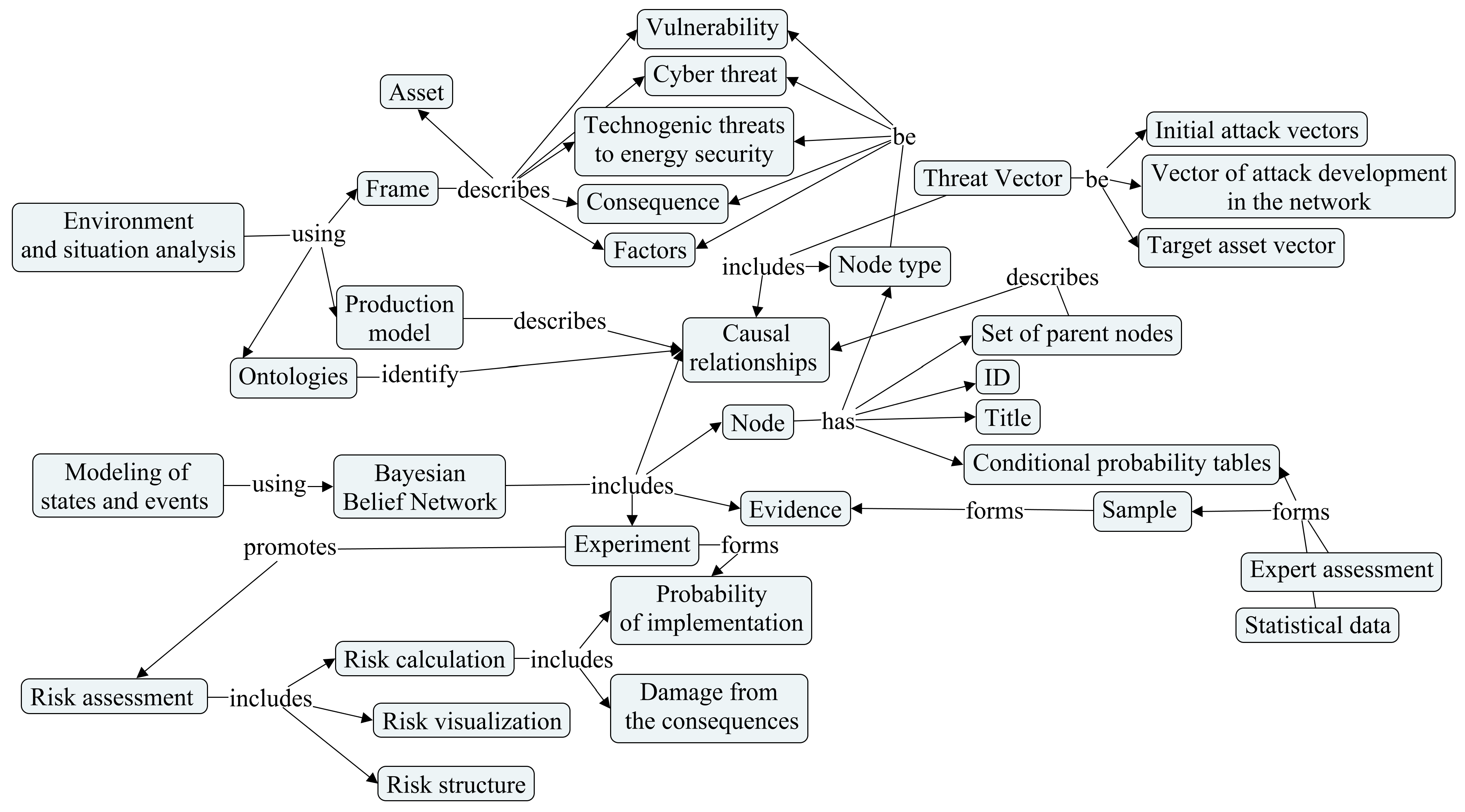
Models of knowledge representation of experts from different fields are used for such analyses in stages 1 and 2. The stage of risk assessment in the cyber environment is usually accompanied by the assessment of the CSA level and the choice of security metrics. The key aspects of assessing the level of CSA are the definition of cyber threats and the choice of security metrics. Figure 1 shows the ontology of the stages of analysis of the CSA of an energy facility using frame, production and semantic models.
Figure 1.
Stages of analysis of CSA of an energy facility using frame, production and semantic models.
2.1. Threat Vectors in the Cyber Environment of an Energy Facility
The importance of energy cyber-physical systems at the national, regional and local levels may motivate attackers to compromise such facilities [17]. The ways of compromising these systems are described by attack vectors. The International Organization for Standardization defines the attack vector as a “path or means by which an attacker can gain access to a computer or network server in order to deliver a malicious outcome” [18]. Attack vectors are often used to describe a targeted attack, which attackers carry out in several stages [19]. Attack vectors are often called threat vectors. There are many approaches to modeling cyber threats and the stages of attack vectors, for example, one of the most well known is the Cyber Kill Chain approach [20], including a life cycle model of cyber attacks.
The paper discusses threat vectors to describe the chains of causal relationships between the use of vulnerabilities of the cyber environment and cyber threats and technogenic threats to energy security and the consequences of the implementation of cyber threats. This characterizes a targeted attack, user actions with cyber negligent and the activities of hacktivists.
The semantic modeling and knowledge engineering methods aim to form the causal relationships in the framework of constructing scenarios of extreme situations in the energy sector caused by cyber threats.
2.2. The Main Stages of Building a Knowledge Representation Model for Threat Vectors
The construction of semantic models in general is reduced to the tasks of identifying the basic concepts, establishing relation between them and defining strategies for decision making in the developed model. It is quite difficult to develop a Bayesian belief network corresponding to the threat vector without prior preparation. In this regard, the construction of a threat vector model in the cyber environment of an energy facility is proposed to be carried out in several stages, presented in Table 1.

Table 1.
The main stages of building a knowledge representation model for the threat vectors.
The knowledge model built at stages 1–3 is used in this work to achieve CSA goals from a cognitive aspect. Such a knowledge model has a number of limitations: (i) threat vectors are limited to the facility under consideration; (ii) threat vectors are considered from the point of view of disrupting business and technological processes that can cause an extreme situation to occur at the facility and/or deeper within the power system; and (iii) threat vectors are built at a sufficiently high level of abstraction and are designed to inform interested parties about possible security incidents from two aspects, i.e., building a threat model and conducting business games.
Stage 1. Identification of the concepts of the subject area. In this case, the understanding of the frame is used as a type of semantic network in which both declarative knowledge and structured procedural knowledge are used [21]. The hierarchical structure of the asset has the form: information asset, the software part and the hardware part. Additional fields include the device type, the segment of the computing network in which the asset is located, the list of incoming assets (for composite complex assets) and the list of related assets. A list of vulnerabilities and a list of threats inherited from the atomic components of the asset are also provided. The functions of adding a vulnerability to the list of vulnerabilities and adding related assets to the list of related assets are provided to perform rule-based reasoning. The vulnerability frame at a high level of abstraction includes the fields type of vulnerability, the asset in which it is contained, the level of danger and complexity of its use and a list of related vulnerabilities. The functions of adding threats to the list of cyber threats and adding vulnerabilities to the list of related vulnerabilities are provided. The cyber threat frame at a high level of abstraction includes the field type of threat, vulnerability that the threat can use, the level of danger and complexity of the attack and a list of related cyber threats. Each frame has a field for a verbal description. The functions of adding cyber threats and human-made threats to the list of related threats are designed. Environment and situation analyses are included in this stage.
Stage 2. Establishing relations between the concepts. Product rules of type 1 “Asset—Vulnerabilities” establish a relation between an asset and its vulnerabilities. Such rules allow one to output all the rules related to the fact of the asset type without introducing specific vulnerabilities. Type 2 “Vulnerability—Threats” rules associate the relations between asset vulnerabilities and cyber threats that can exploit these vulnerabilities. The type 3 “Threats—Threats” rules add the effect of the relationship between threats, including between a cyber-threat and a cyber-threat and between a cyber-threat and technological threat, on energy security. The generated rules store descriptions of the vector stage for the possibility of implementing the explanation subsystem in the expert system. This stage is in preparation for further topology formation of the Bayesian belief networks and it relates to environment and situation analyses.
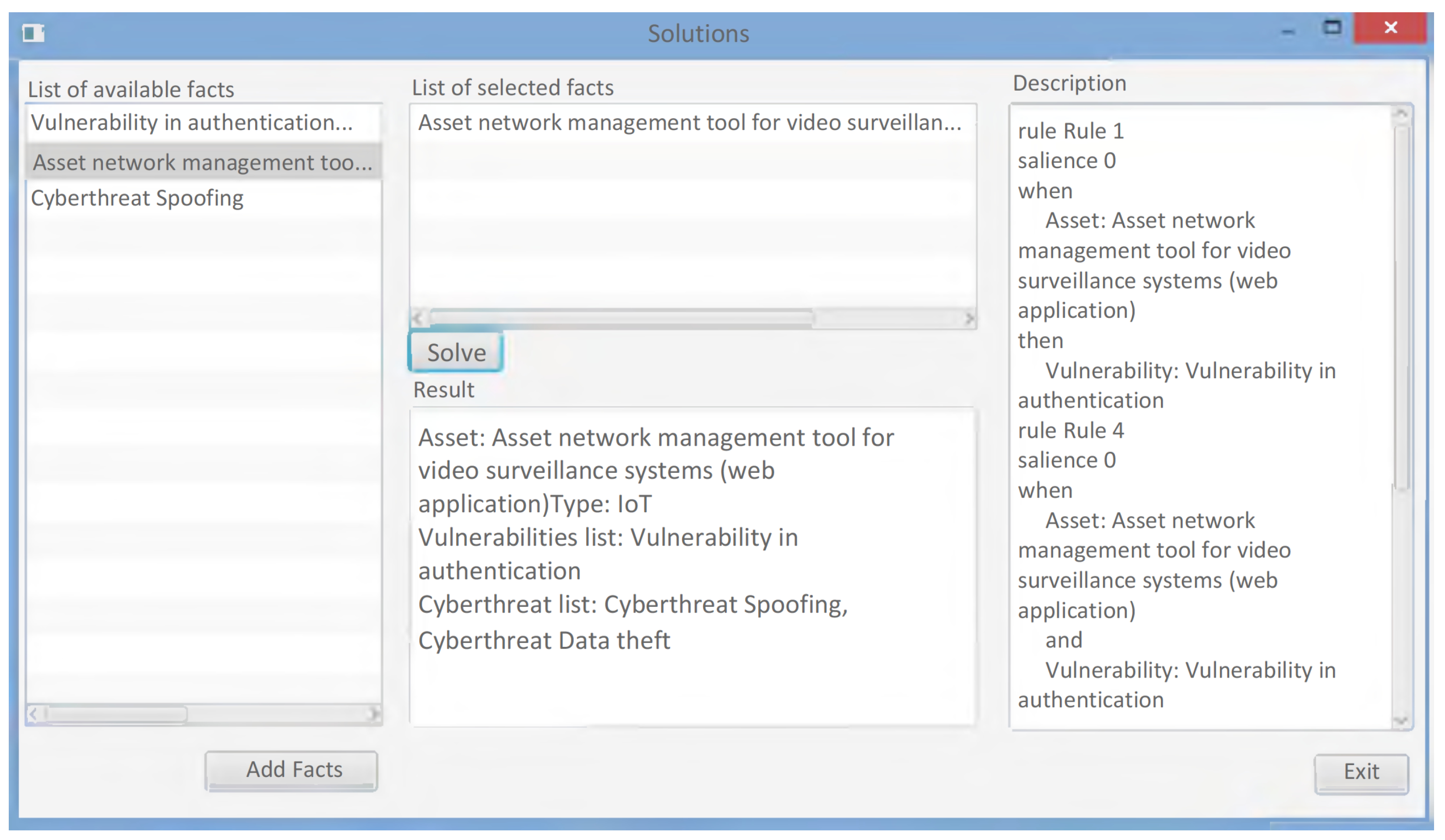
Figure 2 shows the interface of the developed expert system that implements the frame and production models of knowledge representation.
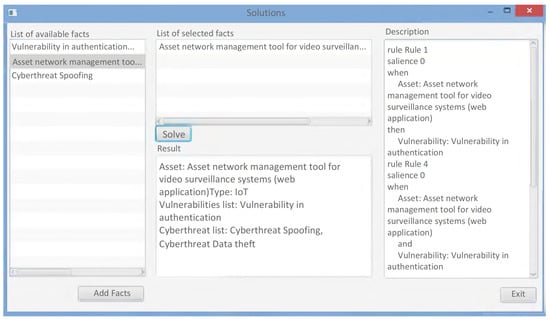
Figure 2.
The interface of the developed expert system for constructing threat vectors of an energy facility.
Stage 3. Defining strategies for decision making. The stage of preparing information for defining strategies and choosing the appropriate metrics and measurement scales is a difficult task. The level of detail of the threat vector based on the Bayesian belief network apparatus depends on the expert’s choice. The analysis of the change in the probability of the end nodes of the network corresponding to technogenic threats or consequences is supposed to be used as a part for managing risks in the cyber environment and justifying the choice of means of protection for the corresponding assets. The following aspects are being developed: (i) the construction of an information model of the threat vector in accordance with the topology of the Bayesian belief network based on the fields of frames containing descriptions of concepts, as well as a verbal description of the stages included in rules and (ii) an algorithm to evidence introduction into nodes, which are vector points of entry and further progress. This stage is performed when modeling states and events in the cyber environment and assessing the risks of the cyber environment.
Modeling scenarios of extreme situations in the energy sector caused by cyber threats based on Bayesian belief networks are presented in [22]. A joint probability distribution for the developed model of extreme situation scenarios in an energy facility caused by cyber threats is described in accordance with the chain rule for Bayesian networks:
where is the joint probability distribution for X, stands for the sets of parent nodes of , n is a number of vertices of the graph and denotes a set of discrete random variable such that:
where are discrete random variables corresponding to vulnerabilities, are discrete random variables corresponding to cyber threats, are discrete random variables corresponding to technogenic threats to energy security caused by cyber threats and are discrete random variables corresponding to consequences.
The graph topology of the proposed model has the form:
Moreover is a conditional probability distribution for each variable from X, and if , then are a priori probabilities of .
The presented model is aimed at solving the predictive task of analysis and further assessment of the risk of cyber threats at energy facilities. In this paper, risk is considered as a probability distribution of damage [23]. This probability distribution corresponds to the a posteriori probability of a random variable corresponding to each of the simulated consequences, provided that a certain set of vulnerabilities and threats is implemented, i.e., , where are nodes with given evidence and are observed values of the evidence variables with . The ThreatNet component is implemented in the presented model.
2.3. Decision Making Based on a CSA Analysis of an Energy Facility
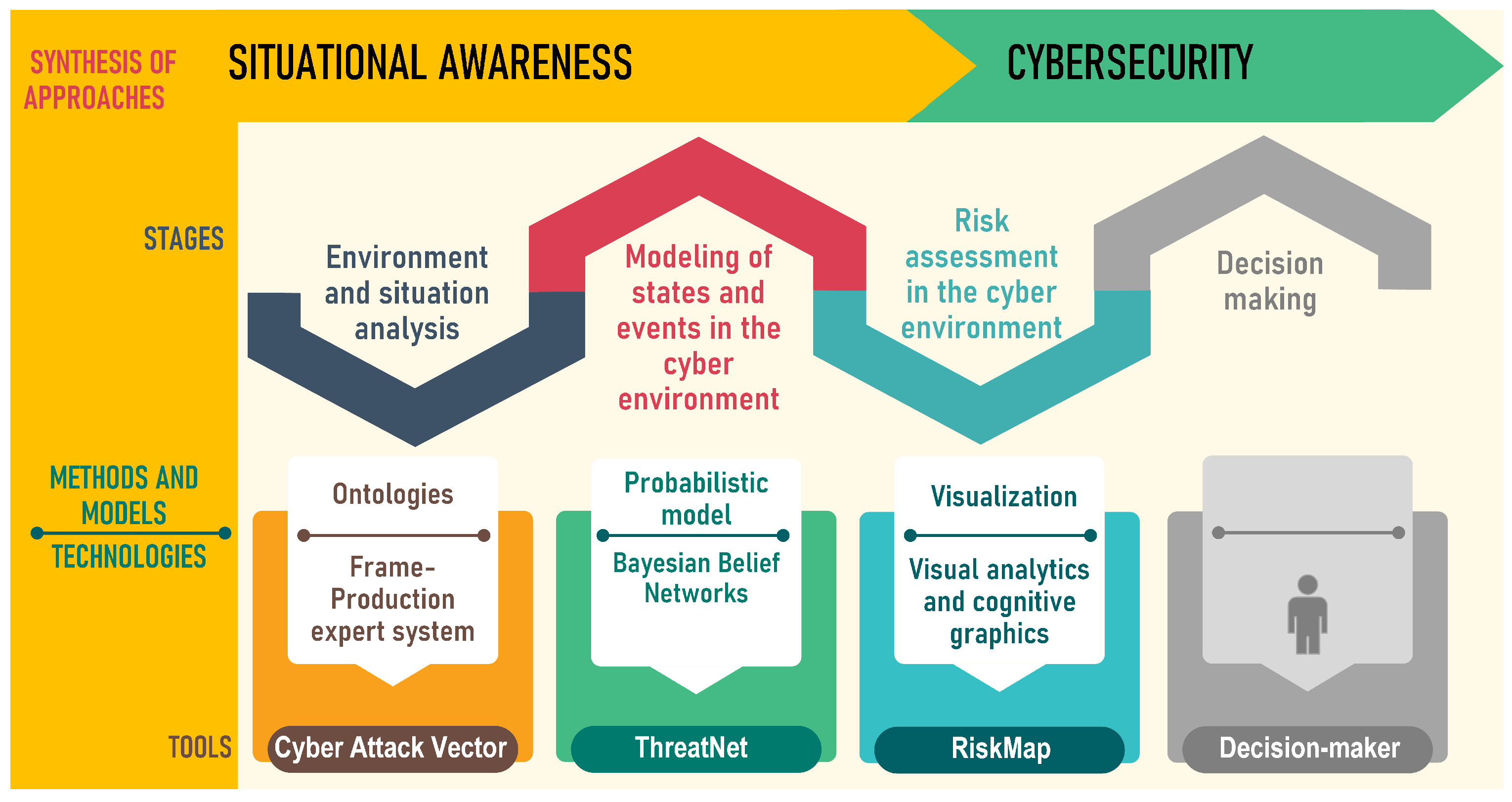
The scheme in Figure 3 shows the building of a knowledge representation model for threat vectors in the cyber environment of an energy facility and the stages of the CSA analysis of the energy facility.
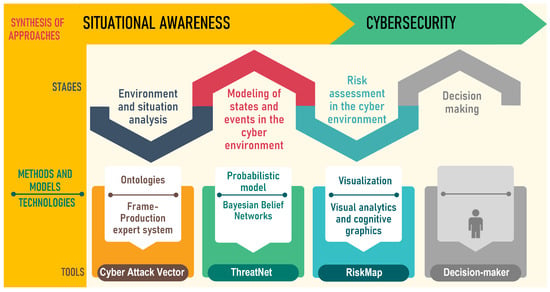
Figure 3.
Scheme of analysis stages of the CSA of an energy facility.
The analysis of cyber situational awareness of an energy facility is a rather complex task combining at least three areas of knowledge: (i) cybersecurity of an energy facility; (ii) the aspect of energy security associated with the emergence of technogenic threats (accidents, explosions and fires) due to the possibility of influencing the functioning of energy units and installations from the cyber environment; and (iii) an assessment of the current situation and a risk analysis and decision making on securing the assets of the cyber environment with means of protection. In this regard, three groups of experts have been identified: (i) specialists in the field of cyber security; (ii) energy experts; and (iii) analysts.
Table 2 presents the conditions for assessing extreme situations in the energy sector caused by cyber threats.

Table 2.
Conditions for assessing extreme situations in the energy sector caused by cyber threats.
The semantic modeling of threat vectors is aimed at identifying critical assets and formalizing ways to compromise them. The constructed models contribute to a better understanding and choice of security methods such as secure data links based on VPN, an emulator of the software operating environment (honeypot), a demilitarized zone for services and tools, increasing the computer literacy of the organization’s employees, etc. The task of selecting suitable security metrics is performed by the enterprise. The use of methods of system analysis and semantic modeling contributes to the selection of the necessary metrics for security assessment and decision making based on their results.
3. Conclusions
This article presents a study aimed at modeling possible illegitimate actions in the network and raising awareness about such behavior. Threat vectors to the cyber environment of an energy facility are built as a chain of possible interrelated events in the cyber environment under consideration in this regard. A Bayesian belief network allows the creation of such vectors and observation of the changes in the probability of possible events, turning them into security incidents.
Within the framework of a three-stage CSA analysis of an energy facility, it is planned to use topological metrics related to the number of vulnerabilities detected, the number of vulnerabilities involved in threat vectors, the complexity of their use of cyber threats, the number of vectors of attack development in the computer network and the amount of attacks on the target asset vectors. The joint use of safety metrics and approaches to assessing the adequacy and depth of models used in semantic modeling allow one to better improve the interaction of people involved in modeling and evaluate the quality of the resulting subjective model.
Author Contributions
Investigation, D.G.; methodology, D.G. and E.G.; software, D.G.; writing—original draft, D.G.; writing—review and editing, E.G. All authors have read and agreed to the published version of the manuscript.
Funding
The research was carried out under State Assignment Project (no. FWEU-2021-0003 and no. FWEU-2021-0007) of the Fundamental Research Program of Russian Federation 2021–2030 using the resources of the High-Temperature Circuit Multi-Access Research Center (Ministry of Science and Higher Education of the Russian Federation, project no 13.CKP.21.0038).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Edsley, M.R. Situation awareness global assessment technique (SAGAT). In Proceedings of the IEEE 1988 National Aerospace and Electronics Conference, Dayton, OH, USA, 23–27 May 1988; pp. 789–795. [Google Scholar]
- Frank, U.; Brynielsson, J. Cyber Situational Awareness—A systematic review of literature. Comput. Secur. 2014, 46, 18–31. [Google Scholar] [CrossRef]
- Bazrafkan, M.H.; Gharaee, H.; Enayati, A. National Cyber Situation Awareness Model. In Proceedings of the 2018 9th International Symposium on Telecommunications (IST), Tehran, Iran, 17–19 December 2018; pp. 216–220. [Google Scholar]
- Cheng, Y.; Deng, J.; Li, J.; DeLoach, S.A.; Singhal, A.; Ou, X. Metrics of Security. In Advances in Information Security; Springer: Berlin/Heidelberg, Germany, 2014; Volume 62, pp. 263–295. [Google Scholar]
- Flater, D. Bad Security Metrics Part 1: Problems. IT Prof. 2018, 20, 64–68. [Google Scholar] [CrossRef] [PubMed]
- Metrics. NIST Glossary. Available online: https://csrc.nist.gov/glossary/term/metrics (accessed on 4 August 2022).
- Flater, D. Bad Security Metrics Part 2: Solutions. IT Prof. 2018, 20, 76–79. [Google Scholar] [CrossRef] [PubMed]
- Kotenko, I.; Polubelova, O.; Saenko, I.; Doynikova, E. The Ontology of Metrics for Security Evaluation and Decision Support in SIEM Systems. In Proceedings of the 2013 International Conference on Availability, Reliability and Security, Regensburg, Germany, 2–6 September 2013; pp. 638–645. [Google Scholar]
- Ramos, A.; Lazar, M.; Filho, R.H.; Rodrigues, J. Model-Based Quantitative Network Security Metrics: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 2704–2734. [Google Scholar] [CrossRef]
- Abramova, N.A. Human factors in the cognitive approach. Manag. Large Syst. 2007, 16, 5–25. (In Russian) [Google Scholar]
- Massel, L.V.; Massel, A.G. Semantic technologies based on the integration of Ontological, Cognitive and Event modeling. In Proceedings of the III International Science and Technology Conference “OSTIS-2013”, Minsk, Belarus, 21–23 February 2013; pp. 247–250. (In Russian). [Google Scholar]
- Abramova, N.A. About some limitations of cognitive modeling methodology and ways to overcome them. In Proceedings of the 12th International Conference “Managing the Development of Large-Scale Systems” MLSD’2019, Moscow, Russia, 1–3 October 2019; pp. 335–337. (In Russian). [Google Scholar]
- Abramova, N.A.; Kovriga, S.V.; Portsev, R.Y. On the development of a reflexive approach to the analysis of the substantiation of subjective managerial decisions through cognitive modeling. Manag. Large Syst. Proc. 2018, 76, 26–68. (In Russian) [Google Scholar]
- Gavrilova, T.A.; Leshcheva, I.A. Building Collaborative Ontologies: A Human Factors Approach. In Collaborative Knowledge in Scientific Research Networks; IGI Publishing: Hershey, PA, USA, 2015; pp. 305–324. [Google Scholar]
- Lindley, D.V. The Philosophy of Statistics. J. R. Stat. Soc. Ser. D 2000, 49, 293–337. [Google Scholar] [CrossRef]
- Aven, T. Risk analysis and science. Int. J. Reliab. Qual. Saf. Eng. 2004, 11, 1–15. [Google Scholar] [CrossRef]
- Zografopoulos, I.; Ospina, J.; Liu, X.; Konstantinou, C. Cyber-Physical Energy Systems Security: Threat Modeling, Risk Assessment, Resources, Metrics, and Case Studies. IEEE Access 2021, 9, 29775–29818. [Google Scholar] [CrossRef]
- ISO. Online Browsing Platform. Available online: https://www.iso.org/obp/ui/#iso:std:iso-iec:27032:ed-1:v1:en:term:4.10 (accessed on 4 August 2022).
- Encyclopedia of Kaspersky. Targeted Attacks. Available online: https://encyclopedia.kaspersky.ru/glossary (accessed on 4 August 2022). (In Russian).
- Khan, M.S.; Siddiqui, S.; Ferens, K.A. Cognitive and Concurrent Cyber Kill Chain Model. In Computer and Network Security Essentials; Springer: Cham, Switzerland, 2018; pp. 585–602. [Google Scholar]
- Ramirez, C.; Valdes, B. A General Knowledge Representation Model of Concepts. In Advances in Knowledge Representation; IntechOpen: London, UK, 2012; pp. 3–76. [Google Scholar]
- Gaskova, D.A.; Massel, A.G. Modeling scenarios of extreme situations in the energy sector caused by cyber threats. In Proceedings of the International Conference of Young Scientists “Energy Systems Research” 2021, Irkutsk, Russia, 25–28 May 2021. [Google Scholar]
- SRA Glossary. Society for Risk Analysis Glossary. Available online: https://www.sra.org/wp-content/uploads/2020/04/SRA-Glossary-FINAL.pdf (accessed on 4 August 2022).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).