Implementation of Secure End-to-End Encrypted Chat Application Using Diffie–Hellman Key Exchange and AES-256 in a Microservice Architecture †
Abstract
1. Introduction
2. Literature Review
2.1. Previous Research
2.2. Microservice
2.3. Asymmetric Encryption
- Public Key: This key can be freely shared with anyone. It is used to encrypt data.
- Private Key: This key is confidential and known only to the recipient. It is used to decrypt data that has been encrypted with the public key.
- Symmetric encryption
- b.
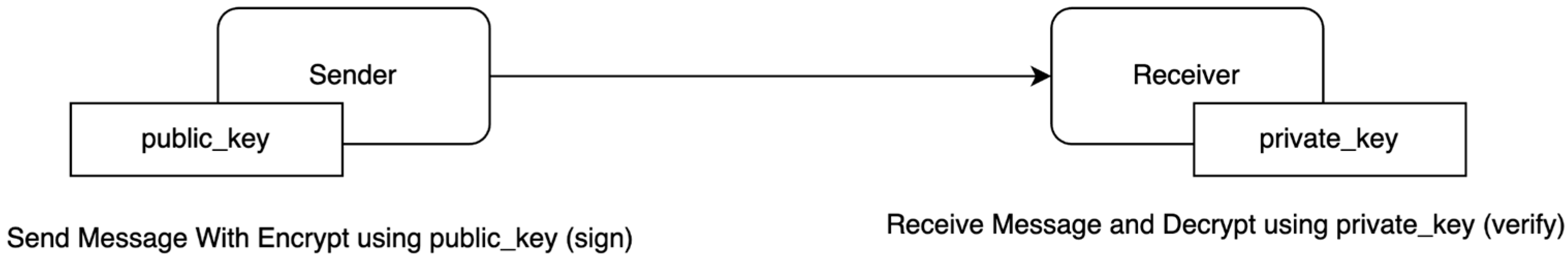
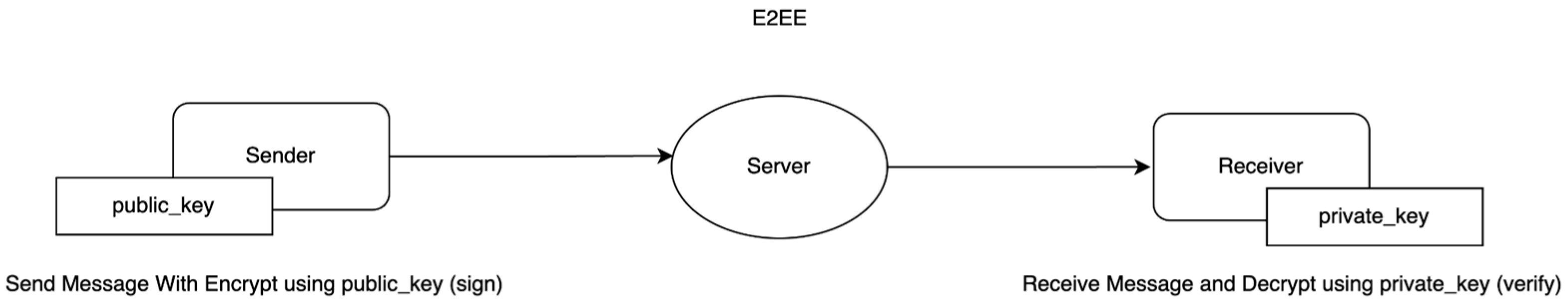
- End-to-End Encryption
- Sender:
- The sender encrypts the message using the receiver’s public key. This ensures that only the intended receiver, who possesses the corresponding private key, can decrypt the message.
- The encryption process transforms the original message into an encrypted format that is unreadable to unauthorized parties.
- 2.
- Server:
- The encrypted message is transmitted through a server or intermediary.
- The server only acts as a conduit for delivering the encrypted message and does not have the ability to decrypt it. This ensures that the content of the communication remains confidential even if the server is compromised.
- 3.
- Receiver:
- The receiver decrypts the message using their private key. The private key is kept secret and is mathematically linked to the public key used for encryption.
- Upon decryption, the original message is restored and can be read by the receiver.
- 4.
- Key Features:
- Public Key: shared openly and used by the sender to encrypt the message.
- Private Key: kept confidential by the receiver and used to decrypt the message.
- Confidentiality: only the receiver can decrypt and access the message content, ensuring secure communication.
- This system exemplifies the basic ideas of public-key cryptography, which is used in E2EE to protect communications while they are being sent.
- c.
- AES-256 (Advanced Encryption Standard)
- Symmetric Encryption Type:
- Advantages:
- High Security: AES-256 offers a very high level of security and is still considered safe against brute-force attacks.
- Speed: the AES is very fast, both in hardware and software implementations.
- Wide Adoption: the AES is used in many secure communication protocols such as HTTPS and VPNs.
- d.
- Diffie–Hellman (DH)
- Public Values:
- A prime number (P = 23) and a primitive root (g = 5) are agreed upon and shared publicly.
- 2.
- Private Keys:
- Alice chooses her private key a = 3
- Bob chooses his private key b = 7
- Both values are kept secret and never shared.
- 3.
- Public Computation:
- Alice computes her public value using:With a = 3, this results in A = 10.
- Bob computes his public value using:With b = 7, this results in B = 17.
- 4.
- Public Exchange:
- Alice and Bob exchange their public values over the insecure channel:
- 5.
- Shared Key Computation:
- Alice computes the shared key using Bob’s public value:
- Bob computes the shared key using Alice’s public value:
- Because of the properties of modular arithmetic, both results are identical, giving Alice and Bob the same shared secret key. Key = 14.
- e.
- ECDH (Elliptic Curve Diffie–Hellman)
- Key Steps in ECDH
- 1.
- Generate Key Pairs:
- ⃝
- Each party generates the following:
- Private Key: a large random number kept secret.
- Public Key: a point on the elliptic curve derived from the private key using the curve’s generator point GGG.
- 2.
- Exchange Public Keys:
- ⃝
- The two parties exchange their public keys over an insecure channel.
- 3.
- Compute Shared Secret:
- ⃝
- Both parties use their private key and the other party’s public key to compute the same shared secret due to the properties of elliptic curves:
- Shared Secret = , where and with G being the generator point of the elliptic curve. This ensures that both Alice and Bob arrive at the identical shared secret:
- Advantages of ECDH
- High Security with Smaller Keys: a 256-bit key in ECDH offers security equivalent to a 3072-bit key in classic Diffie–Hellman.
- Efficiency: computations on elliptic curves are faster and require less processing power.
- Wide Compatibility: ECDH is widely used in protocols like TLS/SSL, IPsec, and SSH.
- Mathematical Foundation
- Elliptic Curve Equation:
- where coordinates of a point on the curve. : curve parameters that
- Hard Problem: the Elliptic Curve Discrete Logarithm Problem (ECDLP) ensures security by making it computationally infeasible to derive the private key from the public key.
- Applications
- Secure Key Exchange in TLS/SSL: used to negotiate shared secrets for encrypted web communications (HTTPS).
- Symmetric Key Derivation: the shared secret is used to generate keys for symmetric encryption (e.g., AES).
- Security Considerations
- Confidentiality: private keys are never transmitted, ensuring secrecy.
- Authentication: to prevent man-in-the-middle attacks, ECDH is often combined with authentication methods like ECDSA.
- Standards and Libraries
- Standards: NIST P-curves (e.g., P-256, P-384) and RFC 7748 define common elliptic curves and implementation practices.
- Libraries: popular cryptographic libraries like OpenSSL, libsodium, and WebCrypto API provide ECDH implementations.
- Why ECDH Matters
3. Research Method
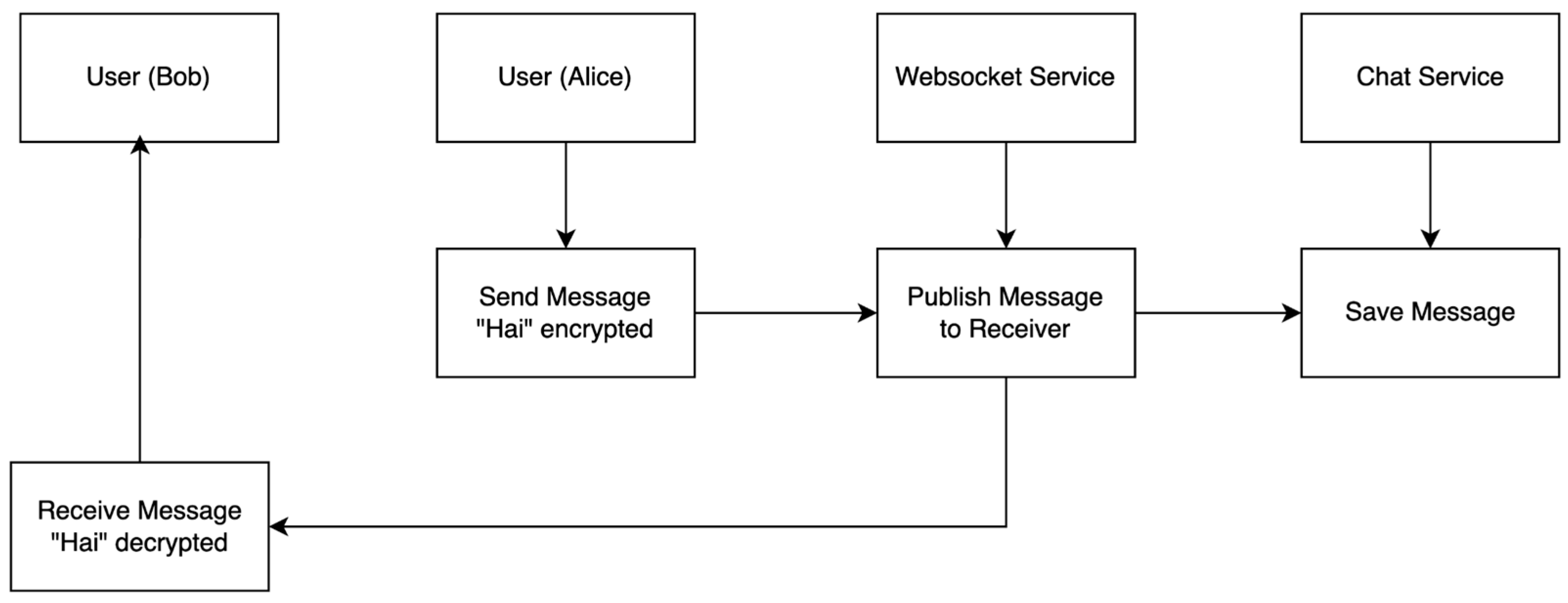
3.1. Implementing in Server
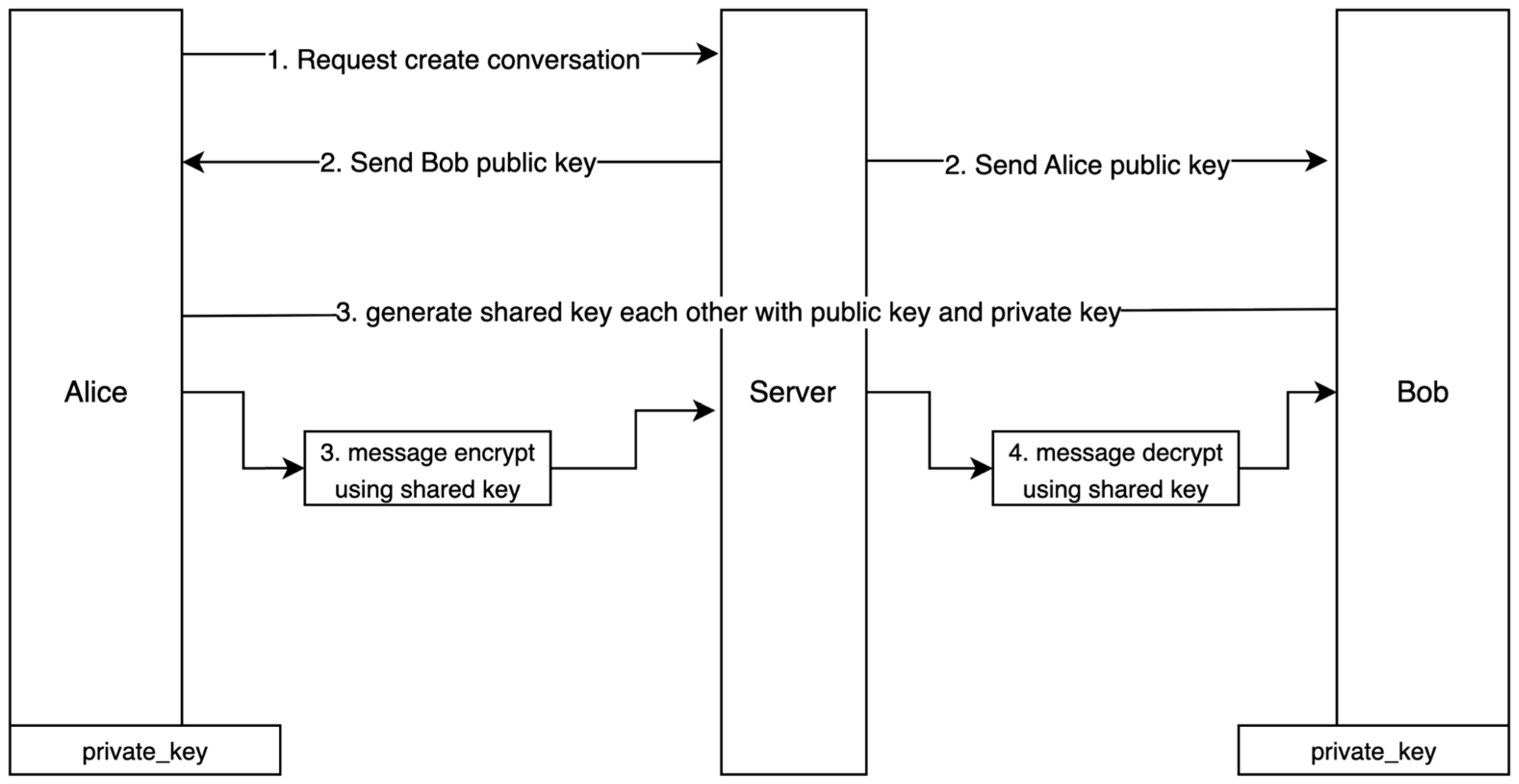
- Alice sends her public key to Bob: Alice shares her public key, allowing Bob to use this key in calculations to generate a shared key.
- Bob sends his public key to Alice: similarly, Bob shares his public key with Alice.
- Alice and Bob generate a shared key: Both parties use a combination of the received public key and their own private key to generate the same shared key. This shared key is then used for secure communication.
- Alice encrypts the message using the generated shared key.
- Bob then decrypts the message using the same shared key.
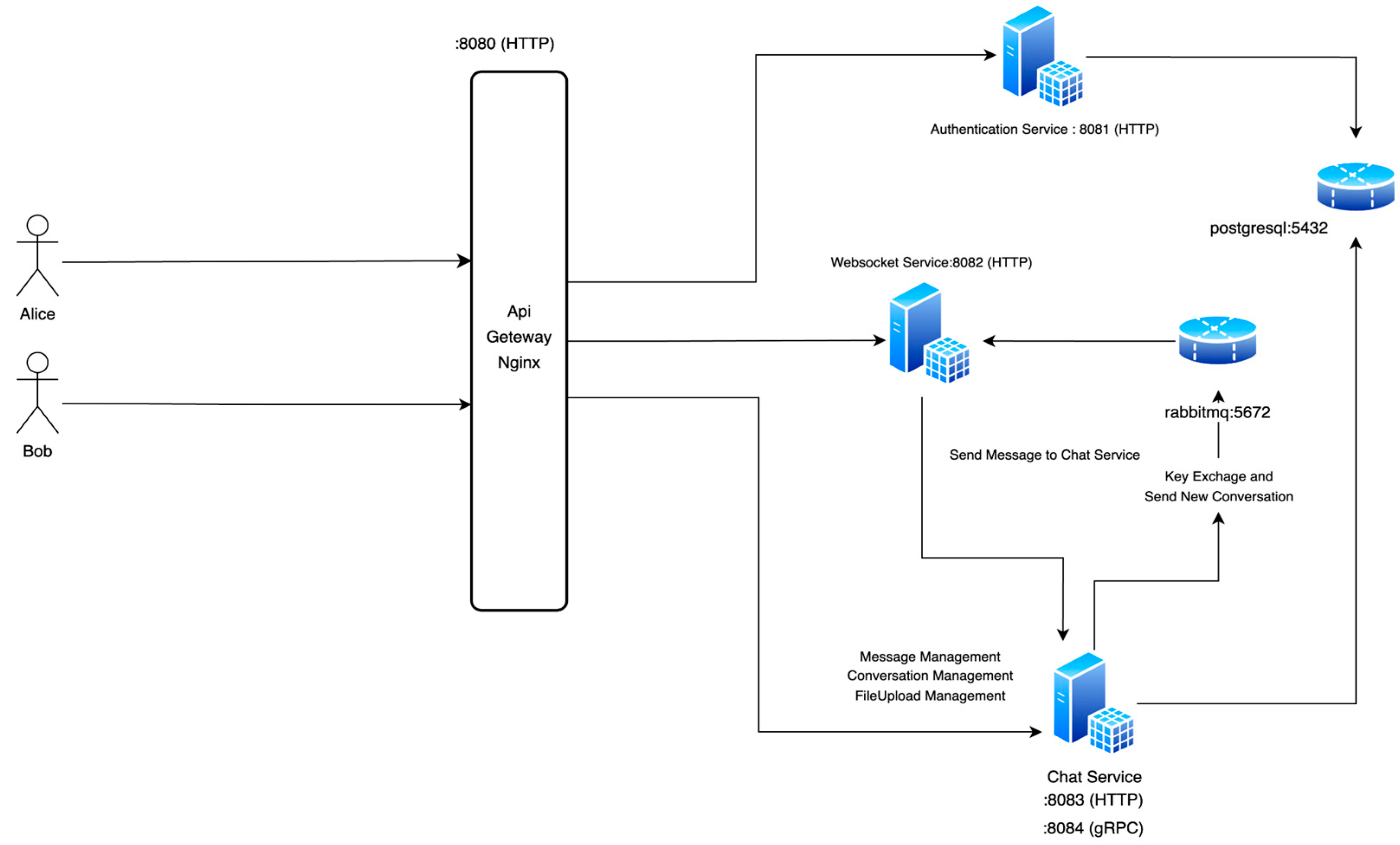
3.2. Designing Microservice Architecture
- Key Flowchart Highlights:
- User Request Flow:
- ⃝
- Alice and Bob initiate communication via a web/mobile client. Requests are first routed to the API Gateway.
- ⃝
- The API Gateway processes and routes the requests to the appropriate services:
- ▪
- Authentication Service for user verification.
- ▪
- WebSocket Service for establishing real-time communication.
- ▪
- Chat Service for message storage and retrieval.
- 2.
- Authentication Flow:
- ⃝
- The Authentication Service interacts with the PostgreSQL Database to validate credentials and issue JWT tokens.
- ⃝
- Upon successful authentication, the token is sent back through the API Gateway to the client.
- 3.
- Real-Time Communication Flow:
- ⃝
- The WebSocket Service establishes a persistent connection with clients, routing real-time messages securely between Alice and Bob.
- 4.
- Message Processing Flow:
- ⃝
- Messages sent by users are processed by the Chat Service, encrypted, and stored in the PostgreSQL Database.
- ⃝
- RabbitMQ facilitates communication between services, ensuring efficient delivery and handling of background tasks.
- 5.
- Scalability and Load Balancing:
- ⃝
- Multiple instances of services (e.g., Chat Service on ports 8083 and 8084) allow for load balancing and horizontal scaling to handle increased traffic and high concurrency.
- Key Architectural Features:
- Scalability:
- ⃝
- Modular design enables independent scaling of services to accommodate increased traffic.
- Real-Time Communication:
- ⃝
- The WebSocket Service ensures low-latency interactions between users.
- Security:
- ⃝
- JWT tokens for authentication.
- ⃝
- End-to-end encryption for chat messages.
- Reliability:
- ⃝
- PostgreSQL ensures data persistence, while RabbitMQ enhances communication robustness.
- Extensibility:
- ⃝
- Modular architecture allows the addition of new features, such as advanced analytics, AI–driven chatbots, or integration with third-party services.
3.3. Create User—Generate Asymmetric Key (Generate ECDH Public and Private Key)
3.4. Create Conversation—Key Exchange
3.5. Send and Receive Message
4. Result and Discussion
4.1. Create User
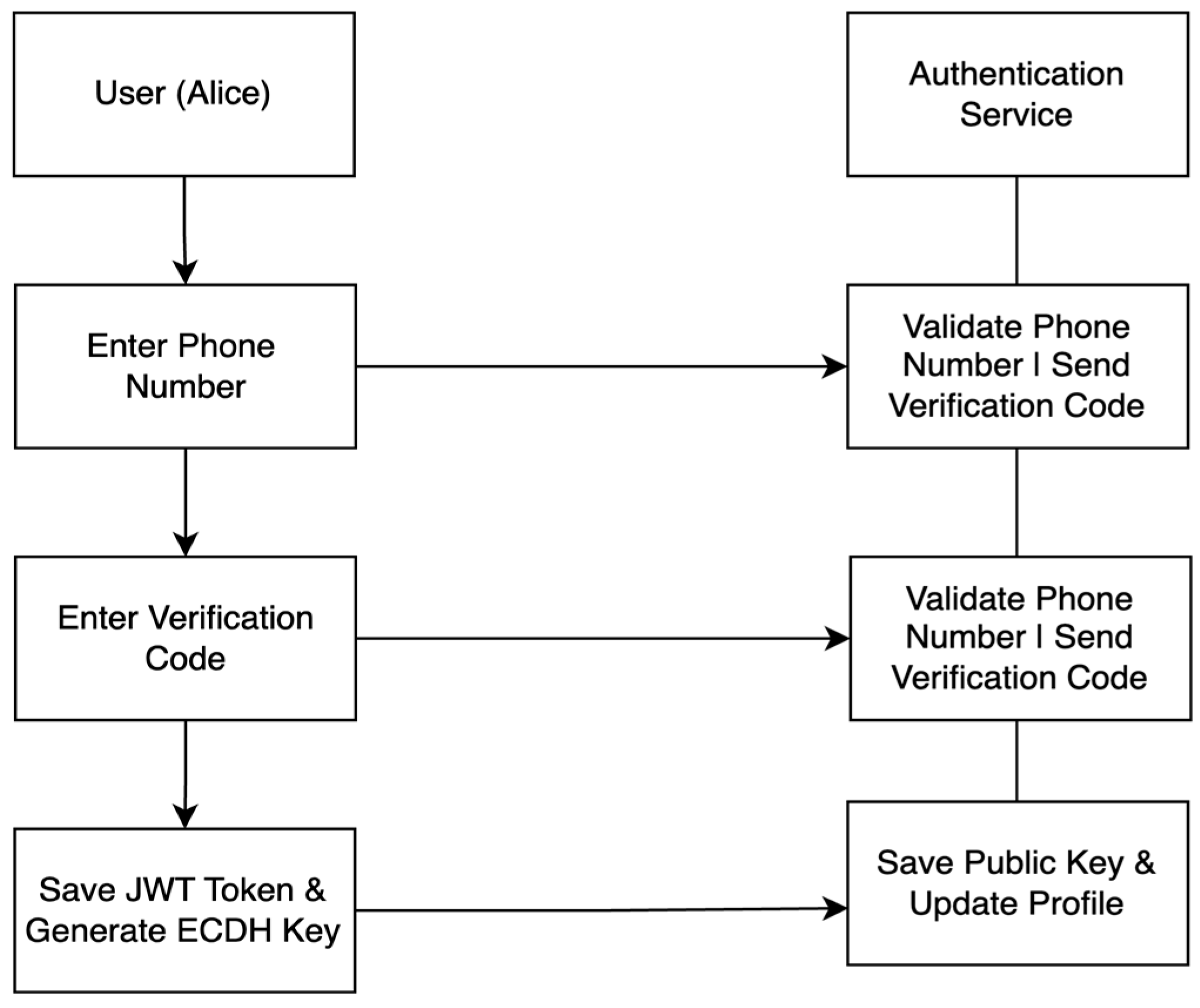
4.1.1. Login
4.1.2. Verification
4.1.3. JWT Token Generation and ECDH Key Generation
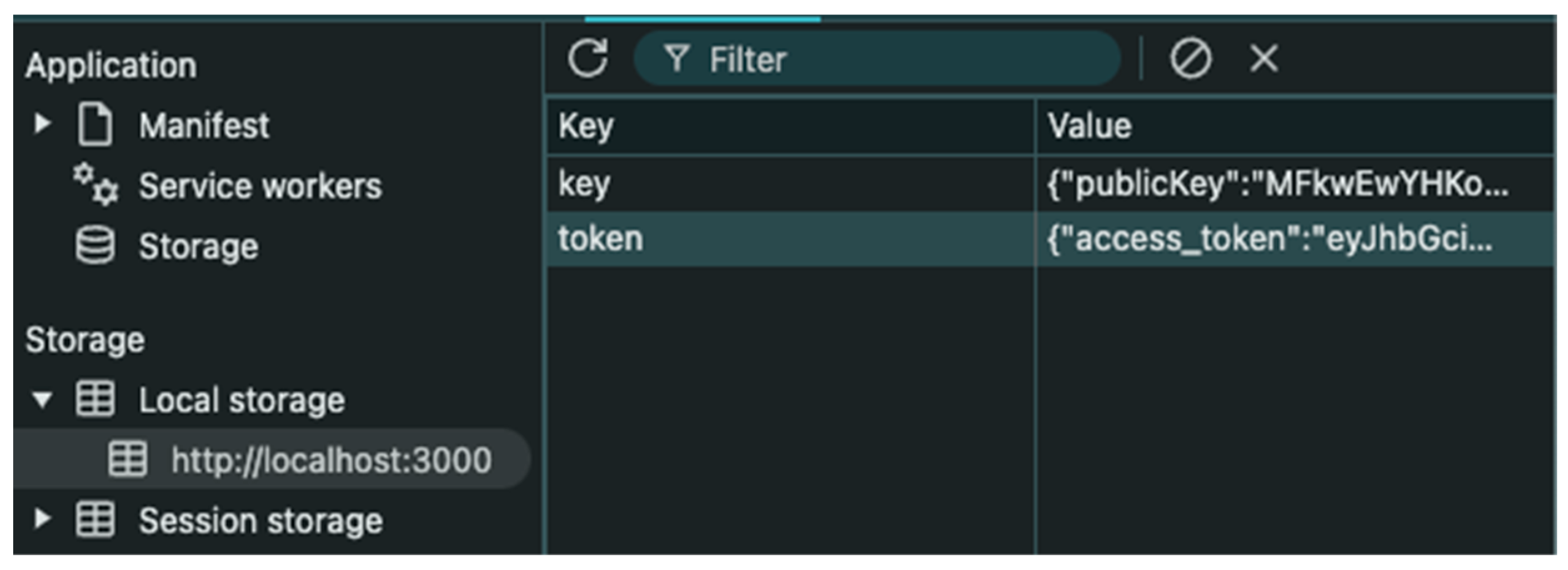
- Log: JWT and Public Key stored in local storage
| [INFO]—User entered verification code: 123456 [INFO]—Authentication service verified code and issued JWT token [INFO]—JWT Token generated: { “access_token”:“eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoiZjEwNTViMTQtNWU3OS00NWE5LTkxMmUtYjkxMDc4NWM0YzFkIiwiZXhwIjoxNzM3OTczNTM2fQ.9fjva92mWvMAGmSBhGwLqyuDnN7Qx74r2SYECCCfBOE”, “refresh_token”:“eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoiZjEwNTViMTQtNWU3OS00NWE5LTkxMmUtYjkxMDc4NWM0YzFkXzE3Mzc5Njk5MzYiLCJleHAiOjE3MzgwNTYzMzZ9.iAqN9p9gQ6YgFlFnohtB8hn3_XHF6rYb8bT8r-PF-9E”, “expires_in”:“2025-01-27T17:25:36.368513422+07:00”, “refresh_expires_in”:“2025-01-28T16:25:36.368518506+07:00” } [INFO]—ECDH key generation successful for user Alice [INFO]—Generated ECDH Key Pair: { “publicKey”:“MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEccxI69eSnTngR7PIJjRMCFecdizar8cTGqpH58CWoPBBqAYv3fHRSH/tOSvuqAuUr9RrYeEZEvFEkxN1ItKuuw==“, “privateKey”:“MIGHAgEAMBMGByqGSM49AgEGCCqGSM49AwEHBG0wawIBAQQgxVFHISjq6LF88Yi5VLg7yWeUTg5uOc8VxCxH4GipTfChRANCAARxzEjr15KdOeBHs8gmNEwIV5x2LNqvxxMaqkfnwJag8EGoBi/d8dFIf+05K+6oC5Sv1Gth4RkS8USTE3Ui0q67” } |
4.1.4. Send Public Key Chat Service
| { “name”: “Alice”, “picture”: “assets/icon.png”, “public_key”: “MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEccxI69eSnTngR7PIJjRMCFecdizar8cTGqpH58CWoPBBqAYv3fHRSH/tOSvuqAuUr9RrYeEZEvFEkxN1ItKuuw==“ } |
- Logs Server (Chat Service)
| 2025-01-29 22:54:37 Payload {“name”:“Alice”,”picture”:“assets/icon.png”,”public_key”:“MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEccxI69eSnTngR7PIJjRMCFecdizar8cTGqpH58CWoPBBqAYv3fHRSH/tOSvuqAuUr9RrYeEZEvFEkxN1ItKuuw==“} 2025-01-29 22:54:36 2025-01-29 22:54:51 [4.367ms] [rows:1] SELECT * FROM “users” WHERE uuid = ‘df98b75d-6261-442d-970b-caf982c9d4b3’ ORDER BY “users”.”id” LIMIT 1 2025-01-29 22:54:51 2025-01-29 22:54:51 2025/01/29 15:54:51 /usr/src/app/internal/repository/postgresql/user_repository.go:43 2025-01-29 22:54:51 [3.585ms] [rows:1] UPDATE “users” SET “uuid”=‘df98b75d-6261-442d-970b-caf982c9d4b3’,”name”=‘Test’,”picture”=‘assets/icon.png’,”phone_number”=‘0839873543’,”public_key”=‘MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAElg/ueB3TClDdqCwGCjqNcU/bdQiBzeTVwyWmeLYEyefRqeH8rU7TDe2GP7IOJclESXnUtnJhE0/DjH0ukJXfhw==‘,”status”=‘’,”created_at”=‘2025-01-29 15:54:04.142’ WHERE “id” = 8 2025-01-29 22:54:51 15:54:51 | 201 | 13.549375ms | 172.22.0.7 | PUT | /users | - |
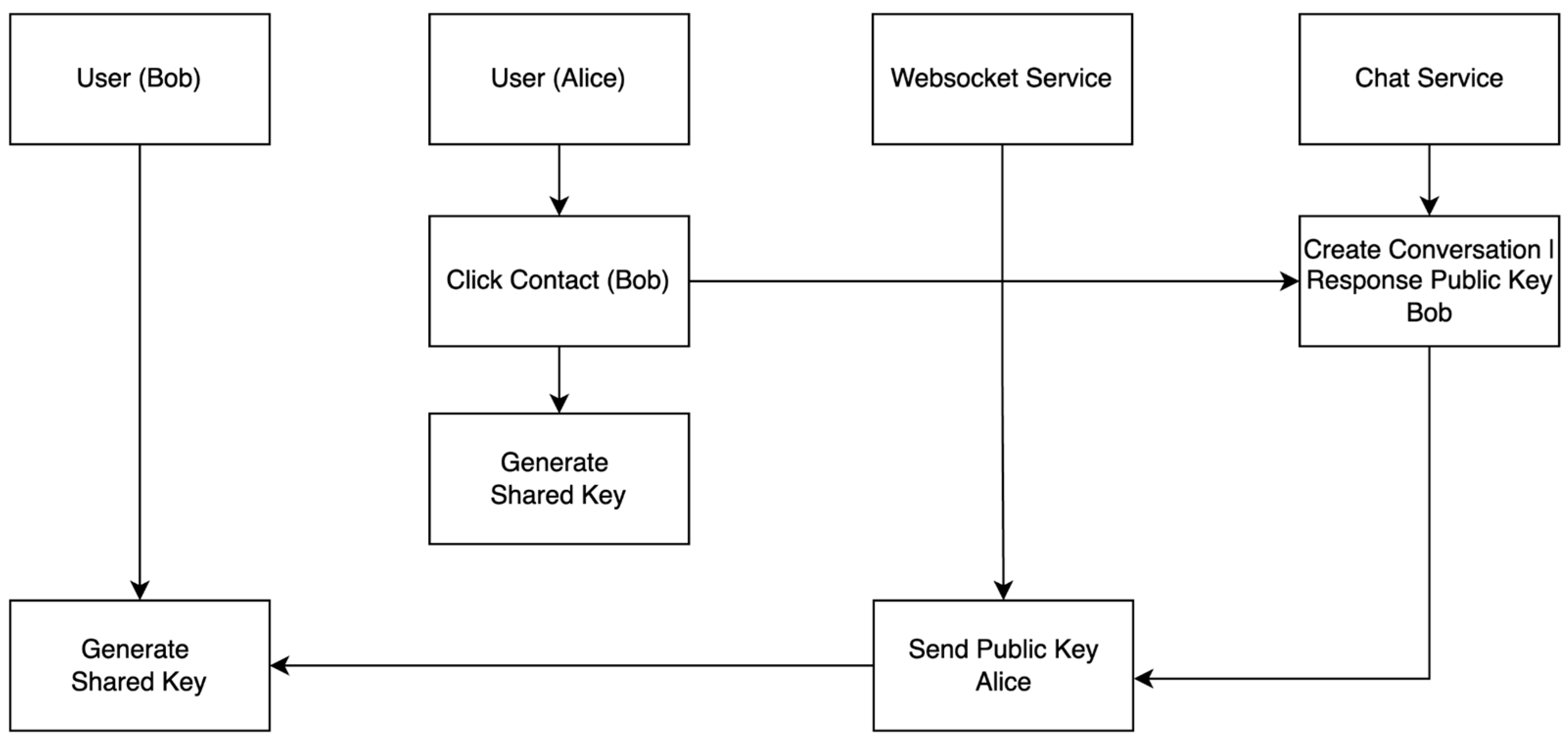
4.2. Key Exchange and Conversation Creation
- 1. User (Alice)
- Click Contact
- ⃝
- As shown in Figure 15, The user selects a contact (e.g., Bob) to start a conversation.
- Send Request and Key Exchange
- ⃝
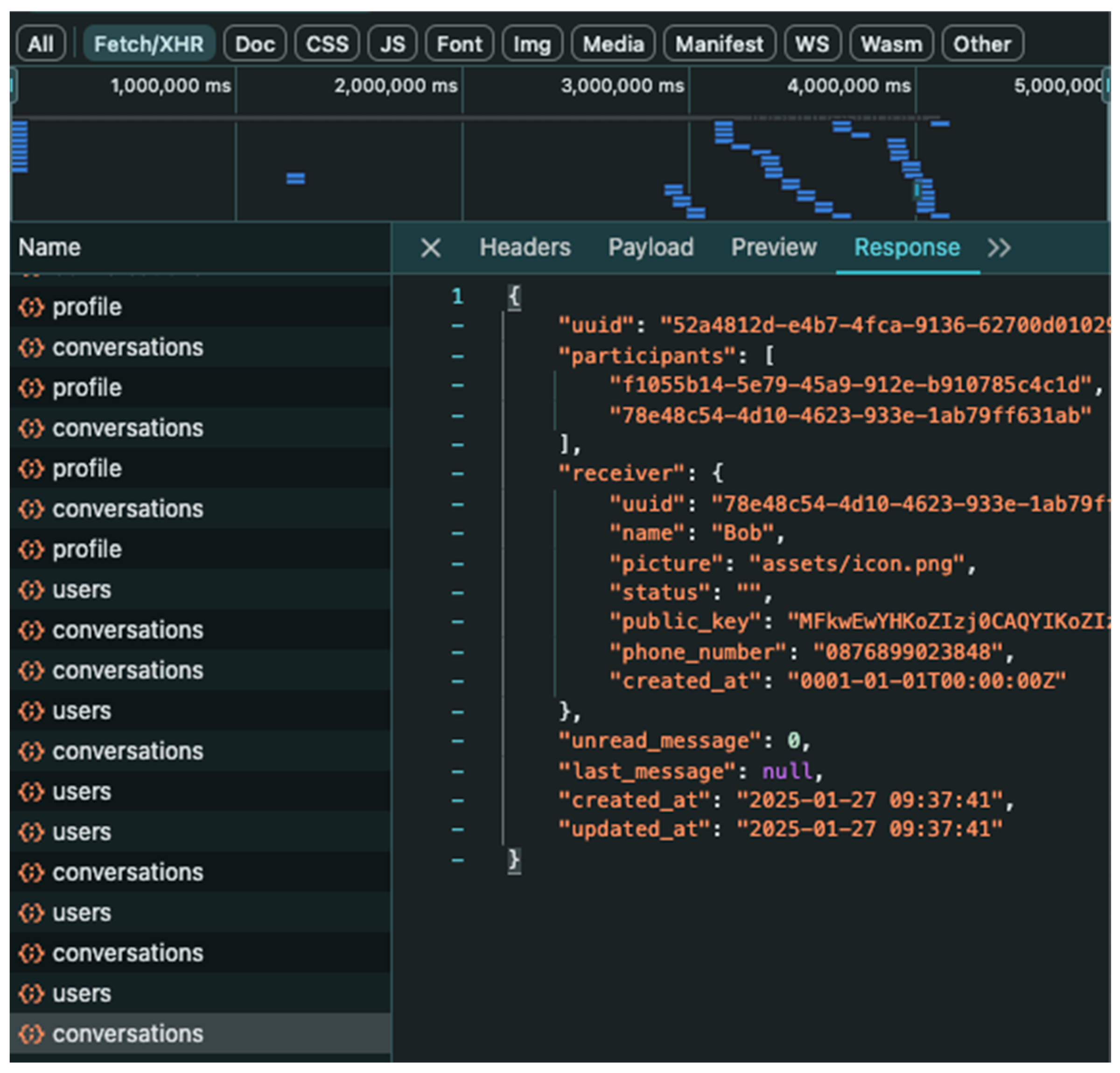
- As shown in Figure 16, Conversation and key exchange requests are sent to the server. The server sends Alice public key to be used as a shared key.
- Logs request for conversation creation (Chat Service)
| 2025-01-29 23:46:18 Payload { “participants”: [“”, “”] } 2025-01-29 23:46:18 [7.317ms] [rows:2] INSERT INTO “conversation_participants” (“conversation_id”,”user_id”) VALUES (27,8),(27,7) ON CONFLICT DO NOTHING 2025-01-29 23:46:18 2025-01-29 23:46:18 2025/01/29 16:46:18 /Users/mochjuang/projects/go/test-chat-telkomsel/chat-service/internal/repository/postgresql/conversation_repository.go:20 2025-01-29 23:46:18 [28.239ms] [rows:1] INSERT INTO “conversations” (“uuid”,”type”,”created_at”) VALUES (‘8c20c29d-396c-4ec3-80c4-f853f2a34e20’,’private’,’2025-01-29 16:46:18.556’) RETURNING “id” 2025-01-29 23:46:18 2025-01-29 23:46:18 16:46:18 | 201 | 59.713ms | 172.22.0.7 | POST | /conversations | - |
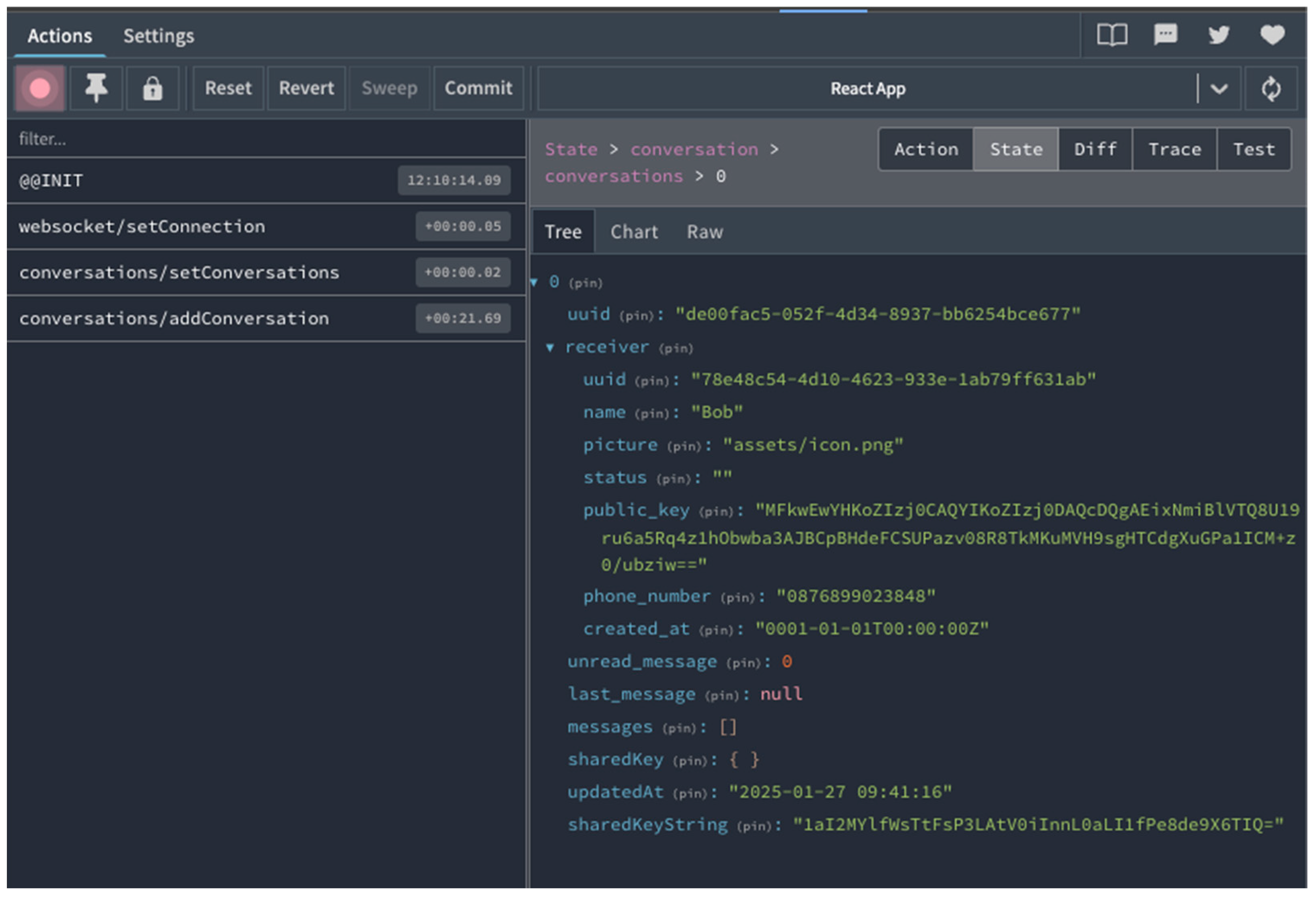
- Generate Shared Key and Encrypt using AES-CBC
- ⃝
- JS uses the public key received from the rest API to generate a shared key using ECDH.
- ⃝
- The shared key is then encrypted using AES-CBC before being used to encrypt subsequent messages.
- 2. Users (Bob)
- WebSocket Response
- Logs Server
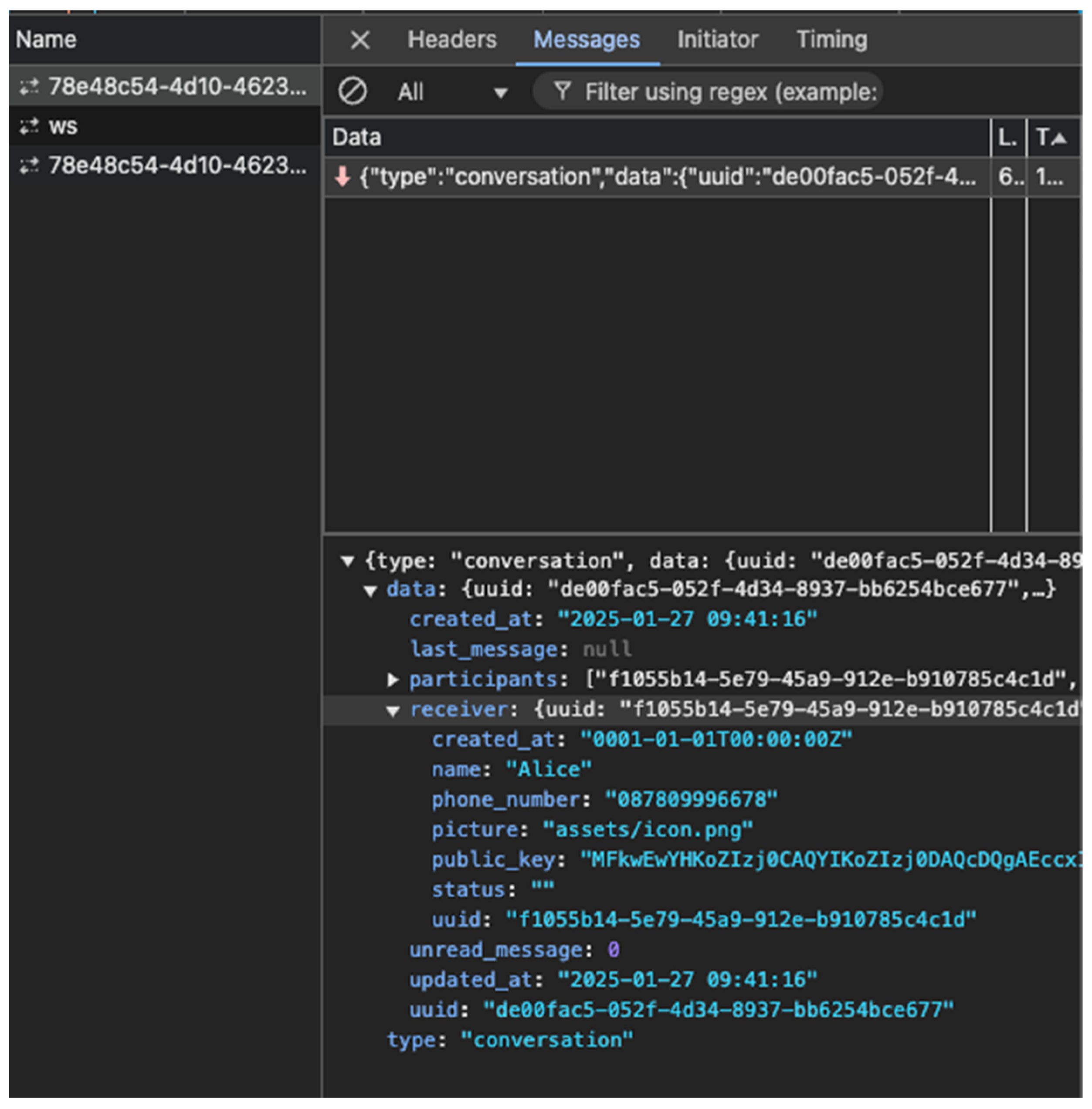
| 2025-01-29 23:46:18 [4.820ms] [rows:0] SELECT “messages”.”id”,”messages”.”uuid”,”messages”.”sender_id”,”messages”.”conversation_id”,”messages”.”content”,”messages”.”is_read”,”messages”.”send_at” FROM “messages” INNER JOIN conversations ON messages.conversation_id = conversations.id WHERE conversations.uuid = ‘8c20c29d-396c-4ec3-80c4-f853f2a34e20’ ORDER BY send_at asc LIMIT 30 2025-01-29 23:46:18 16:46:18 | 200 | 5.47625ms | 172.22.0.7 | GET | /conversations/8c20c29d-396c-4ec3-80c4-f853f2a34e20/messages | - 2025-01-29 23:46:18 2025/01/29 16:46:18 [x] Sent to conversation: {“uuid”:“8c20c29d-396c-4ec3-80c4-f853f2a34e20”,”participants”:[“6a6a700a-0637-4fff-abfd-a278c6a11cc3”,”df98b75d-6261-442d-970b-caf982c9d4b3”],”receiver”:{“uuid”:“df98b75d-6261-442d-970b-caf982c9d4b3”,”name”:“Test”,”picture”:“assets/icon.png”,”status”:“”,”public_key”:“MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAElg/ueB3TClDdqCwGCjqNcU/bdQiBzeTVwyWmeLYEyefRqeH8rU7TDe2GP7IOJclESXnUtnJhE0/DjH0ukJXfhw==“,”phone_number”:“0839873543”,”created_at”:“0001-01-01T00:00:00Z”},”unread_message”:0,”last_message”:null,”created_at”:“2025-01-29 16:46:18”,”updated_at”:“2025-01-29 16:46:18”} |
| 2025-01-29 23:46:18 2025/01/29 16:46:18 Received a message from conversation: {“uuid”:“8c20c29d-396c-4ec3-80c4-f853f2a34e20”,”participants”:[“6a6a700a-0637-4fff-abfd-a278c6a11cc3”,”df98b75d-6261-442d-970b-caf982c9d4b3”],”receiver”:{“uuid”:“df98b75d-6261-442d-970b-caf982c9d4b3”,”name”:“Test”,”picture”:“assets/icon.png”,”status”:“”,”public_key”:“MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAElg/ueB3TClDdqCwGCjqNcU/bdQiBzeTVwyWmeLYEyefRqeH8rU7TDe2GP7IOJclESXnUtnJhE0/DjH0ukJXfhw==“,”phone_number”:“0839873543”,”created_at”:“0001-01-01T00:00:00Z”},”unread_message”:0,”last_message”:null,”created_at”:“2025-01-29 16:46:18”,”updated_at”:“2025-01-29 16:46:18”} 2025-01-29 23:46:18 2025/01/29 16:46:18 jobing message to 1 users: {“type”:“conversation”,”data”:{“uuid”:“8c20c29d-396c-4ec3-80c4-f853f2a34e20”,”participants”:[“6a6a700a-0637-4fff-abfd-a278c6a11cc3”,”df98b75d-6261-442d-970b-caf982c9d4b3”],”receiver”:{“uuid”:“df98b75d-6261-442d-970b-caf982c9d4b3”,”name”:“Test”,”picture”:“assets/icon.png”,”status”:“”,”public_key”:“MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAElg/ueB3TClDdqCwGCjqNcU/bdQiBzeTVwyWmeLYEyefRqeH8rU7TDe2GP7IOJclESXnUtnJhE0/DjH0ukJXfhw==“,”phone_number”:“0839873543”,”created_at”:“0001-01-01T00:00:00Z”},”unread_message”:0,”last_message”:null,”created_at”:“2025-01-29 16:46:18”,”updated_at”:“2025-01-29 16:46:18”}} |
- Generate Shared Key and Encrypt using AES-CBC
- ⃝
- JS uses the public key received from the WebSocket to generate a shared key using ECDH.
- ⃝
- The shared key is then encrypted using AES-CBC before being used to encrypt subsequent messages.
4.3. Message Encryption and Sending to WebSocket
- 1. Submit Message (Alice)
- 2. Encrypt Message with Shared Key (AES-256 CBC)
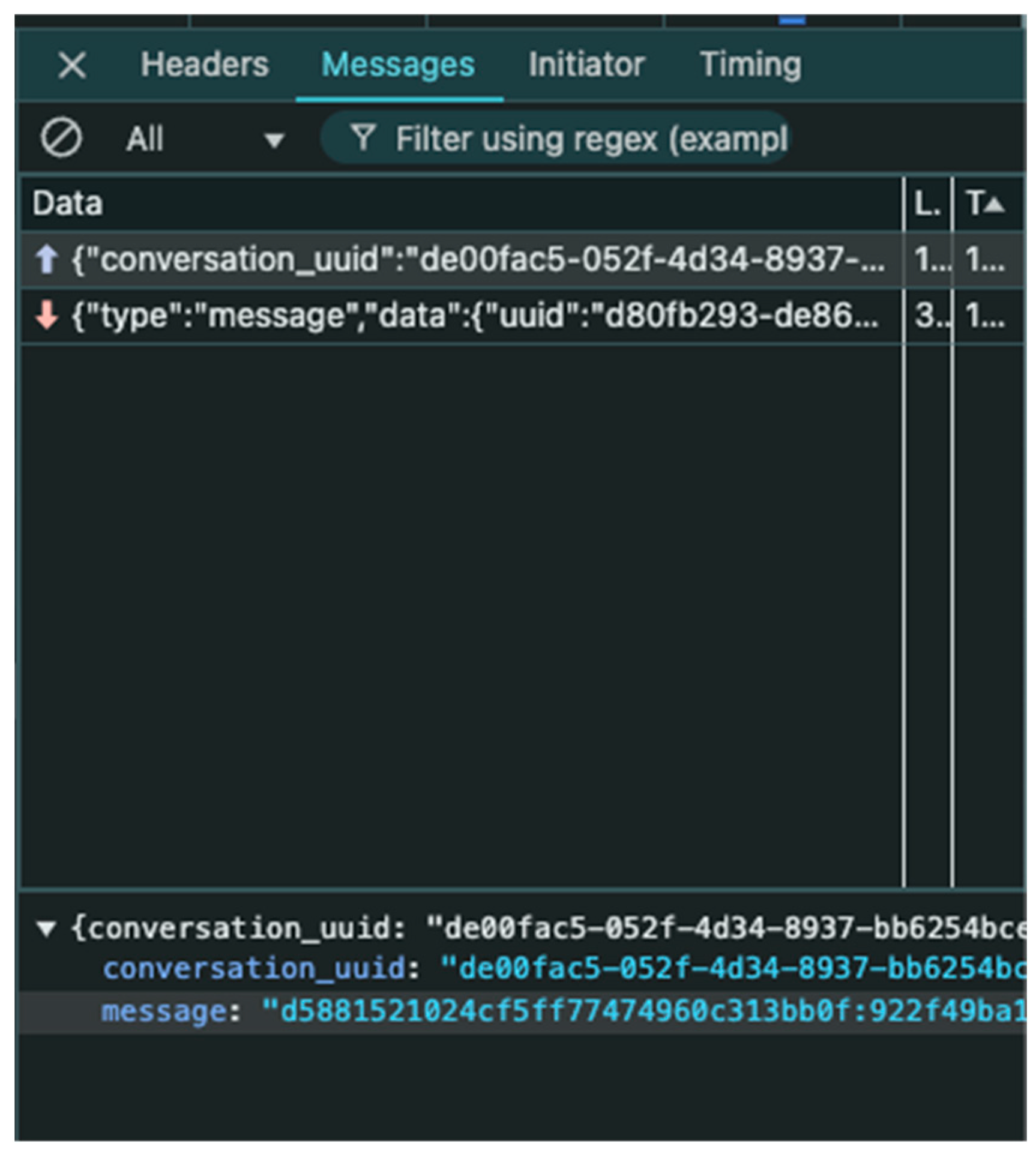
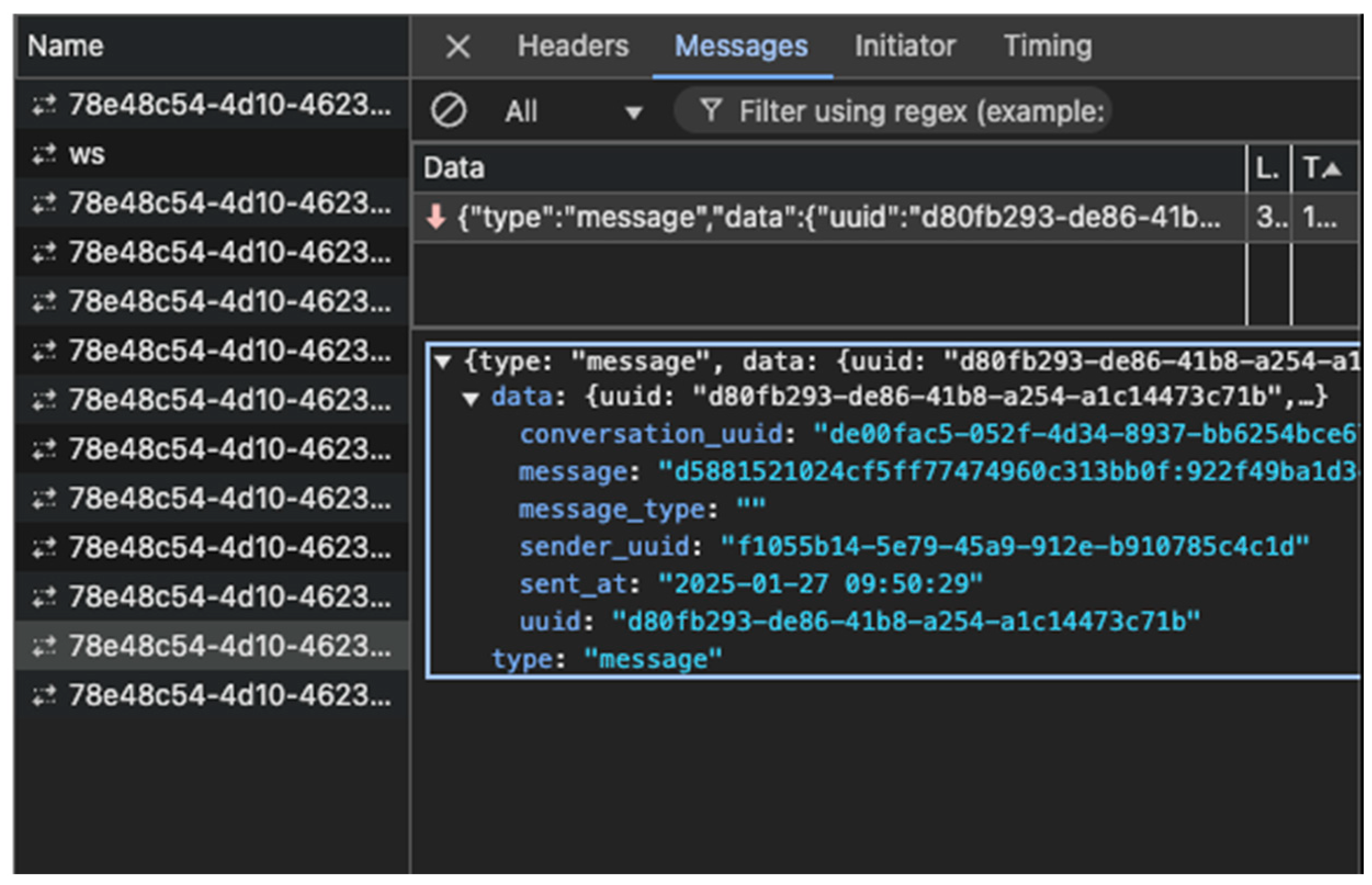
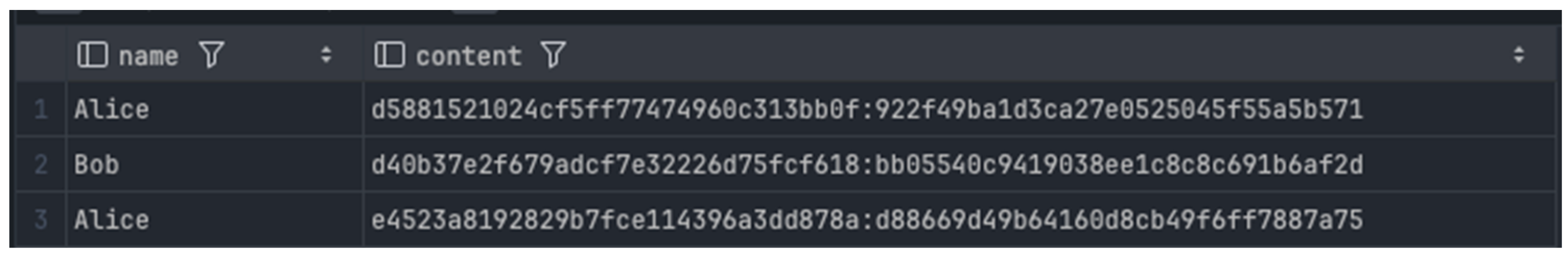
| 2025-01-30 00:15:14 (service) Process message: {e4523a8192829b7fce114396a3dd878a:d88669d49b64160d8cb49f6ff7887a75 de00fac5-052f-4d34-8937-bb6254bce677} 2025-01-30 00:15:14 (service) Send Message: {e4523a8192829b7fce114396a3dd878a:d88669d49b64160d8cb49f6ff7887a75 de00fac5-052f-4d34-8937-bb6254bce677} 2025-01-30 00:15:14 (service) Get conversation: {e4523a8192829b7fce114396a3dd878a:d88669d49b64160d8cb49f6ff7887a75 de00fac5-052f-4d34-8937-bb6254bce677} 2025-01-30 00:15:14 (service) Get conversation: de00fac5-052f-4d34-8937-bb6254bce677 |
- 3. Send Encrypted Message via WebSocket
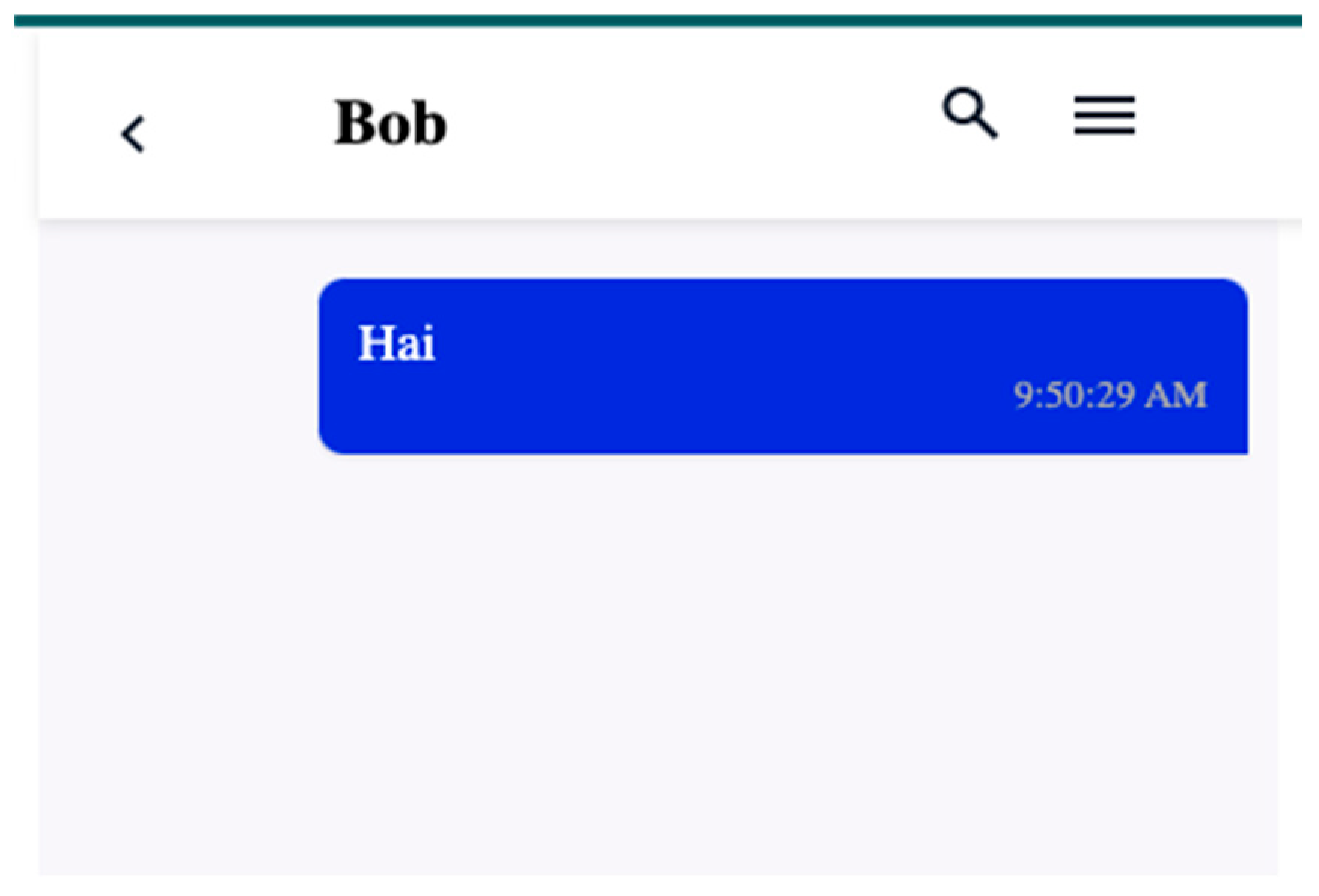
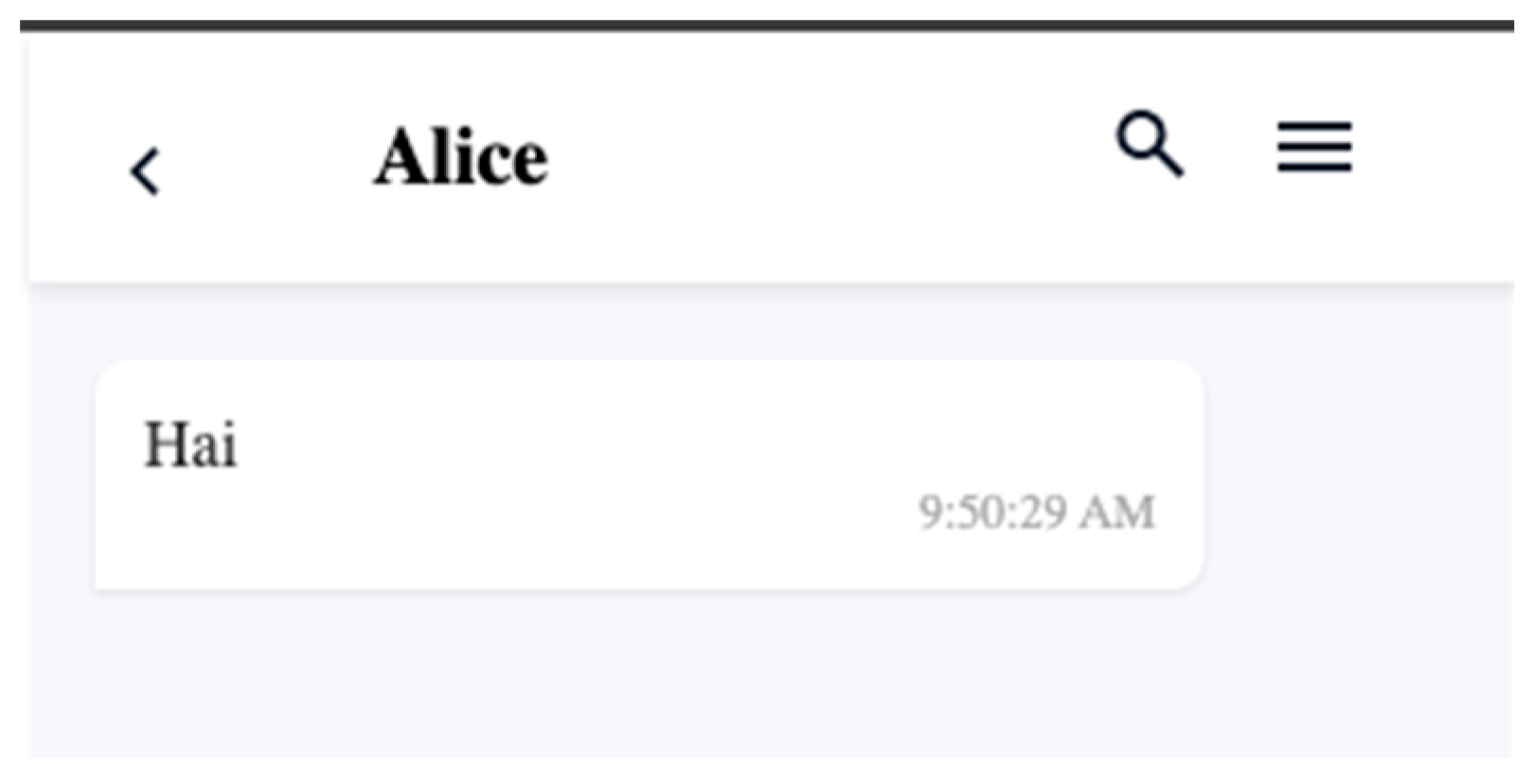
- 4. Decrypt Message on Receiving Side (Bob)
- Logs Server (WebSocket Service)
| 2025-01-30 00:15:14 2025/01/29 17:15:14 Received message from user f1055b14-5e79-45a9-912e-b910785c4c1d: {“conversation_uuid”:“de00fac5-052f-4d34-8937-bb6254bce677”,”message”:“e4523a8192829b7fce114396a3dd878a:d88669d49b64160d8cb49f6ff7887a75”} 2025-01-30 00:15:14 2025/01/29 17:15:14 jobing message to 2 users: {“type”:“message”,”data”:{“uuid”:“39f7ccf8-afdb-46ce-901f-e34aa9ae2ab4”,”conversation_uuid”:“de00fac5-052f-4d34-8937-bb6254bce677”,”sender_uuid”:“f1055b14-5e79-45a9-912e-b910785c4c1d”,”sent_at”:“2025-01-29 17:15:14”,”message_type”:“”,”message”:“e4523a8192829b7fce114396a3dd878a:d88669d49b64160d8cb49f6ff7887a75”}} |
4.4. Benchmarking AES Encryption and Decryption Performance on Various Number of Messages
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Rivest, L.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Components. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Thönes, J. Microservices. IEEE Softw. 2015, 32, 116. [Google Scholar] [CrossRef]
- Ermoshina, K.; Musiani, F.; Halpin, H. End-to-End Encrypted Messaging Protocols: An Overview. In Internet Science. INSCI 2016; Springer: Cham, Switzerland, 2016; Volume 9934, pp. 244–254. [Google Scholar] [CrossRef]
- Shamir, A. New Directions in Cryptography. In Cryptographic Hardware and Embedded Systems—CHES 2001; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2162, p. 159. [Google Scholar] [CrossRef]
- Vaidehi, M.; Rabi, B.J. Design and Analysis of AES-CBC Mode for High Security Applications. In Proceedings of the Second International Conference on Current Trends in Engineering and Technology—ICCTET 2014, Coimbatore, India, 8 July 2014; pp. 499–502. [Google Scholar] [CrossRef]
- Simmons, G.J. Symmetric and Asymmetric Encryption. ACM Comput. Surv. 1979, 11, 305–330. [Google Scholar] [CrossRef]
- Torvekar, N.; Game, P.S. Microservices and Its Applications: An Overview. Int. J. Comput. Sci. Eng. 2019, 7, 803–809. [Google Scholar] [CrossRef]
- Baškarada, S.; Nguyen, V.; Koronios, A. Architecting Microservices: Practical Opportunities and Challenges. J. Comput. Inf. Syst. 2020, 60, 428–436. [Google Scholar] [CrossRef]
- Wei, P.; Wang, X.A.; Yang, X. Proxy Re-Encryption Schemes with Proxy Having Its Own Public/Private Keys. In Proceedings of the 2010 2nd International Workshop on Database Technology and Applications, Prague, Czech Republic, 7–9 July 2010; pp. 2–5. [Google Scholar] [CrossRef]
- Yassein, M.B.; Aljawarneh, S.; Qawasmeh, E.; Mardini, W.; Khamayseh, Y. Comprehensive Study of Symmetric Key and Asymmetric Key Encryption Algorithms. In Proceedings of the 2017 International Conference on Engineering and Technology (ICET), Antalya, Turkey, 21–23 August 2017. [Google Scholar]
- Mahalle, V.S.; Shahade, A.K. Enhancing the Data Security in Cloud by Implementing Hybrid (RSA & AES) Encryption Algorithm. In Proceedings of the 2014 International Conference on Power, Automation and Communication (INPAC), Maharashtra, India, 6–8 October 2014; pp. 146–149. [Google Scholar] [CrossRef]
- Endeley, R.E. End-to-End Encryption in Messaging Services and National Security—Case of WhatsApp Messenger. J. Inf. Secur. 2018, 9, 95–99. [Google Scholar] [CrossRef]
- Borcea, C.; Gupta, A.; Polyakov, Y.; Rohloff, K.; Ryan, G. PICADOR: End-to-End Encrypted Publish–Subscribe Information Distribution with Proxy Re-Encryption. Future Gener. Comput. Syst. 2017, 71, 177–191. [Google Scholar] [CrossRef]
- Utama, F.P.; Wijaya, G.; Faurina, R.; Vatresia, A. Implementasi Algoritma AES 256 CBC, Base 64, dan SHA 256 dalam. J. Teknol. Inf. Ilmu Komput. 2023, 10, 945–954. [Google Scholar] [CrossRef]
- Khalkar, K. Decentralized Chat Application Using Blockchain Technology. Int. J. Res. Appl. Sci. Eng. Technol. 2023, 11, 813–816. [Google Scholar] [CrossRef]
- Biswas, S. Diffie-Hellman Key Exchange in End-to-End Encryption (E2EE). Available online: https://shubhomoybiswas.medium.com/diffie-hellman-key-exchange-in-end-to-end-encryption-e2ee-2366e056661 (accessed on 25 December 2024).
- Van Nghi, N.; Trung, D.Q.; Thanh, D.T. Two Novel Variants of ECDH Key Exchange Protocol Using Schnorr Zero-Knowledge Proof. In Proceedings of the 2023 15th International Conference on Knowledge and Systems Engineering (KSE), Ha Noi, Vietnam, 18–20 October 2023. [Google Scholar]
- Azaim, M.H.; Sudiharto, D.W.; Jadied, E.M. Design and Implementation of Encrypted SMS on Android Smartphone Combining ECDSA-ECDH and AES. In Proceedings of the 2016 Asia Pacific Conference on Multimedia and Broadcasting (APMediaCast), Bali, Indonesia, 17–19 November 2016; pp. 18–23. [Google Scholar] [CrossRef]
- Vo, A.T. Elliptic Curve Cryptography—A New Approach to Public Key Cryptography. Int. J. Eng. Sci. Res. Technol. 2014, 3, 69–73. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Saepulrohman, A.; Negara, T.P. Implementation of Elliptic Curve Diffie-Hellman (ECDH) for Encoding Messages Becomes a Point on the GF(p). Int. J. Adv. Sci. Technol. 2020, 29, 3264–3273. [Google Scholar]
- Nadareishvili, I.; Mitra, R.; Mclarty, M.; Amundsen, M. Modular Supercomputing Architecture; O’Reilly: Sebastopol, CA, USA, 2022. [Google Scholar]
- Jiang, Y.; Zhang, N.; Ren, Z. Research on Intelligent Monitoring Scheme for Microservice Application Systems. In Proceedings of the 2020 International Conference on Intelligent Transportation, Big Data & Smart City (ICITBS), Vientiane, Laos, 11–12 January 2020; pp. 791–794. [Google Scholar] [CrossRef]
- Waseem, M.; Liang, P.; Shahin, M.; Di Salle, A.; Márquez, G. Design, Monitoring, and Testing of Microservices Systems: The Practitioners’ Perspective. J. Syst. Softw. 2021, 182, 111061. [Google Scholar] [CrossRef]
- Assafli, H.T.; Hashim, I.A. Security Enhancement of AES-CBC and Its Performance Evaluation Using the Avalanche Effect. In Proceedings of the 2020 3rd International Conference on Engineering Technology and Its Applications (IICETA), Al-Najaf, Iraq, 6–7 September 2020; pp. 7–11. [Google Scholar] [CrossRef]
- Yusfrizal, Y.; Meizar, A.; Kurniawan, H.; Agustin, F. Key Management Using Combination of Diffie-Hellman Key Exchange with AES Encryption. In Proceedings of the 2018 6th International Conference on Cyber and IT Service Management (CITSM), Parapat, Indonesia, 7–9 August 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Dahri, F.; El Hanafi, A.M.; Handoko, D.; Wulan, N. Implementation of Microservices Architecture in Learning Management System E-Course Using Web Service Method. Sinkron 2022, 7, 76–82. [Google Scholar] [CrossRef]





| No | Name | Role | Responsibilities |
|---|---|---|---|
| 1 | Alice and Bob | End-users of the chat application | Alice and Bob interact with the system through a web or mobile client to initiate communication. Their requests are routed to the backend via the API Gateway for further processing. |
| 2 | 1API Gateway (NGINX) | Acts as the entry point for all user requests. | Routes traffic to the appropriate backend service depending on the type of request (e.g., authentication, WebSocket connections, and chat messages). Real-Time Communication: upgrades HTTP connections to WebSocket for bi-directional communication. Load Balancing and Reverse Proxy: distributes traffic evenly across multiple backend services for high availability and ensures security |
| 3 | Authentication Service (Port 8081) | Handles user login, authentication, and authorization processes. | Credential Verification: verifies user credentials against the database (e.g., username and password). JWT Token Issuance: issues a JSON Web Token (JWT) to users upon successful authentication. Data Storage:
|
| 4 | WebSocket Service (Port 8082) | Facilitates real-time, bi-directional communication between users (Alice and Bob) using WebSocket connections. | Connection Management: establishes, maintains, and terminates WebSocket connections as required. Message Routing: routes encrypted messages between users in real-time. Intermediary Role: acts as the intermediary between clients (web or mobile) and the Chat Service, ensuring secure and low-latency communication. |
| 5 | Chat Service (Ports 8083/8084) | Responsible for managing chat-specific functionalities, such as processing messages, handling conversations, and supporting advanced features like file uploads. | Message Storage: stores encrypted chat messages in the PostgreSQL Database Conversation Management: manages user conversations, including threads and metadata (e.g., timestamps and status). Additional Features:
|
| 6 | PostgreSQL Database (Port 5432) | Centralized database for storing authentication data, chat messages, and other metadata. | Data Security: securely stores user authentication data and encrypted chat messages Persistence and Reliability: ensures that all chat data and user-related information are durable and retrievable. High Performance: supports high-volume read/write operations for real-time message delivery and user interaction. |
| 7 | RabbitMQ Message Broker (Port 5672) | Acts as a message broker to enable asynchronous communication between microservices | Handles queue-based message passing between the API Gateway, WebSocket Service, and Chat Service. Ensures decoupled communication for better system scalability and fault tolerance. Processes and prioritizes background tasks like message delivery confirmations and notifications. |
| No | Function | Responsibilities |
|---|---|---|
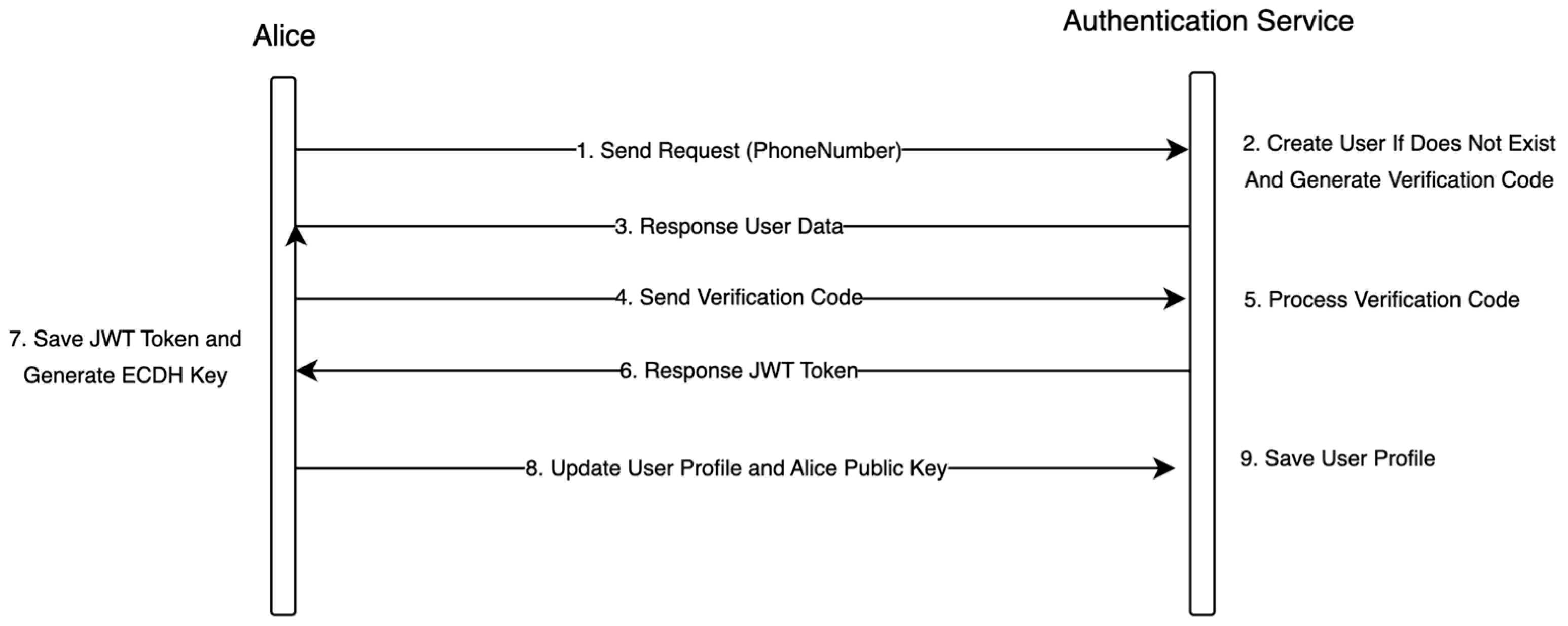
| 1 | User | Sends a request with a phone number to initiate the authentication process. |
| 2 | Authentication Service | Creates a user if they do not exist and generates a verification code for new or existing users. |
| 3 | Authentication Service | Sends user-related data as a response to the authentication request. |
| 4 | User | Sends the received verification code to verify the phone number. |
| 5 | Authentication Service | Processes and validates the verification code sent by the user. |
| 6 | Authentication Service | Sends a JWT token to authenticate the user after successful verification. |
| 7 | User | Saves the JWT token and generates an ECDH key to ensure secure communication. |
| 8 | User | Updates the user profile and sends Alice’s public key for encryption purposes. |
| 9 | Authentication Service | Stores the user profile for future authentication purposes. |
| No | Function | Responsibilities |
|---|---|---|
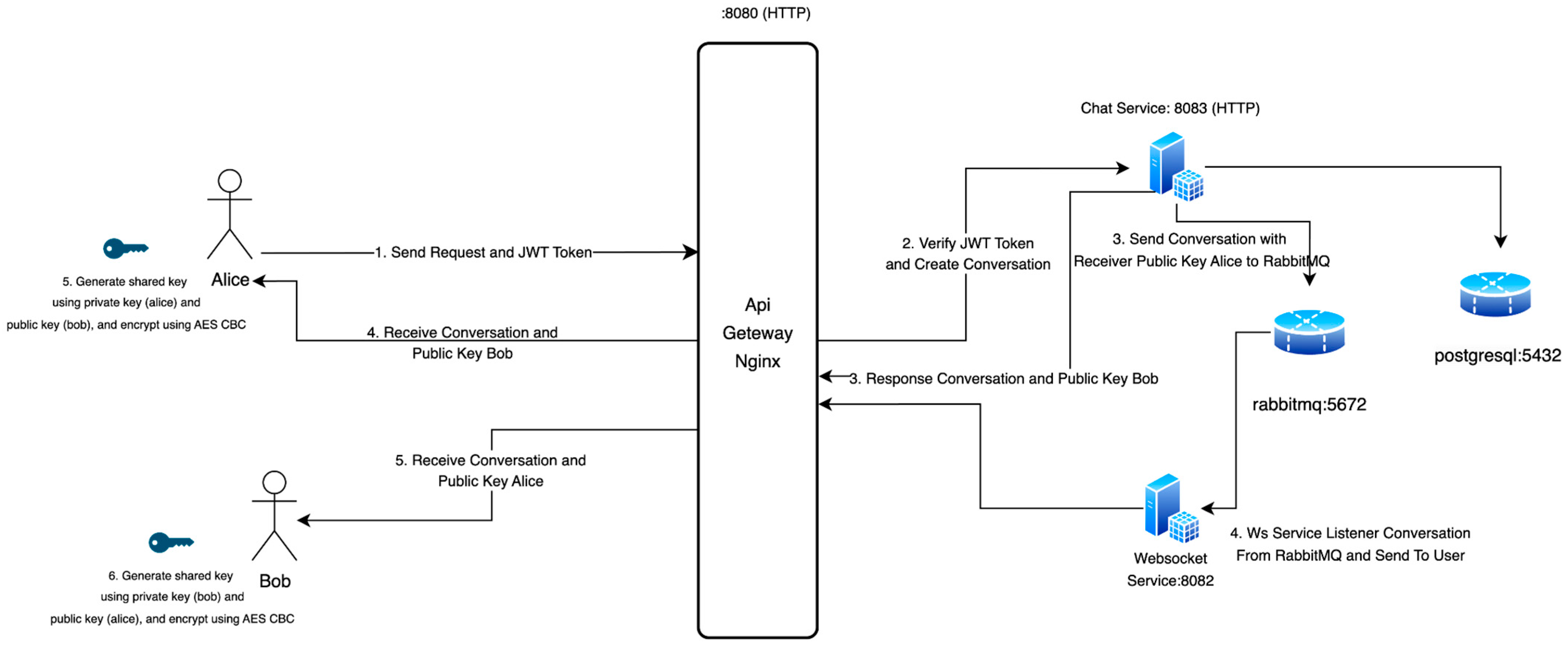
| 1 | User (Alice) | Sends request and JWT Token |
| 2 | Chat Service | Verifies JWT Token and creates conversation |
| 3 | Chat Service | Sends conversation and public key (Bob) to Alice |
| 4 | User (Alice) | Receives and stores conversation and public key (Bob) |
| 5 | User (Alice) | Generates a shared key using private key (Alice) and public key (Bob) and then encrypts using AES CBC |
| 3 | Chat Service | Sends conversation with public key (Alice) to RabbitMQ |
| 4 | WebSocket Service | WebSocket Service listener for conversation from RabbitMQ and sends to user (Bob) |
| 5 | User (Bob) | Receives conversation and public key Alice |
| 6 | User (Bob) | Generates a shared key using private key (Bob) and public key (Alice) and then encrypts using AES-256 CBC |
| No | Function | Responsibilities |
|---|---|---|
| 1 | Users (Alice) | Send JWT Token and user ID to authenticate and connect websocket. |
| 2 | WebSocket Service | Verify tokens and improve protocols for WebSocket communications. |
| 3 | WebSocket Service | Upgrade protocol to 101 real-time communication status. |
| 4 | Users (Alice) | Confirm protocol upgrade with status 101. |
| 5 | Users (Alice) | Send an encrypted chat message to user B using the shared key. |
| 6 | WebSocket Service | Process text requests and forward messages. |
| 7 | Chat Service | Save messages to the database. |
| 8 | Chat Service | Confirm that the message was saved successfully. |
| 9 | WebSocket Service | Send a message to user B’s connection. |
| 10 | Users (Bob) | Receive messages via WebSocket and decrypt them using a shared key. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Perkasa, M.J.P.; Ramdan, H.M.; Maliki, A.J.; Somantri. Implementation of Secure End-to-End Encrypted Chat Application Using Diffie–Hellman Key Exchange and AES-256 in a Microservice Architecture. Eng. Proc. 2025, 107, 98. https://doi.org/10.3390/engproc2025107098
Perkasa MJP, Ramdan HM, Maliki AJ, Somantri. Implementation of Secure End-to-End Encrypted Chat Application Using Diffie–Hellman Key Exchange and AES-256 in a Microservice Architecture. Engineering Proceedings. 2025; 107(1):98. https://doi.org/10.3390/engproc2025107098
Chicago/Turabian StylePerkasa, Moch Juang Pajri, Hari Muhammad Ramdan, Abdul Jabar Maliki, and Somantri. 2025. "Implementation of Secure End-to-End Encrypted Chat Application Using Diffie–Hellman Key Exchange and AES-256 in a Microservice Architecture" Engineering Proceedings 107, no. 1: 98. https://doi.org/10.3390/engproc2025107098
APA StylePerkasa, M. J. P., Ramdan, H. M., Maliki, A. J., & Somantri. (2025). Implementation of Secure End-to-End Encrypted Chat Application Using Diffie–Hellman Key Exchange and AES-256 in a Microservice Architecture. Engineering Proceedings, 107(1), 98. https://doi.org/10.3390/engproc2025107098






