Securing Keyboard Data Communication
Abstract
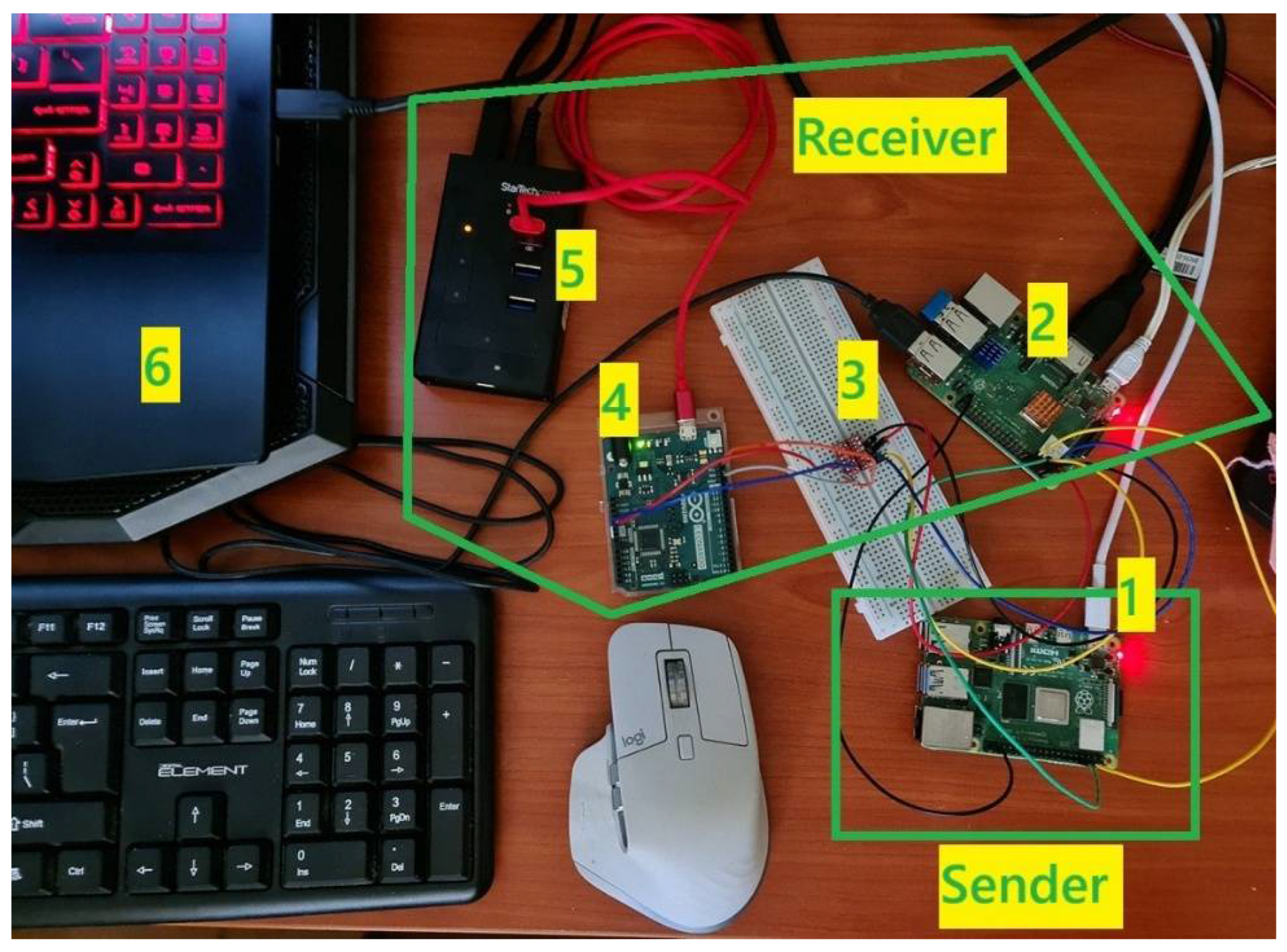
1. Introduction
- Fiber optic keyboard.
- AES-encrypted wired keyboard.
- Modified ECC-encrypted wired keyboard.
- XOR-encrypted wired keyboard.
- Spritz-encrypted wired keyboard.
- AES-encrypted wireless keyboard using Zigbee modules.
- Encrypted IR connection at 940 nm.
2. Related State of the Art
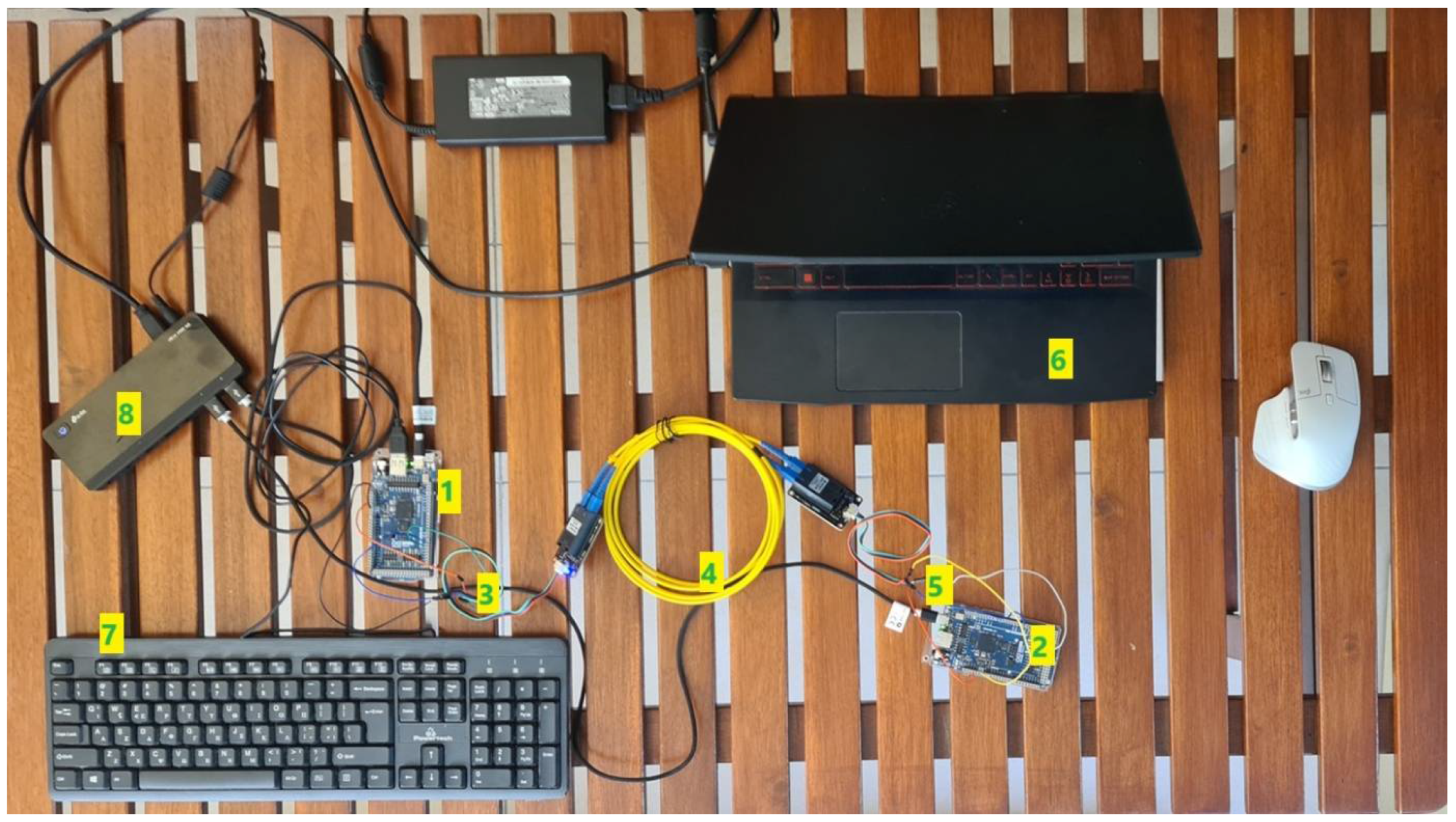
3. Fiber Optic Cable
- USB keyboard with US keys.
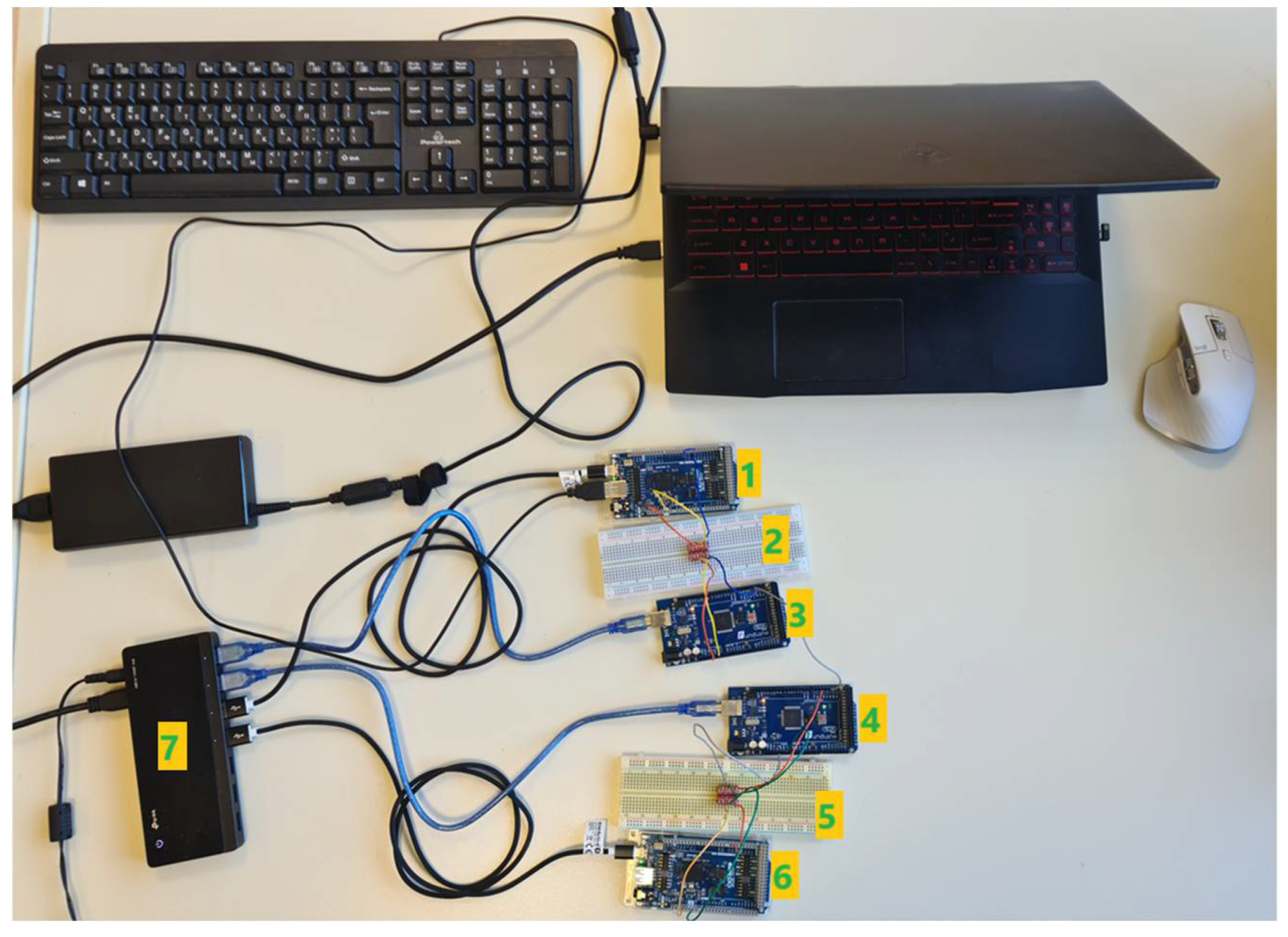
- two Arduino GIGA R1.
- two Single Core Fiber Optic cable (Connlink FO SC/SC 9/125 OS2 SM 2 m).
- two Gravity UART Fiber Optic Transceiver Module [20].
- two USB cables for supplying and programming the two Arduino.
- USB power hub.
- Laptop computer for reading the keys sent from the USB keyboard.
- Supply Voltage: 3.3 V~5 V.
- Signal Voltage: 3.3 V~5 V.
- Maximum Speed: 2,000,000 baud.
- Communication Distance: 10 km.
- Operating Wavelength: 1310 nm.
- Fiber Optic Type: Single Mode.
- Fiber Optic Interface: SC.
- Operating Temperature: 0~70 °C.
4. Encryption over Wired Communication
4.1. AES-Encrypted Wired Keyboard
4.2. Modified ECC-Encrypted Wired Keyboard
4.3. XOR-Encrypted Wired Keyboard
4.4. Spritz-Encrypted Wired Keyboard
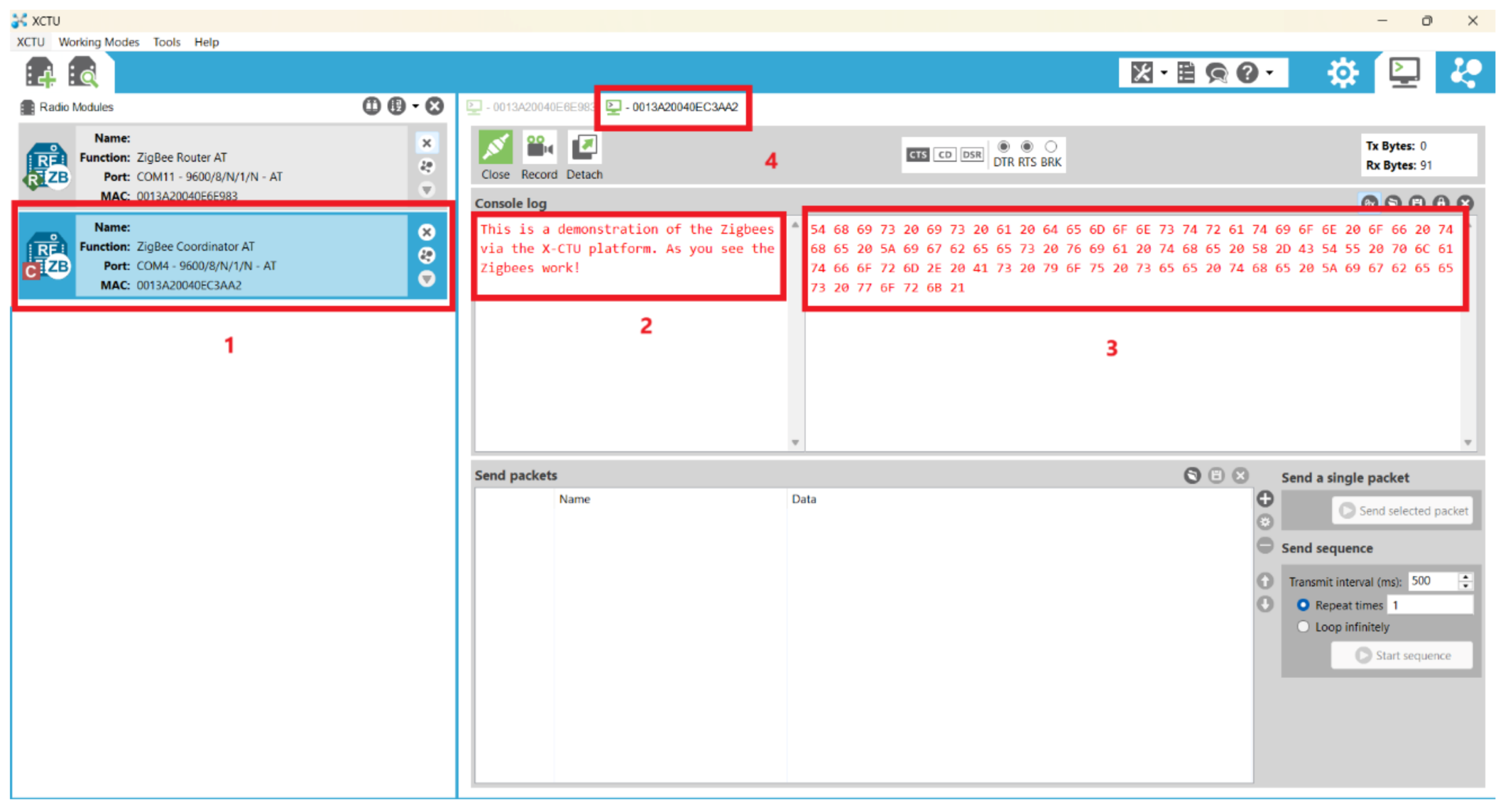
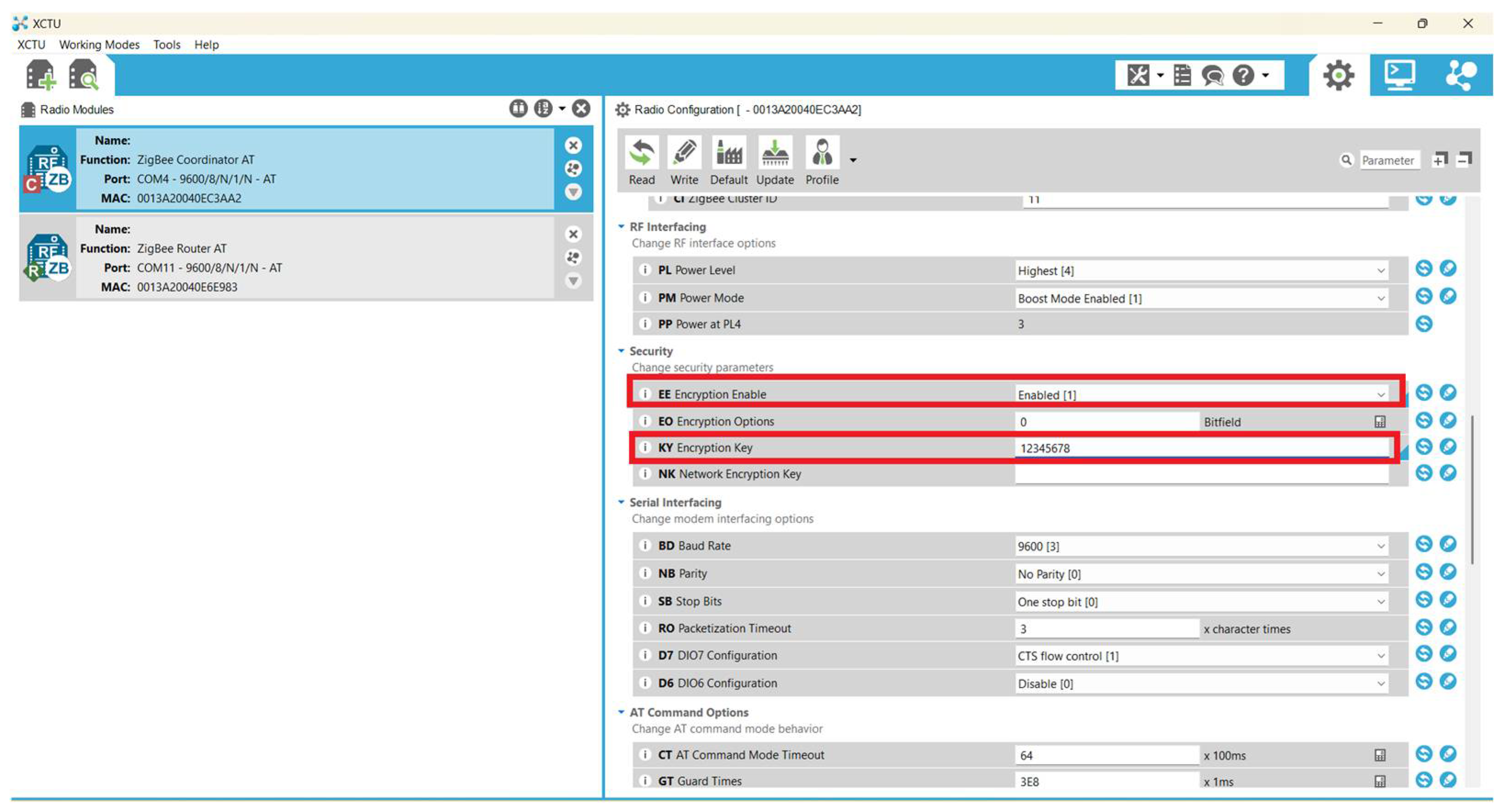
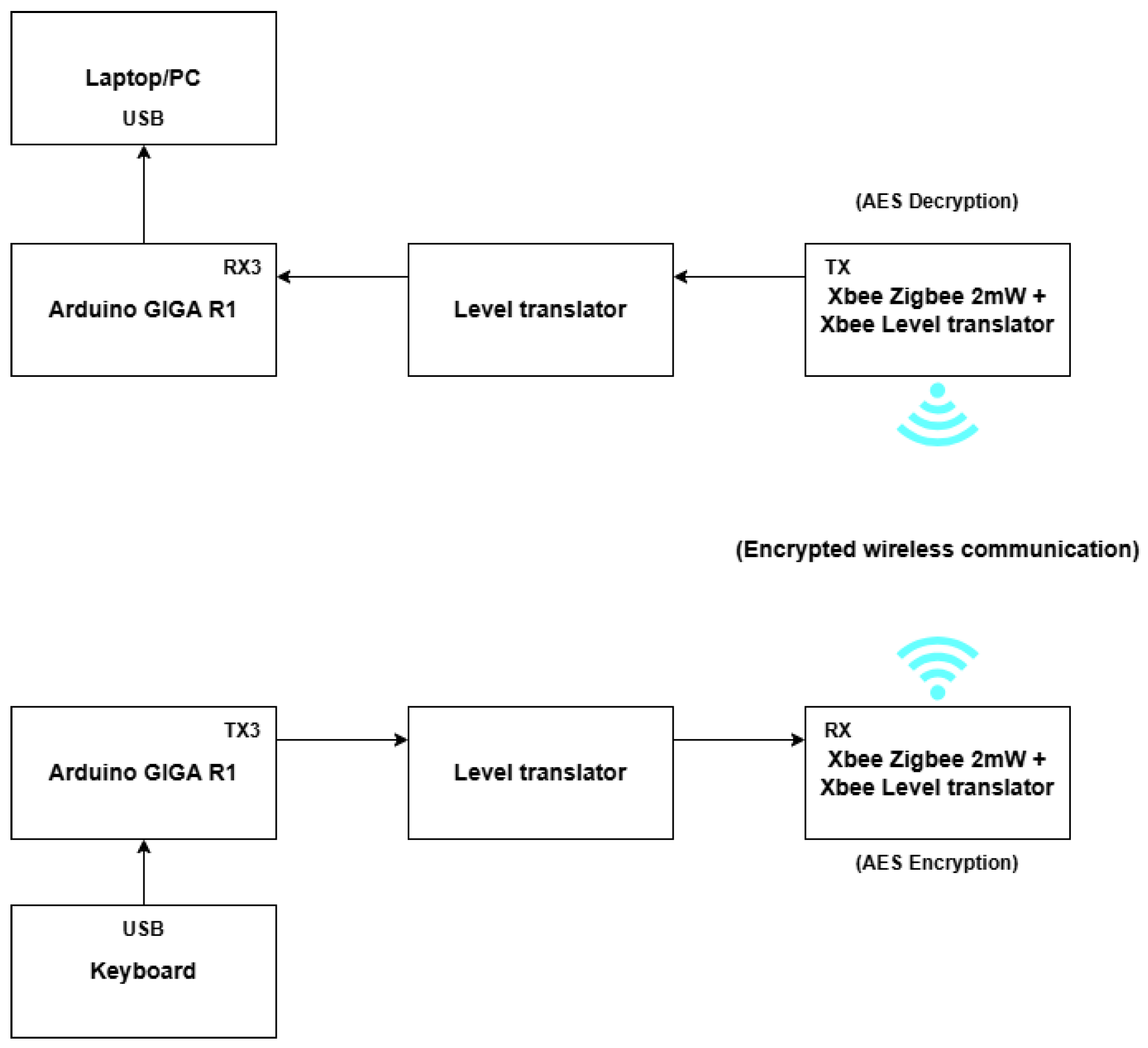
5. AES-Encrypted Wireless Keyboard Using Zigbee Modules
- 3.3 V @ 40 mA.
- 250 kbps Max data rate.
- 2 mW output (+3 dBm).
- 400 ft (120 m) range.
- Built-in antenna.
- Fully FCC-certified.
- Six 10 bit ADC input pins.
- Eight digital IO pins.
- 128 bit encryption.
- Local or over-air configuration.
- AT or API command set.
- (a)
- Point-to-Point.
- (b)
- Star.
- (c)
- Mesh.
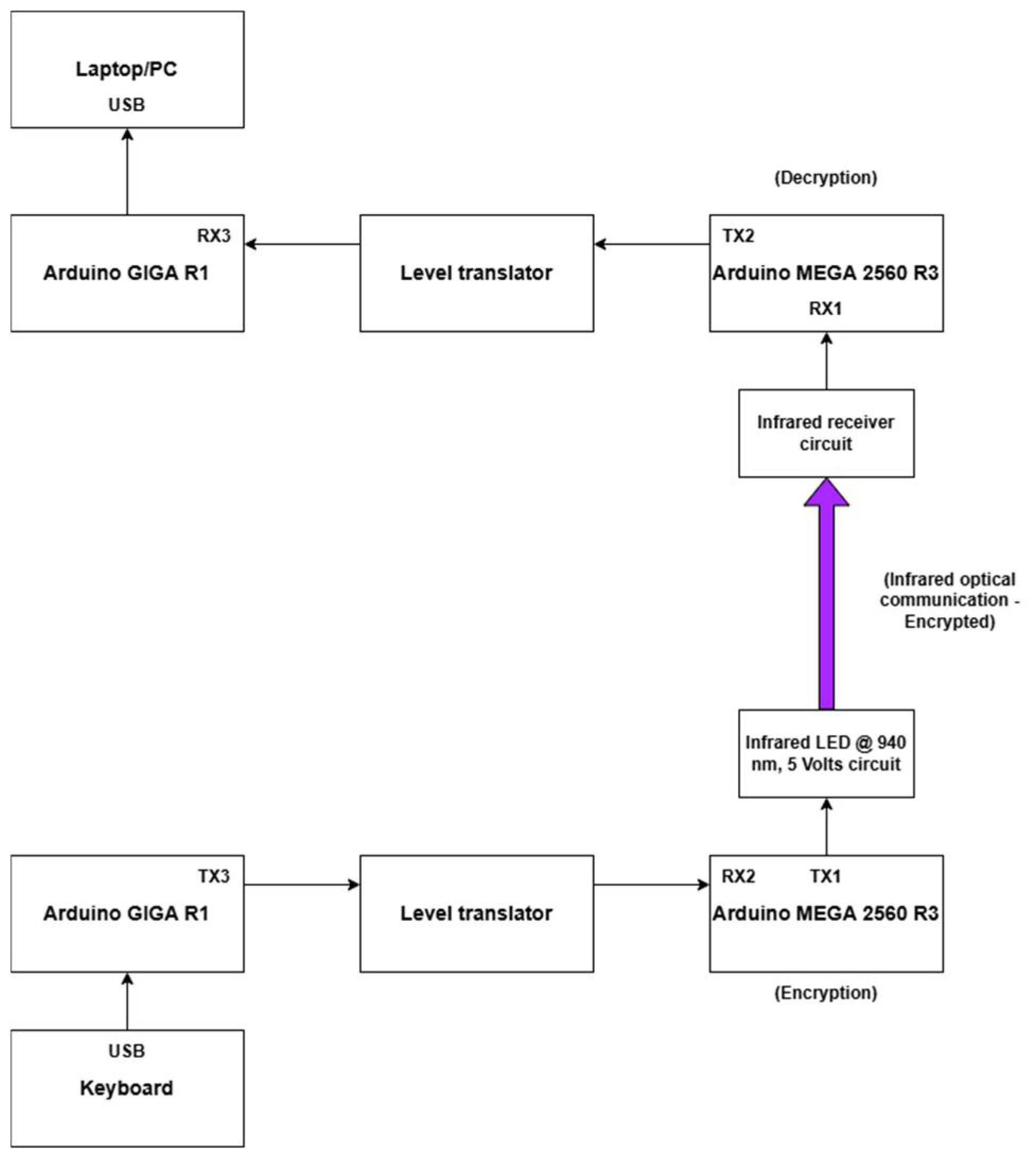
6. Encrypted Infrared Connection at 940 nm
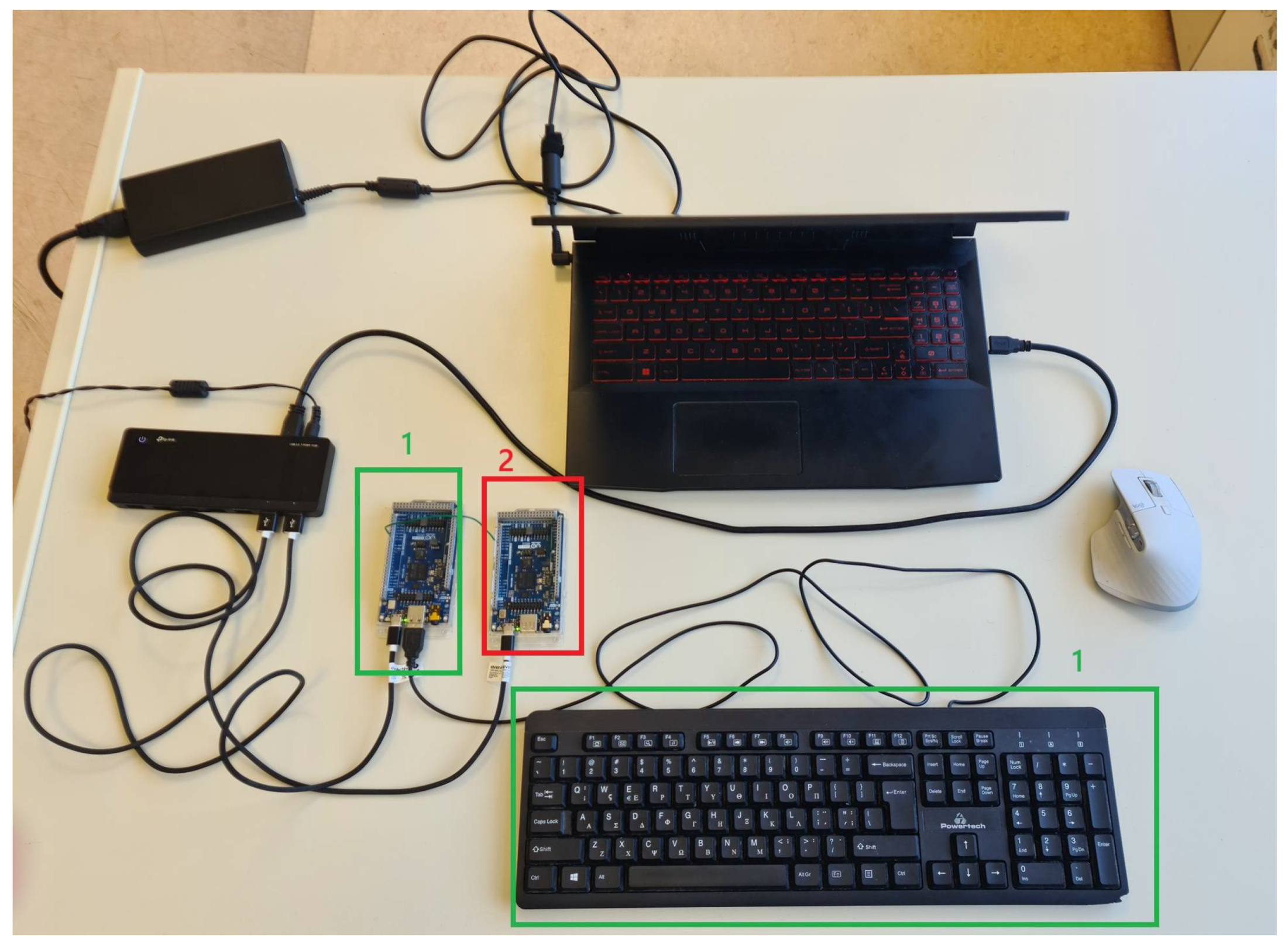
7. Unencrypted USB Keyboard Communication
8. Key Points for Making the Circuits Work Correctly Without Problems and (Possible) Attacks
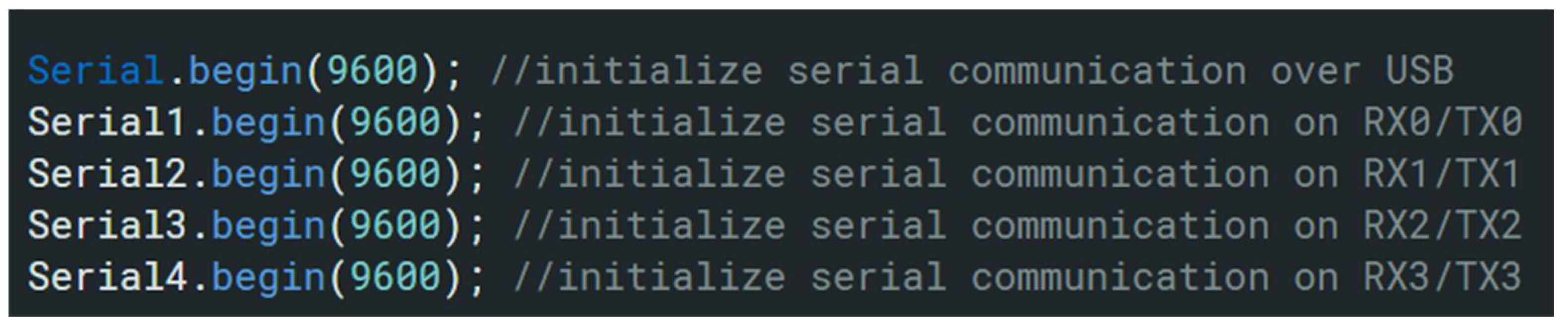
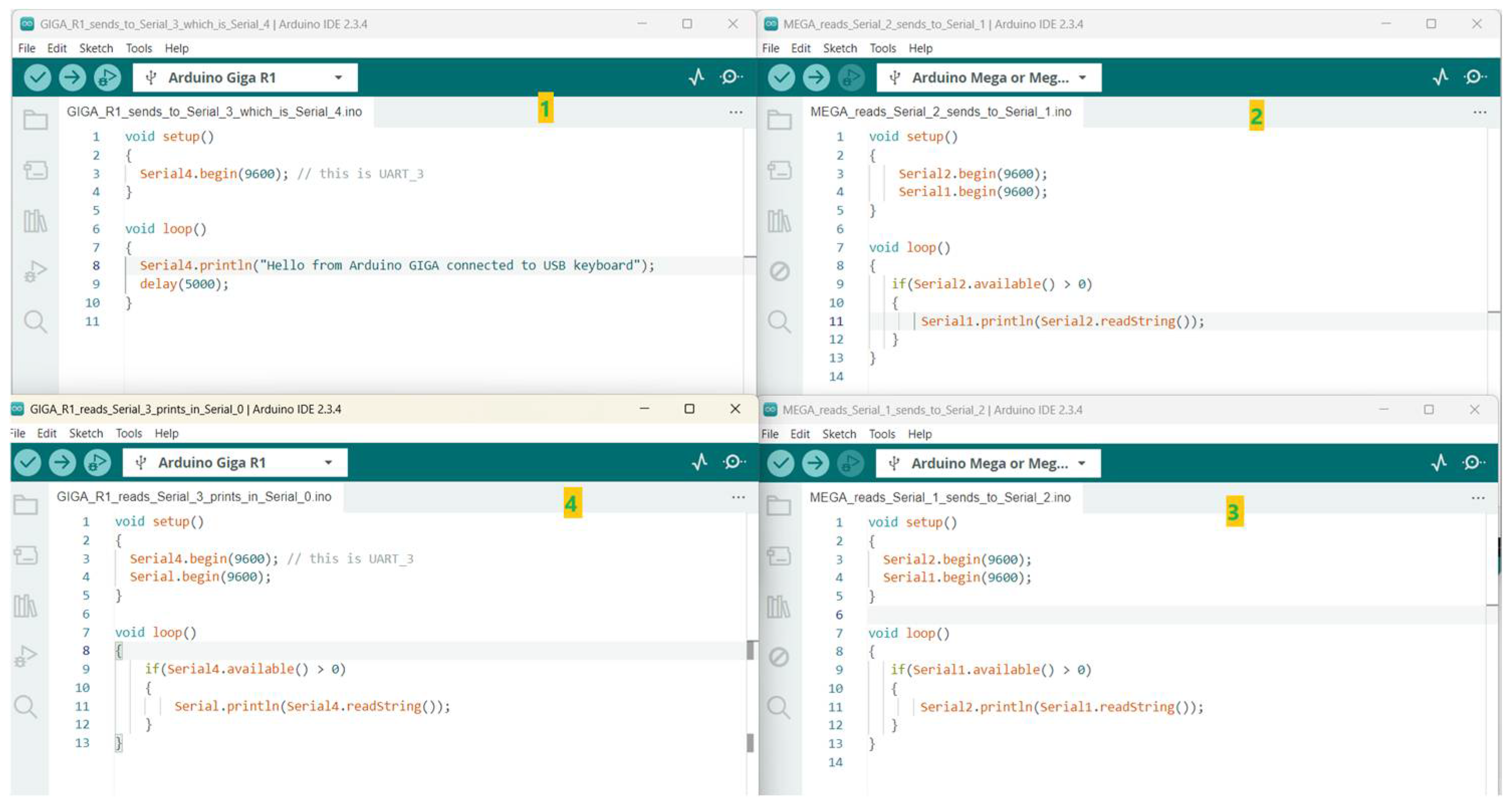
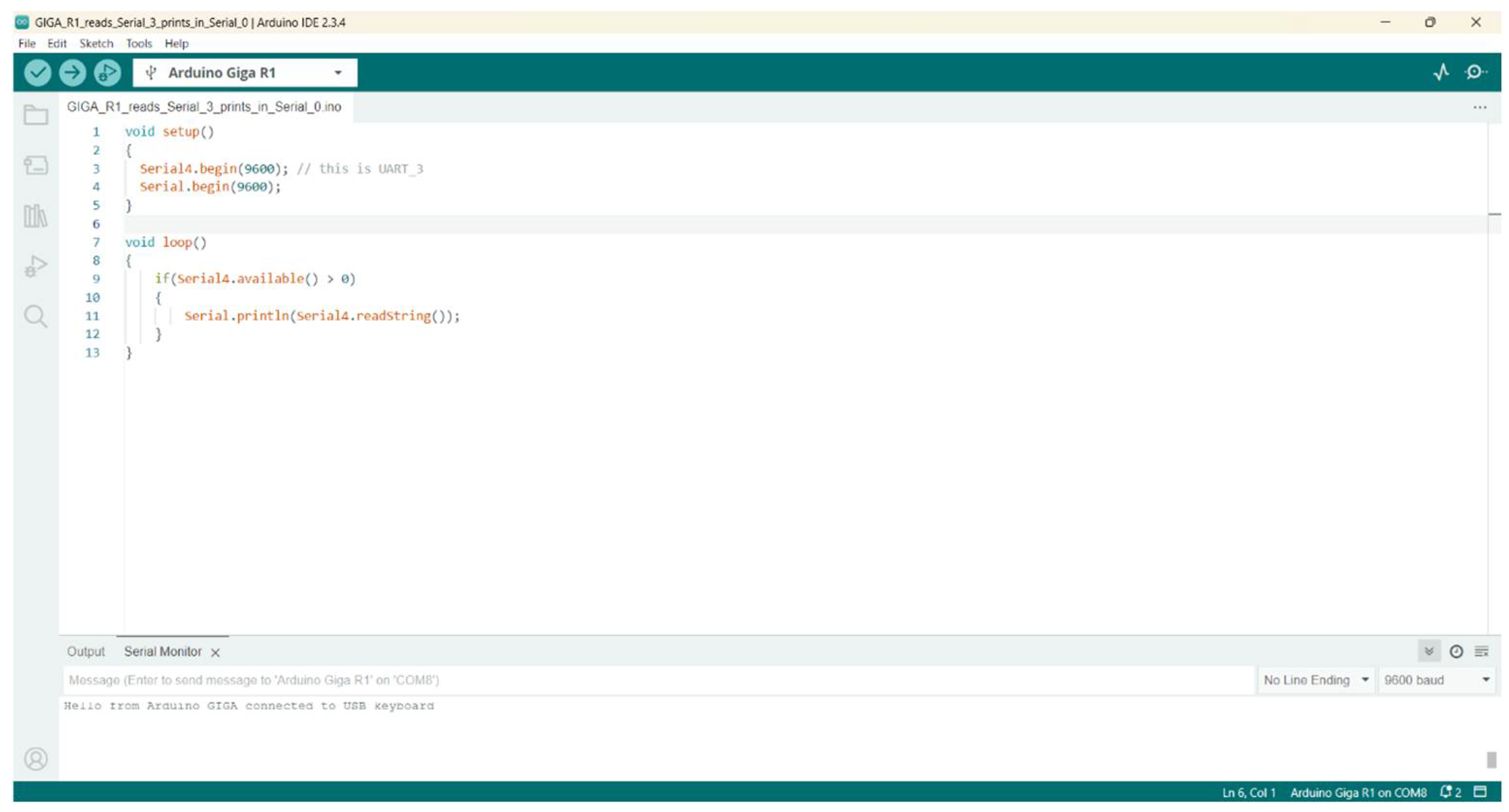
8.1. UART Problems
8.2. “Garbage” When IR Emitter and IR Receiver Are Not Aligned
8.3. Interference of Infrared Communication with Ambient Light
- It incorporates an AS7341 chip, which integrates eight visible spectrum channels, one near-infrared channel, and one no filter channel.
- Contains six independent 16 bit ADC, which enables processing of data in parallel.
- Specified channel to identify ambient light flicker on the specific frequency.
- two high brightness LEDs, that can be used as fill light in a dim environment.
- Interrupt pin to output inner ADC real-time operating status.
- Features spectrum interrupt detection, with programable high/low thresholds.
- Provides GPIO (General Purpose Input/Output) pin.
- Voltage translator, compatible with 3.3 V/5 V operating voltage.
8.4. Comparison of Evaluated Approaches
- Connecting the two Arduino MEGA 2560 R3s and the two Arduino GIGA R1s in the supply hub, without having connected any other module or wires, the current draw is around 363 mA, at 5 Volts, so there seems to be a power consumption of about 1815 mWatts.
- Implementation with AES encryption communication with the two Arduino MEGA 2560 R3s and the two Arduino GIGA R1s, with the two level translators, and the related wires connected, the meter showed 394 mA current draw, at 5 Volt, with a 1970 mWatts power consumption.
- Implementing the ECC encryption scheme, with the two Arduino GIGA R1s, the two Arduino MEGA 2560 R3s, the two level translators, and the related wires connected, the power meter displayed 403 mA current draw at 5 Volts, so there seems to be a power consumption of 2015 mWatts.
- Construction of the fiber optic communication, without using the two Arduino MEGA 2560 R3s or the level translators, but including the two fiber optic transceivers and the fiber optic cable, indicates reduced power consumption of about 1770 mWatts, with current draw 354 mA at 5 Volts, which is reasonable, since not all modules were used.
- The realization using XOR and Spritz ciphers followed the same circuit construction as the AES and the ECC. XOR encryption/decryption scheme shows a power consumption of 2030 mW, with a current draw around 406 mA, which is similar to the ECC-based experiments. The surprise is that Spritz-based scheme needs 423 mA, guiding to 2115 mW power consumption, which makes it the most energy harvesting experiment of all the implementations regarding secure keyboard communication.
- Regarding IR LED-encrypted communication, using the two Arduino MEGA 2560 R3s, the two Arduino GIGA R1s, the two level translators, extra resistors, an IR LED, and an IR receiver, indicates a power consumption of 2030 mWatts at 5 Volts, with 406 mA current draw.
- Zigbee communication between the two Arduino GIGA R1, the level translators, and the Xbee Zigbee with their adapter, but without using Arduino MEGA 2560 R3, needs around 330 mA current at 5 Volts, so there seems to be a power consumption of about 1650 mWatts.
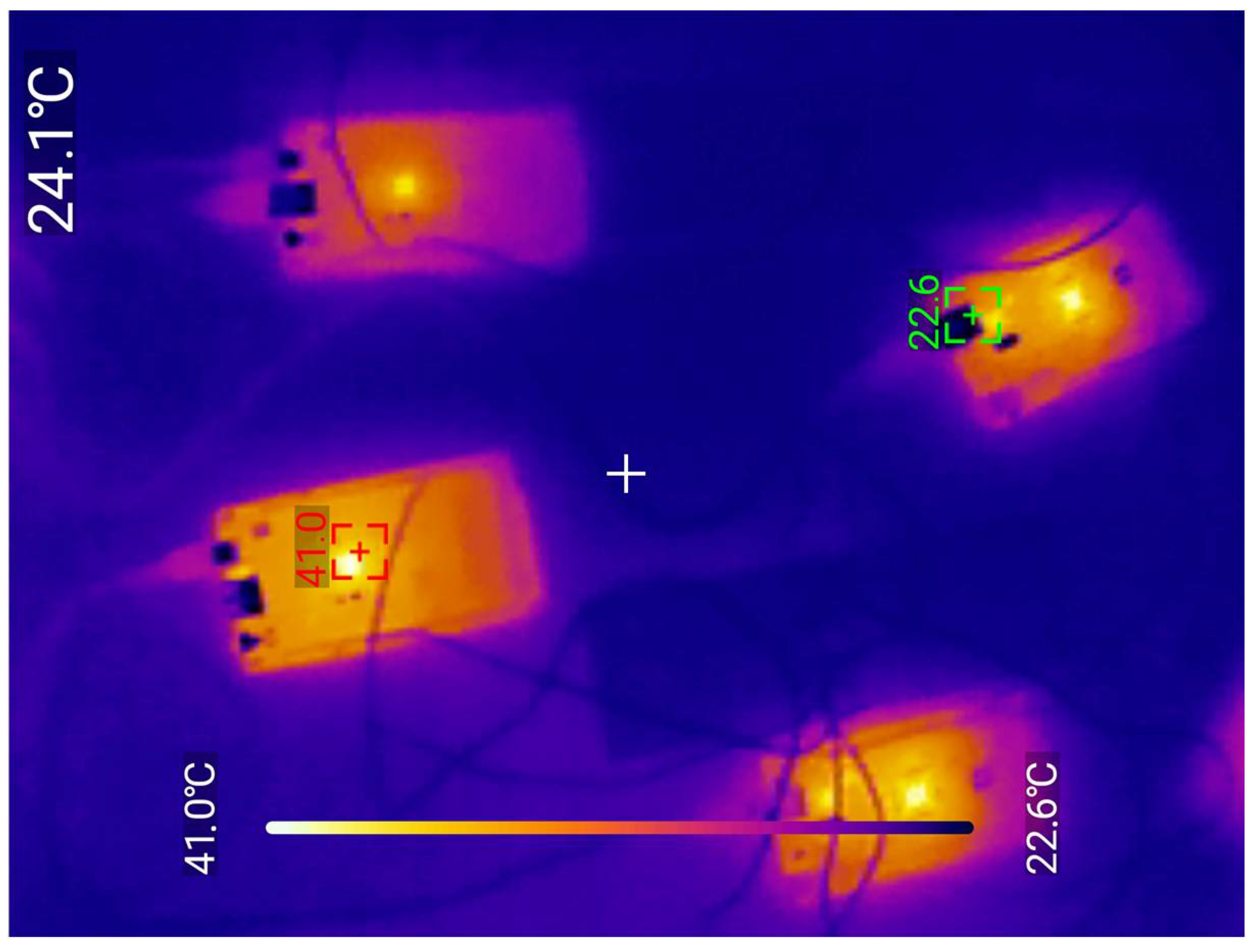
8.5. Testing the Fiber Optic Cable with Spectrum Analyzer
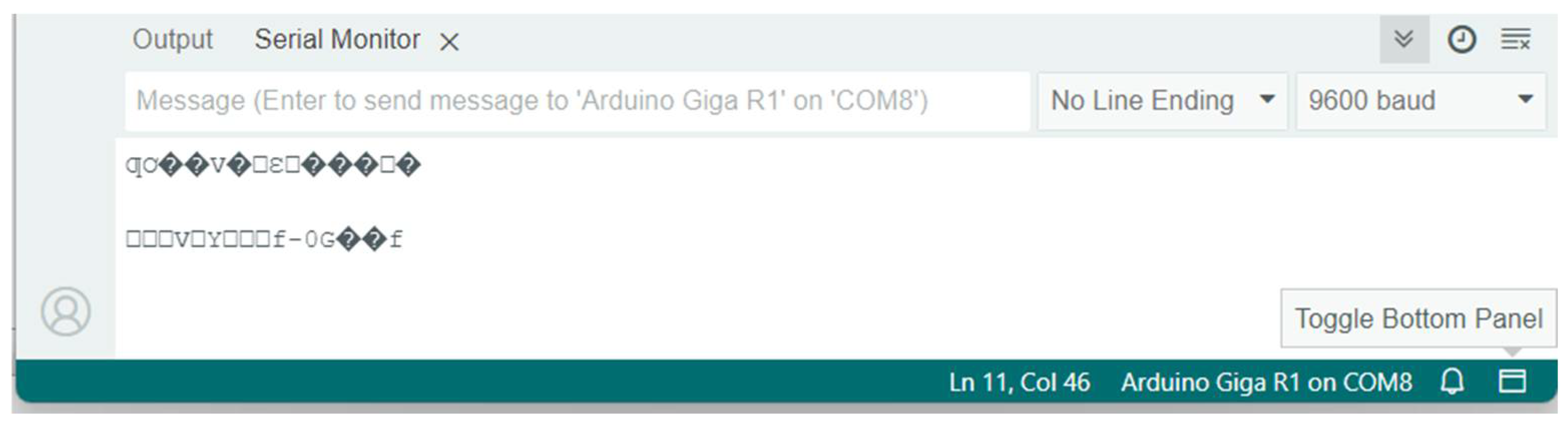
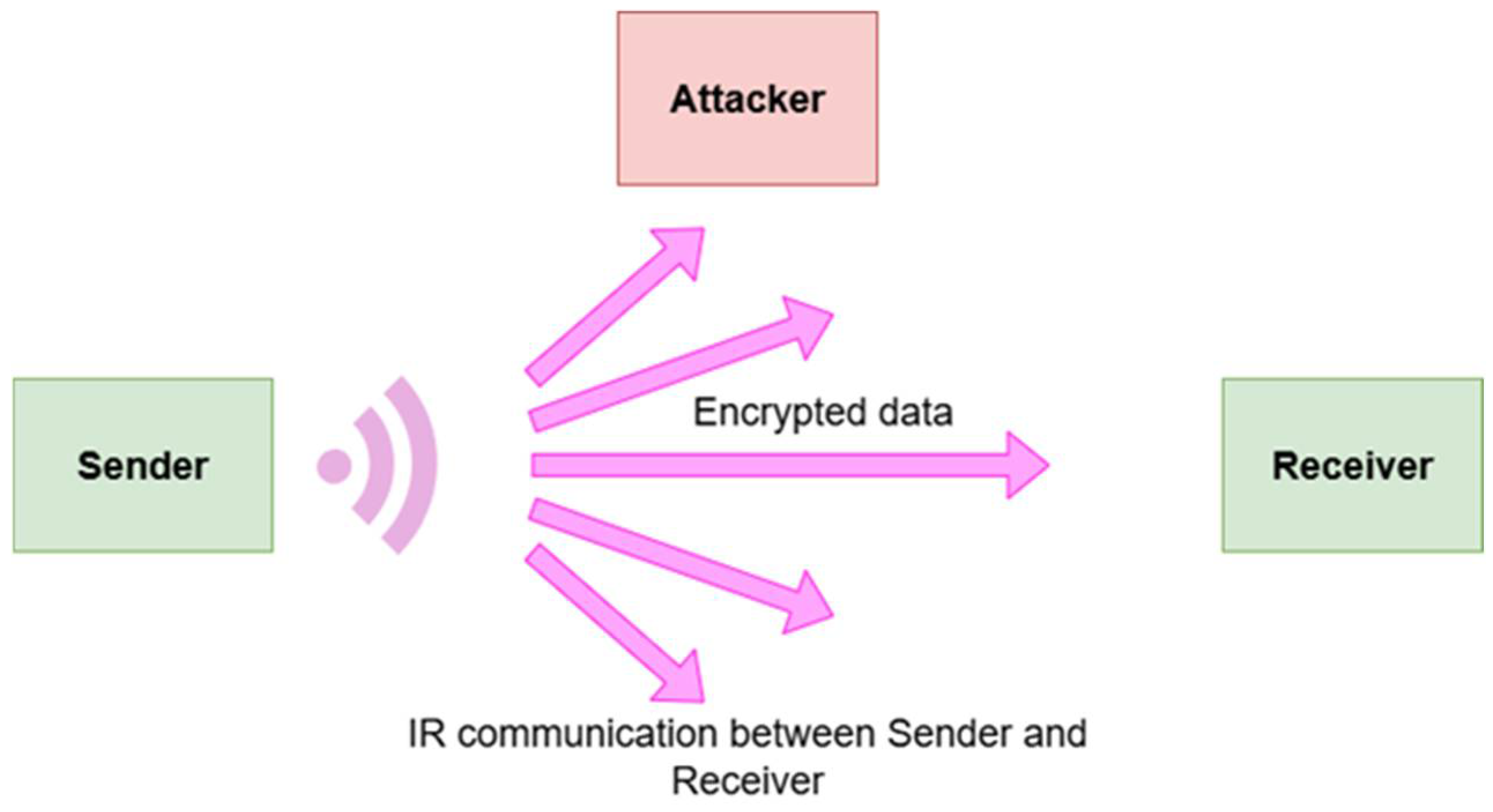
8.6. Attacking the AES- and ECC-Encrypted Keystrokes
8.7. An Attack on the IR Communication
8.8. Possible Attack in the Zigbee Keyboard Communication
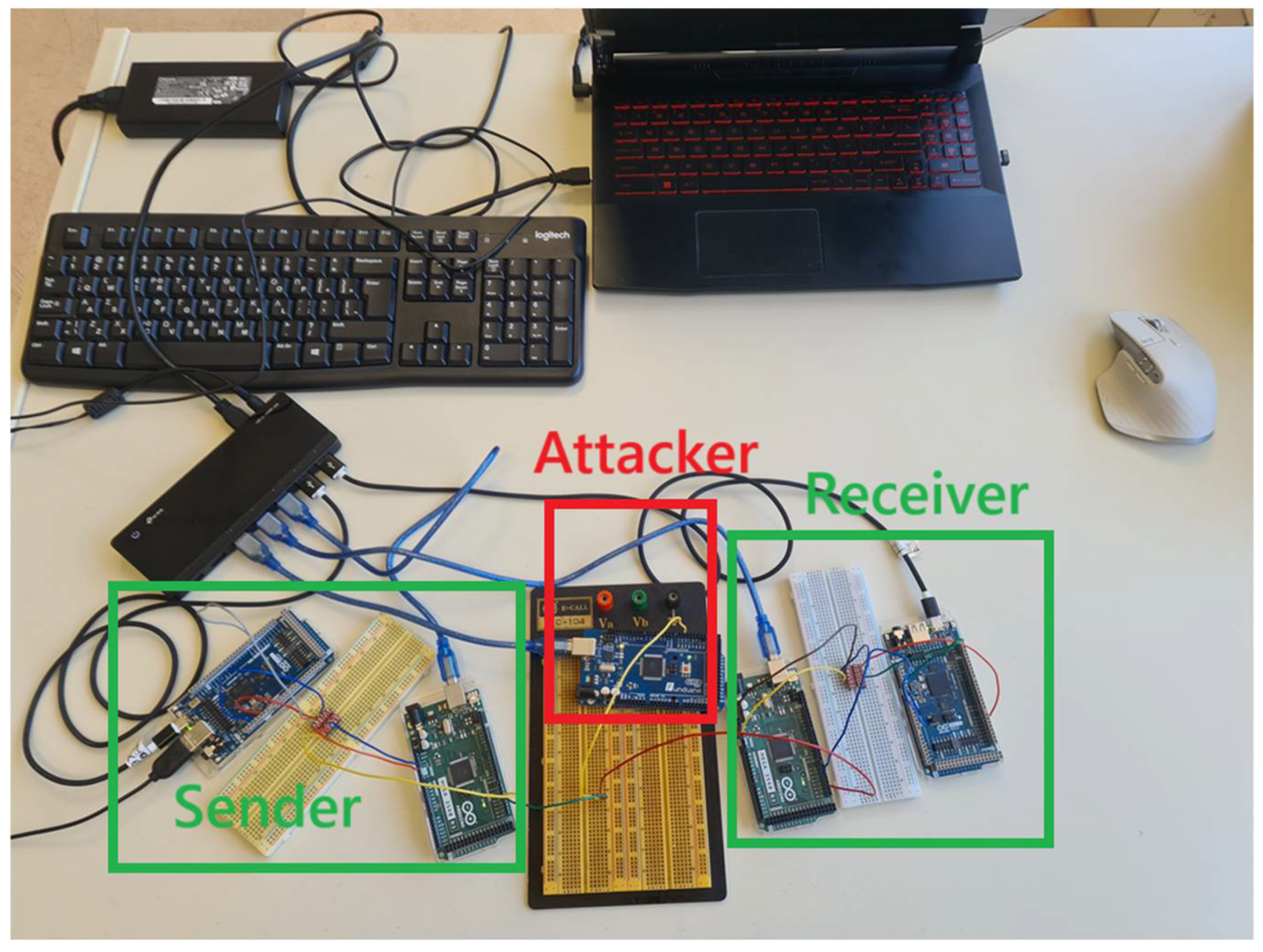
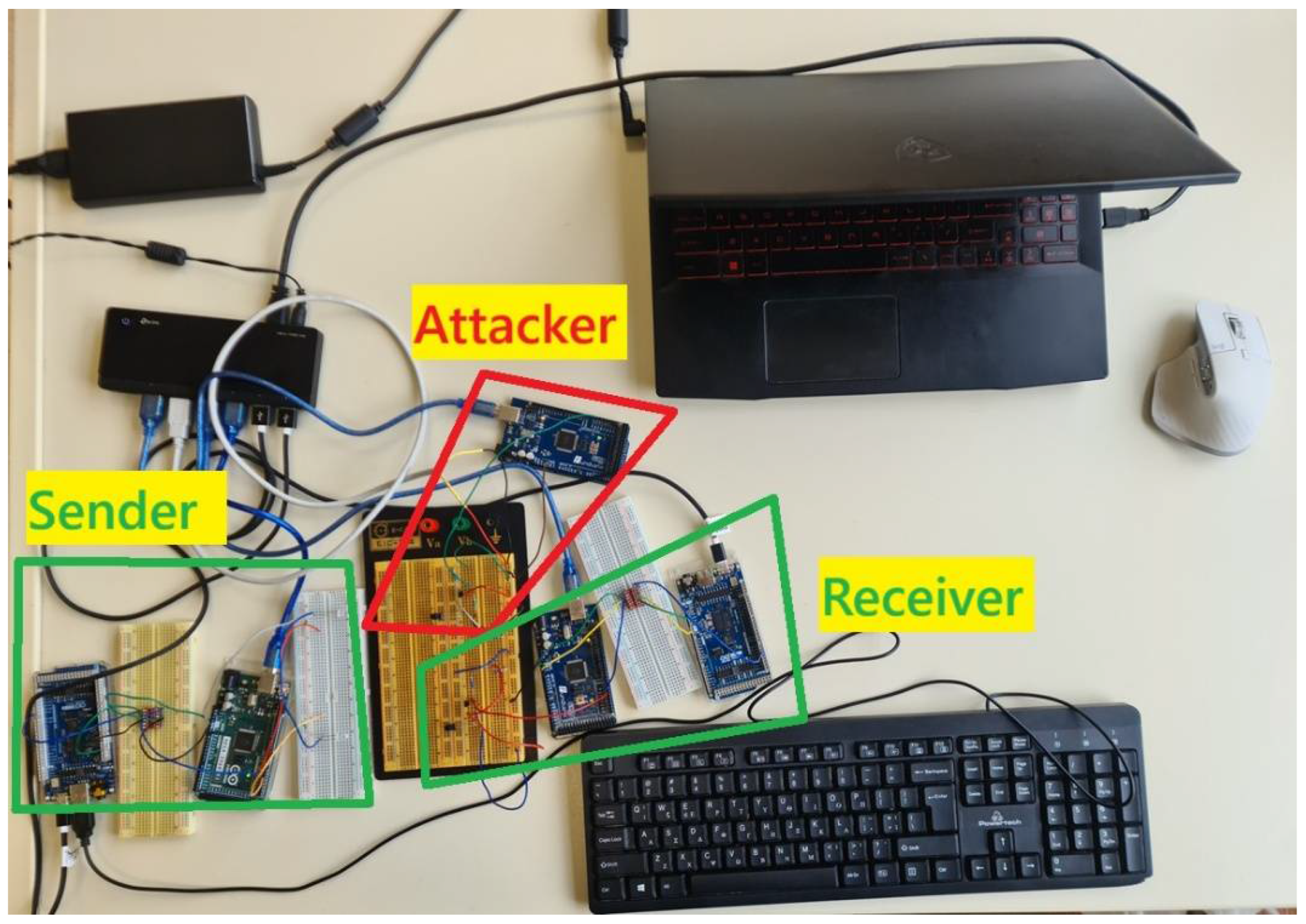
8.9. Realization of the Above Experiments in Different Modules
- Broadcom BCM2711, Quad core Cortex-A72 (ARM v8) 64 bit SoC @ 1.8 GHz.
- 1 GB, 2 GB, 4 GB, or 8 GB LPDDR4-3200 SDRAM (depending on model).
- 2.4 GHz and 5.0 GHz IEEE 802.11ac wireless, Bluetooth 5.0, BLE.
- Gigabit Ethernet.
- Two USB 3.0 ports; two USB 2.0 ports.
- Raspberry Pi standard 40 pin GPIO header.
- Micro-SD card slot for loading operating system and data storage.
- 5 V DC via USB-C connector (minimum: 3 Ampere).
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Jin, W.; Murali, S.; Zhu, H.; Li, M. Periscope: A Keystroke Inference Attack Using Human Coupled Electromagnetic Emanations. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 15–19 November 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 700–714. [Google Scholar]
- Wang, L.; Yu, B. Analysis and Measurement on the Electromagnetic Compromising Emanations of Computer Keyboards. In Proceedings of the 2011 Seventh International Conference on Computational Intelligence and Security, Sanya, China, 3–4 December 2011; pp. 640–643. [Google Scholar]
- Choi, H.-J.; Lee, H.S.; Sim, D.; Yook, J.-G.; Sim, K. Reconstruction of Leaked Signal from USB Keyboards. In Proceedings of the 2016 URSI Asia-Pacific Radio Science Conference (URSI AP-RASC), Seoul, Republic of Korea, 21–25 August 2016; IEEE: New York, YN, USA, 2016; pp. 1281–1283. [Google Scholar]
- Vuagnoux, M.; Pasini, S. An Improved Technique to Discover Compromising Electromagnetic Emanations. In Proceedings of the 2010 IEEE International Symposium on Electromagnetic Compatibility, Fort Lauderdale, FL, USA, 25–30 July 2010; pp. 121–126. [Google Scholar]
- Chen, B.; Yenamandra, V.; Srinivasan, K. Tracking Keystrokes Using Wireless Signals. In Proceedings of the 13th Annual International Conference on Mobile Systems, Applications, and Services, Florence, Italy, 18–22 May 2015; Association for Computing Machinery: New York, NY, USA, 2015; pp. 31–44. [Google Scholar]
- Hu, J.; Wang, H.; Zheng, T.; Hu, J.; Chen, Z.; Jiang, H.; Luo, J. Password-Stealing without Hacking: Wi-Fi Enabled Practical Keystroke Eavesdropping. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 239–252. [Google Scholar]
- Chen, Y.; Yu, J.; Chen, Y.; Kong, L.; Zhu, Y.; Chen, Y.-C. RFSpy: Eavesdropping on Online Conversations with Out-of-Vocabulary Words by Sensing Metal Coil Vibration of Headsets Leveraging RFID. In Proceedings of the 22nd Annual International Conference on Mobile Systems, Applications and Services, Tokyo, Japan, 3–7 June 2024; Association for Computing Machinery: New York, NY, USA, 2024; pp. 169–182. [Google Scholar]
- Choi, D.-H.; Lee, E.; Yook, J.-G. Reconstruction of Video Information Through Leakaged Electromagnetic Waves From Two VDUs Using a Narrow Band-Pass Filter. IEEE Access 2022, 10, 40307–40315. [Google Scholar] [CrossRef]
- Hayashi, Y.-I.; Homma, N.; Watanabe, T.; Price, W.O.; Radasky, W.A. Introduction to the Special Section on Electromagnetic Information Security. IEEE Trans. Electromagn. Compat. 2013, 55, 539–546. [Google Scholar] [CrossRef]
- Lee, H.S.; Choi, D.H.; Sim, K.; Yook, J.-G. Information Recovery Using Electromagnetic Emanations From Display Devices Under Realistic Environment. IEEE Trans. Electromagn. Compat. 2019, 61, 1098–1106. [Google Scholar] [CrossRef]
- Eltholth, A.A. Improved Spectrum Coexistence in 2.4 GHz ISM Band Using Optimized Chaotic Frequency Hopping for Wi-Fi and Bluetooth Signals. Sensors 2023, 23, 5183. [Google Scholar] [CrossRef] [PubMed]
- Bari, M.F.; Chowdhury, M.R.; Sen, S. Is Broken Cable Breaking Your Security? In Proceedings of the 2023 IEEE International Symposium on Circuits and Systems (ISCAS), Monterey, CA, USA, 21–25 May 2023; pp. 1–5. [Google Scholar]
- Wireshark • Undefined. Available online: https://www.wireshark.org/ (accessed on 20 June 2025).
- Landman, D. DavyLandman/AESLib 2025. Available online: https://github.com/DavyLandman/AESLib (accessed on 20 June 2025).
- ShubhamAnnigeri ShubhamAnnigeri/tinyECC-ArduinoIDE 2024. Available online: https://github.com/ShubhamAnnigeri/tinyECC-ArduinoIDE (accessed on 20 June 2025).
- Kelasrobot/SimpleArduinoEncryption 2025. Available online: https://github.com/kelasrobot/SimpleArduinoEncryption (accessed on 3 October 2025).
- Adjal, A. Abderraouf-Adjal/ArduinoSpritzCipher 2025. Available online: https://github.com/abderraouf-adjal/ArduinoSpritzCipher (accessed on 3 October 2025).
- Babani, S.; Bature, A.A.; Faruk, M.I.; Dankadai, N.K. Comparative study between fiber optic and copper in communication link. Int. J. Tech. Res. Appl. 2014, 2, 59–63. [Google Scholar]
- López-Cardona, J.D.; Vázquez, C.; Montero, D.S.; Lallana, P.C. Remote Optical Powering Using Fiber Optics in Hazardous Environments. J. Light. Technol. 2018, 36, 748–754. [Google Scholar] [CrossRef]
- Gravity: UART Fiber Optic Transceiver Module Wiki—DFRobot. Available online: https://wiki.dfrobot.com/SKU_TEL0153_Gravity_UART_Fiber_Optic_Transceiver_Module (accessed on 20 June 2025).
- Al-fatlawi, A.H.; Abdul Zahra, M.M.; Rassool, H.A. Simulation of Optical Fiber Cable Regarding Bandwidth Limitations. Int. J. Nonlinear Anal. Appl. 2021, 12, 1159–1174. [Google Scholar]
- Abdullah, A.M. Advanced Encryption Standard (AES) Algorithm to Encrypt and Decrypt Data. Cryptogr. Netw. Secur. 2017, 16, 11. [Google Scholar]
- Hamza, A.; Kumar, B. A Review Paper on DES, AES, RSA Encryption Standards. In Proceedings of the 2020 9th International Conference System Modeling and Advancement in Research Trends (SMART), Moradabad, India, 4–5 December 2020; IEEE: New York, YN, USA, 2020; pp. 333–338. [Google Scholar]
- Paar, C.; Pelzl, J.; Güneysu, T. Understanding Cryptography: From Established Symmetric and Asymmetric Ciphers to Post-Quantum Algorithms; Springer: Berlin/Heidelberg, Germany, 2024; ISBN 978-3-662-69006-2. [Google Scholar]
- Ramya, C.M.; Shanmugaraj, M.; Prabakaran, R. Study on ZigBee Technology. In Proceedings of the 2011 3rd International Conference on Electronics Computer Technology, Kanyakumari, India, 8–10 April 2011; Volume 6, pp. 297–301. [Google Scholar]
- Zigbee. Wikipedia 2024. Available online: https://en.wikipedia.org/w/index.php?title=Zigbee&oldid=1246713824 (accessed on 20 June 2025).
- WRL-08665 SparkFun | Mouser Greece. Available online: https://gr.mouser.com/ProductDetail/SparkFun/WRL-08665?qs=WyAARYrbSnbfBpB%252BN4iLCg%3D%3D&srsltid=AfmBOoqllDf-ZNZjEni8rEI2chgCx1QDcxFAwLy_7ZpTaL_BYhWPofLX (accessed on 20 June 2025).
- SparkFun XBee 2mW Wire Antenna—Series 2 (ZigBee Mesh): Amazon.in: Computers & Accessories. Available online: https://www.amazon.in/XBee-2mW-Wire-Antenna-ZigBee/dp/B007R9U1QA (accessed on 20 June 2025).
- Digi International XBee Pro 63mW Wire Antenna—Series 2B (ZigBee Mesh): Amazon.Co.Uk: Electronics & Photo. Available online: https://www.amazon.co.uk/XBee-Pro-63mW-Wire-Antenna/dp/B00Q6Y79W6 (accessed on 20 June 2025).
- Adi, P.D.P.; Sihombing, V.; Siregar, V.M.M.; Yanris, G.J.; Sianturi, F.A.; Purba, W.; Tamba, S.P.; Simatupang, J.; Arifuddin, R.; Subairi, S.; et al. A Performance Evaluation of ZigBee Mesh Communication on the Internet of Things (IoT). In Proceedings of the 2021 3rd East Indonesia Conference on Computer and Information Technology (EIConCIT), Surabaya, Indonesia, 9–11 April 2021; pp. 7–13. [Google Scholar]
- Industries, A. XBee Module—ZB Series S2C—2mW with Wire Antenna. Available online: https://www.adafruit.com/product/968 (accessed on 3 October 2025).
- Willner, A.E.; Zhou, H.; Duan, Y.; Jiang, Z.; Ramakrishnan, M.; Su, X.; Zou, K.; Pang, K. Advances in Multi-Channel Mid-IR Free-Space Optical Communications. J. Light. Technol. 2024, 42, 6739–6748. [Google Scholar] [CrossRef]
- Zhu, Y.; Chen, H.; Han, R.; Qin, H.; Yao, Z.; Liu, H.; Ma, Y.; Wan, X.; Li, G.; Chen, Y. High-Speed Flexible near-Infrared Organic Photodiode. Natl. Sci. Rev. 2023, 11, nwad311. [Google Scholar] [CrossRef] [PubMed]
- Zhong, R.; Ji, J.; Zeng, T.; Wang, K.; Song, Y. Performance Analysis of Physical-Layer Security in Mid-Infrared FSO Communication System. Opt. Quantum Electron. 2024, 56, 463. [Google Scholar] [CrossRef]
- Use Multiple Serial Ports on the Arduino Mega | Arduino Documentation. Available online: https://docs.arduino.cc/built-in-examples/communication/MultiSerialMega/ (accessed on 20 June 2025).
- Arduino GIGA R1 User Manual | Arduino Documentation. Available online: https://docs.arduino.cc/tutorials/giga-r1-wifi/cheat-sheet/ (accessed on 20 June 2025).
- Moreira, A.J.C.; Valadas, R.T.; De Oliveira Duarte, A.M. Optical Interference Produced by Artificial Light. Wirel. Netw. 1997, 3, 131–140. [Google Scholar] [CrossRef]
- Park, T.-J.; Kim, K.; Moon, S. Securing Infrared Communication in Nuclear Power Plants: Advanced Encryption for Infrared Sensor Networks. Sensors 2024, 24, 2054. [Google Scholar] [CrossRef] [PubMed]
- Kim, M.; Suh, T. Eavesdropping Vulnerability and Countermeasure in Infrared Communication for IoT Devices. Sensors 2021, 21, 8207. [Google Scholar] [CrossRef] [PubMed]
- AS7341 Spectral Color Sensor—Waveshare Wiki. Available online: https://www.waveshare.com/wiki/AS7341_Spectral_Color_Sensor (accessed on 3 October 2025).
- Device.Report Ams AS7341 Sensor Chip User Guide. Available online: https://device.report/manual/8764433 (accessed on 3 October 2025).
- Mega 2560 Rev3 | Arduino Documentation. Available online: https://docs.arduino.cc/hardware/mega-2560/ (accessed on 3 October 2025).
- Arduino GIGA R1 WiFi. Available online: https://store.arduino.cc/products/giga-r1-wifi (accessed on 3 October 2025).
- Ltd, R.P. Raspberry Pi 4 Model B Specifications. Available online: https://www.raspberrypi.com/products/raspberry-pi-4-model-b/specifications/ (accessed on 3 October 2025).
- BoppreH Boppreh/Aes 2025. Available online: https://github.com/boppreh/aes (accessed on 20 September 2025).
- I2C. Wikipedia 2025. Available online: https://en.wikipedia.org/w/index.php?title=I%C2%B2C&oldid=1312382986 (accessed on 5 October 2025).




















| Proposed Solution | Communication Type | Encryption Used (Y/N) | Encryption Protocol | Configuration Difficulty (Software and Hardware) | Experiment Cost (Without Laptop and Mouse) in Euros | Scalability | Bandwidth |
|---|---|---|---|---|---|---|---|
| 1 | IR light (fiber optic cable) | No | - | 1 | 234.56 | Medium | 2 Mbps |
| 2 | Wire | Yes | AES | 2 | 353.96 | Medium | 500 kbps (limited due to Arduino MEGA 2560 R3) |
| 3 | Wire | Yes | ECC | 2 | 353.96 | Medium | 500 kbps (limited due to Arduino MEGA 2560 R3) |
| 4 | Wire | Yes | XOR | 2 | 353.96 | Medium | 500 kbps (limited due to Arduino MEGA 2560 R3) |
| 5 | Wire | Yes | Spritz | 2 | 353.96 | Medium | 500 kbps (limited due to Arduino MEGA 2560 R3) |
| 6 | Wireless (Zigbee)—one Arduino GIGA R1 | Yes | AES | 2 | 167.25 | High | 250 kbps max (provided by the manufacturer) |
| 7 | Free-space IR communication | Yes | AES | 2 | 374.56 | Medium | 9600 bps (tested) |
| Algorithm | Encryption Time (ms) | Decryption Time (ms) |
|---|---|---|
| ECC | 4864 | 2218.5 |
| AES | 0.286 | 0.3256 |
| XOR | 0.181 | 0.696 |
| Spritz | 0.116 | 0.116 |
| Scheme | Delay (in Seconds) |
|---|---|
| Arduinos with AES encryption/decryption circuit | 4 |
| Arduinos with ECC encryption/decryption circuit | 6 |
| Arduinos with XOR encryption/decryption circuit | 4 |
| Arduinos with Spritz encryption/decryption circuit | 3 |
| Arduinos circuit with fiber optic (no Arduino MEGA 2560 R3 used) | 1 |
| Arduinos circuit with IR LED communication | 4 |
| Arduinos with Zigbee communication (no Arduino MEGA 2560 R3 used) | 1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Routis, G.; Roussaki, I. Securing Keyboard Data Communication. Telecom 2025, 6, 85. https://doi.org/10.3390/telecom6040085
Routis G, Roussaki I. Securing Keyboard Data Communication. Telecom. 2025; 6(4):85. https://doi.org/10.3390/telecom6040085
Chicago/Turabian StyleRoutis, George, and Ioanna Roussaki. 2025. "Securing Keyboard Data Communication" Telecom 6, no. 4: 85. https://doi.org/10.3390/telecom6040085
APA StyleRoutis, G., & Roussaki, I. (2025). Securing Keyboard Data Communication. Telecom, 6(4), 85. https://doi.org/10.3390/telecom6040085








