6G Mobile Networks: Key Technologies, Directions, and Advances
Abstract
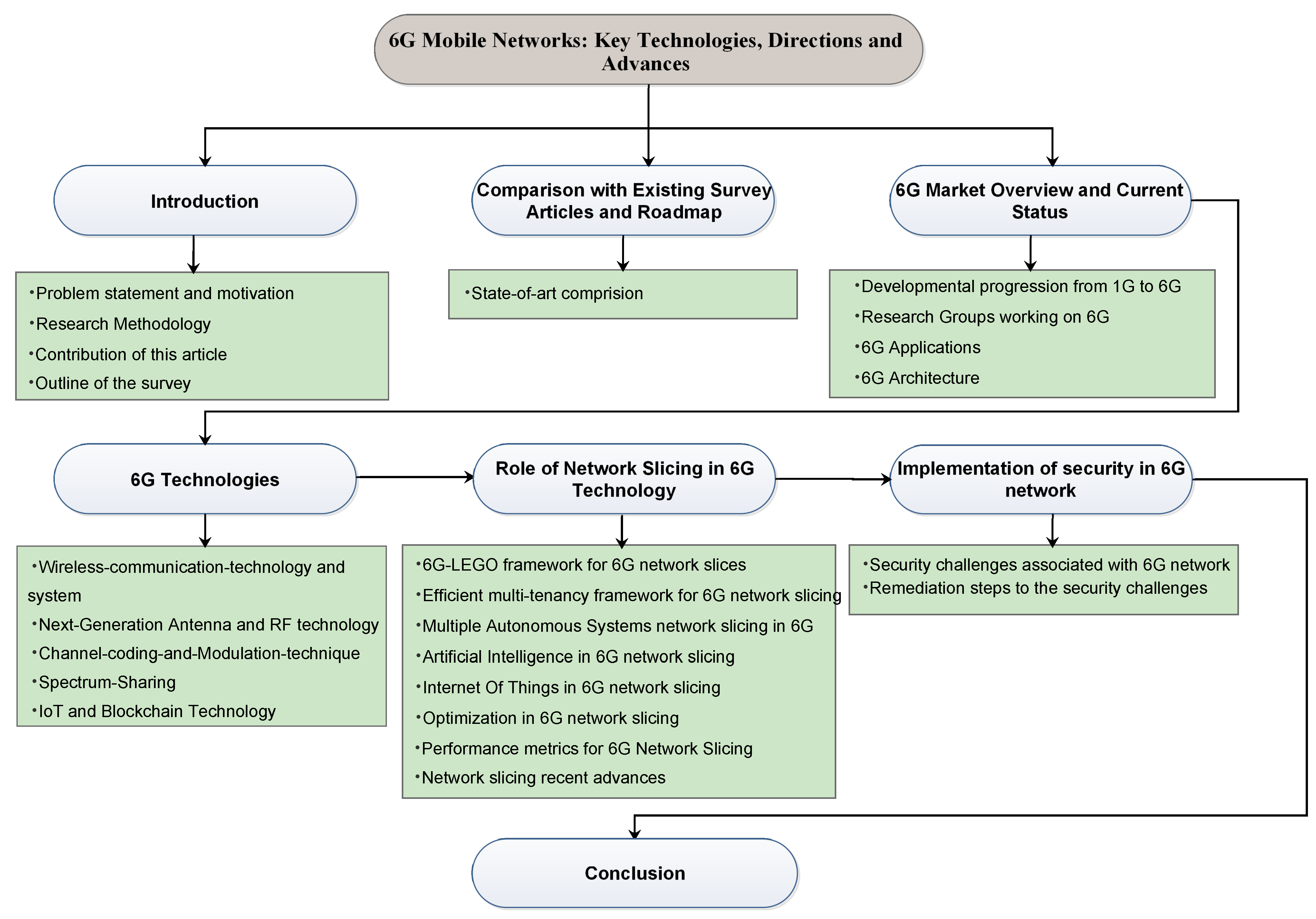
:1. Introduction
1.1. Problem Statement and Motivation
1.2. Research Methodology
1.3. Key Contributions
- This survey covers the most recent advances & progress in the 6G age, as well as new benefits received by the experimental group and crucial elements of the 6G evolution.
- The evolution of mobile network technology is the topic of this research. The growth of mobile communications and its many facets are also explored.
- With a comprehensive classification, this study explores the emerging operational and research groups working on 6G and the many exploration domains in 6G wireless communication systems.
- This analysis considers the benefits, features, key technologies, and fundamental concepts of a 6G network. The potential for network slicing and security in the 6G network is also investigated with an eye to future use cases. The 6G IoT-based approaches and optimisation techniques were also highlighted in the survey.
- We provide a thorough overview and a summary of recent developments in the emerging technologies of the 6G cellular connection, including Wireless Communication Technology and Systems, which also covers Terahertz (THz), Next-Generation Antenna and RF Technology, Channel Coding and Modulation Technique, Spectrum Sharing, Internet-of-Things, and Blockchain Technology. By stressing the surroundings of current techniques and accompanying obstacles, a specialised overview is also circulated.
- The improvements in softwarization, agile control, and deterministic services over the 6G armature are explored, and an architectural perspective for Network Slicing for the 6G network is presented.
- In this study, we examine the potential difficulties and opportunities presented by Network Security throughout the development of 6G technology. This survey also includes discussions on security considerations, focusing on data processing, threat detection, network monitoring, and data encryption.
1.4. Outline of the Survey
2. Comparison with Existing Survey Articles and Roadmap
| Authors & References | Network Security | Network Slicing | Wireless Communication Technology and System | Next-Generation Antenna and RF Technology | Channel Coding and ModulationTechnique | Spectrum Sharing | IoT & Blockchain Technology |
|---|---|---|---|---|---|---|---|
| Soon Xin Ng et al. [3] | - | - | - | - | Yes | - | - |
| Marco Giordani et al. [4] | - | - | Yes | Yes | - | - | - |
| Sudeep Bhattarai et al. [5] | - | - | - | - | - | Yes | - |
| RAMESH SEKARAN et al. [6] | - | - | - | - | - | - | Yes |
| MostafaZaman Chowdhury et al. [7] | - | Yes | Yes | Yes | - | - | Partially (only For Blockchain) |
| Walid Saad et al. [8] | - | - | Yes | Yes | - | - | - |
| Haitham Hassan H. Mahmoud et al. [9] | - | Yes | Yes | Yes | - | - | - |
| Samar Elmeadawy et al. [10] | Yes | - | Yes | - | - | - | Yes |
| Ashish Kr. Gupta et al. [11] | - | - | Yes | - | - | - | - |
| Yang Lu et al. [12] | - | - | Yes | Yes | Yes | Yes | Yes |
| Anutusha Dogra et al. [1] | - | Yes | Yes | - | - | Yes | Partially (only For IoT) |
| Wen Wu et al. [14] | - | Yes | - | - | - | - | - |
| Hao Xu et al. [15] | Yes | Yes | Yes | - | - | Yes | Yes |
| Rodrigo Moreira et al. [16] | - | Yes | - | - | - | - | Partially (only For Blockchain) |
| Slawomir Kuklinski et al. [17] | - | Yes | - | - | - | - | - |
| Maansa Krovvidi [18] | - | Yes | Yes | - | - | - | Partially (only For IoT) |
| Our paper | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
3. 6G Market Overview and Current Status
- Massive URLLC: The acronym URLLC stands for communications with increased availability, reduced delay, and reliability for critical applications like the industrial internet of things and remote surgery. Massive-URLLC is a new service class that combines traditional mMTC with 5G-URLLC. It will come about because 6G will need to make the 5G URLLC service huge. One of the applications for huge URLLC that some want to deploy is autonomous intelligent driving (AID). AID necessitates juggling many priorities at once, including obstacle detection, automatic driving, motion planning, and others. Interesting alternatives to Massive-URLLC include multiple access techniques like OMA, NOMA, and assertion of multiple access. By using OMA techniques like massive-URLLC, the amount of bandwidth required for 6G might grow exponentially as more devices are added. Other multiple access techniques, such as NOMA, can be used to strike the ideal balance between scalability, reliability, and latency. Massive-URLLC demands the delivery of a lot of little data packets for “time-critical” 6G applications to ensure high resource efficiency and low latency [20].
- eMBB: Applications like holographic meetings, AR, and VR often require fast transmission speeds, minimal latency, and great reliability. Additionally, these demands must be met in situations demanding a great deal of mobility, including sea and air travel. As a result, the following new service class for 6G has proposed an enhanced mobile broadband URLLC. For this service class, the importance of energy-efficiency is a priority. In comparison to the URLLC along with eMBB in 5G networks, this new network class should be extremely skilled in improving mobile communications networks, with regard to handover, interference, and huge data transmission and processing. Additionally, the improved mobile broadband URLLC communication service’s security and privacy issues need to be considered [20].
- Massive eMBB—The link frequency will be quite high in Industry 4.0-based scenarios in order to acquire tactile perceptions and convert them into digital data. As a result, big eMBB will be a hot topic in the 6G network as a way to improve large-scale IIoT operations and functionalities by enabling the vast connection between worker, sensor, and an actuator that has low-latency [20].
- Frequency Bands—For fixed access, 5G provides millimeter wave and sub-5GHz frequency bands. While 6G enables sub-6 GHz frequency bands, millimeter waves for mobile communication investigation of THz bands, non-RF bands, etc.
- Data Rate—20 Gbps downlink and 10 Gbps uplink data rates are provided by 5G. On the other hand, 6G offers 1 Tbps for both the uplink and the downlink.
- Latency—5G offers a latency of around 1 ms, whereas 6G aims to achieve a latency of less than 1 µs.
- Architectural Style—The 5G architecture uses Mmwave tiny cells with a range of roughly 100 metres and dense sub-6 GHz smaller BSs with umbrella macro BSs. While 6G design comprises cell-free smart surfaces operating at higher frequencies, transient hotspots generated by BSs placed on drones, and tests with miniature THz cells.
- Device Type—5G comprises devices like Smartphones, Sensors and Drones. 6G consists of gadgets including smart implants, CRAS, XR, and BCI technology, as well as DLT gadgets.
- Reliability—5G has a reliability of 10–5 and 6G has 10 to 9.
- Accuracy in localization—For 5G networks, 10 cm on 2D, and 1 cm on 3D for 6G based networks.
- Customer engagement—50 Mbps 2D anywhere for 5G and for 6G network it is 10 Gbps 3D everywhere.
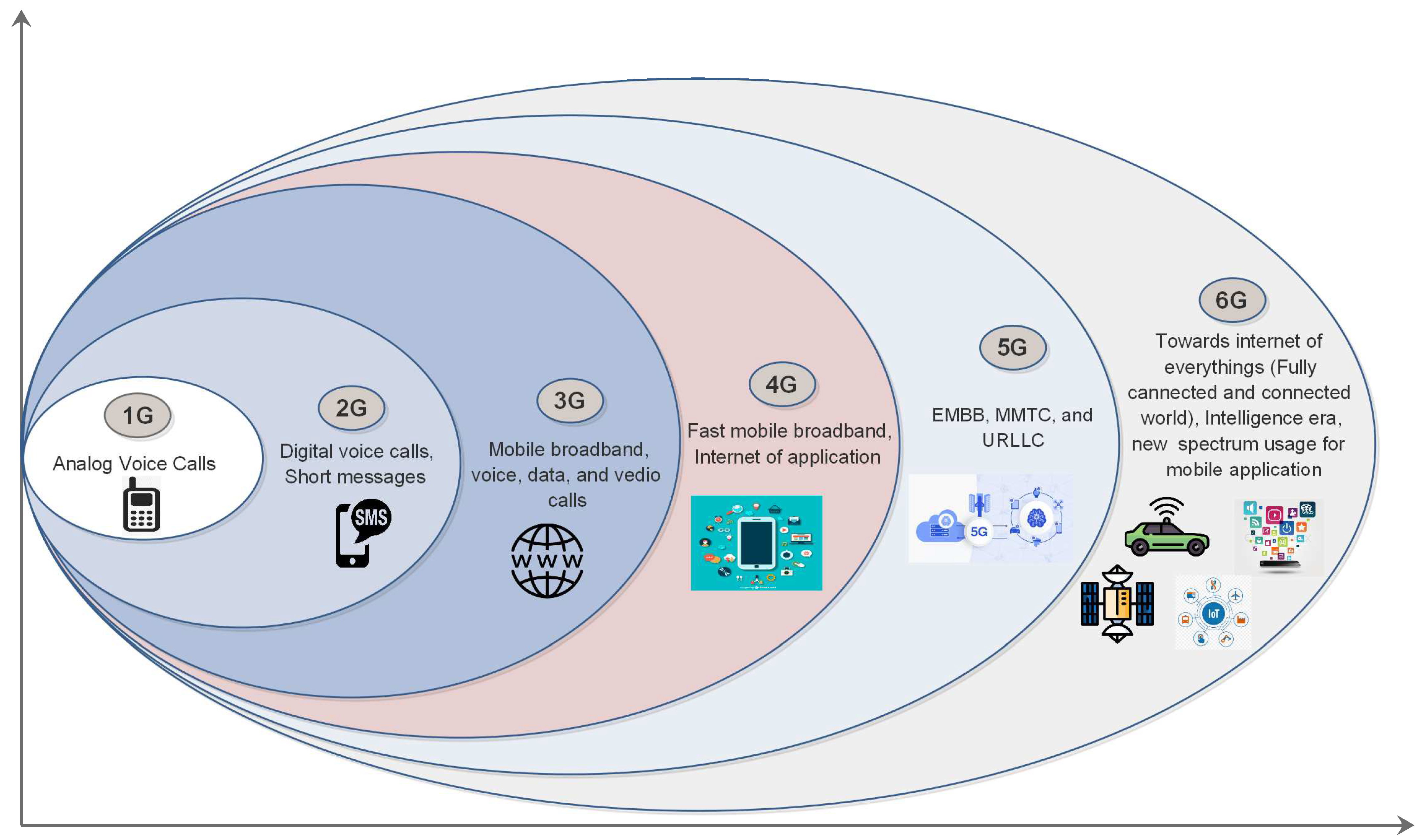
3.1. Developmental Progression from 1G to 6G
3.2. Research Groups Working on 6G
- NTT Docomo: NTT Docomo released a journal paper in January 2020, following the distribution of its first white paper discussed above in September 2019. An intriguing viewpoint presented in this study for new remote transmission advancements that could be used in 6G proposes that faster-than-Nyquist (FTN) flagging, which folds up and sends signals non-symmetrically using an evaluation rate faster than that of the recurrence data transfer capacity in the space-time, would be used in place of OFDM approaches. Additionally, it recommends employing virtual massive MIMO technology to fulfil the specifications for receiving wire gains [24].
- Rohde and Schwarz: Rohde and Schwarz create, deliver, and market a large number of electronic capital products for industry, foundation administrators, and government clients. All the free gathering is among the innovation and market pioneers in its business fields, including remote correspondences and RF test and estimation, broadcast and media, airport regulation and military radiocommunications, online protection, and organization technology. Around March 2020, Rohde and Schwarz distributed a study. The ideas and details mentioned in the article are very comparable with NTT Docomo’s article [25].
- The Finnish 6G Flagship: 6G Flagship is the world’s most memorable 6G exploration program. We are a piece of the Finnish government’s public exploration lead program from 2018 to 2026. We want to make the fundamental 6G mechanical parts, the instruments, and the hardware to construct a 6G Test Network, foster picked vertical applications for 6G to speed up cultural digitization, and keep on being a perceived vision pioneer and pursue research accomplice in overall 6G exploration. In June 2020, they delivered eleven further 6G White papers, resulting in a total of documents from Flagship to twelve. Later, in July 2020, Samsung’s white paper was released as one of the most recent upgrades [26].
- Samsung Corp.: The University of Oulu white paper appears to be technologically superior to Samsung’s research, which was published in July 2020 [26]. Here are a few recent events that have been determined to be important.
- A clearer explanation of the Novel Antenna Technologies needed for THz parallelism is provided. Here two specialized advancements have indeed been explored:
- -
- RF-front ends and antennas based on metamaterials: A metamaterial is frequently built by assembling a multitude of movable components in various ways on scales smaller than the frequencies. Despite the fact that research on terahertz communication has been done in this area since 2002, 2012, and 2015, Samsung’s work specifically looks at 3 different ways to use metamaterials. The employment of a meta-area focal point to refine a shaft form may be advantageous. The operation of a receiving wire for metadata is comparable to that of a radio wire used only for sending commands. Modifiable smart surfaces could be used for a proliferating path in cases when there is no LoS connectivity.
- -
- Orbital Angular Momentum: OAM enables high-request spatial multiplexing in environments where it would have been impossible to do so using conventional MIMO advances, such as LOS channels. In whatever instance, it seems like its realistic implementation ain’t perfectly possible.
- Range Sharing: An effect of area utilisation was examined in such a trial of distinctive range sharing. The study suggests using AI to foresee use from various aspects and so help minimise accidents with minimum overhead. By using split computing, devices may delegate complex computation tasks to other computing resources available within the company.
- Bharti Airtel & Vodafone India: An ambitious start into nearby 6G enhancement will result in licensed innovation (IP) creation for the Indian telecom biological system, according to 0.79% and Vodafone Idea NSE 2.60%. They stated that the Indian telecom sector and the academic community needed to work together with the telecom office and contribute to the 6G standard structure in accordance with international regulations. They stated that it was necessary for the Indian telecom sector and the academic community to collaborate with the telecom office and contribute to the 6G standard framework in accordance with global standards endorsed by the Third Generation Partnership Project (3GPP).
- Huawei Technologies Co. Ltd.: The most advanced mobile communications system available now is 6G, but it will do much more than just support exchanges. The introduction of 6G will truly usher in a time when everything will be sensed, connected, and clever. 6G will function as a circulated brain network that provides correspondence links to join the physical, digital, and natural universes. This will provide the eventual concept of Intelligence of Everything with a solid foundation to build upon. According to this CNET article, the Chinese corporation is reportedly looking into 6G at its research and development facility in Ottawa, Canada [27].
- LG Corp.: The 6G innovation would be displayed during LG’s participation in the 2021 Korea Science and Technology Exhibition from 22–24 December 2021, according to the tech titan from South Korea. During the Exhibition being held at Kintex, Ilsan, the organisation will highlight its efforts in 6G remote transmission and gathering. Interestingly, LG will announce a powered speaker for 6G in partnership with the German Fraunhofer Research Institute. In August 2021, LG aggressively tested the 6G power speaker in Berlin. Using the 6G recurrent frequency, the company had the possibility to efficiently communicate and obtain remote information within a 100-meter direct distance outside. The race for the business sending of 6G innovation is on and LG is focusing on 2029 for the commercialization of its 6G innovation. We’ll see whether LG will be pipped to the diadem by different organizations. LG, a regional rival of Samsung, launched a 6G testing facility in January 2019 in collaboration with the Korea Advanced Institute of Science and Technology (KAIST) [28].
- ZTE Corp.: Incorporating RIS, one of the core innovations of 5G-Advanced and 6G, into the 5G organisation, and understanding the co-location and co-inclusion of mmWave and Sub-6GHz in densely populated metropolitan areas, the organisation begins to take the lead in this area. This effectively lowers the cost of the arrangement, shortens the sending time, uses less network energy, and aids in the growth of green, low-carbon, and high-efficiency businesses. The RIS system from ZTE is the result of cross-disciplinary collaboration between electromagnetic meta-materials and contemporary distant correspondence technology. It’s a cutting-edge innovation in the area of distant communication and has become one of the key advancements of 5G-Advanced and 6G. ZTE’s RIS arrangement has some control over the bar shape through the control data sent by the base station to achieve precise beamforming, unlike the diffuse reflection or specular impression of normal materials. As a result, it is able to comprehend programmable remote channels and transform the latent versatile remote channels of traditional distant correspondence innovation into versatile reconfigurable remote channels. On 17 May 2020, Chinese telecom equipment provider ZTE and big transporter Chinese Unicom came to an agreement to jointly explore 6G possibilities and innovation patterns as well as to look into crucial innovation and standard collaborations [26].
- Beijing University of Posts and Telecommunications: Beijing Post and Telecommunications made a significant leap forward, lauded by CCTV, and held onto track assets. Be that as it may, the improvement of Chinese innovation organizations in the 6G field is certainly not clear. In actuality, according to the advancement of Chinese innovation organizations in the 6G organization, the United States is probably going to lose 6G once more. To “go with the run”! In the field of 6G organizations, Huawei Ren Zhengfei said before that Huawei’s 6G organization innovation is done at the same time as 5G, which likewise shows that Huawei has for quite some time been sent in the 6G field, and Huawei has additionally sent off a satellite client’s 6G innovation innovative work. This likewise shows that Huawei has proactively begun to create in the 6G field. We found two licenses by the school, which are unequivocally associated with Beyond 5th Generation and 6G advancements. The licenses, which guarantee require the beginning of August 2019, are CN110392350A & CN110430550A [29].
- College of Padova, Italy: This specific 6G White Paper is one of the twelve fresh, thematic 6G White Papers that the 6G Flagship initiative supports. It was funded by more than 50 professionals and supporters of impending 6G innovations. Here, it is anticipated that cutting-edge systems administration features will be explored in detail. These features will eventually influence the development of the 6G mobile network beyond the current 5G standard. Therefore, our focus is on the advancements and recommendations provided by the development of software and administration-based design. We also explore the major advancements that serve as the pillars for the advancement of 6G systems administration, taking into account the advancement of a cloud-based local mobile communication system and the adoption of a new IP design that supports high-accuracy services. In this white paper, we investigate the different examinations that can be acquired from the various sections engaged with the conveyance of a specific correspondence administration. We additionally examine the utility of high-accuracy start-to-finish telemetry and cross-portion examination. In a report titled Towards 6G Networks: Use Cases and Technologies, published by the University of Padova, the college’s specialists identify the major difficulties, chances, and use cases of 6G advancements that they feel will define 6G firms [26].
- College of Aveiro, Portugal: The necessity for 6G research is also made evident by such a test paper dated March 2019. The paper examines the major factors that are expected to propel the development of 6G. Additionally, it explores how applications for AI and machine learning can be effective in 6G technology. It introduces brand-new elements which are typical to find within the 6G range, including quantum correspondence and satellite coordination. Colleges are probably getting ignored or just not receiving much attention at a certain time, but they nevertheless seem to have played a pioneering role in setting the groundwork of 6G and selecting how that basis and development would be [30].
3.3. 6G Applications
- Ultra smart cities: Potential scenarios in an ultra-smart city would call for data rates around 1 Tbps, 3D connectivity, localization within 1 cm, and the reliability of 99.99%, for example, for autonomous vehicles, e-health, or smart industries. The measurements required for such apps in a smart city cannot be managed by 5G networks. Most 6G users will need mobility assistance between 240 and 1200 km/h. In order to coordinate while moving at high speeds, a self-driving car needs to interact with other vehicles and roadside sensors. In a different situation, drones would be needed to track the cars and act as information relays or hover ground stations for cross-communication. Extremely diminished-delay connectivity is among the essential criteria for autonomous cars and judgement, and under the aforementioned scenarios, 6G ought to be able to provide it [31].
- Multi-dimension Materiality: Online games that incorporate user-machine interaction with extremely high-quality graphics data and use AR or VR technologies generate a lot of data. Soon, 3D games and other cross-media will combine VR and AR to create totally immersive gaming experiences that reproduce reality utilising all five senses. The remarkable capacity, reliability, and information rate we need to convey enhanced information across a wireless medium will be made available by 6G. To put it another way, we want a great customer experience, low latency, excellent reliability, and high information density [31].
- Haptic communication: Imagine a healthcare system where an injured patient can only express their feelings verbally. In this case, a headband with intelligence may reconstruct brain signals and display them as a 3D video of a person’s vision, which a carer can view in real time using mobile networks. These haptic communication approaches will enable them to transmit information through touch. This situation is one of the planned applications of 6G technology, in which the network can support significantly higher data rates than 5G. Brain-controlled computer interfaces are another haptic network that is frequently used. In these networks, users use haptics to interact with their surroundings and control them using digital devices like a wireless chip installed in the brain that responds to emotions [31].
- Healthcare and remote-surgeries: Critical applications can benefit from ultra-low latency of less than 1 millisecond in 5G networks. Remote surgeries, on the other hand, are exceedingly sensitive, requiring a latency of less than 1 ms. The introduction of 6G networks will revolutionise telemedicine and remote medical care since it will eliminate time and location constraints [32]. The 6G vision calls for a data throughput of 1 Tbps and data reliability of at least 99.99%. In contrast to past networking technologies, 6G must strive to meet simultaneously the lowest and highest latency requirements. This is necessary for remote surgery because certain data streams should be received at the destination within a given minimal delay and other data streams should arrive within a specified maximum delay [31].
- Holographic communication: We will rapidly discover that the virtual world doesn’t really give us access to every aspect of reality as AR/VR apps develop. Telepresence has just exceeded in-person gatherings due to the current COVID-19 pandemic epidemic. For this project to remotely show an object or a person in actual, advanced virtual reality technology, bandwidth, and computations are required. To put it another way, a visual during a virtual conference might be a multi-dimensional, real-time projection that communicates the audio-visual impact of a person or thing. For a fully immersive VR experience, movies with 16 K resolution, 240 Hz scanning rate, and 3600 circular coverage must be delivered as a hologram. For example, in a social performance, a faraway musician may be introduced as a virtual presence to entertain those present. The same is true for remote and difficult-to-access regions such as mines and deep-ocean ports, where holographic communication might be employed for excavation and crew training. These transfers entail significant amounts of data, which 6G networks can handle [31].
- Tactile internet: Several devices are expected to communicate with each other instantly and interactively over 6G networks, allowing for data transmission, control, and real-time touch feedback. The sensations of touch and taste are combined with voice, video, and other forms of communication in tactile internetworking. For instance, employing virtualized holographic representations to access subsea boats and containers, perform remote operations, and educate astronauts in space stations calls for just a feeling of contact to do maintenance & perform distant instruction with incredibly reduced delay. Additionally, as the food industry aims to digitise users’ food access experiences, a key focus will be on the conveyance of taste and smell to improve users’ experiences. The 6G network can satisfy the requirements because of its increased data capacity and low latency [31].
- Internet-of-Things: The Internet of Things (IoT) is evolving into a crucial component of such future Internet and also is generating a significant amount of interest both from academics and businesses because of its enormous potential to provide services to customers in many facets of modernity. The introduction of 6G is expected to lead to new IoT apps. The most recent 6G applications in a variety of significant IoT fields, including Healthcare Internet of Things (H-IoT), Vehicular-Internet-of-Things (V-IoT), Autonomous Driving, Unmanned-Aerial-Vehicles (UAVs), Social Internet of Things (S-IoT), and IIoT, are extensively evaluated and assessed. They are briefed as below:
- 6G for Healthcare-Internet-of-Things (HIoT): By utilizing its technological solutions, 6G connectivity will transform the Internet of Things. In reality, to accomplish virtually significant health service with a quick and accurate remote medical, healthcare areas like remote patient monitoring demand reduced delay communications with the consistency requirement of over 99% [33]. It’s worth noting that with such a milliseconds latency and high reliability, 6G-robotics may indeed be utilised to do remote operations, enabling doctors who are located elsewhere to direct the process using robotic tools. Specifically, agreements are being implemented that really can take power over the exchange of health information throughout the operation and automated verification for demands for health information [34].
- 6G for Vehicular-Internet-of-Things (VIoT) and Autonomous-Driving (AD): The development of 6G technology has drastically altered vehicle IoT networks, which has revolutionised smart transportation systems. The study uses mMTCs in VIoT networks on 6G to enable V2X communication for the transmission of brief automotive data payloads by a large number of vehicles without the need for human interaction. In order to arrange available radio resources for V2X data connections within the specified frequency budget, signature features like time frames and hashing techniques are updated to reduce the likelihood of false positives. To fully utilise the potential of vehicle intelligence in VIoT, cutting-edge intelligence features with machine learning are integrated alongside the road components, which are responsible for evaluating traffic volume and weather forecasts relying on the accumulation of measurements from automobiles [34].
- 6G for Unmanned-Aerial-Vehicles (UAVs): UAVs network enables 6G-based broad IoT with simply a focus on UAV aviation process optimization. To do this, the issue of maximising the effectiveness of sending data must be addressed, taking into account large-scale channel status, onboard energy, and interfering temperature limitations. The appeal of clustered IoT stations led to the creation of a station grouping technique based on intra-cluster NOMA communication, which allows UAVs to broadcast radio transmissions to IoT terminals [35]. A synergistically optimal outcome of UAV path prediction and subplot allocation is reached by splitting the down-link transfer of energy and up-link data transfer subplots. A three-dimensional non-stationarity geometrical probabilistic model based on AV elevation, spatial consistency, and three-dimensional random UAV motion routes is constructed in order to accomplish this, and it makes use of a variety of channel arrangements [34].
- 6G for Satellite-Internet-of-Things (SIoT): It is essential to integrate satellite technology into current wireless connections if widespread IoT connectivity is to be achieved with 6G. Theoretically, satellites consist of three main network levels, namely LEO, MEO, and GEO, to provide global operations to terrestrial Internet of Things (IoT) customers. But in the 6G network, several satellites might be deployed in hundreds of orbits just above the earth, enabling LEO systems to truly achieve global reach and improved efficiency through frequency reuse. In addition, inter-satellite linkages will be constructed to enable interactions between satellites using THz bands, which have a much wider bandwidth than their mmWave and optical equivalents and can accommodate more satellites while attaining higher link stability. Every IoT device actually has to develop an asynchronous procedure by choosing one accessible preface from the offered preface collection for transmitting data in order to interact with the ground station through the uplink ports. In order to conduct yet another fractional time advance estimate and minimise extra signalling complexity and energy costs, an improved preface sequencing method is provided [34].
- 6G for Industrial-Internet-of-Things (IIoT): The Industrial IoT area has recently looked at the functions of 6G. Given the scarcity of IIoT devices, sensors are frequently deployed at random, which adds needless energy expenditures. Big data, prediction based on neural training algorithms, and engagement during the learning phase with historical datasets are all effective methods for doing smart sensor grouping using Convolutions. Much improved resource management with less energy use and much less complexity is confirmed by simulation analysis. By considering block size, CPU and memory utilisation, and network latency, a unified fog cloud computing architecture is used to manage blockchain information analytics. The 6G-IIoT apps that may use information learning to explain their very complicated design and extraordinarily large data quantities should pay special attention to this. Additionally, using UAVs for space-to-terrestrial communication has the significant potential to increase smart farming by enabling aerial-based soil measuring using their sensor system across a wide area of coverage. So, in order to give a comprehensive picture of a farm for automated development of land output, UAVs may also be used to assist crop photography from a low height. While 6G offers the IIoT previously unheard-of advantages, privacy and security pose serious obstacles that must be overcome [36].
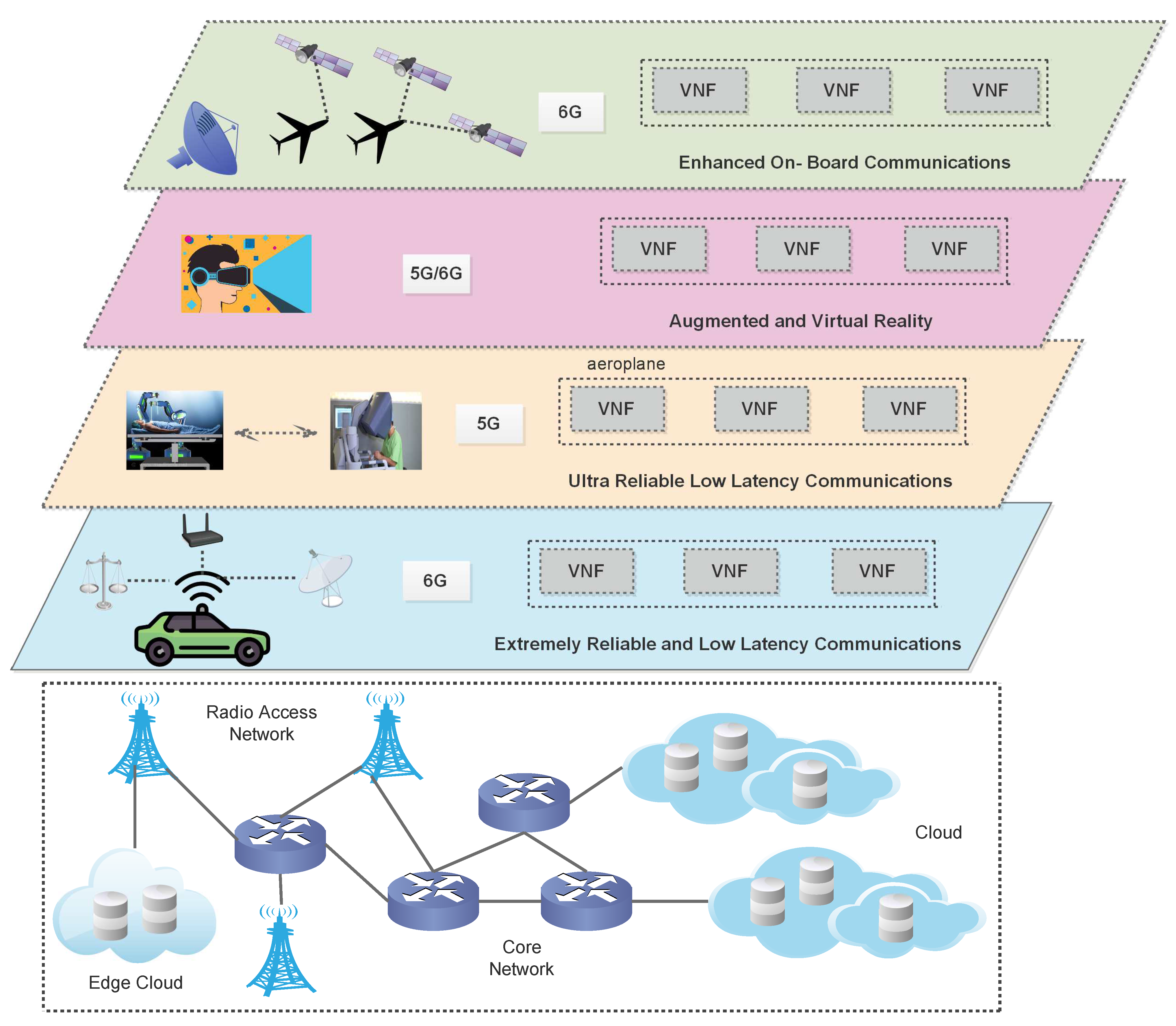
3.4. 6G Architecture
3.4.1. From Terrestrial to Ubiquitous 3D Coverage
- Space-Network: High throughput satellite (HTS) devices are known to provide broadband Internet solutions with prices and capacity that are equivalent to terrestrial offerings. Geostationary orbit (GEO), where the majority of communications satellites are located, is at a height of 35,786 km, which inevitably causes significant latency and makes connectivity with terrestrial mobile networks impossible. A non-geostationary orbit (NGSO) satellite system is proposed, and multiple satellite constellations are about to begin making a lot of money to provide low-latency, extremely high Internet connectivity. compared to a network of terrestrial optical fibres. Reduced latency connectivity may be available with an LEO system using co-routing radio-frequency and laser technologies.
- Aerial-Network: High altitude platforms (HAP), which normally work the stratosphere, and low altitude platforms (LAP), which are usually at a height little and over a few kilometres, can be generally categorised as two types of aerial networks. HAP networks can provide more coverage and can last longer than LAP networks. Unmanned aerial vehicle (UAV)-based LAP networks, on either hand, could be deployed faster, more easily modified to properly serve the communication system, and function great narrow communication. When facilities are severely damaged or absent altogether, such as in disaster emergency circumstances, UAV networks offer mobile communication. The suggested new trajectory optimisation & path guidance techniques considerably help save energy.
- Undersea-Network: The three main categories of underwater wireless networks are radio frequency, acoustical, and optical communications. Due to the unexpected and complex undersea setting, which results in challenging network coverage, severe signal attenuation, and mechanical damage to the equipment. There are numerous issues to be solved.
3.4.2. Direction to Smart Network Connectivity
- Real-time intelligent edge: The provision of engaging Intelligence applications will be necessary for the next-generation network, as well as a few services, notably autonomous cars, particularly susceptible to response delay and hence take real-time, intelligent interaction with their surroundings. These services cannot be provided by centralised cloud AI using static data; instead, the RTIE, which makes intelligent predictions, inferences, and decisions based on real-time information, is urgently needed.
- Intelligent-radio: IR is a richer and larger idea that distinguishes computational techniques and hardware. It runs as a single-entity methodology for estimating hardware resources Transceiver methods are capable of dynamic configuration in accordance with the hardware data. From this viewpoint, IR can utilise the spectrum available. Thanks to the physical layer. IR also can modify transmission methods and signal strength.
- Distributed-AI: The networking of the future would be a sizable decentralised framework where smart choices will be taken at many bitwise steps. Distributed AI uses shared resources in the system via a parallel procedure which necessitates separating the information and models in a suitable way to speed up understanding and increase inference consistency.
3.4.3. Novel Infrastructure
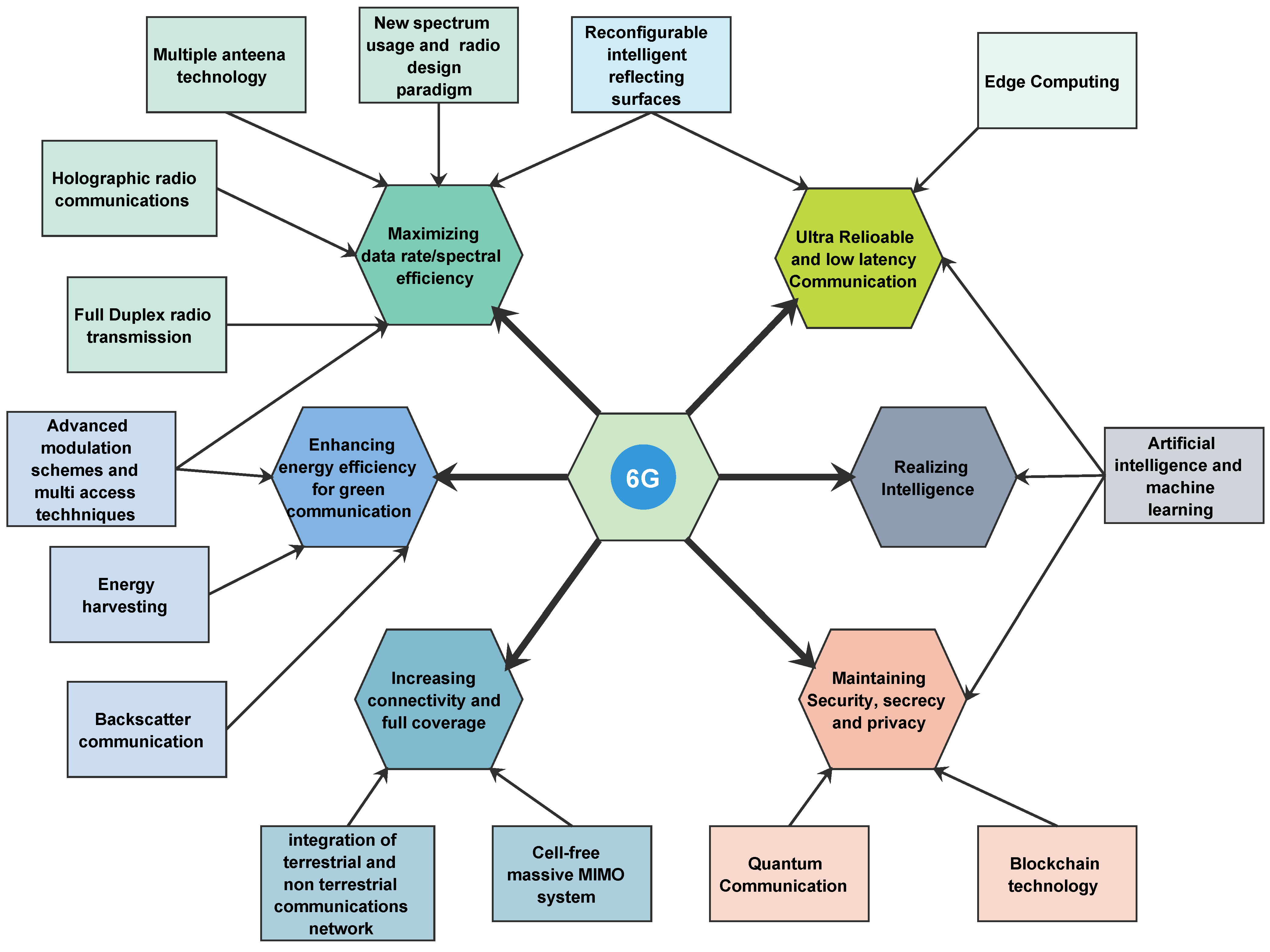
4. 6G Technologies
4.1. Wireless-Communication-Technology and System
Terahertz-Communication
- Proposals for transmission channels for terahertz space & terrestrial communications that are comparable in terms of channel size, modeling, and algorithms.
- THz Straight transmission, terahertz mongrel modulation, waveforms, multichannel coding, and terahertz broadcast modulation are a few examples of terahertz signal coding and modulation techniques.
- Synchronous THz transmission, essential transmitter architecture, increased baseband, signal technology computation, and design of integrated circuits methodologies are some examples of the research and development that goes into Radio wave system and THz tower architecture [12].
- Trials and error with the terahertz communication network and outfit developmental progress.
- The air’s humidity readily absorbs the terahertz spike as it travels through it. Additionally, it is appropriate for wireless high-speed and close-range communication.
- The beam is more focused, has greater directionality, and is more capable of interfering.
- Wider bandwidth and an advanced frequency characterise terahertz swells. They are able to satisfy the need for dB of wireless broadband transmission. The potential diapason bandwidth is knockouts of GHz, and the terahertz surge diapason has a frequency between 108 and 1013 GHz. It is capable of communicating at speeds more than Tb/s.
- The frequency of terahertz waves is a clear window in the atmosphere itself around bands of 350 µm, 450 µm, 620 µm, 735 µm, and 870 µm for communication in outer space. They are able to communicate across great distances with less power and reduced transmission rates.
- The Terahertz wavelengths, which have a limited spectrum, can also be used for Massive MIMO with extra antenna rudiments.
- Despite having a better energy efficiency than wireless optical communications, terahertz swells photon energy is very low—roughly eV. There is just 1/40th of visible light. It has an exceptionally high energy efficiency while carrying information.
- Robust penetration Matter may be accessed by terahertz waves with less attenuation. In certain unique instances, they’re appropriate for communication requirements [12].
- The bit rate may be raised by using high frequency carriers like millimetre and terahertz waves.
- Perfect connectivity between wired and wireless networks is made possible by the grounded signal generation and modulation techniques of photonics.
- The wireless connection in the 300 GHz band using the direct discovery approach has attained 30 Gbit/s error-free. The 600 GHz band guarantees advanced.
- Coherent discovery strategy has been investigated in order to boost bit rate and receiver perceptivity; a proof-of-conception experiment has been shown in the 100 GHz range.
- The usage of RTDs in 300 GHz band, in addition to Si grounded Tx/Rx, has been shown. Electronics grounded technique is crucial for low cost and/or consumer operations.
4.2. Next-Generation Antenna and RF Technology
4.3. Channel Coding for the Next Generation
4.4. Spectrum-Sharing
4.5. IoT and Blockchain Technology
5. Role of Network Slicing in 6G Technology
5.1. 6G-LEGO Framework for 6G Network Slices
5.2. Efficient Multi-Tenancy Framework for 6G Network Slicing
5.3. Multiple Autonomous Systems’ Network Slicing in 6G through NASOR
5.4. Artificial Intelligence in 6G Network Slicing
- Deep Learning: Network slicing and deep reinforcement learning are essential 6G network technologies. Multiple network slices from various tenants may be present in a 6G network. To enable intelligent and effective resource management, network providers must provide slices that fulfil the 6G use cases and quality of service and experience standards.Intelligent and efficient resource management necessitates anticipating tenant demand for services and achieving autonomous slice behavior. DRL allows for the analysis of techniques based on the optimization objective, network emphasis (core, edge, and end-to-end networks, for example), state space, action space, algorithms, and network architecture [58].
- ML: ML-based algorithms make it feasible for app-based traffic direction between networking devices, dynamic network segmentation for addressing various situations with variable quality of service needs, and pervasive connection across diverse 6G communication channels [59].In 6G wireless communication networks, machine learning technologies are used. Supervised, unsupervised, and reinforcement strategies are among these methods:
- Supervised learning: A labelled data set is used to train supervised learning algorithms. The system is aware of both the desired output data and the input data needed to make a supervised prediction. To be effective in any application, supervised learning requires a sufficient amount of data [60].
- Unsupervised learning: Unsupervised-learning algorithms must correctly anticipate the output from a set of unlabeled inputs, which is the main difference between supervised and unsupervised learning algorithms. These methods are most commonly employed for grouping and aggregation problems, but they can also be utilised to solve regression problems with excellent results [60].
- Reinforcement Learning: A performance indicator obtained from the model’s environment is used to accomplish RL. The model maximises the reward indication in an effort to produce the best performance level. Combining supervised and unsupervised learning techniques is what is known as RL [60].
5.5. Internet of Things in 6G Network Slicing
5.6. Optimization in 6G Network Slicing
5.7. Performance Metrics for 6G Network Slicing
5.7.1. Resource Allocation
5.7.2. Load Balancing
5.7.3. Slice Failure Management
5.8. Network Slicing Recent Advances
6. Implementation of Security in 6G Network
6.1. Security Challenges Associated with 6G Network
- Based on Artificial Intelligence: AI technologies have a stronger influence on privacy. In certain ways, the proper use of AI could safeguard privacy in 6G; however, in other ways, privacy breaches may happen. AI models are vulnerable to privacy threats throughout the development & training stages.
- Poisonous attacks: false regression results and misclassification due to the modification of training data using malicious samples that have been purposefully created (e.g., inadequate flagging or alteration of annotated data).
- Evasion attacks: by adding problems to the test cases, one might try to go past the learned model during the testing stage.
- ML API-based Attacks: Whenever a malicious party makes API requests and attacks a machine learning model to get predictions on feature vector inputs, model inverting (recovering data for training), model extract (revealing architectures while jeopardising model confidentiality), & membership inferences (using the model output to make predictions based upon training examples and ML models) could all be part of it.
- Physical assaults upon infrastructure and communications disruption choices and data management are hampered by deliberate interruptions & deficiencies in communication and computing infrastructure, which may even bring down whole AI systems.
- AI framework infringement: The majority of AI remedies make use of current AI/ML frameworks. The legitimacy of AI/ML functionalities is targeted by flaws in such artifacts or conventional attack vectors against its software, firmware, and hardware environment (particularly cloud-centric operations).
- Based on Distributed Ledger Technology: It’s probable that now the security concerns in Blockchain and smart contracts will have an implied impact on 6G networks as a consequence of the planned collaboration among DLT and 6G. The bulk of these attacks are the consequence of issues with software development, limitations imposed by programming languages, and vulnerabilities in network access protection. Additionally, both corporate and commercial blockchain systems could face similar security issues [82].
- The potential for an eclipse attack: blockchain nodes might receive misleading information that might lead to the validation of bogus transactions whenever connections are interrupted or dispersed.
- 51% Attack: Cyber attackers can dominate the blockchain if they corrupt open-source blockchain apps and get or control at least 51% of the mining power.
- End-user vulnerabilities: People may overlook or lose their private keys, which might compromise their blockchain-stored resources (e.g., identity theft, malware, phishing attacks).
- Software Vulnerability: The decentralised paradigm of several blockchains may be permanently damaged when such DLT initiatives attempt to deploy shakily specific responses on operational blockchains.
- Based on Quantum Communication: It’s really anticipated that quantum-safe encryption will be implemented in the post-quantum era as a result of the development of quantum computing. Due to its propensity to exploit the quantum characteristics of data, quantum computing might already be able to provide total randomization & security to enhance overall transmission quality. Physical layer security and post-quantum cryptography integration might lead to safe 6G lines of communication. Quantum security procedures have the ability to be used in prospective 6G app scenarios. Well, with quantum gains for supervised and unsupervised learning for clustering and classification jobs, quantum machine learning algorithms may increase confidentiality and security in communications systems [83].
- Quantum replication attack: making a perfect clone of a piece of data in a randomised quantum state without changing the data’s initial condition.
- Quantum collisions attack: Whenever 2 distinct inputs to a hashing algorithm deliver alike outputs in a quantum context, this is known as a quantum collision attack.
- Based on Terahertz: THz communications have been anticipated to play a crucial role in 6G technology. With enhanced security at the physical layer, the THz frequencies have improved signal directivity that prevents unauthorised parties from being in the same direct relationship as the authorised user to capture signals. Nevertheless, by positioning an item in the route of transmission to deflect radiation toward himself, an eavesdropper could also capture a signal in line-of-sight (LoS) broadcasts [84].
- Access control attacks For gaining entry to restricted resources or changing system settings, parties violate access rules, steal information, or kidnap users.
- Eavesdropping attack: Despite being resistant to intercepting assaults, broadcasts with strong polarity in small ranges are nevertheless vulnerable to hostile nodes capturing the signals.
- Based on Visible Light Communication: Owing to the benefits of radio frequency (RF) systems, like fast data speeds, a broad accessible spectrum, resilience over interference, & intrinsic security, VLC is indeed an optical wireless technology that has gained significant attention. Contrary to RF systems, VLC mechanisms can provide a better protection level since light cannot pass through solid objects like walls. The broadcasting format & LoS propagation of VLC systems, make them open to eavesdropping by unauthorised nodes present within the transmitters’ broadcasting area. For such construction of useful VLC systems, the confidentiality of the systems is an essential concern [85].
- Data-tampering or jamming attacks: Unauthorized transmissions can go unnoticed in VLC or hybrid VLC-RF systems. The likelihood of an effective assault is increased via a finely focused transmitter, such as those created by optical beamforming methods [86].
- Eavesdropping attack: Whenever node terminals are placed in public spaces, wide screens are present in the covering zones, & there are cooperative eavesdroppers, they become just as susceptible as RF.
- Metasurface-in-the-Middle Attack: Experts claim that 6G would potentially be greatly secured over wireless technology having greater beamwidths since it uses highly directional antennas. The idea is that by tightly focusing communication between the receiver and transmitter, the possibility of an eavesdropper intercepting a channel is reduced. Scientists at Rice University reported a man-in-the-middle attack targeted at 6G frequencies to highlight genuine security issues in an effort to verify that 6G is secured while technologies are being explored [87]. A well constructed metasurface may be used by an attacker to capture communication at 6G frequency, according to the experts, who refer to their assault as a metasurface-in-the-middle attack (MSITM). Through creating a metasurface & positioning it exactly in the path of vision between transmitter and receiver, the attacker can divert some part of sensitive communication. The resultant programmable scattering radiation patterns may create a diffraction-based eavesdropping route for the enemy. This could cause a phasing mismatch at the surface interface [88].
- Parameter attack: Injection assaults against cross-domain data services might result from improperly vetted parameters. Logic corruption, data manipulation, & data injection all happen. Data on the topology of the network is changed to introduce hostile nodes and fictitious linkages. Fake parameter injection that is ongoing might result in a denial-of-service assault that leaves data services unusable [89].
- Identity attack: Using vulnerabilities in identification & authorisation procedures for gain Harvested API keys are utilized as credentials. Unprotected E2E domain orchestration services are taken advantage of to alter settings in such an effort to violate service level agreements as well as to launch new instances that consume a lot of network resources [90].
- Man-in-the-middle attack: Through starting false failure occurrences & intercepting domain control messages, MITM assaults can redirect traffic through rogue endpoints [91].
- DDoS attacks: For 6G, DDoS assaults are anticipated to be significantly severe. Numerous vulnerable Internet of Things (IoT) devices might send enormous amounts of harmful traffic toward intruders. Edge servers that are frequently accessed, though, have less effective DDoS mitigation features. DDoS assaults can potentially be harmful to end devices [92].
- Deception attack: The 6G network’s transmitted data will be manipulated on purpose [93].
- Data leakage: Obtaining data about unauthorised parties’ intentions to undermine system security goals such as privacy and confidentiality, etc. Additional assaults might start as a result of all this.
- Improper configurations: Intent-based links, which are comparable to Zero-touch Ntworks & Service Management (ZSM) in that they may be open to data uncovering, may be used by 6G networks, opening them up to assaults including unwanted configurations & strange behavior. Unwanted setup of intent-based interfaces, like switching the security level from high to low or altering the linking of intent to action, might risk the security of the entire management architecture [94].
6.2. Remediation Steps to the Security Challenges
- Distributed and Scalable AI/ML security: Self-X (self-configuration, self-monitoring, self-healing, and self-optimization) tasks would be carried out by autonomous networks in 6G with little to no user intervention. Distributed AI/ML approaches should impose quick controls & analytics on the enormous quantity of data obtained in 6G networks because the ubiquitous usage of AI/ML would be implemented in such a distributed and large-scale system across multiple use cases, including network management. Distributed AI/ML may be used for security at many stages of 6G cybersecurity defence & prevention. The benefits of autonomous operation, improved precision, and predictive capabilities for security analytics are where AI/ML-driven cybersecurity finds its usefulness.
- Security for Quantum Communication: Quantum communication rules like quantum key distribution have the ability to be used in a variety of 6G scenarios, including those for ocean communication, satellite communication, terrestrial wireless networks, and THz communications systems. Quantum key distribution (QKD) uses quantum theory to create a private key and distribute it among two lawful parties, making it suitable for traditional key distribution systems. Quantum-safe encryption is expected to be implemented in the post-quantum period as a result of the development of quantum computing. The advent of quantum algorithms might enable the polynomial-time solution of the discrete logarithmic issue, the fundamental difficulty in existing asymmetric cryptography.
- Physical Layer Security: At each level, the network has security methods that may be employed individually to build an additional defence or collectively throughout levels for applications with low resources. 6G will make use of physical-level security techniques to offer an adaptable extra layer of security in an environment of novel enabling technologies. Classifying the channel’s backscatter as a protective measure against this eavesdropping method can help certain eavesdroppers be found, but not everyone of them. Molecular communication (MC) is a potential technology for 6G in several healthcare systems since bionanomachines interact using chemical signals or molecules in an aqueous environment. While dealing with a number of privacy and safety concerns relating to the communication, authentication, and encryption processes, MC manages to provide security for extremely confidential material.
- Solution to Parameter attack: Input validation, user authentication, access control, and rate restriction are ways to stop parameter assaults.
- Identity security: Identity assaults may be avoided by implementing authenticating (Signed JWT tokens, OpenID connect), authorising (role-based access control, attribute-based access control, and access control lists), and both.
- Prevention against Man-in-the-middle attack: Utilization of VPNs and safe secured communications (e.g., IPsec, SSLffLS & HIP).
- Prevention against DDoS attacks: Throttling or rate-limiting the use of APIs, deploying API gateways and micro gateways, and using AI-based API security to conduct continuous monitoring can all help avoid assaults that direct distributed denial of service.
- Resolution against Data leakage: The following methods can be used to prevent data exposure: authenticating the relationship among the intent producer and consumer, like signed JWT tokens and OpenID Connect; limiting access through access control measures like role-based access control and OAuth 2.0; and further utilising communication security through TCP/IP protocols (TLS 1.2).
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Dogra, A.; Jha, R.K.; Jain, S. A survey on beyond 5G network with the advent of 6G: Architecture and emerging technologies. IEEE Access 2020, 9, 67512–67547. [Google Scholar] [CrossRef]
- Attanasio, B.; Mazayev, A.; du Plessis, S.; Correia, N. Cognitive Load Balancing Approach for 6G MEC Serving IoT Mashups. Mathematics 2021, 10, 101. [Google Scholar] [CrossRef]
- Ng, S.X.; Zhu, K.; Hanzo, L. Distributed source-coding, channel-coding and modulation for cooperative communications. In Proceedings of the 2010 IEEE 72nd Vehicular Technology Conference-Fall, Ottawa, ON, Canada, 6–9 September 2010; pp. 1–5. [Google Scholar]
- Giordani, M.; Polese, M.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Toward 6G networks: Use cases and technologies. IEEE Commun. Mag. 2020, 58, 55–61. [Google Scholar] [CrossRef]
- Bhattarai, S.; Park, J.M.J.; Gao, B.; Bian, K.; Lehr, W. An overview of dynamic spectrum sharing: Ongoing initiatives, challenges, and a roadmap for future research. IEEE Trans. Cogn. Commun. Netw. 2016, 2, 110–128. [Google Scholar] [CrossRef]
- Sekaran, R.; Patan, R.; Raveendran, A.; Al-Turjman, F.; Ramachandran, M.; Mostarda, L. Survival study on blockchain based 6G-enabled mobile edge computation for IoT automation. IEEE Access 2020, 8, 143453–143463. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6G wireless communication systems: Applications, requirements, technologies, challenges, and research directions. IEEE Open J. Commun. Soc. 2020, 1, 957–975. [Google Scholar] [CrossRef]
- Saad, W.; Bennis, M.; Chen, M. A vision of 6G wireless systems: Applications, trends, technologies, and open research problems. IEEE Netw. 2019, 34, 134–142. [Google Scholar] [CrossRef]
- Mahmoud, H.H.H.; Amer, A.A.; Ismail, T. 6G: A comprehensive survey on technologies, applications, challenges, and research problems. Trans. Emerg. Telecommun. Technol. 2021, 32, e4233. [Google Scholar] [CrossRef]
- Elmeadawy, S.; Shubair, R.M. 6G wireless communications: Future technologies and research challenges. In Proceedings of the 2019 International Conference on Electrical and Computing Technologies and Applications (ICECTA), Ras Al Khaimah, United Arab Emirates, 19–21 November 2019; pp. 1–5. [Google Scholar]
- Gupta, A.; Singh, M. A study of wireless network: 6G technology. In Proceedings of the National Conference on Recent Innovation in Emerging Technology & Science, JB Institute of Technology, Dehradun, Indian, 6–7 April 2018. [Google Scholar]
- Lu, Y.; Zheng, X. 6G: A survey on technologies, scenarios, challenges, and the related issues. J. Ind. Inf. Integr. 2020, 19, 100158. [Google Scholar] [CrossRef]
- Ullah, Y.; Roslee, M.B.; Mitani, S.M.; Khan, S.A.; Jusoh, M.H. A Survey on Handover and Mobility Management in 5G HetNets: Current State, Challenges, and Future Directions. Sensors 2023, 23, 5081. [Google Scholar] [CrossRef]
- Wu, W.; Zhou, C.; Li, M.; Wu, H.; Zhou, H.; Zhang, N.; Shen, X.S.; Zhuang, W. AI-native network slicing for 6G networks. IEEE Wirel. Commun. 2022, 29, 96–103. [Google Scholar] [CrossRef]
- Xu, H.; Klaine, P.V.; Onireti, O.; Cao, B.; Imran, M.; Zhang, L. Blockchain-enabled resource management and sharing for 6G communications. Digit. Commun. Netw. 2020, 6, 261–269. [Google Scholar] [CrossRef]
- Moreira, R.; de Oliveira Silva, F. Towards 6G Network Slicing. In WORKSHOP DE REDES 6G (W6G); Sociedade Brasileira de Computação: Porto Alegre, Brazil, 2021; pp. 25–30. [Google Scholar] [CrossRef]
- Kukliński, S.; Tomaszewski, L.; Kołakowski, R.; Chemouil, P. 6G-LEGO: A framework for 6G network slices. J. Commun. Netw. 2021, 23, 442–453. [Google Scholar] [CrossRef]
- Krovvidi, M. Framework for slicing 6G networks for efficient multi-tenancy. Int. J. Adv. Res. Ideas Innov. Technol. 2021, 7, 703–708. [Google Scholar]
- 6G Market Size, Share, Growth Analysis, Opportunities, and Industry Forecast by 2028: Report Analysis 2021–2027. Available online: https://brandessenceresearch.com/technology-and-media/g-market-growth (accessed on 5 June 2023).
- Shahraki, A.; Abbasi, M.; Piran, M.; Taherkordi, A. A comprehensive survey on 6G networks: Applications, core services, enabling technologies, and future challenges. arXiv 2021, arXiv:2101.12475. [Google Scholar]
- 5G, vs. 6G | Difference between 5G and 6G. Available online: https://www.rfwireless-world.com/Terminology/Difference-between-5G-and-6G.html (accessed on 5 June 2023).
- Gawas, A.U. An overview on evolution of mobile wireless communication networks: 1G-6G. Int. J. Recent Innov. Trends Comput. Commun. 2015, 3, 3130–3133. [Google Scholar]
- Dangi, R.; Lalwani, P.; Choudhary, G.; You, I.; Pau, G. Study and investigation on 5G technology: A systematic review. Sensors 2021, 22, 26. [Google Scholar] [CrossRef]
- NTT Docomo, Inc. 5G Evolution and 6G. Available online: https://www.nttdocomo.co.jp/binary/pdf/corporate/technology/rd/docomo5g/20200122_01/DOCOMO_6G_White_PaperEN_20200124.pdf (accessed on 5 November 2022).
- Tripathi, N.D.; Reed, J.H. 5G Evolution—On the Path to 6G. Available online: https://www.mobilewirelesstesting.com/wp-content/uploads/2019/10/5G-evolution-on-the-path-to-6G-_wp_en_3608-3326-52_v0100.pdf (accessed on 5 November 2022).
- Top Companies and Universities mapping the 6G Technology. Available online: https://www.greyb.com/6g-companies/ (accessed on 10 October 2022).
- Boom, V.D. Huawei Starts Research on 6G Internet. Available online: https://www.cnet.com/tech/mobile/huawei-starts-research-on-6g-internet/ (accessed on 12 November 2022).
- Tomás, P.J. LG Electronics Showcases 6G Systems at Tech Conference. Available online: https://rcrwireless.com/20220523/5g/lg-electronics-showcases-6g-systems-tech-conference (accessed on 11 November 2023).
- Zhang, J.H.; Tang, P.; Yu, L.; Jiang, T.; Tian, L. Channel measurements and models for 6G: Current status and future outlook. Front. Inf. Technol. Electron. Eng. 2020, 21, 39–61. [Google Scholar] [CrossRef]
- Routray, S.; Mohanty, S. Why 6G? arXiv 2019, arXiv:1903.04837. [Google Scholar]
- Bhat, J.R.; Alqahtani, S.A. 6G ecosystem: Current status and future perspective. IEEE Access 2021, 9, 43134–43167. [Google Scholar] [CrossRef]
- Nasralla, M.M.; Khattak, S.B.A.; Ur Rehman, I.; Iqbal, M. Exploring the Role of 6G Technology in Enhancing Quality of Experience for m-Health Multimedia Applications: A Comprehensive Survey. Sensors 2023, 23, 5882. [Google Scholar] [CrossRef] [PubMed]
- Qadir, Z.; Le, K.N.; Saeed, N.; Munawar, H.S. Towards 6G Internet of Things: Recent advances, use cases, and open challenges. ICT Express 2023, 9, 296–312. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Ding, M.; Pathirana, P.N.; Seneviratne, A.; Li, J.; Niyato, D.; Dobre, O.; Poor, H.V. 6G Internet of Things: A comprehensive survey. IEEE Internet Things J. 2021, 9, 359–383. [Google Scholar] [CrossRef]
- Thantharate, A.; Tondwalkar, A.V.; Beard, C.; Kwasinski, A. ECO6G: Energy and cost analysis for network slicing deployment in beyond 5G networks. Sensors 2022, 22, 8614. [Google Scholar] [CrossRef] [PubMed]
- Kodrič, Ž.; Vrhovec, S.; JelovÄan, L. Securing edge-enabled smart healthcare systems with blockchain: A systematic literature review. J. Internet Serv. Inf. Secur. (JISIS) 2021, 11, 19–32. [Google Scholar]
- Ziegler, V.; Viswanathan, H.; Flinck, H.; Hoffmann, M.; Räisänen, V.; Hätönen, K. 6G architecture to connect the worlds. IEEE Access 2020, 8, 173508–173520. [Google Scholar] [CrossRef]
- Alhashimi, H.F.; Hindia, M.N.; Dimyati, K.; Hanafi, E.B.; Izam, T.F.T.M.N. Joint Optimization Scheme of User Association and Channel Allocation in 6G HetNets. Symmetry 2023, 15, 1673. [Google Scholar] [CrossRef]
- Wang, C.X.; You, X.; Gao, X.; Zhu, X.; Li, Z.; Zhang, C.; Wang, H.; Huang, Y.; Chen, Y.; Haas, H.; et al. On the road to 6G: Visions, requirements, key technologies and testbeds. IEEE Commun. Surv. Tutor. 2023, 25, 905–974. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Hasan, M.K.; Jang, Y.M. The role of optical wireless communication technologies in 5G/6G and IoT solutions: Prospects, directions, and challenges. Appl. Sci. 2019, 9, 4367. [Google Scholar] [CrossRef]
- Chen, Z.; Ma, X.; Zhang, B.; Zhang, Y.; Niu, Z.; Kuang, N.; Chen, W.; Li, L.; Li, S. A survey on terahertz communications. China Commun. 2019, 16, 1–35. [Google Scholar] [CrossRef]
- Kürner, T.; Priebe, S. Towards THz communications-status in research, standardization and regulation. J. Infrared Millim. Terahertz Waves 2014, 35, 53–62. [Google Scholar] [CrossRef]
- Song, H.J.; Nagatsuma, T. Present and future of terahertz communications. IEEE Trans. Terahertz Sci. Technol. 2011, 1, 256–263. [Google Scholar] [CrossRef]
- Kürner, T. Towards future THz communications systems. Terahertz Sci. Technol. 2012, 5, 11–17. [Google Scholar]
- Koenig, S.; Lopez-Diaz, D.; Antes, J.; Boes, F.; Henneberger, R.; Leuther, A.; Tessmann, A.; Schmogrow, R.; Hillerkuss, D.; Palmer, R.; et al. Wireless sub-THz communication system with high data rate. Nat. Photonics 2013, 7, 977–981. [Google Scholar] [CrossRef]
- Fischer, G. Next-generation base station radio frequency architecture. Bell Labs Tech. J. 2007, 12, 3–18. [Google Scholar] [CrossRef]
- Razaq, A.; Khan, A.A.; Shakir, U.; Arshad, A. Next generation flexible antennas for radio frequency applications. Trans. Electr. Electron. Mater. 2018, 19, 311–318. [Google Scholar] [CrossRef]
- Lassalle, R.; Alard, M. Principles of modulation and channel coding for digital broadcasting for mobile receivers. EBU Tech. Rev. 1987, 224, 68–190. [Google Scholar]
- Peha, J.M. Approaches to spectrum sharing. IEEE Commun. Mag. 2005, 43, 10–12. [Google Scholar] [CrossRef]
- Poryazov, S.A.; Saranova, E.T.; Andonov, V.S. Overall Model Normalization towards Adequate Prediction and Presentation of QoE in Overall Telecommunication Systems. In Proceedings of the 2019 14th International Conference on Advanced Technologies, Systems and Services in Telecommunications (TELSIKS), Nis, Serbia, 23–25 October 2019; pp. 360–363. [Google Scholar]
- Louvros, S.; Paraskevas, M.; Chrysikos, T. QoS-Aware Resource Management in 5G and 6G Cloud-Based Architectures with Priorities. Information 2023, 14, 175. [Google Scholar] [CrossRef]
- Bojović, P.D.; Malbašić, T.; Vujošević, D.; Martić, G.; Bojović, Ž. Dynamic QoS management for a flexible 5G/6G network core: A step toward a higher programmability. Sensors 2022, 22, 2849. [Google Scholar] [CrossRef]
- Rahmadika, S.; Astillo, P.V.; Choudhary, G.; Duguma, D.G.; Sharma, V.; You, I. Blockchain-based Privacy Preservation Scheme for Misbehavior Detection in Lightweight IoMT Devices. IEEE J. Biomed. Health Inform. 2022, 27, 710–721. [Google Scholar] [CrossRef] [PubMed]
- Kang, M. Examining the Impact of ICT Access and ICT Use on Trade in Services: Focused on Selected Service Categories. J. Internet Serv. Inf. Secur. (JISIS) 2021, 11, 58–75. [Google Scholar]
- Kumari, A.; Gupta, R.; Tanwar, S. Amalgamation of blockchain and IoT for smart cities underlying 6G communication: A comprehensive review. Comput. Commun. 2021, 172, 102–118. [Google Scholar] [CrossRef]
- Dangi, R.; Jadhav, A.; Choudhary, G.; Dragoni, N.; Mishra, M.K.; Lalwani, P. ML-Based 5G Network Slicing Security: A Comprehensive Survey. Future Internet 2022, 14, 116. [Google Scholar] [CrossRef]
- Yang, H.; Alphones, A.; Xiong, Z.; Niyato, D.; Zhao, J.; Wu, K. Artificial-intelligence-enabled intelligent 6G networks. IEEE Netw. 2020, 34, 272–280. [Google Scholar] [CrossRef]
- Hurtado Sánchez, J.A.; Casilimas, K.; Caicedo Rendon, O.M. Deep Reinforcement Learning for Resource Management on Network Slicing: A Survey. Sensors 2022, 22, 3031. [Google Scholar] [CrossRef]
- Patil, A.; Iyer, S.; Pandya, R.J. A Survey of Machine Learning Algorithms for 6G Wireless Networks. arXiv 2022, arXiv:2203.08429. [Google Scholar]
- Rekkas, V.P.; Sotiroudis, S.; Sarigiannidis, P.; Wan, S.; Karagiannidis, G.K.; Goudos, S.K. Machine Learning in Beyond 5G/6G Networks—State-of-the-Art and Future Trends. Electronics 2021, 10, 2786. [Google Scholar] [CrossRef]
- Choudhary, G.; Astillo, P.V.; You, I.; Yim, K.; Chen, R.; Cho, J.H. Lightweight misbehavior detection management of embedded IoT devices in medical cyber physical systems. IEEE Trans. Netw. Serv. Manag. 2020, 17, 2496–2510. [Google Scholar] [CrossRef]
- Zhou, Y.; Liu, L.; Wang, L.; Hui, N.; Cui, X.; Wu, J.; Peng, Y.; Qi, Y.; Xing, C. Service-aware 6G: An intelligent and open network based on the convergence of communication, computing and caching. Digit. Commun. Netw. 2020, 6, 253–260. [Google Scholar] [CrossRef]
- Guan, W.; Zhang, H.; Leung, V.C. Customized slicing for 6G: Enforcing artificial intelligence on resource management. IEEE Netw. 2021, 35, 264–271. [Google Scholar] [CrossRef]
- Khan, S.; Hussain, A.; Nazir, S.; Khan, F.; Oad, A.; Alshehri, M.D. Efficient and reliable hybrid deep learning-enabled model for congestion control in 5G/6G networks. Comput. Commun. 2022, 182, 31–40. [Google Scholar] [CrossRef]
- Andonov, V.; Poryazov, S.; Saranova, E. Generalized net model of a serial composition of services with intuitionistic fuzzy estimations of uncertainty. In Proceedings of the International Conference on Intelligent and Fuzzy Systems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 616–623. [Google Scholar]
- Poryazov, S.; Andonov, V.; Saranova, E.; Atanassov, K. Two approaches to the traffic quality intuitionistic fuzzy estimation of service compositions. Mathematics 2022, 10, 4439. [Google Scholar] [CrossRef]
- Khan, L.U.; Yaqoob, I.; Tran, N.H.; Han, Z.; Hong, C.S. Network slicing: Recent advances, taxonomy, requirements, and open research challenges. IEEE Access 2020, 8, 36009–36028. [Google Scholar] [CrossRef]
- Rost, P.; Mannweiler, C.; Michalopoulos, D.S.; Sartori, C.; Sciancalepore, V.; Sastry, N.; Holland, O.; Tayade, S.; Han, B.; Bega, D.; et al. Network slicing to enable scalability and flexibility in 5G mobile networks. IEEE Commun. Mag. 2017, 55, 72–79. [Google Scholar] [CrossRef]
- Zhang, S.; Liu, J.; Guo, H.; Qi, M.; Kato, N. Envisioning device-to-device communications in 6G. IEEE Netw. 2020, 34, 86–91. [Google Scholar] [CrossRef]
- Baumgartner, A.; Bauschert, T.; Koster, A.M.; Reddy, V.S. Optimisation models for robust and survivable network slice design: A comparative analysis. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar]
- Mei, J.; Wang, X.; Zheng, K. An intelligent self-sustained RAN slicing framework for diverse service provisioning in 5G-beyond and 6G networks. Intell. Converg. Netw. 2020, 1, 281–294. [Google Scholar] [CrossRef]
- Choudhary, G.; Kim, J.; Sharma, V. Security of 5G-mobile backhaul networks: A survey. arXiv 2019, arXiv:1906.11427. [Google Scholar]
- Sihag, V.; Choudhary, G.; Vardhan, M.; Singh, P.; Seo, J.T. PICAndro: Packet InspeCtion-Based Android Malware Detection. Secur. Commun. Netw. 2021, 2021, 9099476. [Google Scholar] [CrossRef]
- Porambage, P.; Gür, G.; Osorio, D.P.M.; Liyanage, M.; Gurtov, A.; Ylianttila, M. The roadmap to 6G security and privacy. IEEE Open J. Commun. Soc. 2021, 2, 1094–1122. [Google Scholar] [CrossRef]
- Wang, M.; Zhu, T.; Zhang, T.; Zhang, J.; Yu, S.; Zhou, W. Security and privacy in 6G networks: New areas and new challenges. Digit. Commun. Netw. 2020, 6, 281–291. [Google Scholar] [CrossRef]
- Narteni, S.; Vaccari, I.; Mongelli, M.; Aiello, M.; Cambiaso, E. Evaluating the Possibility to Perpetrate Tunneling Attacks Exploiting Short-Message-Service. J. Internet Serv. Inf. Secur. (JISIS) 2021, 11, 30–46. [Google Scholar]
- Siriwardhana, Y.; Porambage, P.; Liyanage, M.; Ylianttila, M. AI and 6G security: Opportunities and challenges. In Proceedings of the 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 616–621. [Google Scholar]
- Ylianttila, M.; Kantola, R.; Gurtov, A.; Mucchi, L.; Oppermann, I.; Yan, Z.; Nguyen, T.H.; Liu, F.; Hewa, T.; Liyanage, M.; et al. 6G white paper: Research challenges for trust, security and privacy. arXiv 2020, arXiv:2004.11665. [Google Scholar]
- Dave, G.; Choudhary, G.; Sihag, V.; You, I.; Choo, K.K.R. Cyber security challenges in aviation communication, navigation, and surveillance. Comput. Secur. 2022, 112, 102516. [Google Scholar] [CrossRef]
- Porambage, P.; Gür, G.; Osorio, D.P.M.; Livanage, M.; Ylianttila, M. 6G security challenges and potential solutions. In Proceedings of the 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 622–627. [Google Scholar]
- Nayak, S.; Patgiri, R. 6G communication technology: A vision on intelligent healthcare. In Health Informatics: A Computational Perspective in Healthcare; Springer: Berlin/Heildeberg, Germany, 2021; pp. 1–18. [Google Scholar]
- Alraih, S.; Shayea, I.; Behjati, M.; Nordin, R.; Abdullah, N.F.; Abu-Samah, A.; Nandi, D. Revolution or evolution? Technical requirements and considerations towards 6G mobile communications. Sensors 2022, 22, 762. [Google Scholar] [CrossRef] [PubMed]
- Syed, S.A.; Sheela Sobana Rani, K.; Mohammad, G.B.; Kumar, G.A.; Chennam, K.K.; Jaikumar, R.; Natarajan, Y.; Srihari, K.; Barakkath Nisha, U.; Sundramurthy, V.P.; et al. Design of resources allocation in 6G cybertwin technology using the fuzzy neuro model in healthcare systems. J. Healthc. Eng. 2022, 2022, 5691203. [Google Scholar] [CrossRef] [PubMed]
- Nayak, S.; Patgiri, R. 6G Communication: A Vision on the Potential Applications. In Edge Analytics; Springer: Berlin/Heildeberg, Germany, 2022; pp. 203–218. [Google Scholar]
- Wei, Z.; Liu, F.; Masouros, C.; Su, N.; Petropulu, A.P. Toward Multi-Functional 6G Wireless Networks: Integrating Sensing, Communication, and Security. IEEE Commun. Mag. 2022, 60, 65–71. [Google Scholar] [CrossRef]
- Shah, K.; Chadotra, S.; Tanwar, S.; Gupta, R.; Kumar, N. Blockchain for IoV in 6G environment: Review solutions and challenges. In Cluster Computing; Springer: Berlin/Heildeberg, Germany, 2022; pp. 1–29. [Google Scholar]
- Hakeem, S.A.A.; Hussein, H.H.; Kim, H. Vision and research directions of 6G technologies and applications. J. King Saud-Univ.-Comput. Inf. Sci. 2022, 34, 2419–2442. [Google Scholar]
- Asghar, M.Z.; Memon, S.A.; Hämäläinen, J. Evolution of Wireless Communication to 6G: Potential Applications and Research Directions. Sustainability 2022, 14, 6356. [Google Scholar] [CrossRef]
- Zuppelli, M.; Carrega, A.; Repetto, M. An Effective and Efficient Approach to Improve Visibility Over Network Communications. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. (JoWUA) 2021, 12, 89–108. [Google Scholar]
- Heinz, C.; Zuppelli, M.; Caviglione, L. Covert Channels in Transport Layer Security: Performance and Security Assessment. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. (JoWUA) 2021, 12, 22–36. [Google Scholar]
- Kim, J.; Choudhary, G.; Heo, J.; Duguma, D.G.; You, I. 5G wireless P2MP backhaul security protocol: An adaptive approach. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 265. [Google Scholar] [CrossRef]
- Nowakowski, P.; ÅÃrawski, P.; Cabaj, K.; Mazurczyk, W. Detecting Network Covert Channels using Machine Learning, Data Mining and Hierarchical Organisation of Frequent Sets. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. (JoWUA) 2021, 12, 20–43. [Google Scholar]
- Shaikhanov, Z.; Hassan, F.; Guerboukha, H.; Mittleman, D.; Knightly, E. Metasurface-in-the-middle attack: From theory to experiment. In Proceedings of the 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks, San Antonio, TX, USA, 16–19 May 2022; pp. 257–267. [Google Scholar]
- Chen, X.; Feng, W.; Ge, N.; Zhang, Y. Zero Trust Architecture for 6G Security. arXiv 2022, arXiv:2203.07716. [Google Scholar] [CrossRef]


| Abbreviations | Full Forms | Abbreviations | Full Forms |
|---|---|---|---|
| 3GPP | Third Generation Partnership Project | MNO | Mobile network operator |
| 5G | Fifth Generation Wireless Network | MSITM | Metasurface-in-the-middle Attack |
| 6G | Sixth Generation Wireless Network | NASOR | Network And Slice Orchestrator |
| AI | Artificial Intelligence | NFV | Network function virtualization |
| AMPS | Advanced Mobile Phone Service | NOMA | Non-orthogonal Multiple Access |
| AR | Augmented Reality | NS | Network Slicing |
| BDMA | Beam Division Multiple Access | OAM | Operations, Administration and Maintenance |
| CN | Core Network | OCC | Optical Communication Channel |
| DDoS | Distributed Denial-of-Service Attack | OFDM | Orthogonal Frequency Division Multiplexing |
| DLT | Distributed ledger technology | OMA | Orthogonal Multiple Access |
| D-OMA | Delta-Orthogonal Multiple Access | ORAN | Open Radio Access Network |
| DoS | Denial-of-Service | OWC | Optical wireless communication |
| DRL | Deep Reinforcement Learning | PKI | Public Key Infrastructure |
| DRM | Digital Rights Management | RAN | Radio access network |
| DSCM | Digital Sub-Carrier Multiplexing | QOS | Quality of Service |
| DTTCM | Distributed Turbo Trellis Coded Modulation | RF | Radio Frequency |
| E2E | End to End | RIS | Reconfigurable intelligent surfaces |
| ECC | Elliptic Curve Encryption | RL | Reinforcement Learning |
| eMBB | Enhanced Mobile Broadband | RSMA | Resource Spread Multiple Access |
| eMTC | Enhanced Machine Type Communication | RTD | Real Time Difference |
| ETSI | European Telecommunications Standards Institute | RTIE | Real-time intelligent edge |
| eURLLC | Enhanced Ultra-Reliable Low Latency Communications | SDN | Software-Defined Networking |
| FBMC | Filterbank Multicarrier | SLA | Service-Level Agreement |
| FDMA | Frequency Division Multiplex Access | TDMA | Time Division Multiple Access |
| feUMBB | Further Enhance Ultra-Mobile Broadband | THz | Terahertz |
| FSO | Free-space optical communication | TLS | Transport Layer Security |
| FTN | Faster-than-Nyquist | TPG | Test Pattern Generator |
| HAP | High-Altitude Platform | TTCM | Turbo Trellis enCiphered Modulation |
| IIoT | Industrial Internet of things | UAV | Unmanned Aerial Vehicle |
| IoE | Internet of Everything | UHDD | ultra-High Density Data services |
| IoT | Internet of Things | uHEE | ultra-High Energy Efficiency |
| IPsec | Internet Protocol Security | uHRS | ultra-High Reliability and Sensing |
| IR | Infrared radiation | uHRUx | ultra-High Reliability and User experience |
| JWT | JSON Web Token | uHS | ultra-High Security |
| KPIs | Key Programmable Interface | uHSLLC | ultra High Sensing Low Latency Communications |
| LAP | Link Access Protocol | uHSLo | ultra-High Sensing and Localization |
| LDPC | Low-Density Parity-Check | uLLRS | ultra-Low Latency Reliability and Secure |
| LiFi | Light-Fidelity | UMTS | Universal Mobile Telecommunications Service |
| LMDS | Local Multipoint Distribution Service | uRLLC | Ultra-Reliable Low Latency Communication |
| LoS | Line of sight | V2X | Vehicle to Everything |
| LTE-A | Long Term Evolution-Advance | VLC | Visible light communication |
| MIMO | Multiple-Input Multiple-Output | VNF | Virtualized Network Functions |
| MITM | Man In The Middle Attack | VR | Virtual Reality |
| ML | Machine Learning | WCDMA | Wideband Code Division Multiple Access |
| mMTC | Massive Machine Type Communication | WiMAX | Worldwide Interoperability for Microwave Access |
| mmWave | millimeter Wave | XR | Extended Reality |
| Generations | Access Techniques | Switching Techniques | Error Correction Mechanism | Data Rate | Frequency Band | Bandwidth | Application | Description |
|---|---|---|---|---|---|---|---|---|
| 1G | FDMA | Circuit Switching | NA | 2.4 kbps | 800 MHz | 30 KHz | Voice | Let us to have a conversation. |
| 2G | TDMA, CDMA | Circuit Switching | NA | 10 kbps | 800 MHz, 900 MHz, 1800 MHz, 1900 MHz | 200 kHz | Voice and Data | Allow us to send messages and travel with better data services. |
| 3G | CDMA, WCDMA | Circuit and Packet Switching | Turbo Codes | 384 kbps to 5 Mbps | 800 MHz, 850 MHz, 900 MHz, 1800 MHz, 1900 MHz, 2100 MHz | 5 MHz | Voice, Data, and Video Calling | Allow us to experiment by surfing the internet and using mobile applications. |
| 4G | OFDMA | Packet switching | Turbo Codes | 100 Mbps to 200 Mbps | 2.3 GHz, 2.5 GHz and 3.5 GHz initially | 15 MHz | Voice, Data, Video Calling, HD Television, and Online Gaming. | Allow us to use unified network topologies and IP protocols to communicate voice and data via fast broadband internet. |
| 5G | NOMA | Packet Switching | LDPC | 10 Gbps to 50 Gbps | 1.8 GHz, 2.6 GHz and 30–300 GHz | 5–100 MHz | Voice, Data, Video Calling, Ultra HD video, Virtual Reality applications | IoT and V2Xhave broadened the scope of broadband wireless services beyond mobile internet. |
| 6G | D-OMA, RSMA | Packet Switching | LDPC with improved encoder and decoder(TPG decoder) | Up to 1 Tbps | 90 GHz-140 GHz, 110 GHz to 170 GHz, 140 GHz to 220 GHz, 170 GHz to 260 GHz, 220 GHz to 325 GHz, 325 GHz to 500 GHz, 500 GHz to 750 GHz, 750 GHz to 1100 GHz, up to 3000 GHz | 7–20 GHz | Voice, Data, Video Calling, AI, optical wireless communication (OWC), 3D networking, unmanned aerial vehicles (UAV), and wireless power transfer | End-users will be ableto smoothly and rapidly access a variety of high-end servicesthrough 6G. End-users, on the other hand, will require devices with powerful batteries in order to access high-end services without delayor disruption. The goal of 6G is to double the battery life of gadgets. |
| Authors | Throughput | Latency | Energy Efficiency | Spectral Efficiency | Transmission Rate | Coverage | Cost |
|---|---|---|---|---|---|---|---|
| Yang Lu et al. [12] | ✓ | ✓ | ✓ | * | * | ✓ | * |
| MostafaZaman Chowdhury et al. [7] | * | ✓ | ✓ | ✓ | * | * | ✓ |
| MostafaZaman Chowdhury et al. [40] | * | ✓ | * | * | * | * | X |
| Chen, Z. et al. [41] | * | X | X | * | ✓ | X | * |
| Kürner, T. [44] | * | X | X | * | * | X | X |
| Song [43] | X | X | X | X | ✓ | X | X |
| Kürner, T. [42] | X | X | X | * | X | X | X |
| Fischer, G. [46] | X | X | X | X | X | X | ✓ |
| Razaq, A et al. [47] | X | X | X | X | * | * | ✓ |
| Lassalle, R. et al. [48] | X | X | X | * | ✓ | X | X |
| Ng, S.X. et al. [3] | ✓ | X | X | X | X | X | X |
| Peha, J.M. [49] | X | X | X | ✓ | * | X | X |
| Bhattarai, S. et al. [5] | X | * | X | * | X | * | ✓ |
| Sekaran, R. et al. [6] | * | ✓ | X | X | X | * | ✓ |
| Kumari, A. et al. [55] | ✓ | ✓ | X | X | X | X | ✓ |
| Authors | Key Contribution | R1 | R2 | LB | RA | SFM | Z1 | Z2 | Z3 | SEC |
|---|---|---|---|---|---|---|---|---|---|---|
| [14] | (AI)-native network slicing architecture | ✓ | X | X | ✓ | X | ✓ | ✓ | X | X |
| [69] | Implementation of intelligent D2D in future 6G. | ✓ | X | X | ✓ | X | ✓ | ✓ | ✓ | ✓ |
| [67] | Artificial Intelligence-based Network slicing framework for future 6G. | X | ✓ | X | ✓ | X | ✓ | ✓ | ✓ | ✓ |
| [15] | Blockchain’s potential for resource management and sharing in 6G. | X | X | X | ✓ | X | ✓ | X | ✓ | ✓ |
| [64] | Hybrid deep learning-enabled efficient congestion control technique. | X | X | ✓ | ✓ | ✓ | ✓ | X | ✓ | ✓ |
| [70] | Mathematical model for the generic network slice design. | X | X | X | ✓ | ✓ | X | X | X | ✓ |
| [63] | Resource management paradigm employing deep reinforcement learning. | ✓ | ✓ | X | ✓ | X | ✓ | ✓ | X | X |
| [1] | 6G Network Architecture based on virtualized network slicing | ✓ | ✓ | X | ✓ | X | ✓ | ✓ | ✓ | ✓ |
| [17] | Self-managed and self-orchestrated slices sustained using 6G-LEGO. | ✓ | ✓ | X | ✓ | X | X | X | ✓ | ✓ |
| [16] | Recursive network slicing between several Autonomous Systems using NASOR. | X | X | X | X | X | ✓ | X | X | ✓ |
| [58] | Deep Reinforcement Learning for network slicing resource management. | ✓ | ✓ | X | ✓ | X | X | ✓ | ✓ | ✓ |
| [57] | Smart 6G Networks with AI. | X | ✓ | X | ✓ | X | ✓ | ✓ | X | ✓ |
| [59] | Algorithms for Machine Learning in 6G Wireless Networks | X | X | X | ✓ | X | ✓ | ✓ | ✓ | ✓ |
| [62] | A smart and open 6G network. | ✓ | X | X | X | X | X | ✓ | ✓ | ✓ |
| [71] | For 6G, an intelligent self-sustaining RAN slicing framework has been developed. | X | ✓ | X | ✓ | X | ✓ | ✓ | ✓ | X |
| [2] | 6G Cognitive Load Balancing Methodology | X | ✓ | ✓ | X | X | ✓ | ✓ | ✓ | X |
| [20] | The report discusses potential 6G requirements and trends. | X | X | X | ✓ | X | ✓ | ✓ | ✓ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dangi, R.; Choudhary, G.; Dragoni, N.; Lalwani, P.; Khare, U.; Kundu, S. 6G Mobile Networks: Key Technologies, Directions, and Advances. Telecom 2023, 4, 836-876. https://doi.org/10.3390/telecom4040037
Dangi R, Choudhary G, Dragoni N, Lalwani P, Khare U, Kundu S. 6G Mobile Networks: Key Technologies, Directions, and Advances. Telecom. 2023; 4(4):836-876. https://doi.org/10.3390/telecom4040037
Chicago/Turabian StyleDangi, Ramraj, Gaurav Choudhary, Nicola Dragoni, Praveen Lalwani, Utkarsh Khare, and Souradeep Kundu. 2023. "6G Mobile Networks: Key Technologies, Directions, and Advances" Telecom 4, no. 4: 836-876. https://doi.org/10.3390/telecom4040037
APA StyleDangi, R., Choudhary, G., Dragoni, N., Lalwani, P., Khare, U., & Kundu, S. (2023). 6G Mobile Networks: Key Technologies, Directions, and Advances. Telecom, 4(4), 836-876. https://doi.org/10.3390/telecom4040037








