Abstract
The increasing adoption of electric vehicles (EVs) within intelligent transportation systems (ITSs) has elevated the importance of cybersecurity, especially with the rise in Vehicle-to-Everything (V2X) communications. Traditional intrusion detection systems (IDSs) struggle to address the evolving and complex nature of cyberattacks in such dynamic environments. To address these challenges, this study introduces a novel deep learning-based IDS designed specifically for EV communication networks. We present a hybrid model that integrates convolutional neural networks (CNNs), long short-term memory (LSTM) layers, and adaptive learning strategies. The model was trained and validated using the VeReMi dataset, which simulates a wide range of attack scenarios in V2X networks. Additionally, an ablation study was conducted to isolate the contribution of each of its modules. The model demonstrated strong performance with 98.73% accuracy, 97.88% precision, 98.91% sensitivity, and 98.55% specificity, as well as an F1-score of 98.39%, an MCC of 0.964, a false-positive rate of 1.45%, and a false-negative rate of 1.09%, with a detection latency of 28 ms and an AUC-ROC of 0.994. Specifically, this work fills a clear gap in the existing V2X intrusion detection literature—namely, the lack of scalable, adaptive, and low-latency IDS solutions for hardware-constrained EV platforms—by proposing a hybrid CNN–LSTM architecture coupled with an elastic weight consolidation (EWC)-based adaptive learning module that enables online updates without full retraining. The proposed model provides a real-time, adaptive, and high-precision IDS for EV networks, supporting safer and more resilient ITS infrastructures.
1. Introduction
The global shift toward sustainable transportation has accelerated the adoption of electric vehicles (EVs), driven by environmental concerns, energy efficiency, and the rapid development of intelligent transportation systems (ITSs) [1,2]. A core enabler of this transformation is Vehicle-to-Everything (V2X) communication, which integrates Vehicle-to-Infrastructure (V2I), Vehicle-to-Vehicle (V2V), Vehicle-to-Pedestrian (V2P), and Vehicle-to-Cloud (V2C) protocols. These interconnections support real-time data exchange for traffic optimization, collision avoidance, and autonomous navigation [3,4]. However, this growing connectivity significantly increases the cyberattack surface of modern EVs. Embedded electronic control units (ECUs), telematics systems, over-the-air (OTA) updates, and edge-computing-based V2X modules are vulnerable to threats such as spoofing, denial-of-service (DoS) attacks, packet injection, and data tampering [5,6,7]. As EVs evolve into networked, intelligent entities, the complexity of their security requirements increases, leading to a demand for robust and adaptive protection mechanisms that can function in real-time and within hardware constraints.
Traditional cybersecurity mechanisms such as rule-based intrusion detection systems (IDSs) and static firewalls fall short in addressing the evolving threat landscape [8]. These systems often fail to detect unknown or zero-day attacks and cannot adapt to emerging attack patterns due to their reliance on predefined signatures and fixed logic [9]. In response, artificial intelligence (AI) and machine learning (ML) techniques—particularly deep learning (DL)—have emerged as powerful alternatives that are capable of identifying complex patterns in high-dimensional data and learning from evolving threat vectors [10]. Convolutional neural networks (CNNs) and long short-term memory (LSTM) networks are among the most promising DL techniques for intrusion detection. CNNs are effective in extracting spatial features from network traffic, while LSTMs are adept at capturing temporal dependencies in sequential data [11]. Hybrid architectures combining CNN and LSTM layers have shown considerable success in cybersecurity applications across various domains, including Industrial IoT and cloud computing [12]. When applied to V2X environments, these models offer the potential for real-time accurate threat detection by leveraging both spatial and temporal dimensions of vehicular communication. Nevertheless, implementing such intelligent models in the context of EVs presents specific challenges, with the limited computational resources of on-board units (OBUs) and roadside units (RSUs), heterogeneity of V2X protocols, lack of large and diverse labeled datasets, and need for low-latency responses constraining the practical deployment of advanced AI models [13]. Furthermore, maintaining low false-positive rates, fast adaptability to novel threats, and energy efficiency are critical for ensuring the real-world viability of such models [14].
In light of these considerations, this study proposes a hybrid deep learning architecture designed to improve cybersecurity in V2X communications. The proposed model integrates CNN and LSTM layers to extract both spatial and temporal threat signatures from vehicular data streams, allowing for enhanced detection of known and unknown intrusions. To address the need for adaptability, we incorporate an adaptive learning module that enables online updates without full retraining, thus improving resilience to emerging attack vectors. The system is engineered to operate within the computational limits of EV platforms, and is evaluated in simulated ITS environments to determine its detection accuracy and real-time responsiveness.
The primary contributions of this study are as follows:
- We propose a novel hybrid deep learning model that captures both spatial and temporal patterns in V2X communications to detect cyber threats with high accuracy.
- An adaptive learning module is integrated to enable real-time learning and threat model updating, increasing the system’s robustness against evolving attack types.
- A complete cybersecurity monitoring framework is implemented and optimized for in-vehicle and roadside hardware, including modules for traffic capture, threat classification, and mitigation strategies.
The remainder of this paper is structured as follows: Section 2 presents a review of the related work and identifies gaps in current IDS approaches for EVs. Section 3 details the proposed framework. Section 4 discusses the experimental results and performance benchmarking. Section 5 concludes this study and outlines directions for future work.
2. Related Work
The cybersecurity landscape of EV communication networks has attracted significant attention in recent years, especially as V2X systems grow more complex and widely deployed. A variety of AI-based IDSs have been proposed with the aim of detecting and mitigating cyber threats across vehicle infrastructures. However, existing approaches face several limitations in terms of their adaptability, real-world applicability, and performance under dynamic network conditions.
Basnet [15] proposed an LSTM-based IDS to detect false data injection (FDI) and distributed denial-of-service (DDoS) attacks in 5G-enabled EV charging stations powered by photovoltaics. While their solution effectively detected covert attacks using electrical fingerprints, the reliance on synthetic datasets limits its generalizability.
Zhang et al. [16] introduced a cybersecurity evaluation framework (CSEF) for electronic control units (ECUs), extending the threat analysis and risk assessment (TARA) methodology. Though useful for security validation of on-board systems, its absence of real-time simulations and scalability tests limits its feasibility for deployment. Meanwhile, Das et al. [17] conducted a holistic threat analysis using the STRIDE model across five security domains. Their framework was successfully used to assess practical EV attack scenarios, but lacked adaptability to evolving technologies and dynamic threat models.
Machine learning has also been employed in hybrid and federated architectures. Venkatasamy et al. [18] proposed a privacy-preserving AI-based IDS using deep learning for vehicular networks. Although the system achieved high accuracy, it still requires real-world validation and improved adaptability. Khalil et al. [19] advanced this concept by applying a BiGAN-based IDS deployed on edge nodes selected using the TOPSIS method. Their system exhibited high precision in isolating malicious nodes in V2V networks, but was constrained by its lack of adaptability to changing environments.
Efforts to address scalability and heterogeneity concerns in edge-to-cloud environments have been led by Shrivastwa et al. [20], who introduced a programmable IDS framework that correlates anomalies across a distributed IoT fleet. Despite its improved detection accuracy, their solution struggled with heterogeneous data formats. Talaat et al. [21] proposed a fog-based eco-assistive traffic management system combining V2X data and an AI-based incentive engine for green driving. Although effective for mobility optimization, its static learning approach hinders its responsiveness to real-time cyber threats.
Several studies have focused on securing in-vehicle networks; for example, Chen et al. [22] developed CNN and CNN–LSTM models trained on the OCTANE dataset to detect spoofing and flooding attacks on the CAN bus. Despite achieving high accuracy, these models still require broader architectural validation and improved real-time adaptability. Ali et al. [23] addressed data privacy issues by introducing a federated learning-based IDS (FL-IDS) that maintains model accuracy while avoiding centralized data aggregation; however, there remained concerns regarding its scalability and robustness under real-world conditions.
In their recent work, Alsokhiry et al. [24] introduced a dynamic offense–defense strategy for malware mitigation in sensor-enabled EV networks, emphasizing the energy cost of attacks; however, their evaluation was limited to simulations. ElKashlan et al. [25] proposed an ensemble IDS architecture using CNN, LSTM, and GRU networks for intrusion detection in EV charging stations. This multi-class classification model achieved high accuracy but requires further validation in operational environments. To summarize and compare these approaches, Table 1 provides a high-level overview of the AI-based IDS models in terms of the associated techniques, achievements, and limitations.

Table 1.
Comparative overview of AI-based intrusion detection approaches in the EV cybersecurity literature.
While numerous deep learning-based IDS solutions have shown promise in simulations and lab-scale tests, significant challenges in deploying these systems within real-world EV environments remain unresolved. In particular, most existing frameworks suffer from: (a) Limited real-world validation—many systems are evaluated on synthetic or constrained datasets, limiting their generalizability. (b) Lack of adaptability—fixed learning models struggle to detect new, evolving cyber threats. (c) Scalability constraints—IDS models often fail to scale across heterogeneous V2X nodes and edge-based computing infrastructures. (d) Incomplete integration—Few systems offer comprehensive, real-time monitoring across OBUs and RSUs.
These challenges create a gap between academic innovation and practical deployment, impeding the development of robust, low-latency, and generalizable threat detection systems for connected EVs. There remains a pressing need for intelligent, adaptive, and hardware-efficient IDS frameworks that can detect diverse cyber threats in real-time, operate within computational constraints, and evolve with the threat landscape. This study addresses these limitations by proposing an integrated CNN–LSTM model with an adaptive learning mechanism optimized for deployment in V2X-based EV environments. The proposed framework bridges the gap between real-time responsiveness and intelligent threat detection while remaining viable for embedded systems in smart transportation networks.
More recent research has investigated advanced AI-driven security approaches in emerging vehicular paradigms. For example, secure offloading in NOMA-assisted vehicular edge networks using asynchronous deep reinforcement learning has been proposed to jointly optimize the latency and secrecy capacity, demonstrating the potential of reinforcement learning for adaptive vehicular security [26]. Similarly, energy-efficient cooperative secure communications in mmWave vehicular networks have been explored through deep recurrent reinforcement learning, highlighting how sequential learning agents can optimize both power usage and defense strategies in high-frequency vehicular links [27]. These works underscore the growing role of reinforcement learning in vehicular cybersecurity, although they have primarily targeted resource allocation and physical-layer security rather than intrusion detection in network-layer traffic—which is the focus of the present study.
Prior AI-based IDS approaches for vehicular networks have demonstrated strong promise but commonly exhibit three gaps that limit real-world deployment: (1) limited adaptability to novel and evolving attack patterns; (2) insufficient validation across heterogeneous, real-world V2X traffic; and (3) scalability and integration challenges for resource-constrained OBUs and RSUs. The remainder of this study addresses these gaps by introducing a hybrid CNN–LSTM architecture with an EWC-based adaptive learning module, which is optimized for low-latency inference and incremental updates when implemented on in-vehicle and roadside hardware.
3. Proposed Framework
This study proposes an AI-driven hybrid deep learning model designed for real-time cybersecurity threat detection in V2X communications in the context of electric vehicles. The system integrates CNNs and LSTM networks to effectively capture both spatial and temporal patterns within V2X network traffic. The architecture is optimized to operate within the computational limitations of EV OBUs and RSUs, delivering high accuracy, low false positives, and adaptability to emerging threats.
3.1. System Architecture
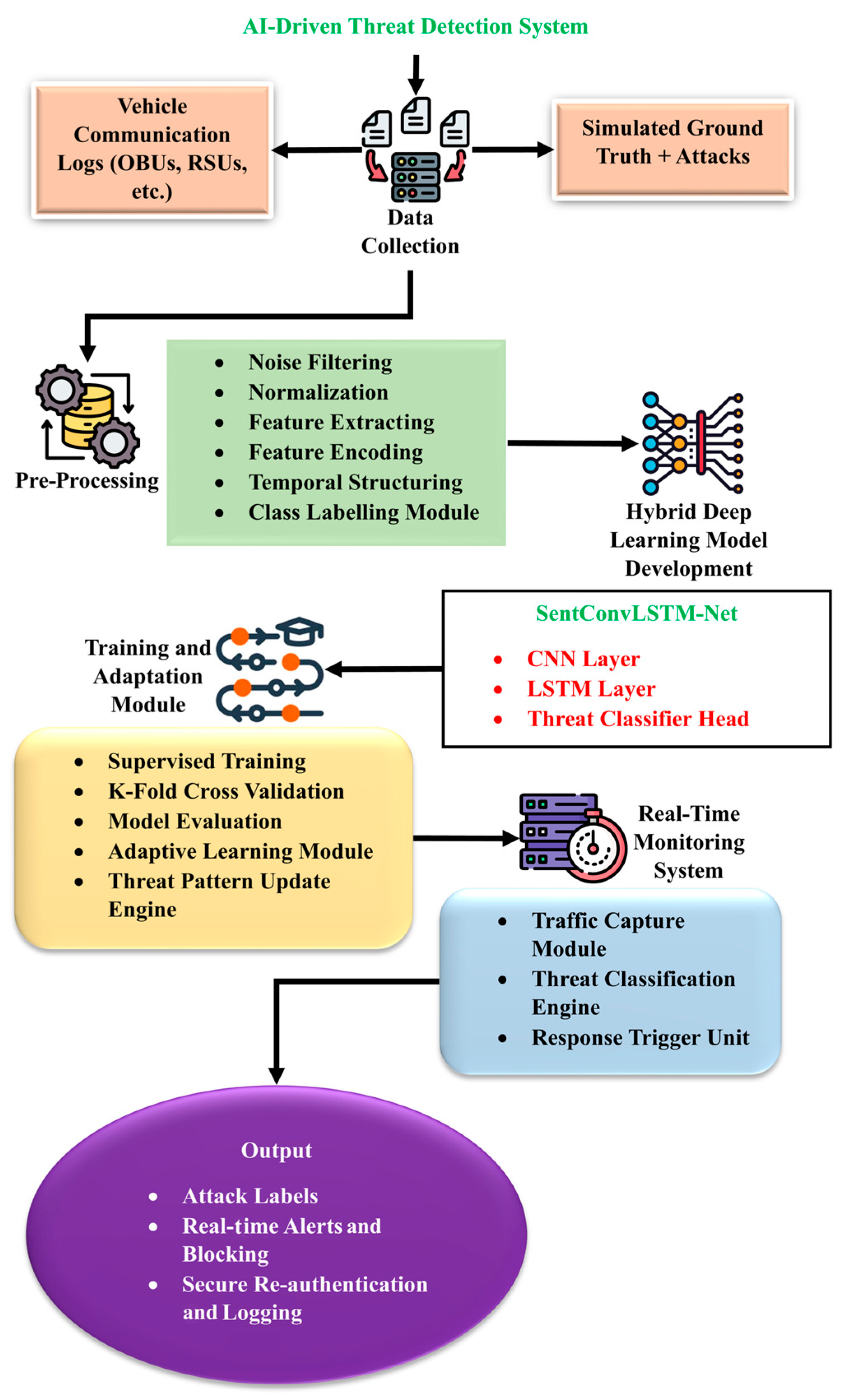
The proposed architecture is composed of three core modules: (1) A data acquisition and preprocessing unit, (2) a hybrid CNN–LSTM deep learning model, and (3) an adaptive learning module for continuous threat evolution handling as shown in Algorithm 1. Figure 1 illustrates the overall pipeline.
| Algorithm 1. Hybrid CNN–LSTM with Adaptive Learning: |
| Input: V2X traffic streams {CAM, DENM, BSM} |
| Output: Predicted class ∈ {benign, spoofing, DoS, injection, other attacks} |
| 1: Acquire raw V2X packets from OBUs and RSUs |
| 2: Apply preprocessing (normalization, label encoding, windowing) |
| 3: Balance the dataset using SMOTE |
| 4: Extract spatial features with CNN layers (Conv–ReLU–Pooling × 3) |
| 5: Pass spatial features to stacked LSTM layers (128, 64 units |
| 6: Generate temporal-aware feature vectors |
| 7: Apply a softmax classifier for multi-class prediction |
| 8: If new traffic patterns emerge → update weights incrementally via EWC |
| 9: Output prediction and trigger mitigation if malicious |
Figure 1.
Overall workflow of the proposed model.
- Data Acquisition and Preprocessing
V2X communication data, consisting of message payloads from cooperative awareness messages (CAMs), decentralized environmental notification messages (DENMs), and basic safety messages (BSMs), were captured and structured into traffic sessions. Standard data normalization and label encoding were performed. Time windows were generated to preserve the sequential nature of message streams and facilitate LSTM processing. Following prior best practices [28], the dataset was balanced using the synthetic minority over-sampling technique (SMOTE) to prevent class imbalance. To reflect vehicle mobility in the dataset, temporal windows were generated that capture consecutive message exchanges over short intervals, effectively embedding mobility-driven dynamics into the input sequences; for example, variations in beacon frequency, packet inter-arrival times, and handover events between RSUs introduce sequential patterns that LSTMs can learn as indicators of mobility-influenced anomalies. By modeling such sequences, the system indirectly encodes vehicular mobility effects without requiring explicit trajectory data.
- 2.
- CNN–LSTM Model Integration
The hybrid architecture begins with convolutional layers that extract spatial features from network traffic matrices, such as header fields, payload sizes, and transmission timestamps. These features are then passed into LSTM layers that model temporal dependencies and detect deviations from normal traffic behaviors over time. The CNN module comprises three convolutional blocks with ReLU activations and max-pooling, designed to compress and abstract relevant traffic features. The LSTM module consists of two stacked layers with 128 and 64 hidden units, respectively, which capture long-range temporal dependencies and generate context-aware threat detection signals. Finally, a softmax output layer enables multi-class threat classification, such as spoofing, DoS, data injection, and benign traffic. The architecture is trained using the Adam optimizer, the categorical cross-entropy loss, and an initial learning rate of 0.0001. Furthermore, dropout layers and batch normalization are incorporated to prevent overfitting and improve generalization.
The CNN–LSTM hybrid architecture was selected to exploit the complementary strengths of the respective networks. Convolutional layers efficiently learn spatial patterns and local correlations in network traffic matrices—for example, header field relationships and payload size distributions—while LSTM layers capture temporal dependencies across message sequences, such as sequences of CAMs/DENMs, which are essential to detect temporal attack signatures. The adaptive learning module based on elastic weight consolidation enables incremental model updating using small batches of recent traffic samples while protecting previously learned parameters from catastrophic forgetting, enabling online adaptation without full retraining. The key training settings are as follows: epochs = 100, batch size = 64, optimizer = Adam with an initial learning rate = 1 × 10−4. These were chosen after preliminary tuning experiments, in order to balance convergence speed and generalization. Regularization was applied to reduce overfitting, while SMOTE was used to mitigate the class imbalance present in the training data by generating representative synthetic minority samples, improving the classifier’s stability across classes.
- 3.
- Adaptive Learning Module
To maintain high detection performance amid the evolving threat landscape, an adaptive online learning mechanism is integrated into the proposed system. This module allows for incremental updating of model weights using small batches of recent traffic samples. Inspired by prior work on continual learning [29], we implemented elastic weight consolidation (EWC) to preserve stability in previously learned knowledge while adapting to new threats. This avoids catastrophic forgetting and ensures robustness during real-time operations.
3.2. Deployment Framework
The proposed system is designed for deployment on a distributed ITS infrastructure. The onboard units handle initial data capture, lightweight preprocessing, and first-stage anomaly detection using pruned CNN layers, while roadside units perform full threat classification and invoke dynamic countermeasures such as isolating malicious nodes or alerting traffic management centers. Communications between OBUs and RSUs are encrypted using the TLS 1.3 protocol. This modular design enables partial inference at the edge and cloud-based retraining when needed, balancing latency and performance.
The technical workflow integrates three coordinated processes: (1) lightweight feature extraction at the OBU level using pruned convolutional filters to minimize computational load, (2) temporal modeling of traffic sessions at the RSU level via stacked LSTMs for sequential anomaly detection, and (3) adaptive learning through EWC to incrementally fine-tune the model weights as new traffic is observed. These steps ensure that the system maintains real-time responsiveness while remaining robust against evolving threats. Section 4 further details how these modules were evaluated across multiple metrics, emphasizing both detection accuracy and operational latency.
3.3. Dataset and Evaluation Strategy
The system was trained and validated using a combination of real and synthetic data. VeReMi [30] and CARLA-generated V2X traffic formed the core dataset. Synthetic attack scenarios, such as coordinated DoS and message falsification, were injected following the taxonomy in [31]. The dataset contained over 200,000 labeled instances across five classes. The utilized evaluation metrics included accuracy, precision, recall, F1-score, and false-positive rate (FPR). ROC-AUC analysis was conducted for binary and multi-class classification, and a five-fold cross-validation strategy was applied to ensure robustness. Additionally, ablation studies were conducted to compare the performances of the individual CNN and LSTM modules versus the hybrid proposed system.
4. Results and Discussion
4.1. Results
This section presents a detailed analysis and discussion of the experimental outcomes obtained with the proposed model. Performance evaluation metrics including accuracy, precision, specificity, latency, robustness, and others were calculated to comprehensively assess the model’s effectiveness. To validate the proposed model’s superiority, resilience, and real-time applicability in securing EV communication networks, we conducted comparative analyses against existing models as well as an ablation study.
4.1.1. Experimental Setup
- Tools: MATLAB R2022b was utilized for data preprocessing and evaluation tasks.
- Programming Framework: Model development and training were conducted in Python 3.9.13, leveraging TensorFlow 2.10 and Keras 2.9.
- Hardware: Experiments were performed on a system equipped with an Intel Core i7 processor (Intel Corporation, Santa Clara, CA, USA), 16 GB RAM, and an NVIDIA RTX 3060 GPU with 6 GB VRAM (NVIDIA Corporation, Santa Clara, CA, USA).
- Operating System: Windows 11 (64-bit; Microsoft Corporation, Redmond, WA, USA).
- Software Libraries: NumPy 1.23.5, Pandas 1.5.2, Scikit-learn 1.2.0, Matplotlib 3.6.2, SHAP 0.41.0, and Seaborn 0.12.1 (all open-source, Python Software Foundation, Wilmington, DE, USA) were employed for data handling, analysis, and visualization.
- Training Configuration:
- ○
- Epochs: 100;
- ○
- Batch size: 64;
- ○
- Optimizer: Adam;
- ○
- Loss function: Categorical Cross-Entropy;
- ○
- Validation split: 15%;
- ○
- K-Fold Cross-Validation: 5 folds.
4.1.2. Dataset Description
The VeReMi dataset, containing labeled benign and malicious communication logs within VANET environments, was utilized for model training and evaluation. This dataset simulates various cyberattacks, enabling the effective training of real-time V2X security models.
4.1.3. Comparative Performance Analysis
The performance of the proposed model was benchmarked against traditional CNN, LSTM, and other baseline models, and demonstrated superior results in multiple key metrics. The comparative baselines (CNN, LSTM, GoogLeNet) were selected because they represent widely used and well-established IDS architectures in vehicular and IoT security research, providing a fair and transparent benchmark against both single-model and alternative deep learning approaches. While not the most recent reinforcement learning-based IDS methods, these baselines reflect the state-of-practice for deep learning-driven intrusion detection, making them suitable reference points for evaluating the contribution of our hybrid adaptive framework.
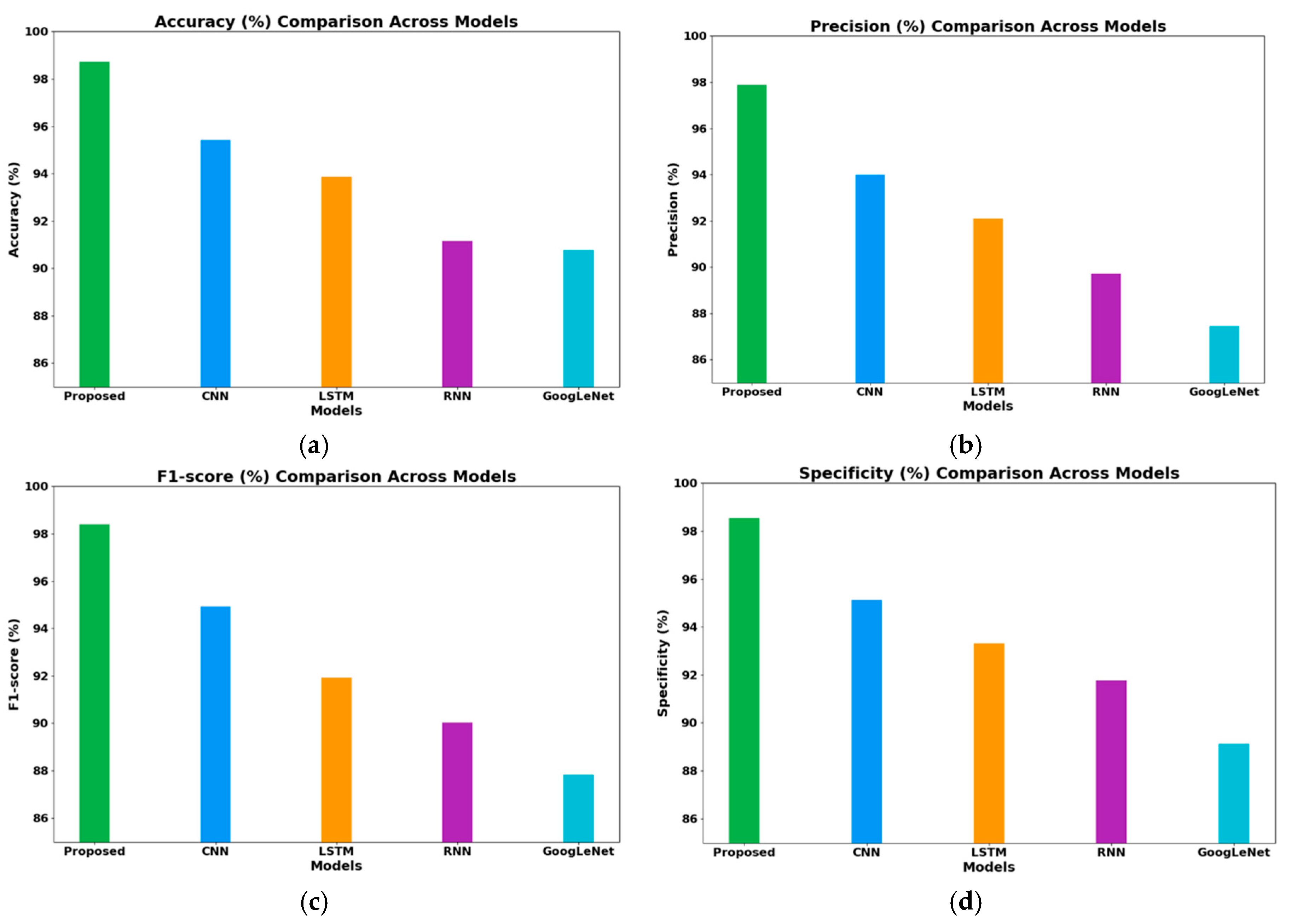
- Accuracy: As shown in Figure 2a, the proposed model achieved an outstanding overall accuracy of 98.73%, outperforming the CNN (95.42%) and LSTM (93.87%) models. This result indicates its superior capability in correctly classifying normal and malicious traffic, which is essential for reliable V2X network security.
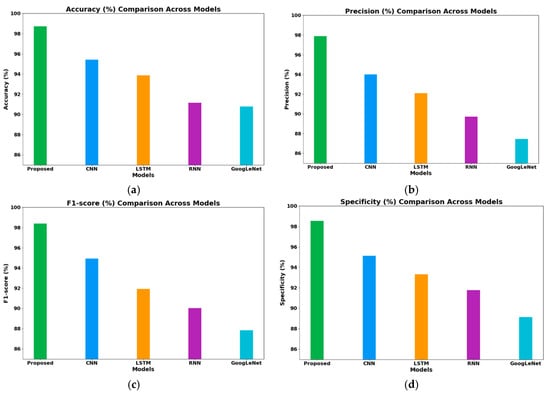 Figure 2. Comparison of the proposed model with other existing models. (a) Accuracy of the compared models, (b) precision of the compared models, (c) F1-score of the compared models, and (d) specificity of the compared models.
Figure 2. Comparison of the proposed model with other existing models. (a) Accuracy of the compared models, (b) precision of the compared models, (c) F1-score of the compared models, and (d) specificity of the compared models. - Precision: Figure 2b illustrates a precision of 97.88%, significantly better than those of the CNN (94.01%) and GoogLeNet (87.45%) models, indicating a reduced number of false alarms and its ability to prevent unnecessary disruptions in V2X systems.
- F1-Score: The model’s F1-score of 98.39% (Figure 2c) exceeded those of the CNN (94.92%) and LSTM (91.92%) models, demonstrating a strong balance between precision and recall, which is crucial for holistic threat detection.
- Specificity: Figure 2d shows the specificity of the proposed model at 98.55%, indicating its ability to effectively identify benign traffic, surpassing the CNN (95.12%) and GoogLeNet (89.12%) model, thus reducing the number of false positives while conserving system resources.
Further metrics are detailed as follows:
- Sensitivity: The proposed model achieved 98.91% sensitivity, outperforming the CNN (95.85%) and LSTM (91.74%) models, highlighting its robustness in detecting true threats.
- Matthews Correlation Coefficient (MCC): At 0.964, the proposed model showed excellent classification quality even with data imbalance, surpassing the CNN (0.902) and GoogLeNet (0.781) models.
- Negative Predictive Value (NPV): With 98.85%, the model reliably classified benign traffic, reducing the number of false negatives compared to the CNN (94.88%) and RNN (90.88%) models.
- False-Positive Rate (FPR): The low FPR of 1.45% achieved by the proposed model was substantially better than those of the CNN (4.88%) and GoogLeNet (10.88%) model, indicating its ability to minimize wasted resources due to false alerts.
Additional evaluation metrics include:
- False-Negative Rate (FNR): The proposed model’s FNR of 1.09% was markedly lower than those of the CNN (4.15%) and GoogLeNet (11.8%) models, ensuring minimal missed attacks.
- Cohen’s Kappa: The proposed model attained a kappa of 0.962, reflecting near-perfect agreement with true labels and exceeding those of the CNN (0.894) and GoogLeNet (0.765) models.
- AUC-ROC: The proposed model’s AUC-ROC of 0.994 signifies its almost perfect discrimination between threat and benign classes.
- Robustness Score: At 98.8%, the proposed model exhibited high resilience to adversarial inputs, surpassing the CNN (95.46%) and GoogLeNet (88.63%) models.
Regarding real-time performance:
- Latency: The model processed inputs with a latency of only 28 ms, a 35% improvement over the CNN model (43 ms), thus meeting the stringent V2X timing requirements.
- Detection Rate: The proposed model’s high detection rate of 98.45% confirms the effective identification of threats with minimal misses.
To further emphasize its real-time capability, the latency of the proposed model (28 ms) was directly compared with that of the CNN model (43 ms) and other baselines, confirming that the hybrid model not only improves the detection accuracy but also delivers faster response times, thus making it suitable for stringent V2X safety requirements.
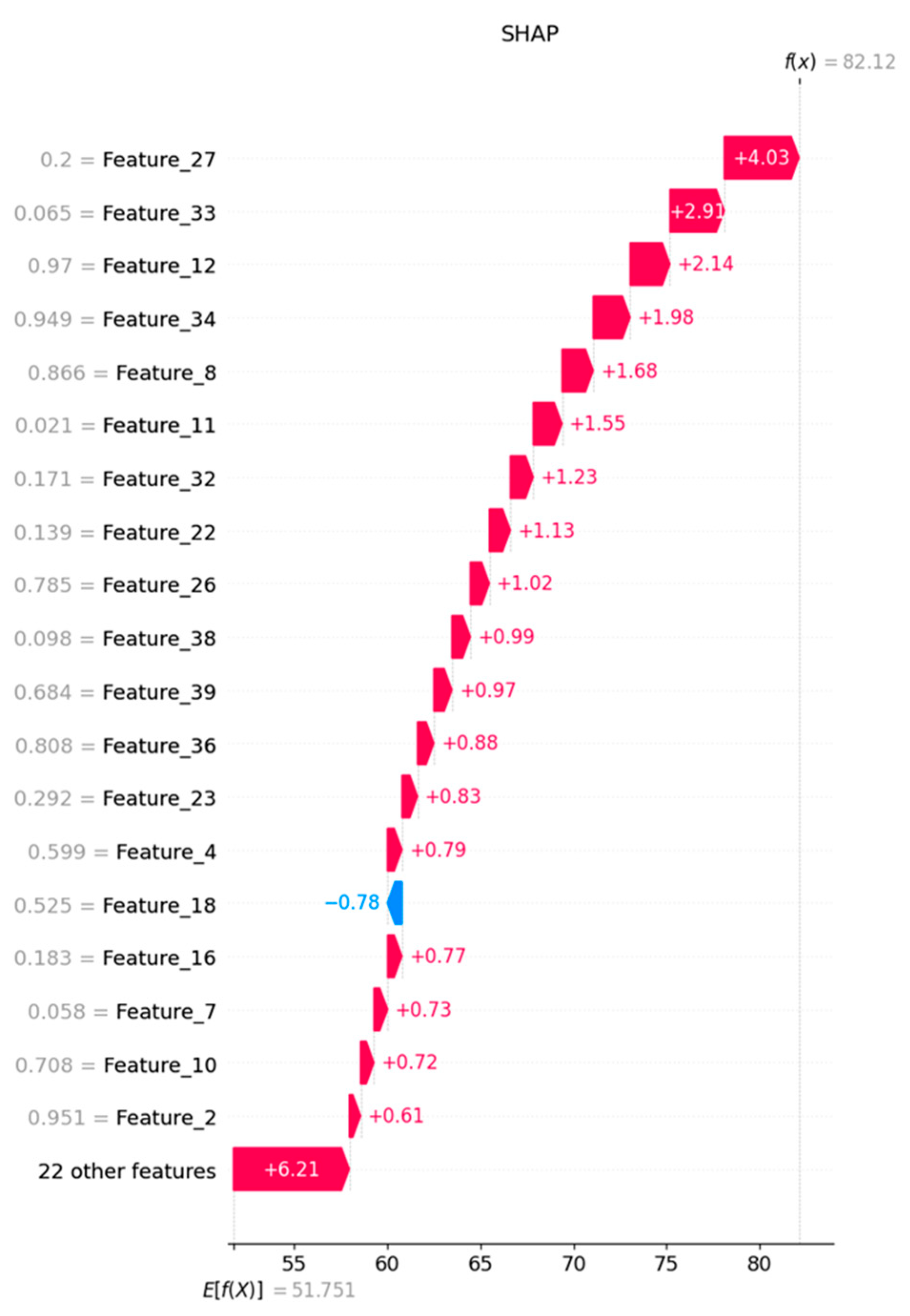
The ROC analysis further confirmed the superior performance of the model, with the curve closely hugging the top-left corner, indicating an optimal trade-off between high true positive and low false-positive rates. The training and validation curves exhibit consistent improvement and minimal overfitting, with both accuracies close to 100% and loss values approaching zero after 100 epochs. The confusion matrix confirms the model’s accuracy, demonstrating its strong ability to classify all attack types with minimal misclassification. The SHAP analysis, as shown in Figure 3, provides interpretability insights. The feature importance plot highlights Feature_2 and Feature_34 with the highest SHAP values, indicating that these variables had the most significant impact on model predictions. This identification enhances transparency and enables actionable security improvements.
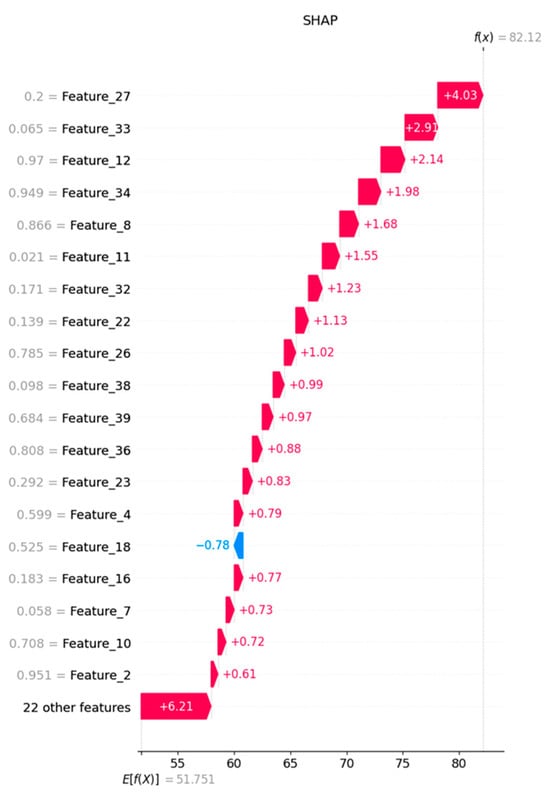
Figure 3.
SHAP analysis of the proposed model.
4.1.4. Ablation Study
To quantify the contribution of each module (CNN, LSTM, and Adaptive Learning), an ablation study was conducted by systematically removing modules:
- Accuracy: The full model’s 98.73% accuracy surpassed that of all ablation variants, including the removal of adaptive learning (97.21%), LSTM (95.42%), and CNN (93.87%) modules.
- Precision: Similarly, the precision decreased in ablated models, with the full model achieving 97.88% compared to 95.96% (w/o adaptive learning), 94.01% (w/o LSTM), and 92.1% (LSTM-only).
- F1-Score: The hybrid model maintained the highest F1-score of 98.39%, outperforming all ablated versions.
- Specificity: The full model’s specificity of 98.55% indicates its superior benign traffic detection performance, with notable decreases in simpler architectures.
The sensitivity, MCC, NPV, and FPR presented similar trends, with the full model outperforming the ablated variants, confirming the synergy between the modules for effective and balanced detection. The False-Negative Rate, Cohen’s Kappa, AUC-ROC, and Robustness scores also demonstrated the hybrid model’s superior reliability and resilience, while the latency and detection rate results further highlighted the hybrid model’s efficiency and superior threat identification capability when compared to the ablated variants.
4.1.5. Cross-Validation Results
The five-fold cross-validation results reaffirmed the robustness of the hybrid model, with an average accuracy of 98.73% and fold accuracies consistently above 98.6%. Comparatively, the CNN and LSTM models alone yielded lower average accuracies of 95.42% and 93.87%, respectively, underscoring the advantage of combining spatial and temporal features with adaptive learning for enhanced performance in EV cybersecurity settings.
4.2. Discussion
The results demonstrated that the proposed model significantly enhances the security of EV communication systems. Achieving a high accuracy of 98.73%, precision of 97.88%, and specificity of 98.55%, the model consistently outperformed the benchmark models such as CNN and GoogLeNet. Its low false-positive rate of 1.45% and false-negative rate of 1.09% indicate its ability to effectively minimize unnecessary alerts and missed attacks, which are critical concerns in real-time V2X applications. Furthermore, the model’s exceptional sensitivity of 98.91% and Matthews correlation coefficient of 0.964 highlight its reliability in accurately classifying both benign and malicious traffic. The model’s low detection latency of 28 ms and high detection rate of 98.45% underscore its real-time operational capability, which is essential for responsive EV cybersecurity systems. Its near-perfect AUC-ROC score of 0.994 further confirms the proposed model’s superior discriminatory power between threat and benign classes.
Beyond numeric improvements, the proposed model’s performance has concrete operational implications for EV V2X systems. The measured average detection latency of 28 ms supports timely mitigation actions within the time windows required by many V2X safety and control applications, enabling the network or the vehicle to initiate countermeasures before an attack causes unsafe behavior. A low false-positive rate (1.45%) reduces unnecessary mitigation actions and preserves communication and computational resources, while a low false-negative rate (1.09%) minimizes missed attacks—both critical requirements for safety-critical vehicular functions. Moreover, the observed accuracy gains over the standard CNN and LSTM baselines (≈ +3.31 and +4.86 percentage points, respectively), as shown in Table 2, translate to substantially fewer misclassifications over large message volumes, improving the overall reliability of connected mobility services.

Table 2.
Key performance metrics of proposed vs. baseline models.
A potential concern with deep CNN and LSTM architectures is their computational complexity and tendency to overfit when trained on limited or imbalanced datasets. In our design, these risks are mitigated in three ways. First, the CNN layers are pruned and regularized using dropout and batch normalization, reducing model size while improving generalization. Second, the integration with LSTMs leverages sequential dependencies that reduce reliance on large CNN stacks, thereby balancing the complexity across modules. Third, the adaptive learning strategy incrementally fine-tunes weights without exhaustive retraining, preventing overfitting while allowing the model to remain responsive to new traffic patterns. These design decisions demonstrate that the hybrid architecture not only achieves superior accuracy, but also maintains efficiency and robustness against overfitting.
The ablation study results underscore the importance of integrating the CNN, LSTM, and adaptive learning modules, as removal of any of these modules resulted in a noticeable degradation in detection accuracy, reduced specificity, and an increase in false alarms. Overall, the proposed hybrid model was found to be robust, scalable, and adaptable, making it well-suited for the dynamic and evolving nature of EV cybersecurity threats and thereby contributing substantially to the advancement of intelligent threat detection systems.
5. Conclusions
This study proposed and validated a hybrid AI-driven threat detection framework designed to improve the security of EV communication networks in dynamic V2X environments. Combining convolutional neural networks, long short-term memory units, and adaptive learning mechanisms, the model effectively captures spatial and temporal features and adapts to evolving cyber threats without requiring full retraining. Extensive experiments using the VeReMi dataset demonstrated that the proposed model significantly outperforms traditional methods, achieving an accuracy of 98.73%. Its low latency of 28 ms satisfies real-time detection requirements while maintaining a high threat detection rate of 98.45%. The ablation study results further confirmed the essential roles of the CNN, LSTM, and adaptive learning modules in achieving optimal performance. This research not only addresses critical cybersecurity challenges in EV networks but also delivers a scalable, low-latency, and robust solution that is ready for deployment in real-world intelligent transportation systems, thus paving the way for safer and more resilient connected mobility infrastructure.
While the results demonstrated the feasibility and strong performance of the proposed hybrid approach for EV V2X cybersecurity, we note some limitations. The experimental evaluation was conducted primarily on the VeReMi dataset supplemented with CARLA-generated traffic; therefore, full validation under operational on-road conditions and on broader real-world datasets remains necessary. Additionally, while the proposed framework demonstrated strong simulation-based results, deployment in real vehicular environments and real-time validation remain essential next steps to fully confirm its operational readiness. Future work should prioritize real-world field trials, expanded dataset collection across diverse urban scenarios, and energy profiling to confirm the proposed model’s suitability for implementation in resource-constrained OBUs and RSUs. The proposed framework provides a scalable, low-latency, and adaptable IDS foundation that can be extended through these next steps to enable its robust deployment in real ITS environments.
Funding
The author thanks the Deanship of Postgraduate Studies and Scientific Research at Majmaah University for funding this research (project number ER-2025-2034).
Data Availability Statement
The original data presented in this study are openly available on GitHub 3.15.12 at https://veremi-dataset.github.io/ (accessed on 15 May 2025).
Conflicts of Interest
The author declares no conflicts of interest.
References
- Teimoori, Z.; Yassine, A. A Review on Intelligent Energy Management Systems for Future Electric Vehicle Transportation. Sustainability 2022, 14, 14100. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Yoon, M.; Seo, D.; Kim, S.; Kim, K. V2X Network-Based Enhanced Cooperative Autonomous Driving for Urban Clusters in Real Time: A Model for Control, Optimization and Security. Electronics 2025, 14, 1629. [Google Scholar] [CrossRef]
- Alnasser, A.; Sun, H.; Jiang, J. Cyber security challenges and solutions for V2X communications: A survey. Comput. Netw. 2019, 151, 52–67. [Google Scholar] [CrossRef]
- Saeed, Z.; Masood, M.; Khan, M.U. A review: Cybersecurity challenges and their solutions in connected and autonomous vehicles (CAVs). JAREE (J. Adv. Res. Electr. Eng.) 2023, 7, 44–51. [Google Scholar] [CrossRef]
- Hussain, R.; Zeadally, S. Autonomous cars: Research results, issues, and future challenges. IEEE Commun. Surv. Tutor. 2018, 21, 1275–1313. [Google Scholar] [CrossRef]
- Almehdhar, M.; Albaseer, A.; Khan, M.A.; Abdallah, M.; Menouar, H.; Al-Kuwari, S.; Al-Fuqaha, A. Deep learning in the fast lane: A survey on advanced intrusion detection systems for intelligent vehicle networks. IEEE Open J. Veh. Technol. 2024, 5, 869–906. [Google Scholar] [CrossRef]
- Sonko, S.; Etukudoh, E.A.; Ibekwe, K.I.; Ilojianya, V.I.; Daudu, C.D. A comprehensive review of embedded systems in autonomous vehicles: Trends, challenges, and future directions. World J. Adv. Res. Rev. 2024, 21, 2009–2020. [Google Scholar] [CrossRef]
- Imamverdiyev, Y.N.; Abdullayeva, F.J. Deep learning in cybersecurity: Challenges and approaches. Int. J. Cyber Warf. Terror. (IJCWT) 2020, 10, 82–105. [Google Scholar] [CrossRef]
- Mittal, H.; Tripathi, A.K.; Pandey, A.C.; Alshehri, M.D.; Saraswat, M.; Pal, R. A new intrusion detection method for cyber–physical system in emerging industrial IoT. Comput. Commun. 2022, 190, 24–35. [Google Scholar] [CrossRef]
- Taneja, A.; Kumar, G. Attention-cnn-lstm based intrusion detection system (acl-ids) for in-vehicle networks. Soft Comput. 2024, 28, 13429–13441. [Google Scholar] [CrossRef]
- Idrissi, I.; Azizi, M.; Moussaoui, O. A lightweight optimized deep learning-based host-intrusion detection system deployed on the edge for IoT. Int. J. Comput. Digit. Syst. 2022, 11, 209–216. [Google Scholar] [CrossRef] [PubMed]
- Ji, H.; Alfarraj, O.; Tolba, A. Artificial intelligence-empowered edge of vehicles: Architecture, enabling technologies, and applications. IEEE Access 2020, 8, 61020–61034. [Google Scholar] [CrossRef]
- Kumar, A.; Das, T.K. CAVIDS: Real time intrusion detection system for connected autonomous vehicles using logical analysis of data. Veh. Commun. 2023, 43, 100652. [Google Scholar] [CrossRef]
- Basnet, M. Deep Learning-Powered Computational Intelligence for Cyber-Attacks Detection and Mitigation in 5G-Enabled Electric Vehicle Charging Station. Ph.D. Thesis, The University of Memphis, Memphis, TN, USA, 2022. [Google Scholar]
- Zhang, H.; Pan, Y.; Lu, Z.; Wang, J.; Liu, Z. A cyber security evaluation framework for in-vehicle electrical control units. IEEE Access 2021, 9, 149690–149706. [Google Scholar] [CrossRef]
- Das, P.; Asif, M.R.A.; Jahan, S.; Ahmed, K.; Bui, F.M.; Khondoker, R. STRIDE-Based Cybersecurity Threat Modeling, Risk Assessment and Treatment of an In-Vehicle Infotainment System. Vehicles 2024, 6, 1140–1163. [Google Scholar] [CrossRef]
- Venkatasamy, T.K.; Hossen, M.J.; Ramasamy, G.; Aziz, N.H.B.A. Intrusion detection system for V2X communication in VANET networks using machine learning-based cryptographic protocols. Sci. Rep. 2024, 14, 31780. [Google Scholar] [CrossRef]
- Khalil, A.; Farman, H.; Nasralla, M.M.; Jan, B.; Ahmad, J. Artificial Intelligence-based intrusion detection system for V2V communication in vehicular adhoc networks. Ain Shams Eng. J. 2024, 15, 102616. [Google Scholar] [CrossRef]
- Shrivastwa, R.R.; Bouakka, Z.; Perianin, T.; Dislaire, F.; Gaudron, T.; Souissi, Y.; Karray, K.; Guilley, S. An embedded AI-based smart intrusion detection system for edge-to-cloud systems. In Proceedings of the International Conference on Cryptography, Codes and Cyber Security, Casablanca, Morocco, 26–28 October 2022; Springer Nature: Cham, Switzerland, 2023; pp. 20–39. [Google Scholar] [CrossRef]
- Talaat, F.M.; Shaban, W.M.; ZainEldin, H.; Badawy, M.; Elhosseini, M. Integrating V2X solutions in intelligent green cities: An AI-driven point exchange system approach. Neural Comput. Appl. 2025, 37, 15311–15343. [Google Scholar] [CrossRef]
- Chen, M.; Zhao, Q.; Jiang, Z.; Xu, R. Intrusion detection for in-vehicle CAN networks based on auxiliary classifier GANs. In Proceedings of the 2021 International Conference on High Performance Big Data and Intelligent Systems (HPBD&IS), Macau, China, 5–7 December 2021; IEEE: New York, NY, USA, 2022; pp. 186–191. [Google Scholar] [CrossRef]
- Ali, W.; Din, I.U.; Almogren, A.; Rodrigues, J.J. Federated learning-based privacy-aware location prediction model for internet of vehicular things. IEEE Trans. Veh. Technol. 2024, 74, 1968–1978. [Google Scholar] [CrossRef]
- Alsokhiry, F.; Annuk, A.; Kabanen, T.; Mohamed, M.A. A Malware Attack Enabled an Online Energy Strategy for Dynamic Wireless EVs within Transportation Systems. Mathematics 2022, 10, 4691. [Google Scholar] [CrossRef]
- ElKashlan, M.; Elsayed, M.S.; Jurcut, A.D.; Azer, M. A Machine Learning-Based Intrusion Detection System for IoT Electric Vehicle Charging Stations (EVCSs). Electronics 2023, 12, 1044. [Google Scholar] [CrossRef]
- Ju, Y.; Cao, Z.; Chen, Y.; Liu, L.; Pei, Q.; Mumtaz, S.; Dong, M.; Guizani, M. NOMA-Assisted Secure Offloading for Vehicular Edge Computing Networks with Asynchronous Deep Reinforcement Learning. IEEE Trans. Intell. Transp. Syst. 2024, 25, 2627–2640. [Google Scholar] [CrossRef]
- Ju, Y.; Gao, Z.; Wang, H.; Liu, L.; Pei, Q.; Dong, M.; Mumtaz, S.; Leung, V.C.M. Energy-Efficient Cooperative Secure Communications in mmWave Vehicular Networks Using Deep Recurrent Reinforcement Learning. IEEE Trans. Intell. Transp. Syst. 2024, 25, 14460–14475. [Google Scholar] [CrossRef]
- Zolanvari, M.; Teixeira, M.A.; Gupta, L.; Khan, K.M.; Jain, R. Machine learning-based network vulnerability analysis of industrial Internet of Things. IEEE Internet Things J. 2019, 6, 6822–6834. [Google Scholar] [CrossRef]
- Kirkpatrick, J.; Pascanu, R.; Rabinowitz, N.; Veness, J.; Desjardins, G.; Rusu, A.A.; Milan, K.; Quan, J.; Ramalho, T.; Grabska-Barwinska, A. Overcoming catastrophic forgetting in neural networks. Proc. Natl. Acad. Sci. USA 2017, 114, 3521–3526. [Google Scholar] [CrossRef] [PubMed]
- Van Der Heijden, R.W.; Lukaseder, T.; Kargl, F. Veremi: A dataset for comparable evaluation of misbehavior detection in vanets. In Proceedings of the International Conference on Security and Privacy in Communication Systems, Singapore, 8–10 August 2018; Springer International Publishing: Cham, Switzerland, 2018; pp. 318–337. [Google Scholar] [CrossRef]
- Petit, J.; Shladover, S.E. Potential cyberattacks on automated vehicles. IEEE Trans. Intell. Transp. Syst. 2014, 16, 546–556. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).