Abstract
Blockchain technologies offer transformative potential in terms of addressing the security, trust, and identity management issues that exist in large-scale Internet of Things (IoT) deployments. This narrative review provides a comprehensive survey of various studies, focusing on decentralized identity management, trust mechanisms, smart contracts, privacy preservation, and real-world IoT applications. According to the literature, blockchain-based solutions provide robust authentication through mechanisms such as Physical Unclonable Functions (PUFs), enhance transparency via smart contract-enabled reputation systems, and significantly mitigate vulnerabilities, including single points of failure and Sybil attacks. Smart contracts enable secure interactions by automating resource allocation, access control, and verification. Cryptographic tools, including zero-knowledge proofs (ZKPs), proxy re-encryption, and Merkle trees, further improve data privacy and device integrity. Despite these advantages, challenges persist in areas such as scalability, regulatory and compliance issues, privacy and security concerns, resource constraints, and interoperability. By reviewing the current state-of-the-art literature, this review emphasizes the importance of establishing standardized protocols, performance benchmarks, and robust regulatory frameworks to achieve scalable and secure blockchain-integrated IoT solutions, and provides emerging trends and future research directions for the integration of blockchain technology into the IoT ecosystem.
1. Introduction
The Internet of Things (IoT) has rapidly evolved into a transformative technological paradigm that enables interconnectivity between billions of devices, including smart home appliances, industrial sensors, healthcare monitors, autonomous vehicles, and more. The IoT ecosystem can offer significant benefits in terms of automation, efficiency, and real-time decision-making [1]. However, with the increasing number of heterogeneous devices and resource-constrained devices, as well as physically exposed devices, the IoT faces substantial challenges related to trust, security, identity management, and data integrity. However, establishing trust and managing identity remain significant challenges in the IoT environment. Maintaining consistent security policies and trust relationships becomes a complex challenge because IoT devices are dynamic, diverse, and spread across different environments. Traditional Public Key Infrastructure (PKI) and certificate-based models cannot scale effectively within the expansive and diverse IoT environment. Furthermore, issues such as privacy leakage, lack of transparency, and the inability to verify data provenance continue to undermine user and device trust in IoT services. These challenges are particularly acute in critical domains such as healthcare, industrial automation, and smart cities, where trust breaches can result in significant safety, security, and financial repercussions [2]. Moreover, conventional centralized trust models usually rely on third-party authorities, and are increasingly being viewed as inadequate for addressing the unique requirements of decentralized and large-scale IoT environments [3]. These models often suffer from single-point failure, scalability limitations, and increased vulnerability to cyberattacks. Moreover, large-scale IoT networks pose unprecedented challenges in terms of securing communication, decentralized trust, and scalable identity management. Conventional IoT infrastructure, often built on centralized cloud-based models, are susceptible to single points of failure, unverified device authentication, and data integrity breaches. These limitations compromise the reliability of IoT deployments in sensitive applications such as healthcare, autonomous transportation, and critical infrastructure monitoring [4,5].
1.1. Centralized Trust Management Issues
Centralized trust management techniques commonly employed in IoT systems have inherent limitations. There are various studies in the literature based on centralized trust management, such as centralized Reputation Systems, Cloud-based access control approaches, brokering schemes, etc. [6,7,8,9]. Trusted Third Parties (TTPs), such as Certificate Authorities and cloud providers, may introduce significant vulnerabilities due to their reliance on central control points. Centralized authorities suffer from single points of failure that make the entire IoT ecosystem susceptible to disruptions or failures in the case of an authority being compromised or experiencing outages. Additionally, TTPs are highly vulnerable to insider threats, where individuals with privileged access could intentionally or unintentionally compromise the system’s integrity and potentially affect millions of interconnected IoT devices. Moreover, the scalability of centralized trust solutions is also limited, especially when faced with the enormous number of IoT devices deployed in varied and distributed environments [6].
Other approaches, such as centralized Reputation Systems, also involve reputation assessments managed by a single central server or platform that aggregates user feedback and device behavior data. While these systems aim to enforce trust through collected reputation metrics, they lack transparency, which limits stakeholders’ ability to verify the fairness and accuracy of reputation evaluations independently. Moreover, centralized reputation management systems are highly susceptible to manipulation, particularly through Sybil attacks, where malicious entities create multiple fake identities to skew reputation assessments unfairly. These systems also demonstrate limited adaptability, struggling to dynamically respond to rapid changes and evolving behaviors in complex IoT networks [10,11].
Cloud-based access control mechanisms utilize centralized cloud services to enforce authentication policies and manage trust via access control lists (ACLs). Despite their advantages in simplifying policies, these systems introduce risks related to data privacy and dependency on external cloud providers for trust [9]. Data stored or processed in the cloud may be vulnerable to unauthorized access or breaches, significantly increasing the risk exposure of sensitive IoT applications. Additionally, centralized cloud systems inherently involve latency issues, making real-time decision-making more difficult and often impractical. The centralized enforcement approach can become a performance bottleneck, impeding effective and timely access control decisions crucial for many IoT scenarios [8,12].
Trust Brokers or Mediators serve as dedicated entities designed to intermediate and validate trust relationships among IoT devices. Although they facilitate initial trust establishment, these intermediaries inadvertently become critical communication bottlenecks, potentially slowing down interactions and decision-making processes. Moreover, relying on trust brokers significantly expands the potential attack surface, introducing additional security vulnerabilities that adversaries could exploit. Centralizing trust mediation can restrict the autonomy and self-governance of edge devices, which might otherwise achieve greater efficiency through decentralized or direct peer-to-peer trust management [13,14].
1.2. Blockchain-Based Trust Management
Blockchain can be used in the IoT environment to offer intrinsic properties such as decentralization, immutability, transparency, and cryptographic security that are well-suited to mitigating the trust-related vulnerabilities prevalent in IoT environments [2]. According to the current studies, blockchain aligns well with the trust and security requirements inherent to IoT ecosystems as it can eliminate the reliance on centralized authorities and enable peer-to-peer trust through consensus mechanisms and cryptographic proofs [15]. Moreover, blockchain provides innovative approaches to decentralized identity management, access control, and secure data sharing, and can be leveraged for more resilient and autonomous IoT infrastructures [16,17]. The potential of blockchain to secure data transmission, enforce decentralized access control, and detect intrusions autonomously has been extensively studied in the literature [18,19,20]. Blockchain can enable decentralized identity frameworks, support tamper-proof audit trails, and facilitate trustless interactions through smart contracts. These capabilities are well-aligned with the growing demand for more autonomous, resilient, and secure IoT infrastructures. Recent advances such as self-sovereign identities (SSIs), decentralized identifiers (DIDs) [21], Verifiable Credentials (VCs) [22], and smart contracts dynamically assess trust levels or access rights in real time [23,24]. Blockchain-based trust management schemes further illustrate the potential of blockchain to fundamentally reshape how trust and identity are conceptualized and enforced in IoT ecosystems.
However, the integration of blockchain technology into IoT environments still faces several challenges, especially in real-world adoption. The high resource demands of consensus algorithms such as Proof-of-Work (PoW) present significant obstacles in resource-constrained IoT settings. Thus, the researchers motivated to explore alternative approaches such as lightweight Proof-of-Trust (PoT) and hierarchical blockchain models [25,26]. Furthermore, the immutable nature of blockchain often conflicts with regulations such as the General Data Protection Regulation (GDPR), particularly regarding data erasure and localization [27]. Challenges also include robustness against attacks, energy efficiency in consensus, and scalability metrics like throughput.
This review aims to provide a comprehensive synthesis of current blockchain–IoT research, categorizing contributions under trust models, identity management strategies, cryptographic protocols, and implementation challenges. This survey provides an extensive review of state-of-the-art blockchain-based approaches for trust management in IoT environments. The related articles based on the trust framework designed into the IoT ecosystem have been reviewed and analyzed. This paper offers a thematic structure to navigate the literature and sets the stage for future interdisciplinary work that bridges blockchain innovation with scalable, privacy-compliant IoT architectures.
1.3. Key Contributions
The main contributions of this survey article are as follows:
- We analyze and classify existing architectural models that leverage blockchain to establish trust within IoT ecosystems, highlighting common patterns and design considerations.
- We explore decentralized identity solutions, including self-sovereign identities and decentralized identifiers, and their role in reinforcing trust in IoT.
- We survey the most commonly used approaches, techniques, and methodologies for utilizing blockchain-related solutions for the IoT environment in the existing literature.
- We present a broad spectrum of applications across various sectors, including healthcare, smart cities, supply chains, and energy systems, underscoring both practical advancements and persistent challenges.
- We articulate key research gaps, unresolved challenges, and potential future directions for advancing blockchain-enabled trust in IoT.
The remainder of this paper is structured as follows. Section 2 provides a comprehensive review of existing trust management frameworks in IoT, with a particular focus on decentralized identity management, smart contract design and automation, and the integration of AI and machine learning into trust systems. Section 3 discusses the key challenges associated with blockchain-based trust management, including both regulatory and compliance issues, as well as the practical difficulties of implementation. Section 4 explores emerging applications and use cases where blockchain-enabled trust frameworks are being deployed or proposed across various IoT domains. Section 5 presents a critical discussion and outlines future research directions, addressing current gaps and potential opportunities for further advancements. Finally, Section 6 concludes the paper by summarizing key findings and reflecting on the future trajectory of blockchain-enabled trust in IoT environments.
1.4. Methodology
This narrative review adopts a structured approach to identify and analyze scholarly contributions at the intersection of blockchain and IoT. Figure 1 presents the structured methodology of the survey, ensuring that this review captures the most relevant, rigorous, and representative studies addressing blockchain-enabled trust and identity solutions within IoT ecosystems. The subsequent sections leverage these findings to provide detailed analysis, classification, and synthesis. To identify the literature relevant to blockchain-enabled trust and identity management in IoT, we searched leading academic databases, including IEEE Xplore, ACM Digital Library, SpringerLink, MDPI, and Google Scholar.
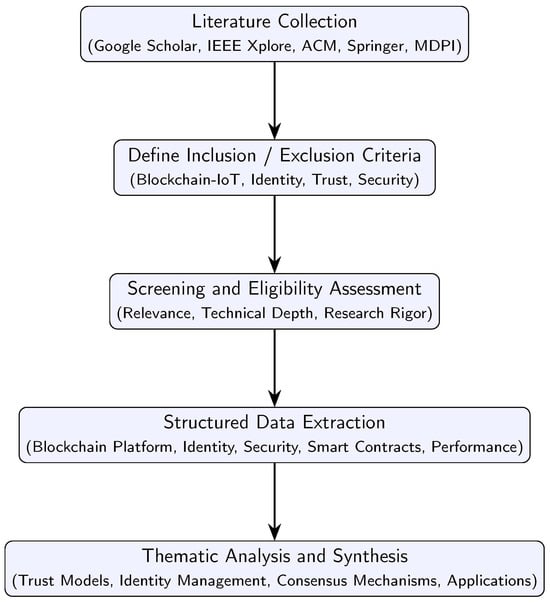
Figure 1.
Structured Flow of the Survey Methodology.
1.4.1. Scope, Search Strategy, and Eligibility Criteria
This review covers blockchain-enabled mechanisms for identity, access control, and trust in IoT. The core question is: how do blockchain and adjacent standards (DIDs/VCs/SSI, smart contracts, and consensus) improve trust, identity, and policy enforcement for heterogeneous, resource-constrained IoT applications? We queried IEEE Xplore, ACM Digital Library, SpringerLink, MDPI, and Google Scholar for English-language works published from January 2020 to October 2025. Earlier influential papers (pre-2020) are cited as the foundational context. Search strings included (“blockchain” AND “IoT” AND (trust OR identity OR “access control” OR “authorization” OR “decentralized identifier” OR “verifiable credential” OR “self sovereign identity” OR “PUF” OR “consensus”)) with venue-specific syntax, supplemented by backward/forward snowballing from seed surveys and standards.
Inclusion criteria comprised peer-reviewed journals or full conference papers with an IoT focus (device/edge/system), utilizing blockchain/DLT for identity, access control, trust, or policy, and reporting a method (prototype, formal model, analysis, testbed, or simulation) with evaluation details. Works were prioritized from high-quality venues, such as Q1 journals (e.g., IEEE IoT Journal) and A*-ranked conferences (e.g., USENIX Security). Exclusion criteria included tutorials/positions without methods, non-IoT scope, purely cryptographic works without IoT linkage, non-peer-reviewed papers, workshop/short abstracts, and duplicates/overlaps (retaining the most complete version). Alternative benchmarks were excluded if lacking IoT linkage or empirical evaluation. Full-text exclusion reasons and counts are reported in the PRISMA flow (see Table 1).

Table 1.
PRISMA-style flow for study selection (2020–2025).
Two reviewers independently screened titles/abstracts, then full texts; disagreements were resolved by discussion. PRISMA-style counts are provided in Table 1 to minimize bias, with backward/forward snowballing and diversity across publishers and venues ensured. We also document full-text exclusion reasons to reduce selection bias.
1.4.2. Data Extraction, Synthesis, and Quality Assessment
For each of the 77 included studies, we recorded author; venue/year, IoT domain, blockchain/DLT and consensus, identity model (DIDs/VCs/SSI/PUF), access control logic (ABAC/CapBAC), privacy mechanism (ZKP, proxy re-encryption, and Merkle anchoring), evaluation method, and performance (latency, throughput, energy/CPU, scalability, and finality time), plus real-world adoption notes where present. Synthesis employed narrative methods supported by comparative tables, highlighting trade-offs (security guarantees vs. latency/energy), implementation maturity, and regulatory alignment (e.g., revocation or data localization).
To assess study quality, venue tiers included 59 journal papers (Q1: 40; Q2: 12; Q3–Q4: 7, by Scimago/SJR where available) and 16 conference papers (CORE A*: 2; A: 3; B: 6; other: 5). This helps readers calibrate evidence strength by venue tier. Internal evidence quality was scored on a 0–8 rubric (method clarity; dataset/testbed; reproducibility; evaluation depth; threat analysis; policy/identity rigor; performance coverage; and availability of code/data). The median score was 5/8 (IQR 4–6). Bias mitigation involved multi-database searches, duplicate tracking, exclusion reason documentation, and domain distribution reporting (Industrial: 15, Smart city: 14, Vehicular/IoV: 12, Healthcare: 13, Cross-domain frameworks: 23) to avoid over-weighting a single vertical.
1.4.3. Benchmarks, Limitations, and Risk Mitigation
To broaden benchmarking, we normalized and reported latency (end-to-end for auth/tx), throughput (tps or events/s), energy/CPU (device/node level), storage footprint (on/off-chain), scalability (# devices, # tx/block, # domains), finality time, robustness (tolerance to churn/attacks), and compliance hooks (revocation, localization, and consent traces). Unbenchmarked aspects (e.g., some ZKP schemes omitting device-side energy) are noted, with exclusions justified (tutorials/positions without methods and purely cryptographic works without IoT deployment paths). Alternative consensus families (PoA, PBFT, DPoS, DAG, and PoT) and identity rails (DIDs/VCs/SSI, PUFs) are represented to avoid method bias.
Limitations include publication bias (few negative results), variable energy metric reporting, and inconsistent latency definitions, flagged where interpretation may be affected. Risk of bias was further mitigated by ensuring representativeness across IoT domains and documenting these challenges.
1.5. Related Work
Prior surveys examine blockchain-enabled trust in IoT from several angles, but each leaves gaps that our review addresses. Research on trust and identity in IoT predates blockchain and has focused on centralized or brokered models for reputation, policy, and key management, approaches that struggle with scale and single points of failure [28,29,30,31,32]. More recent surveys address blockchain as a substrate for trust formation in IoT, but typically emphasize either broad security themes [33] or identity and access management at a high level [34,35]. Liu et al. review blockchain based trust management and outline open problems around scalability and interoperability [2]. Compared with those efforts, this survey makes three contributions. First, we synthesize decentralized identity (DIDs, VCs, and SSI) specifically for IoT onboarding and lifecycle management, connecting identity design to policy enforcement via smart contracts (ABAC/ CapBAC) [17,19,23,24,27,36,37]. Second, we analyze IoT-aware consensus including trust-weighted and hierarchical designs that shift work to edges to capture the performance/energy realities of constrained devices [25,26,38,39]. Third, we map privacy preserving mechanisms (e.g., ZKPs, off chain/IPFS anchoring) to regulatory needs (e.g., consent or revocation) in operational scenarios [18,24,40]. Collectively, this positions our work at the intersection of identity, access control, trust scoring, and deployability in heterogeneous IoT networks.
2. Trust Management Frameworks
Trust management serves as a cornerstone of secure IoT ecosystems, especially in contexts marked by device heterogeneity, decentralized ownership, and constantly shifting network topologies. Traditional trust management in IoT has typically depended on centralized authorities or reputation-based mechanisms. Yet, these approaches remain constrained by issues of scalability, limited resilience, and heightened vulnerability to insider threats. Such constraints have prompted increasing scholarly interest in blockchain, which is examined as a decentralized and tamper-resistant basis for establishing trust in IoT networks. Figure 2 illustrates IoT ecosystems that depend on centralized trust management systems to facilitate communication across different layers and components. Traditional centralized trust models prove inadequate for addressing the dynamic topology and scale of IoT systems. Yet, reducing dependence on such centralized mechanisms remains a persistent challenge in the literature. In this section, we examine state-of-the-art research on trust management in IoT environments, with particular attention to approaches for decentralized identity management and the use of smart contracts in supporting trust within decentralized systems.
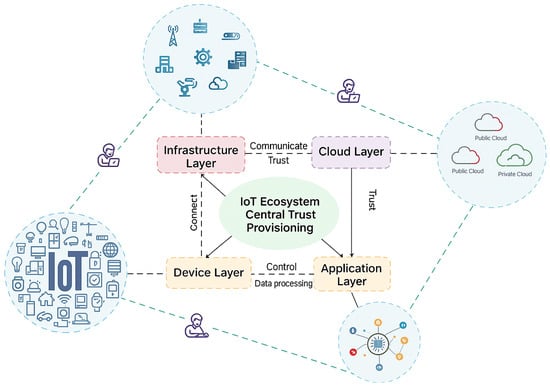
Figure 2.
Trust Framework in IoT Ecosystems.
Trust management in IoT environments remains a pressing challenge given the decentralized, heterogeneous, and frequently adversarial nature of device interactions. Leveraging distributed consensus and immutability, blockchain has facilitated the emergence of decentralized frameworks that evaluate trust through device behavior, interaction histories, and context-aware mechanisms [15,41,42].
The prevailing IoT ecosystem continues to depend heavily on trusted third parties (TTPs) for data storage and processing [6]. Yet, TTP-based frameworks are inherently constrained by the shortcomings of centralized architectures, notably limited scalability, bandwidth inefficiencies, heightened privacy risks, and susceptibility to single points of failure [43,44,45,46]. In recent years, various schemes have been introduced to enhance trust management in IoT and mitigate emerging security challenges [47]. Much of the existing literature, however, remains centered on trust mechanisms rooted in centralized models, with particular emphasis on device and user authentication protocols as well as data access control mechanisms [44,48,49]. Table 2 summarizes the key characteristics and limitations of centralized trust management techniques.

Table 2.
Centralized Trust Management Techniques and Their Limitations in IoT Systems.
Several studies have investigated trust management in IoT, yet many reveal significant shortcomings in handling the complexities of heterogeneous environments. Sicari et al. [28] outlined numerous open research challenges in IoT ecosystems, but their contribution was limited to high-level observations without proposing concrete frameworks for practical trust establishment. Although privacy, authentication, and user–device trust are consistently recognized as critical requirements, existing solutions remain fragmented. Behrouz et al. [29] provided a comprehensive taxonomy of trust management in IoT, categorizing it into four primary categories: reputation-based, policy-based, prediction-based, and recommendation-based schemes, with a comparative analysis using trust metrics. However, their review remains anchored in traditional models and does not sufficiently engage with recent developments such as blockchain-based and decentralized mechanisms. Moreover, while the benefits and drawbacks of each category were discussed, the study offered little assessment of scalability or real-world deployment feasibility. Later works [30] broadened the scope by addressing challenges such as heterogeneity, integrity, scalability, and device management, yet they largely presented conceptual perspectives rather than actionable strategies for large-scale systems. Similarly, comparative studies in [31,32] examined different TMS designs, highlighting commonalities and differences but again focusing on abstract characteristics rather than practical adaptability to dynamic, decentralized, and privacy-sensitive IoT environments. Taken together, these works establish a valuable foundation for understanding IoT trust management but fall short of addressing the integration of decentralized technologies, smart contract automation, and AI-driven trust evaluation models, gaps this survey seeks to address.
Bhatt et al. [8] introduced an Attribute-Based Access Control (ABAC) model tailored for cloud-enabled IoT environments. Their approach highlights dynamic, context-aware authorization that enables fine-grained control by incorporating factors such as user roles, device characteristics, environmental conditions, and resource sensitivity. The model’s applicability was demonstrated through use cases including smart home automation and smart parking, effectively addressing key challenges related to security, privacy, and scalability in cloud-based IoT systems. A widely adopted strategy is behavior-based trust assessment. Uzair et al. [15] introduced a blockchain-enabled protocol that evaluates dynamic trust values using historical vehicular data, while P. et al. [42] proposed an adaptive model employing smart contracts to penalize malicious nodes and incentivize compliant behavior in vehicular networks. Both approaches demonstrate notable effectiveness in mitigating Sybil attacks and false data injection.
Rouzbahani and Taghiyareh [50] proposed SCoTMan, a scalable smart contract–based trust framework for the Social IoT that integrates context-aware constraints and behavior tracking to assess trustworthiness in real time. By enabling dynamic weighting of social interactions and role hierarchies, their model improves both flexibility and resilience in highly dynamic environments. In parallel, Asiri and Miri [51] developed a Sybil-resistant trust model that leverages blockchain-based voting to validate device reputation in densely populated IoT networks.
Multi-dimensional trust models have also attracted growing interest. Ma et al. [52] proposed a secure usage control framework that evaluates trust through service credibility, user behavior, and temporal metrics, all managed via blockchain. Likewise, Hassan et al. [18] employed IPFS and smart contracts to support secure trust data streaming, enabling consensus formation while maintaining low latency and scalability.
2.1. Decentralized Identity Management
Effective identity management is central to securing IoT ecosystems. Conventional identity models, which rely on centralized credential issuance and verification, often suffer from bottlenecks, privacy risks, and single points of failure. To address these shortcomings, Decentralized Identity Management (DIM) has emerged as a promising alternative, leveraging blockchain and distributed ledger technologies (DLTs) to shift control of digital identities from central authorities to individual devices and users [23,24]. In these frameworks, trust is anchored in cryptographic proofs, immutable records, and verifiable credentials maintained on decentralized networks. Core technologies underpinning DIM in IoT include: (i) Decentralized Identifiers (DIDs), which provide globally unique identifiers directly controlled by the entity without requiring a central registry; (ii) verifiable credentials, enabling entities to present digitally signed credentials from trusted authorities that can be selectively disclosed and verified without exposing unnecessary personal data; (iii) blockchain/distributed ledgers, offering the infrastructure to store DIDs, manage cryptographic proofs, and ensure transparency and auditability; and (iv) self-sovereign identity (SSI), a paradigm granting individuals and devices full ownership and control of their digital identities, including the ability to grant or revoke access without intermediaries [22]. Table 3 provides a comparative summary of blockchain-based identity management approaches and their defining features. Figure 3 illustrates core technologies which underpin decentralized identity management in IoT.

Table 3.
Blockchain-Based Identity Management Approaches.
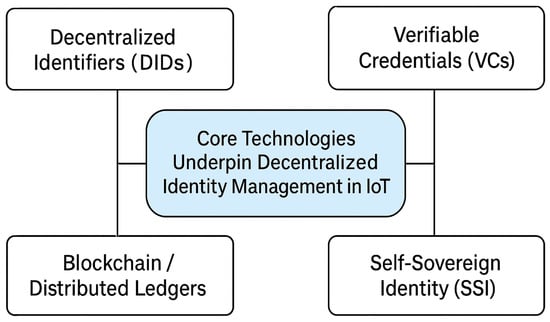
Figure 3.
Decentralized identity management uses several core technologies in IoT.
2.1.1. Decentralized Identifiers (DIDs)
Ansey et al. [54] proposed Gnomon, a decentralized identifier framework that replaces conventional PKI with self-sovereign DIDs to streamline 5G IoT device onboarding and ensure secure software maintenance. In this model, each device is provisioned with a DID generated through the Sidetree-based Microsoft ION method, with operations anchored to the Bitcoin blockchain and DID documents stored in IPFS for tamper-resistant, large-scale storage. Using its DID, the device acquires verifiable credentials from an identity hub, enabling it to authenticate software publishers and cryptographically verify firmware images before installation, thereby overcoming certificate revocation and expiry issues that hinder traditional PKI systems.
Zhang et al. [55] introduced TrID, a DID-centric framework designed to secure the full lifecycle of IoT data, spanning device authentication, access authorization, transmission, and storage, while avoiding the overhead of blockchain-based solutions. The framework embeds immutable DIDs directly into device hardware during manufacturing and issues Verifiable Credentials (VCs) and Verifiable Presentations (VPs) to establish an end-to-end trust chain for data consumers. To achieve efficiency, TrID employs four lightweight protocols, mutual authentication, data-access authorization, VP-based validation, and encrypted storage, which collectively reduce mutual-authentication latency to roughly 10% of comparable on-chain methods and enable decryption of 10 MB ciphertext in under 100 ms. These results demonstrate that DID-based schemes can provide both robust security assurances and practical performance for large-scale IoT deployments.
Waleed et al. [56] presented a DID framework built on IOTA Chrysalis, replacing energy-intensive, fee-based blockchains with the Tangle’s feeless DAG to provide a scalable and cost-efficient identity layer for heterogeneous IoT devices. The architecture introduces lightweight APIs and smart-contract hooks to create, update, revoke, and resolve device DIDs, all maintained on-ledger without reliance on centralized intermediaries. Proof-of-concept experiments demonstrated that broadcasting DID payloads of up to 30 kB from both desktop systems and Raspberry Pi devices is feasible, confirming the framework’s practicality on resource-constrained hardware. The authors further envision evolving this prototype into a full-scale DID registry on Tangle, enabling richer trust services and enhanced interoperability across future IoT ecosystems.
Polychronaki et al. [24] proposed a DID-based scheme that integrates Verifiable Credentials with smart contracts to enable both role-based and attribute-based access control, ensuring privacy, scalability, and alignment with legal frameworks such as GDPR. In parallel, Samir et al. [23] introduced DT-SSIM, a self-sovereign identity model that employs secret sharing and cryptographic proofs to facilitate secure multi-domain authentication and credential portability.
In the healthcare domain, Akkaoui [4] implemented a DID-based model designed to secure patient device identities and regulate data access. Likewise, Alkhamisi and Alboraei [5] proposed a lightweight DID framework that enables privacy-aware access control by incorporating real-time device behavior.
Ramezan and Meamari [40] proposed zk-IoT, a zero-knowledge proof-based system that enables identity verification while preserving anonymity and unlinkability by eliminating the need to disclose private information. Complementing this approach, Rouzbahani and Taghiyareh [41] demonstrated the integration of dynamic DIDs in social IoT environments, facilitating peer-to-peer trust negotiation without reliance on third-party validation.
2.1.2. Verifiable Credentials (VCs)
Mazzocca et al. [57] introduced EVOKE, an IoT-oriented revocation scheme that augments W3C Verifiable Credentials (VCs) with an elliptic curve-based cryptographic accumulator, enabling large-scale and offline revocation with minimal overhead on constrained devices (around 1.5 KB per node for the accumulator value and witness). Their prototype, EvalAccess Control (CapBAC) framework that encodes an IoT user’s fine-grained rights within W3C Verifiable Credentials (VCs), thereby removing the need for device-side access control on connected nodes within the first hour, even when half the network initially misses revocation updates, while issuers can generate witnesses efficiently (around 80 ms per million VCs). By decoupling trust from centralized PKI and providing scalable, efficient credential life-cycle management, EVOKE illustrates how VCs can achieve lightweight, fine-grained identity assurance across heterogeneous IoT environments, addressing a key barrier to large-scale adoption in resource-constrained settings.
Fotiou et al. [58] proposed a capabilities-based access control (CapBAC) framework that encodes an IoT user’s fine-grained rights within W3C Verifiable Credentials (VCs), removing the need for device-side access control lists and the continuous presence of a trusted intermediary. Each VC is bound to a Decentralized Identifier, enabling privacy-preserving proof-of-possession during access requests, while lightweight revocation is supported through a compact bit string list. To ensure interoperability, issuance and verification processes are aligned with standard OAuth 2.0 flows. Prototype evaluations on Raspberry Pi and ESP32 boards showed VC generation in under 0.1 ms and on-device verification in approximately 10–160 ms, confirming the framework’s practicality for resource-constrained IoT deployments without compromising security or user unlinkability.
Lagutin et al. [37] demonstrated that W3C-standardised Verifiable Credentials (VCs) can be leveraged even by highly constrained IoT devices when intensive cryptographic operations are delegated to an OAuth-compliant authorization server (AS). In their printing service case study, a university-issued VC encoding a user’s printing rights is converted into a zero-knowledge proof submitted to the AS, which then issues a proof-of-possession access token that the printer can validate without parsing the credential itself, thereby reducing device overhead and preserving privacy. By integrating this workflow with ACE-OAuth, the authors presented a practical, fine-grained, and self-sovereign access-control mechanism that avoids traditional certificate management while maintaining compatibility with existing OAuth infrastructures.
2.1.3. Blockchain/Distributed Ledgers
A Distributed Ledger is a technology that maintains replicated, shared, and synchronized digital records across participants in both private and public networks, often distributed over multiple locations, organizations, and jurisdictions.
Ghaffari et al. [34] provide a comprehensive survey of how blockchain and other distributed-ledger technologies (DLTs) can serve as the foundation for modern identity-and-access-management (IAM) infrastructures. Their analysis highlights how DLTs, through immutability and decentralized consensus, eliminate the single points of failure characteristic of server-centric IAM, while smart contracts enable self-sovereign identity, auditable policy enforcement, and fine-grained access control across diverse IoT, cloud, and 5G environments. The authors further propose a three-dimensional taxonomy that classifies over sixty state-of-the-art approaches by IAM function (registration, authentication, authorization, and monitoring), by access-control model (e.g., RBAC, ABAC, and capability-based), and by application domain. They also identify ongoing challenges concerning ledger scalability, interoperability, and privacy-preserving data minimization in both permissioned and permissionless settings. Ref. [59] proposed DLedger, a lightweight private distributed-ledger architecture for IoT business networks that replaces energy-intensive blockchains with a Directed Acyclic Graph (DAG) of records and substitutes Proof-of-Work with a resource-efficient Proof-of-Authentication (PoA), where each record is signed using the originator’s certified key. This approach enables constrained devices to “mine” their own data while ensuring non-repudiation and tamper resistance through inter-record locking. To address intermittent connectivity, DLedger is built on Named Data Networking (NDN), which employs in-network caching, multicast, and stateful forwarding, allowing disjoint sub-networks to continue appending records and later reconcile without creating forks. Simulation results indicate that the unconfirmed-record set remains bounded and confirmation latency stable as the number of IoT nodes increases, highlighting the system’s scalability, resilience to network partitions, and suitability for compliance-critical applications in industrial and smart-grid contexts [60].
Bouras et al. [35] present a comprehensive survey of distributed-ledger technology (DLT) applications in eHealth identity management, emphasizing how blockchain’s decentralized consensus and immutable audit trail can overcome the single-authority bottlenecks of conventional IAM systems. Their review highlights how permissioned ledgers and self-sovereign identity (SSI) frameworks enable patients to maintain cryptographic ownership of their identifiers while selectively disclosing verifiable claims, thereby strengthening privacy, regulatory compliance, and interoperability across hospitals, insurers, and research institutions. At the same time, the authors identify unresolved challenges, including performance limitations, data-standard harmonization, and incentive mechanisms that must be addressed for blockchain-based identity management to scale to national eHealth infrastructures, outlining a concrete research agenda for future exploration.
2.1.4. Self-Sovereign Identity (SSI)
Self-Sovereign Identity (SSI) [61] is a decentralized identity paradigm that grants individuals and devices full ownership and control of their digital identities. By leveraging blockchain, decentralized identifiers, and verifiable credentials, SSI enables secure and privacy-preserving interactions without dependence on centralized authorities.
Kulabukhova et al. [62] explore how distributed-ledger technology supports self-sovereign identity (SSI) for IoT devices, contending that a permissioned blockchain can serve as the “root of trust” traditionally assigned to central authorities, thereby mitigating the single point of failure in conventional public key infrastructures. Their study evaluates multiple ledger-based SSI frameworks, including Hyperledger Indy/Sovrin, uPort, Civic, Jolocom, and Veres One, highlighting trade-offs in transaction costs, consensus overhead, and DID-method compliance. They also propose an authentication protocol in which IoT wallets resolve decentralized identifiers (DIDs) to on-chain public keys and establish pairwise encrypted channels without requiring out-of-band key exchange. Demonstrating the use of ledger-anchored identities to secure logistics “smart boxes” and other resource-constrained devices, the authors underscore the viability of blockchain as a scalable, tamper-resistant foundation for identity and access management in heterogeneous IoT supply-chain environments.
Efat et al. [23] introduced DT-SSIM, a decentralized self-sovereign identity management framework designed to tackle trust, privacy, and interoperability challenges in IoT systems. Built on a consortium blockchain, DT-SSIM allows users to generate decentralized identifiers (DIDs) and manage identity credentials independently, enabling device-to-device trust establishment without reliance on centralized identity providers. The framework leverages smart contracts to automate policy enforcement and employs cryptographic proofs to validate identities and regulate access. By decoupling identity ownership from service providers and supporting verifiable interactions across heterogeneous domains, DT-SSIM illustrates the potential of blockchain-based identity models to deliver secure and scalable IoT trust infrastructures.
Weingaertner and Camenzind [63] proposed a blockchain-based identity management framework for IoT devices that applies the principles of self-sovereign identity (SSI) to establish immutable, decentralized, and verifiable device identities. In their model, each device is provisioned with a unique identifier at the manufacturing stage, which is then recorded on the Ethereum blockchain. This design enables secure bootstrapping, ownership tracking, and proof of origin through smart contracts and Decentralized Identifiers (DIDs). The framework further supports asynchronous registration via JSON Web Tokens (JWTs), thereby enhancing trust and laying the groundwork for scalable device inventories and firmware updates within a distributed ledger environment.
2.1.5. Smart Contract Design and Automation
Smart contracts are autonomous programs that execute predefined conditions, enabling automated access control, auditing, and resource coordination within IoT systems. Ethereum remains the leading platform owing to its flexibility and strong developer ecosystem, while permissioned frameworks such as Hyperledger provide enhanced privacy and scalability, making them well-suited for industrial deployments [17,19].
Loukil et al. [19] proposed a behavior-aware smart contract model in which device access rights adapt dynamically to behavioral inputs, thereby strengthening privacy and security in both home and industrial IoT settings. Similarly, Fotiou et al. [17] designed smart contracts to enable secure, large-scale IoT access, incorporating immutable logs and fine-grained permission controls to ensure accountability and flexibility.
Zaidi et al. [27] employed smart contracts to automate identity revocation and attribute validation in large-scale IoT systems, enhancing both efficiency and security. In parallel, Abubakar et al. [53] proposed a scalable blockchain framework integrated with MQTT, enabling lightweight and effective identity management tailored for resource-constrained IoT environments.
Zaidi et al. [27] developed attribute-based contract enforcement mechanisms that grant or deny access according to user or device metadata, integrating ABAC with smart contracts to provide decentralized yet policy-compliant identity management. In a related direction, Javaid et al. [15] combined Physical Unclonable Functions (PUFs) with smart contracts to enable secure vehicular identity verification, thereby mitigating risks of spoofing and impersonation.
Haya et al. [18] utilized smart contracts to support secure logging and real-time data validation in IoT networks, with IPFS employed to offload bulk data storage. Similarly, Samir et al. [23] automated identity lifecycle processes, such as revocation, renewal, and escalation through verifiable triggers embedded in smart contracts.
These implementations highlight the crucial importance of integrating smart contracts with adaptive privacy controls and robust audit mechanisms. Table 4 summarizes selected trust management strategies and the blockchain platforms used.Table 5 summarizes key smart contract designs across diverse IoT applications.

Table 4.
Blockchain-Based Trust Management Frameworks for IoT.

Table 5.
Smart Contract Applications in Blockchain–IoT Systems.
2.1.6. Consensus Mechanisms and Performance
Consensus protocols are essential for maintaining consistency across decentralized ledgers, yet their high computational and energy requirements make them impractical for IoT settings. Conventional mechanisms such as Proof-of-Work (PoW) are particularly unsuitable for resource-constrained devices, driving the exploration of lightweight, trust-aware alternatives that balance efficiency with robust security guarantees [25,26,50]. Table 6 presents notable consensus innovations for blockchain–IoT networks, including the key feature applied for the proposed method.

Table 6.
Consensus Mechanisms for Blockchain–IoT Networks.
Ye et al. [25] introduced Proof-of-Trust (PoT), a consensus algorithm that incorporates device reputation into decision-making, thereby reducing computational redundancy by prioritizing high-trust nodes. In a related effort, Liu et al. [26] developed a cross-domain authentication management system built on a hierarchical blockchain architecture, where consensus tasks are distributed between edge-layer and core-layer chains, resulting in significant improvements in both latency and throughput.
Rouzbahani and Taghiyareh [50] employed a hybrid consensus model in their SCoTMan framework, dynamically alternating between Byzantine Fault Tolerance (BFT) and Proof-of-Trust (PoT) based on node behaviour and energy availability. Likewise, Javaid et al. [15] incorporated credibility metrics into consensus voting weights, thereby discouraging malicious activity and strengthening network reliability.
Other notable contributions include the adaptive PBFT approach by Mizna et al. [38], which adjusts quorum thresholds according to IoT network density, thereby improving scalability and efficiency. Similarly, Alkadi et al. [39] integrated energy-aware consensus into a federated IoT intrusion detection system, enabling sustained operation across low-power nodes while maintaining reliable security monitoring.
These emerging protocols illustrate a clear shift in consensus design toward greater flexibility and adaptability, aligning with the dynamic requirements and resource constraints of IoT environments.
2.2. Security and Privacy Mechanisms
Security and privacy are central to trust management in IoT, where heterogeneous, resource-constrained devices interact autonomously across decentralized and often untrusted networks [40]. Ensuring trust in such environments demands mechanisms that both authenticate entities and protect sensitive data from unauthorized access and inference attacks [65]. In blockchain-enabled IoT frameworks, security is commonly reinforced through cryptographic primitives and consensus protocols. Public key cryptography, hash functions, and digital signatures secure device identities, preserve message integrity, and prevent tampering with blockchain-stored data. Additionally, smart contracts automate access control and enforce trust relationships without centralized oversight, thereby mitigating insider threats and eliminating single points of failure.
Consensus mechanisms are fundamental to ensuring the security and consistency of distributed ledgers. Yet, traditional protocols such as Proof-of-Work (PoW) are ill-suited for IoT due to their computational and energy intensity. Consequently, lightweight alternatives such as Proof-of-Authority (PoA), Delegated Proof-of-Stake (DPoS), and Practical Byzantine Fault Tolerance (PBFT) are increasingly employed to balance security with efficiency in resource-constrained environments. Complementing these approaches, cryptographic schemes like attribute-based encryption (ABE) and identity-based encryption (IBE) enable fine-grained access control, allowing resource access to be governed by attributes rather than fixed identities. Together, these techniques strengthen confidentiality while supporting adaptable and scalable security policies.
Privacy preservation is a central challenge in IoT systems, where large volumes of personal and sensitive data are continuously generated and exchanged. While blockchain’s transparency and immutability enhance trust and accountability, they also introduce significant privacy risks in IoT contexts. To mitigate these risks, trust management frameworks increasingly incorporate privacy-enhancing technologies. Zero-knowledge proofs (ZKPs) enable parties to verify information without disclosing the underlying data, facilitating trust establishment while safeguarding privacy. Likewise, ring signatures and homomorphic encryption provide mechanisms for protecting confidentiality while still supporting verifiable interactions on public or semi-public ledgers. Such techniques are especially critical in regulatory contexts, such as GDPR compliance, where strict limitations on the exposure of personal data must be upheld.
Furthermore, off-chain storage solutions are often employed to mitigate privacy risks by keeping sensitive data outside the blockchain while storing only cryptographic hashes or access pointers on-chain. This hybrid approach strikes a balance between the benefits of blockchain integrity assurances and the privacy requirements of sensitive IoT applications.
Furthermore, off-chain storage solutions are frequently adopted to mitigate privacy risks by retaining sensitive data off-chain, while recording only cryptographic hashes or access pointers on-chain. This hybrid design preserves the integrity and auditability afforded by blockchain while meeting the stringent privacy requirements of sensitive IoT applications. Table 7 summarizes key security and privacy challenges in IoT environments and outlines corresponding blockchain-based mitigation strategies.

Table 7.
Security and Privacy Challenges and Blockchain-Based Mitigation Strategies (* P: Privacy).
IoT systems remain vulnerable to threats such as spoofing, replay, and man-in-the-middle attacks, mainly due to weak device authentication and the absence of centralized oversight. While blockchain enhances baseline integrity, additional security and privacy layers are essential to ensure compliance with data protection standards, such as the GDPR [18,24,40].
Zero-knowledge proofs (ZKPs) have become pivotal in enabling authentication while preserving data confidentiality. Ramezan and Meamari [40] introduced zk-IoT, a protocol that supports anonymous authentication alongside encrypted access logs. In a complementary approach, Samir et al. [23] integrated secret-sharing schemes into decentralized identity management, allowing credential recovery without reliance on central servers.
Haya et al. [18] employed Merkle trees in combination with IPFS to secure IoT data streams, creating tamper-evident logs suitable for forensic auditing. In parallel, Loukil et al. [19] leveraged smart contracts to dynamically adjust access permissions in response to user behavior, thereby enhancing intrusion resilience and enabling fine-grained access control.
Attribute-Based Access Control (ABAC) models, such as those proposed by Zaidi et al. [27], enable context-aware access decisions based on device metadata, thereby minimizing risks of over-permissioning. Complementarily, Rouzbahani and Taghiyareh [41] incorporated social trust constraints into privacy models, strengthening the reliability and accountability of device collaborations [67].
Blockchain’s immutability also supports robust forensic logging. Al-Turjman et al. [20] integrated deep learning with blockchain for federated intrusion detection, while Alkhamisi and Alboraei [5] emphasized the role of decentralized logs as verifiable evidence for policy enforcement.
To mitigate device spoofing and eavesdropping without exposing sensitive data, several studies integrate zero-knowledge proofs (ZKPs) directly into the blockchain layer. For example, the zk-IoT protocol enables anonymous device authentication while maintaining encrypted access logs on-chain [40]. In scenarios requiring credential revocation or recovery, secret-sharing schemes distribute key shards among multiple peers, preventing any single entity from compromising the identity while still supporting deterministic restoration following loss or key rotation [23].
Immutable hash pointers remain central to ensuring data integrity, yet Merkle tree anchoring with off-chain storage offers a more storage-efficient approach. Haya et al. [18] store only root hashes on-chain while maintaining streaming sensor data in IPFS, producing tamper-evident but lightweight audit trails. To comply with GDPR’s “right to erasure,” privacy-aware frameworks encrypt personal data off-chain and record only cryptographic anchors on the ledger; when users withdraw consent, smart contract logic can revoke or re-key these anchors [5]. This encrypted anchoring mechanism also strengthens credential security by binding each claim to a verifiable on-chain hash, thereby preventing forgery.
Attribute-Based Access Control (ABAC) enforced through smart contracts enables dynamic, metadata-driven permissions, thereby reducing over-provisioning in large-scale IoT deployments [27]. Behavior-aware extensions refine these permissions at runtime; for example, Loukil et al. [19] adapt access levels in response to real-time usage patterns, strengthening intrusion resilience without manual oversight. Extending further, social-trust privacy filters incorporate peer reputation into access decisions, helping to mitigate collusion and insider threats in collaborative IoT environments [41].
Deep learning models integrated with consortium blockchains enable intrusion detection systems (IDSs) that both identify coordinated attacks at the edge and immutably log forensic evidence. Al-Turjman et al. demonstrated that such federated IDSs preserve data locality while maintaining high accuracy in detecting complex threat signatures [39]. Complementing these systems, policy verification smart contracts allow regulators and auditors to query proof-of-compliance logs on demand, thereby eliminating the single points of failure that undermine traditional, centrally managed SIEM platforms [5].
Physical Unclonable Function (PUF) fingerprints bind blockchain identities directly to device hardware, mitigating Sybil and cloning attacks even under adversarial network control. Javaid et al. [15] showed that coupling PUF challenges with smart contract logic effectively blocks rogue-node injection in vehicular IoT, while avoiding the storage burden associated with certificate revocation lists.
Resource-constrained devices can still engage in trust formation through lightweight cryptographic primitives. Jingwei et al. [25] applied trust-weighted signatures alongside a Proof-of-Trust (PoT) leader-election algorithm, achieving lower authentication latency and reduced energy consumption compared with traditional PKI-based handshakes. When integrated with complementary mechanisms, such consensus optimisations contribute to a holistic, defence-in-depth strategy for blockchain-enabled IoT deployments.
2.3. AI and Machine Learning Integration with IoT Trust Management
The integration of Artificial Intelligence (AI) and Machine Learning (ML) into trust management frameworks has been widely explored as a means to enhance adaptability, scalability, and intelligence in IoT environments [68]. Traditional rule-based or static trust models often fail to accommodate the dynamic, heterogeneous, and evolving nature of IoT networks. In contrast, AI- and ML-based approaches enable data-driven, context-aware, and adaptive trust evaluation mechanisms that learn from historical behavior, detect anomalies, and predict trustworthiness in real time. When combined with blockchain, this synergy becomes particularly powerful: ML contributes predictive analytics and anomaly detection, while blockchain ensures traceability and auditability of both trust data and AI model outputs [20,69].
Existing research demonstrates the application of AI and ML across multiple dimensions of IoT trust management [33,68,70,71]. For instance, behavioral analysis examines communication patterns, resource consumption, and service interactions to identify anomalous or malicious activity, thereby supporting dynamic trust assessment [68]. Trust prediction employs models such as decision trees, neural networks, and Bayesian networks to estimate the future trustworthiness of devices and services using historical data [72]. Reputation systems leverage AI-driven aggregation and interpretation of trust feedback from diverse sources, producing more accurate and resilient trust decisions [68,73]. Finally, anomaly and intrusion detection techniques [74,75] enable resource-constrained IoT networks to detect and mitigate trust violations autonomously, thereby reducing their dependence on human oversight.
Al-Turjman et al. [20] proposed a federated intrusion detection system that integrates deep learning with blockchain to identify sophisticated cyberattacks in Industrial IoT (IIoT) environments. Their decentralized architecture supports cross-node intelligence sharing while preserving data privacy. Building on this work, Motamarri et al. [20] incorporated real-time feedback loops into smart contracts, allowing dynamic threshold adjustments for predictive alerting and more adaptive threat mitigation.
Chandan et al. [69] proposed an adaptive blockchain–IoT framework that fuses smart contract logic with reinforcement learning to enable proactive resource management. This integration enhances system efficiency and responsiveness, making it particularly well-suited for dynamic environments such as smart cities and industrial automation.
Zaidi et al. [27] applied machine learning algorithms to adjust access thresholds dynamically according to device behavior, embedding the results into ABAC-driven smart contracts for decentralized enforcement. In parallel, Alkadi et al. [39] designed a collaborative ML-based intrusion detection framework that leverages blockchain to log, verify, and autonomously respond to detected threats.
AI-enabled blockchain approaches are increasingly being investigated for dynamic trust scoring. Singh et al. [42] employed supervised learning to develop adaptive trust models that integrate historical interaction data with blockchain logs. This line of research opens promising opportunities for automated trust negotiation in rapidly evolving IoT environments.
AR and Katiravan [74] proposed a hybrid deep learning framework for IoT trust assessment that integrates social and behavioral indicators to strengthen resilience against advanced attacks. Their model combines Bi-GRU (Bidirectional Gated Recurrent Unit) and Bi-LSTM (Bidirectional Long Short-Term Memory) architectures to analyze dynamic trust features derived from device interaction histories. This approach enables accurate detection of abnormal behavior while adapting to real-time contextual changes, outperforming conventional static trust models in both precision and robustness. The findings highlight how deep-learning techniques can advance decentralized trust management by continuously capturing nuanced trust patterns in heterogeneous IoT environments.
Chithanuru and Ramaiah [75] introduced an AI-driven anomaly detection framework for blockchain-based IoT systems that combines an artificial neural network (ANN) with an adaptive linear regression algorithm. The system continuously monitors blockchain transactional flows to identify deviations signalling malicious behavior, such as data manipulation or unauthorized access. Implemented within a Hyperledger Fabric environment, the framework achieves real-time detection with minimal computational overhead, making it well-suited for resource-constrained IoT deployments. This work demonstrates how AI can enhance blockchain infrastructures by enabling early, autonomous threat detection, thereby strengthening trust and resilience in distributed IoT ecosystems.
AlGhamdi et al. [72] proposed a framework for developing trusted IoT healthcare information systems integrating AI and blockchain. The approach includes a smart unsupervised medical clinic designed to provide safe and fast services during pandemics without exposing medical staff to danger, a deep learning algorithm for COVID-19 detection based on X-ray images using transfer learning with the ResNet152 model, and a novel blockchain-based pharmaceutical system. These components aim to enhance efficiency, security, and transparency in healthcare, with the algorithms and systems proven effective and secure for use in healthcare environments. In federated IoT settings, combining blockchain with AI-driven reputation systems offers a robust mechanism for trust management. Fortino et al. [73] introduced a multi-agent architecture in which each IoT device is represented by a software agent that cooperates based on a quantifiable reputation capital (RC). This RC is continuously updated through blockchain-certified interactions and feedback loops, enabling AI-enhanced group formation and partner selection in decentralized environments. Experimental evaluations showed that when the proportion of malicious agents remained below 25%, nearly all adversarial actors were successfully identified, while honest agents incurred significantly lower service costs. This hybrid framework highlights the effectiveness of integrating AI-based behavioral models with blockchain to foster trust-aware cooperation in dynamic and distributed IoT ecosystems.
The integration of AI into blockchain-enabled trust management frameworks for IoT brings notable advantages but also presents significant challenges. AI, particularly machine learning, supports dynamic and adaptive trust evaluations by continuously learning from device behaviors, contextual factors, and historical data. This adaptability improves the precision of trust decisions and enhances security through early anomaly detection, identification of malicious activity, and recognition of compromised devices. Automated, AI-driven assessments further reduce reliance on manual oversight, enabling scalable, self-managing IoT ecosystems. Privacy-preserving approaches such as federated learning complement blockchain’s decentralized architecture, allowing devices to collaboratively train trust models without exposing sensitive raw data.
Nonetheless, significant limitations remain. Many AI algorithms require substantial computational, storage, and energy resources, which pose difficulties for deployment on resource-constrained IoT devices. Their effectiveness is also contingent on access to high-quality, diverse datasets an asset that is often scarce or fragmented in practice. Privacy concerns persist, as behavioral data collected for training may still reveal sensitive information if not properly protected. Moreover, AI models especially deep learning architectures tend to lack transparency and interpretability, complicating auditability and regulatory compliance in trust-sensitive environments. Finally, AI itself introduces vulnerabilities, such as susceptibility to adversarial manipulation, which can undermine the reliability and robustness of trust evaluations.
Table 8 summarizes key studies integrating AI and ML techniques into blockchain–IoT trust management frameworks.

Table 8.
AI and ML integration into Blockchain–IoT.
3. Blockchain-Based Trust Management Challenges
3.1. Regulatory and Compliance Challenges
Blockchain’s permanence and decentralisation, while advantageous for transparency and audit trails, often clash with privacy regulations such as the General Data Protection Regulation (GDPR). Core GDPR principles like the “right to be forgotten,” data localisation, and consent-driven data in smart contracts, allowing privacy obligations to be enforced in real-time across nodes [24,27].
Polychronaki et al. [24] advanced the discussion by applying Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs). Their approach gives individuals greater autonomy over personal data, while smart contracts enable access rights to be granted or withdrawn dynamically, partially satisfying GDPR’s requirements for consent and minimization. While DIDs offer high privacy, they trade off scalability compared to VCs, which prioritize verification speed but increase latency in resource-constrained IoT.
Similarly, Zaidi et al. [27] explored attribute-based access control (ABAC) with revocation functions, ensuring expired credentials can no longer be used even in immutable environments. Smart contracts automate access but introduce adoption barriers in legacy IoT due to gas costs and interoperability.
Alkhamisi and Alboraei [5] contributed a decentralized protocol that separates user credentials from blockchain records, enabling localized enforcement of regional data rules.
Together, these strategies reveal a trend towards balancing blockchain’s technical strengths with the evolving legal requirements of global IoT ecosystems. Together, these strategies reveal a trend towards balancing blockchain’s technical strengths with the evolving legal requirements of global IoT ecosystems, as detailed in Table 9.

Table 9.
Compliance Strategies in Blockchain-Based IoT Systems.
3.2. Implementation Considerations and Challenges
Applying blockchain to IoT is rarely straightforward. Beyond theoretical advantages, deploying blockchain across heterogeneous devices and networks raises concerns around scale, interoperability, cost, and energy demand [25,26,38].
Lightweight devices at the edge often lack the resources to perform consensus or advanced cryptographic functions. Ye et al. [25] addressed this through a Proof-of-Trust (PoT) consensus model, where only reliable nodes, judged by behaviour and reputation shoulder heavy validation work. This reduces overall computational overhead. PoW offers strong security but poor energy efficiency versus PoT’s lightweight approach for constrained devices.
Scalability has been tackled by Liu et al. [26], who proposed a hierarchical ledger model. In their framework, local edge blockchains perform fast and lightweight validation, periodically syncing with a global chain to maintain overall consistency.
Standardised protocols are also vital for interoperability. Polychronaki et al. [24] advocated for DIDs and VCs as a unifying identity layer to ease device onboarding across diverse manufacturers. Akkaoui [4], working in the medical IoT space, highlighted the need for fault-tolerant blockchain nodes to ensure compliance and high availability in safety-critical applications.
At the network level, Mizna et al. [38] explored the integration of Software-Defined Networking (SDN) as a flexible control plane that pairs with blockchain to enforce dynamic access rules. Complementing this, Rouzbahani and Taghiyareh [41] proposed modular smart contracts that can be tailored to device classes, streamlining deployments in mixed environments. Furthermore, Vinay et al. [76] proposed a blockchain-powered solution to safeguard IoT devices against attacks, utilizing smart contracts created in Remix IDE for IoT device registration and network monitoring. The approach includes algorithms for registration and monitoring, along with validation and verification techniques to identify and prevent cyber-attacks, demonstrating successful detection in results. Together, these approaches address key implementation challenges, as summarized in Table 10.

Table 10.
Blockchain–IoT Implementation Challenges and Solutions.
4. Emerging Applications and Use Cases
Blockchain’s promise for IoT is increasingly visible in sector-specific deployments. Its ability to strengthen identity management, ensure secure transactions, and enhance operational resilience is demonstrated in healthcare, transportation, smart cities, industry, and beyond.
In healthcare, Akkaoui [4] presented a blockchain-based framework for managing medical IoT devices. The system supports secure patient identities, ensures traceability of sensitive records, and aligns with stringent privacy regulations. Also, in healthcare, pilots like [65] validate key management for WBANs, reducing latency by 20%.
Vehicular networks have also embraced blockchain. Javaid et al. [15] integrated Physical Unclonable Functions (PUFs) with blockchain protocols to authenticate vehicles, mitigating spoofing risks and improving trust in connected transportation systems.
Smart city deployments [48] show DID-based data collection improving integrity in real-time monitoring. Similarly, smart city projects show similar benefits. Polychronaki et al. [24] proposed a decentralized model for IoT device registration and authorization, strengthening transparency and trust in urban infrastructure.
Industrial IoT (IIoT) has increasingly merged blockchain with AI. Motamarri et al. [20] developed blockchain–ML hybrids for intrusion detection, enabling predictive threat detection in real-time. IIoT testbeds [49] demonstrate blockchain-based federated learning for device failure detection, enhancing robustness in industrial settings.
In smart homes, Ref. [77] proposed SSHCEth, a secure smart home communications system based on Ethereum blockchain and smart contract, to address challenges like resource limitations, server overload, and privacy concerns in IoT, optimizing resource consumption while maintaining security and privacy benefits, with quantitative and qualitative evaluations under common threat models highlighting its effectiveness.
Energy systems are another critical use case. Alkadi et al. [39] designed blockchain-supported intrusion detection for smart grids, ensuring reliable energy distribution while minimizing cyber risks.
Supply chain operations also benefit from blockchain’s traceability. Ali et al. [64] showed how blockchain improves logistics by recording immutable product journeys. The same principles extend to agriculture, where blockchain combined with IPFS secures agricultural IoT data sharing [64].
Environmental monitoring is another frontier. Cui et al. [16] used blockchain to secure sensor streams, ensuring tamper-proof environmental records. Public safety has also seen progress: Loukil et al. [19] presented a blockchain-driven access control model that adapts permissions dynamically during emergencies.
Table 11 summarizes key blockchain–IoT applications across various domains, highlighting sector-specific use cases and their corresponding references.

Table 11.
Blockchain–IoT Applications Across Domains.
Future research should continue validating these applications in real-world conditions, refining compliance with evolving regulations, and developing cost-effective strategies for deployment at scale. Gaps include AI-driven trust explainability and economic incentives for blockchain participation in IoT.
5. Discussion and Future Directions
In this article, we have presented a comprehensive narrative review on blockchain technologies that are applicable to the IoT environment based on a proposed trust framework in the IoT ecosystem. We have also offered a significant potential to resolve core limitations in IoT ecosystems, particularly about trust decentralization, privacy-preserving identity (as discussed in Section 2), and secure automation. Through the integration of decentralized identity management schemes such as DIDs and VCs, paired with cryptographic protocols like ZKPs, blockchain provides scalable and tamper-resistant frameworks capable of enforcing dynamic trust and access control in real-time [23,24,40].
We further investigated blockchain-based trust management challenges including regulatory and compliance alongside with practical implementation challenges (discussed in Section 3). In this section, we further discuss emerging trends and future directions, together with some open issues and research challenges.
Despite significant advancements in leveraging blockchain-based trust systems in IoT environments, several open issues and research challenges persist.
- The widespread deployment of blockchain-based trust management technologies in the EoT ecosystem faces practical and systemic barriers, remaining an open issue. Although various studies have responded with hierarchical blockchain models, lightweight consensus mechanisms, and stratified node roles to mitigate these bottlenecks [25,26,41] scalability emerges as a leading challenge, especially in public blockchain networks such as Ethereum, where gas fees and network latency limit the viability of high-frequency IoT operations [25,26].
- Regulatory compliance is another critical frontier. While decentralization enhances data sovereignty and auditability, it simultaneously complicates adherence to privacy laws such as GDPR. Solutions such as off-chain storage, smart contract revocation logic, and policy-embedded blockchain applications are crucial to strike a balance between transparency and privacy [24,27].
- Interoperability poses additional concern, particularly in cross-domain IoT networks with heterogeneous device types and identity schemes. The integration of standards for decentralized identity and secure firmware update processes will be essential for achieving functional convergence across verticals such as healthcare, transportation, and industrial systems [4,5,26].
- The synergy between AI/ML and blockchain remains underexplored but promising. Projects such as federated learning-based intrusion detection or predictive maintenance demonstrate how decentralized intelligence can extend the autonomy and security of blockchain-powered IoT [20]. Smart contracts serve as policy enforcement agents for these AI-driven decisions, ensuring transparency and auditability of model outputs.
Addressing these open issues requires interdisciplinary collaboration, integrating insights from cybersecurity, networking, cryptography, machine learning, and distributed systems research.
According to the literature comprehensively reviewed in this survey paper, the following sections outline further research directions and future directions based on both research areas and priority focuses in blockchain-based trust management.
- Scalability: The need for lightweight Proof-of-Trust algorithms and edge–ledger architectures is critical to support massive IoT deployments and address the scalability issue. Future work may focus on reducing computational overhead while maintaining security.
- Privacy Enhancement: Advanced cryptographic techniques such as zero-knowledge proofs (ZKPs) and proxy re-encryption can enable data sharing without compromising confidentiality. Research is needed to adapt these schemes for resource-constrained IoT devices.
- Compliance Integration: The need for automation of regulatory compliance is also an important matter. For instance, GDPR-aware smart contract templates are required to enforce regulatory compliance automatically. This direction calls for frameworks that can provide a balance between legal requirements and decentralized execution.
- AI and Blockchain Fusion: Federated learning combined with on-chain triggers can enable a collaborative method for privacy-preserving model training. Future studies can investigate the integration of federated learning and blockchain in the IoT context.
- Smart Contract Governance: More modular and upgradeable contract systems are necessary to address evolving requirements in IoT ecosystems. Researchers may investigate secure upgrade mechanisms without disrupting existing services.
- IoT Interoperability: Standardized decentralized identity (DID) schemas and onboarding protocols are crucial for seamless device integration. Future work may focus on cross-vendor interoperability and trust establishment.
- Real-Time Trust Evaluation: Designing efficient mechanisms to process dynamic IoT interactions with low latency for real-time trust evaluation is required.
- Energy Efficiency: The need for proposing green consensus algorithms designed for constrained IoT devices is also a critical matter. Studies may focus on minimizing energy consumption while preserving both decentralization and security.
- Security Forensics: Immutable IoT forensics and auditability logs can enhance accountability in decentralized environments. Future work may explore scalable evidence collection and tamper-proof forensic analysis.
6. Conclusions
The combination of blockchain and decentralized identity can provide the IoT environment with a strong foundation for trust management and user-focused authentication. This integration can benefit various sectors, including healthcare, transportation, smart cities, and industrial automation. This survey paper has provided a comprehensive analysis of the role of blockchain in addressing trust, identity, and security challenges within the IoT environment through a trust framework in the IoT ecosystem. As IoT ecosystems expand across various sectors, addressing the inherent weaknesses of centralized trust managements by utilizing decentralized identity management methods that are robust, scalable, and adaptive solutions is paramount. Blockchain technologies enable resilient architectures for secure and scalable IoT ecosystems through decentralization, immutable logarithmic computation, and autonomous enforcement through smart contracts. We have studied various current methods that combine cryptographic algorithms such as ZKPs, Merkle trees, and proxy re-encryption to further strengthens the confidentiality and integrity of communications among constrained devices. Research should focus on establishing common standards embedding various compliance requirements directly into system design, and leveraging AI-based automation to unlock the full potential of blockchain in the IoT environment. Current implementations suffer from scalability limitations, regulatory misalignment, and resource limitations. However, novel architectural strategies such as hierarchical blockchains, lightweight consensus models, and federated intrusion detection mechanisms show viable pathways for addressing these limitations and still needs further investigation. Moreover, there is a need for cross-disciplinary collaboration between legal experts, system architects, cryptographers, and machine learning specialists to translate these innovations into resilient and real-world deployments.
Author Contributions
Conceptualization, B.K. and S.M.; methodology, B.K.; software, B.K.; validation, B.K., S.M., H.A. and A.S.S.; formal analysis, B.K.; investigation, B.K.; resources, B.K.; data curation, B.K.; writing—original draft preparation, B.K.; writing—review and editing, B.K., S.M., H.A. and A.S.S.; visualization, B.K.; supervision, S.M. and A.S.S.; project administration, B.K.; funding acquisition, A.S.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data sharing is not applicable to this article as no new data were created or analyzed in this study. All data supporting the reported results are derived from previously published studies cited within the manuscript.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Ande, R.; Adebisi, B.; Hammoudeh, M.; Saleem, J. Internet of Things: Evolution and technologies from a security perspective. Sustain. Cities Soc. 2020, 54, 101728. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, J.; Yan, Z.; Wan, Z.; Jäntti, R. A survey on blockchain-based trust management for Internet of Things. IEEE Internet Things J. 2023, 10, 5898–5922. [Google Scholar] [CrossRef]
- Khalil, U.; Malik, O.A.; Uddin, M.; Chen, C.L. A comparative analysis on blockchain versus centralized authentication architectures for IoT-enabled smart devices in smart cities: A comprehensive review, recent advances, and future research directions. Sensors 2022, 22, 5168. [Google Scholar] [CrossRef]
- Raifa, A. Blockchain for the Management of Internet of Things Devices in the Medical Industry. IEEE Trans. Eng. Manag. 2021, 70, 2707–2718. [Google Scholar] [CrossRef]
- Abrar, O. Alkhamisi and Fathy Alboraei Abrar O. Alkhamisi Alboraei. Privacy-aware Decentralized and Scalable Access Control Management for IoT Environment. J. King Abdulaziz-Univ.-Comput. Inf. Technol. Sci. 2019, 8, 71–84. [Google Scholar] [CrossRef]
- Zhang, J.; Li, T.; Ying, Z.; Ma, J. Trust-based secure multi-cloud collaboration framework in cloud-fog-assisted IoT. IEEE Trans. Cloud Comput. 2022, 11, 1546–1561. [Google Scholar] [CrossRef]
- Battah, A.A.; Iraqi, Y.; Damiani, E. A trust and reputation system for IoT service interactions. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2987–3005. [Google Scholar] [CrossRef]
- Bhatt, S.; Lo’ai, A.T.; Chhetri, P.; Bhatt, P. Authorizations in cloud-based internet of things: Current trends and use cases. In Proceedings of the 2019 Fourth International Conference on Fog and Mobile Edge Computing (FMEC), Rome, Italy, 10–13 June 2019; IEEE: New York, NY, USA, 2019; pp. 241–246. [Google Scholar]
- Li, X.; Ma, H.; Zhou, F.; Yao, W. T-broker: A trust-aware service brokering scheme for multiple cloud collaborative services. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1402–1415. [Google Scholar] [CrossRef]
- Aaqib, M.; Ali, A.; Chen, L.; Nibouche, O. IoT trust and reputation: A survey and taxonomy. J. Cloud Comput. 2023, 12, 42. [Google Scholar] [CrossRef]
- Shahraki, A.S.; Rudolph, C.; Grobler, M. Attribute-based data access control for multi-authority system. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; IEEE: New York, NY, USA, 2020; pp. 1834–1841. [Google Scholar]
- Almutairi, M.; Sheldon, F.T. IoT–Cloud Integration Security: A Survey of Challenges, Solutions, and Directions. Electronics 2025, 14, 1394. [Google Scholar] [CrossRef]
- Al-Hasnawi, A.; Niu, Y.; Tawfeq, J.F.; Pradhan, M.R.; Salahat, M.; Ghazal, T.M. IoT security frameworks: A comparative review with a focus on privacy. In Proceedings of the 2024 2nd International Conference on Cyber Resilience (ICCR), Dubai, United Arab Emirates, 26–28 February 2024; IEEE: New York, NY, USA, 2024; pp. 01–10. [Google Scholar]
- Shahraki, A.S.; Rudolph, C.; Alavizadeh, H.; Kayes, A.; Rahayu, W.; Tari, Z. Securing cross-domain data access with decentralized attribute-based access control. Ad Hoc Netw. 2025, 173, 103807. [Google Scholar] [CrossRef]
- Uzair, J.; Muhammad, A.; Biplab, S. A Scalable Protocol for Driving Trust Management in Internet of Vehicles With Blockchain. IEEE Internet Things J. 2020, 7, 11815–11829. [Google Scholar] [CrossRef]
- Cui, H.; Chen, Z.; Xi, Y.; Chen, H.; Hao, J. IoT Data Management and Lineage Traceability: A Blockchain-based Solution. In Proceedings of the 2019 IEEE/CIC International Conference on Communications Workshops in China (ICCC Workshops), Changchun, China, 11–13 August 2019. [Google Scholar] [CrossRef]
- Fotiou, N.; Pittaras, I.; Siris, V.A.; Voulgaris, S.; Polyzos, G.C. Secure IoT Access at Scale Using Blockchains and Smart Contracts. In Proceedings of the IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Washington, DC, USA, 10–12 June 2019. [Google Scholar] [CrossRef]
- Haya, R.H.; Salah, k.; Yaqoob, I.; Jayaraman, R.; Pesic, S.; Omar, M. Trustworthy IoT Data Streaming Using Blockchain and IPFS. IEEE Access 2022, 10, 17707–17721. [Google Scholar] [CrossRef]
- Loukil, F.; Ghedira-Guegan, C.; Boukadi, K.; Benharkat, A.; Benkhelifa, E. Data Privacy Based on IoT Device Behavior Control Using Blockchain. ACM Trans. Internet Techn. 2021, 21, 1–20. [Google Scholar] [CrossRef]
- Motamarri, N.; Satish, G.; Uma, H.R.; Barve, A.; Patil, H.; Taqui, S.N. Identification and Containment of Intrusion Attacks in an IIoT Network based on Machine Learning and Blockchain Technology. In Proceedings of the 2024 2nd International Conference on Intelligent Data Communication Technologies and Internet of Things (IDCIoT), Bengaluru, India, 4–6 January 2024. [Google Scholar] [CrossRef]
- Kortesniemi, Y.; Lagutin, D.; Elo, T.; Fotiou, N. Improving the privacy of iot with decentralised identifiers (dids). J. Comput. Netw. Commun. 2019, 2019, 8706760. [Google Scholar] [CrossRef]
- Mazzocca, C.; Acar, A.; Uluagac, S.; Montanari, R.; Bellavista, P.; Conti, M. A survey on decentralized identifiers and verifiable credentials. IEEE Commun. Surv. Tutor. 2025; early access. [Google Scholar]
- Samir, E.; Wu, H.; Azab, M.; Xin, C.; Zhang, Q. DT-SSIM: A Decentralized Trustworthy Self-Sovereign Identity Management Framework. IEEE Internet Things J. 2022, 9, 7972–7988. [Google Scholar] [CrossRef]
- Polychronaki, M.; Kogias, D.G.; Leligkou, H.C.; Karkazis, P.A. Blockchain Technology for Access and Authorization Management in the Internet of Things. Electronics 2023, 12, 4606. [Google Scholar] [CrossRef]
- Ye, J.; Kang, X.; Liang, Y.-C.; Sun, S. A Trust-Centric Privacy-Preserving Blockchain for Dynamic Spectrum Management in IoT Networks. IEEE Internet Things J. 2021, 9, 13263–13278. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; Xia, Y.; Hu, B.; Liu, J.; Wu, Q.; Tiwari, P. A Blockchain-Based Cross-Domain Authentication Management System for IoT Devices. IEEE Trans. Netw. Sci. Eng. 2024, 11, 115–127. [Google Scholar] [CrossRef]
- Zaidi, S.Y.A.; Shah, M.A.; Khattak, H.A.; Maple, C.; Rauf, H.T.; El-Sherbeeny, A.M.; El-Meligy, M.A. An Attribute-Based Access Control for IoT Using Blockchain and Smart Contracts. Sustainability 2021, 13, 10556. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Net. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Pourghebleh, B.; Wakil, K.; Navimipour, N.J. A comprehensive study on the trust management techniques in the Internet of Things. IEEE Internet Things J. 2019, 6, 9326–9337. [Google Scholar] [CrossRef]
- Aldowah, H.; Ul Rehman, S.; Umar, I. Trust in iot systems: A vision on the current issues, challenges, and recommended solutions. In Advances on Smart and Soft Computing: Proceedings of ICACIn 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 329–339. [Google Scholar]
- Ebrahimi, M.; Tadayon, M.H.; Haghighi, M.S.; Jolfaei, A. A quantitative comparative study of data-oriented trust management schemes in Internet of Things. ACM Trans. Manag. Inf. Syst. (TMIS) 2022, 13, 1–30. [Google Scholar] [CrossRef]
- Yao, X.; Farha, F.; Li, R.; Psychoula, I.; Chen, L.; Ning, H. Security and privacy issues of physical objects in the IoT: Challenges and opportunities. Digit. Commun. Netw. 2021, 7, 373–384. [Google Scholar] [CrossRef]
- Atlam, H.F.; Azad, M.A.; Alzahrani, A.G.; Wills, G. A Review of Blockchain in Internet of Things and AI. Big Data Cogn. Comput. 2020, 4, 28. [Google Scholar] [CrossRef]
- Ghaffari, F.; Gilani, K.; Bertin, E.; Crespi, N. Identity and access management using distributed ledger technology: A survey. Int. J. Netw. Manag. 2022, 32, e2180. [Google Scholar] [CrossRef]
- Bouras, M.A.; Lu, Q.; Zhang, F.; Wan, Y.; Zhang, T.; Ning, H. Distributed ledger technology for eHealth identity privacy: State of the art and future perspective. Sensors 2020, 20, 483. [Google Scholar] [CrossRef] [PubMed]
- Siris, V.A.; Dimopoulos, D.; Fotiou, N.; Voulgaris, S.; Polyzos, G.C. Trusted D2D-Based IoT Resource Access Using Smart Contracts. In Proceedings of the IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Washington, DC, USA, 10–12 June 2019. [Google Scholar] [CrossRef]
- Lagutin, D.; Kortesniemi, Y.; Fotiou, N.; Siris, V.A. Enabling Decentralised Identifiers and Verifiable Credentials for Constrained IoT Devices using OAuth-based Delegation. In Proceedings of the Workshop on Decentralized IoT Systems and Security. Internet Society, San Diego, CA, USA, 24 February 2019. [Google Scholar]
- Khalid, M.; Hameed, S.; Qadir, A.; Shah, S.A.; Draheim, D. Towards SDN-based smart contract solution for IoT access control. Comput. Commun. 2022, 198, 1–31. [Google Scholar] [CrossRef]
- Alkadi, O.; Moustafa, N.; Turnbull, B.; Choo, K.-K.R. A Deep Blockchain Framework-Enabled Collaborative Intrusion Detection for Protecting IoT and Cloud Networks. IEEE Internet Things J. 2021, 8, 9463–9472. [Google Scholar] [CrossRef]
- Ramezan, G.; Meamari, E. zk-IoT: Securing the Internet of Things with Zero-Knowledge Proofs on Blockchain Platforms. In Proceedings of the 2024 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Dublin, Ireland, 27–31 May 2024. [Google Scholar] [CrossRef]
- Rouzbahani, A.; Taghiyareh, F. Trust Management Enhancement for the Internet of Things: A Smart Contract Approach. In Proceedings of the 2023 13th International Conference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 1–2 November 2023. [Google Scholar] [CrossRef]
- Singh, P.K.; Singh, R.; Nandi, S.K.; Ghafoor, K.Z.; Rawat, D.B.; Nandi, S. Blockchain-Based Adaptive Trust Management in Internet of Vehicles Using Smart Contract. IEEE Trans. Intell. Transp. Syst. (Print) 2021, 22, 3616–3630. [Google Scholar] [CrossRef]
- Cheng, G.; Wang, Y.; Deng, S.; Xiang, Z.; Yan, X.; Zhao, P.; Dustdar, S. A lightweight authentication-driven trusted management framework for IoT collaboration. IEEE Trans. Serv. Comput. 2024, 17, 747–760. [Google Scholar] [CrossRef]
- Zhang, L.; Ye, Y.; Mu, Y. Multiauthority access control with anonymous authentication for personal health record. IEEE Internet Things J. 2020, 8, 156–167. [Google Scholar] [CrossRef]
- Xu, Z.; Shahraki, A.S.; Chilamkurti, N. A Fault-Tolerant Sharding Mechanism for Resilience and Scalability in Blockchain Using Backup Pool. Future Gener. Comput. Syst. 2026, 174, 107982. [Google Scholar] [CrossRef]
- Ding, X.; Wang, X.; Xie, Y.; Li, F. A lightweight anonymous authentication protocol for resource-constrained devices in Internet of Things. IEEE Internet Things J. 2021, 9, 1818–1829. [Google Scholar] [CrossRef]
- Aman, M.N.; Javaid, U.; Sikdar, B. A privacy-preserving and scalable authentication protocol for the internet of vehicles. IEEE Internet Things J. 2020, 8, 1123–1139. [Google Scholar] [CrossRef]
- Cullen, A.; Ferraro, P.; Sanders, W.; Vigneri, L.; Shorten, R. Access control for distributed ledgers in the internet of things: A networking approach. IEEE Internet Things J. 2021, 9, 2277–2292. [Google Scholar] [CrossRef]
- Zhang, W.; Zhang, H.; Fang, L.; Liu, Z.; Ge, C. A secure revocable fine-grained access control and data sharing scheme for SCADA in IIoT systems. IEEE Internet Things J. 2021, 9, 1976–1984. [Google Scholar] [CrossRef]
- Rouzbahani, A.; Taghiyareh, F. SCoTMan: A Scalable Smart Contract for Trust Management in Social IoT With Real-World Constraints. IEEE Access 2024, 12, 137836–137850. [Google Scholar] [CrossRef]
- Asiri, S.; Miri, A. A Sybil Resistant IoT Trust Model Using Blockchains. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018. [Google Scholar] [CrossRef]
- Ma, Z.; Wang, L.; Wang, X.; Wang, Z.; Zhao, W. Blockchain-Enabled Decentralized Trust Management and Secure Usage Control of IoT Big Data. IEEE Internet Things J. 2020, 7, 4000–4015. [Google Scholar] [CrossRef]
- Abubakar, M.A.; Jaroucheh, Z.; Al-Dubai, A.; Liu, X. Blockchain-based identity and authentication scheme for MQTT protocol. In Proceedings of the ICBCT ’21: 2021 The 3rd International Conference on Blockchain Technology, Shanghai, China, 26–28 March 2021. [Google Scholar] [CrossRef]
- Ansey, R.; Kempf, J.; Berzin, O.; Xi, C.; Sheikh, I. Gnomon: Decentralized identifiers for securing 5g iot device registration and software update. In Proceedings of the 2019 IEEE Globecom Workshops (GC Wkshps), Big Island, HI, USA, 9–13 December 2019; IEEE: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Zhang, B.; Shi, R.; Li, X.; Zhang, M. Decentralized identifiers based IoT data trusted collection. Sci. Rep. 2025, 15, 4796. [Google Scholar] [CrossRef]
- Waleed, M.; Skouby, K.E.; Kosta, S. Decentralized identifiers for iot systems: Current status and future vision. In Proceedings of the International Symposium on Distributed Computing and Artificial Intelligence, Guimaraes, Portugal, 12–14 July 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 408–417. [Google Scholar]
- Mazzocca, C.; Acar, A.; Uluagac, S.; Montanari, R. {EVOKE}: Efficient Revocation of Verifiable Credentials in {IoT} Networks. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security 24), Philadelphia, PA, USA, 14–16 August 2024; pp. 1279–1295. [Google Scholar]
- Fotiou, N.; Siris, V.A.; Polyzos, G.C.; Kortesniemi, Y.; Lagutin, D. Capabilities-based access control for IoT devices using Verifiable Credentials. In Proceedings of the 2022 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 22–26 May 2022; IEEE: New York, NY, USA, 2022; pp. 222–228. [Google Scholar]
- Zhang, Z.; Vasavada, V.; Ma, X.; Zhang, L. Dledger: An iot-friendly private distributed ledger system based on dag. arXiv 2019, arXiv:1902.09031. [Google Scholar]
- Xu, Z.; Salehi Shahraki, A.; Rudolph, C. Blockchain-based malicious behaviour management scheme for smart grids. Smart Cities 2023, 6, 3005–3031. [Google Scholar] [CrossRef]
- Mühle, A.; Grüner, A.; Gayvoronskaya, T.; Meinel, C. A survey on essential components of a self-sovereign identity. Comput. Sci. Rev. 2018, 30, 80–86. [Google Scholar] [CrossRef]
- Kulabukhova, N.; Ivashchenko, A.; Tipikin, I.; Minin, I. Self-sovereign identity for IoT devices. In Proceedings of the International Conference on Computational Science and Its Applications, Saint Petersburg, Russia, 1–4 July 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 472–484. [Google Scholar]
- Weingaertner, T.; Camenzind, O. Identity of things: Applying concepts from self sovereign identity to IoT devices. J. Br. Blockchain Assoc. 2021, 4, 1–7. [Google Scholar] [CrossRef] [PubMed]
- Ali, M.S.; Vecchio, M.; Antonelli, F. A Blockchain-Based Framework for IoT Data Monetization Services. Computer/Law J. 2020, 64, 195–210. [Google Scholar] [CrossRef]
- Salehi, A.; Han, R.; Rudolph, C.; Grobler, M. DACP: Enforcing a dynamic access control policy in cross-domain environments. Comput. Netw. 2023, 237, 110049. [Google Scholar] [CrossRef]
- Arshad, J.; Azad, M.A.; Amad, R.; Salah, K.; Alazab, M.; Iqbal, R. A review of performance, energy and privacy of intrusion detection systems for IoT. Electronics 2020, 9, 629. [Google Scholar] [CrossRef]
- Salehi Shahraki, A.; Lauer, H.; Grobler, M.; Sakzad, A.; Rudolph, C. Access control, key management, and trust for emerging wireless body area networks. Sensors 2023, 23, 9856. [Google Scholar] [CrossRef]
- Yzzogh, H.; Kandil, H.; Benaboud, H. A comprehensive overview of AI-driven behavioral analysis for security in Internet of Things. In The Art of Cyber Defense; CRC Press: Boca Raton, FL, USA, 2025; pp. 40–51. [Google Scholar] [CrossRef]
- Trivedi, C.; Rao, U.P.; Parmar, K.; Bhattacharya, P.; Tanwar, S.; Sharma, R. A transformative shift toward blockchainbased IoT environments: Consensus, smart contracts, and future directions. Secur. Priv. 2023, 6, e308. [Google Scholar] [CrossRef]
- Mitra, A.; Bera, B.; Das, A.K.; Jamal, S.S.; You, I. Impact on blockchain-based AI/ML-enabled big data analytics for Cognitive Internet of Things environment. Comput. Commun. 2023, 197, 173–185. [Google Scholar] [CrossRef]
- Ahmed, I.; Zhang, Y.; Jeon, G.; Lin, W.; Khosravi, M.R.; Qi, L. A blockchain-and artificial intelligence-enabled smart IoT framework for sustainable city. Int. J. Intell. Syst. 2022, 37, 6493–6507. [Google Scholar] [CrossRef]
- AlGhamdi, R.; Alassafi, M.O.; Alshdadi, A.A.; Dessouky, M.M.; Ramdan, R.A.; Aboshosha, B.W. Developing trusted IoT healthcare information-based AI and blockchain. Processes 2022, 11, 34. [Google Scholar] [CrossRef]
- Fortino, G.; Messina, F.; Rosaci, D.; Sarné, G.M. Using blockchain in a reputation-based model for grouping agents in the Internet of Things. IEEE Trans. Eng. Manag. 2019, 67, 1231–1243. [Google Scholar] [CrossRef]
- AR, S.; Katiravan, J. Enhancing anomaly detection and prevention in Internet of Things (IoT) using deep neural networks and blockchain based cyber security. Sci. Rep. 2025, 15, 22369. [Google Scholar] [CrossRef] [PubMed]
- Chithanuru, V.; Ramaiah, M. An anomaly detection on blockchain infrastructure using artificial intelligence techniques: Challenges and future directions–A review. Concurr. Comput. Pract. Exp. 2023, 35, e7724. [Google Scholar] [CrossRef]
- Maurya, V.; Rishiwal, V.; Yadav, M.; Jat, D.S.; Agarwal, U.; Verma, V.R. Blockchain-Powered Solution to Safeguard IoT Devices Against Attacks. In Proceedings of the 2023 International Conference on Emerging Trends in Networks and Computer Communications (ETNCC), Windhoek, Namibia, 16–18 August 2023. [Google Scholar] [CrossRef]
- Imad, B.; Anass, S.; Khalid, C.; El-Mehdi, A. SSHCEth: Secure Smart Home Communications based on Ethereum Blockchain and Smart Contract. In Proceedings of the GLOBECOM 2023—2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).