1. Introduction
The rapid growth of devices on the Internet of Things (IoT), ranging from wearables to industrial sensors, has revolutionised data-driven systems. However, this expansion has introduced significant challenges in balancing security requirements with strict resource constraints. IoT devices typically operate in energy-limited environments, making the computational overhead of cryptographic operations a central concern. Despite limited resources, these devices routinely process sensitive data, necessitating robust security protocols, particularly those that ensure integrity and authentication [
1,
2,
3].
Among the most widely used cryptographic primitives in IoT, SHA-256 has long been the default to ensure data integrity. However, with increasing concerns over its long-term resilience, particularly in the face of quantum threats, SHA-3 has emerged as a promising alternative. SHA-3, and in particular the KangarooTwelve (K12) variant, offers flexibility through extendable outputs and a fundamentally different construction based on sponge functions. However, the energy and computational implications of adopting SHA-3 in constrained environments remain underexplored [
4].
Although prior work has investigated the performance of SHA-256 and SHA-3 on embedded platforms, these studies often rely on hardware acceleration, focus on a single mote type, or omit SHA-3 variants such as KangarooTwelve. Furthermore, variations in simulation conditions, such as inconsistent duty cycling protocols, make direct comparisons difficult.
This paper addresses these gaps through a uniform software-only evaluation of SHA-256 and SHA-3 (K12) on three widely used IoT devices representing distinct hardware classes: Sky Mote (legacy), Z1 Mote (mid-tier), and Wismote (modern) [
5]. Using Contiki 3.0 and the Cooja simulator, we evaluated both memory usage and power consumption under identical conditions, including a consistent radio duty cycling configuration (ContikiMAC) in all experiments. The results reveal that while SHA-3 (K12) significantly increases the energy demands on legacy platforms, its cost is more manageable on modern hardware, making it a viable option for high-security deployments in capable IoT nodes.
The experimental setup involves modifying the standard RPL-UDP example in Contiki to include SHA-256 or SHA-3 hashing of payload data at the source node before transmission. Energy consumption and memory footprint are analysed for each hashing method, compared to a non-cryptographic baseline. All tests are performed using software-only implementations to reflect common deployment conditions in Contiki-based systems.
By isolating the energy costs of cryptographic hashing and avoiding network-related variability, this study provides reproducible and directly comparable results across hardware generations. It aims to offer practical guidance to IoT developers and security architects in selecting cryptographic mechanisms that balance energy constraints with long-term security goals.
The remainder of this paper is structured as follows.
Section 1.1 introduces the cryptographic algorithms evaluated and the simulation tools used.
Section 2 reviews the relevant literature and highlights how our study extends existing work.
Section 3 outlines the design and methodology of the experiment.
Section 4 presents the results, including memory and power measurements.
Section 5 discusses the implications and offers directions for future research.
1.1. Hashing SHA256/SHA3
SHA-2 was introduced in 2001 and officially standardised by the National Institute of Standards and Technology (NIST) in August 2002 as FIPS PUB 180-2, offering stronger security and a longer hash output than its predecessor [
6]. Later, SHA-3, based on the Keccak algorithm, was announced as the winner of the NIST hash function competition on 2 October 2012, and formally standardised in August 2015 as FIPS 202 [
7].
In the Internet of Things (IoT) landscape, SHA-256 has long been a cornerstone of security, ensuring data integrity and authentication in resource-constrained environments [
8]. It plays a critical role in firmware security, communication protection, and device authentication in low-power IoT networks. Many IoT security frameworks rely on SHA-256 for cryptographic hashing, much like blockchain technology, which uses it to safeguard transactions and maintain immutable records [
9].
SHA-3 takes a fundamentally different approach from SHA-2, particularly in its algorithm and structural design. While SHA-2 is built on the Merkle–Damgård construction, which processes data in fixed-size blocks using linear operations, SHA-3 uses the Keccak algorithm and a sponge construction. This allows SHA-3 to dynamically absorb and process data before squeezing out the final hash, offering greater flexibility in security and output size.
Both SHA-2 and SHA-3 provide multiple fixed-length hash function variants, including SHA-224, SHA-256, SHA-384, and SHA-512. However, SHA-3 introduces extendable output functions (XOFs), such as SHAKE128 and SHAKE256, which allow the generation of hashes of variable length. This adaptability makes SHA-3 particularly useful for applications that require flexible output sizes, such as key derivation functions and cryptographic protocols. Unlike SHA-2, which always produces a fixed-length output, SHA-3’s sponge construction enables a more versatile implementation, where hash lengths can be adjusted as needed.
However, this flexibility comes with trade-offs. For short input messages such as the 128-bit payloads used in this study, the sponge construction of SHA-3 (K12) may incur greater computational overhead due to its absorb–pad–squeeze process. While both SHA-256 and SHA-3 (K12) were configured to produce fixed 256-bit digests for consistency, it is worth noting that longer or variable-length outputs (common in MACs or key derivation) would amplify the energy cost on resource-constrained platforms. These performance implications, while not the focus of this work, are relevant for real-world deployment scenarios.
Although SHA-256 remains widely used and secure against practical attacks, recent discussions with NIST have raised concerns about its long-term resilience [
10,
11]. The growing potential of quantum computing and evolving cryptographic threats suggest that the security margin of SHA-256 may decrease with time. This presents a significant challenge for IoT security, where cryptographic solutions must be lightweight and robust. As a result, the shift to postquantum-resistant solutions such as SHA-3 is becoming increasingly important, ensuring future-proof protection for sensitive IoT data and securing systems against evolving threats [
12].
While both SHA-256 and SHA-3 (K12) currently offer strong collision resistance, SHA-3 (K12) benefits from a newer design based on sponge construction, which provides improved resistance to length-extension attacks and other structural vulnerabilities inherent to Merkle–Damgård-based functions such as SHA-256. Moreover, SHA-3 (K12) is considered more robust to emerging quantum threats, offering a higher security margin in future IoT deployments [
13]. This additional security comes at a computational and energy cost, particularly important to resource-constrained environments, but may be justified in high-integrity or long-lifespan IoT scenarios where future proofing is critical.
1.2. Contiki Cooja Simulator
Contiki 3.0, a lightweight operating system specifically designed for devices with limited resources, provides a solid foundation for the development of applications in IoT and wireless sensor networks [
14]. Contiki’s event-driven kernel is engineered for resource-constrained environments, prioritising energy efficiency and real-time responsiveness. The kernel design facilitates rapid reaction to external stimuli while minimising power consumption, a critical attribute for energy-sensitive applications [
15]. The multithreading capabilities enable concurrent task execution within a process, thereby enhancing system responsiveness and optimising the use of limited computational resources. This architecture is particularly advantageous for applications that require low-latency performance and extended operational lifetimes.
To facilitate network communication, Contiki incorporates a lightweight TCP/IP stack known as uIP. This stack is optimised for resource-constrained devices and provides essential networking functionalities, enabling seamless integration with existing network infrastructure.
By combining these features, Contiki offers a comprehensive and efficient platform for building applications that operate on resource-limited devices. Its lightweight nature, coupled with its powerful capabilities, makes it an ideal choice for developers seeking to create innovative and scalable IoT solutions.
Cooja, a versatile simulation environment specifically designed for the Contiki operating system, provides developers with a powerful tool to design, test, and deploy applications on devices with limited resources [
16]. Its application simulation capabilities enable developers to execute and evaluate applications without the need for physical hardware, significantly accelerating the development process.
To facilitate seamless integration with real-world devices, Cooja leverages the Java Native Interface (JNI). This interface allows simulated applications to run on actual sensor nodes without requiring modifications, enabling a smooth transition from development to deployment. Additionally, Cooja’s support for multiple hardware platforms ensures its compatibility with a wide range of devices, enabling the simulation of heterogeneous networks and diverse IoT scenarios.
1.3. Motes
The implementation focused on the Sky, Z1, and Wismote motes, given their widespread use in Contiki Cooja.
The Tmote Sky node is one of the earliest and most widely used wireless sensor network (WSN) platforms, widely adopted for IoT research and development due to its low power consumption and compact form factor [
17]. Featuring an MSP430F1611 microcontroller with limited RAM and processing power, it serves as an ideal benchmark for evaluating cryptographic overhead on older, highly resource-constrained devices. Its minimalist design and ease of use make it particularly well suited for initial prototyping and experimentation. However, these constrained resources pose a significant challenge when implementing computationally intensive algorithms such as SHA-256. Despite its ageing hardware, while Sky Mote remains a valuable tool for educational purposes and protocol testing within simulated environments, its role in real-world IoT applications has diminished in favour of more advanced hardware platforms that better meet the demands of current IoT needs.
The Z1 Mote, a more recent addition to the Tmote family, offers a significant performance boost over its predecessors, making it a versatile development platform for WSN [
18]. Although it inherits many of the characteristics of the Tmote Sky, including low power consumption and a compact form factor, it introduces several hardware enhancements that improve its computational capabilities. Equipped with an MSP430F2617 microcontroller, the Z1 features 8 KB of RAM (slightly less than Sky Mote’s 10 KB) but compensates with increased ROM (96 KB vs. 48 KB in Sky Mote). These enhancements make it better suited for handling computationally intensive cryptographic operations, such as SHA-256, even within resource-constrained environments [
19]. As a mid-range IoT device, the Z1 Mote is often deployed in industrial monitoring, environmental sensing, and other low-power IoT applications, where achieving a balance between performance and energy efficiency is critical.
The Wismote MSP430F5437, part of the Tmote family, shares key design elements with the Tmote Sky and Z1 Mote, particularly in terms of form factor and power efficiency [
20,
21]. However, it introduces distinct architectural differences, such as enhanced processing capabilities, expanded memory allocation, and improved peripheral support, making it better suited for computationally intensive tasks such as SHA-256 implementation. These hardware differences significantly impact execution speed, energy consumption, and overall feasibility within resource-constrained IoT environments [
22]. As a more advanced mote, the Wismote features an MSP430F5437 microcontroller with 16 KB RAM and 128 KB Flash memory, enabling it to handle more demanding cryptographic and data processing operations. Due to its improved hardware, it represents modern high-end IoT nodes, often deployed in energy-aware IoT applications, where optimising power consumption is a critical design factor.
The mote parameters listed in
Table 1 were essential for interpreting the analysis results.
These three motes collectively provide a progression of IoT hardware generations, from older, highly constrained nodes (Sky Mote) to more modern, capable devices (Wismote). They are representative of broader IoT device classes, including
Legacy IoT Devices—Ultralow power, simple processing units still in deployment;
Mid-tier IoT Devices—Moderate computational capabilities with constrained energy budgets;
High-end IoT Devices—More memory and processing power, suitable for security-intensive tasks.
By selecting these motes, this study ensures a comprehensive analysis of cryptographic energy trade-offs across a range of real-world IoT deployments. This helps researchers and engineers understand how these hashing algorithms affect different classes of devices, helping in future optimisations and security design choices for IoT systems.
2. Related Work
In the study [
23], Bertoni et al. introduced KangarooTwelve as a highly performance-expandable output hash function designed to outperform SHA-3 and SHAKE variants in software environments. The function leverages a reduced round (12 round) Keccak-p permutation and a Sakura-compatible tree hashing mode to achieve high throughput with minimal computational overhead, especially for large messages. Although the original work focusses on performance on general-purpose processors and does not directly address embedded or IoT platforms, its reduced efficiency characteristics, extendable output, and compatibility with low-memory implementations make it a promising candidate for constrained environments. Unlike previous work, which benchmarks SHA-3 (K12) primarily in server class or desktop scenarios, our study evaluates its feasibility on low-power IoT devices through empirical analysis of memory and energy consumption in Contiki OS, demonstrating its trade-offs and practical viability in constrained deployments.
In their study [
24], Mufidah et al. present a comprehensive empirical evaluation of lightweight cryptographic hash functions, specifically SHAKE128, SHAKE256, BLAKE2s, SHA-256, SHA3-256, SipHash, and xxHash on the Arduino Uno platform. Their analysis includes performance metrics such as throughput, memory usage, and the avalanche effect, offering a detailed comparison across a range of data sizes. BLAKE2s is identified as a balanced performer, combining efficient memory usage, robust avalanche properties, and strong throughput, while xxHash and SipHash achieve high throughput at the expense of weaker avalanche effects. In particular, the study emphasises the practical implications of memory and performance trade-offs in constrained devices and calls for standardised evaluation frameworks to assess hash function robustness in real-world scenarios. While their work highlights function-specific efficiencies, it does not explore the implications of energy costs in heterogeneous IoT hardware or within network settings. In contrast, our study specifically focusses on comparing SHA-256 and SHA-3 (K12), evaluating their energy and memory impact over three generations of Contiki-based IoT motes in a unified simulation environment.
In the study of [
25], Dalwadi et al. examine the power consumption of various wireless motes in IoT applications, highlighting the critical role of energy efficiency in battery-powered devices. Using the Cooja simulator, the research evaluates motes such as Sky, Z1, Wismote, and EXP5438, comparing their energy consumption during data transmission and reception. The experiments, conducted on Contiki OS with a unicast communication setup, use the powertrace tool to monitor CPU, TX, RX, and LPM usage. The results reveal significant differences in power consumption, largely influenced by the microcontroller architectures of the motes, despite all using the CC2420 transceiver.
Beyond hardware differences, the study underscores the importance of choosing energy-efficient motes and communication protocols such as ZigBee, Bluetooth, and BLE. It also explores challenges in scalability and interoperability within IoT environments, stressing the need for standardised protocols to ensure seamless integration. Ultimately, optimising power consumption is vital for extending device lifespans and improving overall system efficiency in real-world IoT deployments.
While previous research has explored the performance of cryptographic algorithms in IoT settings, much of it relies on hardware-accelerated platforms, targets a single device type, or evaluates only the standard SHA3-256 variant. These limitations reduce the applicability of results to real-world deployments, where software-only hashing is often necessary due to cost and hardware constraints. In contrast, our study provides a uniform software-only evaluation of SHA-256 and the less commonly benchmarked variant SHA-3 (K12), across three generations of widely used IoT motes (Sky, Z1, and Wismote). By maintaining consistent duty cycling and implementation conditions across all devices, this work isolates cryptographic overhead and offers a practical assessment of hash function viability for constrained IoT deployments lacking dedicated acceleration.
While existing studies often benchmark SHA-3 variants such as SHAKE128 or SHA3-256 on microcontrollers, they typically focus on a single hardware platform, use hardware acceleration, or omit energy profiling entirely. A summary of related work is presented in
Table 2. This study is the first to provide a software-only cross-generational comparison of SHA-256 and SHA-3 (K12) under uniform conditions on Sky, Z1, and Wismote motes.
Collectively, these studies underscore the need for a consistent software-only benchmarking approach across hardware generations. Our work responds to this need by isolating the hashing overhead under standardised conditions in Contiki.
3. Proposal
To compare the energy and memory implications of SHA-256 and SHA-3 (K12), we implemented both hashing functions on three representative IoT platforms: Sky, Z1, and Wismote. All experiments were carried out using the Contiki 3.0 operating system within the Cooja simulator. ContikiMAC (Medium Access Control protocol) was used for radio duty cycling across all devices to ensure consistent and realistic energy behaviour. User Datagram Protocol (UDP) communication was employed in a client–server topology, representative of typical IoT network traffic.
Each client node generated a 128-bit (16-byte) random input, which was then hashed using either SHA-256 or SHA-3 (K12). This input size reflects typical sensor data payloads in real-world IoT deployments. The resulting digest was embedded in a UDP packet and transmitted to a sink node. Each test run involved 100 such transmissions, with a new hash computed for every packet. Energest was used to measure the time spent in key power states: central processing unit (CPU), transmit (TX), receive (RX), and low power mode (LPM). Total energy consumption was calculated using Equation (
1), applying the standard voltage and current values listed for each mote in
Table 1.
All hashing was conducted in software, using custom cryptographic libraries for SHA-256 and SHA-3 (K12) integrated into Contiki 3.0. The SHA-3 (K12) implementation was adapted from the Keccak Code Package to meet Contiki’s memory and runtime constraints. These libraries were manually ported, tested, and compiled into the firmware for each mote.
To isolate the energy cost of cryptographic processing, we disabled non-essential background processes that could interfere with measurement accuracy. These included RPL routing, neighbour discovery, sensor polling, and diagnostic output. However, ContikiMAC and its required timers and MAC-layer functions were fully retained, ensuring consistent and realistic radio duty cycling across all motes. Debug output confirmed that no unintended processes were triggered at runtime.
Each mote operated in a minimal UDP-based client–server configuration, performing only the following operations per packet:
A random 128-bit input is generated.
The input is hashed with either SHA-256 or SHA-3 (K12).
The resulting digest is transmitted into a unicast UDP packet.
Although input generation contributes to minimal CPU load, this setup reflects common IoT sensing patterns. Energest was used to log power state transitions (CPU, TX, RX, LPM), enabling fine-grained energy profiling.
ContikiMAC served as the standard radio duty cycling (RDC) configuration for all scenarios (baseline, SHA-256, SHA-3 (K12)). Notably, the Wismote platform defaults to NullRDC (an always-on radio), which significantly inflates RX power consumption. To ensure comparability, Wismote was explicitly configured to use ContikiMAC, aligning its transmission and reception behaviour with Sky and Z1 [
29]. While ContikiMAC introduces packet strobing that affects TX characteristics, it remains consistent across all experiments, ensuring that observed power differences are attributable to the cryptographic workload not network behaviour.
4. Results
4.1. Memory Requirement Analysis
Table 3 presents the memory footprint (in bytes) for the cryptographic implementations of the Read-Only Memory (ROM), Random Access Memory (RAM) and Block Started by Symbol (BSS) segment in the three IoT motes. The results indicate that both SHA-256 and SHA-3 (K12) increase the use of ROM, and SHA-3 (K12) requires slightly less memory overall. On average, SHA-3 (K12) increases ROM by 4.54%, while SHA-256 results in a higher increase of 7.68%. In contrast, RAM usage, reflected in the Block-Started segment (BSS), which stores uninitialised global and static variables, sees a more significant impact by SHA-3 (K12), with an average increase of 3.57%, compared to just 0.1% for SHA-256.
These findings highlight that while SHA-3 (K12) is a feasible alternative to SHA-256, its implementation in resource-limited IoT devices should be carefully assessed, particularly with respect to the available RAM and ROM capacity.
4.2. Node Power Usage
The Energest module in Contiki OS provides a comprehensive mechanism to analyse power consumption using hardware timers to measure the operational time of key components of the system [
30]. Tracking four primary metrics: the time the central processing unit (CPU) remains active, the duration the CPU spends in low power mode (LPM), the time spent transmitting data over the radio (TX), and the time spent listening for incoming transmissions (RX).
Through continuous monitoring of these parameters throughout the simulation, variations in power consumption were accurately recorded and analysed. Using the parameters described in
Table 1, we were able to calculate the energy consumption for each scenario.
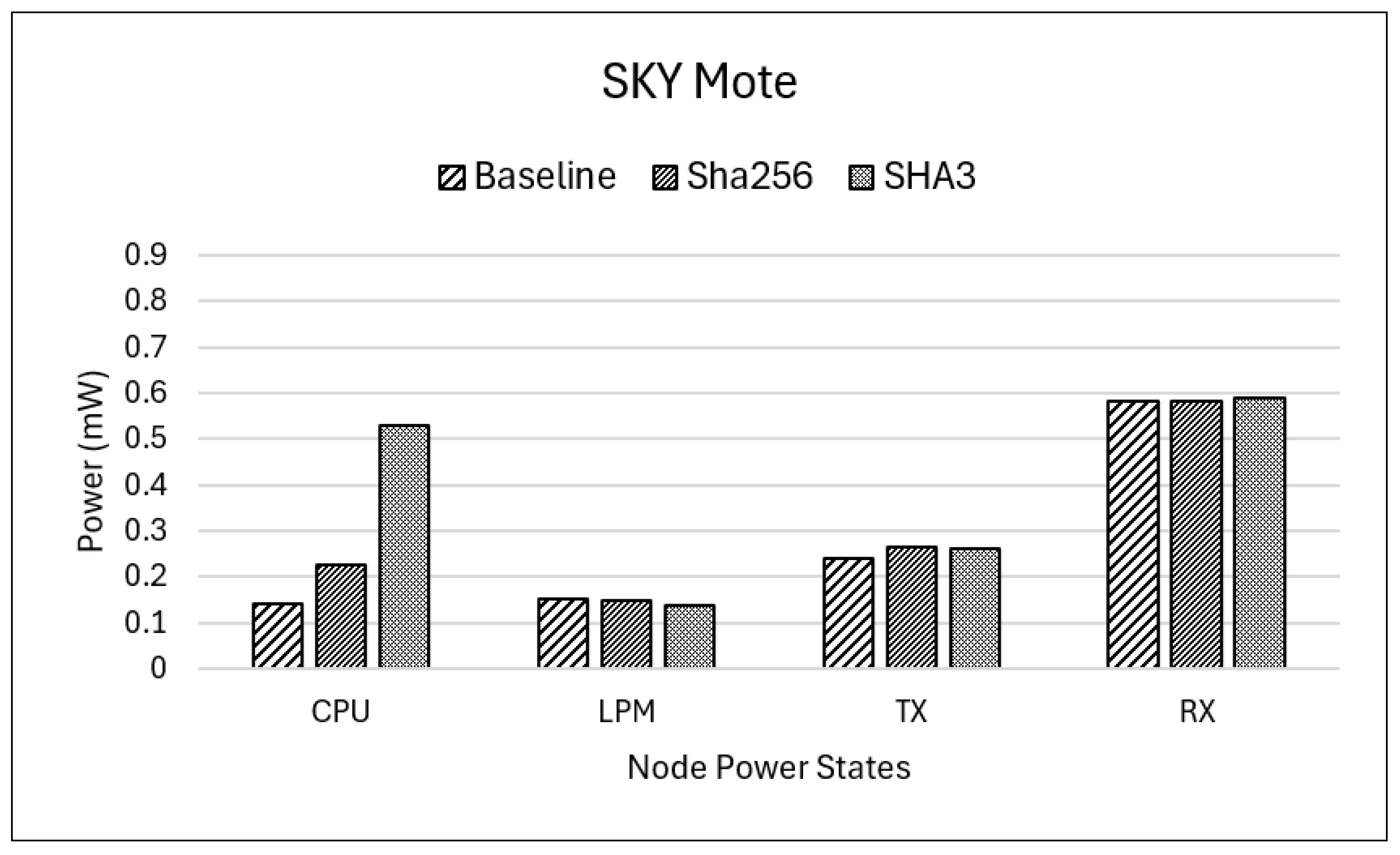
Both
Table 4 and
Figure 1 present the power consumption of the Sky Mote in different operational states, comparing the baseline scenario with the implementations of SHA-256 and SHA-3 (K12). Each data point represents the mean of ten simulation runs, with standard deviations included for the baseline configuration to indicate consistency across trials. The results show that while SHA-256 significantly increases CPU power consumption by 60%, SHA-3 (K12) has a much greater impact, increasing CPU power usage by 274% compared to the baseline. This substantial increase in processing demand results in an overall increase in power consumption of 36.7% for SHA-3 (K12), compared to 9.9% for SHA-256.
Despite these differences, LPM consumption remains relatively stable, showing only minor reductions across both cryptographic implementations. Similarly, the power usage of TX and RX exhibits minimal variations, suggesting that the main contributor to the increase in energy demand is the computational overhead of the hashing operations. The low standard deviation values for the baseline runs (e.g., 0.00095 mW for CPU, 0.00100 mW for LPM) demonstrate good repeatability of the simulation conditions, reinforcing the reliability of the comparative analysis. These findings highlight that while SHA-3 (K12) provides stronger cryptographic security, its significantly higher power consumption makes it a less suitable option for resource-constrained IoT devices such as the Sky Mote.
Table 5 and
Figure 2 present the power consumption of the Z1 Mote in different operational states, comparing the baseline scenario with the implementations of SHA-256 and SHA-3 (K12). Each measurement reflects the mean of ten simulation runs, with standard deviations provided for the baseline configuration. The results show that SHA-256 increases the CPU power consumption by 40%, leading to an overall power increase of 22%. In contrast, SHA-3 (K12) introduces a much greater computational load, with CPU usage increasing by 216% relative to the baseline. This results in a dramatic overall energy increase of 201%, making SHA-3 (K12) substantially more power intensive than SHA-256.
Although LPM power remains relatively stable for SHA-256, SHA-3 (K12) causes a slight decrease as a result of the mote spending more time in active states. Additionally, while SHA-3 (K12) significantly increases CPU power consumption more than doubling that of SHA-256 the TX and RX power consumption remain largely comparable across all configurations. This suggests that the overhead introduced by SHA-3 (K12) is primarily computational rather than communicative, with a negligible additional burden on the radio module.
Despite the improved hardware of the Z1 over the Sky Mote, these findings indicate that SHA-3 (K12)’s energy demands nearly triple the total power consumption compared to the baseline. Baseline measurements showed low variability (e.g., CPU standard deviation: 0.00010 mW; overall: 0.00203 mW), reinforcing the reliability of the comparative results. As such, while SHA-256 already incurs a notable energy cost, the adoption of SHA-3 (K12) on mid-range IoT devices such as the Z1 Mote should be carefully considered, particularly in battery-constrained deployments.
Table 6 and
Figure 3 present the power consumption of the Wismote in different operating states, comparing the baseline scenario with the implementations of SHA-256 and SHA-3 (K12). Each value represents the mean of ten simulation runs, and the corresponding standard deviations for the baseline configuration are provided to assess measurement consistency. The results indicate that CPU power consumption increases by 24% with SHA-256 and by 126% with SHA-3 (K12), reflecting the computational overhead introduced by cryptographic hashing. Despite these increases, the overall energy impact remains moderate, with SHA-256 increasing total consumption by 4.5% and SHA-3 (K12) by 8.6% compared to baseline.
The Wismote’s LPM power usage remains largely stable across all configurations, showing only a 1.9% decrease with SHA-3 (K12). TX power increases by approximately 10% for both hash functions, while RX remains effectively unchanged. These results suggest that the Wismote’s more advanced hardware mitigates the energy cost of SHA-3 (K12) far more effectively than the other motes evaluated.
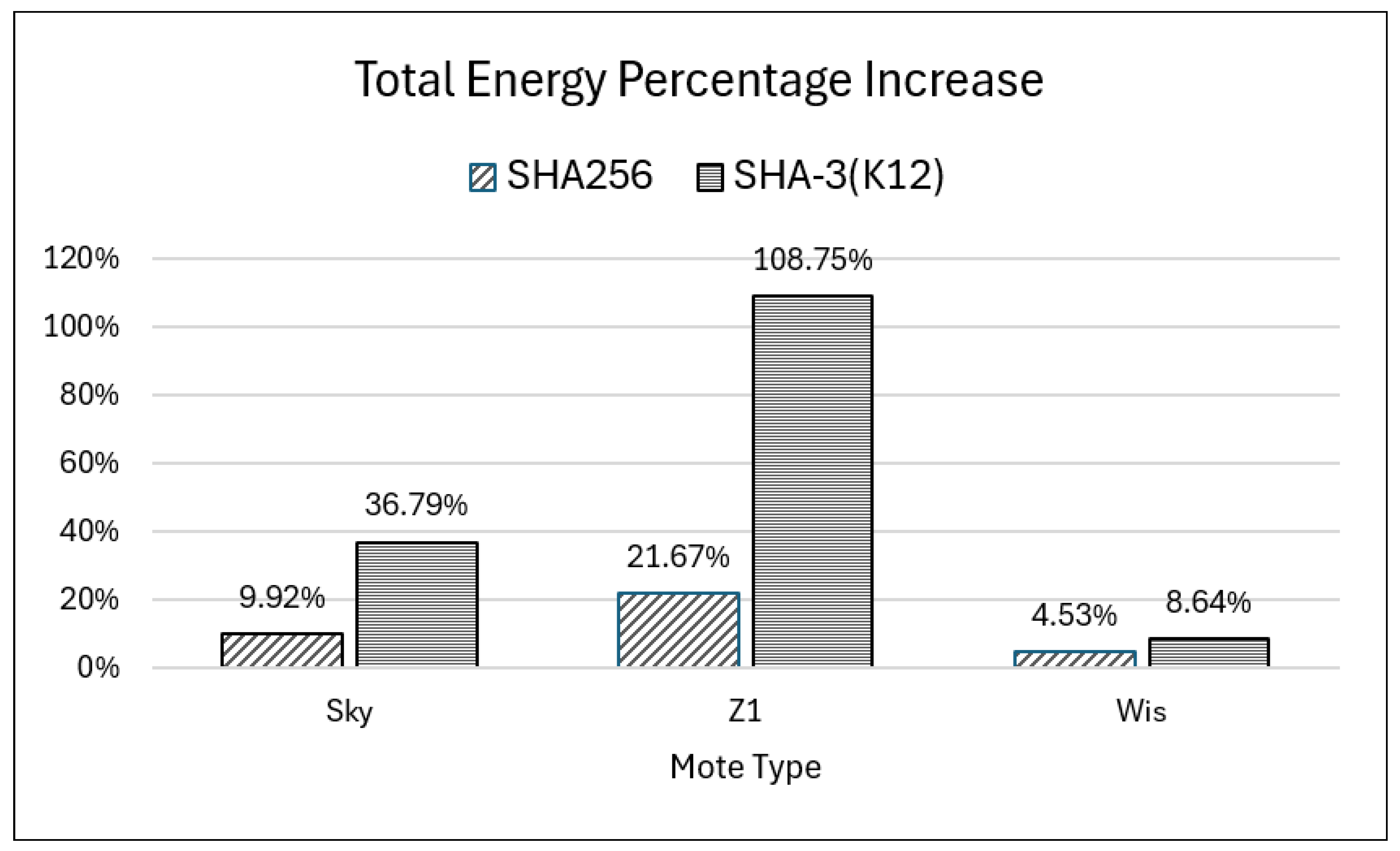
To further highlight the comparative impact of hashing,
Figure 4 presents the percentage increase in total energy consumption for SHA-256 and SHA-3 (K12) across the three motes. This visual summary reinforces the measured data, clearly showing how SHA-3 (K12) imposes a disproportionately higher energy cost on legacy and mid-tier platforms, while remaining more manageable on modern devices like Wismote.
Standard deviation values for the baseline scenario were consistently low (e.g., CPU 0.00087 mW, Overall 0.00203 mW), indicating strong consistency across the ten repeated runs and supporting the reliability of the averaged results. These findings support the conclusion that advanced IoT platforms can accommodate stronger cryptographic functions like SHA-3 (K12) without significantly compromising energy efficiency.
5. Conclusions
This paper presents a comparative evaluation of SHA-256 and SHA-3 (K12) over three generations of Contiki-compatible IoT motes: Sky, Z1, and Wismote. By implementing a consistent, software-only hashing workload under uniform radio duty cycling, we isolated the energy and memory costs of each hash function across varying hardware constraints. The results show that while SHA-256 remains more efficient on legacy platforms such as Sky, SHA-3 (K12) demonstrates acceptable performance on more capable motes like Wismote, suggesting its viability for deployments where extended hash outputs or sponge-based construction provided by SHA-3 (K12) are desirable.
In contrast to prior studies that assess SHA-3 using general-purpose processors or hardware-accelerated designs often achieving multi-gigabit throughput under ideal conditions, this work aims to provide a practical view of cryptographic overhead in real-world, software-constrained IoT environments. Our findings offer developers a clearer understanding of the trade-offs involved in hash function selection, helping to guide protocol and hardware choices in resource-sensitive deployments.
To our knowledge, this is the first side-by-side evaluation of SHA-256 and SHA-3 (K12) implemented in pure software across three representative IoT motes using Contiki OS. The findings offer unique insight into the trade-offs of deploying post-quantum hash functions in real-world, constrained environments.
To complement the current simulation-based results, future experiments will incorporate direct energy measurements on physical hardware using digital instrumentation. This will validate the simulation-derived energy profiles and ensure real-world applicability. Further investigation into the interaction between hashing performance and system-level constraints, such as duty cycling policies and radio buffer contention, could also yield valuable insights for optimising security-efficiency trade-offs in operational IoT networks.
Author Contributions
Conceptualisation, I.B.; methodology, I.B.; software, I.B.; validation, I.B.; investigation, I.B.; resources, I.B.; data curation, I.B.; writing—original draft preparation, I.B.; writing—review and editing, I.W., B.G. and C.T.; supervision, I.W., B.G. and G.R.; project administration, I.B.; All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data that support the findings of this study are available from the corresponding author upon reasonable request.
Acknowledgments
During the preparation of this manuscript, the authors used “ChatGPT-4o” and “Writefull for Overleaf Premium” to assist with spell-checking, grammar corrections, and suggesting alternative wording to improve clarity and readability. The authors have reviewed and edited the output and take full responsibility for the content of this publication.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| BSS | Block Started by Symbol |
| CPU | Central Processing Unit |
| FIPS | Federal Information Processing Standards |
| IoT | Internet of Things |
| JNI | Java Native Interface |
| K12 | KangarooTwelve |
| LBR | Low-power and Lossy Network Border Router |
| LD | Linear Dichroism |
| LLN | Low-power and Lossy Network |
| LPM | Low Power Mode |
| MAC | Medium Access Control |
| NIST | National Institute of Standards and Technology |
| OS | Operating System |
| RAM | Random Access Memory |
| RDC | Radio Duty Cycling |
| ROM | Read-Only Memory |
| RPL | Routing Protocol for Low-power and Lossy Networks |
| RX | Receive |
| SHA-256 | Secure Hash Algorithm 256-bit |
| SHA-3 | Secure Hash Algorithm 3 |
| SHAKE128 | SHA-3 Extendable Output Function 128-bit |
| SHAKE256 | SHA-3 Extendable Output Function 256-bit |
| TLA | Three-Letter Acronym |
| TX | Transmit |
| UDP | User Datagram Protocol |
| uIP | micro IP (lightweight TCP/IP stack) |
| WSN | Wireless Sensor Network |
| XOF | eXtendable Output Function |
References
- Batalla, J.M.; Mavromoustakis, C.X.; Mastorakis, G.; Xiong, N.N.; Wozniak, J. Adaptive positioning systems based on multiple wireless interfaces for industrial IoT in harsh manufacturing environments. IEEE J. Sel. Areas Commun. 2020, 38, 899–914. [Google Scholar] [CrossRef]
- Nolan, K.E.; Kelly, M.Y.; Nolan, M.; Brady, J.; Guibene, W. Techniques for resilient real-world IoT. In Proceedings of the 2016 International Wireless Communications and Mobile Computing Conference (IWCMC), Paphos, Cyprus, 5–9 September 2016; pp. 222–226. [Google Scholar] [CrossRef]
- Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar]
- Román, R.; Baturone, I. A quantum-resistant and fast secure boot for IoT devices using hash-based signatures and SRAM PUFs. In The Fifth International Conference on Safety and Security with IoT: SaSeIoT 2021; Springer: Berlin/Heidelberg, Germany, 2022; pp. 121–136. [Google Scholar]
- Gaur, R.; Prakash, S. Performance and parametric analysis of IoT motes with different network topologies. In Innovations in Electrical and Electronic Engineering: Proceedings of ICEEE 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 787–805. [Google Scholar]
- National Institute of Standards and Technology (NIST). FIPS PUB 180-4: Secure Hash Standard (SHS); Federal Information Processing Standards Publication: Gaithersburg, MD, USA, 2012. [Google Scholar]
- FIPS PUB 202; Dworkin, M. SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015. [CrossRef]
- Gilbert, H.; Handschuh, H. Security analysis of SHA-256 and sisters. In International Workshop on Selected Areas in Cryptography; Springer: Berlin/Heidelberg, Germany, 2003; pp. 175–193. [Google Scholar]
- Zhai, S.; Yang, Y.; Li, J.; Qiu, C.; Zhao, J. Research on the application of cryptography on the blockchain. J. Phys. Conf. Ser. 2019, 1168, 032077. [Google Scholar] [CrossRef]
- Moody, D.; Perlner, R.; Regenscheid, A.; Robinson, A.; Cooper, D. Transition to Post-Quantum Cryptography Standards; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2024. [Google Scholar]
- Claburn, T. Quantum anxiety sees Australia ban some crypto tech by 2030. The Register, 17 December 2024. Available online: https://www.theregister.com/2024/12/17/australia_dropping_crypto_keys/ (accessed on 13 February 2025).
- Kelsey, J.; Chang, S.J.; Perlner, R. SHA-3 Derived Functions: cSHAKE, KMAC, TupleHash, and ParallelHash; NIST Special Publication: Gaithersburg, MD, USA, 2016; Volume 800, p. 185. [Google Scholar]
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. The Keccak SHA-3 Submission; Submission to NIST (Round 3). 2011. Available online: https://keccak.team/keccak.html (accessed on 21 March 2025).
- Dunkels, A.; Gronvall, B.; Voigt, T. Contiki—A lightweight and flexible operating system for tiny networked sensors. In Proceedings of the 29th Annual IEEE International Conference on Local Computer Networks, Tampa, FL, USA, 16–18 November 2004; IEEE: Piscataway, NJ, USA, 2004; pp. 455–462. [Google Scholar]
- Durmaz, C.; Challenger, M.; Dagdeviren, O.; Kardaş, G. Modelling Contiki-based IoT systems. In Proceedings of the 6th Symposium on Languages, Applications and Technologies (SLATE 2017), Vila do Conde, Portugal, 26–27 June 2017; Schloss Dagstuhl–Leibniz-Zentrum für Informatik: Wadern, Germany, 2017; pp. 5:1–5:8. [Google Scholar]
- Österlind, F. A Sensor Network Simulator for the Contiki OS; Swedish Institute of Computer Science: Stockholm, Sweden, 2006. [Google Scholar]
- The Sensor Network Museum: Projects—Tmote Sky Browse. 2024. Available online: https://www.snm.ethz.ch/snmwiki/Projects/TmoteSky.html (accessed on 25 September 2024).
- Z1 Datasheet v1.0 by Zolertia. 2024. Available online: https://issuu.com/zolertia/docs/z1_datasheet (accessed on 25 September 2024).
- Khan, R.; Mian, A.N. Sustainable IoT sensing applications development through GraphQL-based abstraction layer. Electronics 2020, 9, 564. [Google Scholar] [CrossRef]
- Texas Instruments. SLAS612 Data Sheet|TI.com. 4 February 2025. Available online: https://www.ti.com/document-viewer/msp430f5437/datasheet (accessed on 4 February 2025).
- Texas Instruments. CC2520 Data Sheet, Product Information and Support. 4 February 2025. Available online: https://www.ti.com/product/CC2520 (accessed on 4 February 2025).
- Logix, S. Distinguish Skymote, Z1mote, and Wismote in Cooja. 2024. Available online: https://slogix.in/source-code/contiki-cooja-samples-for-IoT/difference-between-skymote-and-z1mote-and-wismote-in-contiki-cooja-simulation/ (accessed on 19 September 2024).
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G.; Van Keer, R.; Viguier, B. KangarooTwelve: Fast hashing based on Keccak-p. In Applied Cryptography and Network Security, Proceedings of the 16th International Conference, ACNS 2018, Leuven, Belgium, 2–4 July 2018, Proceedings 16; Springer: Berlin/Heidelberg, Germany, 2018; Volume 10892, pp. 400–418. [Google Scholar]
- Mufidah, N.F.; Nuha, H.H. Performance and security analysis of lightweight hash functions in IoT. J. Inform. 2024, 9, 264–270. [Google Scholar] [CrossRef]
- Dalwadi, N.; Padole, M. Performance analysis of wireless motes in IoT. In ICT Analysis and Applications: Proceedings of ICT4SD 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 383–397. [Google Scholar]
- Liu, X.; Zhang, X.; Yang, Y. Efficient hardware implementation of hash algorithm SHA-3 for IoT information security. In Proceedings of the 2024 5th International Seminar on Artificial Intelligence, Networking and Information Technology (AINIT), Nanjing, China, 29–31 March 2024; pp. 368–372. [Google Scholar] [CrossRef]
- Zhang, J.; Sadredini, E. Inhale: Enabling high-performance and energy-efficient in-SRAM cryptographic hash for IoT. In Proceedings of the 41st IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Diego, CA, USA, 29 October–3 November 2022; pp. 1–9. [Google Scholar]
- Özcan, M.M.; Ayaz, B.A.; Karagöz, M.M.; Yolaçan, E. Performance evaluation of SHA-256 and BLAKE2b in proof of work architecture. Eskişehir Türk Dünyası Uygul. AraşTırma Merk. Bilişim Derg. 2022, 3, 60–65. [Google Scholar] [CrossRef]
- Dunkels, A. The ContikiMAC Radio Duty Cycling Protocol, 12th ed.; Swedish Institute of Computer Science: Stockholm, Sweden, 2011; Available online: https://urn.kb.se/resolve?urn=urn:nbn:se:ri:diva-22724 (accessed on 16 February 2025).
- Sabovic, A.; Delgado, C.; Bauwens, J.; De Poorter, E.; Famaey, J. Accurate online energy consumption estimation of IoT devices using Energest. In Advances on Broad-Band Wireless Computing, Communication and Applications; Barolli, L., Hellinckx, P., Enokido, T., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 363–373. [Google Scholar]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).