Abstract
The purpose of this study is to discuss epidemic communication for drones to share information in flight and to develop a wireless system for implementation. Various theoretical studies have been conducted on epidemic communication, but their applications are not clear, so a system that assumes practical use is developed. As the main evaluation items, we analyzed the effect of communication interference between drones on the amount of data transmission, and furthermore, proposed an optimal transmission method depending on the flight speed. In these analysis results, we designed functions to be implemented in drones, developed wireless devices, and confirmed their operation through demonstration tests using actual drones. Based on the results of this research, we succeeded in identifying issues to be addressed in order to implement the system on drones and in developing an epidemic communication system based on the results of demonstration experiments, thereby contributing to the realization of inter-drone communication in the future.
1. Introduction
With the development of the Internet of Things (IoT), objects that were previously not connected to the Internet have been connected. The IoT is used in various fields for communicating and sharing information between objects. The information that is shared includes the data acquired by various sensors. In systems utilizing IoT technology, ad hoc communication methods have long been considered, and protocols such as the ad hoc on-demand distance vector (AODV) and optimized link state routing (OLSR) have been established [1,2,3,4,5]. Ad hoc communication serves as a relay technology between wireless stations, allowing for flexible links to be established and information to be shared among wireless stations. Although the collected information is determined by humans, ad hoc communication is representative of the device-to-device communication technology of the IoT.
As a special case in IoT, communication applications that involve extremely long delays, ranging from seconds to hours or more, are emerging. Examples include the interplanetary Internet (IPN) for communication between planets or space stations, underwater communication for environmental monitoring, and communication between sensors attached to animals. These applications face challenging conditions, including intermittent connections between planned and unplanned communication links. Traditionally, communication systems have not been designed to address these conditions.
Therefore, the traditional framework of Internet communication does not consider scenarios where vehicles or individuals physically move to locations without an established wired or wireless infrastructure to transport information. Delay-tolerant networking (DTN) addresses the challenges posed by the constraints of traditional communication technologies in such scenarios [6,7,8,9,10,11,12,13,14,15,16,17,18,19,20].
A communication method related to DTN is called epidemic communication. Epidemic communication is useful for constructing more complex ad hoc network environments than the conventional ad hoc construction methods. For instance, the conventional ad hoc wireless networks may not always form a multi-hop wireless route between the source and destination nodes. In scenarios where the nodes frequently move and the spatial relationships among the moving nodes performing as relays between source and destination nodes as well as the availability of wireless links between each node vary, routing paths may not always exist between the source and destination nodes. Moreover, in situations with a low node density, such occurrences are more likely and multi-hop wireless communication may not function effectively. The theoretical framework of epidemic communication, in which information is shared among nodes to propagate as an epidemic, has been recently applied for analyses, such as in predicting the spread of the novel coronavirus infection (COVID-19). However, to date, the practical utilization of this communication method in communication services has not resulted in many optimal deployment methods.
Therefore, we propose a specific application of epidemic communication for mobile devices such as robots and drones. Robots and drones have been rapidly adopted in various practical applications, and the control technologies for these devices have been standardized. For example, a robot operating system is an open-source robotics framework middleware that facilitates various R&D activities and practical applications to satisfy specific goals and requirements [21,22,23]. Robots and drones intended for deployment in disaster-stricken areas are designed to perform activities remotely, replace human labor, and collaborate with other robots and drones via information sharing. For example, drones are used for pollination tasks in agriculture and for transmitting data concerning instructions and flight control information [14,24,25]. In systems in which multiple robots or drones collaborate, accurate sharing of information among them is essential. In practical applications, related studies have utilized the sharing of environmental information between drones, as shown in Figure 1a. This shared information is then used for autonomous flight control. Additionally, the sharing of sensor data collected by robots has been employed to create maps [26,27,28]. In environments where the conditions for wireless communication are not ideal, epidemic communication allows nodes with information (wireless stations) to communicate autonomously and carry information by pas. Considering this background, we designed a wireless device to implement epidemic communication for drones and developed an epidemic communication system. We designed the system for practical use and considered the interference between wireless devices, the optimization of communication areas, and the amount of transmitted data.
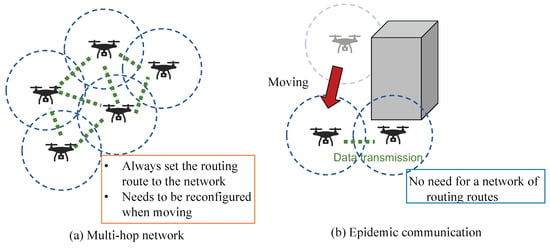
Figure 1.
Examples of autonomous networks with robots.
Epidemic communication is characterized by the spread of infection without the construction of routing paths. Common wireless network evaluation seeks end-to-end throughput and latency performance. Since radio waves are widely radiated, it is important to improve communication efficiency by expanding the communication area.
However, since epidemic communication is carried out locally with many simultaneous connections, the evaluation of the entire network is not important, i.e., there is not always the connection terminals, but data are stored in a buffer and moved, and data are transmitted (infected) when the connection terminals appear. Therefore, communication opportunities occur locally.
And, for localized communication, radio wave emissions should be kept as small as possible to minimize radio interference to the surroundings. Ideally, only infected parties passing by should be able to communicate with each other, and radio waves should not reach a large perimeter. Therefore, in this study, we set up a restricted transmission area for local transmission, evaluated the amount of data (amount of infection) that a radio station can transmit while moving within the restricted transmission area, and developed an implementation of the results.
The contribution of this study is to discuss epidemic communication for drones to share information in flight, and thereby develop the wireless system that assumes implementation.
- #1
- The system is designed for practical use, since there are various theoretical studies on epidemic communication, but their applications are not clear.
- #2
- The main problem solved is to analyze the effect of between-drone interference on the infection rate (data transmission rate), and to propose the optimal transmission method according to the flight speed.
- #3
- Based on the results of these analyses, we designed functions to be implemented in drones, developed wireless devices, and confirmed their operation through demonstration tests.
In the results of this study, we successfully extract issues to be addressed for implementation on drones and developed a wireless system based on the results of demonstration experiments, contributing to the realization of between-drone communications in the future.
The remainder of this paper is organized as follows. In Section 2, we introduce related work on epidemic communication and discuss its implementation challenges. Section 3 describes the implementation method of epidemic communication and presents the interference models and analysis results for the transmitted data volume. Finally, in Section 4, we evaluate the proposed model based on the experimental results and recorded video.
2. Related Works and Issues
Epidemic communication differs from conventional mobile communication systems in that it is an ad hoc network based on multi-hop transmission, similar to a mobile communication network without any infrastructure. Multi-hop transmission involves communication through a connected multi-hop wireless route between the source and destination nodes. With epidemic communication, this is further adapted by enabling direct wireless communication between mobile nodes, and spatially spreading information through their movement. That is, epidemic communication utilizes a technique known as information floating, in which direct wireless communication is allowed only in specific regions, thereby preventing uncontrolled information diffusion while conveying information to unspecified nodes in the designated area [7,8]. These methods leverage the capability of exchanging information between moving entities and disseminating information through their movement, making them suitable communication techniques for autonomously moving nodes, such as robots and drones. Figure 2 illustrates the operation. Nodes with information data (transmitting nodes) move consistently while retaining the data. If communication-capable nodes are in the vicinity of other nodes after moving, these nodes become the receiving nodes, and the transmitting nodes send data to them. Subsequently, the receiving nodes that receive the information then move, and upon encountering another node, repeat the transmission process. In essence, nodes carry and disseminate information, spreading it like an infection through repeated transfers. The advantage of using epidemic communication for such flower searches is that information data can be collected even in complex flight environments. For example, if there are obstacles such as leaves or stems, direct communication may not be able to transmit properly due to interference or diffraction. However, with epidemic communication, multiple drones can relay information data in such a way that they can avoid the obstacles and go around them, thus creating dynamic and flexible networks. Epidemic communication faces the following challenges.
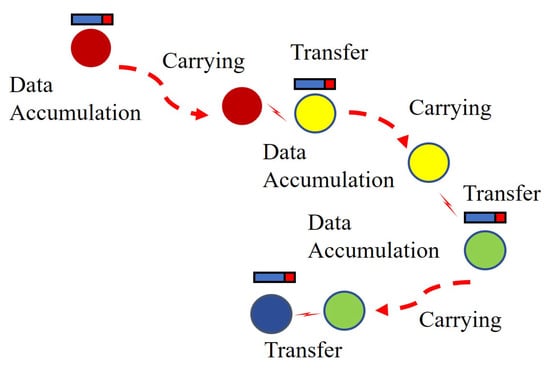
Figure 2.
Example of epidemic communication in action.
- (A)
- Numerous theoretical studies have been conducted and various technical applications have been proposed. However, few examples of actual system implementations have been realized. The requirement for wireless devices with various functions such as relaying, connecting, disconnecting, and storing data is a challenge for construction of these systems.
- (B)
- The designs of actual communication systems are difficult to optimize with respect to specific communication distances and interferences between radio stations. In addition, the amount of data that can be transmitted must be calculated when nodes pass each other.
- (C)
- The system is assumed to be unsuitable from the viewpoint of information security for communications that may include personal information, such as handheld tablets, and few systems have been used practically or commercialized because of such problems. That is, no dedicated device has been developed because establishing it as a service is difficult.
The challenges in (A) have been actively addressed using various methods, and intensive theoretical analyses have been conducted. For example, diverse approaches have been proposed for theoretical analysis. For the infection method, efforts have been made to reduce the duplication of infection instances of information data, thereby reducing the amount of information data held by each node. Additionally, the use of vaccine data has been explored to analyze the spread rate of infection and recovery [10]. The theoretical analysis of infection utilizes Markov chain models, and evaluations under various conditions have been conducted by modifying the parameters. Moreover, in [11], epidemic communication algorithms were evaluated by comparing gossip and push algorithms. These algorithms are used to transmit information in distributed systems; among which, the epidemic algorithm demonstrated resilience to network delays and uncertainties with a small protocol overhead. The results of these evaluations indicated that the epidemic algorithm could transmit information more efficiently than the other algorithms. Epidemic communication has been shown to efficiently disseminate data, particularly when the number of terminals is high. However, realizing any of these algorithms is challenging, given the network conditions and device constraints.
Next, we introduce an example of implementing epidemic communication to address the challenges in (B). In [12], the authors implemented an epidemic routing protocol using Network Simulator ns-3. Message diffusion was achieved using direct communication between the nodes for implementation. Although the simulation confirms that data are diffused in space up to the destination node using epidemic communication [12], factors such as radio interference affecting the surrounding nodes are not considered. However, few studies have been found on radio interference issues related to epidemic communications because many researchers are interested in mathematical models and do not assume implementation. Therefore, we investigated radio interference in ad hoc networks, which is similar to epidemic communication. Interference models for ad hoc networks have evaluated the impact of interference at various layers [29,30]. The reason why the impact of interference per layer is evaluated is that ad hoc networks are based on the assumption that network routing is constructed, and the impact of interference varies depending on the configuration of the network topology. In addition, authentication and association procedures must be followed in the communication protocol. Epidemic communication, on the other hand, does not require the construction of network topologies or routing tables in order to cause infection. The connection procedure is also not suitable for infectious disease communication and cannot be solved by conventional ad hoc communication technology issues. Therefore, the challenges are to optimize the transmission and reception power that can be communicated, and the communication area for communication while moving, as well as interference when nodes are densely packed in a simple short distance.
Finally, the challenges in (C) concern the absence of commercially available wireless devices designed for the services envisioned. However, epidemic communication is considered as an effective communication method in scenarios such as information sharing between ITSs, robots, and drones, where the information does not include personal data.
The novelty of this paper is to design and develop a wireless system that is designed to be implemented in drones, based on the organization of the issues in these related works. Epidemic communication is the random spread of information by an infection method. Ref. [14] proposed the efficient method of conveying information by giving directionality to infection. For example, they proposed increasing the efficiency of infection by adding the distance that drones move in a specific direction to randomly moving drones, or by giving them radio wave directionality. On the other hand, in this study, we have examined the issues involved in actually implementing epidemic communication in a device, and solved these issues by evaluating them through theoretical analysis and experiments. However, the proposed method in Ref. [14] can be made into the device developed in this study, and this is a theme for future work. Moreover, the communication distance of the drone depends on the wireless device to be implemented. However, for epidemic communication, it is desirable to communicate at short distances, where interference to the surroundings can be avoided. In other words, the upper limit of the number of drones in a cluster is not a problem if it is not affected by interference. However, if the number of drones increases too much in a limited space, the problem of physical contact between drones will arise. Epidemic communication, which is not dependent on transmission time, has issues that must be considered in determining the optimal number of drones for operation, as well as the flight speed of the drones. These are discussed in Ref. [14].
There are few wireless devices capable of performing epidemic communication operations. For example, Transfer Jet is a device that may be used for epidemic communication. This is a technology being standardized in the IEEE802.15.3e [31,32], and it is specialized for close-proximity wireless transfer [33,34]. Another, Wi-Fi Direct [35] of Wi-Fi Alliance standard is a technology that enables simple direct connections and has been implemented in smart phones and notebook PCs, etc. These technologies eliminate or simplify the authentication and association process, and the time spent for the connection procedure between wireless stations is extremely short. Therefore, epidemic communication may be implemented, because these can achieve pure communication of the infected part. However, although these devices are implemented in commercial products, they are very difficult to obtain as devices for development. Therefore, in this study, we did not use these unique devices, but used wireless LAN (Wi-Fi) devices that are readily available and can be developed universally. Although wireless LANs can be easily implemented, the development was conducted after considering issues such as connection time, since authentication and association procedures are used in the communication protocols. The purpose of this study is to establish the implementation method for epidemic communication, and although maximum performance may not be achieved, the final result is that the design policy and assumed behavior can be realized, and providing this information is a contribution to other researchers.
3. Implementation Method for Epidemic Communication
In this section, we propose an implementation method of epidemic communication. Section 3.1 describes the use cases of epidemic communication and the problem of radio interference that arises in such cases. Section 3.2 explains how to calculate the transmission rate considering the interference among radio stations; Section 3.3 describes the method to evaluate the amount of transmission data that can be transmitted while a radio station is moving in the communication range of another radio station. Section 3.4 describes the evaluation results of the theoretical calculations in each subsection.
3.1. Interference between Multiple Nodes and Transmission Area
The proposed model of the epidemic communication system employs a network in which drones relay images of flowers, as shown in Figure 3. The background of this system model is an autonomous drone system for pollinating tomato flowers or pear flowers, where clustered drones fly around the stem of a tomato or the tree of a pear, searching for pollinatable flowers [13,14,15,16]. The drones are equipped with cameras, and by relaying the captured images of flowers to an external network, an external server performs artificial intelligence (AI) image classification. In this system, drones capture flower images repeatedly, relay data to other drones during exploration, and deliver the image data to an external server using the epidemic communication. The epidemic communication used in the proposed system is in the broadcast mode. In the broadcast mode, whenever a drone with flower data encounters another drone, it transfers the data. Therefore, as shown in Figure 4, each wireless station autonomously transfers data to nearby wireless stations during relay transmission. However, in the circled part of the figure, simultaneous communication between different wireless stations occurs, leading to radio interference. Figure 5 illustrates the conditions for the interference. In this interference model, wireless station A was assumed to transfer data to wireless station B, and simultaneously, wireless station C transferred data to wireless station D in its vicinity. The desired signal from C to D is omnidirectional and propagates to its surroundings, thereby causing interference with the desired signal from A to B. While increasing the distance between B and C reduces the interference, it decreases the node density within the cluster, resulting in a lower encounter probability between drones and a reduction in the infection speed. In addition, modulation schemes with interference have lower modulation orders, resulting in a decrease in the transmission rate. To address these challenges, the available transmission rates based on the distance between B and C were calculated using the following formula and Table 1. In this study, it is necessary to evaluate the effects of interference and other factors in order to design a transmission system suitable for epidemic communication for implementation in drones. However, there are no wireless devices dedicated to epidemic communications. Therefore, we adopted a wireless LAN system as a wireless device that we can develop. For the IEEE 802.11g wireless LAN standard, we calculated the available transmission rate based on the relationship between the minimum received sensitivity level and the signal-to-noise-plus-interference ratio (SINR) [36], which includes the amount of interference, using Equations (1) to (3).
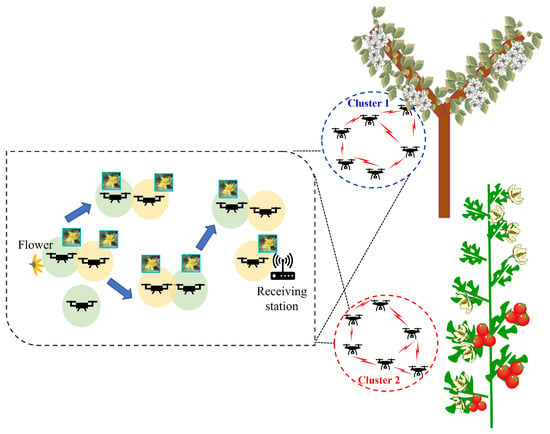
Figure 3.
Models for using epidemic communication.
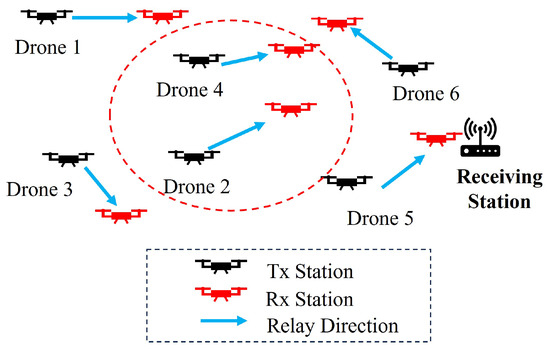
Figure 4.
Example of simultaneous relay transmissions.
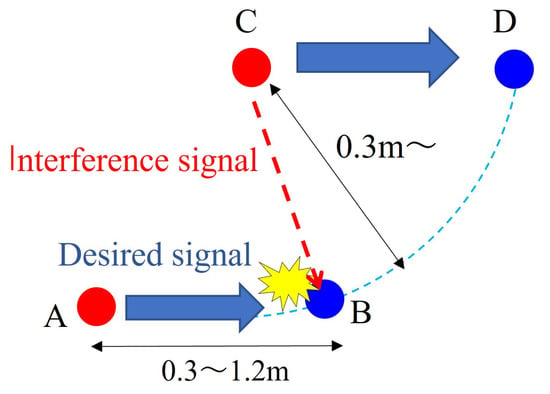
Figure 5.
Interference wave model for desired wave.

Table 1.
Transmission rate, receiver sensitivity, and SINR of IEEE802.11g standard.
In Equation (1), d represents the distance between antennas (inter-wireless station distance), c denotes the speed of light, and f represents the frequency. Additionally, let W be the bandwidth, be the antenna gain of the transmitting station, and be the antenna gain of the receiving station. In Equation (1), the transmit power is denoted as , and the received power is calculated. To determine the inter-wireless station transmission rate, the signal-to-noise-plus-interference ratio (SINR) is computed, including the noise power (NP). In Equation (1), represents the received power between wireless stations A and B, while denotes the received power between wireless stations B and C.
Equation (2) calculates the SINR.
Equation (3) determines the minimum receive sensitivity level (). This equation is obtained by subtracting the attenuation of the thermal noise N from the SINR, and the thermal noise is obtained by the following equation [37]:
where k is the Boltzmann coefficient, is the absolute temperature [K], is the bandwidth [Hz], and is the noise figure [dB]. If [Hz] and [dB], , and is obtained.
3.2. Interference Model Evaluation Method and Selection of Received Power Threshold
The parameters used in this simulation are the values specified for actual wireless LANs [17]. The conditions under which interference occurs are calculated based on the transmitted and received power using these values and assuming the actual distance based on the drone’s flight position, etc. Therefore, we believe that the scenario created by this simulation is reasonable. The calculated results of the available transmission rates based on the distance between the A and B wireless stations when the distance between the B and C wireless stations, which serve as an interference source, is changed for the previous section are shown in Table 2. Figure 6 illustrates the transmission rates obtained from Table 2 and the corresponding received power for distances between the A and B wireless stations set to the minimum and maximum values of 0.3 m and 1.2 m, respectively.

Table 2.
Distance between B and C with transmission rate achieved depending on distance between A and B.
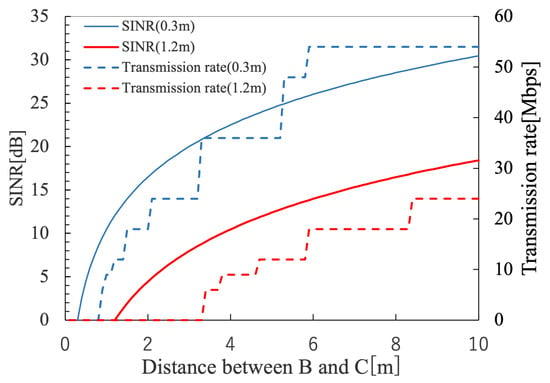
Figure 6.
SINR and transmission rate evaluation.
Table 2 determines the distance between the A and B wireless stations, where wireless station C does not interfere as an interfering wave, and hence, the achievable transmission rate between the A and B wireless stations, when the distance from wireless station A to wireless station B, where communication begins, varies from 0.3 m to 1.2 m. For example, when the distance between the A and B wireless stations is 0.3 m, to achieve a transmission rate of 9 Mbps or more, it is necessary to keep the distance between the B and C wireless stations at 1.0 m or more. Therefore, based on these results, in the development of wireless devices for epidemic communication, the transmit–receive range is set to 0.3 m, and the received power at that distance is calculated using Equation (2). Setting the transmit power to = 0 dBm (1 mW) and using d = 0.3 m, f = 2.4 GHz, , and = 0 dB, the calculated is dBm. Thus, in the design of wireless devices, communication is designed to start within the range where the RSSI (received signal strength indicator) is within dBm. However, it is assumed that the distance between the B and C wireless stations is at least 0.9 m to obtain the minimum transmission rate.
3.3. Change in Amount of Data Transferred Due to Movement of Radio Stations
In epidemic communication, as depicted in Figure 7, wireless stations establish connections to receiving stations and transfer data while moving within the communication range of other wireless stations. The communication range is utilized for data transfer while moving, and the connection is terminated when leaving the communication range. When approaching other wireless stations, these operations are repeated.
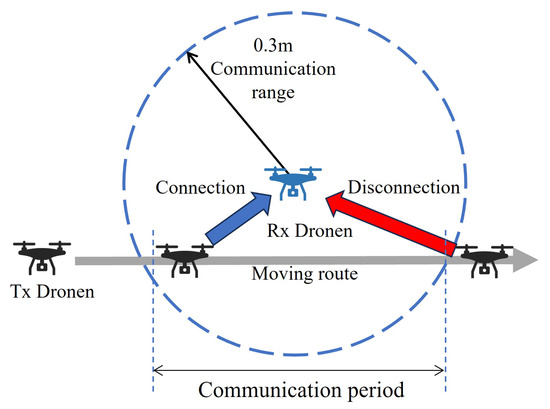
Figure 7.
Connection and transmission behavior within the communication range.
However, when passing through this communication range, there is overhead involved in connection time and the procedures for sending and receiving packet data. The actual time available for data transmission is the time remaining after deducting these overheads.
The connection procedure and the sequence of data transmission are illustrated in Figure 8. In this study, the transmitting station uses passive scanning to find surrounding available receiving stations by receiving beacon signals sent by receiving stations for a certain period. Subsequently, as an authentication procedure, the transmitting station sends an authentication request to the receiving station, and the receiving station responds with an authentication response to confirm its availability. Once the authentication procedure is completed, an association request is sent to initiate the connection procedure, and the connection is completed when the receiving station responds with an association response. In addition to these procedures, data transmission and reception involve carrier-sensing procedures and transmission–reception periods as specified in the IEEE 802.11g standard.
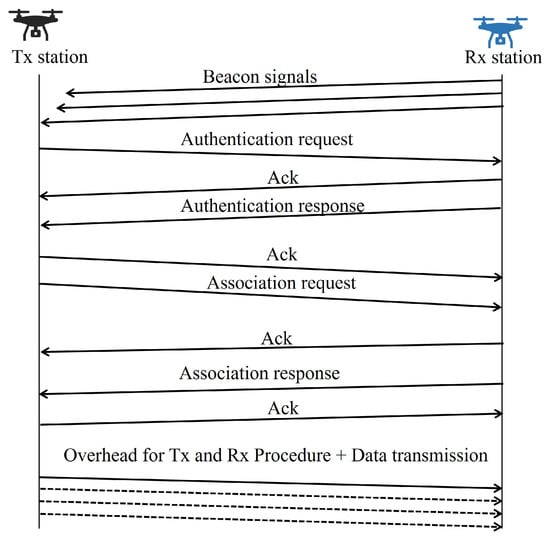
Figure 8.
Sequence of connection and data transmission procedures.
For the evaluation of communication time and transmitted data volume, the beacon interval is set to 50 ms, and other overhead times for transmission and reception periods comply with the IEEE 802.11g standard [17].
3.4. Evaluation of the Amount of Data That Can Be Sent
The evaluation involves assessing the amount of data transmitted when the transmitting station passes through the communication range of the receiving station. While there are various routes for passing through the communication range, a simplified method was employed to calculate the average transmitted data volume within the communication range.
As an evaluation model, it was assumed that wireless stations pass through the communication area in different linear routes, as illustrated in Figure 9. The passage routes are considered to be evenly spaced, and the average transmitted data volume during all passages is calculated. In this model, the closer a point is to the center of the communication range, the greater the transmitted data volume, while points closer to the outside of the communication area result in a lower transmitted data volume. Under these conditions, the average amount of data that the transmitting station can transmit was calculated using the following formula:
where denotes the radius of the communication range obtained in Section 3.1; we set to 0.3 m. When the moving route of the transmitting station passing through the communication range varies by at evenly spaced intervals, the time spent within the communication range and transferable transmitted data volume is calculated based on the transmission rate. Additionally, R denotes the distance from the center when approaching the center by . v is the moving speed of the drone. To determine the time to pass within the communication range, we calculated the distance through the communication area using the Pythagorean theorem. We attempted this n times and calculated the transmission time when approaching the center of the communication range , transmission rate used during communication b, and amount of data that can be transferred at that time. Next, we determined the average amount of data using the amount of transmission data that can be transferred on each route and number of times N () passed through the communication range.
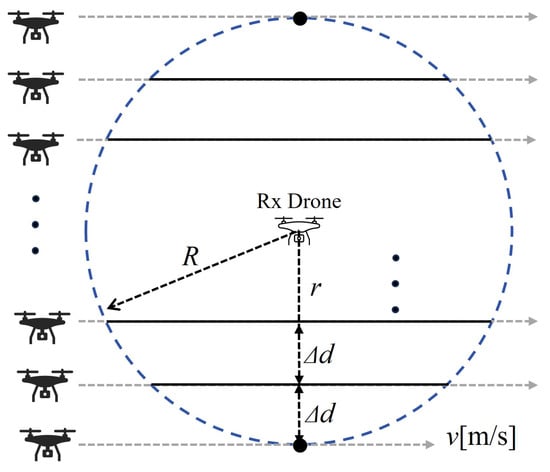
Figure 9.
Model for calculating transferable data volume.
Figure 10 shows the amount of data transferred relative to the movement speed for each transmission rate. The legend of Figure 10 indicates the respective transmission rates, and the x-axis indicates the movement speed of the wireless station. We observed a significant decrease in the transferable data amount when the movement speed changed from 0.1 to 0.2 m/s. In this study, the drone was assumed to capture flower image data of 500 KB, and the amount of data to be transmitted increased each time it passed another wireless station holding data, requiring the ability to transfer up to approximately 10 MB of data. Considering interference waves from the surroundings, transmission at lower rates may occur. Therefore, a drone speed below 0.2 m/s was desirable. The speed of infection (i.e., the rate of spread) of the entire system depends greatly on the number of drones and their speed of movement, but epidemic communication is originally based on a delay method called DTN. Although the physical transport speed (movement speed) of data is not important, a higher transmission rate is desirable when passing each other, increasing the amount of data that can be shared.
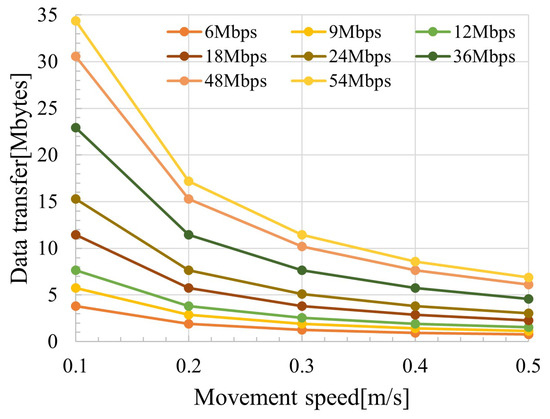
Figure 10.
Average amount of data that can be transferred relative to the distance of the interfering station.
4. Development of the Epidemic Communication System
4.1. Device Implementation
The parameters of the wireless devices were determined based on the analysis in Section 3. The RSSI value for connection was set to dBm, which was measured to achieve a communication range of 0.3 m. First, as shown in Figure 7, the actions and conditions from searching for the receiving station to connecting and disconnecting are explained in the flowchart presented in Figure 11. The STA scans the beacon signals of the surrounding APs, and acquires the SSID and RSSI upon receiving the beacon signal. This information is then passed to Python and saved in a list. The RSSI is compared with dBm, and the AP with the highest RSSI, i.e., the nearest AP, is then searched for. The connection process is then executed. After the connection, the image data are transmitted, and the connection is disconnected when the RSSI falls below dBm or when the transmission of image data completes. This operation can be repeated to transfer data to the destination. The transmission and reception algorithm for epidemic communication was implemented using a Raspberry Pi 3B+ (RasPi) [38] and external wireless device dongle. The RasPi is a low-cost and lightweight single-board computer with communication features such as Wi-Fi and USB ports. Some information on the use of Raspberry Pi 3 Model B+ [39] is as follows. Operating temperature: approximately 60 °C; current consumption: approximately 500 mA; CPU utilization: approximately 8%.
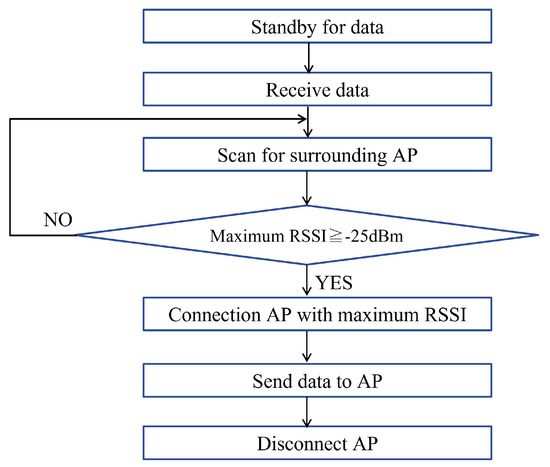
Figure 11.
Connection and disconnection control flowchart.
Figure 12 shows the configuration of the developed device. Both a receiving and transmitting interface are required for relay communication. The external wireless LAN dongle served as the receiving interface, and the built-in wireless LAN of the RasPi served as the transmission interface. The receiving interface uses the infrastructure mode access point (AP) function to transmit beacon signals, and the transmitting interface uses the station (STA) function.
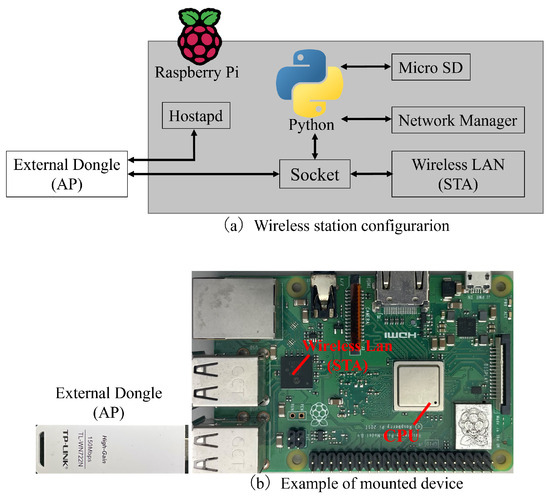
Figure 12.
Configuration of the developed wireless system.
For relay communication during the connection process, the STA of the transmitting interface was connected to the AP of the receiving interface to establish an affiliation relationship. The connection destination was unrestricted because we had multiple interfaces on a single device to enable flexible connections between devices. If a device has only one interface, it cannot transmit or receive information simultaneously, which leads to a decrease in communication opportunities. We implemented the epidemic communication algorithm in Python. The switching of the STA’s connection destination was performed using NetworkManager, which is a Linux operating system function.
To establish links with multiple wireless stations, the connection process must be performed every time the devices approach each other. At this time, the connection process time incurs overhead in communication time, leading to a decrease in the amount of actual data transfer. Therefore, using NetworkManager to complete the authentication process in advance, we reduced unnecessary connection process time. The Hostapd software MAC, which is a RasPi feature, was used for AP control.
Figure 13 shows the implemented protocol stack. Epidemic communication generally involves a bundle layer that accumulates data. This layer is inserted into the protocol stack above the transport layer and below the application layer. The bundle layer [40] implements a store–carry–forward mechanism in which nodes store data in their own buffers and transfer the data when it becomes available to other connected nodes. Data created in the application layer are converted into variable-length data called a bundle and stored in persistent storage for a long time; when a node is within the communication distance, the data are retrieved from this persistent storage for transfer. This layer enables the accumulation of data, helps handle data corruption during transfers, and retains the data to be transmitted. However, wireless LANs do not have such accumulation functions. Therefore, in this study, the data were pseudo-accumulated in memory using Python, as shown in Figure 13. The data received from the socket function were first reconstructed into an image using Python, and then, saved in memory. Additionally, the data payload size that could be passed from the application and bundle layers to the session layer was 65,507 bytes, which was obtained by subtracting the UDP header (8 bytes) and IP header (20 bytes) from the maximum datagram length of the IP layer, which was 65,535 bytes.
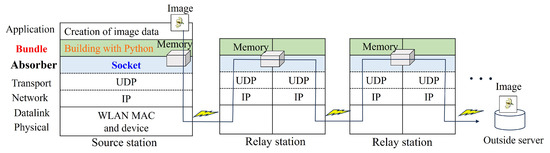
Figure 13.
Configured protocol stacks including the bundle layer and the socket function.
Sockets [41] were used to connect the transmitting and receiving stations. A socket function enables the transmission and reception of data between two endpoints, thereby allowing a network node to be treated as a node that is identified by a specific IP address and port number within the network. The receiving station enters a waiting state for data by binding to the IP address and port number, and the transmitting station can send and receive data by sending requests to the bound information. In particular, Figure 14 shows the socket function procedure of the session layer. After affiliating with the wireless LAN, a socket function is created for communication between the sending and receiving stations. The sending station reads the file to be sent and obtains the data size. The receiving station waits until it receives the data. If the flower image size is 500 KB, the sending station extracts data in chunks of the maximum datagram length of the IP layer, which is 65,507 bytes; calculates the number of transmissions; and notifies the receiving station of that value. The sending station then transmits data in chunks of 65,507 bytes. The receiving station saves the received data as a list-type variable. When saving the data in a list-type variable, the operation speed is faster than that when writing to a file, and errors in the continuously transmitted data are reduced. Finally, the transmitting station sends the remaining data, and the receiving station outputs the data saved in the variable to a file. Finally, the socket function is closed in preparation for the next connection, and the entire process concludes.
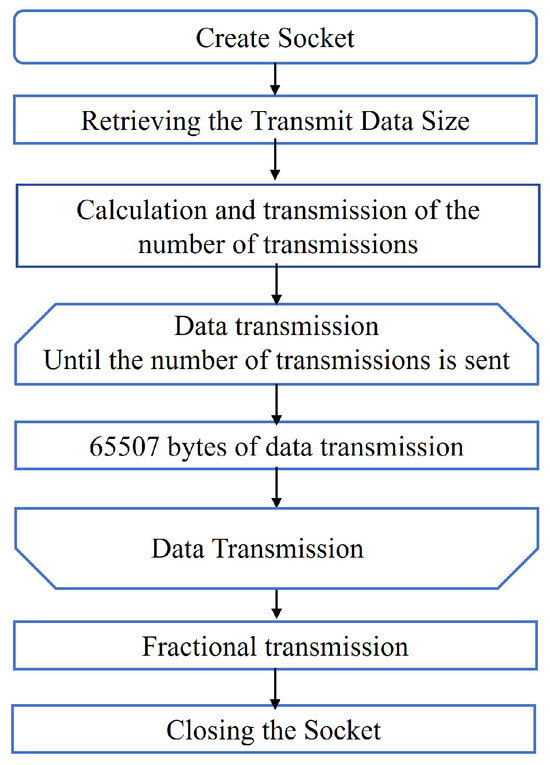
Figure 14.
Procedure for data-transfer processing using a socket function.
It is assumed that image data transferred using these protocols will be received at the receiving station, after which the data will be transferred to a cloud server in the wired network. For example, the cloud server uses AI classification technology by analyzing image data to classify flowers that can be pollinated [13]. In this case, duplicate images can be discarded. In addition, drones with pollination capabilities have been developed to fly to the coordinates of flowers to perform pollination work [42].
4.2. Evaluation of Epidemic Communication Systems through Experiments
The experiment involved comparing the theoretical values based on the operation depicted in Figure 9. The resolution of the flower image was set to high definition at 640 × 480 pixels, and the acquired data size was 500 KB. The movement speed varied, as in the evaluation in Figure 10, and ranged from 0.1 to 0.5 m/s; the data amount that was actually received was then evaluated. Experiments were performed based on the conditions shown in Table 3 to align the theoretical calculations with the actual experimental conditions. The experimental method was to manually move within the communication area. In other words, the time to pass through the area was measured precisely according to the speed of movement. We provide a video of the experiment as the Supplemental Material.

Table 3.
Experimental conditions.
Figure 15 presents the results of data reception. From Figure 15, we observe that as the moving speed increases, the data reception monotonically decreases. Moreover, compared with the theoretical values in Figure 10, the characteristics of the amount of received data show a similar trend; overall, the amount of received data decreases. This is believed to be because the theoretical calculation does not include the overhead of data buffering in the bundle layer and data splitting processing in the socket function, in addition to the overhead of UDP headers, IP headers, and other components. That is, because the UDP and IP headers are added for each divided data point, the overhead increases with the number of transmissions. Moreover, the processing speed observed when performing these operations depends on the device. Because RasPi was used, high performances cannot be expected. This is because RasPi is a small, single-board computer and cannot provide sufficient processing power. However, the data transfer characteristics tend to be similar. In future practical applications, the use of a dedicated high-performance machine is desirable. High-performance machines require a board capable of multitasking and driver tuning for wireless devices in order to increase transfer processing.
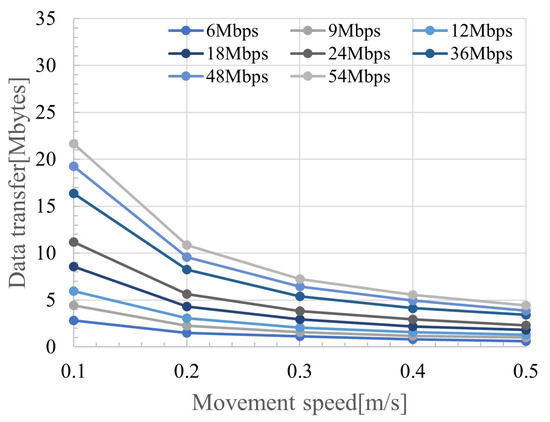
Figure 15.
Evaluation of data reception based on the experiment.
Therefore, although the infection rate decreased, we confirmed that the epidemic communication system operated normally. We fabricated seven wireless devices, as shown in Figure 16. Flower images were first captured, and the operation was confirmed by relaying the data from the source to the destination while transferring the data. A blue LED indicates wireless devices without holding data, and a red LED indicates the state of the wireless devices infected and holding the data. The wireless devices holding the data move according to the red arrows in the figure, and when they approach other wireless stations, their states change from blue to red. This operation was repeated to confirm that all wireless devices were infected and holding the data. As the implementation uses a wireless LAN, the connection time is theoretically longer than that shown in Figure 15, resulting in a decrease in the amount of data that can be transmitted. Therefore, other communication standards must be considered. This implementation also implements IP and UDP protocol stacks, since general-purpose software was used to measure throughput in the experiment. However, actual epidemic communication is the technology for spreading information through infection, and does not require a routing protocol that uses IP, etc., and the specification can work even if the IP and UDP layer layers are removed.
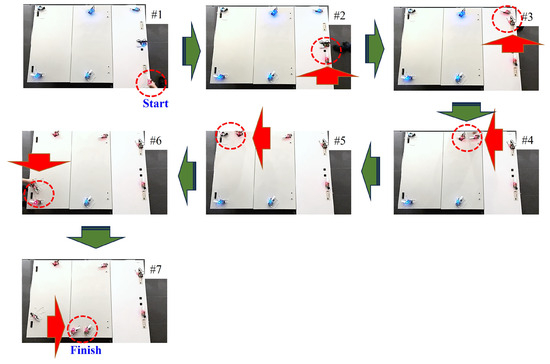
Figure 16.
Setup of the demonstration experiment.
5. Conclusions
We designed and developed an epidemic communication system and experimentally confirmed its operation. In this study, we analyzed the interference between wireless stations and the relationship between the transfer and movement speeds when using an epidemic communication method. We designed functionalities by considering the implementation of drones and confirmed their operation through the development of wireless devices and practical experiments with actual devices. The results show that the infection speed was lower than the theoretical value owing to the device processing speed. However, the design policies and implemented functionalities proved to be suitable for implementation in drones. Moreover, we successfully confirmed the normal infection operation between wireless stations through practical experiments. Based on the results of the demonstration experiment, we will tackle the development of a wireless system using epidemic communication.
Supplementary Materials
The demonstration experiments of the epidemic system in the laboratory are available as supplementary video material. This video can be viewed on YouTube at https://www.youtube.com/watch?v=keHns2rybbE (accessed on 20 May 2024).
Author Contributions
Conceptualization, T.H. and T.M.; method, T.H., T.K. and H.S.; validation, N.Y. and T.H.; investigation, T.H. and T.K.; resources, N.Y.; data curation, N.Y.; writing—original draft preparation, N.Y., T.H. and T.K.; writing—review and editing, T.H., T.K. and T.M.; visualization, N.Y.; supervision, Y.T. and T.M.; project administration, T.H. and Y.T.; funding acquisition, T.H. and Y.T. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the development and improvement program of strategic smart agricultural technology grants (JPJ011397) from the Project of the Bio-oriented Technology Research Advancement Institution (BRAIN).
Data Availability Statement
Data are available from the authors upon request.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Perkins, C.E. Ad Hoc Networking; Pearson Education India: Hoboken, NJ, USA, 2008. [Google Scholar]
- Kleinrock, L.; Silvester, J. Optimum transmission radii for packet radio networks or why six is a magic number. In Proceedings of the IEEE National Telecommunications Conference, Birmingham, Alabama, 3–6 December 1978; Volume 4, pp. 1–4. [Google Scholar]
- Takagi, H.; Kleinrock, L. Optimal transmission ranges for randomly distributed packet radio terminals. IEEE Trans. Commun. 1984, 32, 246–257. [Google Scholar] [CrossRef]
- Royer, E.M.; Perkins, C.E. An implementation study of the AODV routing protocol. In Proceedings of the 2000 IEEE Wireless Communications and Networking Conference. Conference Record (Cat. No. 00TH8540), Chicago, IL, USA, 23–28 September 2000; IEEE: Piscataway, NJ, USA, 2000; Volume 3, pp. 1003–1008. [Google Scholar]
- Clausen, T.; Jacquet, P. RFC3626: Optimized Link State Routing Protocol (OLSR), Nternet Eng; Tech. Rep. RFC 3626; Task Force (IETF): Fremont, CA, USA, October 2003; Available online: http://www.rfc-editor.org/rfc/rfc3626.txt (accessed on 14 May 2024).
- Burleigh, S.; Hooke, A.; Torgerson, L.; Fall, K.; Cerf, V.; Durst, B.; Scott, K.; Weiss, H. Delay-tolerant networking: An approach to interplanetary internet. IEEE Commun. Mag. 2003, 41, 128–136. [Google Scholar] [CrossRef]
- Fall, K. A delay-tolerant network architecture for challenged internets. In Proceedings of the 2003 conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Karlsruhe, Germany, 25–29 August 2003; pp. 27–34. [Google Scholar]
- Castro, A.A.V.; Serugendo, G.D.M.; Konstantas, D. Hovering information–self-organizing information that finds its own storage. In Autonomic Communication; Springer: Boston, MA, USA, 2009; pp. 111–145. [Google Scholar]
- Virtamo, J.; Hyytiä, E.; Lassila, P. Criticality condition for information floating with random walk of nodes. Perform. Eval. 2013, 70, 114–123. [Google Scholar] [CrossRef]
- Matsuda, T.; Takine, T. (p, q)-Epidemic routing for sparsely populated mobile ad hoc networks. IEEE J. Sel. Areas Commun. 2008, 26, 783–793. [Google Scholar] [CrossRef]
- De Abreu, C.S.; Salles, R.M. Modeling message diffusion in epidemical DTN. Ad Hoc Netw. 2014, 16, 197–209. [Google Scholar] [CrossRef]
- Alenazi, M.J.; Cheng, Y.; Zhang, D.; Sterbenz, J.P. Epidemic routing protocol implementation in ns-3. In Proceedings of the 2015 Workshop on ns-3, Barcelona, Spain, 13–14 May 2015; pp. 83–90. [Google Scholar]
- Hiraguri, T.; Kimura, T.; Endo, K.; Ohya, T.; Takanashi, T.; Shimizu, H. Shape classification technology of pollinated tomato flowers for robotic implementation. Sci. Rep. 2023, 13, 2159. [Google Scholar] [CrossRef] [PubMed]
- Kurosawa, T.; Kimura, T.; Shimizu, H.; Hiraguri, T. Epidemic communication control methods suitable for inter-drone relay in pollination systems. IEICE Commun. Express 2023, 12, 236–241. [Google Scholar] [CrossRef]
- Keita, E.; Kimura, T.; Nobuhiko, I.; Hiraguri, T. Semantic segmentation based field detection using drones. In Proceedings of the 2022 IEEE International Conference on Consumer Electronics-Taiwan, Taipei, Taiwan, 6–8 July 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 213–214. [Google Scholar]
- Yamada, N.; Hiraguri, T.; Shimizu, H.; Kimura, T.; Shimada, T.; Shibasaki, A.; Takemura, Y. Drone Flight Experiment using RTK Positioning for Pear Pollination. In Proceedings of the 2023 International Conference on Consumer Electronics-Taiwan (ICCE-Taiwan), Taipei, Taiwan, 6–8 July 2022; IEEE: Piscataway, NJ, USA, 2023; pp. 655–656. [Google Scholar]
- IEEE 802.11 p Working Group IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments. Available online: https://ieeexplore.ieee.org/document/5514475 (accessed on 14 May 2024).
- Rashidi, L.; Towsley, D.; Mohseni-Kabir, A.; Movaghar, A. On the performance analysis of epidemic routing in non-sparse delay tolerant networks. IEEE Trans. Mob. Comput. 2022, 22, 4134–4149. [Google Scholar] [CrossRef]
- Rashidi, L.; Dalili-Yazdi, A.; Entezari-Maleki, R.; Sousa, L.; Movaghar, A. Modeling epidemic routing: Capturing frequently visited locations while preserving scalability. IEEE Trans. Veh. Technol. 2021, 70, 2713–2727. [Google Scholar] [CrossRef]
- Hu, Y.; Tian, T.; Zhang, F.; Chen, Q.; Yu, G.; Ma, D. Restricted epidemic routing method in large-scale delay-tolerant networks. In Proceedings of the 2021 IEEE 21st International Conference on Communication Technology (ICCT), Tianjin, China, 13–16 October 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 380–386. [Google Scholar]
- Prasad, A.O.; Mishra, P.; Jain, U.; Pandey, A.; Sinha, A.; Yadav, A.S.; Kumar, R.; Sharma, A.; Kumar, G.; Salem, K.H.; et al. Design and development of software stack of an autonomous vehicle using robot operating system. Robot. Auton. Syst. 2023, 161, 104340. [Google Scholar] [CrossRef]
- Tomic, T.; Schmid, K.; Lutz, P.; Domel, A.; Kassecker, M.; Mair, E.; Grixa, I.L.; Ruess, F.; Suppa, M.; Burschka, D. Toward a fully autonomous UAV: Research platform for indoor and outdoor urban search and rescue. IEEE Robot. Autom. Mag. 2012, 19, 46–56. [Google Scholar] [CrossRef]
- Anggraeni, P.; Mrabet, M.; Defoort, M.; Djemai, M. Development of a wireless communication platform for multiple-mobile robots using ROS. In Proceedings of the 2018 6th International Conference on Control Engineering & Information Technology (CEIT), Istanbul, Turkey, 25–27 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Trautman, P.; Ma, J.; Murray, R.M.; Krause, A. Robot navigation in dense human crowds: The case for cooperation. In Proceedings of the 2013 IEEE International Conference on Robotics and Automation, Karlsruhe, Germany, 6–10 May 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 2153–2160. [Google Scholar]
- Prassler, E.; Scholz, J.; Fiorini, P. A robotics wheelchair for crowded public environment. IEEE Robot. Autom. Mag. 2001, 8, 38–45. [Google Scholar] [CrossRef]
- Xuexi, Z.; Guokun, L.; Genping, F.; Dongliang, X.; Shiliu, L. SLAM algorithm analysis of mobile robot based on lidar. In Proceedings of the 2019 Chinese Control Conference (CCC), Guangzhou, China, 27–30 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 4739–4745. [Google Scholar]
- Malavazi, F.B.; Guyonneau, R.; Fasquel, J.B.; Lagrange, S.; Mercier, F. LiDAR-only based navigation algorithm for an autonomous agricultural robot. Comput. Electron. Agric. 2018, 154, 71–79. [Google Scholar] [CrossRef]
- Gatesichapakorn, S.; Takamatsu, J.; Ruchanurucks, M. ROS based autonomous mobile robot navigation using 2D LiDAR and RGB-D camera. In Proceedings of the 2019 First International Symposium on Instrumentation, Control, Artificial Intelligence, and Robotics (ICA-SYMP), Bangkok, Thailand, 16–18 January 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 151–154. [Google Scholar]
- Cardieri, P. Modeling interference in wireless ad hoc networks. IEEE Commun. Surv. Tutor. 2010, 12, 551–572. [Google Scholar] [CrossRef]
- Dhanik, S.; Vijai, C.; Reddy, Y.M.; Dutt, A.; Shaaker, A.M.; Raj, V.H. Ad Hoc Networks: Adaptable Connectivity for Contemporary Business Needs. In Proceedings of the 2023 10th IEEE Uttar Pradesh Section International Conference on Electrical, Electronics and Computer Engineering (UPCON), Greater Noida, India, 1–3 December 2023; IEEE: Piscataway, NJ, USA, 2023; Volume 10, pp. 1694–1698. [Google Scholar]
- Noda, M. Proposal for IEEE802. 15.3 e-Single Carrier PHY; IEEE Doc; IEEE: Piscataway, NJ, USA, 2015; p. 15. [Google Scholar]
- Toshimitsu, K.; Hiraga, K.; Lee, J.; Maekawa, I.; Noda, M. Proposal for IEEE802. 15.3 e-MAC: Superframe and Association; IEEE Doc; IEEE: Piscataway, NJ, USA, 2015; p. 15. [Google Scholar]
- Noda, A.; Shinoda, H. Inter-IC for Wearables (I 2 We): Power and data transfer over double-sided conductive textile. IEEE Trans. Biomed. Circuits Syst. 2018, 13, 80–90. [Google Scholar] [CrossRef] [PubMed]
- Fukui, Y.; Noda, A.; Shinoda, H. Noise factor of active-tile for two-dimensional communication. IEICE Commun. Express 2017, 6, 160–165. [Google Scholar] [CrossRef]
- Alliance, W.F. Wi-Fi Direct Services Draft Technical Specification. version 0.1, Wi-Fi Alliance Technical Committee, Wi-Fi Direct Services Task Group. 2013; 1–86. [Google Scholar]
- Pozar, D.M. Microwave Engineering; John Wiley & Sons: Hoboken, NJ, USA, 2011. [Google Scholar]
- Vizmuller, P. RF Design Guide: Systems, Circuits, and Equations; Artech House: London, UK, 1995. [Google Scholar]
- Raspberry Pi 3 Model B+. Available online: https://www.raspberrypi.com/products/raspberry-pi-3-model-b-plus/ (accessed on 13 December 2023).
- Raspberry Pi 3 Model B+ Benchmark. Available online: https://community.element14.com/products/raspberry-pi/w/documents/3459/a-comprehensive-raspberry-pi-3-model-b-plus-benchmark (accessed on 14 May 2024).
- Scott, K.; Burleigh, S. Bundle Protocol Specification; Technical Report. 2007. Available online: https://www.rfc-editor.org/rfc/rfc5050 (accessed on 14 May 2024).
- Kalita, L. Socket programming. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 4802–4807. [Google Scholar]
- Hiraguri, T.; Shimizu, H.; Kimura, T.; Matsuda, T.; Maruta, K.; Takemura, Y.; Ohya, T.; Takanashi, T. Autonomous drone-based pollination system using AI classifier to replace bees for greenhouse tomato cultivation. IEEE Access 2023, 11, 99352–99364. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).