1. Introduction
Crime continues to be a prevalent issue with significant economic, social, and political consequences in countries across the globe [
1]. Approximately 83% of the world’s population resides in areas characterized by elevated levels of criminal activity [
2]. Contemporary home security systems have undergone significant advancements, expanding the system’s reach beyond mere residential protection by integrating home automation capabilities. Incorporating these modern features helps improve security measures, provides convenience to consumers in their daily lives, and contributes to endeavors aimed at convenience and energy conservation.
In our rapidly evolving digital age, the Internet of Things (IoT) has emerged as a critical smart application for modern security living [
3,
4,
5,
6,
7,
8,
9]. Integrating IoT devices, automation detection, and notification systems with smart home technology offers a comprehensive security solution for everyday activities [
8,
10,
11]. Cost optimization and facilitation are significant benefits provided by IoT-driven transformations for real-time remote-access systems [
12] through cellular and Wi-Fi networks [
4,
6,
13]. Integrating mobile access points within an IoT-driven home security system can significantly enhance the system’s ability to manage energy resources and maintain robust communication with various sensors and devices. By dynamically adjusting to the optimal positions within a home, these mobile access points ensure that the system’s throughput is maximized, resulting in a more responsive and energy-efficient security network [
14,
15]. The integration of IoT technology and internet connectivity enables users to remotely manage and react to smart home security system functions, including appliance control, security monitoring, intrusion alert, and automation lighting control [
4,
6,
12,
16].
Furthermore, incorporating energy monitoring and control is essential in designing and developing smart home security [
17,
18,
19]. Smart home security systems are implemented using a single-board computer (SBC) to reduce energy consumption effectively. Famous microcontrollers, including but not limited to Raspberry Pi, Arduino, and ModeMCU, propel progress in the IoT domains of smart homes and security [
7,
20,
21,
22,
23,
24]. The compatibility of lighting management and intrusion detection exemplifies the revolutionary capacity of IoT technologies. Alarms throughout the property may be automatically illuminated or sounded upon the detection of an intruder by a hub. This interconnectivity improves security, so the responsiveness of IoT systems and user alerts demonstrate how the requirements for home safety are strengthened. Existing studies [
25,
26,
27,
28] have established that integrating IoT-enabled PIR (passive infrared sensor) intrusion detection into home automation systems positively influences security by providing comfort, energy, responsiveness, cost savings, remote control, and convenience.
Similarly, customizing smart home security systems to cater to the most stringent user demands poses unique obstacles, particularly concerning hands-free dictation. The use of voice-activated commands has transformed both automation and human-liberated control. Voice recognition technology has surfaced as a potentially effective intelligent security application for enhancing user convenience and natural command methods. Based on our previous research [
29], an earlier study proposed IoT-enabled intruder detection via voice and motion to support a smart light. When an intruder was spotted via a PIR sensor, the system could activate the relay to switch the lights on or off. The research results were observed and summarized on user commands via the Blynk button and Google voice assistance in Thai and English during varying delay times of PIR sensors. However, the prior research gap of voice-activated commands in different wireless network communications, accuracy, responsiveness, detection angles, and multilanguage supports through the smart home security and automation system can continuously be explored for further motivation.
Therefore, this study aims to design an IoT-based home security framework, develop system operations, and investigate accuracy, responsiveness, and outcome sensor delays using PIR sensors to support hardware, processes, and systems for enhanced user interaction and system control through voice and button commands in various communication technologies. The IoT-based proposed framework can improve and optimize lighting and security management by utilizing voice and buttons developed on Raspberry Pi to detect intruder motions. The research methodology includes hands-on experiments to evaluate the precision and responsiveness of the system under typical user-controlled circumstances, such as voice commands in Thai and English via Wi-Fi, 4G, and 5G internet connectivity. The experimental investigation can determine, construct, and assess a smart home automation system that operates on IoT devices, specifically focusing on lighting control and intrusion detection. The authors propose a novel matric factor of critical system efficiency and responsiveness to ensure the system can sustainably support voice commands for light controls, intrusion detection, home wireless networks, and evolving cellular network systems. In addition, the accuracy and responsiveness of intruder detection using PIR sensors based on varying delay detection times are investigated. Thus, the study addresses the following fundamental research questions:
How can the hardware and software components of an IoT-based smart home system be integrated to ensure seamless communication and cooperation between home automation, intruder detection, and lighting control functions?
How is the extent of the proposed framework effective in achieving smart lighting control? Consider factors of system effectiveness related to response time, accuracy, and internet connection performances in the context of voice and motion detection on various internet connections.
How do IoT-based smart home systems affect the accuracy of intruder detection on various PIR delay detection times?
By focusing on combining home automation and intrusion detection using voice commands, the results of this research contribute to the design and development of an IoT-based framework, hardware, and processes, and assess the system accuracy and responsive performances of various multilanguage commands on internet connections, including Wi-Fi, 4G, and 5G relating to the delay time settings of PIR sensor detection. The study recognizes the transformative potential of 5G networks to guarantee that an IoT-enabled smart home system operates accurately. By expanding on our previous study, this study explores the extended domain of 5G to comprehend how emerging cellular technology can impact the accuracy, efficiency, dependability, and user responsiveness of the proposed IoT-powered smart home automation and security system. The integration of 5G networks ensures increased data transfer speeds and enables a more precise response time for an ecosystem of interconnected IoT smart home devices. The proposed IoT-based smart home integration utilizing Raspberry Pi 4 can revolutionize human life in the fast-paced digital age of hectic schedules and expand responsibilities for the home, allowing us to create smart, responsive, and secure living environments, improving people’s daily lives.
3. Materials and Methods
Section 3 of this article provides an in-depth analysis of the operational and design components of our novel IoT-driven smart home automation and security system. This segment has been carefully structured to optimize logical progression and comprehension by methodically dissecting the intricate elements of our system.
Section 3.2 provides a primer to the comprehensive framework of our IoT-based smart home security architecture solution, elucidating its interconnectedness and stratified arrangement.
Section 3.3 establishes the groundwork for a comprehensive examination of the hardware and system design, clarifying the functions of every element comprising the IoT smart home security ecosystem.
Section 3.4 describes our experimental configuration and method of data collection, illustrating how our system was evaluated in real-world scenarios. Every subsection is interrelated, building upon the preceding one in order to furnish a thorough comprehension of the architecture, components, and performance evaluation of our system.
3.1. Research Methodology
This study aims to implement an IoT-based smart home automation system efficiently to detect intrusions and notify a user using lights and buzzers. The Raspberry Pi 4 can be utilized in conjunction with voice commands. This study includes two primary empirical investigations. The fundamental objective of the experiment is to consistently evaluate the system’s accuracy and responsiveness in common user-controlled scenarios, such as switching lights on and off and establishing internet connections via Wi-Fi, 4G, and 5G networks. Another objective is to assess the accuracy of intruder detection. This evaluation zeroes in on the system’s performance in scenarios involving intruder detection, specifically scrutinizing the response times of the PIR setting. These response times are categorized as low (5 s), medium (2.5 s), and high (1 s). This exhaustive evaluation aims to foster confidence in the audience about the system’s capabilities.
Assessing various PIR delay time settings in the IoT-based smart home system is essential for comprehending the system’s performance in different situations along with communication protocols. This study rigorously analyzed the performance of the PIR sensor, specifically emphasizing its ability to detect intruders, even when no people are present promptly. The significance of this evaluation lies in its capacity to uncover the functional characteristics of the system and its potential for improvement, particularly in applications.
To mimic real-life conditions for the secondary objective, a PIR sensor is strategically placed in front of the testing area at a height of 1.8 m, adhering to the recommended guidelines for PIR sensor installation [
37]. During the system’s testing phase, data are collected from three distinct sources: Thai speech, English speech, and the control buttons of the Blynk mobile application. Each experimental scenario is repeated 100 times, demonstrating our rigorous approach to data collection. This thorough method ensures a comprehensive evaluation of the proposed intrusion detection and smart lighting control system that leverages the IoT. The resulting system lays the groundwork for understanding the capabilities and limitations of the developed system in practical situations.
3.2. Design of IoT-Based Smart Home Framework
The design of the IoT framework makes a substantial contribution to the domains of home automation and security, as demonstrated in this study. Integrating multiple technological aspectual components and layers [
12,
16,
58], and encompassing user interface applications and physical hardware, the framework offers a comprehensive approach to smart home solutions. The IoT-based smart home framework introduces a groundbreaking multilayered approach, drawing inspiration from various system design domains. This innovative method enhances user interaction with the system, employing fresh techniques for user engagement. Unlike previous models, the framework uniquely integrates aspectual layering components, offering more modular and replaceable parts. The proposed design leads to more straightforward upgrades and maintenance, and showcases a unique ability to adapt to emerging technologies, such as the latest generations of network connectivity like 5G communication technology. The framework’s security features, particularly the inclusion of PIR sensors and real-time alert systems, are more advanced and integrated uniquely compared to previous systems.
The smart home environment’s interpretation and processing of user commands and sensor data necessitate a range of sensors and commands with a responsive and accurate methodology. Integrating multilayering semantics adaptation in services has significantly enhanced our framework’s design. Each framework layer operates independently by employing this strategy while integrating seamlessly, ensuring smooth operation and intuitive user engagement. This innovative adaptation boosts the system’s responsiveness and enhances its ability to learn and adapt to the homeowner’s habits and preferences over time. This integration establishes a comprehensive system that simplifies home automation and security management, incorporates sustainability principles and quality assessment mechanisms, and enhances user interaction and knowledge capabilities. Combining these diverse components from various fields results in an innovative and potentially transformative IoT smart home design methodology.
The system’s architecture enables real-time control and monitoring, essential for improving a smart home’s security, comfort, and energy efficiency. Incorporating well-known platforms and protocols, such as Google Assistant for voice control and MQTT for communication, demonstrates the adaptability and future compatibility of the IoT-enabled system with evolving smart homes.
The IoT-based smart home framework, illustrated in
Figure 1, is a meticulously engineered and stratified system that provides a comprehensive approach to safeguarding residential premises. The framework is composed of hardware, software, and applications, which are all distinct layers. Each layer is composed of a multitude of components that work in conjunction to establish a secure and efficient smart home environment.
Physical elements such as PIR sensors, buzzers, lights, a Raspberry Pi, and a relay comprise the foundational level. These devices are of the utmost importance as they function as the central control unit (Raspberry Pi) that processes input from various sensors and generates signals to execute actions such as activating lights or triggering alarms, in addition to detecting intrusions via the PIR sensor and issuing alerts via buzzers and lights.
The software layer functions as an intermediary, facilitating the conversion of hardware signals to executable data, situated superior to the hardware and vice versa. The Raspberry Pi software package consists of various software components, including the operating system and system drivers. The elements as mentioned earlier comprise Internet connection protocols (TCP/IP), coding libraries for Python and Java, a WebSocket server facilitating real-time communication, MQTT enabling lightweight messaging, and application programming interfaces (APIs) integrating with smart devices and enabling voice command capabilities, as exemplified by Blynk and Google Assistant.
The user interacts with the system at the highest layer. The system consists of user-friendly interfaces and applications that deliver notifications and enable voice and button commands for system management and control. The visual presentation and user interaction are the responsibility of the user interface layer, irrespective of the user’s location or remote access to the system via Wi-Fi, 4G, or 5G networks.
By compartmentalizing functionalities into discrete layers, the IoT-based framework offers many advantages. This layering methodology allows for flexibility in selecting and integrating various components, ensuring the system’s adaptability to evolving technologies. It also promotes compatibility between different devices and services, facilitating seamless integration. Moreover, the layered structure enables accurate configuration, allowing for comprehensive adjustments and calibrations at every tier, promising precise reactions to security threats, and optimizing the performance of smart home automation functionalities.
The flexibility of the IoT framework has been intentionally engineered to accommodate the rapidly advancing domain of smart home technology. From the physical hardware to the user interface, the structural layers can be subdivided into numerous layers, allowing for the autonomous updating or replacement of each segment in response to the emergence of more advanced technologies. This IoT-enabled home automation and security system is designed with user-friendliness and seamless integration. Utilizing widely recognized communication protocols such as TCP/IP and MQTT guarantees seamless connectivity with many devices and services.
The system can effortlessly adapt to evolving requirements or emerging technologies by updating or substituting specific layers or components—all without requiring a comprehensive system redesign. The implementation of the layering methodology provides the advantage of flexibility in selecting software and hardware components. The framework is illustrated by the smooth incorporation of an innovative sensor into the hardware layer, which has no observable impact on the software or applications layers.
Every successive layer functions as a modular interface, guaranteeing compatibility between various components and technologies. The capability to establish standardized communication protocols that ensure compatibility with a wide variety of multiple application interfaces and hardware devices is implicit in the software layer. A layered framework facilitates the configuration procedure during implementation. These framework features enable comprehensive adjustments and calibrations at every tier, promising precise reactions to security threats and optimizing the performance of smart home automation functionalities. Compatibility with the system is extensive and wide-ranging, extending from primitive sensors to intricate sensors along with cloud-based platforms.
3.3. Hardware and System Design
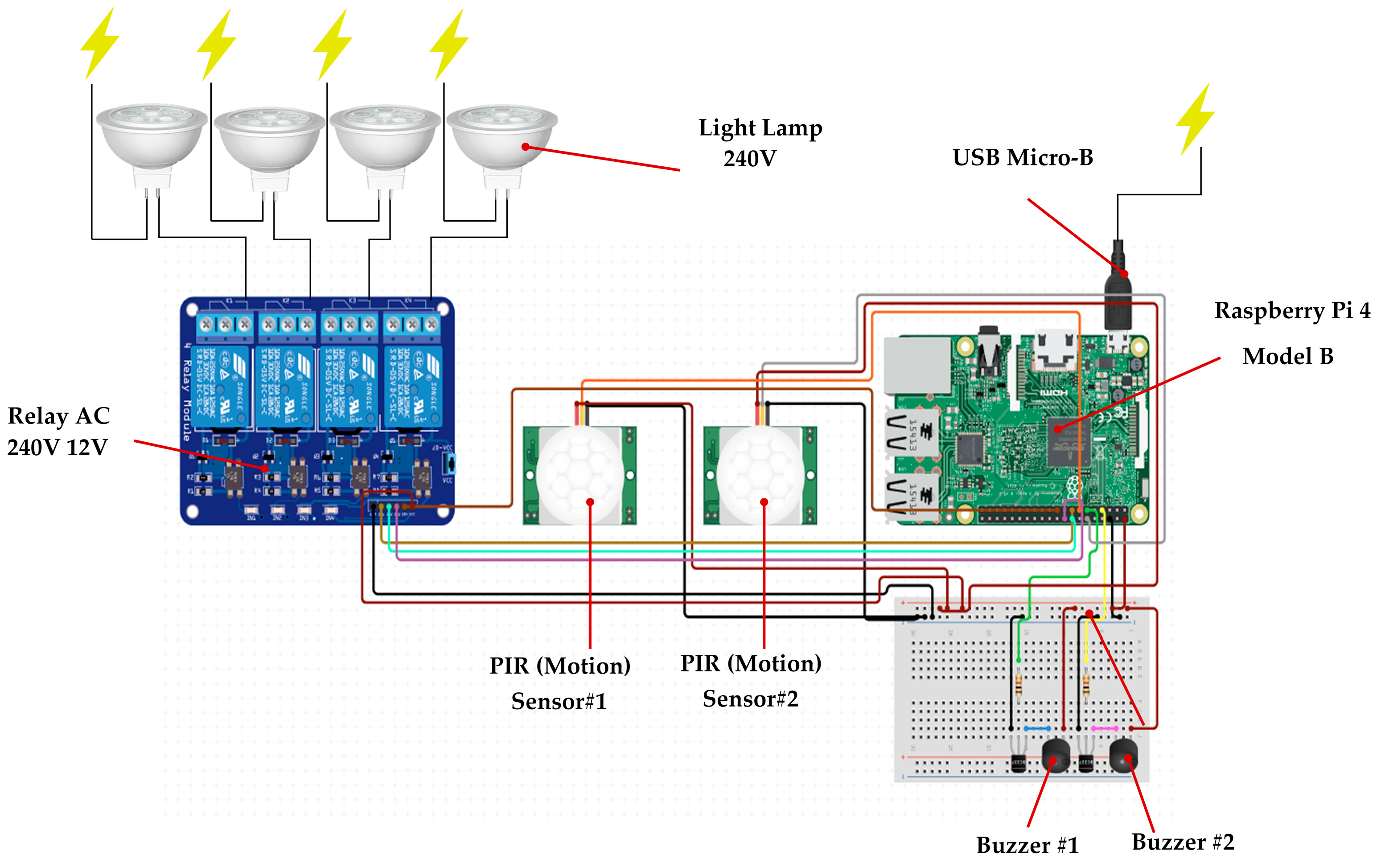
The practical system under investigation includes Wi-Fi connectivity tested within a smart home environment, while scenarios involving 4G and 5G mobile connections were tested outdoors. The results illustrate the system’s agility in enabling remote access and the control of electrical devices through smartphones. The system is precisely engineered to automate lighting control and enhance security, utilizing motion detection to activate lights or alarms. The system’s functionality relies on the precise programming of a microcontroller board built on a Raspberry PI. This microcontroller board processes the input from the PIR sensors and manages the output to the lights and buzzers through the relay module, as depicted in
Table 1.
Figure 2 illustrates the visual structure of a smart home security automation system. The incorporation of vital elements guarantees a unified and adaptable structure. The system consists of a Raspberry PI that facilitates communication and interaction between a relay, PIR sensors, light lamps, buzzers, and a USB micro-B connection. The integration of these components creates a smart home security automation system that is responsive and adaptable, effectively utilizing technology to protect and improve the security of the home environment.
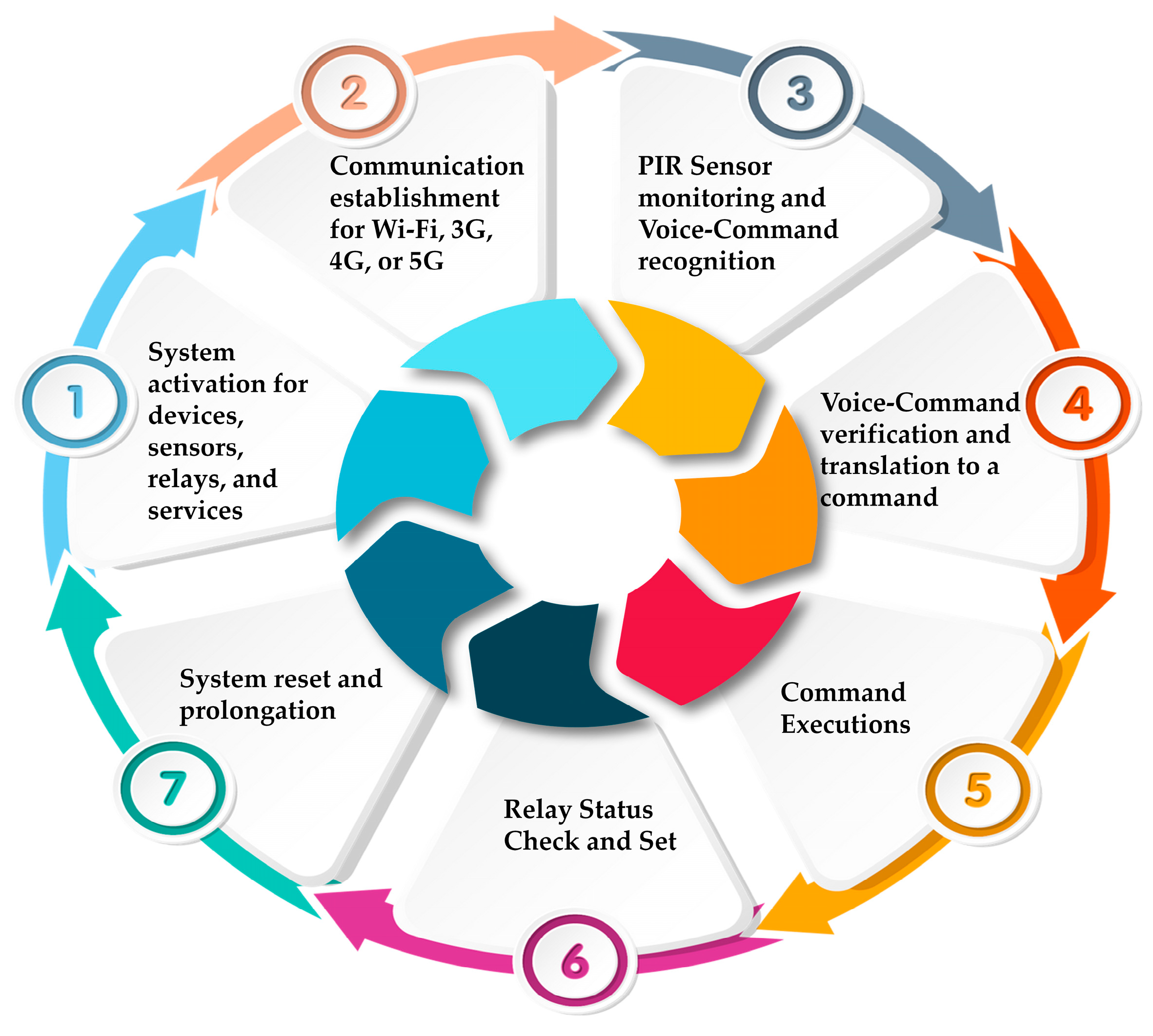
The proposed smart home security and automation system utilizes a seven-step algorithm that combines IoT technology with user-friendly interfaces, as depicted in
Figure 3. The system algorithm comprises the following:
System activation: The process begins by supplying power to the Raspberry Pi 4, which functions as the central control unit for the system.
PIR sensor surveillance: The system utilizes PIR sensors to detect motion. Upon detecting motion, the system promptly triggers the buzzer and illuminates the lights as an instant security measure.
Relay status verification: When no motion is detected, the system verifies the status of the relay. When the relay is activated, the lights stay illuminated; when deactivated, the lights are switched off to conserve energy.
The system actively listens for voice commands, simultaneously prepared to interpret instructions from the user.
Voice command authentication: When a voice command is received, the system verifies its authenticity to decide whether to activate or deactivate the lights.
Command execution: The system performs the command by activating the relay to switch the lights on or off, demonstrating the system’s ability to respond promptly to automated sensor inputs and user commands.
System reset: After actioning any command, the system resets to its original state, ready to detect new motions or receive further voice commands.
In this study, the synthesis steps enhance security through efficient intruder detection and provide convenience for remote lighting and alarm control as follows:
Enhanced security: The immediate activation of buzzers and lights upon motion detection by the PIR sensors deters potential intruders and alerts the user.
Remote control: Users can control lighting and alarms remotely via the Blynk application or voice commands through Google Assistant.
User notifications: The system notifies the user of detected intrusions, allowing for the quick deactivation of alerts if necessary.
Multilingual support: With support for both Thai and English, the system caters to a diverse user base.
Protocol utilization: The use of MQTT and IFTTT protocols enables smooth integration with various devices and services, making the system adaptable to a wide range of scenarios.
User-centric design: The system’s design considers the user’s importance, conveniences, and needs in smart home solutions on responsive control and usability.
3.4. Experimental Setup and Data Collection
This study examines an IoT-based smart home automation system centered on intrusion detection and lighting control using a Raspberry Pi 4. The setup includes PIR sensors for motion detection and an array of smart devices for lighting, operating over Wi-Fi, 4G, and 5G networks to assess performance across diverse connectivity scenarios. Data collection is a hybrid of automated processes using Google Assistant and manual processes using user inputs. The voice-activated assistants interact with Raspberry Pi 4 devices using the MQTT and IFTTT protocols. These protocols are essential for converting spoken commands into electronic signals, allowing users to control the system with their voices. The manual processes capture system responses to Thai and English voice commands and inputs from the Blynk, alongside manual recordings by the authors for comprehensive analysis. The proposed IoT-based system incorporates PIR sensors for intrusion detection based on area. PIR sensors have a specific detection range and angle limitations based on [
20]. This research employs two sensors to collectively cover a more extensive detection range and a variety of angles, thereby improving the system’s detection capabilities.
Upon detecting an intruder within the range of PIR sensors, the system immediately activates the corresponding light bulb and initiates a buzzer system to notify the user promptly. The Blynk application has the capability to turn off the light and buzzer for the sake of convenience. The system initialization commences with activating the relay located in the adjacent state. Both the Blynk application and Google Assistant can manually activate the light. The system, equipped with PIR sensors, operates as a multitasking device and maintains constant vigilance for intruders. When the system detects an object in its field of view, it promptly triggers the light and buzzer while also displaying a notification that says, “An intruder has been detected”. The user retains control via the Google Assistant application and can promptly deactivate the light and buzzer. The system integrates IoT technology, voice recognition, motion detection, and user-friendly interfaces. The system’s main advantage lies in its heightened security through intruder detection and the convenience of remotely controlling lighting and alarms using user-friendly smartphone applications. Furthermore, its ability to function effectively in Thai and English and its compatibility with MQTT and IFTTT protocols showcase its versatility in diverse practical scenarios.
This study examines the precision of intruder detection using different PIR sensor detections. It introduces two metrics: average effectiveness response time (AERT), which measures the time it takes for the system to respond after a command is issued, and average accurate intruder detection (AAID), which evaluates the system’s accuracy in detecting intrusions. The data sampling strategy is systematically designed to capture a wide range of system performances, with regular intervals and customization based on the experiment’s characteristics. To replicate real-life usage scenarios, an experimental investigation is carried out under diverse conditions, encompassing varying time periods throughout the day and network environments. The entirety of the data are systematically documented and stored within specialized IoT data management systems. Prior to analysis, the data undergo meticulous preprocessing procedures such as cleaning and normalization to ensure precise results. In order to guarantee the trustworthiness and accuracy of the data, every experimental scenario is duplicated numerous times, frequently reaching up to 100 repetitions. This process establishes a strong basis for assessing the effectiveness and flexibility of the system in different circumstances and with various inputs.
4. Results and Discussion
Emphasizing user-centric design, this study offers a sophisticated approach to home automation, promising increased convenience, efficiency, and security, and thus contributing substantially to the evolution of a solution using an IoT-based smart home framework. The proposed framework marks a notable advancement in the IoT-based smart home security domain. It demonstrates a significant improvement in voice command recognition, particularly for adapting multilanguage commands, indicating a leap in language processing effectiveness. The system shows impressive adaptability across various network technologies, especially in integrating the emerging 5G communication technology, aligning it with current global technological trends. This study also highlights the precise detection capabilities of PIR sensors, suggesting configuration settings that enhanced real-time security monitoring. Furthermore, the in-depth evaluation of system responsiveness across different conditions underscores its operational efficiency.
This experiment thoroughly investigated a system-controlled smart lighting and detection system, analyzing its performance in various scenarios, including manufacturing variations, extended usage, and changes in manufacturing techniques. The characteristics of the PIR detector can influence the system’s operational efficiency. This study found the comparison of detection capabilities among detectors deployed in the same environment but configured with different delay detection responses to be particularly intriguing. This study methodically categorized testing conditions into three groups according to the levels of delay: low, medium, and high. These experiment approaches were made using two different methodologies called Blynk and Google Assistant. Every method was thoroughly assessed through 100 iterations to evaluate response times in four communication modes: direct, 4G (300 Mbps), 5G (1 Gbps), and Wi-Fi (866 Mbps). Therefore, each experiment’s average effective response time was calculated with great attention to detail, providing valuable insights into the system’s performance under different circumstances. This study precisely determined the detector’s coverage area by specifying a height of 180 cm and a reach of up to 700 cm, as indicated in reference [
20]. This configuration facilitated the evaluation of the latency of Blynk button commands and Google Assistant voice commands. The response time of the Blynk application relied heavily on the system’s capacity to detect an intruder entering the equipped room or effectively execute commands to control the system-controlled lights. The primary objective of the investigation was to clarify the intricacies of response times across various communication modes.
Table 2 displays the outcomes of the experiments that aimed to assess the efficiency of the IoT-based smart home system in different network scenarios, such as 4G, 5G, and Wi-Fi. The system employed Blynk button commands and Google Assistant in Thai and English. Concerning the commands “Turn on light” and “Turn off light”, the system exhibited satisfactory performance, with a consistently low average error rate time (AERT) ranging from 2.4 to 5.3 s under different network conditions and voice assistant platforms. The English voice assistant had an 18% failure rate in activating the lights. The system’s commendable accuracy was demonstrated through intruder detection scenarios using AAID. The system consistently attained AAID scores within the range of 2.2 to 4.7 in scenarios characterized by low response times of 1 s. The AAID results showcase the system’s capacity to promptly and precisely identify trespassers in real time. In situations where the response times were moderate (2.5 s), the system consistently demonstrated high accuracy, as indicated by AAID scores ranging from 2.7 to 5.6. The precise identification of intruders showcases the system’s dependability in promptly detecting unauthorized individuals with a delay of only 2.5 s. Despite a 5 s delay, the system’s AAID scores ranged from 5.8 to 7.5 in intrusion detection scenarios, indicating its accuracy in detecting intruders. The IoT-based smart home system successfully detected intruders, even under fluctuating network conditions and response times, as depicted in
Figure 4. Nevertheless, there were occasional problems executing voice commands, specifically when utilizing the English voice assistant. To enhance the overall reliability and responsiveness of the system, it is essential to analyze these occasional failures and make necessary adjustments.
Figure 4 depicts the performance of different commands carried out through different network connections (Wi-Fi, 4G, 5G) in three experimental configurations: Google Assistant voice commands in English, Google Assistant in Thai, and Blynk button commands. The commands encompass PIR detection with adjustable delays and operations for managing security and lighting. The execution of “Turn off light” commands was nearly flawless in all scenarios, demonstrating high performance. Instructions to “Disable security” were also highly effective, although with slightly lower implementation rates in Thai voice assistance. The PIR detection commands correlated with the delay’s duration, whereby shorter delays resulted in improved execution. However, these commands were still less effective than the light and security ones. The shift from Wi-Fi to 4G and subsequently to 5G led to decreased command failures, especially in voice assistance experiments. This result indicates that newer network technologies can improve the reliability of command execution. Moreover, voice commands in Thai encountered slightly more significant obstacles in their implementation than in English, indicating possible difficulties in language processing. To summarize, the data indicate that both network technology and command type impact performance. However, overall, there is a high success rate in executing commands, particularly when using 5G connectivity and commands that do not experience delays or time-related issues.
The experiments revealed that the system’s ability to promptly respond to the “Set alarm on” command, regardless of the type of network connection, is a noteworthy discovery. The result in
Table 3 demonstrates button-command responsiveness and accurate results for intruder detection. The data table displays the outcomes of different Blynk notification experiments, including metrics for command execution on 4G, 5G, and Wi-Fi networks, as well as detection failures at different times of the day. The prompt occurrence of alarms upon receiving instructions was evidenced by the low AERT of button commands across various communication networks. It performed admirably regarding 4G, 5G, and Wi-Fi networks, respectively.
This finding holds considerable importance for real-world security applications, as it guarantees the prompt activation of alarm systems in reaction to potential intruders or security threats. This feature showcases the system’s reliability in promptly executing crucial user instructions, enhancing its effectiveness as an intelligent security solution. The primary conclusions derived from this dataset are as follows:
PIR detection with low and medium delays, as well as commands to turn on and off alarms, achieves a flawless success rate throughout the entire day, without any failed detection in the morning, midday, evening, or at night.
AERT-Wi-Fi typically provides the quickest response times for turning alarms on and off and for PIR detection with low to medium delays, followed by AERT-5G, and AERT-4G provides the most extended response times. This result may suggest that Wi-Fi offers a more responsive connection for the aforementioned tasks in the tested environment, which contradicts the anticipated faster speeds of 5G.
PIR detection experiences a substantial increase in response time, accompanied by a substantial delay of 5 s (AAID). This result is especially pronounced in the AERT-4G and AERT-5G setups, which have longer response times than AERT-Wi-Fi.
For PIR detection with a high delay, there is a notable number of detection failures at all times of day, with the highest number of failures occurring at noon (22 failures), followed by evening (17 failures), night (16 failures), and morning (18 failures). This result indicates that an increase in AAID consistently negatively impacts the system’s dependability over the day.
From the data, we can deduce that while the type of network does impact the response times for commands (with Wi-Fi often outperforming 4G and 5G in this respect), the AAID set for PIR detection exerts a more significant effect on the system’s reliability. Increased delays lead to a higher number of failures.
The insights gained from the IoT-based smart home system offer essential observations about the system’s responsive performance, underlining its adaptability and operational design features in various scenarios relating to wireless communication protocols and PIR delay configurations. This detailed analysis features the system’s capability to manage smart lighting controls through voice activation and identifying trespassers, key aspects of home automation powered by emerging IoT technology.
This study thoroughly analyzed the PIR sensor’s effectiveness in detecting intruders in real time. This study explored the sensor’s sensitivity and delay configurations, uncovering its versatility and the capacity for users to customize detection settings. Users can customize the system according to their precise security requirements by modifying the delay time from one to five seconds. The empirical results demonstrated the system’s adaptability, as different network communication modes, facilitated by the Blynk application and Google Assistant, impacted the system’s response times.
This study revealed that delayed PIR motion detection slowdown caused the overall increase in the system’s response times. This study presents comprehensive evaluations of different command types and internet wireless connection methods in the IoT-based smart lighting control system, as shown in
Table 2 and
Table 3. The evaluated command sets include Blynk button and voice-button commands, Google Assistant in Thai, and Google Assistant in English. Significantly longer response times were observed for Google Assistant commands, particularly in English, with certain instances lasting up to 7.5 s and multiple malfunctions being recorded.
Despite these challenges, the system exhibited impressive proficiency in assessing the detection capabilities using PIR motion sensors under different response delay settings, particularly in situations with minimal response times at low delay configurations. The findings emphasize the importance of enhancing the speed of voice command responses, especially for English commands, to boost user satisfaction and overall system performance.
Moreover, this research showcases the system’s efficacy in identifying intruders using PIR motion sensors under different delay situations, accenting its dependability in security surveillance. This in-depth analysis of the workings of an IoT-enabled smart lighting control and intrusion detection system confirms the system’s functionality and points out significant system components that need improvement, most markedly voice command processing and wireless network connectivity efficiency.
The system’s computational complexity is a critical factor to be considered in the advanced functionalities of the IoT system, including voice command processing and real-time PIR sensor-based intruder detection. By integrating numerous sensors on Raspberry Pi 4, communication protocols, and processing units, the system’s architecture is optimized to manage complex tasks efficiently. Nevertheless, the complexities associated with controlling numerous concurrent operations, particularly in extreme demand, may create considerable computational demands. The analysis reveals that the complexity of the tasks the system executes impacts its response time, which is otherwise relatively efficient. An example of this can be seen in the augmented response time for English voice commands, which indicates that language processing and interpretation require more computational resources. As a result, it is critical to maintain the system’s operational effectiveness by optimizing its computational architecture to manage these complex tasks more efficiently.
Data validation and security verification are additional critical components of the system’s architecture. Due to the critical nature of home security and automation systems, safeguarding data integrity and preventing unauthorized access are of the utmost importance. This study delineates the security protocols implemented by the system, which cover secure wireless communication channels and data encryption to protect against potential breaches. The PIR motion sensors and voice command interfaces are constructed with embedded security measures to ensure accurate data capture and prevent tampering. However, it is crucial to continuously adapt and update security measures to mitigate emerging threats and vulnerabilities, just as with any IoT system. The integration capability of the system with sophisticated security systems and protocols has the potential to considerably reinforce its resistance to cyber threats.
5. Conclusions
Our findings represent a significant leap in the development of IoT-based home automation systems, showcasing a functional and practical innovative system with potential real-world applications. As technology continues to advance, the quest to enhance convenience, reduce task duration, and strengthen security in daily life through such systems remains, highlighting the need for ongoing research and innovation in this field.
5.1. Theoretical Contributions
An IoT-based smart home framework for automation and intruder detection system was designed, developed, and assessed to support a comprehensive, responsive system. The proposed framework ensured the incorporation of components, such as Raspberry Pi 4, relays, PIR motion sensors, buzzers, and software, such as Google Assistant, Blynk application, Raspbian, and Node-Red. The comprehensive evaluation of command types and wireless internet connection methods contributes to the system’s capabilities by encompassing Blynk button commands, Blynk voice-button commands, and Google Assistant in multiple languages. The proposed IoT-based system offers the potential for substantial advancements in convenience, efficiency, and security surveillance in daily life. In addition, this study presents a novel and inclusive assessment of the effectiveness of the proposed IoT-based system in intruder detection, employing a meticulous approach to calculate AERT and AAID. The precision of intruder detection was systematically examined using different eco-friendly wireless communication modes and varied time periods that can be applied to assess the real-world usefulness of smart home security solutions based on IoT, particularly through accuracy and response time.
5.2. Practical Implications
Evaluating the response time of IoT-based smart home systems is critical due to its impact on system effectiveness and user experience. Home security depends on the system’s ability to recognize and counteract assailants. It is critical for a residential security system to have a quick response time, as it can prevent a security violation. Robust security solutions are predicated on the ability of the system to react to any suspicious activity promptly. Responses of various system components and parameters—in response to stimuli such as PIR motion sensor latency times, communication technology, or user interaction commands—depend on system response. Additionally, response time reflects system dependability. A dependable and stable system shows a consistent and rapid response time. In contrast, response times that fluctuate or are delayed may suggest challenges in the system’s design or implementation. Understanding the impact of configurations such as PIR motion-sensor delay settings on response time enables the customization of systems to meet the needs and conditions of the user. The flexibility of the IoT-based smart home framework renders the home system secure, effective, and adaptable to the requirements of users. With modifications adapted to the aims of a responsive experimental inquiry, the data were statistically evaluated with exactitude at consistent intervals.
The statistical data gathered during our study not only reveal impressive levels of accuracy and effectiveness in different wireless communication environments but also mark a significant achievement in the design and development framework of IoT-based home automation systems. The voice command recognition maintained an accuracy rate above 90%, demonstrating the system’s reliability even in varying network conditions under Wi-Fi, 4G, and 5G networks. Additionally, the PIR motion sensors showed consistent effectiveness across all tested communication modes, with intruder detection accuracy remaining high. These results validate the system’s robustness and adaptability to network conditions, ensuring user convenience and security in various technological circumstances. The implications of these findings are profound, potentially shaping the future of home automation systems.
5.3. Limitations and Future Work
While our comprehensive assessment of the proposed system has revealed its strengths, it has also highlighted areas where improvements can be made, sparking interest in future developments. The potential limitations discussed include IoT response time variability including voice commands, dependency only on wireless network communication modes, and the lifespan of PIR sensors. This study assessed response time variations for Google Assistant based on cloud-based translation technology, making voice commands take longer to process on wireless communication technology. This limitation concerns the system’s consistency and reliability that can be improved by advancing voice command processing processes, especially for non-native English speakers who have difficulty pronouncing English fluently. The impact of different wireless communication network modes on response times was also studied, with Wi-Fi generally outperforming 4G and 5G. However, the reliance on network connectivity poses a potential vulnerability, as disruptions or network failures may compromise the system’s reliability and services. Finally, PIR motion sensors have a finite operational lifespan. Continuous usage and exposure to environmental factors such as temperature variations, humidity, and other external conditions can impact the longevity and accuracy of sensors.
This roadmap for future research and development not only provides a clear direction for the field but also underscores the potential of IoT-based home automation systems. Given the findings of our study, advance design and development create numerous opportunities for enhancing IoT-based home automation systems in a sustainable way. Future research could support the real-world implementation of fail-safe mechanisms for hardware, system operations, network communications, and renewal electrical systems to enhance system robustness. Optimizing the energy consumption of IoT devices used in the system to lead more sustainable and eco-friendly solutions, expanding the system’s language capabilities, enhancing the user interface for broader accessibility, and incorporating advanced machine learning algorithms to further refine voice recognition and response times, adapting to user behaviors and preferences remain critical areas for development. Additionally, training in more algorithms can be performed using locally based multilingual systems and refining the user interface to make the system more accessible and user-friendly. User acceptance and trust, which are critical for the widespread adoption of IoT technologies in home automation, are supported by these enhancements and supplement the system’s technical sturdiness.