1. Introduction
The Internet of Things (IoT) has gained significant recognition and popularity since its inception as a network model by Ashton and Gamble in 1999. Its widespread adoption has been driven by the vast number of interconnected nodes, networks, and protocols that offer convenience and efficiency in various industries. However, the growing scale and complexity of the IoT ecosystem have raised significant security concerns [
1,
2].
In the IoT, physical objects are connected to enable them to exchange data, which then require analysis. Sensors in devices collect and store data in the cloud for examination, which both offer possibilities and pose problems, such as the difficulty of data extraction from devices with restricted capabilities. Privacy problems with the IoT have also emerged, and industries with academics are striving to overcome them [
3]. The number of IoT-connected devices is expected to reach an astonishing number above 75 billion in the coming years, and this has intensified the urgency of addressing the associated security challenges [
4].
At the core of the IoT ecosystem are fundamental elements such as sensors, computing nodes, receivers, actuators, and devices [
5]. The IoT framework consists of several layers, each of which serves a distinct purpose: the business layer, the application layer, the middle layer, the network layer, and the physical/sensor layer [
6].
These interconnected components work together to collect, process, and exchange data, thus enabling the seamless functioning of IoT systems. However, modern linked IoT systems encounter difficulties in terms of efficiently allocating their limited energy resources while maintaining a strong focus on privacy and security. Although centralized security solutions are commonly deployed, they may not fully meet the unique requirements of IoT systems, leaving them vulnerable to potential threats [
7].
Massive IoT refers to the potential scenario where networks support billions of connected devices and applications that interact at extremely high data rates, facilitating a major technological revolution with the implementation of diverse and advanced systems such as telepresence, virtual-reality devices, swarms of drones, autonomous driving, and biosensors. This extensive network of IoT devices, while enabling innovative services in many domains, also raises significant security concerns due to the vulnerability of devices and the importance of the information they carry, making protection against cyber threats a crucial challenge [
8].
To overcome these limitations, one emerging approach involves integrating the IoT with cognitive environments by leveraging cognitive technologies such as artificial intelligence and machine learning to enhance the capabilities of intelligent devices. Through the incorporation of cognitive capabilities, IoT devices can adapt to changing environments, optimize energy consumption, and offer advanced functionalities. Furthermore, this integration enables users to remotely monitor and interact with their IoT networks, resulting in improved efficiency and effectiveness [
9].
Ensuring safety and privacy via trust management is crucial [
10]. In addition, in industries where asset tracking is necessary, data immutability becomes a major concern [
11], particularly in IoT applications that involve direct interactions with humans. Examples of such applications include medical implants, smart gadgets, and autonomous cars, to name a few. It is essential to establish trust in order to promote confidence in these systems and to protect the privacy and safety of the user [
12]. However, IoT networks face various security and privacy risks, including distributed denial of service (DDoS) attacks, privacy breaches, false data injection, and data integrity issues [
1]. Previous researchers have proposed a limited range of solutions due to the lack of trust and transparency in data processing, which highlights the need for innovative approaches [
13].
Research scientists Stuart Haber and W. Scott Stornetta pioneered the development of blockchain technology in 1991 [
14]. In 2008, Satoshi Nakamoto introduced Bitcoin, a decentralized virtual currency that resolved data privacy issues in economic transactions. The blockchain, a distributed ledger offering security and transparency, has gained in popularity and has begun to serve diverse industries worldwide. It stores distributed records over a number of nodes, which allows users to access and verify transactions. Key functionalities include routing, storage, wallet services, mining, and recovery [
11,
15].
Blockchain technology, which was initially introduced as a means to prevent double-spending in digital currencies, has evolved to find applications in diverse fields such as the IoT, logistics, and healthcare [
16]. The inherent benefits of the blockchain, including the immutability of append-only chained data, a decentralized and non-changeable ledger, the absence of third-party involvement, transparency, and cryptographic security, make it a promising solution to address the IoT security challenges described above [
17,
18].
Among the various types of blockchain frameworks, such as public, permissioned, permissionless, and private, Hyperledger Fabric stands out as an enterprise-grade solution. Hyperledger Fabric is a private and permissioned blockchain that offers modularity, scalability, and a flexible permission model and is suitable for IoT deployments. Unlike public blockchains, permissioned blockchains such as Hyperledger Fabric restrict content publication to selected nodes, where access is controlled by a third party that manages user privileges [
19,
20]. This makes Hyperledger Fabric an ideal choice for meeting the specific security and privacy requirements of IoT applications.
The authors of [
21] introduced two new concepts:
The storage of sensor data off the blockchain, keeping only the sensor ID and the transaction details on a local blockchain.
The use of “RESET” transactions that move local blockchain data to free up storage and store the hash on the global blockchain (GB) for data integrity.
These concepts can be used to connect local blockchains to the GB, which ensures data integrity and has its own chaincode and policies. Overall, they can improve scalability and efficiency in terms of data storage and transaction management.
The authors of [
22] discussed a system configuration that included a root server, Hyperledger Fabric, and multiple users. They outlined the registration and verification process for users as agents and highlighted the roles of different certificate authorities. Their system allowed for the creation and management of multiple groups, with periodic monitoring and agent changes for stability and security purposes.
The article in [
23] introduced a new architecture that used blockchain technology to enable interactivity among IoT devices. This architecture had four blocks, consisting of the sensors, the web service, the Ethereum blockchain (ETH), and the users and administrators. This system was shown to operate successfully under various conditions, and the secure and efficient use of the blockchain was showcased. However, its drawbacks included a reliance on a private ETH blockchain with low transaction processing capacity, the high cost of implementation in a public ETH blockchain, and a lack of encryption, privacy, and security on the device side.
In [
24], the authors focused on the integration of IoT systems with a private blockchain deployed on an ad-hoc IoT network. The choice of a private blockchain was motivated by its advantages, which include a lower node count and reduced power and resource consumption. The study described the establishment of an Ethereum-based private blockchain on top of the network, with each IoT device utilizing the Ethereum execution client (Geth client) to form a full blockchain connection with other nodes. This research aimed to assess the performance of an integrated IoT-private blockchain system, with a specific focus on the connections between the IoT devices and the underlying network.
In another article [
25], the authors examined the benefits of utilizing off-chain data storage and conducted a comparative analysis of the associated gas costs in Ethereum (ETH) for each transaction executed with a smart contract deployed on the Ethereum blockchain. They highlighted the importance of pre-processing in the fog layer and described the process of creating data chunks, which was governed by policies set by the administrator. Users could access these chunks through the blockchain, and smart contracts were utilized for validation purposes. However, several drawbacks were identified, such as the use of the ETH blockchain, leading to a low TPS rate, and the absence of a specific data structure for managing data chunks.
The goal of this research is to improve the security and efficiency of the Massive Internet of Things (MIoT) by developing a cohesive, four-layered IoT blockchain infrastructure. This method combines IoT devices with Hyperledger Fabric, a private and permissioned blockchain, to provide a secure, decentralized ledger for data transfers. the aim is to optimize data processing and secure storage inside this framework, solving issues like latency by using proper chaincode through hyperledger fabric and scalability by adding an off-chain data structure. To analyze the system’s scalability, security, and efficiency, we use data validation through trials in diverse IoT domains. This strategy represents a big step forward in solving the collective difficulties of MIoT security and data management.
In the next section, we focus on the connection between IoT devices and the blockchain. We explore the best four-layered architecture for IoT deployment and resolve the problems associated with performance and storing IoT data on the blockchain. In
Section 3, we present the findings of the integration between the blockchain and the IoT platform, elucidating its implications and consequences in the context.
Section 4 presents an in-depth assessment of the features of the proposed platform, highlighting its advantages and beneficial outcomes. In the final section, we summarize the most important results and conclusions of this study.
2. Materials and Methods
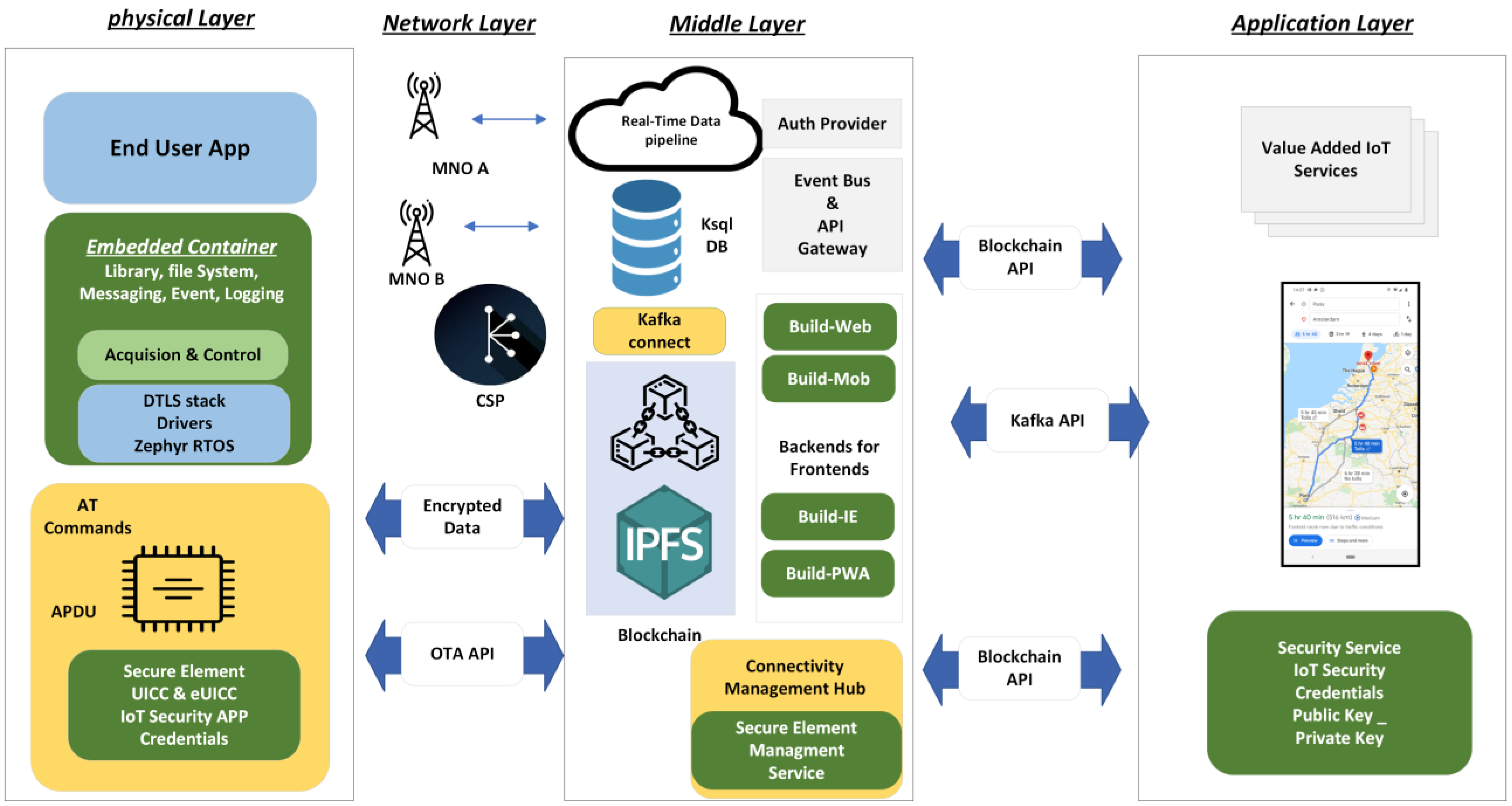
We developed a comprehensive four-layer architecture with the specific aim of establishing connectivity between various IoT devices and end users. This architecture can provide a robust and efficient framework for integrating IoT devices into everyday applications. In this simplified overview, we consider a wide range of such IoT devices, including sensors, cars, smart city infrastructure, and even sensors from aircraft.
Table 1 briefly outlines the four essential layers of an Internet of Things (IoT) architecture, ranging from physical IoT devices and sensors at the first layer, through network protocols, and data processing, up to end-user applications at the fourth layer. Each level plays a vital role in ensuring integration and functionality within the IoT ecosystem.
Figure 1 provides a comprehensive illustration of the four-layer architecture, detailing the various technologies utilized to ensure its complete functionality.
2.1. First Layer (Physical Layer)
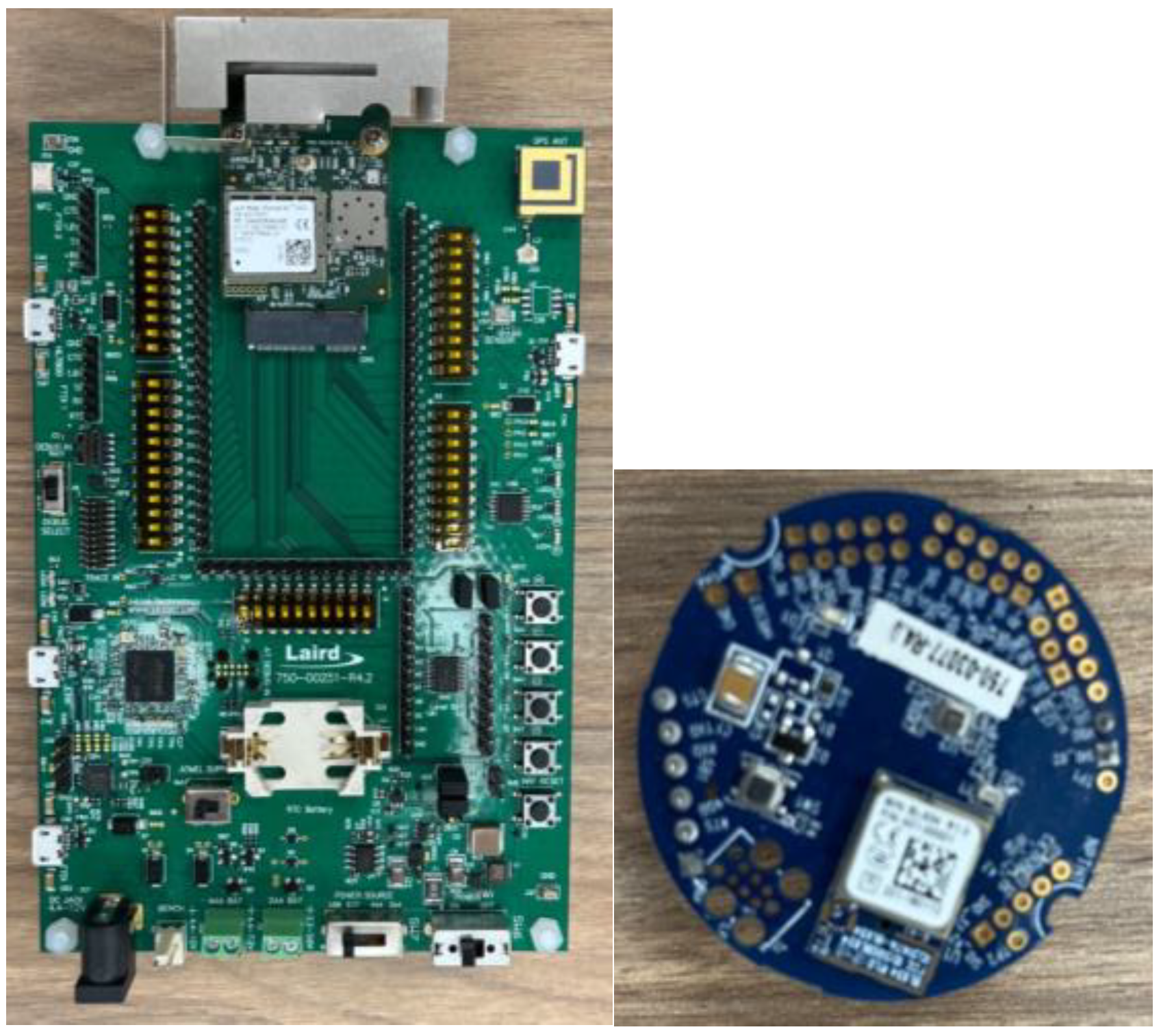
The physical layer in an IoT architecture involves a wide range of devices that enable the collection and sensing of data. In our specific implementation, we utilized the Laird connectivity device combined with Nordic RF Silicon, the BL654 model as the sensor. For the gateway functionality, we used the Pinnacle™ 100 DVK, devices from Laird Connectivity manufacturing company in Akron, OH, USA, which is equipped with a SIM card for connectivity.
To facilitate data transmission within the physical layer, we employed Bluetooth technology as the communication protocol. This allowed the sensors, represented by the BL654 model, to send their data efficiently to the Pinnacle™ 100 DVK.
Table 2 provides a comparative analysis of devices considered for gateway purposes. We selected the Pinnacle™ 100 DVK due to its low power consumption, inherent cellular connectivity, and additional features.
At this layer, we considered three specific types of sensors: humidity, pressure, and temperature; however, it is important to note that the versatility of IoT systems enables the integration of various other types of sensors depending on the specific requirements of the application. This flexibility allows for the incorporation of a diverse range of sensor technologies that can cater to a wide array of use cases and scenarios.
Figure 2 The Pinnacle™ 100 is prominently featured on the left side, offering a sharp and detailed visual portrayal. Concurrently, the BL654 sensors are presented on the right side of the image.
2.2. Second Layer (Network Layer)
The network layer plays a crucial role in facilitating the transfer of data from the first layer (IoT devices) to the third layer (middle layer). It serves as the communication bridge between these layers, and various technologies can be employed to ensure efficient and reliable data transmission.
In our experimental setup presented in
Figure 3, the second-generation Nutaq PicoLTE was used as a software-defined radio-network-in-a-box. This served as a versatile and powerful simulator, allowing us to create and emulate an LTE-based network environment for our IoT experiments, and facilitating the simulation and evaluation of the proposed IoT system. The Nutaq PicoLTE also allowed for the configuration and customization of various network parameters, such as signal strength, bandwidth, and interference, meaning that we could mimic real-world network conditions.
One notable aspect of our experiment was the use of LTE-M technology for data transmission from the IoT devices to the third layer, which served as the access network. This offered efficient and reliable connectivity for IoT devices, enabling them to transmit data over long distances while consuming minimal power.
Table 3 shows a few characteristics and supporting features of the Nutaq PicoLTE.
2.3. Third Layer (Middle Layer)
In the proposed architecture, the middle layer is responsible for handling and processing the data generated by the IoT devices. This layer will monitor and handle activities such as data storage, administration, and processing. Data storage enables the effective organization and retrieval of enormous volumes of IoT data, whereas data administration includes the management of data input, translation, and aggregation while ensuring data quality and dependability. Data processing entails leveraging technologies to execute activities such as analytics, machine learning, and real-time decision-making. The middle layer enables the smooth integration and use of IoT data for a variety of applications.
In this layer, it is proposed to use Kafka which would play a pivotal role as a powerful real-time data streaming pipeline for smooth data transfer to the blockchain. Kafka’s capabilities were leveraged to ensure that the data generated by the IoT devices were efficiently collected and effortlessly transmitted to the blockchain network.
The blockchain, which resides in this layer along with the database, serves as a decentralized and secure ledger. It ensures the integrity and immutability of the data by storing hashed representations of the transmitted information. We employed an off-chain storage solution, with just the hash of this data maintained on the Hyperledger Fabric blockchain. This method dramatically decreases ledger size while retaining the blockchain network’s efficiency and speed. We assure data integrity and speedy verification processes, since the on-chain hash may be used to authenticate the validity of the whole data stored off-chain. Using Hyperledger Fabric’s features, such as private channels and chaincode, enables greater optimization and control over data management, resulting in a balanced and efficient system that adheres to security and decentralization principles.
In the specific implementation described here, the InterPlanetary File System (IPFS) was chosen as the database solution. IPFS offers a distributed and decentralized storage system that complements the characteristics of the blockchain. However, it is important to note that other proprietary databases such as MongoDB and MySQL could also be used within this layer, depending on the specific requirements and preferences.
Apache Kafka acts as a bridge, receiving data from devices and efficiently transmitting it through the pipeline to the database. We use a smart data transformation strategy to manage the massive data volumes generated by IoT sensors. We start by collecting raw data from sensors, which are typically vast in volume. This raw data is subsequently processed, resulting in a considerable reduction in bulk. Finally, we produce the collected data into usable insights, minimizing data quantity while maximizing value. This simplified technique assures efficient storage, rapid data access, and relevant results, successfully overcoming the issues of handling enormous data volumes.
Figure 4 provides a visual representation of the various data types being stored and illustrates the corresponding volume of data at each stage.
2.4. Fourth Layer (Application Layer)
In the IoT architecture, the responsibility of the application layer includes data visualization and processing, as well as supporting firmware upgrades. In a smart device ecosystem, for example, the application layer may analyze sensor data, produce visual representations of the performance of devices, and provide a user interface for initiating firmware upgrades. Firmware upgrades guarantee that devices are equipped with the most recent features, security fixes, and performance enhancements. Users can easily upgrade firmware via the application interface, allowing for smooth device maintenance and feature enhancement. In the IoT ecosystem, the application layer therefore helps with both data visualization and firmware management.
User authentication is essential in this layer to enable communication with the blockchain with the proper data owner. A two-layer authentication mechanism was used in this case to ensure safe access. The first layer handles initial user authentication, which can securely store user profiles and information such as usernames, passwords, email addresses, etc. The second layer relied on the blockchain’s built-in authentication procedures. It has been specifically designed to interact with the blockchain. After the user’s credentials have been verified by the first layer, the process advances to the second layer, which has the responsibility to handle any requests from the blockchain. The built-in authentication method included in our platform makes use of JSON Web Tokens (JWTs), which are produced securely utilizing a pair of public and private keys. These keys are created randomly, resulting in a secure and distinct key for each instance. The length of the phrase in our deployment varies from 13 to 17 words, providing enough complexity and security.
Each user is given a unique phrase to get their own keys, ensuring a safe and personalized experience. This method is critical to the operation of our crypto wallet. We took the effort to create our own wallet, which has been rigorously built to store and preserve these sensitive credentials, assuring the secure storage of user credentials. To authenticate the user’s identity, both layers can execute authentication. The type of data shown to the user is governed by their unique requirements and access credentials.
This layer acts as the user interface for communicating with the blockchain, letting users submit and receive requests. The data are visualized on a web page to create a more user-friendly experience, fully secured, decentralized and immutable.
2.5. Data Flow in the Proposed Architecture
In this section, we will discuss the data flow through the deployed massive IoT platform.
Each user was assigned a unique public and private key, and RSA 2048-bit encryption which is a robust encryption standard that ensures the security of the key pairs used. For each public-private key pair, we used a JSON Web Token (JWT) with RSA-based encryption that can be verified by parties who have access to the public key, ensuring the authenticity of the token. The Hyperledger-Fabric Software Development Kit (SDK) was employed to validate the JWT to ascertain the integrity of the data.
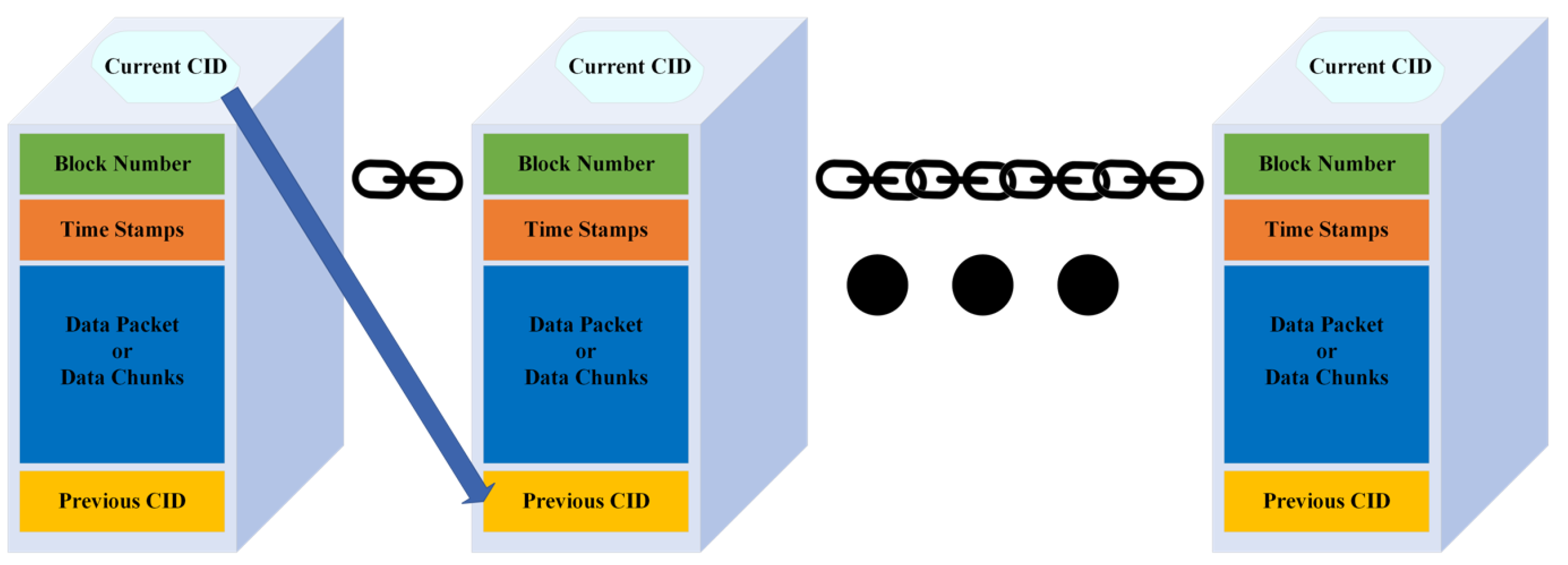
We developed a specialized data flow procedure that consisted of multiple phases to assist in the secure and quick transfer of data from each sensor to the blockchain. The data from all sensors of each user were then converted into larger blocks containing many bits of information, such as the time of creation of the block, the processed data, and the IPFS Content IDentifier (CID) of previously inserted blocks to IPFS.
In the proposed scheme, each block is connected to the CID of the preceding block added to the IPFS, in order to guarantee the consistency and security of the data, and the first block (or ‘genesis block’) is given a CID of zero. This procedure helps to maintain the sequential order of the data and ensures that any changes or efforts to alter the data are readily discernible.
Figure 5 illustrates how data blocks are interconnected in a chain, enhancing their immutability, and details the contents of each block.
This creates a unique information chain for each user. Users may have several gateways and sensors associated with these gateways, each with their own information chain. Notably, this chain is stored separately from the main blockchain on IPFS. The CID of each block, on the other hand, is stored on the blockchain, connecting the two systems.
Figure 6 shows every user maintains an individual chain, which is accountable for managing data originating from that specific user.
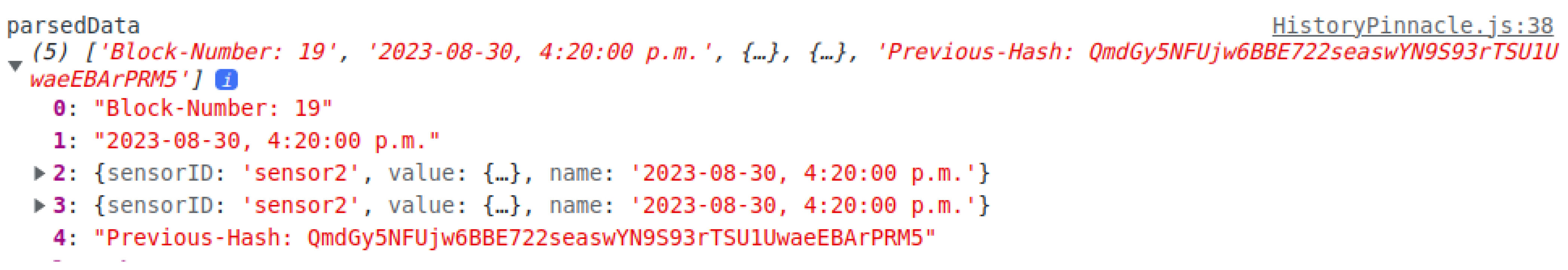
Once the blocks have been produced and contain all the required information, they are sent to IPFS for storage. The data are then given a distinct CID with a length of 53 characters, which remains unaffected by the volume of the data. This CID acts as a permanent record of the data as it appeared at the time, allowing it to be readily traced and accessed. Here’s a sample CID: Qmbt153PLWidJEv2PBMHDiLLBxQo3N14MbagEveQnK5EM5ZYv1. Each block of data possesses the capacity to incorporate readings from numerous sensors. The dimension of the data is directly proportional to the congestion observed within the network.
Figure 7 depicts real-world scenarios. In this example, the quantity of collected data is 2.
Finally, the entire CID is transmitted to the blockchain, which allows for efficient and safe contact between devices. This data structure allows us to operate independently of the number of users; it scales efficiently, focusing solely on the users’ count. We encrypt the data throughout the entire transfer using the provided public and private keys for each of the entries. This ensures the privacy of the data and allows us to verify its integrity.
Overall, this flexible data storage, which we may alter relying on the scenario and the congestion of the network, also the transmission mechanism provides a secure and fast transfer of data from sensors to the blockchain. This guarantees the security, anonymity, and accessibility of data, maintains the network’s scalability, and helps us to handle large volumes of data or massive IoT devices.
3. Experiment, Results and Analysis
In this section, we present the results from the performance evaluation of the proposed Massive IoT architecture using our blockchain and chain code. To assess these aspects, we use Hyperledger Caliper (
https://hyperledger.github.io/caliper/ accessed on 5 September 2023), a reliable benchmarking tool that was designed to measure the efficiency of blockchain implementations using a predefined set of use cases.
Hyperledger Fabric’s performance is closely tied to the hardware utilized. Enhanced equipment typically yields improved outcomes. For the purposes of this experiment, we utilized a MacBook Pro featuring an M2 Pro chip, detailed by the following specifications:
Hyperledger Caliper operates through worker processes, each of which is responsible for generating the workload independently of the others. This design allows for efficient workload generation, even if a particular worker process reaches the capacity limit of its host machine. By employing multiple worker processes across various machines, we can further enhance Caliper’s scalability and overall workload rate.
The architecture has been designed to be independent of the number of devices, focusing instead on the number of users. This means that each transaction is associated with a user, who may have multiple devices linked to their account.
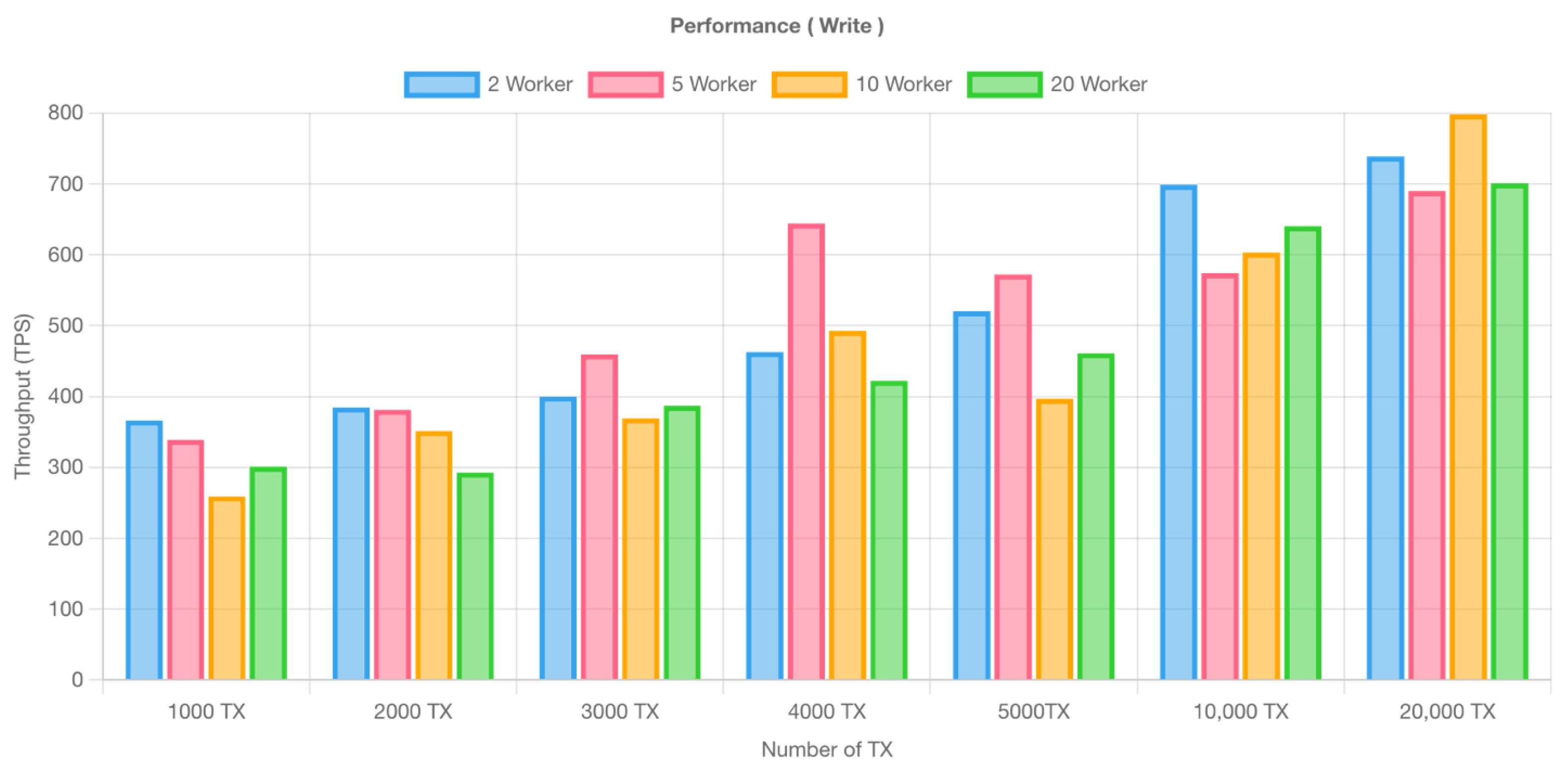
Figure 8 and
Figure 9 show that the throughput ranges from 366.4 TPS to a peak of 798.3 TPS. As the TPS increases, there is a corresponding rise in the transaction failure rate, which reaches 7% when the number of workers is increased to 20 and the network is handling 20,000 transactions.
To address this challenge, we can leverage the advantages of the data structure proposed earlier. By regularly monitoring the performance over time, we can dynamically adjust and optimize the data size within our data structure. This approach aims to strike a balance between the throughput and transaction success rates, thereby ensuring more stable and efficient overall performance.
Figure 8.
Transaction throughput (TPS) of hyperledger-fabric.
Figure 8.
Transaction throughput (TPS) of hyperledger-fabric.
Figure 9.
Inquiry performance of hyperledger-fabric.
Figure 9.
Inquiry performance of hyperledger-fabric.
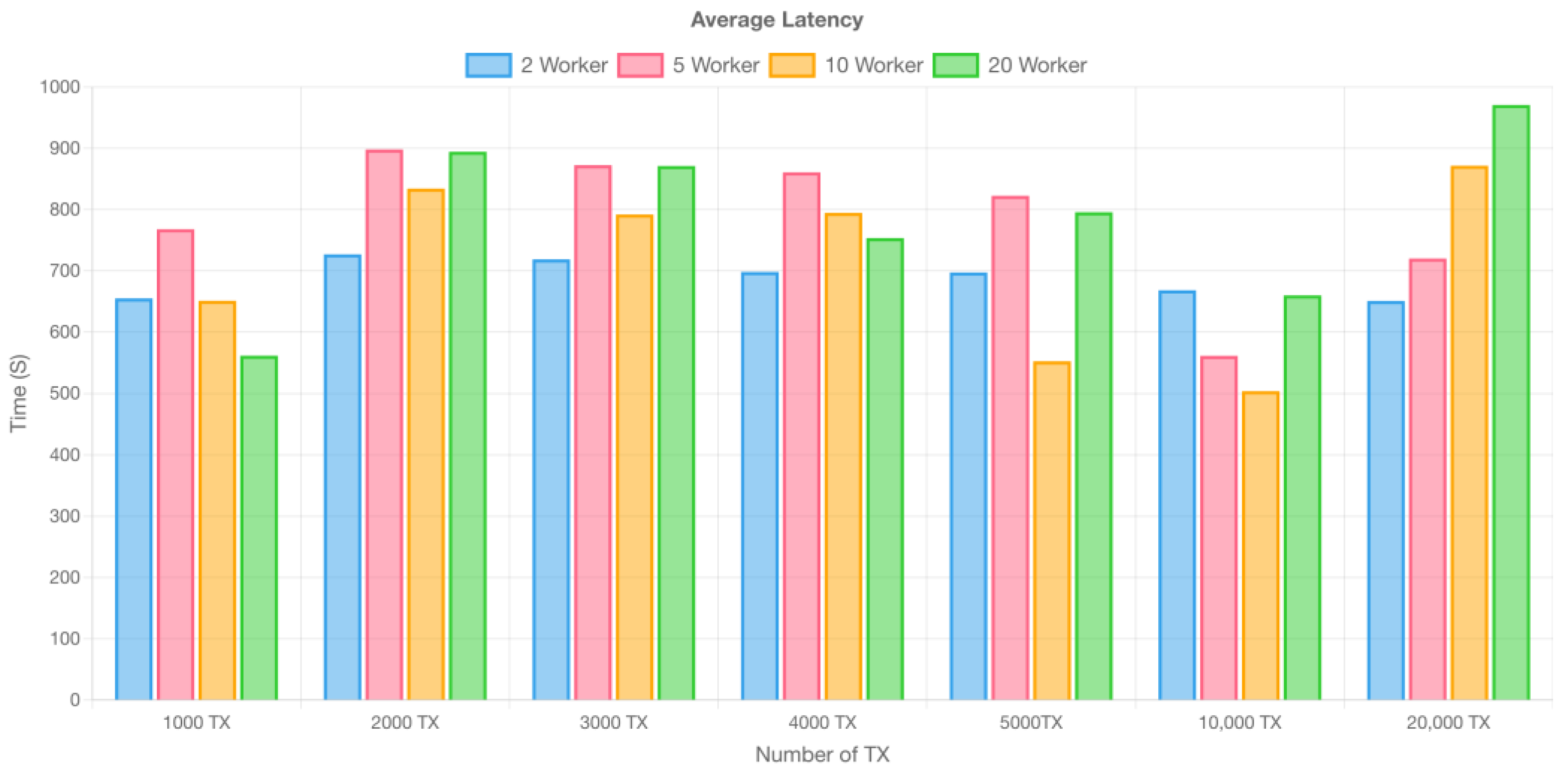
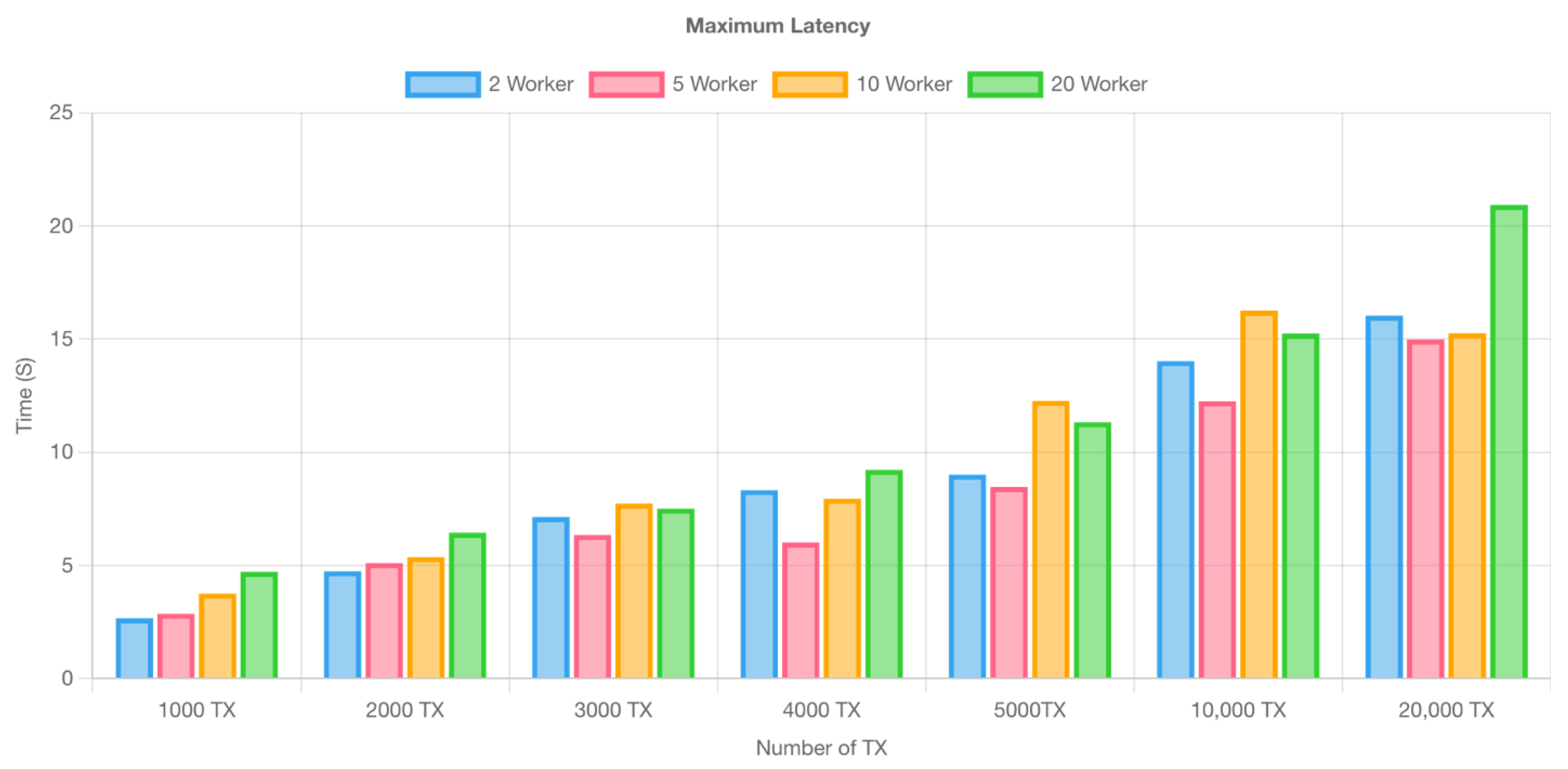
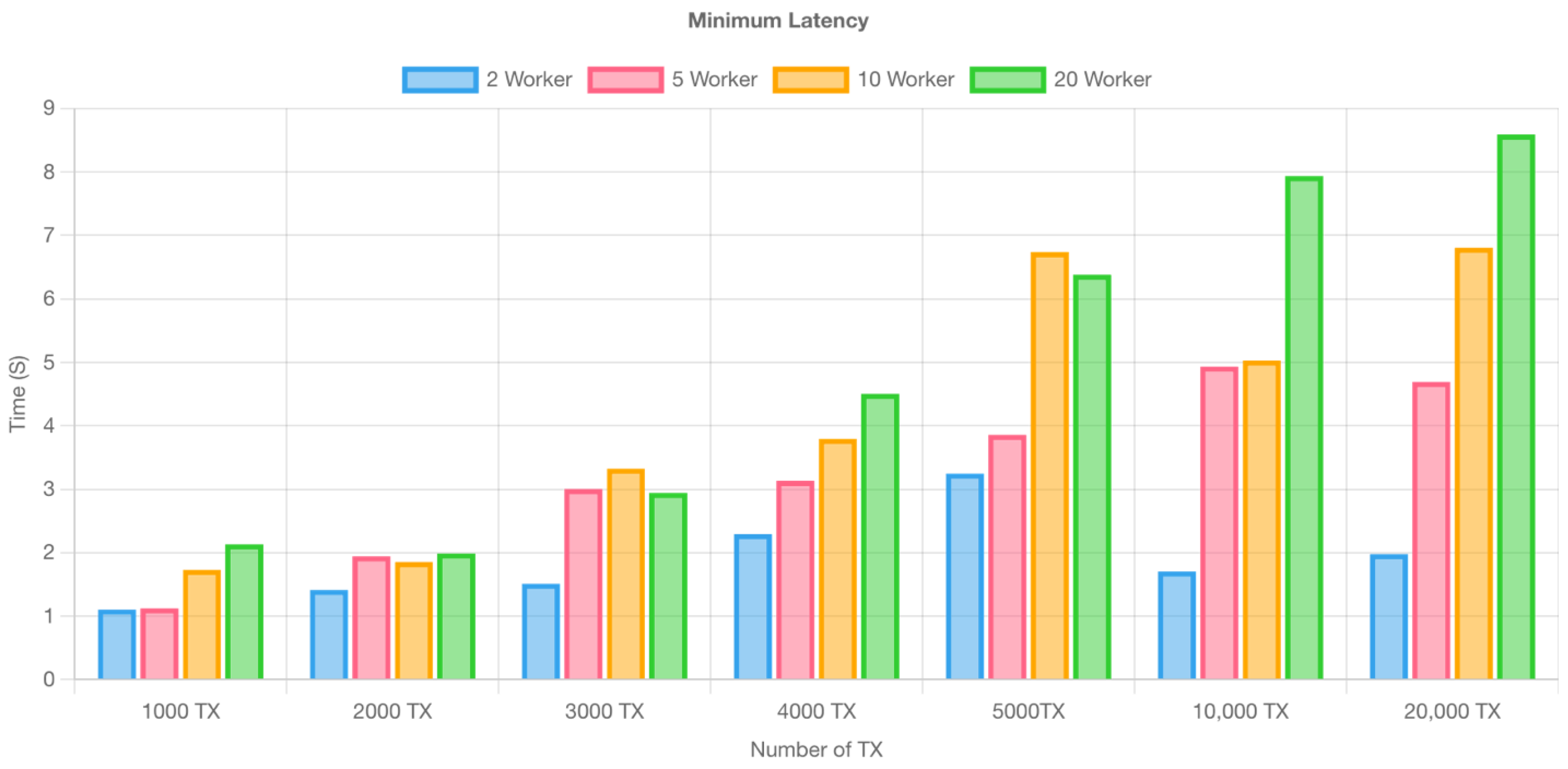
Figure 10,
Figure 11 and
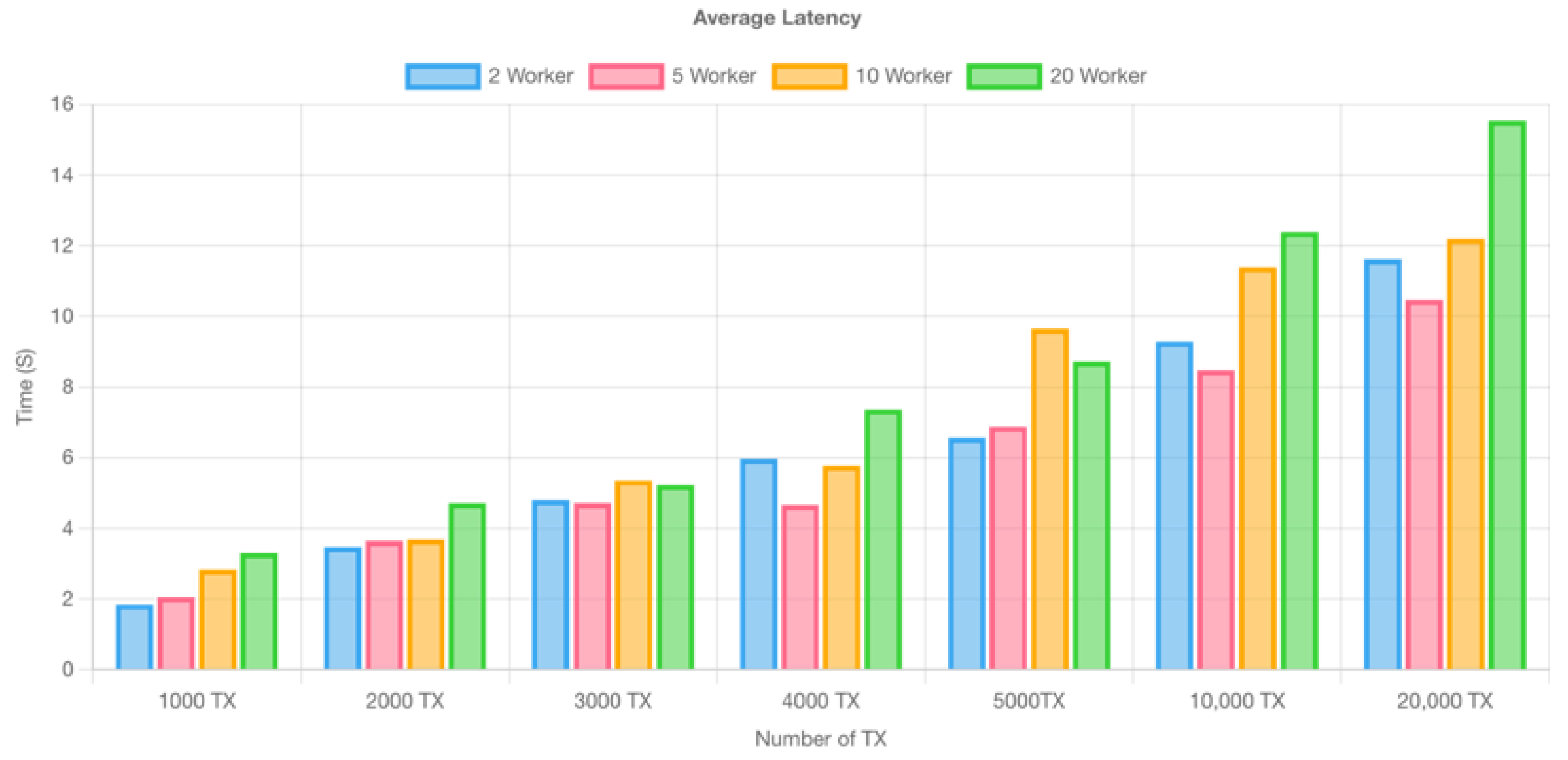
Figure 12 show the latency of Hyperledger Fabric, which is divided into minimum, average, and maximum values. Minimum latency displays the network’s best efficiency, maximum latency determines imaginable congestion, and average latency provides a balanced perspective of general performance, administering in thorough Hyperledger Fabric performance examination and optimization.
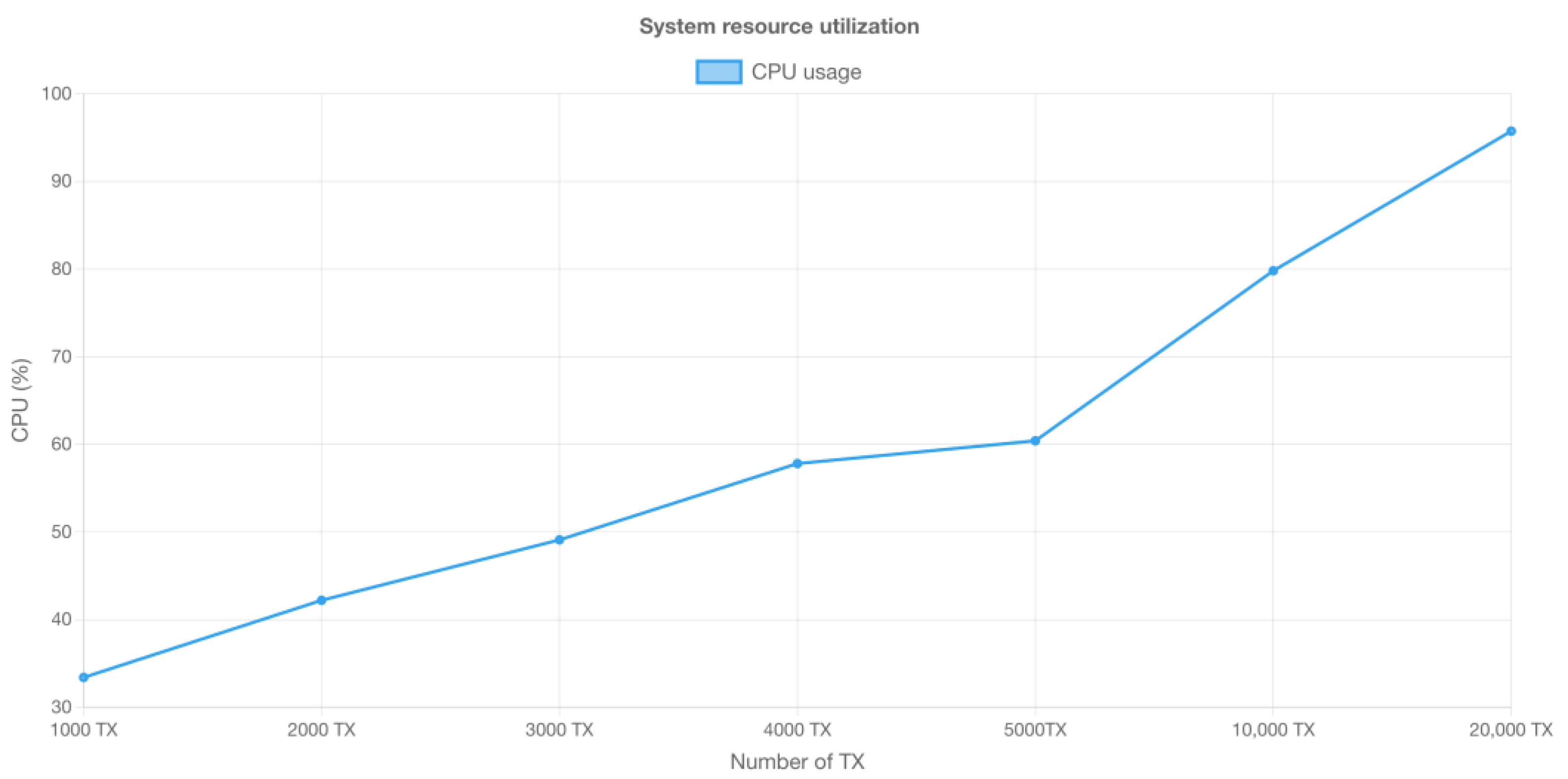
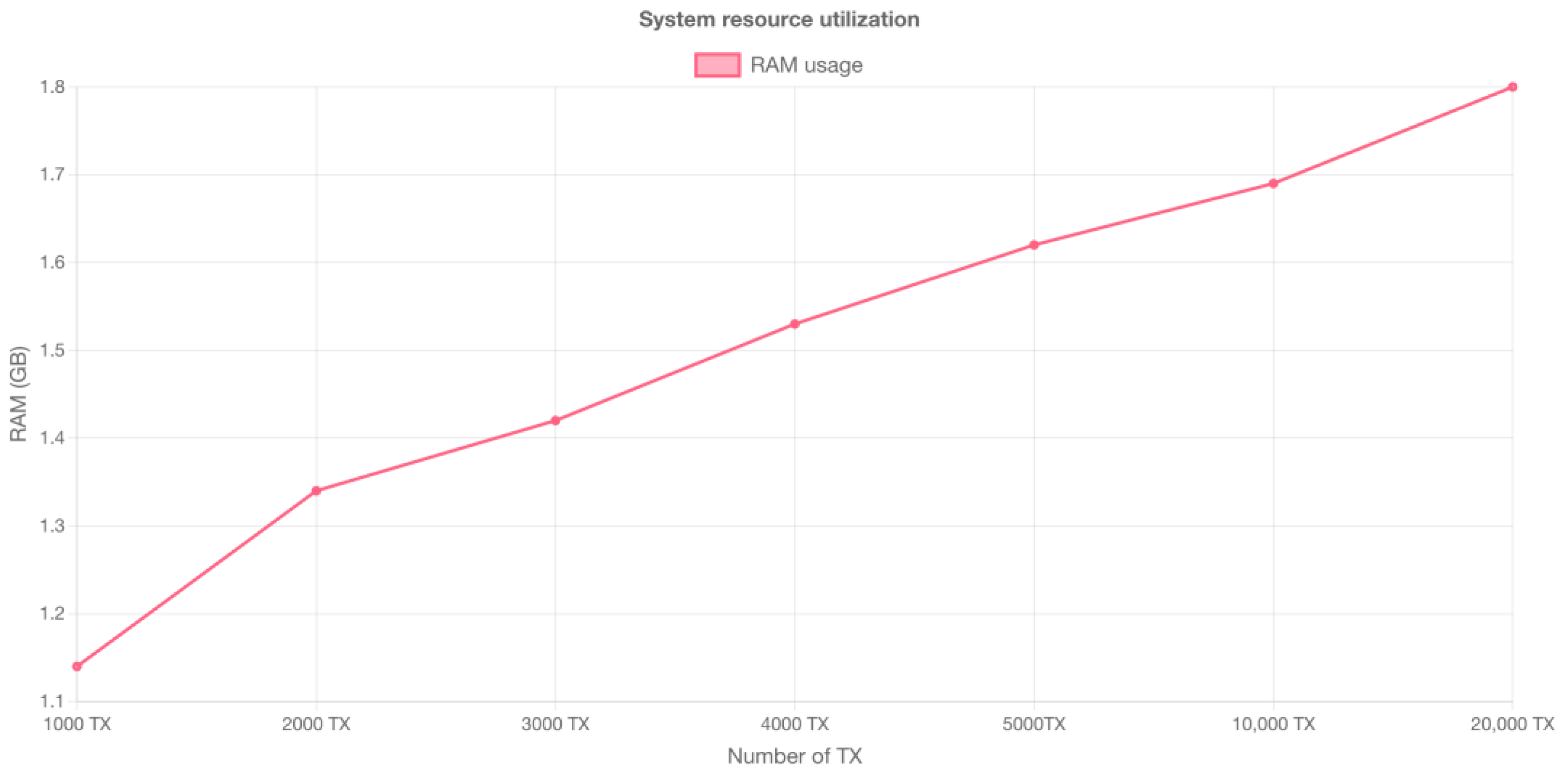
Figure 13 and
Figure 14 show the resource utilization during a single round of transactions performed by Hyperledger Caliper. The graphs allow for critical insights into CPU and memory usage. These metrics offer a comprehensive view of how efficiently the system manages its resources during transactional activity.
As transaction volumes grow, we witness an increase in CPU and RAM usage, with the CPU undergoing a significant pinpoint. This pattern implies that higher transaction volumes set a powerful pressure on the CPU, potentially endangering system overload and performance issues. To ensure smooth operations, it is important to regularly monitor and optimize system resources, adopting a proactive approach to system maintenance. By doing so, we can actually manage CPU usage and maintain stable performance, even as transaction requests increase, potentially exploring scaling solutions to accommodate the increasing load gracefully.
Figure 10.
Maximum latency of transactions in hyperledger fabric.
Figure 10.
Maximum latency of transactions in hyperledger fabric.
Figure 11.
Minimum latency of transactions in hyperledger fabric.
Figure 11.
Minimum latency of transactions in hyperledger fabric.
Figure 12.
Average latency of transactions in hyperledger fabric.
Figure 12.
Average latency of transactions in hyperledger fabric.
5. Conclusions
This paper has presented a novel database-based blockchain using Hyperledger Fabric, with a four-layer architecture, which can effectively address data security and privacy concerns. The integration of Kafka as a streaming pipeline also gives enhanced overall system performance, and the introduction of a new flexible data structure has been shown to be instrumental in improving the efficiency of the platform.
We have successfully linked an enormous amount of IoT devices with blockchain technology, creating a data structure that allows the platform to scale regardless of sensor count. Instead, scalability is directly related to the quantity of users. We have 20,000 registered users on the platform thus far. Despite current numbers indicating a high level of resource consumption, the platform retains solid security, ensuring good device management and monitoring. Our findings suggest that our solution, which employs advanced architectures and data formats, effectively addresses Hyperledger Fabric’s scaling difficulties. This integration represents a significant advancement in the development of secure and scalable IoT blockchain networks, and it contributes to greater scholarly conversation on this subject.
In the next phase of this study, we will focus on building an algorithm that allows for easy performance verification and dynamic modifications to the volume of data that is saved and communicated between the database and the blockchain. This dynamic adaptability is essential for maintaining high performance and ensuring the long-term success of the system.
We predict that by applying this technique, we will be able to achieve even higher levels of efficiency, scalability, and reliability in database operations, thereby opening new opportunities for real use cases in a variety of sectors. Our findings have the potential to significantly enhance the field of blockchain-based databases and pave the way for future advances in safeguarding sensitive data and improving system performance.