1. Introduction
The Internet of Things (IoT) is a rapidly growing network of interconnected devices that communicate with each other to perform various tasks. As the number of IoT devices increases, so does the need for secure communication between them. Cryptography is an essential tool for securing IoT devices, and secret sharing schemes are one of the most promising cryptographic elements for IoT. For example, the Datachest application encrypts and stores sensitive data in commercial cloud storage systems using secret sharing [
1]. The application uploads the data in encrypted form, and cryptographic keys are divided into shares. Each cloud receives one share, and this solution improves the security of users’ sensitive data in the cloud. In this paper, we identify the importance of applicability of secret sharing schemes to IoT, and pay particular attention to the value our proposed distribution design may introduce through frameproofness of the underlying scheme in such applications as well as possibilities for integrating multiple or multi-level systems without complete loss of distinction of the underlying individual systems.
A secret sharing scheme is a useful tool in modern cryptography. They are distinctive in distributing a secret amongst multiple devices, ensuring that no single device has access to the entire secret. This makes secret sharing schemes ideal for IoT applications where multiple devices need to work together to perform a task. For example, in a smart home system, multiple devices such as sensors, cameras, and smart locks need to communicate with each other to provide security and convenience to the homeowner. In secret sharing-based IoT (SBIoT), each cloud server is given a share constructed using a secret sharing scheme. A collection of servers can reconstruct the secret provided that they satisfy the reconstruction criteria of the underlying scheme (instead of privately owned keys in encryption-based schemes). Such a scheme enables processing without the need of decryption. Energy efficiency refers to the total energy consumption of an IoT network, which affects the lifetime of a network [
2]. It is well-known that use of a ramp-type scheme improves the security and energy efficiency in SBIoT networks [
3]. It provides better security against various types of attacks, including replay attack, modification attack, selective forwarding attack, and data leakages when a passive attacker is encountered. These benefits contribute to enhancing the overall security and performance of data transfer in SBIoT networks. Using a threshold scheme enhances personal information protection for eID cards by not storing any personal information per se in the card [
4]. Instead, sensitive personal information is divided into two parts for distributed storage in the client and the eID card. This ensures safety even when eID cards are lost because none of the original information can be figured out from a single secret share. With this structure, no information whatsoever on the original can be known from only the secret share in the card.
Consider b players and a positive integer . Suppose a dealer distributes a secret to these b players such that any collection of players can reconstruct the secret with their shares, but no smaller collection of players can do so. This is called a -threshold secret sharing scheme with threshold . If the dealer distributes shares to b players such that any collection of players can reconstruct the secret but no collection of or less players can do so (for ), then it is called a -ramp scheme. Thus, if , then it is a -threshold scheme. In this paper, we shall present a repairable ramp scheme, which we call a tensor design.
Secret sharing schemes also play a crucial role in ensuring secure data storage within cloud environments. These schemes involve the division of data into multiple shares, which are then stored on different servers. This approach provides a safeguard against any potential compromise of a single server, thereby maintaining the security of the data. In [
5], the authors present an exploration of the comparative performance of Shamir’s secret sharing algorithm [
6] and Rabin’s IDA [
7] within a private cloud framework utilizing the OpenStack cloud infrastructure. The experimental results indicated that Shamir’s secret sharing algorithm outperformed Rabin’s IDA in terms of generating the shares and reconstructing the data. However, Rabin’s IDA exhibited a lower storage overhead when compared to Shamir’s secret sharing algorithm. These findings underscore the importance of considering various factors, such as generation time, reconstruction time, and storage requirements, when selecting an appropriate secret sharing scheme for secure data storage in cloud environments.
In their 2019 work, Stinson and Kacsmar [
8] demonstrated non-ideal secret sharing schemes stemming from an ideal scheme (viz. Shamir scheme) as the base scheme. They presented a distribution design which was a threshold scheme with the ability to repair lost shares with a certain probability, and secure against any adversary with lesser players than the threshold. Our work further generalizes the domain over which our distribution designs are defined, in addition to providing it with easier secret reconstruction and share repairability, and securing it in more than one context. In short, we revisit the combinatorial design and some of its key properties first.
1.1. Combinatorial RTS
Consider the problem of securely reconstructing the lost share of a player by that player and a subset of the other players. A combinatorial solution to this problem was proposed by Stinson and Wei [
9]. These schemes are termed
combinatorial RTS. A
repairable threshold scheme (RTS) is a
-threshold scheme in which a subset of players can repair another player’s share in the event that their share is lost or corrupted, without the participation of the dealer who set up the scheme. The repairing protocol should not compromise the (unconditional) security of the threshold scheme.
1.2. A Drawback and an Idea of Extension
The combinatorial model proposed so far produces shares that are in a finite field
. Whether we can extend this notion to an integer ring is the first question. In this work, we propose a method to construct a distribution design with entries from an integer ring, thus generalizing the domain. We further show that this is a ramp scheme and consequently give a method of secret reconstruction for it, which is significantly easier in comparison to [
8]. The size of the authorized coalition that can recover the secret is significantly reduced in our framework. Example 3 will demonstrate the fact.
Repairability Problem
Techniques from network reliability theory are heavily used in reliability studies of these combinatorial repairable threshold schemes in a setting where players may not be available to take part in the repair of a given player’s share. Reference [
8] deals with the problem of reliability of such schemes and reconstruction of secrets and repairing shares without participation of the dealer.
The scheme proposed in this paper produces a far more efficient share repairability, which is possible due to the generalized domain, and based heavily on the easier secret reconstruction mentioned beforehand.
1.3. Frameproofness
Moving forward with the concept of repairing shares, another similar possibility was recently explored, called framing. Instead of simply specifying the minimum size of a set of players that can access the secret, suppose the dealer defines the share distribution through some other process. Say (where denotes the power set of the set of all players ) such that any coalition of players can access the secret if and only if (thus, in a Shamir scheme, if and only if ). If maps to 1 through f, then is called an authorized coalition; if it maps to 0, then is an unauthorized coalition.
Given such an
access structure over a secret sharing scheme, suppose a coalition
of players can gain information about the share of a player
dishonestly. Then
can wrongly accuse
P of releasing information about the secret that only
is not authorized to access, i.e.,
can
frame P. Framing a player (or players) evidently undermines the security of any secret sharing scheme, as it allows a group of players to access extra information about the secret illegally. Thus, it is imperative to limit such capabilities and/or size of any such coalition when constructing a combinatorial RTS. The concept of frameproofness was examined by Desmedt et al. in their recent paper [
10]. In this paper, we improve the extension scheme so that no framing is possible for any coalition of smaller size than the threshold. The question of what can be the minimum size of a coalition that can frame a player under this modification currently remains open.
2. Results
In this paper, we first introduce an operation, the Krönecker product of two matrices, extendable to a Krönecker product of two BIBDs. Following up with some properties of this operation, we present methods to solve two inherent problems with Krönecker products; firstly, the operation does not produce a BIBD from two BIBDs, and secondly, we resolve the issue of uniqueness that arises with the introduction of this operation. Our next theorem deals with the existence of secret reconstruction, which we prove by producing an algorithm. A probabilistic proof is given next.
An immediate consequence of our results on the new scheme is its extendability to multiple BIBDs. We discuss it briefly though a dealer’s algorithm. We proceed with an example to illustrate our algorithms further. We make considerable improvements on the method of share repair described in [
8] for our proposed Krönecker product-induced BIBDs.
Next, we explore the concept of frameproofness for our proposed model and improve it significantly through certain changes in the model. We also prove existence of frameproofness of the modified scheme through results based on matchings of bipartite graphs.
Finally, we note the importance of secret sharing schemes in varied IoT applications, especially for their lightweight functionality, uniquely encapsulated through the non-accessibility of the full secret to any single entity, which we strengthen by frameproofness and can expand by incorporating multiple systems by our Krönecker product.
Organization of the Paper
Our paper starts with a brief review of the work performed by Stinson and Wei [
9] in
Section 3. We then move on to describe our construction, beginning with an introduction of the Krönecker product of two BIBDs in
Section 4. We describe the secret reconstruction procedure for such an object illustrated through an example in
Section 5. Next, we briefly describe the method of share repair and compute the corresponding repair probabilities, much like in [
8], in
Section 6. We then proceed to modify this scheme to give a frameproof construction in
Section 7. Furthermore, we answer the question of existence of such a modified construction in
Section 8. Finally, we draw the reader’s attention to the applicability of our results to secret sharing applications on the Internet of Things, especially in a secure, lightweight context, in
Section 9.
3. Stinson and Wei’s Model [9]
The classical Shamir scheme is defined over a finite field . It involves the following:
an initialization phase, in which the dealer chooses distinct, non-zero public elements from , and gives value to player ;
a share distribution phase in which the dealer chooses a secret , then secretly chooses independently and uniformly at random, and finally computes the share and gives it to player .
The combinatorial solution proposed by Stinson and Wei [
9] to the share repairability problem is based on an old technique by Benaloh and Leichter, namely, giving each player a subset of shares from an underlying threshold scheme called a base scheme (which is, say, a
-Shamir scheme over the base field
). Each player is then given a certain subset of
d of the
m shares, by use of a set system (or
design) consisting of
b blocks of size
d, defined on a set of
m points. This design is termed the
distribution design:
The resulting expanded -threshold scheme consists of each player corresponding to a block of the distribution design. For each point , the player is given the subshare . If X denotes the set of m points on which the design is defined and is the set of all blocks, then this forms an -distribution design.
Definition 1. Suppose . A -balanced incomplete block design or a -BIBD is a design such that:
- 1.
;
- 2.
each block contains exactly k points;
- 3.
every pair of distinct points from X is contained in exactly λ blocks.
Observe that if each point occurs in exactly r blocks, then the parameters of a BIBD satisfy the following relations [11]: - (i)
;
- (ii)
;
- (iii)
(and hence ).
Definition 2. We shall call a distribution design a tensor design if it simply satisfies property (i) above.
Design Properties
Next, we consider an example to demonstrate the fact that the object constructed in
Section 4 is in fact a ramp scheme. For the purpose of computations, we recall some results from [
8] on block designs.
Theorem 1 (Replication Number). Every point in a -BIBD occurs in exactly blocks. The value r is termed the replication number of the scheme.
Theorem 2 (Blocks and Block Size). A -BIBD has exactly
blocks of size k.
4. Tensor Design Generated by Two BIBDs
Given two matrices and , the usual matrix product operation can be carried out only when the column size of the left matrix is equal to the row size of the right matrix . The Krönecker product can be applied on any two matrices, irrespective of their dimension. This operation has several applications in Linear Algebra, of which, we consider some properties that shall be useful for working with BIBDs.
4.1. Definition of the Krönecker Product
The
Krönecker product of two matrices
and
is the block matrix
where
denotes the entry in the
row and
column of
.
Observe that Krönecker products follow the associative property. Thus, for matrices
,
, and
,
Another interesting property of Krönecker products is that they maintain structure over block matrices. Thus, if
is written as a block matrix
4.2. Krönecker Product of Two BIBDs
Let
and
be the share matrices generated by ramp schemes with, respectively,
and
blocks having shares of sizes
and
. Suppose
and
also denote the
and
matrices corresponding to the two schemes. The Krönecker product of
is therefore
where
(
) is the
row-block submatrix of
M containing rows
. If the share matrix
is defined over the field
and
over the field
for some primes
and
, then we define the scalar multiplication by simple integer multiplication:
The reason behind taking such a multiplication is that the product elements are not distinguishable from integers. Therefore, M is a matrix over the integer ring .
At this point, the first observation that we make is that the Krönecker product of two BIBDs and does not always produce a BIBD. To illustrate the fact, we start with a small example, and then we describe a method for resolving this issue. Also, the Krönecker product in general does not produce an injective mapping from to the matrix space . So it is hopeless to search for a secret reconstruction procedure from a given Krönecker product matrix. We shall thus impose a condition producing an injective map and in turn, ensuring the existence of secret reconstruction.
Consider an example of two
Shamir schemes in
and
over the points
and
constructed using two polynomials modulo
and
, respectively. These can be represented by share matrices
and
, respectively, with
:
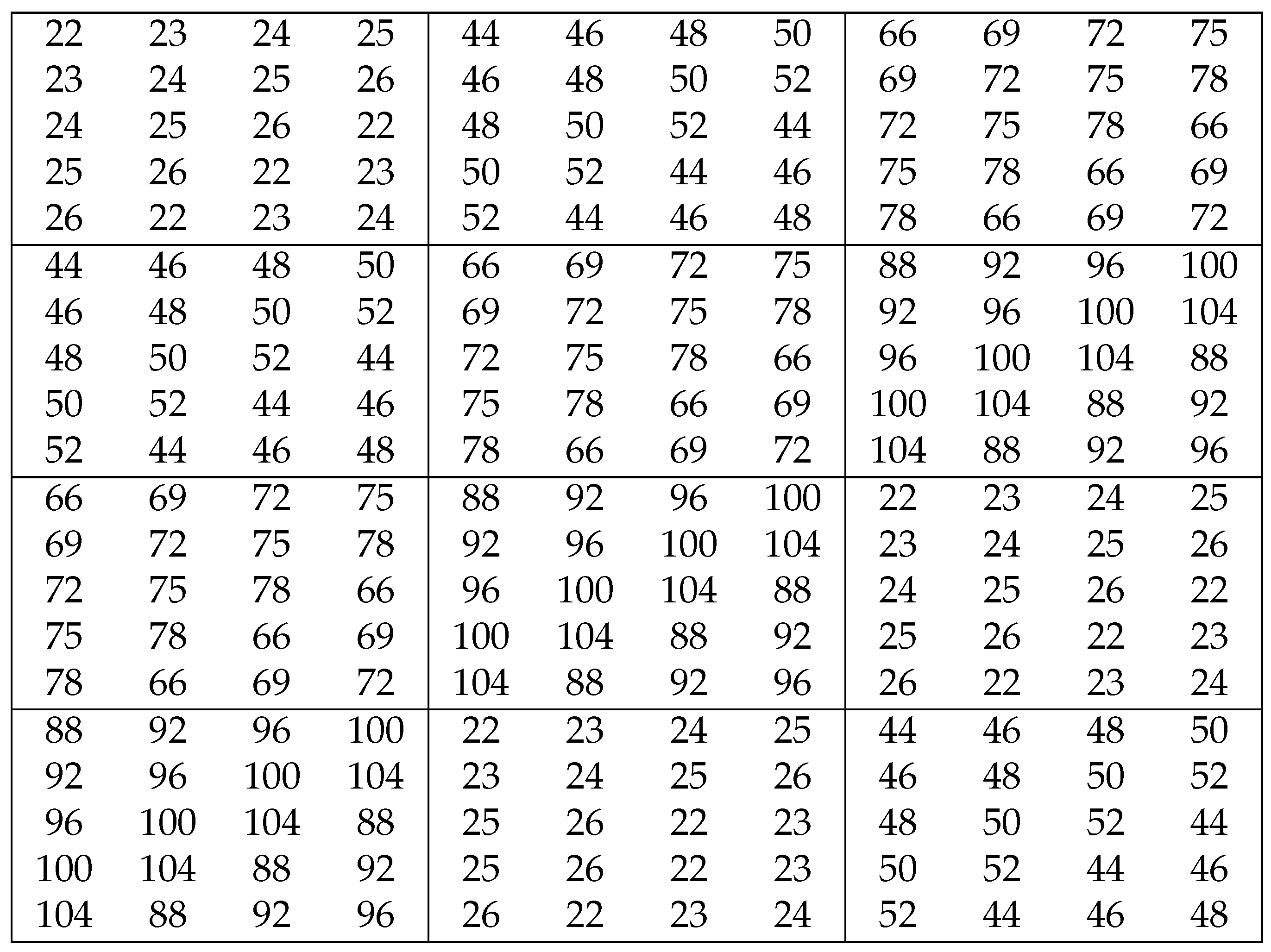
The Krönecker product of the BIBDs
and
is as follows:
| 1 | 2 | 3 | 2 | 4 | 6 | 3 | 6 | 9 |
| 2 | 3 | 5 | 4 | 6 | 10 | 6 | 9 | 15 |
| 3 | 5 | 1 | 6 | 10 | 2 | 9 | 15 | 3 |
| 5 | 1 | 2 | 10 | 2 | 4 | 15 | 3 | 6 |
| 2 | 4 | 6 | 1 | 2 | 3 | 4 | 8 | 12 |
| 4 | 6 | 10 | 2 | 3 | 5 | 8 | 12 | 20 |
| 6 | 10 | 2 | 3 | 5 | 1 | 12 | 20 | 4 |
| 10 | 2 | 4 | 5 | 1 | 2 | 20 | 4 | 8 |
| 3 | 6 | 9 | 4 | 8 | 12 | 2 | 4 | 6 |
| 6 | 9 | 15 | 8 | 12 | 20 | 4 | 6 | 10 |
| 9 | 15 | 3 | 12 | 20 | 4 | 6 | 10 | 2 |
| 15 | 3 | 6 | 20 | 4 | 8 | 10 | 2 | 4 |
| 4 | 8 | 12 | 3 | 6 | 9 | 1 | 2 | 3 |
| 8 | 12 | 20 | 6 | 9 | 15 | 2 | 3 | 5 |
| 12 | 20 | 4 | 9 | 15 | 3 | 3 | 5 | 1 |
| 20 | 4 | 8 | 15 | 3 | 6 | 5 | 1 | 2 |
Hence, has the parameters , and ; the parameters r and are not well-defined. Obviously, neither does this satisfy property 3 of a BIBD (Definition 1), nor the relation (i) of a tensor design (Definition 2). Lemmas 1–3 and Theorem 3 ensure that we always obtain a tensor design from a Krönecker product, and furthermore that we always obtain a secret reconstruction for such a share distribution scheme.
4.3. Some Results on the Krönecker Product of BIBDs
We now resolve these issues by defining some properties of a tensor design. Let and be share matrices defined on points and , respectively. Let be the same distribution scheme as , but on the points . The position of an element in the Krönecker product of these two matrices can be found by simple counting, and is stated in the following lemma:
Lemma 1. The product of and can be found in the row (which is also the player number in the repair scheme represented by M), and the column of M.
The next result helps ensure that is indeed a BIBD:
Lemma 2. Let and be two collections of integers. Then there exists an integer d such that and have no multiplicative collisions of the type for .
Proof. Set
. Suppose
.
however, since
, this is a contradiction. Therefore,
and
produce no multiplicative collisions. □
Lemma 3. Given a list of distinct elements , we can choose an integer such that .
Proof. Without loss of generality, we may assume . Let and fix in . Thus, and such that . Choose such that and for some j in . Now, ==. □
Theorem 3 (Reconstruction from Tensor Designs). Consider a -BIBD and a -BIBD .
- 1.
The matrix produces a tensor design (over the integer ring ) for a (public) integer d such that there are no multiplicative collisions of the type for .
- 2.
If ;
if ;
then and can be reproduced from a collection of players in the new scheme , hence enabling share repair and secret reconstruction.
This theorem can be generalized for finitely many such Krönecker products, and motivates us to present the following algorithm for a share distribution scheme.
Proof. The parameters of the Krönecker product are . Part 1 of the theorem therefore follows from Lemma 2, which ensures a well-defined value for r, and Lemma 3, which ensures a well-defined value for .
In order to prove part 2, we describe two ways to reproduce and . Recall first that any rows of produce all points of , and similarly rows for . Furthermore, we claim the following:
- [I]
A collection of players that has
- (i)
players from one row-block of M;
- (ii)
at least one player from distinct row-blocks of the remaining row-blocks
can reconstruct the secret.
- [II]
Let () be the collection of players . A collection of players that contains
- (i)
players from one ;
- (ii)
at least one player from ,
can also reconstruct the secret.
We now present an algorithm to prove claim [I]; claim [II] follows similarly.
The share of the
player
of the
row-block
is of the form
Fix any and choose to ensure that
.
Therefore, the values of become known. Divide by (for and ) to obtain .
Construct the complete matrix using the shares of players of that are now known. Hence construct .
Using the values of the elements in , compute the values for indices that are distinct from each other as well as from i.
Hence, construct from the shares of players of thus obtained.
Finally compute the secret from and .
□
This reconstruction algorithm is clearly better than the one in [
8] in the sense that the size of the authorized coalition is smaller. In fact, the size of the authorized coalition, while not unique, has a lower bound in the number of players. The following section provides a proof that there is always a secret reconstruction for this scheme.
4.4. Proof of Existence of Secret Reconstruction
Let us redefine the problem in terms of random variables. Let
be sampled without replacement from the collection of all players. We assume a uniform probability distribution over the set of all players.
We further define and . Then the condition for reconstruction becomes
- [I]
- (i)
,
- (ii)
for at least indices k.
- [II]
- (i)
,
- (ii)
for at least indices j.
Let be the event that condition [I] is satisfied and be the event that condition [II] is satisfied. Also, let be the event that . We find an such that . This is equivalent to . In fact, it is sufficient to show and .
As
,
,
Lemma 4. .
Proof. We observe that is the event and is the event that for at most indices k. Thus, if there are players in a collection, then by the pigeonhole principle, either or is violated. □
Lemma 5. .
Proof. We observe that is the event and there are s. Thus, if there are players in a collection, then by the pigeonhole principle, is violated, since there is at least one with or more players. □
Lemma 6. .
Proof. We observe that is the event that for at most indices k. By definition, each can have at most elements. Thus, any collection of players violates . □
Lemma 7. .
Proof. We observe that is the event and is the event that for at most indices j. Thus, if there are players in a collection, then by the pigeonhole principle, either or is violated. □
Lemma 8. .
Proof. We observe that is the event and there are s. Thus, if there are players in a collection, then by the pigeonhole principle, is violated, since there is at least one with or more players. □
Lemma 9. .
Proof. We observe that is the event that for at most indices j. By definition, each can have at most elements. Thus, any collection of players violates . □
For , Lemmas 4–6 imply and , and Lemmas 7–9 imply .
Note that the bound given here for the reconstruction number
is tight, as we might expect. In the example presented in
Section 5, the bound turns out to be 5, which matches all the bounds above. Corresponding counterexamples can be constructed to show that no smaller-sized general collection can complete the reconstruction. This result can be generalized for three or more designs. These results provide us with the tools to present a generalized scheme, which we do now.
4.5. A Generalized Share Distribution Scheme
Dealer selects n (not necessarily distinct) BIBDs , where for , is defined over points .
Dealer finds an integer such that .
For :
Dealer finds an integer (using Lemmas 2 and 3) such that breaks all pairwise multiplicative collisions and makes the gcd of all elements () and is 1.
M←.
Dealer distributes each row i of M as share to player and outputs publicly.
Note that by Theorem 3, M is a tensor design, and the algorithm in the proof of the theorem can be generalized for secret reconstruction of this scheme.
5. Example
Recall the previous example (
5). Using the algorithm in
Section 4.5, we produce a tensor design
using an integer
satisfying Lemma 3. Representing the share matrix modified from
by
(and noting that both share matrices are undeclared), with
:
we still have
,
,
, and
. Observe that
and
are the reconstruction numbers of
and
, respectively. The Krönecker product of the two matrices
and
, represented by the matrix
M, is shown in
Figure 1.
5.1. Secret Reconstruction
The matrix in the above example produces interesting results.
A collection of three players—exactly two from one of the sets and one from another—allows reconstruction of the secret. For example, consider the set of three players . This set can reconstruct the secret:
- (i)
; hence, the first row of is and the first two rows of are and . As , can be obtained from its two rows.
- (ii)
Now, observing , we readily know uses the first row of and the second row of ; this yields the second row of , . Since and we have two rows of , the whole matrix is known.
Any collection of three players—two from one of the sets and one from another—also allows reconstruction of the secret.
Reconstruction of the secret is ensured for a collection of five or more players.
This idea can be generalized to a secret reconstruction algorithm in the general case.
6. Share Repair for a Krönecker Product-Induced Distribution Design
Let
and
be
- and
-BIBDs with
and
blocks, and replication numbers
and
, respectively. Consider player
, whose share is the first block (i.e., row) of
. Thus,
Using the notations and method described in [
8] (and making the same assumption that any player is available with a fixed probability
p), the probability of availability of at least one repair set is
Furthermore, the share of
can also be characterized as
Let us assume that we have
players of type (
9) and
players of type (
10). Then
where
- (i)
are selected from type (
9);
- (ii)
are selected from type (
10);
- (iii)
are selected independently, and
Observe that
. Therefore, the probability of at least one repair set being available in this case is
Let
be the expected number of minimal repair sets. In general, this expected number is the product of the total number of possible repair sets and the probability of availability of each repair set. Ref. [
8] sets
. We denote by
, the number of partitions of a set of size
into three sets of sizes
,
and
. By an argument similar to the previous,
Table 1 shows a comparison of share repair probability on three projective plains for two different methods.
7. Frameproofness
Consider matrix representations of two BIBDs
and
, and their Krönecker product as depicted in Equation (
4). We show here how the share of a player, say
, can be retrieved (i.e., player
can be
framed; see [
10] for more details) by only two other players. For clarity, we mention here that the share of
is
.
There exist players that possess the element for some and , since is the replication number of . Of these, players possess the first elements of the share, i.e., . If any of these players know the ratios , then they could construct the entire share of .
Note that for
, any of the
players with shares
know these ratios.
Therefore, only two players—one from the players possessing and one from the players possessing —can reconstruct the entire share of player , and hence, frame this player.
We try to address this problem by reducing the repetitive nature of shares of the participants. We shall do this by decreasing the size of each share, while retaining all the information that a player had in the previous construction (i.e., Equation (
4)).
7.1. A Modified Scheme
Given two matrices
and
of the same dimension
, we define the operation
as the
matrix generated by position-wise products of elements of
and
, i.e., if
and
, then
The operator ⊙ is well-behaved in the sense that it is commutative and respects scalar multiplication on integer-valued matrices.
Let be a permutation. Given and , we define as , for any integer . Now given BIBDs and , we modify their Krönecker product by first choosing a permutation randomly from the set of all permutations over and producing . Then we produce , , …, by simple translations.
Next, we represent application of the function
to the
block matrix (of size
) of block-row
t in
by
, and define matrix
divided into blocks of size
similarly as
such that
where
is the element in the
row and
column of the
block matrix of
M. Finally, the
row of matrix
produces the share of player
(
) by omitting the zeroes.
7.2. Example
Consider another example, where a
-BIBD and a
-BIBD over the points
and
are represented by matrices
and
, respectively (note that
):
Then , , and ; and are the reconstruction numbers of and , respectively.
Modifying the matrix in
Figure 2, as shown in
Figure 3 and
Figure 4, we obtain a scheme for which it is no longer possible to reconstruct the secret of the scheme in
Figure 4 from just two players (as was possible in the example in
Section 5). In fact, the proceeding section provides an algorithm for secret reconstruction from this scheme using
players.
7.3. Secret Reconstruction for the Modified Scheme
Choose a player (which is the player in the row-block of , or the player from the top), for any and .
Consider elements in the share of player , i.e., and . For such an element , set (note that the value is not known, but the positions at which the matrix contains elements is known).
Construct set
. By Theorem 6, for a maximal set
(if not, then another value
y may be chosen by selecting a different element
) the set
is the set of all values in
.
Construct matrix , since the positions of all values in this matrix are now known.
Compute for ∈ share of player using the known values until all values are known.
Construct matrix , since the positions of all values in this matrix are now known.
Compute from the two known matrices.
Thus, framing any player is not possible for just two other participants, and requires a much larger coalition.
8. Graphical Representation and Proof of Existence of Permutations
Matching in Bipartite Graphs
Given an undirected graph , a matching of is a subgraph containing all vertices of such that each vertex in has either 0 or 1 edge incident to it. is a maximal matching of if it is not a subgraph of any other matching of . Thus, adding even one more edge to a maximal matching ensures that it is no longer a matching. The number of edges in a maximal matching of is called the matching number of .
A perfect matching of is such that each vertex of has an edge incident to it. Furthermore, a vertex cover of a graph is a subgraph containing all edges of such that every edge is incident to at least one vertex in the subgraph, and an edge cover of a graph is a subgraph containing all vertices of such that every vertex has at least one edge incident to it. Thus, if has no isolated vertices, then the sum of the number of vertices in its minimal vertex cover and the number of edges in its minimal edge cover equals the total number of its vertices.
If the vertex set of a graph can be partitioned into two disjoint subsets as such that any edge from a vertex in can only be incident to a vertex in and vice versa, then is called a bipartite graph. Let us recall some interesting results on matching in bipartite graphs.
Theorem 4 (König, [
12])
. In any bipartite graph, the number of edges in a maximum matching equals the number of vertices in a minimum vertex cover. Theorem 5 (Hall, [
13])
. Given a bipartite graph with , has a matching of size if and only if for every we have , where . Figure 5 shows a bipartite graph for the tensor design.
Definition 3. A bipartite graph is said to induce a tensor design if
the vertex set the disjoint union of the set of players and the set of points of ;
the edge set is the collection .
Theorem 6. Given a bipartite graph inducing a tensor design , and given subsets of size s,
- (i)
If , then reconstruction of the modified scheme is possible.
- (ii)
If , then (i) holds.
Proof. Assuming the usual notations for a tensor design, it is clear that in
,
From Equation (
13) and the inclusion-exclusion principle,
Since
, Hall’s theorem (Theorem 5) implies
has a matching of size
v, i.e.,
. Thus, (i) holds by the reconstruction algorithm in
Section 7.3. Now choose
such that each subset contains at least one point matched with
in this matching, so that (ii) holds. This proves the theorem. □
9. Secret Sharing Schemes and the Internet of Things
Secret sharing schemes can be used to distribute the security key amongst numerous devices in an IoT system, ensuring that no single device has access to the entire key. They are also lightweight and require less computational power compared to other cryptographic elements. Additionally, their ability to detect and prevent attacks that attempt to modify or delete parts of the secret is particularly important in IoT applications where security is critical.
For example, in a healthcare IoT system, the security of patient data is of utmost importance. Secret sharing schemes can be used to distribute the patient data amongst multiple devices, ensuring that no single device has access to the entire data. Ref. [
14] proposes an AI heuristic decision algorithm, utilizing a best-first search (BFS) approach. It effectively balances energy load and reduces communication overhead in smart healthcare technologies. The utilization of homomorphic secret sharing in IoT-based e-health applications provides various advantages in terms of privacy and security. It securely distributes secret pairs among medical nodes, ensuring the confidentiality of sensitive health data during transmission and storage within the network. This is achieved by encrypting data through homomorphic secret sharing, thereby preventing unauthorized access to medical data. Access to medical records is limited to authorized entities possessing the necessary secret keys to decrypt and utilize the shared data. Thus, the incorporation of homomorphic secret sharing adds an extra layer of protection against unauthorized modifications or alterations to medical records. A generalization of this scheme to multiple levels—possibly to combine data between different hospitals or chains of healthcare providers, different states within a country, or even different countries—can be easily achieved through the Krönecker product of the individual schemes used by each hospital system. The fields on which these schemes are based provide a perfect foundation for the homomorphism, which can be easily maintained by the integer ring over which the Krönecker product is then defined.
A frameproof tensor product of multiple distribution designs can be distinctly useful for lightweight IoT applications, as it allows for a multi-level or multi-system secret sharing scheme IoT implementation in a secure and efficient manner, while detecting and preventing any attempt to modify or delete parts of the secret data. This approach ensures that even if some levels are compromised, the overall security of the system(s) remains intact.
The wide range of applicability of our generalizations can be further seen in, say, the management of massive data, such as [
15], which proposes a non-interactive approach for IoT data aggregation that utilizes additive secret sharing, addressing numerous challenges including privacy concerns, security risks, high communication overhead, and user interaction. The additive secret sharing effectively masks the original data, preventing malicious analysis by the servers. The scheme also supports offline mobile users, maintains privacy, and provides efficient algorithms for result verification. However, ref. [
15] only splits the secret between two servers at a time. A frameproof tensor product can be smoothly applied in this context for connecting a large number of such systems, due to the underlying fields over which the secrets are split between servers in individual systems, as well as the generalized integer ring over which the tensor product is then defined.
Figure 6 shows an application of tensor design in multi-system IoT.
10. Conclusions and Future Work
In this paper, we have first generalized the concept of combinatorial RTS and then improved our secret sharing scheme by producing a frameproof one. We believe our results can be extended further to an arbitrary number of distribution designs. We also believe that the Krönecker product of BIBDs can be generalized to t-designs, and all corresponding results will hold for these. Furthermore, a frameproof modification for the generalized scheme also remains an open problem.
Furthermore, we have discussed the extensive scope of applicability for our proposed scheme in a diverse array of IoT contexts. A fascinating avenue for further investigation entails the examination of specific instances of these applications.