Knowledge Graphs and Semantic Web Tools in Cyber Threat Intelligence: A Systematic Literature Review
Abstract
1. Introduction
Contribution
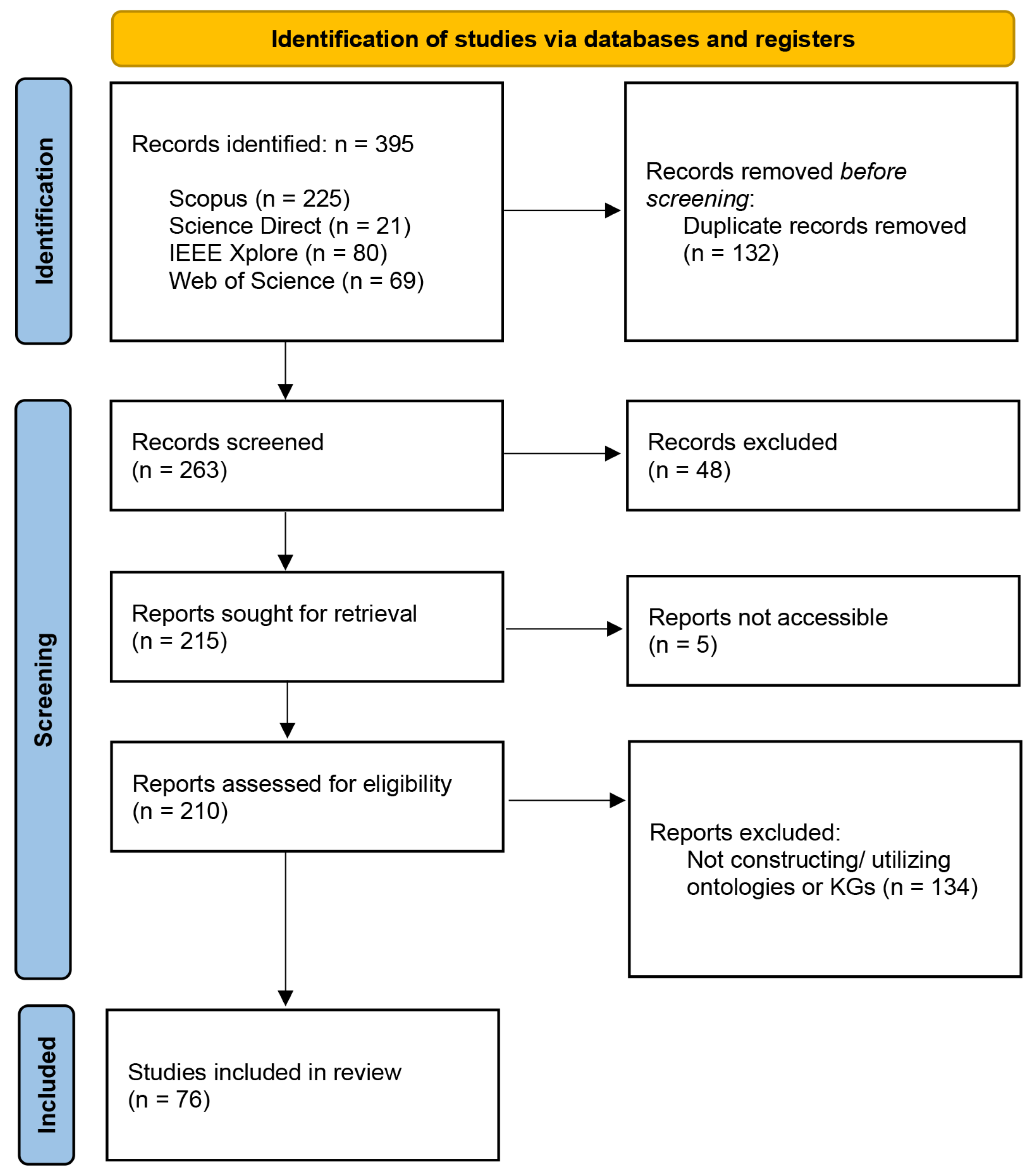
2. Literature Selection Strategy
3. Results
3.1. Ontology and Knowledge Graph Construction
3.2. Utilization of Ontologies and Knowledge Graphs
3.3. Machine Learning and Deep Learning Applications
3.3.1. Deep Learning Methods in Data Extraction
3.3.2. Other Uses of Machine Learning and Deep Learning
4. Discussion
5. Concluding Remarks
5.1. Contribution
5.2. Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AARs | After Action Reports |
| ACT | Semi-Automated Cyber Threat Intelligence |
| ADACO | Attack and Defense Analysis of Cybersecurity Ontology |
| AHG | Attack Hypothesis Generator |
| AI | Artificial Intelligence |
| AML | Adversarial Machine Learning |
| APT | Advanced Persistent Threat |
| BERT | Bidirectional Encoder Representations from Transformers |
| BiLSTM | Bidirectional Long Short-Term Memory |
| CFRaaS | Cloud Forensic Readiness as a Service |
| CNN | Convolutional Neural Network |
| CRF | Conditional Random Fields |
| CTI | Cyber Threat Intelligence |
| CVE | Common Vulnerabilities and Exposures |
| CVSS | Common Vulnerability Scoring System |
| CybOX | Cyber Observable eXpression |
| DFAX | Digital Forensic Analysis eXpression |
| DL | Deep Learning |
| DRAF | Dynamic Risk Assessment Framework |
| FFNN | Feed-Forward Neural Network |
| GBoost | Gradient Boosting |
| GNN | Graph Neural Network |
| GRU | Gated Recurrent Unit |
| IDRS | Intrusion Detection and Response Systems |
| IDS | Intrusion Detection System |
| IoC | Indicators of Compromise |
| IODEF | Incident Object Description Exchange Format |
| IoT | Internet of Things |
| IP | Internet Protocol |
| IR | Information Retrieval |
| IT | Information Technology |
| KG | Knowledge Graph |
| KGaaS | Knowledge Graph as a Service |
| KGCN | Knowledge Graph Convolutional Network |
| LLM | Large Language Model |
| MAP | Mean Average Precision |
| MEE | Malware Entity Extractor |
| ML | Machine Learning |
| NER | Named Entity Recognition |
| NLP | Natural Language Processing |
| NN | Neural Network |
| NSM | Network Security Monitoring |
| NVD | National Vulnerability Database |
| OSINT | Open-Source Intelligence |
| OWL | Web Ontology Language |
| R-MGAT | Relational Multi-Head Graph Attention Network |
| RDF | Resource Description Framework |
| RelExt | Relationship Extractor |
| RF | Random Forest |
| RL | Reinforcement Learning |
| S-MAIDS | Semantic Model of Automated Intrusion Detection Systems |
| SIEM | Security Information Event Management |
| SMEs | Small- and Medium-sized Enterprises |
| STIX | Structured Threat Information eXpression |
| SWRL | Semantic Web Rule Language |
| TAL | Threat Agent Library |
| TEPA | Threat Evolution Prediction Algorithm |
| TTP | Tactics, Techniques and Procedures |
| UI | User Interfaces |
| URL | Uniform Resource Locator |
| USE | Universal Sentence Encoder |
| XSS | Cross-Site Scripting |
References
- The Latest 2024 Cyber Crime Statistics (Updated March 2024). Available online: https://aag-it.com/the-latest-cyber-crime-statistics/ (accessed on 2 April 2024).
- Top Concerns Industry Leaders Have about Cyberattacks in 2024 and beyond. Available online: https://www.ibm.com/blog/top-concerns-industry-leaders-have-about-cyberattacks-in-2024-and-beyond/ (accessed on 2 April 2024).
- Sun, N.; Ding, M.; Jiang, J.; Xu, W.; Mo, X.; Tai, Y.; Zhang, J. Cyber Threat Intelligence Mining for Proactive Cybersecurity Defense: A Survey and New Perspectives. IEEE Commun. Surv. Tutorials 2023, 25, 1748–1774. [Google Scholar] [CrossRef]
- What Is Cyber Threat Intelligence? Available online: https://www.microsoft.com/en-us/security/business/security-101/what-is-cyber-threat-intelligence (accessed on 5 April 2024).
- What Is Cyber Threat Intelligence? Available online: https://www.cisco.com/c/en/us/products/security/what-is-cyber-threat-intelligence.html (accessed on 5 April 2024).
- Saeed, S.; Suayyid, S.A.; Al-Ghamdi, M.S.; Al-Muhaisen, H.; Almuhaideb, A.M. A Systematic Literature Review on Cyber Threat Intelligence for Organizational Cybersecurity Resilience. Sensors 2023, 23, 7273. [Google Scholar] [CrossRef] [PubMed]
- Mavroeidis, V.; Bromander, S. Cyber Threat Intelligence Model: An Evaluation of Taxonomies, Sharing Standards, and Ontologies within Cyber Threat Intelligence. In Proceedings of the 2017 European Intelligence and Security Informatics Conference (EISIC), Athens, Greece, 11–13 September 2017; pp. 91–98. [Google Scholar] [CrossRef]
- Available online: https://stixproject.github.io/ (accessed on 10 May 2024).
- Asgarli, E.; Burger, E. Semantic ontologies for cyber threat sharing standards. In Proceedings of the 2016 IEEE Symposium on Technologies for Homeland Security (HST), Waltham, MA, USA, 10–11 May 2016. [Google Scholar] [CrossRef]
- Merah, Y.; Kenaza, T. Proactive Ontology-based Cyber Threat Intelligence Analytic. In Proceedings of the 2021 International Conference on Recent Advances in Mathematics and Informatics (ICRAMI), Tebessa, Algeria, 21–22 September 2021. [Google Scholar] [CrossRef]
- Bratsas, C.; Kapsas, G.; Konstantinidis, S.; Koutsouridis, G.; Bamidis, P.D. A semantic wiki within moodle for Greek medical education. In Proceedings of the 2009 22nd IEEE International Symposium on Computer-Based Medical Systems, Albuquerque, NM, USA, 2–5 August 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Bratsas, C.; Koutkias, V.; Kaimakamis, E.; Bamidis, P.; Maglaveras, N. Ontology-Based Vector Space Model and Fuzzy Query Expansion to Retrieve Knowledge on Medical Computational Problem Solutions. In Proceedings of the 2007 29th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, Lyon, France, 22–26 August 2007; pp. 3794–3797. [Google Scholar] [CrossRef]
- Antoniou, P.E.; Chondrokostas, E.; Bratsas, C.; Filippidis, P.M.; Bamidis, P.D. A Medical Ontology Informed User Experience Taxonomy to Support Co-creative Workflows for Authoring Mixed Reality Medical Education Spaces. In Proceedings of the 2021 7th International Conference of the Immersive Learning Research Network (iLRN), Eureka, CA, USA, 17–10 June 2021; pp. 1–9. [Google Scholar] [CrossRef]
- Spyropoulos, A.Z.; Kornilakis, A.; Makris, G.C.; Bratsas, C.; Tsiantos, V.; Antoniou, I. Semantic Representation of the Intersection of Criminal Law & Civil Tort. Data 2022, 7, 176. [Google Scholar] [CrossRef]
- Spyropoulos, A.Z.; Bratsas, C.; Makris, G.C.; Garoufallou, E.; Tsiantos, V. Interoperability-Enhanced Knowledge Management in Law Enforcement: An Integrated Data-Driven Forensic Ontological Approach to Crime Scene Analysis. Information 2023, 14, 607. [Google Scholar] [CrossRef]
- Filippidis, P.M.; Dimoulas, C.; Bratsas, C.; Veglis, A. A unified semantic sports concepts classification as a key device for multidimensional sports analysis. In Proceedings of the 2018 13th International Workshop on Semantic and Social Media Adaptation and Personalization (SMAP), Zaragoza, Spain, 6–7 September 2018; pp. 107–112. [Google Scholar] [CrossRef]
- Filippidis, P.M.; Dimoulas, C.A.; Bratsas, C.; Veglis, A.A. A Multimodal Semantic Model For Event Identification On Sports Media Content. J. Media Crit. 2018, 4, 295–306. [Google Scholar]
- Bratsas, C.; Chrysou, D.E.; Eftychiadou, E.; Kontokostas, D.; Bamidis, P.D.; Antoniou, I. Semantic Web Game Based Learning: An I18n approach with Greek DBpedia. In Proceedings of the LiLe@WWW, Lyon, France, 17 April 2012. [Google Scholar]
- Kontokostas, D.; Bratsas, C.; Auer, S.; Hellmann, S.; Antoniou, I.; Metakides, G. Internationalization of Linked Data: The case of the Greek DBpedia edition. J. Web Semant. 2012, 15, 51–61. [Google Scholar] [CrossRef]
- Lange, C.; Ion, P.; Dimou, A.; Bratsas, C.; Sperber, W.; Kohlhase, M.; Antoniou, I. Bringing Mathematics to the Web of Data: The Case of the Mathematics Subject Classification. In Semantic Web: Research and Applications; Simperl, E., Cimiano, P., Polleres, A., Corcho, O., Presutti, V., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 763–777. [Google Scholar]
- Karampatakis, S.; Bratsas, C.; Zamazal, O.; Filippidis, P.M.; Antoniou, I. Alignment: A Hybrid, Interactive and Collaborative Ontology and Entity Matching Service. Information 2018, 9, 281. [Google Scholar] [CrossRef]
- Bratsas, C.; Chondrokostas, E.; Koupidis, K.; Antoniou, I. The Use of National Strategic Reference Framework Data in Knowledge Graphs and Data Mining to Identify Red Flags. Data 2021, 6, 2. [Google Scholar] [CrossRef]
- Rastogi, N.; Dutta, S.; Zaki, M.; Gittens, A.; Aggarwal, C. MALOnt: An Ontology for Malware Threat Intelligence. In Proceedings of the First International Workshop, MLHat 2020, San Diego, CA, USA, 24 August 2020; Volume 1271, pp. 28–44. [Google Scholar] [CrossRef]
- Wang, P.; Dai, G.; Zhai, L. Event-Based Threat Intelligence Ontology Model. In Proceedings of the 5th International Conference, SciSec 2023, Melbourne, VIC, Australia, 11–14 July 2023; Volume 14299, pp. 261–282. [Google Scholar] [CrossRef]
- Dora, J.; Nemoga, K. Ontology for Cross-Site-Scripting (XSS) Attack in Cybersecurity. J. Cybersecur. Priv. 2021, 1, 319–339. [Google Scholar] [CrossRef]
- Grigoriadis, C.; Berzovitis, A.; Stellios, I.; Kotzanikolaou, P. A Cybersecurity Ontology to Support Risk Information Gathering in Cyber-Physical Systems. In Proceedings of the CyberICPS, SECPRE, ADIoT, SPOSE, CPS4CIP, and CDT&SECOMANE, Darmstadt, Germany, 4–8 October 2022; Volume 13106, pp. 23–39. [Google Scholar] [CrossRef]
- Piplai, A.; Mittal, S.; Joshi, A.; Finin, T.; Holt, J.; Zak, R. Creating Cybersecurity Knowledge Graphs from Malware after Action Reports. IEEE Access 2020, 8, 211691–211703. [Google Scholar] [CrossRef]
- Yang, F.; Han, Y.; Ding, Y.; Tan, Q.; Xu, Z. A flexible approach for cyber threat hunting based on kernel audit records. Cybersecurity 2022, 5, 11. [Google Scholar] [CrossRef]
- Li, Y.; Guo, Y.; Fang, C.; Liu, Y.; Chen, Q. A Novel Threat Intelligence Information Extraction System Combining Multiple Models. Secur. Commun. Netw. 2022, 2022, 8477260. [Google Scholar] [CrossRef]
- Ahmed, K.; Khurshid, S.K.; Hina, S. CyberEntRel: Joint extraction of cyber entities and relations using deep learning. Comput. Secur. 2024, 136, 103579. [Google Scholar] [CrossRef]
- Khairkar, A.; Kshirsagar, D.; Kumar, S. Ontology for Detection of Web Attacks. In Proceedings of the 2013 International Conference on Communication Systems and Network Technologies, Gwalior, India, 6–8 April 2013; pp. 612–615. [Google Scholar] [CrossRef]
- Strasburg, C.; Basu, S.; Wong, J. S-MAIDS: A semantic model for automated tuning, correlation, and response selection in intrusion detection systems. In Proceedings of the 2013 IEEE 37th Annual Computer Software and Applications Conference, Kyoto, Japan, 22–26 July 2013; pp. 319–328. [Google Scholar] [CrossRef]
- Burger, E.; Goodman, M.; Kampanakis, P.; Zhu, K. Taxonomy model for cyber threat intelligence information exchange technologies. In Proceedings of the 2014 ACM Workshop on Information Sharing & Collaborative Security, Scottsdale, AZ, USA, 3 November 2014; pp. 51–60. [Google Scholar] [CrossRef]
- Casey, E.; Back, G.; Barnum, S. Leveraging CybOX™ to standardize representation and exchange of digital forensic information. Digit. Investig. 2015, 12, S102–S110. [Google Scholar] [CrossRef]
- Available online: https://cyboxproject.github.io/ (accessed on 21 May 2024).
- Meckl, S.; Tecuci, G.; Boicu, M.; Marcu, D. Towards an Operational Semantic Theory of Cyber Defense against Advanced Persistent Threats; George Mason University: Fairfax, VA, USA, 2015; Volume 1523, pp. 58–65. [Google Scholar]
- Falk, C. An Ontology for Threat Intelligence. In Proceedings of the European Conference on Cyber Warfare and Security, Munich, Germany, 7–8 July 2016. [Google Scholar]
- Mohsin, M.; Anwar, Z. Where to Kill the Cyber Kill-Chain: An Ontology-Driven Framework for IoT Security Analytics. In Proceedings of the 2016 International Conference on Frontiers of Information Technology (FIT), Islamabad, Pakistan, 19–21 December 2017; pp. 23–28. [Google Scholar] [CrossRef]
- Qamar, S.; Anwar, Z.; Rahman, M.A.; Al-Shaer, E.; Chu, B.T. Data-driven analytics for cyber-threat intelligence and information sharing. Comput. Secur. 2017, 67, 35–58. [Google Scholar] [CrossRef]
- Mavroeidis, V.; Josang, A.; ACM. Data-Driven Threat Hunting Using Sysmon. In Proceedings of the 2nd International Conference on Cryptography, Security and Privacy, Guiyang, China, 16–19 March 2018; pp. 82–88. [Google Scholar] [CrossRef]
- Diederichsen, L.; Choo, K.K.; Le-Khac, N.A. A Graph Database-Based Approach to Analyze Network Log Files. In Proceedings of the 13th International Conference, NSS 2019, Sapporo, Japan, 15–18 December 2019; Volume 11928, pp. 53–73. [Google Scholar] [CrossRef]
- Doynikova, E.; Fedorchenko, A.; Kotenko, I. Ontology of metrics for cyber security assessment. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019. [Google Scholar] [CrossRef]
- Kim, M.; Dey, S.; Lee, S.W. Ontology-driven security requirements recommendation for APT attack. In Proceedings of the 2019 IEEE 27th International Requirements Engineering Conference Workshops (REW), Jeju, Republic of Korea, 23–27 September 2019; pp. 150–156. [Google Scholar] [CrossRef]
- Liu, Z.; Sun, Z.; Chen, J.; Zhou, Y.; Yang, T.; Yang, H.; Liu, J. STIX-based Network Security Knowledge Graph Ontology Modeling Method. In Proceedings of the 2020 3rd International Conference on Geoinformatics and Data Analysis, Marseille, France, 15–17 April 2020; pp. 152–157. [Google Scholar] [CrossRef]
- Piplai, A.; Mittal, S.; Abdelsalam, M.; Gupta, M.; Joshi, A.; Finin, T. Knowledge Enrichment by Fusing Representations for Malware Threat Intelligence and Behavior. In Proceedings of the 2020 IEEE International Conference on Intelligence and Security Informatics (ISI), Arlington, VA, USA, 9–10 November 2020; pp. 47–52. [Google Scholar] [CrossRef]
- Sills, M.; Ranade, P.; Mittal, S. Cybersecurity Threat Intelligence Augmentation and Embedding Improvement—A Healthcare Usecase. In Proceedings of the 2020 IEEE International Conference on Intelligence and Security Informatics (ISI), Arlington, VA, USA, 9–10 November 2020; pp. 62–67. [Google Scholar] [CrossRef]
- Vrandečić, D.; Krötzsch, M. Wikidata: A free collaborative knowledgebase. Commun. ACM 2014, 57, 78–85. [Google Scholar] [CrossRef]
- Available online: https://accessgudid.nlm.nih.gov/ (accessed on 22 May 2024).
- Hutschenreuter, H.; Çakmakçı, S.; Maeder, C.; Kemmerich, T. Ontology-based Cybersecurity and Resilience Framework. In Proceedings of the 7th International Conference on Information Systems Security and Privacy, Virtual, 11–13 February 2021; pp. 458–466. [Google Scholar] [CrossRef]
- Mavroeidis, V.; Hohimer, R.; Casey, T.; Jesang, A. Threat Actor Type Inference and Characterization within Cyber Threat Intelligence. In Proceedings of the 2021 13th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 25–28 May 2021; pp. 327–352. [Google Scholar] [CrossRef]
- Merah, Y.; Kenaza, T. Ontology-based Cyber Risk Monitoring Using Cyber Threat Intelligence. In Proceedings of the 16th International Conference on Availability, Reliability and Security, Vienna, Austria, 17–20 August 2021. [Google Scholar] [CrossRef]
- Ammi, M.; Adedugbe, O.; Alharby, F.; Benkhelifa, E. Leveraging a cloud-native architecture to enable semantic interconnectedness of data for cyber threat intelligence. Clust. Comput. 2022, 25, 3629–3640. [Google Scholar] [CrossRef]
- Bromander, S.; Swimmer, M.; Muller, L.; Jøsang, A.; Eian, M.; Skjøtskift, G.; Borg, F. Investigating Sharing of Cyber Threat Intelligence and Proposing A New Data Model for Enabling Automation in Knowledge Representation and Exchange. Digit. Threat. Res. Pract. 2022, 3, 1–22. [Google Scholar] [CrossRef]
- Collen, A.; Nijdam, N. Can I Sleep Safely in My Smarthome? A Novel Framework on Automating Dynamic Risk Assessment in IoT Environments. Electronics 2022, 11, 1123. [Google Scholar] [CrossRef]
- National Vulnerability Database. Available online: https://nvd.nist.gov/ (accessed on 17 May 2024).
- Huang, C.C.; Huang, P.Y.; Kuo, Y.R.; Wong, G.W.; Huang, Y.T.; Sun, Y.; Chang Chen, M. Building Cybersecurity Ontology for Understanding and Reasoning Adversary Tactics and Techniques. In Proceedings of the 2022 IEEE International Conference on Big Data (Big Data), Osaka, Japan, 17–20 December 2022; pp. 4266–4274. [Google Scholar] [CrossRef]
- Li, Z.; Zeng, J.; Chen, Y.; Liang, Z. AttacKG: Constructing Technique Knowledge Graph from Cyber Threat Intelligence Reports. In Proceedings of the 27th European Symposium on Research in Computer Security, Copenhagen, Denmark, 26–30 September 2022; Volume 13554, pp. 589–609. [Google Scholar] [CrossRef]
- Satvat, K.; Gjomemo, R.; Venkatakrishnan, V. Extractor: Extracting Attack Behavior from Threat Reports. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy (EuroS&P), Vienna, Austria, 6–10 September 2021; pp. 598–615. [Google Scholar]
- Husari, G.; Al-Shaer, E.; Ahmed, M.; Chu, B.; Niu, X. TTPDrill: Automatic and accurate extraction of threat actions from unstructured text of CTI Sources. In Proceedings of the 33rd Annual Computer Security Applications Conference, Orlando, FL, USA, 4–8 December 2017; Volume F132521, pp. 103–115. [Google Scholar] [CrossRef]
- Rastogi, N.; Dutta, S.; Gittens, A.; Zaki, M.; Aggarwal, C. TINKER: A framework for Open source Cyberthreat Intelligence. In Proceedings of the 2022 IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Wuhan, China, 9–11 December 2022; pp. 1569–1574. [Google Scholar] [CrossRef]
- Sharma, K.; Kumar, A. A Graph Database-Based Method for Network Log File Analysis. In Proceedings of the 2022 11th International Conference on System Modeling & Advancement in Research Trends (SMART), Moradabad, India, 16–17 December 2022; pp. 545–550. [Google Scholar] [CrossRef]
- Akbar, K.; Rahman, F.; Singhal, A.; Khan, L.; Thuraisingham, B. The Design and Application of a Unified Ontology for Cyber Security. In Proceedings of the 19th International Conference, ICISS 2023, Raipur, India, 16–20 December 2023; Volume 14424, pp. 23–41. [Google Scholar] [CrossRef]
- Compastié, M.; López Martínez, A.; Fernández, C.; Gil Pérez, M.; Tsarsitalidis, S.; Xylouris, G.; Mlakar, I.; Kourtis, M.; Šafran, V. PALANTIR: An NFV-Based Security-as-a-Service Approach for Automating Threat Mitigation. Sensors 2023, 23, 1658. [Google Scholar] [CrossRef]
- Dora, J.; Hluchý, L.; Nemoga, K. Ontology for Blind SQL Injection. Comput. Inform. 2023, 42, 480–500. [Google Scholar] [CrossRef]
- Sánchez-Zas, C.; Villagrá, V.; Vega-Barbas, M.; Larriva-Novo, X.; Moreno, J.; Berrocal, J. Ontology-based approach to real-time risk management and cyber-situational awareness. Future Gener. Comput. Syst. 2023, 141, 462–472. [Google Scholar] [CrossRef]
- Riesco, R.; Villagrá, V.A. Leveraging cyber threat intelligence for a dynamic risk framework. Int. J. Inf. Secur. 2019, 18, 715–739. [Google Scholar] [CrossRef]
- Duque-Ramos, A.; Fernandez-Breis, J.; Stevens, R.; Aussenac-Gilles, N. OQuaRE: A SQuaRE-based approach for evaluating the quality of ontologies. J. Res. Pract. Inf. Technol. 2011, 43, 159–176. [Google Scholar]
- Zhang, S.; Su, X.; Shi, P.; Du, T.; Han, Y. Threat Modeling and Application Research Based on Multi-Source Attack and Defense Knowledge. Comput. Mater. Contin. 2023, 77, 349–377. [Google Scholar] [CrossRef]
- Takahashi, T.; Kadobayashi, Y. Mechanism for linking and discovering structured cybersecurity information over networks. In Proceedings of the 2014 IEEE International Conference on Semantic Computing, Newport Beach, CA, USA, 16–18 June 2014; pp. 279–284. [Google Scholar] [CrossRef]
- Takahashi, T.; Kadobayashi, Y.; Fujiwara, H. Ontological approach toward cybersecurity in cloud computing. In Proceedings of the International Conference on Security of Information and Networks, Taganrog, Russia, 7–11 September 2010. [Google Scholar]
- Lu, S.; Kokar, M. A Situation Assessment Framework for Cyber Security Information Relevance Reasoning. In Proceedings of the 2015 18th International Conference on Information Fusion (Fusion), Washington, DC, USA, 6–9 July 2015; pp. 1459–1466. [Google Scholar]
- Takahashi, T.; Landfield, K.; Kadobayashi, Y. An Incident Object Description Exchange Format (IODEF) Extension for Structured Cybersecurity Information; RFC 7203; RFC Editor: Marina del Rey, CA, USA, 2014. [Google Scholar] [CrossRef]
- Monteiro, M.; Sarmento, T.; Barreto, A.; Costa, P. A holistic approach to evaluate cyber threat. STIDS 2016, 1788, 64–68. [Google Scholar]
- de Barros Barreto, A. Cyber-ARGUS Framework—Measuring Cyber-Impact on the Mission. Ph.D. Thesis, Instituto Tecnológico de Aeronáutica, São José dos Campos, São Paulo, Brazil, 2013. [Google Scholar]
- Mozzaquatro, B.; Jardim-Goncalves, R.; Agostinho, C. Situation awareness in the Internet of Things. In Proceedings of the 2017 International Conference on Engineering, Technology and Innovation (ICE/ITMC), Madeira, Portugal, 27–29 June 2017; pp. 982–990. [Google Scholar] [CrossRef]
- Sikos, L.F. Handling Uncertainty and Vagueness in Network Knowledge Representation for Cyberthreat Intelligence. In Proceedings of the 2018 IEEE International Conference on Fuzzy Systems (FUZZ-IEEE), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Bourai, S.B.; Mokhtari, A.; Khellaf, F. Poss–SROIQ (D): Possibilistic description logic extension toward an uncertain geographic ontology. New Trends Databases Inf. Syst. 2014, 241, 277–286. [Google Scholar]
- Klinov, P.; Parsia, B. Understanding a probabilistic description logic via connections to first-order logic of probability. In Proceedings of the International Workshop on Uncertainty Reasoning for the Semantic Web, Karlsruhe, Germany, 26 October 2008; pp. 41–58. [Google Scholar]
- Bal-Bourai, S.; Mokhtari, A. SROIQ (D): Possibilistic Description Logic for Uncertain Geographic Information. In Proceedings of the International Conference on Industrial, Engineering and Other Applications of Applied Intelligent Systems, Morioka, Japan, 2–4 August 2016; pp. 818–829. [Google Scholar]
- Bobillo, F.; Straccia, U. Reasoning with the finitely many-valued Łukasiewicz fuzzy description logic SROIQ. Inf. Sci. 2011, 181, 758–778. [Google Scholar] [CrossRef]
- Aviad, A.; Wecel, K. Cyber Treat Intelligence Modeling. In Proceedings of the 22nd International Conference, BIS 2019, Seville, Spain, 26–28 June 2019; Volume 353, pp. 361–370. [Google Scholar] [CrossRef]
- Available online: https://www.maltego.com/ (accessed on 20 May 2024).
- Najafi, P.; Mühle, A.; Pünter, W.; Cheng, F.; Meinel, C.; ACM. MalRank: A Measure of Maliciousness in SIEM-based Knowledge Graphs. In Proceedings of the 35th Annual Computer Security Applications Conference, San Juan, PR, USA, 9–13 December 2019; pp. 417–429. [Google Scholar] [CrossRef]
- Available online: https://github.com/HewlettPackard/sandpiper (accessed on 21 May 2024).
- Kebande, V.; Karie, N.; Ikuesan, R.; Venter, H. Ontology-driven perspective of CFRaaS. Wiley Interdiscip. Rev. Forensic Sci. 2020, 2, e1372. [Google Scholar] [CrossRef]
- Jung, J.W.; Park, S.H.; Lee, S.W. A Tool for Security Requirements Recommendation using Case-Based Problem Domain Ontology. In Proceedings of the 2021 IEEE 29th International Requirements Engineering Conference (RE), Notre Dame, IN, USA, 20–24 September 2021; pp. 438–439. [Google Scholar] [CrossRef]
- Shaked, A.; Margalit, O. Sustainable Risk Identification Using Formal Ontologies. Algorithms 2022, 15, 316. [Google Scholar] [CrossRef]
- Calyam, P.; Kejriwal, M.; Rao, P.; Cheng, J.; Wang, W.; Bai, L.; Siddhardh Nadendla, V.S.; Madria, S.; Das, S.K.; Chadha, R.; et al. Towards a Domain-Agnostic Knowledge Graph-as-a-Service Infrastructure for Active Cyber Defense with Intelligent Agents. In Proceedings of the 2023 IEEE Applied Imagery Pattern Recognition Workshop (AIPR), St. Louis, MO, USA, 27–29 September 2023; pp. 1–8. [Google Scholar] [CrossRef]
- Sane, K.; Joshi, K.; Mittal, S. Semantically Rich Framework to Automate Cyber Insurance Services. IEEE Trans. Serv. Comput. 2023, 16, 588–599. [Google Scholar] [CrossRef]
- Wu, H.; Li, X.; Gao, Y. An Effective Approach of Named Entity Recognition for Cyber Threat Intelligence. In Proceedings of the 2020 IEEE 4th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chongqing, China, 12–14 June 2020; pp. 1370–1374. [Google Scholar] [CrossRef]
- Gao, P.; Liu, X.; Choi, E.; Soman, B.; Mishra, C.; Farris, K.; Song, D. A System for Automated Open-Source Threat Intelligence Gathering and Management. In Proceedings of the 2021 International Conference on Management of Data, Virtual, 20–25 June 2021; pp. 2716–2720. [Google Scholar] [CrossRef]
- Sarhan, I.; Spruit, M. Open-CyKG: An Open Cyber Threat Intelligence Knowledge Graph. Knowl.-Based Syst. 2021, 233, 107524. [Google Scholar] [CrossRef]
- Li, Z.; Li, Y.; Zhang, H.; Li, J. Construction of TTPS from APT Reports Using Bert. In Proceedings of the 2021 18th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP), Chengdu, China, 17–19 December 2021; pp. 260–263. [Google Scholar] [CrossRef]
- Devlin, J.; Chang, M.W.; Lee, K.; Toutanova, K. BERT: Pre-training of Deep Bidirectional Transformers for Language Understanding. In Proceedings of the North American Chapter of the Association for Computational Linguistics, Mineapolis, MN, USA, 3–5 June 2019. [Google Scholar]
- Sun, L.; Li, Z.; Xie, L.; Ye, M.; Chen, B. APTKG: Constructing Threat Intelligence Knowledge Graph from Open-Source APT Reports Based on Deep Learning. In Proceedings of the 2022 5th International Conference on Data Science and Information Technology (DSIT), Shanghai, China, 22–24 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Manning, C.D.; Surdeanu, M.; Bauer, J.; Finkel, J.R.; Bethard, S.; McClosky, D. The Stanford CoreNLP natural language processing toolkit. In Proceedings of the 52nd Annual Meeting of the Association for Computational Linguistics: System Demonstrations, Baltimore, MD, USA, 23–25 June 2014; pp. 55–60. [Google Scholar]
- Li, Z.; Li, Y.; Liu, Y.; Liu, C.; Zhou, N. K-CTIAA: Automatic Analysis of Cyber Threat Intelligence Based on a Knowledge Graph. Symmetry 2023, 15, 337. [Google Scholar] [CrossRef]
- kbandla/APTnotes: Various Public Documents, Whitepapers and Articles about APT Campaigns. Available online: https://github.com/aptnotes/data (accessed on 16 May 2024).
- Husari, G.; Niu, X.; Chu, B.; Al-Shaer, E. Using Entropy and Mutual Information to Extract Threat Actions from Cyber Threat Intelligence. In Proceedings of the 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), Miami, FL, USA, 9–11 November 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, J.; Zhan, J. Constructing Knowledge Graph from Cyber Threat Intelligence Using Large Language Model. In Proceedings of the 2023 IEEE International Conference on Big Data (BigData), Sorrento, Italy, 15–18 December 2023; pp. 516–521. [Google Scholar] [CrossRef]
- Huguet Cabot, P.L.; Navigli, R. REBEL: Relation Extraction By End-to-end Language generation. In Findings of the Association for Computational Linguistics: EMNLP 2021; Moens, M.F., Huang, X., Specia, L., Yih, S.W.T., Eds.; Association for Computational Linguistics: Punta Cana, Dominican Republic, 2021; pp. 2370–2381. [Google Scholar] [CrossRef]
- Ren, Y.; Xiao, Y.; Zhou, Y.; Zhang, Z.; Tian, Z. CSKG4APT: A Cybersecurity Knowledge Graph for Advanced Persistent Threat Organization Attribution. IEEE Trans. Knowl. Data Eng. 2023, 35, 5695–5709. [Google Scholar] [CrossRef]
- Dhungana, S.; Upadhyaya, P. Optimal Cyber Threat Intelligent System for Nepal. In Proceedings of the 2019 Artificial Intelligence for Transforming Business and Society (AITB), Kathmandu, Nepal, 5 November 2019. [Google Scholar] [CrossRef]
- Elitzur, A.; Puzis, R.; Zilberman, P. Attack hypothesis generation. In Proceedings of the 2019 European Intelligence and Security Informatics Conference (EISIC), Oulu, Finland, 26–27 November 2019; pp. 40–47. [Google Scholar] [CrossRef]
- Pingle, A.; Piplai, A.; Mittal, S.; Joshi, A.; Holt, J.; Zak, R. Relext: Relation extraction using deep learning approaches for cybersecurity knowledge graph improvement. In Proceedings of the 2019 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, Vancouver, BC, USA, 27–30 August 2019; pp. 879–886. [Google Scholar] [CrossRef]
- Mendsaikhan, O.; Hasegawa, H.; Yamaguchi, Y.; Shimada, H. Quantifying the significance and relevance of cyber-security text through textual similarity and cyber-security knowledge graph. IEEE Access 2020, 8, 177041–177052. [Google Scholar] [CrossRef]
- Lim, S.K.; Muis, A.O.; Lu, W.; Ong, C.H. MalwareTextDB: A Database for Annotated Malware Articles. In Proceedings of the 55th Annual Meeting of the Association for Computational Linguistics (Volume 1: Long Papers), Vancouver, BC, Canada, 30 July–4 August 2017; Barzilay, R., Kan, M.Y., Eds.; Association for Computational Linguistics: Vancouver, BC, Canada, 2017; pp. 1557–1567. [Google Scholar] [CrossRef]
- Ding, Z.; Cao, D.; Liu, L.; Yu, D.; Ma, H.; Wang, F. A Method for Discovering Hidden Patterns of Cybersecurity Knowledge Based on Hierarchical Clustering. In Proceedings of the 2021 IEEE Sixth International Conference on Data Science in Cyberspace (DSC), Shenzhen, China, 9–11 October 2021; pp. 334–338. [Google Scholar] [CrossRef]
- Kriaa, S.; Chaabane, Y. SecKG: Leveraging attack detection and prediction using knowledge graphs. In Proceedings of the 2021 12th International Conference on Information and Communication Systems (ICICS), Valencia, Spain, 24–26 May 2021; pp. 112–119. [Google Scholar] [CrossRef]
- Mitra, S.; Piplai, A.; Mittal, S.; Joshi, A. Combating Fake Cyber Threat Intelligence using Provenance in Cybersecurity Knowledge Graphs. In Proceedings of the 2021 IEEE International Conference on Big Data (Big Data), Orlando, FL, USA, 15–18 December 2021; pp. 3316–3323. [Google Scholar] [CrossRef]
- Ranade, P.; Piplai, A.; Mittal, S.; Joshi, A.; Finin, T. Generating Fake Cyber Threat Intelligence Using Transformer-Based Models. In Proceedings of the 2021 International Joint Conference on Neural Networks (IJCNN), Shenzhen, China, 18–22 July 2021. [Google Scholar] [CrossRef]
- Yeboah-Ofori, A.; Ismail, U.; Swidurski, T.; Opoku-Boateng, F. Cyber Threat Ontology and Adversarial Machine Learning Attacks: Analysis and Prediction Perturbance. In Proceedings of the 2021 International Conference on Computing, Computational Modelling and Applications (ICCMA), Brest, France, 14–16 July 2021; pp. 71–77. [Google Scholar] [CrossRef]
- Yeboah-Ofori, A.; Mouratidis, H.; Ismai, U.; Islam, S.; Papastergiou, S. Cyber Supply Chain Threat Analysis and Prediction Using Machine Learning and Ontology. In Proceedings of the 17th IFIP WG 12.5 International Conference, AIAI 2021, Hersonissos, Greece, 25–27 June 2021; Volume 627, pp. 518–530. [Google Scholar] [CrossRef]
- Wang, X.; Chen, R.; Song, B.; An, J.; Jiang, J.; Wang, J.; Yang, P. Learning Cyber Threat Intelligence Knowledge Graph Embedding with Heterogeneous Relation Networks Based on Multi-Head Relational Graph Attention. In Proceedings of the 2022 IEEE Smartworld, Ubiquitous Intelligence & Computing, Scalable Computing & Communications, Digital Twin, Privacy Computing, Metaverse, Autonomous & Trusted Vehicles (SmartWorld/UIC/ScalCom/DigitalTwin/PriComp/Meta), Haikou, China, 15–18 December 2022; pp. 1796–1803. [Google Scholar] [CrossRef]
- Wang, Y.; Lang, B.; Xiao, N.; Chen, Y. Cyber Threat Indicators Association Prediction Based on Weighted Fusion of Semantic and Topological Information. In Proceedings of the 2022 5th International Conference on Algorithms, Computing and Artificial Intelligence, Sanya, China, 23–25 December 2022. [Google Scholar] [CrossRef]
- Piplai, A.; Joshi, A.; Finin, T. Offline RL+CKG: A hybrid AI model for cybersecurity tasks. In Proceedings of the AAAI 2023 Spring Symposium on Challenges Requiring the Combination of Machine Learning and Knowledge Engineering (AAAI-MAKE 2023), San Francisco, CA, USA, 27–29 March 2023; Volume 3433. [Google Scholar]
- Zhang, S.; Li, S.; Chen, P.; Wang, S.; Zhao, C. Generating Network Security Defense Strategy Based on Cyber Threat Intelligence Knowledge Graph. In Proceedings of the First International Conference, ICENAT 2022, Shenzhen, China, 15–17 November 2023; Volume 1696, pp. 507–519. [Google Scholar] [CrossRef]
- Zhang, Y.; Chen, J.; Cheng, Z.; Shen, X.; Qin, J.; Han, Y.; Lu, Y. Edge propagation for link prediction in requirement-cyber threat intelligence knowledge graph. Inf. Sci. 2024, 653, 119770. [Google Scholar] [CrossRef]
- Liu, C.; Wang, B.; Wang, Z.; Tian, J.; Luo, P.; Yang, Y. TCFLTformer: TextCNN-Flat-Lattice Transformer for Entity Recognition of Air Traffic Management Cyber Threat Knowledge Graphs. Aerospace 2023, 10, 697. [Google Scholar] [CrossRef]
- Kaiser, F.K.; Dardik, U.; Elitzur, A.; Zilberman, P.; Daniel, N.; Wiens, M.; Schultmann, F.; Elovici, Y.; Puzis, R. Attack Hypotheses Generation Based on Threat Intelligence Knowledge Graph. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4793–4809. [Google Scholar] [CrossRef]

| Reference | Year Published | Brief Summary | Domain |
|---|---|---|---|
| [31] | 2013 | Proposed the use of Semantic Web and Ontology concepts to define an approach for analyzing security logs for security issues identification. | Web Attacks |
| [32] | 2013 | Introduced S-MAIDS, a semantic approach to IDRS modeling using OWL ontologies. | IDRS |
| [33] | 2014 | Proposed a taxonomy for the classification of existing CTI sharing technologies. | CTI |
| [34] | 2015 | Proposed the DFAX ontology for representing and exchanging digital information. | Digital forensic information |
| [36] | 2015 | Presented an ontology for the enhancement of cyber defense against APTs. | APT |
| [37] | 2016 | Proposed an ontology for the efficient organization of OSINT and threat indicators. | CTI |
| [38] | 2017 | Proposed an ontology-based framework for the IoT environment to safeguard against APTs. | APT in IoT Environments |
| [39] | 2017 | Defined an ontology for threat analytics. | CTI |
| [40] | 2018 | Presented a CTI ontology for the analysis and classification of Sysmon logs. | CTI |
| [41] | 2019 | Proposed an approach of analyzing real-time network log data within a NSM environment by using a graph database. | NSM |
| [42] | 2019 | Proposed an ontology of metrics for security management. | Cybersecurity Management |
| [43] | 2019 | Proposed an ontology knowledge base that can define APT attack patterns and recommend security requirements. | APT |
| Reference | Year Published | Brief Summary | Domain |
|---|---|---|---|
| [44] | 2020 | Proposed a STIX-based network security KG ontology modeling method for the analysis of the concepts of network security knowledge. | Network Security |
| [45] | 2020 | Proposed an enriched cybersecurity KG by merging information about malware behavior data. | CTI |
| [23] | 2020 | Proposed MALOnt, an ontology for malware threat intelligence. | Malware Threat Intelligence |
| [46] | 2020 | Constructed a KG that stores CTI regarding various medical devices. | Vulnerabilities of Medical Devices in IoT |
| [25] | 2021 | Proposed an ontology for XSS attacks. | XSS Attacks |
| [49] | 2021 | Proposed an ontology-based framework with logical inference for the detection of cyber attacks. | Cyber Attacks and Incidents |
| [50] | 2021 | Presented an ontological approach for the automatic inference of threat actor types based on a standardized set of attributes. | Threat Actor |
| [10] | 2021 | Proposed a STIX-based ontological reasoning approach for potential cyber threats | CTI |
| [51] | 2021 | Constructed an ontology for cyber risk monitoring | Cyber Risk Monitoring |
| Reference | Year Published | Brief Summary | Domain |
|---|---|---|---|
| [52] | 2022 | Proposed a cloud-native ontology capable of connecting security-related data from different cloud sources to enhance CTI. | Cloud-native cyber incident response |
| [53] | 2022 | Proposed a CTI ontology that enables the automation and analysis of the available threat intelligence. | CTI |
| [54] | 2022 | Developed a generic ontology for the representation of IoT objects to encapsulate vulnerabilities, attack attribution, impact evaluation and mitigation strategies within a smart home environment. | Risk Assessment in IoT Environments |
| [26] | 2022 | Proposed an ontology for risk assessment modeling. | Security Risk Information |
| [56] | 2022 | Proposed an ontology and an automated information extraction method, capable of integrating the parsed information from CTI reports into each instance. | CTI |
| [57] | 2022 | Proposed AttackKG, a KG used for the automated extraction of attack behavior graphs from CTI reports. | CTI |
| [60] | 2022 | Proposed TINKER, a framework that utilizes ontologies and KGs for capturing cyber threat information. | CTI |
| [61] | 2022 | Supported the use of graph databases for near real time network log monitoring. | Network Log Files |
| [28] | 2022 | Presented a KG based on kernel audit logs for the efficient organization of big data, enabling querying during threat hunting activities. | Cyber Threat Hunting |
| Reference | Year Published | Brief Summary | Domain |
|---|---|---|---|
| [62] | 2023 | Constructed a Unified Ontology encompassing APT techniques, weaknesses, vulnerabilities, and defense countermeasures. | APT |
| [63] | 2023 | Presented a security ontology for cloud, edge and on-premises environments and used it to determine the most appropriate security mechanisms. | CTI |
| [64] | 2023 | Proposed OBSQL, an ontology for detecting blind SQL weaknesses. | Blind SQL Injection |
| [65] | 2023 | Defined an ontology for the description of different types of anomalies and proposed an approach that merges the ontology with previously developed models for CTI. | Risk Management |
| [24] | 2023 | Proposed an event-based threat intelligence ontology for threat detection and response scenarios. | CTI |
| [68] | 2023 | Introduced the ADACO model, constructed by integrating data from multiple cybersecurity databases. | CTI |
| Reference | Year Published | Brief Summary | Tools |
|---|---|---|---|
| [69] | 2014 | Proposed an RDF metadata generation mechanism for cybersecurity information management. | RDF metadata generation |
| [71] | 2015 | Developed a reasoning mechanism for query execution when addressing different cyber situations. | Reasoning, querying |
| [9] | 2016 | Explored the overlap between different information exchange standards using ontologies and library science techniques. | Library science methods |
| [73] | 2016 | Proposed “net vulnerability”, a metric for measuring security risks of networked systems. | Novel metric |
| [75] | 2017 | Leveraged an ontology to gain knowledge about an IoT environment. | OWL |
| [76] | 2018 | Presented a novel description logic-based formalism to model fuzzy and uncertain cyber-related information. | Fuzzy logic |
| [81] | 2019 | Demonstrated the efficiency of semantic technology within CTI use cases by using the STIX representation and the Maltego tool. | Semantics |
| [83] | 2019 | Introduced a SIEM-based KG and MalRank, a graph-based inference algorithm for maliciousness score estimation. | Graph inference algorithm |
| [66] | 2019 | Developed a model relying on ontologies to enhance the risk management capabilities of organizations. | OWL, Reasoning |
| [85] | 2020 | Developed an ontology-driven CFRaaS model for digital evidence gathering. | Description logic |
| [86] | 2021 | Proposed an APT attacks recommendation tool for attack scenario analysis and inference. | Similarity measures |
| [87] | 2022 | Proposed OnToRisk, an ontology-driven risk management analysis method. | Protege, OWL |
| [88] | 2023 | Proposed the KGaaS framework for the generation and maintenance of domain-specific KGs. | Cypher, Natural Language, RDF |
| [89] | 2023 | Developed a novel framework for cyber insurance policy suggestion. | RDF, SPARQL, IR, AI |
| Reference | Year Published | Brief Summary | Technology Used | Evaluation Scores |
|---|---|---|---|---|
| [59] | 2017 | Introduced TTPDrill, a tool that automates threat action knowledge extraction from unstructured reports. | NLP, IR | Precision Recall |
| [27] | 2020 | Created a knowledge extraction pipeline from AARs to fill a cybersecurity KG. | CRF, Gibbs’ sampling, RelExt | Precision Recall F1-score |
| [90] | 2020 | Proposed a model for enhancing NER. | BiLSTM, CRF | F1-score |
| [91] | 2021 | Proposed SECURITYKG, a system for automating the processing of open-source CTI. | NLP | - |
| [92] | 2021 | Created Open-CyKG for presenting APT reports as a queryable KG. | BiGRU, CRF, XLM-RoBERTa | Dataset: Microsoft (CTI) Recall Precision F1-score |
| [93] | 2021 | Used a DL model for knowledge extraction and constructed a cyber threat ontology. | BERT, BiLSTM, CRF | Recall Accuracy |
| [29] | 2022 | Proposed a CTI extraction system using DL models and constructed a KG. | BERT, BiLSTM, CNN | Entity extraction Precision Recall F1-score Accuracy Coreference resolution Precision Recall F1-score Relation extraction Precision Recall F1-score |
| [95] | 2022 | Proposed APTKG, a framework that constructs automatically KGs from open-source APT reports. | BiLSTM, CRF, BERT, CNN, Stanford CoreNLP | F1-score |
| [97] | 2023 | Proposed K-CTIAA to automate CTI analysis with pre-trained models and KGs. | Pre-trained models | Precision Recall F1-score |
| [100] | 2023 | Leveraged LLMs to build a CTI KG. | LLM, ChatGPT | Entity recognition (Relation extraction) Precision Recall F1-score |
| [102] | 2023 | Created CSKG4APT for the organization of APT knowledge from bilingual documents. | BERT | English Macro (Micro) Precision Recall F1-score |
| Reference | Year Published | Brief Summary | Technology Used | Evaluation Scores |
|---|---|---|---|---|
| [103] | 2019 | Used ML and DL methods with ontology mapping to address the cyber-related issues in Nepal. | RF, DL | RF (DL) Accuracy Precision Recall |
| [104] | 2019 | Proposed AHG, which applies link prediction techniques on CTI-derived KGs. | Link prediction, collaborative filtering | Algorithm Precision SupLP: CF(): LPPorjD: CF(): |
| [105] | 2019 | Introduced the RelExt system for predicting relationships between cybersecurity entities. | FFNN | Accuracy |
| [106] | 2020 | Proposed a novel ML- and DL-based mechanism for evaluating quantitatively the relevance of cybersecurity text data. | USE, CRFClassifier, Logistic Regression | Accuracy |
| [108] | 2021 | Used hierarchical clustering techniques to unveil hidden patterns in the MITRE KG. | Hierarchical clustering | - |
| [109] | 2021 | Created the SecKG schema, generated a KG and applied a KGCN for attack prediction. | KGCN | - |
| [110] | 2021 | Associated provenance with the entities and relations of a cybersecurity KG to ensure the authenticity of the data. | NLP | - |
| [111] | 2021 | Leveraged transformer-based models to produce fake CTI data and poison a cybersecurity KG and corpus. | Transformers, GPT-2 | - |
| Reference | Year Published | Brief Summary | Technology Used | Evaluation Scores |
|---|---|---|---|---|
| [112] | 2021 | Modelled APT attacks as an ontology and used supervised AML methods to deceive classifiers during training and testing. | AML | RF (GBoost) Before adversarial attacks: Accuracy After adversarial attacks: Accuracy |
| [113] | 2021 | Combined cyber supply chain security ontology concepts and ML for threat analysis and prediction. | RF, GBoost | Accuracy = |
| [114] | 2022 | Proposed a GNN to learn KG embeddings and constructed a dataset from APT reports. | GNN | Entity Classification (Link Prediction) MR = 201 (223) MRR = 0.316 (0.345) Hits@1 = 0.232 (0.267) Hits@3 = 0.369 (0.394) Hits@10 = 0.607 (0.625) |
| [115] | 2022 | Proposed a Ctiap model that fuses semantic and topological features of a KG to predict relations. | Link prediction, NN | Accuracy Macro F1-score |
| [116] | 2023 | Examined the guidance of RL algorithms with KGs. | RL, CQL | Hits@10 for different malware families |
| [117] | 2023 | Proposed a CTI ontology and KG schema and used link prediction methods to infer new knowledge. | Link prediction | - |
| [118] | 2024 | Proposed EGNN for edge information propagation and applied link prediction on a constructed KG. | GNN | Dataset: FB15K-237, WN18RR, RCTI, WN18 hit@10: , , , hit@3: , , , hit@1: , , , MR: 168, 2828, 3822, 250 MRR: , , , |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bratsas, C.; Anastasiadis, E.K.; Angelidis, A.K.; Ioannidis, L.; Kotsakis, R.; Ougiaroglou, S. Knowledge Graphs and Semantic Web Tools in Cyber Threat Intelligence: A Systematic Literature Review. J. Cybersecur. Priv. 2024, 4, 518-545. https://doi.org/10.3390/jcp4030025
Bratsas C, Anastasiadis EK, Angelidis AK, Ioannidis L, Kotsakis R, Ougiaroglou S. Knowledge Graphs and Semantic Web Tools in Cyber Threat Intelligence: A Systematic Literature Review. Journal of Cybersecurity and Privacy. 2024; 4(3):518-545. https://doi.org/10.3390/jcp4030025
Chicago/Turabian StyleBratsas, Charalampos, Efstathios Konstantinos Anastasiadis, Alexandros K. Angelidis, Lazaros Ioannidis, Rigas Kotsakis, and Stefanos Ougiaroglou. 2024. "Knowledge Graphs and Semantic Web Tools in Cyber Threat Intelligence: A Systematic Literature Review" Journal of Cybersecurity and Privacy 4, no. 3: 518-545. https://doi.org/10.3390/jcp4030025
APA StyleBratsas, C., Anastasiadis, E. K., Angelidis, A. K., Ioannidis, L., Kotsakis, R., & Ougiaroglou, S. (2024). Knowledge Graphs and Semantic Web Tools in Cyber Threat Intelligence: A Systematic Literature Review. Journal of Cybersecurity and Privacy, 4(3), 518-545. https://doi.org/10.3390/jcp4030025










